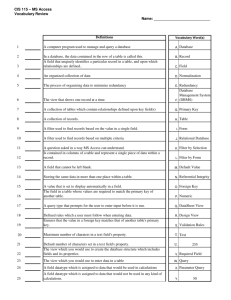
Preventing Data Leaks from Compromised Web Applications
advertisement

SilverLine:
Preventing Data Leaks from
Compromised Web Applications
Yogesh Mundada
Anirudh Ramachandran
Nick Feamster
Georgia Tech
Appeared in Annual Computer Security Applications Conference (ACSAC) 2013
1
Data Breach Incidents
•
•
•
•
Sony Data Breach (SQL Injection, 2011)
Citibank (Web application vulnerability, 2012)
Twitter (2013)
Adobe (2013)
90% of the data leakages occur at server.
95% of those leaks are from external attacks.
2
Common Server-Side Vulnerabilities
• Injection Attacks
• Broken Authentication and Session
Management
• Insecure Direct Object References
• Security Misconfiguration
• Vulnerable Components and Libraries
(Open Web Application Security Project)
3
Current Protection Mechanisms
•
•
•
•
Penetration testing
Automated code review
Application firewalls
Data loss prevention devices
Shortcomings
No protection against zero day attacks
Once compromised, can’t stop data theft
Focus on protecting data,
rather than the underlying system
4
Design Goals
• Security: Decouple data protection from the
application
• Deployment: Minimize changes to existing
applications
• Performance: Minimize overhead
5
SilverLine Design Non-Goals
•
•
•
•
•
Kernel-level vulnerabilities
Covert channels
Malicious software on the database
Inside threats
Data modification attacks
6
SilverLine Overview
Step #1: Tag Sensitive Data
Step #2: Associate User with Session
Step #3: Retrieve Data with Taints
Step #4: Track Data
Step #5: Declassify Response
7
SilverLine Components
• Authentication Module
• Database Proxy
• Information Flow Monitor
• Declassifier
8
SilverLine Architecture
1. User sends
Login request
16. Return
Response
6. Execute
query
Webserver
Process
14. Send
Response
12. Query
Results
Server
Declassifier
Process
Information Flow
Tracking Kernel
Web Application
7
Database
9
Query
RegEx
Table
Database Node
15. Check Session
Permissions
User-Sessions
Table
10
8
Query
Parser
Process
Firewall
ConnectionCapabilities
Table
Database
Proxy
Process
2. Authenticate
User
Trusted Realm
4. Cookies
5. 5-tuple
taints
User
Authentication
Module
3. Authenticate
Authentication Node
User-Auth
Table
Untrusted Realm
Database Table
Process
9
Step #1: Initial Configuration
•
•
•
•
•
•
Indentify and mark sensitive tables
Find unique user key
Find foreign keys
Find table groups
Find tables to monitor for insert query
Create taint-storage tables in each group
10
Step #1: Configuration Example
User Table
User-Taint Table
User-ID
Name
Transact-ID
1
John Smith
100
2
Jane Doe
User-ID
Taint
1
‘A’
2
‘B’
200
Transaction Table
Transact-Taint Table
Transact-ID
SELECTItem
Name
Transact-no
FROM User WHERE
Transact-IDUser-ID = ‘2’
Taint
200
37
DVD
100
‘A’
200
38
PHONE
200
‘B’
100
89
SELECT BRUSH
Name, Taint FROM User u, User-Taint ut
WHERE User-ID = ‘2’ AND u.User-ID = ut.User-ID
SELECT Item FROM Transaction WHERE
Transact-ID = ‘200’ and Transact-no=‘37’
SELECT Item, Taint FROM Transaction t, Transact-Taint tt
WHERE Transact-ID = ‘200’ and Transact-no=‘37’ and t.Transact-ID = tt.Transact-ID 11
Step #2a: Authenticate User
1. User sends
Login request
Webserver
Process
Web Application
Database
Server
Declassifier
Process
Database
Proxy
Process
Information Flow
Tracking Kernel
Firewall
Query
Parser
Process
Query
RegEx
Table
Database Node
2. Authenticate
User
ConnectionCapabilities
Table
User-Sessions
Table
Trusted Realm
User
Authentication
Module
Authentication Node
User-Auth
Table
Untrusted Realm
Database Table
Process
12
Step #2b: Decide Session Capability
ConnectionCapabilities
Table
UserSessions
Table
5. Store
{SIP:SP-DIP:DP-Prot,
Taint1}
4. Store
{Cookie1,
4. Verify
User1}
Cookie
2. Authenticate
{username, password}
User
Authentication
Module
3. Verify &
Authenticate
User-Auth
Table
Authentication Node
Trusted Realm
Process
Database Tables
13
Step #3: Retrieve Taints with Data
1. User sends
Login request
6. Execute
query
Webserver
Process
Web Application
Database
Server
Declassifier
Process
Database
Proxy
Process
Query
Parser
Process
Information Flow
Tracking Kernel
Firewall
Query
RegEx
Table
Database Node
2. Authenticate
User
ConnectionCapabilities
Table
User-Sessions
Table
Trusted Realm
4. Cookies
5. 5-tuple
taints
User
Authentication
Module
3. Authenticate
Authentication Node
User-Auth
Table
Untrusted Realm
Database Table
Process
14
Step #3: DB Proxy Operation
6. Execute query
from Webserver
12. Return results
To Webserver
11. Store
{5-tuple,
Taint}
Connection
Taints
Table
Database
Proxy
Process
10. Execute Data + Taint
Retrieval Query
8. Parse Query
And generate
Regular
expressions
7. Match
Regular
Expression
Query
Parser
Process
Trusted Realm
9. Store
Query, Taint Query
Process
Web Application
Database
Query
RegEx
Table
Database Tables
15
Step #3: Apply Taint to Connection
Database
Server
UserID
Username
SSN
UserID
Taint
1
Alice
999-99-9999
1
0xABCDEF
2
Bob
888-88-8888
2
0x123456
user table
user_taints table
Modified Query
by Proxy
Data Query
“SELECT name, taint
from user u, usertaints ut WHERE
UserID=1 and
u.UserID=ut.UserID”
Query Results
0xABCDEF
1
Alice
999-99-9999
Database
Proxy
“SELECT name
from user WHERE
UserID=1”
Taint applied to
network
connection
1
Alice
999-99-9999
16
Step #4: Track Data
1. User sends
Login request
6. Execute
query
Webserver
Process
12. Query
Results
Server
Declassifier
Process
Database
Proxy
Process
Web Application
7
Database
8
Query
Parser
Process
Information Flow
Tracking Kernel
Firewall
10
9
Query
RegEx
Table
Database Node
2. Authenticate
User
ConnectionCapabilities
Table
User-Sessions
Table
Trusted Realm
4. Cookies
5. 5-tuple
taints
User
Authentication
Module
3. Authenticate
Authentication Node
User-Auth
Table
Untrusted Realm
Database Table
Process
17
Step #4: Information Flow Tracking
• Per-process taint records
• Monitors system calls
–
–
–
–
–
IPC {send, shmat, kill},
File/Device operations {read, unlink},
Process management {fork, execve},
Memory {mmap},
Kernel configuration{sysctl}
• Taint transfer with information exchange
• Network database “connection-taints” to
transfer taints across machines
18
Step #5: Declassification
1. User sends
Login request
16. Return
Response
6. Execute
query
Webserver
Process
14. Send
Response
12. Query
Results
Server
Declassifier
Process
Information Flow
Tracking Kernel
Web Application
7
Database
9
Query
RegEx
Table
Database Node
15. Check Session
Permissions
User-Sessions
Table
10
8
Query
Parser
Process
Firewall
ConnectionCapabilities
Table
Database
Proxy
Process
2. Authenticate
User
Trusted Realm
4. Cookies
5. 5-tuple
taints
User
Authentication
Module
3. Authenticate
Authentication Node
User-Auth
Table
Untrusted Realm
Database Table
Process
19
Implementation
• 60 lines in OSCommerce
• Information Flow Control
– 8,000 lines of ‘C’ Linux kernel code
– Redis key-value store
•
•
•
•
User-Session
Connection-Capabilities
Connection-Taints
Taint-Policy
• Database proxy
– 350 lines of Lua code
20
Implementation
• Configuration
– Identify primary keys
– Table groups
– Foreign key relationship
– Insert query monitoring for each group
In OSCommerce application: Out of 50 tables, 15 were sensitive
• Tables were grouped in sets of 9, 5 and 1
• In all we needed 3 taint-storage tables
21
Evaluation
• File fetch (small: 7%, large: 1%)
• Scalability:
– Login slowdown (21%)
– User session slowdown (30%)
22
Related Work
• Data Isolation
– CLAMP, Nemesis
– CryptDB
• Information Flow Control
– HiStar, Dstar, Asbestos, Flume
• Language-level Taint Tracking
– RESIN, Guardrails, PHPAspis, DBTaint
• Full-system Taint Tracking
– TaintDroid, Neon, Panorama
23
Conclusion
SilverLine: Protect data, rather than the application
• Prevent exfiltration of sensitive data, even if
the application is compromised
• Information flow: associate data with taints,
only allow authorized user sessions to access
• Very little modification to existing applications
• Overhead is about 20–30% over unmodified
applications
25