-
CIA
Confidentiality, Integrity, Availability
-
Confidentiality
Confidentiality prevents the unauthorized disclosure of data
Encryption: scrambles data to make it unreadable by unauthorized people.
Access controls:
-Identification ( claim to be a user)
-Authentication (prove to be the user)
-Authorization (permissions)
-
Integrity
Integrity: provides assurance that data has NOT changed
-Hashing enforces integrity (MD5, SHA1)
-
Availability
Availability: indicates data is available WHEN needed
-Redundancy and fault tolerance help availability.
-Redundancy adds duplication and provides fault tolerance
-Availability is increased by RAID, failover clusters, NIC Teaming, Backups, and Generators.
-
Availability (II)
Scalability satisfies the needs of the system. It scales
-UP - > increasing Hardware resources (RAM, Storage)
-OUT - > Increase nodes or servers
-DOWN - > decreasing Hardware resources (RAM, Storage)
-IN - > decrease nodes or servers
Elasticity: Capability of scaling dynamically
-
Availability (III)
Patching
Resiliency: Helps systems heal themselves or recover from faults with minimal downtime. Resiliency processes expect components to retry processes.
There should always be a balance of security vs resources
TCO: Total Cost of ownership.
-
Risk
Risk is the possibility or likelihood of a threat exploiting a vulnerability resulting in loss.
Threat is any circumstance or event that has the potential to compromise CIA
Vulnerability is a weakness
-
Type of threats
Internal or external.
Natural or human-made.
Intentional or accidental.
-
Risk mitigation
1- Reduces the chance that a threat exploits a vulnerability.
2- Reduces the risk impact by using security controls.
-
Security Control Categories
Managerial: Administrative, focuses on managing risk. It is documented in written policies.
Operational: ensure day-to-day operations complies. It is implemented by people.
Technical: Uses technology such as hardware, software, firmware, etc. to reduce vulnerabilities. It is implemented with technology.
-
Security Controls Categories - Managerial examples
-Risk assessment
-Vulnerability assessment
-
Security Controls Categories - Operational examples
-Awareness and training
-Configuration management: uses baselines
-Media protection
-Physical protection (cameras, door locks, and environmental controls such as heating and ventilation systems)
-
Security Controls Categories - Technical examples
-Encryption
-Antivirus
-IPS
-IDS
-Firewall
-Least privilege principle
-
Security Control Types
Preventative
Detective
Corrective and recovery
Physical
Deterrent
Compensating
Response
-
Security Control Types - Preventative examples
-Hardening
-Training
-Security guards
-Change management
-Account disablement
-IPS
-
Security Control Types - Detective examples
-Log monitoring
-SIEM
-Security audit
-Video surveillance
-Motion detection
-IDS
-
Security Control Types - Corrective and recovery examples
-Backup and system recovery
-Incident handling processes
-
Security Control Types - Physical examples
-Bollards
-Barricades
-Access Control Vestibules (ACVs)
-Signs
-Locks
-
Security Control Types - Deterrent examples
-Guards
-Cable locks
-Physical locks
-
Security Control Types - Compensating examples
-Alternative controls used instead of primary controls
-Time based one time password
-
Security Control Types - Response examples
Incident response control
Create security policies and train personnel
-
NIST SP 800-53 Rev 5
The NIST Special Publication 800-53, Security and Privacy Controls for Information Systems and Organizations is a set of recommended security and privacy controls for federal information systems and organizations to help meet the Federal Information Security Management Act (FISMA) requirements.
-
Command line tools
ping/hping
ipconfig/ifconfig
/ip
netstat/netstat
tracert/traceroute
pathping/
arp/arp
-
ping
check connection of remote systems
verify name resolution
Also used to check security posture by making sure firewalls and IPS are blocking ICMP traffic
-
hping
Same as ping but can use TCP UDP or ICMP protocols
-
ipconfig
/all
/displaydns
/flushdns
-
ifconfig
- a same as ipconfig /all
eth0 promisc (-promisc)
eth0 allmulti (-allmulti)
-
ip
ip link show
ip set eth0 up
ip -s link (stats)
-
netstat
used to view active TCP/IP connections
ESTABLISHED
LISTEN
CLOSE_WAIT
TIME_WAIT
no parameter -> open connections
-a -> open connections + listening ports
-r -> Routing tables
-e -> bytes sent/received
-s -> packets by specific protocols
-p -> specific protocol
-n -> address and port number in numerical order
-
tracert/traceroute
lists all the routes between 2 systems (measured in hops)
hostnames and RTT (round trip times)
-
pathping
tracert and then ping to each of the hops
-
arp
Displays and modifies IP-to-physical address translation tables used by ARP protocol
-
Basic Linux commands
cat -> see contents
| pipe
more display one page at a time
cat file.ext | more
grep to find a specific string in a file
grep "failed" log.txt ~ cat log.txt | grep "failed"
head -n (default 10)
tail -n (default 10)
logger append to /var/log/syslog
journalctl displays logs. may use --since or --until
chmod octal -777 or -444 rwx-rwx-rwx owner/owner group/all others
-
Windows log - Event viewer
-Security logs
-System logs
-Application logs
-
Network logs
Router-firewall-IDS-IPS logs
-
Webserver logs
Host- userID -authuser - date - request -data
-
SIEM - Security Information event management
Combines the services of security event management (SEM) and security information management (SIM) solutions.
A SEM provides real-time monitoring, analysis, and notification of security events, such as suspected security incidents.
A SIM provides long-term storage of data, along with methods of analyzing the data looking for trends, or creating reports needed to verify compliance with laws or regulations.
-
SIEM additional capabilities I
-Log collector
-Data inputs (from various network sources; router, firewalls, IDS, IPS, and various systems such as web servers, proxies, and databases
-Log aggregation (normalization)
-Correlation: Pattern detection
-
SIEM additional capabilities II
-Reports
-Packet capture
-User behavior analysis (UBA): Focuses on what users are doing, such as what applications are launching and their network activity
-Sentiment analysis: use of UBA to detect unwanted behavior *AI*
-
SIEM additional capabilities III
-Security monitoring: predefined alerts, which can provide continuous monitoring of systems and provide notifications of suspicious events
-Automated triggers: Triggers cause an action in response to a predefined number of repeated events.
-Time synchronization: All servers sending data to the SIEM should be synchronized with the same time. Use of GMT
-
SIEM additional capabilities IV
-Event deduplication. Deduplication is the process of removing duplicate entries
-Logs/WORM. A SIEM typically includes methods to prevent anyone from modifying log entries. This is sometimes referred to as write once read many (WORM).
-
Location of SIEM
It’s common to locate the SIEM within the private network, even if it collects data from a screened subnet.
-
Elements of a SIEM dashboard
- Sensors
- Alerts
- Sensitivity: setting the sensitivity levels to limit false positives while avoiding false negatives
-Correlation
-Trends
-
Syslog protocol
Specifies a general log entry format and the details on how to transport log entries
Linux systems include the syslogd daemon, which is the service that handles the syslog messages.
Historically, uses UDP 514. Nowadays uses TCP 6514 with TLS
-
Syslog-ng and Rsyslog
Syslog-ng extends syslogd, allowing a system to collect logs from any source. It also includes correlation and routing abilities to route log entries to any log analysis tool.
Rsyslog came out later as an improvement over syslog-ng.
-
NXLog
Similar to rsyslog and syslog-ng. However, it supports log formats for Windows, such as event log entries.
-
Linux logs
var/log/syslog stores all system activity
var/log/messages wide variety of general system messages
var/log/boot.log
var/log/auth.log successful and un- logins
var/log faillog failed logins
var/log/kern.log
var/log/httpd Used in Apache for webservers
-
Authentication Management
Identification: Claiming identity (username)
Authentication: Proves identity (password)
Authorization: Access level
Accounting: Tracking via activity logs (accountability)
-
Authentication Factors
Something you know: password / pin
Something you have: smart cards / token
Something you are: biometric identification
-
Something you know
Typically refers to a shared secret, such as password, static code or pin.
Least secure.
-
Password Complexity
Should 3 out of 4:- Uppercase characters (26 letters A–Z)
- Lowercase characters (26 letters a–z)
- Numbers (10 numbers 0–9)
- Special characters (such as !, $, and *)
- Minimum length 8, recommended 12
- Expiration: maximum password age
-
Password History
Remembers a number of past passwords to avoid reusing them.
-
Password Vault
Password Manager (i.e. Chrome password manager)
-
Password Keys
Bootable optical disc or bootable USB flash drive. After rebooting the system to the device, they allow you to recover or reset all user and administrator passwords.
-
Knowledge-Based Authentication
Static KBA: Set of questions you have to answer.
Dynamic KBA: Questions that only user will know. Allows a short time to answer.
-
Account Lockout
Threshold: Maximum number of attempts.
Duration: How long account will be locked. If value is 0 is locked until admin unlocks it.
Account lockout policies thwart some password attacks, such as brute force attacks and dictionary attacks
-
Changing Default Passwords
A basic security practice is to change these defaults before putting a system into use.
Changing defaults also includes changing the default name of the Administrator account.
-
Training User About Password Behaviors
Creating strong passwords, not using the same password with other systems, and never giving their password to someone else.
-
Something You Have
The something you have authentication factor refers to something you can physically hold, like smart cards, Common Access Cards, and hardware tokens.
-
Smart Card Authentication
Smart cards are credit card-sized cards that have an embedded microchip and a certificate.
- Embedded Certificate.
- Public Key Infrastructure (PKI).
Smart cards are often used with dual-factor authentication where users have something (the smart card) and know something (such as a password or PIN).
They are used to gain access to secure locations and to log on to computer systems.
-
Token Key
A token key or (sometimes called a key fob or just a token) is an electronic device about the size of a remote key for a car.
Synced with a server. One-time use, rolling password.
RSA sells RSA Secure ID, a popular token used for authentication.
-
HOTP and TOTP
Hash-based Message Authentication Code (HMAC) uses a hash function and cryptographic key for many different cryptographic functions.
HMAC-based One-Time Password (HOTP) is valid until used.
Time-based One-Time Password (TOTP) is a One-time passwords, typically expire after 30 seconds, but the time is adjustable.
-
Authentication Applications
Software that uses HOTP or TOTP to create software tokens used within the application.
i.e. Google Authenticator
-
Two Factor Authentication
Adds an extra layer of security to accounts.
SMS could be used but not safe, could be easily read.
Push notifications send messages to users on another device.
-
Something You Are
The something you are authentication factor uses biometrics for authentication.
This is the strongest method.
-
Biometric Methods
Biometric methods include:
- fingerprints
- palm veins
- retina scans
- iris scans
- voice recognition
- facial recognition
- gait analysis.
Iris and retina scans are the strongest biometric methods mentioned in this section, though iris scans are used instead of retina scans because retina scans are intrusive and reveal private medical issues. Facial recognition and gait analysis can bypass the enrollment process when done for identification instead of authorization.
-
Biometric Efficacy Rates
The biometric efficacy rate refers to the performance of the system under ideal conditions.
False Acceptance: Accepts a non registered user.
- FAR (False Acceptance Rate) identifies the percentage of times false acceptance occurs.
False Rejection: Incorrectly rejects a registered user
- FRR (False Rejection Rate) identifies the percentage of times false rejection occurs.
True Acceptance: Correctly identifies a registered user.
True Rejection: Correctly rejects an unknown user.
-
Crossover Error Rate (CER)
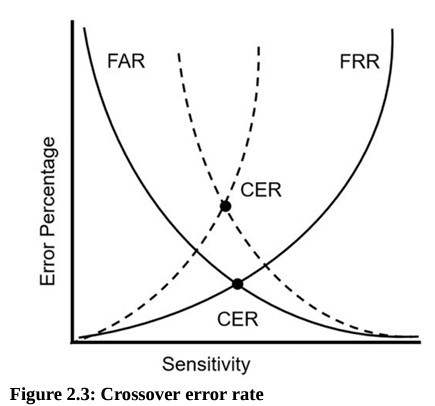
The lower the crossover point the more accurate.
-
Two-Factor and Multifactor Authentication
Must be from different factors to be valid.
-
Authentication Attributes
Somewhere You Are: Impossible travel time.
Something You Can Do: Draw on a touch screen.
Something You Exhibit: Badge, Common Access Cards or Personal Identity Verification.
Someone You Know: Someone is vouching for you.
-
Authentication Log Files
Authentication log files can track both successful and unsuccessful login attempts.
- What happened is either a login success or failure.
- When it happened is determined by the time and date stamps.
- Where it happened is typically an IP address or computer name.
- Who or what did it refers to the user account.
-
Account Management
Account management is concerned with the creation, management, disablement, and termination of accounts.
-
Credential Policies and Account Types
Credential policies define login policies for different personnel, devices, and accounts.
-
Account Types i
Personnel or end-user accounts. Most accounts are for regular users or the personnel working in the organizations. Access based on role.
Administrator and root accounts. Are privileged accounts that have additional rights and privileges beyond what a regular user has.
Service accounts. Some applications and services need to run under the context of an account, and a service account fills this need.
-
Account Types ii
Device accounts. Computers and other devices also have accounts though it isn’t always apparent.
Third-party accounts. Third-party accounts are accounts from external entities that have access to a network.
Guest accounts. Windows OS include a Guest account. These are useful if you want to grant someone limited access to a computer or network without creating a new account.
Shared and generic account/credentials. An organization can create a regular user account that temporary workers will share. Shared accounts are discouraged for normal work.
-
Privileged Access Management (PAM)
PAM implements the concept of just-in-time administration. Also known as Privileged Account Management.
Applies for accounts with elevated privileges, such as administrator or root-level accounts.
Some capabilities include allowing authorized users to access the administrator account without knowing the password, logging all elevated privileges usage, and automatically changing the administrator account password.
-
Require Administrators to Use Two Accounts
They use one for regular day-to-day work. It has the same limited privileges as a regular end user. The other account has elevated privileges required to perform administrative work, and they use this only when performing administrative work.
-
Prohibiting Shared and Generic Accounts
Due to lack of accountability.
-
Disablement Policies
Specifies how to manage accounts in different situations.
Terminated Employee: Disable as soon as possible.
Leave of Absence: Disable while away.
Delete Account: After no longer needed, usually 60 to 90 days. Disabling is better than deleting first.
-
Time-Based Logins
Ensure that users can only log on to computers during specific times. Also known as Time-of-day restrictions.
-
Account Audits
An account audit looks at the rights and permissions assigned to users and helps enforce the least privilege principle.
Permission auditing reviews help ensure that users have only the access they need and no more and can detect privilege creep issues.
-
Authentication Services
Single Sign-On
Kerberos
SSO and Federation
SAML
OAuth
OpenID and OpenID Connection
-
Single Sign-On
Refers to a user’s ability to log on once and access multiple systems without logging on again.
-
Kerberos
Network authentication mechanism used within Windows Active Directory domains and some Unix environments known as realms.
Requirements:
- A method of issuing tickets used for authentication. The Key Distribution Center (KDC) uses a complex process of issuing ticket-granting tickets (TGTs) that expire.
- Time synchronization. Few minutes of each other.
- A database of subjects or users.
Additionally, Kerberos uses symmetric-key cryptography to prevent unauthorized disclosure and to ensure confidentiality.
-
SSO and a Federation
A federation requires a federated identity management system that all members of the federation use.
A federated identity links a user’s credentials from different networks or operating systems, but the federation treats it as one identity.
-
SAML
Security Assertion Markup Language (SAML) is an Extensible Markup Language (XML)–based data format used for SSO on web browsers.
Roles:
- Principal: This is typically a user
- Identity provider: Creates, maintains, and manages identity information for principals.
- Service provider: Entity that provides services to principals. Service provider queries the Identity Provider (IdP) to verify that he has valid credentials before granting access.
-
SAML or Authorization
It’s important to realize that the primary purpose of SSO is for the identification and authentication of users.
It’s possible, however, to use SAML for single sign-on authentication and for authorization.
-
OAuth
OAuth is an open standard for authorization. i.e. Use PayPal on a store.
The key point is that OAuth focuses on authorization, not authentication.
-
OpenID and OpenID Connection
An OpenID provider holds the user’s credentials, and websites that support OpenID prompt users to enter their OpenID, then they are redirected to the OpenID provider for authentication.
OpenID Connection (OIDC) builds on OpenID for authorization and uses the OAuth 2.0 framework for authentication. Instead of an authorization token, OIDC uses a JavaScript Object Notation (JSON) Web Token (JWT), sometimes called an ID token.
-
Access Control Schemes
Access control ensures that only authenticated and authorized entities can access resources.
Schemes:
• Role-based access control
• Rule-based access control
• Discretionary access control (DAC)
• Mandatory access control (MAC)
• Attribute-based access control (ABAC)
Subjects. Subjects are typically users or groups that access an object.
Objects. Objects are items such as files, folders, shares, and printers that subjects access.
-
Role-Based Access Control (role-BAC)
Uses roles to manage rights and permissions for users. Assigns specific rights and permissions to the roles instead of users.
Department Based: Assigns users to roles. Assigns rights to roles
MS Project like: Administrators, Executives, Project Managers & Team Members.
-
Documenting Roles with a Matrix
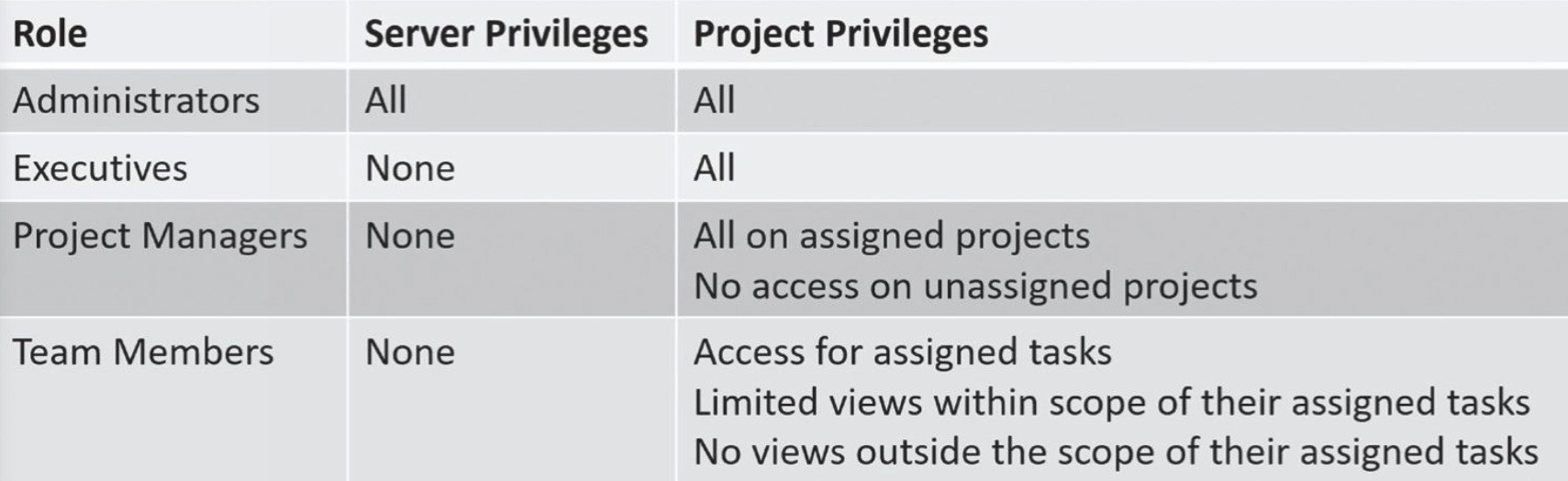
A role-based access control scheme uses roles based on jobs and functions. A matrix is a planning document that matches the roles with the required privileges.
-
Group-Based Privileges
Group-based privileges reduce the administrative workload of access management. Administrators put user accounts into security groups and assign privileges to the groups. Users within a group automatically inherit the privileges assigned to the group.
-
Rule-Based Access Control
The most common example is with rules in routers or firewalls.
Rule-based access control is based on a set of approved instructions, such as an access control list. Some rule-BAC systems use rules that trigger in response to an event, such as modifying ACLs after detecting an attack or granting additional permissions to a user in certain situations.
-
Discretionary Acess Control (DAC)
Objects (such as files and folders) have an owner, and the owner establishes access for the objects.
NTFS provides security by allowing users and administrators to restrict access to files and folders with permissions. NTFS is based on the DAC scheme.
Filesystem Permissions: Write, Read, Read & Execute, Modify, Full control.
-
SIDs and DACLs
Security Identifiers (SIDs): A SID is a long string of characters that is meaningless to most people and may look like this: S-1-5-21-3991871189-223218
Discretionary Access Control LIst (DACL): Is a table that defines what can be access by the SID. Each entry (row) in the DACL is an ACE (Access Control Entries). Each ACE is composed of a SID and the permissions that are granted.
-
The Owner Establishes Access
Owners have full explicit control.
Every object has an owner.
-
Mandatory Access Control (MAC)
Uses labels (sometimes referred to as sensitivity labels or security labels) to determine access. Security administrators assign labels to both subjects (users) and objects (files or folders)
Access is restricted based on a need to know.
Security-enhanced Linux (SELinux) is one of the few operating systems using the mandatory access control scheme.
NTFS uses DAC
-
SELinux modes
Enforcing
Permissive (logs)
Disable
-
Acronyms
MAC: Media Access Control, Mandatory Access Control & Message Authentication Code.

