Network
advertisement

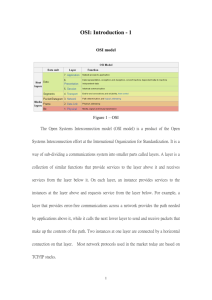
Computer Networks (EC-321) Credits: 3(2,1) Outline • • • • • Instructor/Material/Exam Objectives/Goals Course Contents Course Outcome Introduction Instructor/Material/Exam (1) • Who am I Umar Shahzad – Education: MS (Computer Science and Networking) – Experience: Post graduate (1.5 years in Telecommunication Industry) – Email: engr.umarshahzad@yahoo.com Availability after Class times: – Contact after the class – Email Instructor/Material/Exam (2) Text Book: • Computer Networks – By Andrew S. Tanenbaum, Latest Edition. References: • Computer Networks: a top down approach by Keith Ross and J.Kurose, 3rd Ed • Data and Computer Communication by W.Stalling, 7th Ed • Paper for review Instructor/Material/Exam (3) Exam Policy: Written test • Closed books • Open questions, multiple-choice questions and problems Note: • There can be a slight change in the exam pattern (will be informed) Objectives/Goals • Introduce to fundamental techniques/principles of CN. • Ability to design different networks and analyze the performance by using simulating or monitoring tool. • Develop understanding of the communication protocols used in internet. • Ability to design and analyse MAC, Routing and Transport layer protocols for different networks. • Network programming skills : socket to implement various applications based on client/server paradigm or peer-to-peer communication. • Introduce to emerging networking technologies 3G/4G Course Contents • Introduction – – – – – Uses of Computer Networks Network Hardware and Software Reference Models Example Networks Network Standardization • The Physical Layer – Basis for Conventional Data Communication – – – – – Transmission Media Wireless Transmission Communication Satellites Telephone System, Mobile Telephone System Cable Television Course Contents (cont.) • Data Link Layer – – – – – – Design Issues Error Detection and Correction Elementary Data Link Protocols Sliding Window Protocols Protocol Specification and Verification Example Data Link Protocols • MAC sub-layer – – – – Channel Allocation Problem Multiple Access Protocols Bridges High-Speed LANs Course Contents (cont.) • Wireless Systems, Technologies, Protocols – – – – Evolution and Standards Intro to radio propagation Interference and PHY layer issue Intro to MAC layer design and protocols • Network layer – – – – – Design Issues Routing Algos Congestion Control Algos Internetworking Network Layer in Internet Course Contents (cont.) • Transport Layer – – – – – Transport Service Elements of Transport Protocols TCP and UDP A simple Transport Protocol Performance Issues • The Application Layer – – – – DNS Electronic mail WWW Multimedia Course Outcome • Adequate knowledge of fundamental techniques of computer networks particularly internet. • They will be able to design protocols and implement. Introduction • • • • • • Basics and Background Uses of Computer Networks Network Hardware and Software Reference Models Example Networks Network Standardization Basics and Background • What’s a network? – Merriam-Webster Dictionary: • “A fabric or structure of cords or wires that cross at regular intervals…” • “A system of computers, terminals and databases connected by communication lines” – “A computer network is defined as the interconnection of 2 or more independent computers.” [Ramteke,”Networks”, pg. 24]. Basics and Background (cont.) • Why network? – Before networks: • One large, expensive computer (mainframe) in “computer center” used for all processing in businesses, universities, etc. – Smaller, cheaper computers… • Personal computers or workstations on desktops. • Interconnecting many smaller computers is advantageous! Why? – Large number of separate but interconnected computers do the job. Basics and Background (cont.) • Why network? – Computers everywhere. – Also means ubiquitous communication. • Users connected anywhere/anytime. • PC, laptop, cell phone. – Networking computers together is critical! – Provide access to local and remote resources. – Collection of interconnected end systems: • Computing devices (mainframes, workstations, PCs) • Peripherals (printers, scanners, terminals). Basics and Background (cont.) • Why network? – Resource sharing! • Hardware: printers, disks, terminals, etc. • Software: text processors, compilers, etc. • Data. – Robustness. • Fault tolerance through redundancy. – Load balancing. • Processing and data can be distributed over the network. – Location independence. • Users can access their files, etc. from anywhere in the network Introduction • • • • • • Basics and Background Uses of Computer Networks Network Hardware and Software Reference Models Example Networks Network Standardization Uses of Computer Networks • Business Applications • Home Applications • Mobile Users • Social Issues Business Applications (1) • Resource sharing – All programs, equipment, and especially data available to anyone on the network without regard to the physical location of the resource or the user e.g printer, information sharing (inventory, customer records, product information etc.) • Scattered offices and plants around the globe can be connected e.g VPNs (individual scattered networks ----- one extended network) Business Applications (2) • Power-full computer store company’s data. • A network with two clients and one server. Business Applications (3) • The client-server model involves requests and replies. • IP telephony or Voice over IP (VoIP) • A person at home accesses a page on the World Wide Web, the same model is employed, with the remote Web server being the server and the user’s personal computer being the client. • Desktop sharing lets remote workers see and interact with a graphical computer screen. • e-commerce e.g Airlines • Etc….. Uses of Computer Networks • Business Applications • Home Applications • Mobile Users • Social Issues Home Applications • Access to remote information – surfing the World Wide Web for information or just for fun e.g online newspaper – Online digital library e.g ACM, IEEE, ebooks • Peer-to-Peer – Every person can, in principle, communicate with one or more other people; there is no fixed division into clients and servers e.g BitTorrent. – do not have any central database of content. Home Applications Home Applications • Person-to-person communication – above applications involve interactions between a person and a remote database full of information – Email, Instant messaging, Twitter – Between person-to-person communications and accessing information are social network applications e.g Facebook • Interactive entertainment – MP3 songs, DVD-quality movies and IPTV etc Home Applications • Electronic commerce – Home shopping – Access to financial institutions e.g online bills payment, manage their bank accounts, and handle their investments electronically. • Some forms of e-commerce. Home Applications • ubiquitous computing – Homes equipped with sensors like security systems that include door and window sensors, smoke detectors call to fire department instead of making noise – electricity, gas and water meters could also report usage over the network – Etc….. Uses of Computer Networks • Business Applications • Home Applications • Mobile Users • Social Issues Mobile Users • People on the go often want to use their mobile devices to read and send email, tweet, watch movies, download music, play games, or simply to surf the Web for information • Wireless hotspots, cellular companies provide internet • Smart phones, such as the popular iPhone, combine aspects of mobile phones and mobile computers • m-commerce (mobile-commerce) (Senn, 2000). Short text messages from the mobile are used to authorize payments for food in vending machines, movie tickets, and other small items instead of cash and credit cards • Wearable computers are another promising application. Smart watches with radios. Mobile Users • distinction between fixed wireless and mobile wireless networks Uses of Computer Networks • Business Applications • Home Applications • Mobile Users • Social Issues Social Issues • Along with the good comes the bad, this new-found freedom brings with it many unsolved social, political, and ethical issues. • Social networks, message boards, content sharing sites, and a host of other applications allow people to share their views with like-minded individuals. • As long as the subjects are restricted to technical topics or hobbies like gardening, not too many problems will arise. • The trouble comes with topics that people actually care about, like politics, religion etc. Introduction • • • • • • Basics and Background Uses of Computer Networks Network Hardware and Software Reference Models Example Networks Network Standardization Network Hardware (1) • Two dimensions stand out as important in computer networks – transmission technology – Scale • Types of transmission technology – Broadcast links – Point-to-point links Network Hardware (2) • Point-to-point links – connect individual pairs of machines. – To go from the source to the destination on a network made up of point-to-point links, short messages, called packets in certain contexts, may have to first visit one or more intermediate machines. – Finding good route is important in point-to-point networks. – One sender and exactly one receiver is sometimes called Network Hardware (3) • Broadcast links – the communication channel is shared by all the machines on the network; packets sent by any machine are received by all the others. • intended recipient • all destinations ---broadcasting Network Hardware (4) • Scale – Distance is important as a classification metric because different technologies are used at different scales. Network Hardware (5) • • • • • Personal Area Networks Local Area Networks Metropolitan Area Networks Wide Area Networks Internetworks PAN • PANs (Personal Area Networks) let devices communicate over the range of a person e.g computer connect with its peripherals • Cables • Bluetooth (master, slave paradigm) – master tells the slaves what addresses to use, when they can broadcast, how long they can transmit, what frequencies they can use, and so on • PANs can also be built with other technologies that communicate over short ranges, such as RFID on smartcards and library books Network Hardware (5) • • • • • Personal Area Networks Local Area Networks Metropolitan Area Networks Wide Area Networks Internetworks LAN (1) • LAN (Local Area Network) is a privately owned network that operates within and nearby a single building like a home, office or factory. • widely used to connect personal computers and consumer electronics to let them share resources (e.g., printers) and exchange information. • When LANs are used by companies, they are called enterprise networks. LAN (2) • topology of many wired LANs is built from point-topoint links • Ethernet (802.3), is the most common type of wired LAN LAN (3) • Divide one large physical LAN into two smaller logical LANs is possible – VLAN • Two broadcast networks • (a) Bus • (b) Ring LAN (4) Token Ring (Ring Topology) LAN (5) • Wireless and wired broadcast networks, depending on channel allocation, can be divided into – static (time in discrete intervals, round robin) – dynamic designs (centralized (e.g base station) and decentralized (e.g choas like situation, CSMA/CD)) • Modern Home LAN – Sensors e.g fire sensor – Meter reading, clock (DLS) – IP of Things etc… Network Hardware (5) • • • • • Personal Area Networks Local Area Networks Metropolitan Area Networks Wide Area Networks Internetworks MAN • A MAN (Metropolitan Area Network) covers a city • (WiMAX(802.1 6))Wireless MAN) • A metropolitan area network based on cable TV. Network Hardware (5) • • • • • Personal Area Networks Local Area Networks Metropolitan Area Networks Wide Area Networks Internetworks WAN (1) • A WAN (Long Haul) spans a large geographical area, often a country or continent. Hosts WAN (2) • A WAN (Long Haul) spans a large geographical area, often a country or continent. (Switching Element) Transmission Lines Hosts WAN (3) • Large (long wires) wired LAN. – Differ to LAN • the hosts and subnet are owned and operated by different people (e.g employ and IT’s department) • routers connect different kinds of networking technology (ethernet to SONET) • what is connected to the subnet (dual computers or LANs) WAN (4) • VPN (use resources of internet) • virtual links • mileage vary with Internet service • Wireless • Satellite • Cellular Network Network Software • Protocol Hierarchies • Design Issues for the Layers • Connection-Oriented and Connectionless Services Protocol Hierarchies • Layers to reduce design complexity of network • • • Approach: “Divide and conquer”. Lower layer offer certain service to upper layer Shielding how service is implemented • Protocol is an agreement between the communicating parties on how communication is to proceed • a set of rules governing the format and meaning of the information that is exchanged by the peer processes within the same layer • A set of layers and protocols is called a network architecture Analogy: Air Travel • The problem: air travel. • Decomposed into series of steps: Arrival at airport Departure from airport Check-in Baggage claim Boarding Deplane Takeoff Landing Arrival Departure Check-in Baggage claim Boarding Deplane Takeoff Landing intermediate air traffic sites Airplane routing Traveling Airplane routing Arriving airport Departing airport Analogy: Air Travel Design Issues for the Layers • Reliability – – – – • Making a network that operates correctly in the presence of unreliable components. Error Detection (retransmission, CRC) Error Correction (FEC) Routing (finding a working path through a network) Network Evolution – Addressing and Naming – Internetworking • different network technologies often have different limitations (disassembling, transmitting, and then reassembling messages) – Scalable (designs that continue to work well when the network gets large) • Resource allocation (capacity of transmission medium) – – – – • divide resources so that one host does not interfere with another too much flow control (e.g feedback from rx to tx) Congestion (overloading of network) QoS (Quality of Service (e.g in real time application)) Defend against different kinds of threats Connection-Oriented and Connectionless Services • Layers can offer two different types of services to the layer above: Connection-Oriented and Connectionless. • Connection-Oriented, it is the service that the layer establish a connection, uses the connection, and then releases the connection e.g tube – negotiation about the parameters to be used, such as maximum message size, quality of service required, and other issues – With and without virtual circuits • Connectionless, each message (e.g letter in postal system) carries the full destination address and each one is routed through the intermediate nodes inside the system independent of all the subsequent messages. Connection-Oriented and Connectionless Services • Some services are reliable in the sense that they never loss data. By using Ack. • Reliable connection-oriented service has two minor variations: message sequence (SCTP) (message boundaries are preserved e.g book sent as separate messages) and byte stream (TCP) (e.g DVD movie download). • Unreliable (meaning not acknowledged) connectionless service is often called datagram service • The acknowledged datagram service – not having to establish a connection to send one message, but reliability is essential • Request-replay-service (client-server model) Connection-Oriented and Connectionless Services • Why would anyone actually prefer unreliable communication to reliable one? • May not available in one layer e.g Ethernet • Real Time application e.g multimedia Introduction • • • • • • Basics and Background Uses of Computer Networks Network Hardware and Software Reference Models Example Networks Network Standardization Reference Models • OSI (Open System Interconnection) model – Developed by the International Standards Organization (ISO) – 1st step toward international standardization of the protocols used in the various layers – Protocols are not used any more – Model, quite general, still valid, and the features discussed at each layer are still very important • TCP/IP model – Protocols widely used – Model not of much use OSI 7 Application 6 Presentation 5 Session 4 Transport 3 Network 2 Data Link 1 Physical OSI (cont…) 7 Application 6 Presentation 5 Session 4 Transport 3 Network 2 Data Link 1 Physical • OSI Model - The Lower Layers The bottom four layers of the OSI model are often referred to as the lower layers: Layer-4 – Transport layer Layer-3 – Network layer Layer-2 – Data-Link layer Layer-1 – Physical layer Protocols that operate at these layers control the end-to-end transport of data between devices, and are implemented in both software and hardware. OSI (cont…) 7 Application 6 Presentation 5 Session 4 Transport 3 Network 2 Data Link 1 Physical The Physical Layer • Convert the logical 1’s and 0’s coming from layer 2 into electrical signals. • Controls the signalling and transferring of raw bits onto the physical medium. • Closely related to the Data-link layer, as many technologies (such as Ethernet) contain both datalink and physical functions. • The Physical layer provides specifications for a variety of hardware: • Cabling • Connectors and transceivers • Network interface cards (NICs) • Wireless radios • Hubs OSI (cont…) The Data-Link Layer • Transporting data within a network. • Packages the higher-layer data into frames, so that the data can be put onto the physical wire 6 Presentation • Frame contains the source and destination hardware (or physical) address (uniquely identify host e.g MAC address), 5 Session hardcoded on physical network interface 7 Application 4 Transport 3 Network 2 Data Link 1 Physical The Data-Link layer consists of two sublayers: Logical Link Control (LLC) sublayer • Error control to compensate for the imperfections of the physical layer. • Flow control to keep a fast sender from swamping a slow receiver. • serves as the intermediary between the physical link and all higher layer protocols Media Access Control (MAC) sublayer • Multiple Access (CSMA/CD) OSI (cont…) The Network Layer • Controls internetwork communication • Two key responsibilities: • Logical addressing – provides a unique address that 6 Presentation identifies both the host, and the network that host exists on. 7 Application 5 Session 4 Transport 3 Network 2 Data Link 1 Physical • Routing – determines the best path to a particular destination network, and then routes data accordingly. Two of the most common Network layer protocols are: • Internet Protocol (IP) (IPv4 & IPv6) • Novell’s Internetwork Packet Exchange (IPX). OSI (cont…) 7 Application The Transport Layer • reliable transfer of data, by ensuring that data arrives at its destination error-free and in order. 6 Presentation 5 Session 4 Transport 3 Network 2 Data Link 1 Physical Transport layer communication falls under two categories: • Connection-oriented (TCP (Transmission Control Protocol)) • Connectionless (UDP (User Datagram Protocol )) Connection-oriented protocols provide several important services: • Segmentation and sequencing • Data is segmented into smaller pieces for transport. • Sequence number, to reassemble the data on arrival. • Connection establishment – connections are established, maintained, and ultimately terminated between devices. • Acknowledgments – receipt of data is confirmed through the use of acknowledgments. Otherwise, data is retransmitted, guaranteeing delivery. • Flow control (or windowing) – data transfer rate is negotiated to prevent congestion. OSI (cont…) 7 Application 6 Presentation OSI Model - The Upper Layers The top three layers of the OSI model are often referred to as the upper layers: 5 Session • Layer-7 - Application layer • Layer-6 - Presentation layer • Layer-5 - Session layer 4 Transport Protocols that operate at these layers manage application-level functions, and are generally implemented in software. 3 Network 2 Data Link 1 Physical OSI (cont…) The Session Layer • Responsible for establishing, maintaining, and ultimately terminating sessions between devices. 6 Presentation • Synchronization • Dialog control (keeping track of whose turn it is to transmit), • Token management (preventing two parties from attempting the 5 Session same critical operation simultaneously) 7 Application 4 Transport 3 Network 2 Data Link 1 Physical Sessions communication falls under one of three categories: • Full-Duplex – simultaneous two-way communication • Half-Duplex – two-way communication, but not simultaneous • Simplex – one-way communication OSI (cont…) The Presentation Layer • formatting and syntax of user data for the application layer. • Ensures that data from the sending application can be understood by the receiving application. 6 Presentation 7 Application 5 Session 4 Transport 3 Network 2 Data Link 1 Physical Examples of Presentation layer formats include: • Text - RTF, ASCII, EBCDIC • Images - GIF, JPG, TIF • Audio - MIDI, MP3, WAV • Movies - MPEG, AVI, MOV • conversion or translation services to facilitate communication. • encryption and compression of data, as required OSI (cont…) 7 Application 6 Presentation 5 Session 4 Transport 3 Network 2 Data Link 1 Physical The Application layer • interface between the user application and the network. A web browser and an email client are examples of user applications. • The user application itself does not reside at the Application layer – the protocol does. The user interacts with the application, which in turn interacts with the application protocol. Examples of Application layer protocols include: • FTP, via an FTP client • HTTP, via a web browser • POP3 and SMTP, via an email client • Telnet The Application layer provides a variety of functions: • Identifies communication partners • Determines resource availability • Synchronizes communication OSI (Example) A web browser serves as a good practical illustration of the OSI model and the TCP/IP protocol suite: • The web browser serves as the user interface for accessing a website. The browser itself does not function at the Application layer. Instead, the web browser invokes the Hyper Text Transfer Protocol (HTTP) to interface with the remote web server, which is why http:// precedes every web address. • The Internet can provide data in a wide variety of formats, a function of the Presentation layer. Common formats on the Internet include HTML, XML, PHP, GIF, and JPEG. Any encryption or compression mechanisms used on a website are also considered a Presentation layer function. • The Session layer is responsible for establishing, maintaining, and terminating the session between devices, and determining whether the communication is half-duplex or full-duplex. However, the TCP/IP stack generally does not include session-layer protocols, and is reliant on lowerlayer protocols to perform these functions. OSI (Example) • HTTP utilizes the TCP Transport layer protocol to ensure the reliable delivery of data. TCP establishes and maintains a connection from the client to the web server, and packages the higher-layer data into segments. A sequence number is assigned to each segment so that data can be reassembled upon arrival. • The best path to route the data between the client and the web server is determined by IP, a Network layer protocol. IP is also responsible for the assigned logical addresses on the client and server, and for encapsulating segments into packets. • Data cannot be sent directly to a logical address. As packets travel from network to network, IP addresses are translated to hardware addresses, which are a function of the Data-Link layer. The packets are encapsulated into frames to be placed onto the physical medium. • The data is finally transferred onto the network medium at the Physical layer, in the form of raw bits. Signalling and encoding mechanisms are defined at this layer, as is the hardware that forms the physical connection between the client and the web server. TCP/IP Reference Model • Requirements (remain intact (DoD ), real-time) led to the choice of a packetswitching network based on a connectionless layer that runs across different networks. TCP (Transmission Control Protocol): a reliable connection-oriented protocol. UDP (User Datagram Protocol): an unreliable connectionless protocol Its job is to inject IP packets into any network and have them travel independently to the destination • Describes what links, such as serial lines and classic Ethernet, must do to meet the needs of this connectionless internet layer. • It is not really a layer at all, in the normal sense of the term, but rather an interface between hosts and transmission links A Critique of the OSI Model and Protocols Why OSI did not take over the world • Bad Timing: The apocalypse of the two elephants. • Timings – Widespread adoption of the TCP/IP protocols preceded the formalization of the OSI model. – Vendors already begun offering TCP/IP based products. – OSI emerged about 5 years after industry had adopted TCP/IP. A Critique of the OSI Model and Protocols – Vendors were reticent to add support for a second protocol stack until momentum had gathered behind OSI. – The combination of these factors meant that OSI was never adopted in practice. • Technology – Some parts of the OSI model are fundamentally flawed. • Although there are 7 layers, 2 of these (session, presentation) are almost empty and 2 others (data link, network) are cramped. • Additionally some functions such as addressing, error control are recurring at each layer. • Implementations: – Early implementations of OSI were inefficient, contrast with TCP/IP implementations which are easy to use. • Politics: – OSI was widely perceived as the product of quasi-government standards processes rather than driven by good design processes A Critique of the TCP/IP MODEL • Lack of distinction between concepts. • Doesn’t clearly distinguish between service, interface and protocol. • Not adaptable – Not a general model and hence poorly adapted to other protocol Stacks e.g Bluetooth. • Link Layer is not really a layer, but an interface between network and data link layers. • Omitted layers – Physical and data link layers are not present. • Early implementations were fragile. Introduction • • • • • • Basics and Background Uses of Computer Networks Network Hardware and Software Reference Models Example Networks Network Standardization Wireless LANs: 802.11 • Suitable Frequency Band – operate in unlicensed bands such as the ISM (Industrial, Scientific, and Medical) bands defined by ITU-R (e.g., 902-928 MHz, 2.4-2.5 GHz, 5.725-5.825 GHz) • Architecture Base station Wireless LANs: 802.11 • Multipath Fading • Echoes cancel or reinforce each other • Solution • Space Diversity • 802.11 a/g (OFDM) – 54Mbps • 802.11 n (wider frequency band and 4 antennas per computer) – 450Mbps Wireless LANs: 802.11 • CSMA • Mobility • network consist of multiple cells • change association with AP • Security (encryption) • WEP (Wired Equivalent Privacy) • WPA (WiFi Protected Access) Architecture of the Internet • • • • DSLAM (Digital Subscriber Line Access Multiplexer) converts between signals and packets CMTS (Cable Modem Termination System) ( device at cable head-end) POP (Point of Presence) – location at which customer packets enter the ISP network for service the ISP’s IXPs (Internet eXchange Points) - ISPs connect their networks to exchange traffic at IXP. The connected ISPs are said to peer with each other. Basically an IXP is a room full of routers, at least one per ISP Introduction • • • • • • Basics and Background Uses of Computer Networks Network Hardware and Software Reference Models Example Networks Network Standardization Network Standardization • Who’s Who in the Telecommunications World – ITU (International Telecommunication Union) – ITU-T sector • Who’s Who in the International Standards World – ISO (International Standards Organization) – IEEE (Institute of Electrical and Electronics Engineers) • Who’s Who in the Internet Standards World – IRTF (Internet Research Task Force) – IETF (Internet Engineering Task Force)