Network Technology
Foundations
© 2004 ProsoftTraining
All Rights Reserved
Lesson 4:
Hardware and
Operating System
Maintenance
Objectives
Identify the characteristics of motherboards
Identify common IRQ, I/O address and DMA settings
Identify IDE/ATA, EIDE/ATA-2, SATA and SCSI traits
Identify NICs and common peripheral ports
Identify the characteristics of CD-ROMs and DVDs
Describe the characteristics of file system types
Describe the uses of file system management tools
Identify and suggest corrective measures for
operating system boot problems and application
failures
Identify methods to remotely manage and
troubleshoot workstations
Basic Hardware
and System Maintenance
Fix hardware problems by ensuring:
• Components are plugged in
• Components are turned on
• Components are connected properly in
order to operate (such as connecting the
keyboard to the computer)
Periodically clean hardware components
Establish a preventive maintenance plan
Motherboard
Main circuit board in a computer
Must be securely fastened to system chassis
Should never touch anything metal, except
through proper connections
Most motherboard components are soldered on
and no longer replaceable
If components fail (except for memory and the
microprocessor), the entire motherboard needs
to be replaced
IRQs, I/O Addresses and DMA
IRQs — hardware lines used to identify
when a device wants to communicate with
the processor
• Example: When a printer has finished
printing, it sends an interrupt signal to
the computer so the computer can
decide what to process next
I/O address — memory location that allows
the system processor and system devices
to communicate
DMA — allows a device to access system
memory directly, bypassing the processor
Mass Storage
Device Interfaces
To communicate with a motherboard, mass
storage devices need to be connected to
the motherboard through an interface
Three most common interfaces are:
• IDE
• EIDE
• SCSI
IDE/EIDE
IDE is also known as Advanced Technology
Attachment (ATA)
EIDE (ATA-2) is an enhanced version of IDE that
provides higher drive capacities
IDE/EIDE interface cables are long, thin and gray
in appearance
Serial ATA (SATA)
SATA provides faster speeds than standard ATA
SATA devices are connected using a cable that
somewhat resembles a small Category 5 Ethernet
cable
Small Computer
System Interface (SCSI)
With SCSI, multiple devices can be
connected to a single controller in a daisy
chain configuration
You can attach as many as 127 internal or
external SCSI devices to a single controller
SCSI devices include hard disk drives,
floppy disk drives, printers, scanners and
tape drives
SCSI daisy chain must be terminated at
both ends and only at the ends
Resolving
Device ID Conflicts
LUN conflicts are a common cause of
difficulty when installing a SCSI device
All SCSI device numbers and LUNs must be
unique
Network Interface Card
Each network device must have a network
interface card (or network adapter card)
The network adapter makes the physical
connection between the device and the network
cabling
The network adapter converts the data from
the computer into a format appropriate for
transmission over the network
Transceiver — the network adapter component
that handles data transmission
Common Peripheral Ports
Common Peripheral Ports (cont’d)
PS/2-style ports are for the mouse and keyboard
Serial ports:
• Communicate using serial asynchronous
communication
• Are used for serial communication devices
Parallel ports:
• Communicate using parallel communication
• Are used for parallel communication devices
Common Peripheral Ports (cont’d)
USB ports:
• Support asynchronous and isochronous
transmissions for data transfer
• Communicate using serial communication
• Support as many as 127 peripheral devices in
a daisy chain configuration
FireWire (IEEE 1394):
• A high-speed serial interface to which you can
daisy chain as many as 63 peripheral devices
• Good for devices that need to transfer large
amounts of data
Power Requirements
Electricity is measured according to different
standards in North America and Europe
Computing and networking equipment is also
manufactured to different standards
When traveling from North America to Europe,
you will need:
• A special plug adapter
• A power inverter
CD-ROM
CD-ROM — an optical storage device from which
data can be read only
CD-ROM drives use common mass storage
interfaces
Writable CD-ROM devices allow you to create, or
"burn," your own data and audio CDs
• CD-R (CD-recordable) — write data once
• CD-RW (CD-rewritable) — write data multiple
times
DVD
DVD — optical storage device from which data
can be read only
DVDs are similar to CD-ROMs but have higher
storage capacity
• Initial DVD standard provided 4.7 GB of
storage capacity
• Current DVD standards support dual-layer
discs with a storage capacity of 8.5 GB
• Double-sided disc standard supports 9.4 GB
when writing to one side or 17 GB total when
writing to both sides
CD-ROM and
DVD Maintenance
Keep the drives closed when they are not in
use and check all media for foreign matter
before inserting into the drive
CD-ROMs and DVDs should be handled only
by the edges
Avoid scratching the disc surface
Never directly touch or try to manually
clean the laser
Brush away and vacuum accumulated dust
Manually eject a stuck disc by inserting a
wire into the small hole on the face of the
drive, then pressing hard until the disc is
ejected
Software Licensing
When you purchase software, you are
purchasing the right to use the software under
certain restrictions
These restrictions are outlined in the license
agreement
When you load software, the license agreement
typically displays during the installation process
You must indicate that you have read and
understood the agreement before the
installation procedure will allow you to continue
Software Licensing (cont’d)
Apart from legal consequences, using
unlicensed software can also mean:
• No documentation
• No warranties
• No technical product support
• Greater exposure to software viruses,
corrupt disks, or otherwise defective
software
• Ineligibility for software upgrades
Partitions and
Logical Drives
When installing an operating system on a
new computer or after recovering from a
hard disk failure, prepare the hard disk for
use by:
• Partitioning the hard disk
• Creating logical drives
• Formatting logical drives
Disk Partitioning
Partition disks to
divide total
storage space
Primary partition
— the system’s
boot drive, used
for system
startup
Extended
partition — the
remaining drive
space after you
create the
primary partition
Logical Disk Drives
A disk partition
must be
assigned a
logical drive
identifier
A primary
partition is
treated as a
single logical
drive
Logical Drive Format
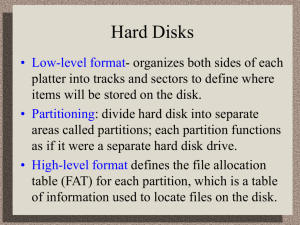
Low-level format:
• Prepares the hard disk before disk partitions
can be defined
• Primarily the responsibility of the hard disk
manufacturer
High-level format:
• Logical drive formatting that prepares the
drive for use by the operating system
• Creates the file system root directory and
the files used to track disk space use
File System Types
Primary partitions and logical drives must be
formatted so the operating system can use them
Formatting creates the file system by adding
information about how files should be stored on
the drive to organize and manage disk storage
File system types include:
• FAT, FAT32 and NTFS (Windows)
• Ext3 and ReiserFS (Linux)
File and
Directory Permissions
NTFS allows you to set permission bits on
system resources
In NTFS, you can protect files so that only
certain users or groups of users can read
them
Concerns:
• If permissions are applied improperly,
users may take security for granted
• Improperly set permissions can disrupt
an operating system
Convert Utility
Information about the files on an NTFS volume
and their attributes is stored in the MFT
Convert utility — used to convert a partition or
logical drive from FAT or FAT32 to NTFS
convert drive /FS:NTFS [/v]
Disk Defragmenter Utility
As files are created and deleted, a partition can
become severely fragmented
Fragmented files are no longer located in
contiguous clusters
You can use the Disk Defragmenter utility to
defragment hard disks and put files back together
in a contiguous format
Chkdsk Utility
You can use the Chkdsk utility in Windows
NT/2000/XP to:
• Create and display a status report for a disk
based on its file system
• List and correct errors on the disk
• Display the status of the disk in the current
drive
Disk Cleanup Utility
Use the Disk Cleanup utility to recover the disk
space used by:
• Temporary files
• Unused applications
• Files in the Recycle Bin
• Files you downloaded as part of Web pages
• Files created when Chkdsk attempted to
recover lost file fragments
Backup and
Restore Utilities
Keep a current backup of all data files to
ensure that data can be recovered if a hard
drive fails
When you back up data, you store copies of
folders and files to a source other than your
computer's hard disk
You restore data when you need to access
the backed up data
Troubleshooting Software
Software troubleshooting refers to anything other
than problems caused by system hardware
Software problems can be caused by:
• Bugs
• Corrupted files
• Incompatibilities
• Virus infections
Operating System
Boot Problems
Error: No operating system
Operating system files missing
Hard disk or controller failure
Startup failure
Blue Screen
of Death (BSOD)
Blue screen that indicates that a critical
operating system failure has occurred
during startup
To troubleshoot:
• Restart the system in Safe mode and use
the Last Known Good Configuration
option
• Reinstall the operating system
• Attempt to diagnose the problem by
parsing the dump file
System Lockup
Lockup causes:
• Applications that are incompatible with the
operating system or with a hardware
component
• IRQ conflicts
• Related problems that you may be able to find
in the system log file
Power down your system by manually pressing
the power key continually for five seconds
Application Failures
Application failure causes:
• Low system RAM
• Current logon environment may have crashed
• Improper permissions
• Improper system resolution or color levels
View the system log
• Windows Event Viewer
• UNIX/Linux “messages”
Application Failures (cont’d)
Windows protection error causes:
• Device drivers that may not be written
specifically for your operating system
• Applications or utilities that attempt to bypass
the operating system and directly access local
system hardware
Dr. Watson — Windows application debug
program that creates a system error report
Application Failures (cont’d)
Application installation and loading failures:
• Application will not load into memory
• Application can cause an illegal operation,
resulting in the blue screen of death
• Application may not install at all
Remote Management
and Troubleshooting
Telnet — TCP/IP command that establishes
a remote connection with a server
SSH — protocol and command interface
that can gain secure access to a remote
computer
VNC — program that controls a remote
computer
• VNC consists of two components:
A server that listens to a specific port
The viewer, which shows the remote
system’s logon environment
Remote Management
and Troubleshooting (cont’d)
Remote Desktop — Windows XP service
used to gain access to a Windows session
that is running on another computer
• Allows multiple users to have active
sessions on a single computer
• Allows you to switch from one user to
another on the same computer
Remote Assistance — Windows XP service
used to seek help from a remote user