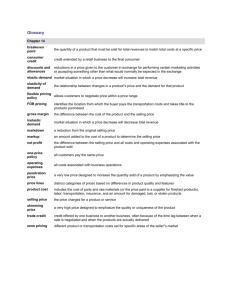
1) Companies such as IBM, CGI, and Accenture (formerly Andersen
advertisement

1) Cyberwar is not considered a viable threat to security. 2) The smallest gender difference in internet usage was reported in Canada. 3) Internet users are less likely to socialize with friends. 4) Bandwidth refers to the transmission of all forms of information, including digital data, voice, fax, sound, and video, from one location to another over some type of network. 5) An electronic brochure is one way of using the Web to disseminate sales and marketing information. 6) Firewalls can be hardware or software but not a combination of both. 7) Telnet allows users to log into any computer on the internet. 8) The keys used by current encryption technologies such as SSL and PGP cannot be cracked. 9) A Virtual Private Network is also called a secure tunnel. 10) Risk reduction, risk acceptance and risk transference are all courses of action arising from a risk analysis. 11) In the late 1990s, InterNIC morphed into SERT/CC. 12) The exchange of medical information from one location to another via a computer network is called electronic medicine or e-medicine. 13) In this Web address, http://www.pcWebopedia.com/index.html, the domain name is ".com". 14) A Denial of Service (DoS) attack is created by SPAM. 15) Distance learning is the process of providing instruction to students who are physically separated from instructors through the use of communications technologies. 16) An Internet connection called DSL stands for Direct Signal Link-up. 17) Videoconferencing is the act of working at home or from another remote location and connecting to the office via computing and networking technologies. 18) Women use the internet more frequently than do men. 19) HTTP stands for HyperText Transmission Permission. 20) Online ordering enables customers to order and, in many cases, actually pay for products and services online. 21) Biometric access controls are becoming obsolete. 22) Websites and specific Web pages within those sites have a unique Internet address called a uniform resource locator. 23) In 2002, the NUA internet Survey reported that 600 million persons wordwide use the internet. 24) Canadians are the most frequent users of the internet, per capita, in the world. 25) The protocol for the Internet is called TCP/IP. 26) Data mining involves the use of telecommunications technology to transfer business information between organizations. 27) Enterprise portals come in two basic forms, the distribution portal and the production portal. 28) E-information is more flexible than traditional promotional methods such as hard-copy catalogues and print advertisements. 29) An extranet is a vehicle for communicating public information with authorized users outside organizational boundaries. 30) Tailoring products and services to particular companies creates a horizontal market. 31) Very few countries have at least some type of Internet access. 32) To gain access to the Internet, the TCP/IP protocol must be implemented on an organizations LAN/WAN. 33) Extranets connect two or more business partners. 34) Providing customers with information or products that they can find nowhere else leads to EC profitability. 35) E-integration, the second stage of EC, is focused on accommodating requests for customized information. 36) In reverse pricing systems customers specify the product they are looking for and how much they are willing to pay for it. 37) XML doesn't specify any particular formatting. Rather it specifies the rules for tagging. 38) The Internet and the World Wide Web are extremely well suited for conducting business electronically. 39) Virtual private networks use a technology called channelling. 40) Push marketing is an advertising strategy that attempts to draw visitors to companies' Web sites. 41) The Web enables interactive (two-way) communication, which is called collaboration. 42) The e-transaction stage of EC helps companies fulfill their goals of collaboration, interactive communication, and transactional support. 43) Ford Motor Company, DamilerChrysler, and General Motors have teamed up to create a procurement portal that suppliers to the big three can access. 44) A 'Value Proposition' is partly defined as 'A summary of how a company will generate revenue.' 45) For semistructured decisions, some procedures to follow can be specified in advance, but not to the extent where a specific recommendation can be made. 46) The Internet has made it much easier to gather hard data to support executive decision making. 47) At the executive level, managers focus on shortterm strategic issues facing the organization. 48) In the current legal environment in Canada, it is legal for employers to collect almost any information they want about what employees are doing on company time. 49) Sources for soft data include transaction systems, simulations and what-if analysis output. 50) A drill-down report provides a summary of critical information on a recurring schedule. 51) Inventory planning is an example of the activities supported by transaction processing systems. 52) At the executive level of the organization, managers focus on tactical issues facing the organization. 53) At the managerial level, the scope of the decision is moderately complex and has a time horizon of a few days to a few months. 54) In a semiautomated data entry system, two computers talk to each other via a computer network without any human intervention. 55) An example of a transnational information system is the foreign exchange systems that allow traders from different parts of the world to interact with each other. 56) Traditionally, organizations have used task forces, which are permanent work groups with a finite task and life cycle, to solve problems. 57) A backbone network on the Internet manages the bulk of network traffic and typically uses higher-speed cabling, such as fiber-optic, rather than the individual LAN segments. 58) Telecapacity is the carrying capacity of telecommunications networks. 59) Voice mail allows callers to leave voice messages in a voice mailbox in a digitized format that can be stored on the computer. 60) The Internet Registry provides central maintenance of the Domain Name Registry (DNS). 61) Numbers such as 1.160.10.240 which enable networks to route messages to the proper destination. These numbers are called domain numbers. 62) Broadband technologies support the transfer of small to medium amounts of data. 63) Packet filtering and proxy servers are associated with firewalls. 64) The transfer of funds from one financial account to another via computer is called electronic funds transfer. 65) Hypermediation is another term for the pricing scheme called "pay by the click." 66) In order to facilitate e-integration, Web sites must be integrated with a company's databases. 67) Menu-driven pricing occurs when the customers set the prices for products and services. 68) Click-only companies are also referred to as "pure click" companies. 69) Successful Web sites present a brief summary of their information along with hyperlinks that allow users to drill down for the information they are seeking. 70) Because structured decisions are relatively complex, they can be programmed directly into operation information systems. 71) Although data in an EIS are provided in a very highly aggregated form, the executive also has the capability to drill down and see the details if necessary. 72) Desktop videoconferencing products are relatively large, expensive units that have video quality similar to that of broadcast television. 73) A data packet that conforms to the IP specification is called an IP datagram. 74) Secure Sockets Layer (SSL) is a popular spam filter used on the internet. 75) RFID technologies use line-of-sight reading techniques. 76) Another term for an electronic marketplace is a trading exchange. 77) Managers at the operational level of an organization make unstructured decisions. 78) The Binary Increase Congestion Transmission Control Protocol (BIC-TCP) is capable of transferring data at 150,000 times the speed of DSL. 79) Part of the 'Revenue Model' is concerned with how a firm will attract customers. 80) Beenox's port of The Incredibles required an average of only four people to produce 25 versions of the game in 13 languages.