Middleware: RPC, MOM, and TP Monitors Explained
advertisement

Middleware
Zongrui Li
Candido Gomez
Peter Tran
Jose Villar
Content:
Introduction
Remote Procedure Call (RPC)
Message-Oriented Middleware (MOM),
Transaction processing (TP) monitors
Conclusion
Key Words
References
What is the Middleware?
Middleware is connectivity software that
consists of a set of enabling services that
allow multiple processes running on one or
more machines to interact across a network.
History
Middleware first appeared in the late 1980s to
represent network connection management
software. Until the mid 1990s, it was general
recognized, when network technology had
accomplished sufficient access to it.
Remote Procedure Call (RPC) was the first
communication-based middleware, which was
first developed by circa 1982 by Birrell and
Nelson.
What are the benefits of middleware?
Simplicity: Putting middleware in the middle can mean
each application needs only one interface—to the
middleware—instead of a separate interface to each
application it needs to talk to.
Persistence: Middleware can capture data and hold on
to it until it has been recorded appropriately by all the
applications or databases that need the information.
Services: If your data needs to be checked for integrity,
printed out, reconciled with data from other applications,
merged, split or reformatted, various kinds of middleware
can handle those tasks efficiently.
Middleware can take on the following
different forms:
Remote Procedure Call (RPC) system, which
enable the logic of an application to be
distributed across the network. Program logic on
remote systems can be executed as simply as
calling a local routine.
Message-Oriented Middleware (MOM), which is
a specific class of middleware that supports the
exchange of general-purpose messages in a
distributed application environment.
Continue:
Transaction processing (TP) monitors,
which provide tools and an environment
for developing and deploying distributed
applications.
Object Request Brokers (ORBs), which
enable the objects that comprise an
application to be distributed and shared
across varied networks.
Remote Procedure Call (RPC)
Origin
Sun Microsystems developed the first widely
used RPC protocol as part of their Open
Network Computing (ONC) it was develop in
the early 1980s. The specification has been
handed off to the Internet Engineering Task
Force (IETF) as a step toward making ONC
RPC an Internet standard.
What is RPC?
Remote Procedure Call (RPC) is a
client/serverRemote Procedure Call (RPC) is
a protocol that one program can use to
request a service from a program located in
another computer in a network without having
to understand network details.
How does it work?
The requesting program is a client and the serviceproviding program is the server. Like a regular or
local procedure call, an RPC is a
synchronous(from Greek syn-, meaning "with,"
and chronos, meaning "time") operation
requiring the requesting program to be
suspended until the results of the remote
procedure are returned.
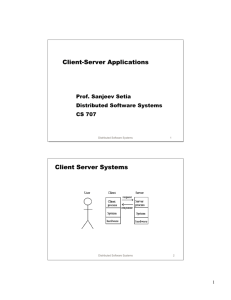
Client
router
Requesting Program
Server
service-providing program
However, the use of lightweight processes
that share the same address space allows
multiple RPCs to be performed concurrently.
When program statements that use
RPC are compiled into an executable
program, a stub is included in the
compiled code that acts as the
representative of the remote procedure
code.
What is a stub?
A stub is a small program routine that
substitutes for a longer program For
example, a program that uses Remote
Procedure Calls (RPC) is compiled with
stubs that substitute for the program
that provides a requested procedure.
When the program is run and the procedure
call is issued, the stub receives the request
and forwards it to a client runtime program in
the local computer. The client runtime
program has the knowledge of how to
address the remote computer and server
application and sends the message across
the network that requests the remote
procedure.
How it is performed?
The network needs to be made
invisible, so that everything looks just
like ordinary procedure calls. All
networking should be done by the RPC
implementation, such as connecting to
the remote machine. On the remote
machine this simple function gets
executed:
int remote_time(char *time_buf) { struct tm
*time; time_t t; time(&t); time =
localtime(&t); strcpy(time_buf,
asctime(time)); return 0; }
Tools are available for a programmer to
use in developing RPC applications
over a wide variety of platforms,
including Windows (3.1, NT, 95),
Macintosh, 26 variants of UNIX, OS/2,
NetWare, and VMS
Source:
http://pandonia.canberra.edu.au/OS/l14_1.
html
Source:
http://www.sei.cmu.edu/str/descriptions/rpc.html
Summary
RPC is a protocol which allows a program running on
one host to cause code to be executed on another host
without the programmer needing to explicitly the code .
RPC is an easy and popular paradigm for implementing
the client-server model. An RPC is initiated by the caller
(client) sending request message to a remote system
(the server) to execute a certain procedure using
arguments supplied. A result message is returned to the
caller.
What is MOM?
1. Mediator for messages (Broker)
2. Asynchronous communcation architecture
CORBA 3.0
1. Messaging (MOM)
2. ORB takes functions from MOM (MOB)
3. no standard
Why do you need a Message-oriented Broker (MOB) ?
1. Accessing to remote data and processes through an internet or
intranet
2. Building applications involving multiple servers and clients
3. Simultaneous acces to heterogeneous information (RDBMS, ODBMS,
Legacy DB)
4. Decoupling of Client and Server
Message Passing (PtP)
•direct communication
•connection oriented
•synchronous transfer
•asynchronous transfer
(callback)
Message Queuing (MQ)
•indirect communication over message
queuing
•connectionless
•asynchronous transfer
(polling,callback)
Publish & Subscribe (Pub/Sub)
•indirect communication over messageoriented Broker
•connectionless
•asynchronous transfer (polling,callback)
Disadvantage
MOM incompatible with other Mom
implementation
Dependent on the MOM vendor for
maintenance and future
enhancement
Transaction Processing Monitor
Transaction Processing Monitor
Origin of TP Monitors
Purpose of TP Monitors
What are TP Monitors?
What do TP Monitors do?
Example of a TP Monitors
Features of TP Monitors
References
Origin of TP Monitors
TP monitor technology emerged 25 years
ago when Atlantic Power and Light created
an online support environment to share
concurrently applications services and
information resources with the batch and
time sharing operating systems
environment.
Purpose of TP Monitors
Transaction processing (TP) monitor
technology provides the distributed
client/server environment the capacity to
efficiently and reliably develop, run, and
manage transaction applications.
What are TP Monitors?
A TPM is a standalone program, distinct from the
Web server and app server.
TP monitor technology controls transaction
applications and performs business logic/rules
computations and database updates.
TP monitor technology is used in data
management, network access, security systems,
delivery order processing, airline reservations,
and customer service
What do TP Monitors do?
Its mission is to monitor workflow
status for transactions that require
multiple steps. The TPM generally
has the capability to post alerts and
rollback errors or generate
compensating transactions when an
error occurs.
Examples of TP Monitors
CICS (Customer Information Control
System) by IBM.
TUXEDO by BEA.
Customer Information Control System
a family of application servers and
connectors that provides industrialstrength, online transaction
management and connectivity for
mission-critical applications.
Customer Information Control System
CICS handles more than thirty billion
transactions per day
Each day CICS processes more than $1
trillion in transactions
More than thirty million people use CICS
CICS can support over nine hundred
thousand concurrent users
Customer Information Control System
CICS supports numerous application
development environments and models
including COBOL, PL/I, Java, EJB and Object
Oriented (OO), in any combination.
CICS provides unmatched scalability,
performance, throughput, reliability, security and
data integrity - all essential for e-business.
CICS runs on z/OS, OS/390 and VSE/ESA.
CICS API is also available on AIX, Windows NT,
Solaris, HP-UX via TXSeries.
TUXEDO
BEA Tuxedo is the backbone for
enabling transactions that
stretch from front-end ecommerce applications to backoffice processes, across any
system, anywhere in the world.
TUXEDO: Features
Business-critical reliability. BEA Tuxedo has been
tested and proven in thousands of the most demanding
mission-critical applications.
Virtually unlimited scalability. As demands increase,
additional servers can be added on the fly without
disrupting ongoing operations.
Simplified development. You can focus on enterprise
applications while BEA Tuxedo handles the underlying
complexity of distributed applications.
Unparalleled high-performance. BEA Tuxedo is
designed for large-scale, Web-to-mainframe enterprise
solutions.
TUXEDO: Client/Server Model
Features of TP Monitors
Load balancing: is a technique used for
distributing service requests evenly among
servers that offer the same service.
Features of TP Monitors
Priorities determine the
order in which service
requests are dequeued
by a server. Priority is
assigned by a client to
individual services and
can range from 1 to100,
where 100 represents
the highest priority.
Other features of TP Monitors
Data compression
Data encoding
Data encryption
Event management
Security management
References
Customer Information Control System
www.ibm.com
Tuxedo
www.bea.com
Transaction Processing Monitor
TPM
Whatis website
www.whatis.com
In Summary:
Middleware is essential to migrating mainframe
applications to client/server applications and to
providing for communication across
heterogeneous platforms.
Middleware is sometimes called plumbing
because it connects two sides of an application
and passes data between them.
Key Words:
Middleware
TP monitors
Message-Oriented Middleware (MOM),
RPC systems
Object Request Brokers (ORBs)
Database access systems
References:
http://www.middleware.org/
http://www.darwinmag.com/learn/curve/col
umn.html?ArticlelD=93
http://www.sei.cmu.edu/str/descriptions/mi
ddleware.html