Chapter One
advertisement

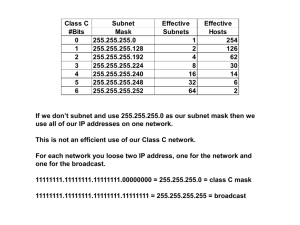
Chapter Eleven Networking with TCP/IP and the Internet IP Planning An IP address contains 32 bits or total of 4 octets i.e. 192.168.0.2 Each bit of the 32 bits can be a member of one and only one of the following sections: Network Host Subnet What is the Network section? A group Identifier (compare to area code number) What is the Host section? Group of individual PC’s or devices within the same network IP Planning How many bits should be under the Network section? Depending on the size of the organization and potential growth, one of the following classes can be obtained from the ICANN organization: A, B, or C How many bits should belong to the host section? 32 – # Network bits How many hosts can a Network have? (2 ^ Number of host bits ) - 2 IP Planning Why are we loosing 2? Network Identifier Network Broadcast Address What is a Network Identifier? The first IP address in a network, known as the “cable identifier”. Represents the entire network. All host bits are turned off (0’s) Example: 192.168.4.0 What class is it? What is it in binary? What is a Broadcast Address? The last IP address in a network. Used to communicate with all the hosts in the network. All host bits are turned on (1’s) Example: 192.168.4.255 What is it in binary? IP Planning Examples: Class A uses the first 8 bits for the network identifier The address range is only up to 126. The binary equivalent to that is 01111110. The MSB is 0 so we use only the last 7 bits. Number of networks that can be created = 27 = 128 – 2 = 126. Why? Number of hosts per Class A network 32 bits – 8 bits = 24 bits 224 = 16,777,216 – 2 = 16,777,214 Class A structure: N.H.H.H Class B uses the first 16 bits for the network identifier The address range is from 128 - 191. The difference is = 64. The binary equivalent to that is 00111110.00000000 The first two MSB are 0 so we use only the last 14 bits Number of networks that can be created = 214 = 16384 Number of hosts per Class A network 32 bits – 16 bits = 16 bits 216 = 65,536 – 2 = 65,534 Class B Structure: N.N.H.H What would be Class C? Exercise Classify the following IP addresses as A, B, or C and label the network and host parts of the IP address: 99.1.1.0 156.1.149.9 171.13.5.233 127.1.1.255 193.4.14.1 IP Planning What is Subnetting? Process of subdividing a single class of network into multiple, smaller networks. Why do we need it? Organization, control, and ease of management Who does it? The Network Administrator of the organization How is subnetting done? Borrow bits from the host section and move them to the “subnet” section How many bits should I borrow? Depends on how many subnets you want to create What are some of the problems associated with subnetting? Loosing IP’s The outside world does not have any knowledge of our Subnetting plan IP Planning What is a Subnetmask? Special 32-bit number that, when combined (Logically Anded) with a device’s IP address, determines which subnetwork that particular device belongs to For an external host to communicate with 166.144.63.12, the router will need to interpret the subnetmask information IP Planning How is it written? All bits under the network and subnetwork sections are turned on (1’s). What is default subnetmask? The subnet mask that will be used if you do not specify one in your TCP/IP Configuration 255.0.0.0 for Class A 255.255.0.0 for Class B 255.255.255.0 for Class C What is the relation between Subnet Mask and Bit Mask? Subnet mask is the dotted decimal notation of the number of network and subnetwork bits Bit Mask is the count of the number of network and subnet bits Default bit mask for class A is 8 Default bit mask for class B is 16 Default bit mask for class C is 24 IP Planning What are the rules? Number of subnets created = (Number of bits borrowed from the host 2^ section) Number of subnets Available = 2 ^ (Number of bits borrowed from the host section) – 2 Number of hosts created per subnet = (Number of bits remaining under the host 2^ section) Number of hosts available per subnet = 2 ^ (Number of bits remaining from the host section) – 2 Agenda Attendance, and Review of subnetting rules Subnetting Class C -- Case Study Building the topology and Interconnecting Networking Devices Using real Cisco routers and switches Gateways – What are they??? Packet Tracer– A quick introduction, and simulating how a packet traverses a simple WAN (How a packet goes from one LAN to another through routers) Subnetting Class C– Group Exercise Logical And Example Say you are assigned a Class C network number of 200.133.175.0 (apologies to anyone who may actually own this domain address:). You want to utilize this network across multiple small groups within an organization. You can do this by subnetting that network. Break this network into 8 subnets of 32 IP addresses each. How many subnets can be used? How many nodes can be in each subnet? Building the Topology Now, we will use real Cisco routers and switches to connect two LANs (Let’s say, the HR department LAN and the IT department LAN) During this lab make sure that you take the time to do the following: Check the different types of interfaces that a router can have Know what each type of an interface is used for Know what type of cable is used with each interface Ask Questions Default Gateway The role of Routers in connecting subnets What is a Gateway? Combination of software and hardware that enable two different network segments to exchange data Examples: Cisco Routers, Linksys routes, Linux servers with multiple NICs and routing services installed, windows 2000 server with multiple NICs and RRAS installed. The IP address of a router’s port through which a network is connected to the router Every device has to have a default gateway to communicate with other devices outside its network Rules 1. Each router’s interface has to be on a separate network ( You can’t have two different interfaces on the same network) 2. Each interface on the router has to be assigned an ip address and a subnet mask 3. Routers’ interfaces usually take the first available IP address on a network 4. Switches are layer 2 devices and do not need an IP address to work 5. Each PC on the network must be configured with the correct IP properties. Your PC will need an IP address and a subnet mask to be able to communicate with other hosts on the same network. Your PC will need a default gateway to be able to communicate with other hosts on a different network 6. PCs and their Default Gateway must belong to the same network. iMac iMac iMac iMac iMac iMac iMac iMac Building The Topology with Packet Tracer Interconnect Devices Simulate how a Packet traverses a simple WAN Group Exercise Do number 2 from the IP Addressing/Subnet Masking Problems Agenda Attendance and questions from last week’s meeting Group discussion about the homework Exercise Logical AND and group exercise Case 1, and 2 (To be studied at home) Sockets, well-known port numbers, DNS, BOOTP, DHCP, and WINS Tools: netstat, nbtstat, snlookup, and tracero Logical And – Why Why: The logical AND function is used to extract the subnet ID from a host IP address and its subnet Mask Question: With out using the table from the previous group exercise, can you tell to which subnet the host 200.133.175.199 belongs??? Logical And – How Host IP Address (in binary format) AND Subnet Mask (in binary format) = Subnet ID 1 And 1 = 1 1 And 0 = 0 0 And 0 = 0 0 and 1 = 0 Short cut: X And 255 = X X And 0 = 0 Logical AND Exercise Given the IP Address: 199.10.10.110/248 What is the subnet mask? How many bits were borrowed? How many subnets were created What is the number of theoretical hosts per subnet? Using the Logical And function, find the subnet ID where the host resides What is the broadcast address for this subnet? Case 1 1. Suppose you are given the IP address 195.5.5.0 and wish to connect Springfield and Bedrock to Southpark. Create an IP addressing scheme that will meet the following requirements: A: Each subnet must support between 25 and 30 devices. B: You must have enough subnets to address each network. i. What is the subnet mask for this network? ii. What is the broadcast address of the 3rd subnet? iii. On the diagram, assign a subnet address to each network and give each router interface an appropriate IP address for that network. List of networks Case 1 Answer for the 195.5.5.0 network with the subnet mask 255.255.255.224 192.5.5.33/27 Hosts Network from 195.5.5.0 195.5.5.1 192.5.5.65/27 Southpark Broadcast Address to 195.5.5.30 195.5.5.31 195.5.5.32 195.5.5.33 195.5.5.62 195.5.5.63 192.5.5.34/27 192.5.5.66/27 195.5.5.64 195.5.5.65 195.5.5.94 195.5.5.95 195.5.5.96 195.5.5.97 195.5.5.126 195.5.5.127 195.5.5.128 195.5.5.129 195.5.5.158 195.5.5.159 Springfield 192.5.5.97/27 Bedrock 192.5.5.129/27 195.5.5.160 195.5.5.161 195.5.5.190 195.5.5.191 195.5.5.192 195.5.5.193 195.5.5.222 195.5.5.223 195.5.5.224 195.5.5.225 195.5.5.254 195.5.5.255 - IP:192.5.5.98/27 SM: 255.255.255.224 GW: 192.5.5.97 IP:192.5.5.130/27 SM: 255.255.255.224 GW: 192.5.5.129 Rules 1. Each router’s interface has to be on a separate network ( You can’t have two different interfaces on the same network) 2. Each interface on the router has to be assigned an ip address and a subnet mask 3. Routers’ interfaces usually take the first available IP address on a network 4. Switches are layer 2 devices and do not need an IP address to work 5. Each PC on the network must be configured with the correct IP properties. Your PC will net an IP address and a subnet mask to be able to communicate with other hosts on the same network. Your PC will net a default gateway to be able to communicate with other hosts on a different network 6. PCs and their Default Gateway must belong to the same network. Case 2 a. b. c. d. e. Given the IP address 199.199.199.172 with a subnet mask of 255.255.255.192. Answer the following: How many bits were borrowed? How many subnets have been created? How many host address per subnet? What is the subnet address of the network containing the given IP address? What is the broadcast address of the network containing the given IP address? Case 2 Answer List of networks for the 199.199.199.0 network with the subnet mask 255.255.255.192 Hosts Network from 199.199.199.0 199.199.199.1 Broadcast Address to 199.199.199.62 199.199.199.63 199.199.199.64 199.199.199.65 199.199.199.126 199.199.199.127 199.199.199.128 199.199.199.129 199.199.199.190 199.199.199.191 199.199.199.192 199.199.199.193 199.199.199.254 199.199.199.255 A: 2 B: 4 C: 64 D: 199.199.199.128 E: 199.199.1299.191 Sockets and Ports Socket Logical address assigned to a specific process running on a computer Sockets and Ports Virtual circuit for the Telnet service Host Names and Domain Name System (DNS) Host name Symbolic name that describes a TCP/IP device Domain Group of computers that belong to the same organization and have part of their IP addresses in common Domain name Symbolic name that identifies an organization Must be registered with the Internet Naming Authority. Must be available (not already taken by another organization) Domain Names Fully qualified domain name (FQDN) Name of a host that includes the full domain name as well as the host name Example: You work at the library of congress and named your machine PeggySue. Your fully qualified hostname is PeggySue.loc.gov Top-level domains (TLDs) Highest-level category used to distinguish domain names A certain suffix that applies to an organization according to the nature of business it conducts. Domain Names Domain naming conventions What other domains are now available? Host Files Text file that associates TCP/IP host names with IP addresses (was used when we had 1000 hosts on the web) Alias Nickname for a node’s host name Example: host file This file is called lmhosts in Windows and /etc/hosts on a UNIX-based computer Domain Name System (DNS) Database that is distributed over several key computers across the Internet. Hierarchical way of tracking domain names and their addresses, devised in the mid-1980s Example: How does the DNS request is processed? From Local, Regional, National To National, Regional, Organizational (local) DNS server hierarchy by geography Domain Name System (DNS) Resolvers Hosts on the Internet that need to look up domain name information Example, type the command telnet support.novell.com and your Telnet client software will kick off the resolver service to find the IP address for support.novell.com Name servers are servers that contain databases of names and their associated IP addresses Each name server manages a group of devices, collectively known as a zone Configuring DNS To view or change the name server information on a Windows 2000PC Right-click My Network Places, then right-click appropriate Network Adapter. Select Properties, Select TCP/IP, Select Properties. In the TCP/IP Properties box, click the DNS tab. DNS Configuration properties tab DNS Name Space Name space Database of Internet IP addresses and their associated names distributed over DNS name servers worldwide (every name server holds a piece of that database) Root server DNS server maintained by InterNIC and acts as the ultimate authority on how to contact the top-level domains (how to get from .edu to .com) Resource record One record for each host Element of a DNS database stored on a name server that contains information about TCP/IP host names and their addresses Bootstrap Protocol (BOOTP) Service that simplifies IP address management. Requires network administrators to enter every IP and MAC address into the BOOTP table • This situation is ideal for Diskless workstations: workstations that do not contain any hard disks Dynamic Host Configuration Protocol (DHCP) Automated means of assigning a unique IP address to every device on a network Reasons for implementing DHCP Reduce the time and planning spent on IP address management Reduce the potential for errors in assigning IP addresses Enable users to move their workstations and printers without having to change their TCP/IP configuration Make IP addressing transparent for mobile users DHCP Leasing Process Lease Agreement between DHCP server and client on how long the client will borrow a DHCP-assigned address NetBIOS Names Defined Each Windows-based host receives a NetBIOS name during the installation of the operating system. This name is used to uniquely identify the machine on the network However the NetBIOS name is not used itself to identify a host: it is used by NetBIOS applications and processes to establish communication with other NetBIOS applications on remote hosts A NetBIOS name consists of 15 alphanumeric characters If a NetBIOS name does not contain 15 characters to fill the name out to the required 15 characters, Windows will add the necessary number of null characters to fill the name out to the required 15 characters A sixteenth character , which is not usually visible, is added to each NetBIOS name to indicate the type of name, service, or group that the NetBIOS name represents Registration, Discovery and Release of NetBIOS Names Process Broadcast WINS Registration (defending a NetBIOS name) Sent to every machine within the same LAN (subnet) to see if any machine is already using the name being requested No broadcast. The name registration request is sent directly to WINS to see if the requested name is available. Discovery A broadcast will be sent to all hosts to request the IP associated with the NetBIOS name. When obtained results will be registered in cache. No Broadcast. Request is sent directly to WINS, which can resolve names of hosts on the entire Network (different subnets) Release During proper shutdown, Release request is sent NetBIOS host sends a directly to WINS broadcast to release its name LMHOSTS File Standard Text file used to resolve NetBIOS names to IP addresses. The LMHOSTS file should be located in: %systemroot%\system32\drivers\etc directory Example: 192.168.0.1 BONGO #PRE # DOM: Resource The LMHOSTS file is read from top to bottom. So would the order of entries matter??? NetBIOS Node Types B-Node: relies completely on broadcast for name registration, discovery and release. Creates great deal of traffic on the network Cache, Broadcast, End P-Node: Point-to-point communication with a WINS server for NetBIOS name services Cache, WINS, End H-Node: default configuration in windows machine Cache, WINS, Broadcast up to 3 requests, LMHOST if exist, End NetBIOS Names and Browsing The Network Resources How do I get to see all these network resources when I click on My Network Places??? What is a browse List? A list of available NetBIOS network resources for a particular network segment. How are the lists built and who keep them? NetBIOS machines announce their presence at the start up then once every 12 minutes. Those announcements will be used by the following special hosts to built the browse lists: Master Browser: One per segment Backup Master Browser: Future Master browser Domain master Browser : Pulls the master browser to get a list of the resources on this particular segment, then sends a complete list with all the resources on the entire network to each Master Browser NetBIOS Switches Windows Internet Naming Service (WINS) Provides a means of resolving NetBIOS names with IP addresses What are NetBIOS names? How are DNS names different from NetBIOS? Make sure that you can differentiate between TCP/IP host names and NetBIOS names Remember that NetBIOS is used primarily with Windows-based systems WINS offers several advantages Guarantees a unique NetBIOS name is used for each computer on a network Support for DHCP Better network performance (eliminates NetBIOS broadcast) TCP/IP Troubleshooting Packet Internet Groper (PING) Troubleshooting utility that can verify TCP/IP is installed, bound to the NIC, configured correctly, and communicating with the network How does it work? It uses ICMP to send echo request and echo replay messages. What is an Echo Request? An echo request is a signal sent out to another computer What is an Echo Replay? An echo reply is the other computer’s response signal Process of sending this signal back and forth is known as pinging Netstat and Nbstat Netstat Displays statistics and the state of current TCP/IP connections Nbstat Provides information about NetBIOS names and their addresses Nslookup and Traceroute Nslookup Allows you to look up the DNS host name of a network node by specifying its IP address, or vice versa. Used to troubleshoot problems related to the DNS server. Tracert Uses ICMP and TTL to trace the path from one networked node to another What is TTL? Numeric measure used to determine how many more network hops a datagram can make. When TTL expires a datagram returns to the source with the identity of the destination. How is it done? By transmitting a series of UDP to a specified destination Next Meeting (After Spring Break) Take Chapter 11 Test (Read the chapter first) Take The Midterm Exam (Make sure that you study both case 1, and 2 before you take the test Download the Project and start working on it; It is due two weeks before the final exam! Make sure that you have the cable kit Read Chapter 6 (Network Hardware) Enjoy your break