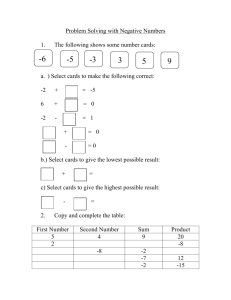
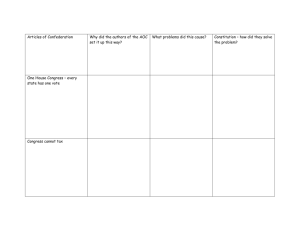
HSS Judicial Deference DA
advertisement

Deference DA 1NC – Deference DA 1NC – Deference DA For NSA surveillance matters, the courts currently grant deference to the executive. Only the executive can make decisions on national security matters. Kalanges 14 – Shaina, second-year law student at the Northern Illinois University College of Law with a Bachelor of Arts from the University of Illinois Urbana-Champaign, Assistant Editor of the Northern Illinois University Law Review, 2014 (“Modern Private Data Collection and National Security Agency Surveillance: A Comprehensive Package of Solutions Addressing Domestic Surveillance Concerns,” Northern Illinois University Law Review (34 N. Ill. U. L. Rev. 643) Available Online to Subscribing Institutions via Lexis-Nexis) [*652] On the other hand, Judge Pauley from the Southern District of New York delivered an opposite ruling in ACLU v. Clapper, nearly ten days after Judge Leon ruled in Klayman. n64 Judge Pauley reasoned that the NSA could not achieve its objective of combating future terrorist attacks if it could not conduct a sweeping collection of every telephone record. n65 Like Judge Leon, Judge Pauley described the querying system the NSA uses on surveillance targets. n66 However, unlike Judge Leon, Judge Pauley discerned a greater purpose behind the queries and held that the system was constitutional and kept with the Smith precedent. n67 Judge Pauley applied Smith to find that the communication records were already handed over to private companies by citizens who could not expect that the information could still be considered private to the individual. n68 Judge Pauley took his analysis a step further and bolstered a need to keep FISC matters secret by citing historical deference to the executive when it comes to matters of national security. n69 Judge Pauley dismissed the ACLU's claim and held that the program was meant to remain classified and unchallenged and that telephony metadata collection is constitutional. n70 Also, Judge Pauley held that a mere fear of chilling of free speech does not provide standing to challenge telephony metadata collection. n71 While cellular technology evolved since Smith, Judge Pauley cited the Klayman court and maintained that metadata remains unchanged and that the information gathered only contains phone numbers, dates, and times. n72 Judge Pauley also commented on the previous issues FISC faced, explaining that the FISC followed court rules to weed out issues of noncompliance in the past. n73 The Intelligence Committees received detailed reports of those noncompliance issues, which were addressed with tighter standards on the NSA from the FISC. n74 Accordingly, the NSA director also did comprehensive evaluations of section 215 practices and established the position of the director of compliance. n75 [*653] While Judge Pauley reasoned that any issues with noncompliance were weeded out of the current surveillance process, one legislative proposal, which gained nearly eighty-five sponsors, reacts to this issue quite differently and suggests that more may be done to insure American civil liberties. n76 Additionally, Judge Leon in Klayman picked apart the examples of metadata collection that the government provided to demonstrate the metadata program's progress in preventing terrorist attacks. n77 The Klayman court discerned that any uncovered terrorists were already found with other evidence that the metadata program merely corroborated. n78 Judge Pauley, in Clapper, held to the contrary and used some examples to demonstrate how section 215 surveillance stops terrorist attacks before they take place. n79 Judge Pauley even explained that the current program would have identified and prevented 9/11 hijacker Khalid Al-Mihdhar from carrying out his attack. n80 Nonetheless, both Judge Leon and Judge Pauley agreed on one point: that the legislature constructed FISA to exclude third party surveillance targets from challenging the NSA's compliance with the statute. n81 But both judges agreed that claims challenging the constitutionality of the statute were not precluded. n82 While Smith may never be overturned, distinguishing NSA surveillance from the surveillance in Smith may open the door to new Supreme Court precedent setting or suggesting constitutional guidelines for certain domestic surveillance practices. n83 The ACLU and the Supreme Court may have the potential to shape domestic privacy expectations with the Constitution under their belt, but Judge Pauley was correct in holding that deference should be granted to the executive in dealing with matters of national security. n84 Ultimately, the executive will decide where NSA surveillance is headed. n85 The Supreme Court will have Judge Pauley's point in mind and avoid appearing to undermine executive determinations if any ruling on the constitutionality of [*654] NSA practices emerges. n86 Accordingly, since President Obama approved continued surveillance under section 702 and section 215, the greatest policy changes in NSA practices may likely be implemented through legislative action that a Supreme Court ruling would heavily influence by articulating some constitutional guidelines, furthering down the path of Keith. n87 Breaking judicial deference to the executive in matters of intelligence gathering undermines executive flexibility. Yoo 14 — John Yoo, Emanuel Heller Professor of Law at the University of California, Berkley, Visiting Scholar at the American Enterprise Institute, J.D. from Yale University, 2014 (“NSA Spying — Will Obama Lead or Punt to Courts, Congress and Harm the Presidency?,” American Enterprise Institute, January 4th, Accessible Online at http://www.foxnews.com/opinion/2014/01/07/nsa-spying-will-obama-lead-or-punt-to-courtscongress-and-harm-presidency.html) Under Barack Obama, the presidency’s control over national security intelligence has come under a [damaging] crippling cross-fire. From the right, in December Bush-appointed Judge Richard Leon found the National Security Agency’s “Orwellian” phone records collection program to violate the Constitution. From the left, the White House’s own blue-ribbon commission recently urged the president to place an “out of control” NSA under unprecedented judicial, bureaucratic, and even private controls. If he makes the same mistake again, Mr. Obama will follow in the footsteps of failed presidents who shrunk before similar challenges, to the long-term harm of their office. Mr. Obama may rise up to defend the NSA from the growing chorus of critics in Congress, the media, and the antiwar wing of his own party. He might blunt the effort to subject the NSA’s national security mission to the stricter rules that govern domestic law enforcement. He might even preserve the intelligence agency’s ability to collect phone calls and email data that, by the account of two successive administrations of both parties, has stopped terrorist attacks on the United States and its allies. But don’t count on it. Mr. Obama’s first instinct is to shift national security responsibility to other branches of government — witness his past attempts to try the 9/11 plotters in civilian court in New York City, move the terrorists in Guantanamo Bay, Cuba to a domestic prison, and ask Congress decide on intervening in Syria. If he makes the same mistake again, Mr. Obama will follow in the footsteps of failed presidents who shrunk before similar challenges, to the long-term harm of their office. Kicking the intelligence question to Congress or the courts undermines the Oval Office by reversing the polarity of its constitutional powers. The Framers created the presidency precisely because foreign affairs and national security pose unique challenges to a legislature, which cannot react quickly to sudden, unforeseen events. “Decision, activity, secrecy, and dispatch will generally characterize the proceedings of one man,” Alexander Hamilton explained in “Federalist 70.” Only a single president could marshal the nation’s resources with the energy and vigor to effectively protect its security. “Of all the cares or concerns of government,” he added in “Federalist 74,” “the direction of war most peculiarly demands those qualities which distinguish the exercise of power by a single hand.” Presidents who have defied the Framers’ design have led the nation into some of its greatest disasters, despite their great intellect or political skills. Executive flexibility is crucial to stopping terrorism, preventing WMD proliferation, deterring rogue nations, and staying in line with multilateral alliances. This trumps constitutionality – the international scene is changing. Li 09 – Zheyao, Candidate, Georgetown University Law Center; B.A., Political Science and History, Yale University, 2009 (“War Powers for the Fourth Generation: Constitutional Interpretation in the Age of Asymmetric Warfare,” Georgetown Journal of Law & Public Policy (Vol. 7, No. 1, p. 373) Available Online to Subscribing Institutions via Lexis-Nexis) IV. WAR POWERS IN THE FOURTH GENERATION OF WARFARE A. The Emergence of Non-State Actors Even as the quantity of nation-states in the world has increased dramatically since the end of World War II, the institution of the nation-state has been in decline over the past few decades. Much of this decline is the direct result of the waning of major interstate war, which primarily resulted from the introduction of nuclear weapons.122 The proliferation of nuclear weapons, and their immense capacity for absolute destruction, has ensured that conventional wars remain limited in scope and duration. Hence, "both the size of the armed forces and the quantity of weapons at their disposal has declined quite sharply" since 1945.123 At the same time, concurrent with the decline of the nation-state in the second half of the twentieth century, non-state actors have increasingly been willing and able to use force to advance their causes. In contrast to nation-states, who adhere to the Clausewitzian distinction between the ends of policy and the means of war to achieve those ends, non-state actors do not necessarily fight as a mere means of advancing any coherent policy. Rather, they see their fight as a lifeand-death struggle, wherein the ordinary terminology of war as an instrument of policy breaks down because of this blending of means and ends.124 It is the existential nature of this struggle and the disappearance of the Clausewitzian distinction between war and policy that has given rise to a new generation of warfare. The concept of fourthgenerational warfare was first articulated in an influential article in the Marine Corps Gazette in 1989, which has proven highly prescient. In describing what they saw as the modem trend toward a new phase of warfighting, the authors argued that: In broad terms, fourth generation warfare seems likely to be widely dispersed and largely undefined; the distinction between war and peace will be blurred to the vanishing point. It will be nonlinear, possibly to the point of having no definable battlefields or fronts. The distinction between "civilian" and "military" may disappear. Actions will occur concurrently throughout all participants' depth, including their society as a cultural, not just a physical, entity. Major military facilities, such as airfields, fixed communications sites, and large headquarters will become rarities because of their vulnerability; the same may be true of civilian equivalents, such as seats of government, power plants, and industrial sites (including knowledge as well as manufacturing industries). 125 It is precisely this blurring of peace and war and the demise of traditionally definable battlefields that provides the impetus for the formulation of a new theory of war powers. As evidenced by Part M, supra, the constitutional allocation of war powers, and the Framers' commitment of the war power to two co-equal branches, was not designed to cope with the current international system, one that is characterized by the persistent machinations of international terrorist organizations, the rise of multilateral alliances, the emergence of rogue states, and the potentially wide proliferation of easily deployable weapons of mass destruction, nuclear and otherwise. B. The Framers' World vs. Today's World The Framers crafted the Constitution, and the people ratified it, in a time when everyone understood that the state controlled both the raising of armies and their use. Today, however, the threat of terrorism is bringing an end to the era of the nation-state's legal monopoly on violence, and the kind of war that existed before-based on a clear division between government, armed forces, and the people-is on the decline. 126 As states are caught between their decreasing ability to fight each other due to the existence of nuclear weapons and the increasing threat from non-state actors, it is clear that the Westphalian system of nation-states that informed the Framers' allocation of war powers is no longer the order of the day. 127 As seen in Part III, supra, the rise of the modem nation-state occurred as a result of its military effectiveness and ability to defend its citizens. If nation-states such as the United States are unable to adapt to the changing circumstances of fourth-generational warfare-that is, if they are unable to adequately defend against low-intensity conflict conducted by non-state actors-"then clearly [the modem state] does not have a future in front of it.' 128 The challenge in formulating a new theory of war powers for fourth generational warfare that remains legally justifiable lies in the difficulty of adapting to changed circumstances while remaining faithful to the constitutional text and the original meaning. 29 To that end, it is crucial to remember that the Framers crafted the Constitution in the context of the Westphalian system of nation-states. The three centuries following the Peace of Westphalia of 1648 witnessed an international system characterized by wars, which, "through the efforts of governments, assumed a more regular, interconnected character."' 130 That period saw the rise of an independent military class and the stabilization of military institutions. Consequently, "warfare became more regular, better organized, and more attuned to the purpose of war-that is, to its political objective."'1 3 ' That era is now over. Today, the stability of the long-existing Westphalian international order has been greatly eroded in recent years with the advent of international terrorist organizations, which care nothing for the traditional norms of the laws of war. This new global environment exposes the limitations inherent in the interpretational methods of originalism and textualism and necessitates the adoption of a new method of constitutional interpretation. While one must always be aware of the text of the Constitution and the original understanding of that text, that very awareness identifies the extent to which fourthgenerational warfare epitomizes a phenomenon unforeseen by the Framers, a problem the constitutional resolution of which must rely on the good judgment of the present generation. 13 Now, to adapt the constitutional warmarking scheme to the new international order characterized by fourth-generational warfare, one must understand the threat it is being adapted to confront. C. The Jihadist Threat The erosion of the Westphalian and Clausewitzian model of warfare and the blurring of the distinction between the means of warfare and the ends of policy, which is one characteristic of fourth-generational warfare, apply to al-Qaeda and other adherents of jihadist ideology who view the United States as an enemy. An excellent analysis of jihadist ideology and its implications for the rest of the world are presented by Professor Mary Habeck. 133 Professor Habeck identifies the centrality of the Qur'an, specifically a particular reading of the Qur'an and hadith (traditions about the life of Muhammad), to the jihadist terrorists. 134 The jihadis believe that the scope of the Qur'an is universal, and "that their interpretation of Islam is also intended for the entire world, which must be brought to recognize this fact peacefully if possible and through violence if not."' 135 Along these lines, the jihadis view the United States and her allies as among the greatest enemies of Islam: they believe "that every element of modern Western liberalism is flawed, wrong, and evil" because the basis of liberalism is secularism. 136 The jihadis emphasize the superiority of Islam to all other religions, and they believe that "God does not want differing belief systems to coexist."' 37 For this reason, jihadist groups such as al-Qaeda "recognize that the West will not submit without a fight and believe in fact that the Christians, Jews, and liberals have united against Islam in a war that will end in the complete destruction of the unbelievers.' 138 Thus, the adherents of this jihadist ideology, be it al-Qaeda or other groups, will continue to target the United States until she is destroyed. Their ideology demands it. 139 To effectively combat terrorist groups such as al-Qaeda, it is necessary to understand not only how they think, but also how they operate. Al-Qaeda is a transnational organization capable of simultaneously managing multiple operations all over the world."14 It is both centralized and decentralized: al-Qaeda is centralized in the sense that Osama bin Laden is the unquestioned leader, but it is decentralized in that its operations are carried out locally, by distinct cells."4 AI- Qaeda benefits immensely from this arrangement because it can exercise direct control over high-probability operations, while maintaining a distance from low-probability attacks, only taking the credit for those that succeed. The local terrorist cells benefit by gaining access to alQaeda's "worldwide network of assets, people, and expertise."' 42 Post-September 11 events have highlighted al-Qaeda's resilience. Even as the United States and her allies fought back, inflicting heavy casualties on al-Qaeda in Afghanistan and destroying dozens of cells worldwide, "alQaeda's networked nature allowed it to absorb the damage and remain a threat." 14 3 This is a far cry from earlier generations of warfare, where the decimation of the enemy's military forces would generally bring an end to the conflict. D. The Need for Rapid Reaction and Expanded Presidential War Power By now it should be clear just how different this conflict against the extremist terrorists is from the type of warfare that occupied the minds of the Framers at the time of the Founding. Rather than maintaining the geographical and political isolation desired by the Framers for the new country, today's United States is an international power targeted by individuals and groups that will not rest until seeing her demise. The Global War on Terrorism is not truly a war within the Framers' eighteenth-century conception of the term, and the normal constitutional provisions regulating the division of war powers between Congress and the President do not apply. Instead, this "war" is a struggle for survival and dominance against forces that threaten to destroy the United States and her allies, and the fourth-generational nature of the conflict, highlighted by an indiscernible distinction between wartime and peacetime, necessitates an evolution of America's traditional constitutional warmaking scheme. As first illustrated by the military strategist Colonel John Boyd, constitutional decision-making in the realm of war powers in the fourth generation should consider the implications of the OODA Loop: Observe, Orient, Decide, and Act. 44 In the era of fourth-generational warfare, quick reactions, proceeding through the OODA Loop rapidly, and disrupting the enemy's OODA loop are the keys to victory. "In order to win," Colonel Boyd suggested, "we should operate at a faster tempo or rhythm than our adversaries." 145 In the words of Professor Creveld, "[b]oth organizationally and in terms of the equipment at their disposal, the armed forces of the world will have to adjust themselves to this situation by changing their doctrine, doing away with much of their heavy equipment and becoming more like police."1 46 Unfortunately, the existing constitutional understanding, which diffuses war power between two branches of government, necessarily (by the Framers' design) slows down decision- making. In circumstances where war is undesirable (which is, admittedly, most of the time, especially against other nation-states), the deliberativeness of the existing decision-making process is a positive attribute. In America's current situation, however, in the midst of the conflict with al-Qaeda and other international terrorist organizations, the existing process of constitutional decision-making in warfare may prove a fatal hindrance to achieving the initiative necessary for victory. As a slow-acting, deliberative body, Congress does not have the ability to adequately deal with fast-emerging situations in fourth-generational warfare. Thus, in order to combat transnational threats such as al-Qaeda, the executive branch must have the ability to operate by taking offensive military action even without congressional authorization, because only the executive branch is capable of the swift decision-making and action necessary to prevail in fourth-generational conflicts against fourth generational opponents. 2NC/1NR – Link Uniqueness Secret State Privilege Doctrine Courts unanimously support deference in the squo – stats – the trend will only continue Ellington 15 Thomas C. Ellington, Associate Professor of Political Science at Weslyan College, 2015, (Secrecy, Law and Society, Routledge, Edited by Greg Martin, Rebecca Bray, and Miiko Kumar: Faculty Members of the Department of Law at the University of Sydney, Chapter 3: Secrecy law and its problems in the United States) - AW Judicial deference at its most extreme, however, is found in the application of the state secrets privilege, under which the government withholds evidence by claiming that revealing it to a judge or opposing counsel would tend to endanger national security. Accordingly, '[b]ecause successful invocation of the privilege involves no independent judicial review of the evidence, critics worry that it opens the door to abuse by the executive branch’. 41 Louis Fisher provides the definitive account of the origins of state secrets privilege and some of the problems in its underlying doctrine.’ 42 Two things are worth noting: 1. the state secrets privilege has its origins in a case in which the government has since been shown definitely to have mischaracterised the nature of the evidence it was withholding; and 2. the US Government has increasingly invoked the state secrets privilege in recent years as a way of shutting down civil litigation in cases involving such subjects as extraordinary rendition and blanket eavesdropping by the NSA. 43 What had once been a moribund piece of judicial doctrine has found new life under the Bush and Obama administrations. Laura K. Donohue counts more than 100 instances in which the Bush administration invoked the state secrets privilege.” Despite setting a new policy that is supposed to limit the circumstances in which the state secrets privilege is invoked, 45 the Obama Justice Department continues to use this flawed doctrine extensively. The Federation of American Scientists maintains an ongoing list of state secrets claims.” 46 Courts, almost unanimously, have east their lot with national security, granting considerable deference to government assertions of the state secrets principle. This deference to state secrets shows no signs of abating; indeed, the growing trend is for counts to dismiss these legal challenges pre-discovery.9 Constitutionality On issues of surveillance, the court currently cedes deference to the executive branch – constitutional authority and practical competence. Margulies 14 – Peter, Professor of Law, Roger Williams University School of Law. B.A. 1978, Colgate University; J.D. 1981, Columbia Law School, 2014 (“Dynamic Surveillance: Evolving Procedures in Metadata and Foreign Content Collection After Snowden,” Hastings Law Journal (66 Hastings L.J. 1) Available Online to Subscribing Institutions via Lexis-Nexis) The first opinion to authorize bulk collection was a 2004 opinion by Judge Kollar-Kotelly that granted the government's application under FISA to use a pen register to collect information on the routing or addressing of e-mails, excluding the content of communications. n48 This opinion introduced a concept that would shape collection in the years to come: it coupled authority for the wide collection of information by the government with significant restrictions on the government's use of that information. Judge Kollar-Kotelly assumed that a relevance standard governed both pen registers and FISC orders under section 215. n49 Finding that the statutory language in the FISA pen register provision did not require that the government identify specific targets prior to collection, Judge Kollar-Kotelly acknowledged that the statute allowed "exceptionally broad" acquisition of e-mail records, n50 most of which would be "unrelated" to terrorism. n51 To avoid giving the government the unchecked ability to rummage through these mountains of data, Judge Kollar-Kotelly added restrictions on government analysts' access to the information collected. When structuring queries of the electronic data, Judge Kollar-Kotelly held that analysts could use only those e-mail addresses specifically linked to particular terrorist organizations. n52 No other queries - for example, addresses of celebrities or government critics - were permissible. Supporting her analysis, Judge Kollar-Kotelly suggested that Congress intended the relevance standard in the pen register provision to broaden information gathering for national security purposes. The relevance standard replaced language that required only a "reasonable suspicion" that the communication facility subject to the pen register be [*13] used by an individual engaged in "international terrorism or clandestine intelligence activities." n53 Collecting e-mail metadata from a range of Internet service providers ("ISPs") would meet the relevance standard, the court found, accepting the government's argument. n54 Broad collection would allow the government to ferret out previously unknown e-mail addresses linked to terrorism, which "more precisely targeted forms of collection against known accounts" would exclude. n55 The court defended its deference to the government's rationale, finding that, "for reasons of both constitutional authority and practical competence, deference should be given to the fully considered judgment of the executive branch in assessing and responding to national security threats and in determining the potential significance of intelligencerelated information." n56 Empirics Judicial deference is empirically proven. The Supreme Court refused to take a major case involving NSA surveillance; instead, leaving it to the executive branch. Richey 13 – Warren, staff writer for The Christian Science Monitor, 2013 (“Supreme Court rejects case on NSA spying on Americans' phone calls; The US Supreme Court on Monday refused to consider whether the NSA, in collecting and storing information about the phone calls of virtually every American, overstepped its authority under the law,” The Christian Science Monitor, Available Online at http://www.csmonitor.com/USA/Justice/2013/1118/SupremeCourt-rejects-case-on-NSA-spying-on-Americans-phone-calls-video) The US Supreme Court on Monday declined to take up a potential major case examining whether the National Security Agency's bulk collection and storage of telephone metadata from virtually every American violate the limits of federal law. The justices turned aside the case without comment. Had they agreed to take up the issue, the stage would have been set for a high-court showdown testing whether the NSA overstepped its authority under the Foreign Intelligence Surveillance Act (FISA) by collecting and storing telephone service information for every telephone call made and received in the US. Several other cases pending in federal district courts challenge the massive collection program as an invasion of Americans' privacy. Aside from the pending court cases, the high court's action on Monday leaves it to the political branches - Congress and the White House - to sort out whether the NSA and other US spy agencies should have the power to make bulk collections of data for later use in intelligence gathering and counter-terrorism. Multiple court cases prove the judiciary defers to the executive on matters of intelligence gathering. Turner 13 Robert Turner, Professor specializing in National Security Law at the University of Virginia, Former Charles H. Stockton Chair of International Law at the U.S. Naval War College, Founder and Associate Director of the Center for National Security Law, 10/21/13, (“First Principles: Are Judicial and Legislative Oversight of NSA Constitutional?”, http://www.fedsoc.org/publications/detail/first-principles-are-judicial-and-legislative-oversight-of-nsaconstitutional) - AW II. Judicial Deference to the Executive That same month, Chief Justice John Marshall—in perhaps the most famous Supreme Court decision of all times—reaffirmed that the Constitution grants the President important powers over foreign affairs that are checked neither by the Legislature nor the Judiciary: By the constitution of the United States, the President is invested with certain important political powers, in the exercise of which he is to use his own discretion, and is accountable only to his country in his political character, and to his own conscience . . . . The subjects are political. They respect the nation, not individual rights, and being intrusted to the executive, the decision of the executive is conclusive. The application of this remark will be perceived by adverting to the act of congress for establishing the department of foreign affairs. This officer, as his duties were prescribed by that act, is to conform precisely to the will of the president. . . . The acts of such an officer, as an officer, can never be examinable by the courts.10 In the 1936 Curtiss-Wright case, the Supreme Court noted that the President “makes treaties with the advice and consent of the Senate; but he alone negotiates. Into the field of negotiation the Senate cannot intrude, and Congress itself is powerless to invade it.”11 In this same landmark case, the Court noted: The marked difference between foreign affairs and domestic affairs in this respect is recognized by both houses of Congress in the very form of their requisitions for information from the executive departments. In the case of every department except the Department of State, the resolution directs the official to furnish the information. In the case of the State Department, dealing with foreign affairs, the President is requested to furnish the information “if not incompatible with the public interest.” A statement that to furnish the information is not compatible with the public interest rarely, if ever, is questioned.12 Now, in candor, I believe the Court in Curtiss-Wright got the right answer for the wrong reasons. Justice Sutherland focused not upon the expressed grant of “executive power” to the President, but instead on the idea that the foreign policy power was a natural attribute of sovereignty that attached to the presidency at the time of America’s independence from Great Britain. It was not an unreasonable explanation (and Curtiss-Wright remains by far the most often cited Supreme Court foreign affairs case), but it is clear that the Framers believed they had expressly vested this power in the President through Article II, Section 1’s grant of “executive power.” This longstanding deference to presidential discretion in foreign affairs was recognized by both the courts and Congress into the second half of the twentieth century. In the 1953 case of United States v. Reynolds, the Supreme Court discussed the executive privilege to protect national security secrets, noting that: “Judicial Experience with the privilege which protects military and state secrets has been limited in this country . . . .” But the Court recognized an absolute privilege for military secrets, explaining: In each case, the showing of necessity [of disclosure] which is made will determine how far the court should probe in satisfying itself that the occasion for invoking the privilege is appropriate. Where there is a strong showing of necessity, the claim of privilege should not be lightly accepted, but even the most compelling necessity cannot overcome the claim of privilege if the court is ultimately satisfied that military secrets are at stake.13 Obviously, intelligence programs run by a Department of Defense agency (NSA) designed to intercept communications from our nation’s enemies during a period of authorized war are among the most sensitive of “military secrets.” Four years later, Professor Edward S. Corwin, one of the nation’s leading constitutional scholars of his era, wrote in his classic volume, The President: Office and Powers: So far as practice and weight of opinion can settle the meaning of the Constitution, it is today established that the President alone has the power to negotiate treaties with foreign governments; that he is free to ignore any advice tendered him by the Senate as to a negotiation; and that he is final judge of what information he shall entrust to the Senate as to our relations with other governments.14 In the 1959 Barenblatt case, the Supreme Court recognized that there are proper limits not only on the power of Congress to control Executive discretion, but even to “inquire” into matters vested by the people in the President: “Congress . . . cannot inquire into matters which are within the exclusive province of one of the other branches of the Government. Lacking the judicial power given to the Judiciary, it cannot inquire into matters that are exclusively the concern of the Judiciary. Neither can it supplant the Executive in what exclusively belongs to the executive.”15 Precedence Actions modifying presidential war power set a precedent. The War Powers Resolution and other historical examples prove. Paul 08 – Christopher, Senior Social Scientist at RAND, 2008 (“US Presidential War Powers: Legacy Chains in Military Intervention Decisionmaking,” Journal of Peace Research (Vol. 45, No. 5) Available Online to Subscribing Institutions via Jstor, p. 665-679) There's an obvious kernel of truth to the old saying, 'Generals always fight the last war'. This article explores one of the sources of this kind of policy inertia, 'legacy chains', by examining the sequence of disputes over military deployments that led up to the United States War Powers Resolution of 1973 and its impact on the US military interventions that have followed. The War Powers Resolution was passed by a Congress attempting to re store balance to war-making powers constitutionally divided between the Congress (as the only body legally allowed to make a 'declaration of war') and the president (the commander in chief). This article traces the war powers legacy chain through the US military operations in Korea, Vietnam, the Dominican Republic, Grenada, Panama, Iraq, Haiti, and Iraq again. The exercise of war powers (and the disputes associated with them) for these military operations show how legacies are formed and institutionalized within a policy sphere; how institutionalized legacies affect subsequent policy (in sometimes unintended ways); and how subsequent policies modify, transform, or reinforce these legacies. Based on the War Powers example and other historical data, this article argues that past policy affects subsequent policy by creating institutional legacies that shape the decision space in which subsequent policy is made. These institutional legacies can be modified, transformed, and/or reinforced by subsequent policymaking and then constitute 'legacy chains'. Legacy Chains Finegold & Skocpol (1995: 222) describe policy legacies: Past and present policies are connected in at least three different ways. First, past policies give rise to analogies that affect how public officials think about contemporary policy issues. Second, past policies suggest lessons that help us to understand the processes by which contemporary policies are formulated and implemented and by which the consequences of contemporary policies will be determined. Third, past policies impose limitations that reduce the range of policy choices available as responses to contemporary problems. All three of the ways in which they connect past policy to present policy can be viewed as changes in the institutional context in which policy is made. These legacies are institutionalized in two different ways: first, through changes in formal rules or procedures, and second, in the 'taken for granteds', 'schemas', and accepted wisdom of policy makers and ordinary citizens alike (Sewell, 1992: 1-29). While a policy or event can leave multiple legacies, it often leaves a single major legacy. For example, the War Powers Resolution formally changed the relationship between the president and the congress with regard to war-making and the deployment of troops. Subsequent military interventions were influenced by this change and have, in turn, left their own legacy (legal scholars might call it precedent) as a link in that chain. Legacy chains can be modified, transformed, or reinforced as they step through each 'link' in the chain. As another example, US involvement in Vietnam left a legacy in the sphere of press/military relations which affected the intervention in Grenada in 1983 (the press was completely excluded for the first 48 hours of the operation). The press legacy chain begun in Vietnam also affected the Panama invasion of 1989 (a press pool was activated, in country, but excluded from the action), but the legacy had been transformed slightly by the Grenada invasion (the press pool system itself grew out of complaint regarding press exclusion in Grenada) (Paul & Kim, 2004). Because of the different ways in which policy legacies are institutionalized, some legacies have unintended institutional consequences. The War Powers Resolution was intended to curtail presidential war-making powers and return some authority to the congress. In practice, the joint resolution failed to force presidents to include congressional participation in their intervention decision making, but it had the unintended consequence of forcing them to change the way they planned interventions to comply with the letter of the law (see the extended ex ample presented later in the article).1 They Say: “Second Circuit Ruling on Section 215 Thumps” The Second Circuit Ruling on Section 215 was a matter of statutory ambiguity, not about constitutionality. On matter of constitutionality, the Second Circuit acknowledges they don’t have the expertise to make decisions that could impact national security and defers its authority. Kerr 15 – Orin, Fred C. Stevenson Research Professor of Law, 2015 (“Second Circuit rules, mostly symbolically, that current text of Section 215 doesn’t authorize bulk surveillance,” The Washington Post, May 7th, Available Online at http://www.washingtonpost.com/news/volokhconspiracy/wp/2015/05/07/second-circuit-rules-mostly-symbolically-that-current-text-ofsection-215-doesnt-authorize-bulk-surveillance/) Edward Snowden’s biggest leak was that the Foreign Intelligence Surveillance Court had interpreted Section 215 of the Patriot Act to authorize bulk collection of everyone’s phone records. This was astonishing news, as nothing on the face of the face of the statute suggested it had that anything like that broad a reach. Legal challenges followed, on both statutory and constitutional grounds. This morning, the Second Circuit finally handed down its opinion on one of the pending legal challenges. It’s the first appellate court ruling on the issue. Today’s decision rules that the text of Section 215 does not authorize the program as a matter of statutory law. The Second Circuit does not reach whether the NSA program violates the Fourth Amendment. My initial reaction, on a first read, is that the Second Circuit’s decision is mostly symbolic. As regular readers know, I agree with the court’s bottom line statutory analysis that Section 215 doesn’t authorize the NSA program. But while you would normally think that a ruling on such an important question by a court as important as the Second Circuit would be a big deal, I’m not sure the Second Circuit’s opinion actually matters very much. The main reason is that Section 215 sunsets in three weeks. The Second Circuit ruling does not enjoin the NSA program. It does not rule on the Fourth Amendment question. It mostly interprets statutory language that goes off the books in a few weeks, with the understanding that the court’s ruling won’t be implemented by the district court in that time window. So from a practical perspective, it’s mostly symbolic. With that said, the decision is a rebuke to the Foreign Intelligence Surveillance Court for the FISC’s statutory analysis that approved the bulk telephone metadata program. Here’s a rundown of the majority opinion, with some additional thoughts of mine at the end. 1. Standing The opinion begins by concluding that any person whose data is collected as part of the program has Article III standing to challenge the program. Article III standing to challenge the program is not limited to those whose data was queried, but rather to anyone whose data was collected. This is perhaps the most confusing part of the opinion, because the Court somewhat oddly blends together Article III and Fourth Amendment principles to create a sort of Article III standing doctrine for challenges that include Fourth Amendment claims — even though the court then doesn’t rule on the Fourth Amendment claims. Here’s what the court says: Appellants challenge the telephone metadata program as a whole, alleging injury from the very collection of their telephone metadata. And, as the district court observed, it is not disputed that the government collected telephone metadata associated with the appellants’ telephone calls. The Fourth Amendment protects against unreasonable searches and seizures. Appellants contend that the collection of their metadata exceeds the scope of what is authorized by § 215 and constitutes a Fourth Amendment search. We think such collection is more appropriately challenged, at least from a standing perspective, as a seizure rather than as a search. Whether or not such claims prevail on the merits, appellants surely have standing to allege injury from the collection, and maintenance in a government database, of records relating to them. “[A] violation of the [Fourth] Amendment is fully accomplished at the time of an unreasonable governmental intrusion.” United States v. Verdugo‐Urquidez, 494 U.S. 259, 264 (1990) (internal quotation marks omitted). If the telephone metadata program is unlawful, appellants have suffered a concrete and particularized injury fairly traceable to the challenged program and redressable by a favorable ruling. Further, there’s Article III standing because there’s a kind of search at issue here, whether or not it is a “search” in the technical Fourth Amendment sense: Finally, the government admits that, when it queries its database, its computers search all of the material stored in the database in order to identify records that match the search term. In doing so, it necessarily searches appellants’ records electronically, even if such a search does not return appellants’ records for close review by a human agent. There is no question that an equivalent manual review of the records, in search of connections to a suspect person or telephone, would confer standing even on the government’s analysis. That the search is conducted by a machine might lessen the intrusion, but does not deprive appellants of standing to object to the collection and review of their data. 2. Preclusion The court next rules that nothing in the text of Section 215 or FISA more generally precludes the usual rule that executive action can be challenged in court under the Administrative Procedure Act: The government has pointed to no affirmative evidence, whether “clear and convincing” or “fairly discernible,” that suggests that Congress intended to preclude judicial review. Indeed, the government’s argument from secrecy suggests that Congress did not contemplate a situation in which targets of § 215 orders would become aware of those orders on anything resembling the scale that they now have. That revelation, of course, came to pass only because of an unprecedented leak of classified information. That Congress may not have anticipated that individuals like appellants, whose communications were targeted by § 215 orders, would become aware of the orders, and thus be in a position to seek judicial review, is not evidence that Congress affirmatively decided to revoke the right to judicial review otherwise provided by the APA in the event the orders were publicly revealed. . . . [T]he government relies on bits and shards of inapplicable statutes, inconclusive legislative history, and inferences from silence in an effort to find an implied revocation of the APA’s authorization of challenges to government actions. That is not enough to overcome the strong presumption of the general command of the APA against such implied preclusion. Congress, of course, has the ability to limit the remedies available under the APA; it has only to say so. But it has said no such thing here. We should be cautious in inferring legislative action from legislative inaction, or inferring a Congressional command from Congressional silence. At most, the evidence cited by the government suggests that Congress assumed, in light of the expectation of secrecy, that persons whose information was targeted by a § 215 order would rarely even know of such orders, and therefore that judicial review at the behest of such persons was a non‐ issue. But such an assumption is a far cry from an unexpressed intention to withdraw rights granted in a generally applicable, explicit statute such as the APA. 3. The Statutory Merits On the statutory merits, the court concludes that Section 215 doesn’t support the program. As drafted and passed by Congress, Section 215 is just a grand jury subpoena authority: In adopting § 215, Congress intended to give the government, on the approval of the FISC, broad‐ ranging investigative powers analogous to those traditionally used in connection with grand jury investigations into possible criminal behavior. Bulk metadata collection just doesn’t fit in the traditional powers of a grand jury subpoena authority: The records demanded are all‐encompassing; the government does not even suggest that all of the records sought, or even necessarily any of them, are relevant to any specific defined inquiry. Rather, the parties ask the Court to decide whether § 215 authorizes the “creation of a historical repository of information that bulk aggregation of the metadata allows,” Appellees’ Br. 32, because bulk collection to create such a repository is “necessary to the application of certain analytic techniques,” Appellants’ Br. 23. That is not the language in which grand jury subpoenas are traditionally discussed. Thus, the government takes the position that the metadata collected – a vast amount of which does not contain directly “relevant” information, as the government concedes – are nevertheless “relevant” because they may allow the NSA, at some unknown time in the future, utilizing its ability to sift through the trove of irrelevant data it has collected up to that point, to identify information that is relevant. We agree with appellants that such an expansive concept of “relevance” is unprecedented and unwarranted. The statutes to which the government points have never been interpreted to authorize anything approaching the breadth of the sweeping surveillance at issue here. . . . .The metadata concerning every telephone call made or received in the United States using the services of the recipient service provider are demanded, for an indefinite period extending into the future. The records demanded are not those of suspects under investigation, or of people or businesses that have contact with such subjects, or of people or businesses that have contact with others who are in contact with the subjects – they extend to every record that exists, and indeed to records that do not yet exist, as they impose a continuing obligation on the recipient of the subpoena to provide such records on an ongoing basis as they are created. The government can point to no grand jury subpoena that is remotely comparable to the real‐time data collection undertaken under this program. As I put the same point in my recent article, for the text of Section 215 to authorize bulk collection, “any federal prosecutor anywhere in the country could have compelled every phone company to hand over all of its telephony metadata on an ongoing basis so long as the prosecutor claimed that it was necessary to help solve a case. It is hard to imagine a federal judge allowing such a subpoena in a criminal case[.]” Also, the Second Circuit rejects the argument that Congress knew about the program and impliedly approved it: The program wasn’t widely known in Congress and the public wasn’t aware of it. And that brings us to the Second Circuit’s bottom line: We conclude that to allow the government to collect phone records only because they may become relevant to a possible authorized investigation in the future fails even the permissive “relevance” test. Just as “the grand jury’s subpoena power is not unlimited,” United States v. Calandra, 414 U.S. 338, 346 (1974), § 215’s power cannot be interpreted in a way that defies any meaningful limit. Put another way, we agree with appellants that the government’s argument is “irreconcilable with the statute’s plain text.” Appellants’ Br. 26. Such a monumental shift in our approach to combating terrorism requires a clearer signal from Congress than a recycling of oft‐used language long held in similar contexts to mean something far narrower. “Congress . . . does not alter the fundamental details of a regulatory scheme in vague terms or ancillary provisions — it does not . . . hide elephants in mouseholes.” Whitman v. Am. Trucking Ass’ns., 531 U.S. 457, 468 (2001). The language of § 215 is decidedly too ordinary for what the government would have us believe is such an extraordinary departure from any accepted understanding of the term “relevant to an authorized investigation.” That’s correct, I think. 4. The Fourth Amendment Having ruled for the challengers on the statutory claim, the court does not rule on the Fourth Amendment challenge. However, the court decides to “discuss” the Fourth Amendment issue anyway because the finds the issue “potentially vexing.” The court’s discussion is mostly about the role of Congress. Congress should take “the primary role . . . in deciding, explicitly and after full debate, whether such programs are appropriate and necessary.” Further, the court would see express statutory authorization as relevant to constitutionality: [W]hether Congress has considered and authorized a program such as this one is not irrelevant to its constitutionality. The endorsement of the Legislative Branch of government provides some degree of comfort in the face of concerns about the reasonableness of the government’s assertions of the necessity of the data collection. Congress is better positioned than the courts to understand and balance the intricacies and competing concerns involved in protecting our national security, and to pass judgment on the value of the telephone metadata program as a counterterrorism tool. Moreover, the legislative process has considerable advantages in developing knowledge about the far‐reaching technological advances that render today’s surveillance methods drastically different from what has existed in the past, and in understanding the consequences of a world in which individuals can barely function without involuntarily creating metadata that can reveal a great deal of information about them. A congressional judgment as to what is “reasonable” under current circumstances would carry weight – at least with us, and, we assume, with the Supreme Court as well – in assessing whether the availability of information to telephone companies, banks, internet service providers, and the like, and the ability of the government to collect and process volumes of such data that would previously have overwhelmed its capacity to make use of the information, render obsolete the third‐party records doctrine or, conversely, reduce our expectations of privacy and make more intrusive techniques both expected and necessary to deal with new kinds of threats. As a result, Congress passes an executive supported bill – the FREEDOM Act. Peterson and Paletta 15 – Kristina and Damian, both reporters for The Wall Street Journal, 2015 (“Congress Reins In NSA’s Spying Powers,” The Wall Street Journal, June 2nd, Available Online at http://www.wsj.com/articles/senate-passes-house-bill-overhauling-nsasurveillance-program-1433277227) WASHINGTON—A long-running congressional battle over privacy and surveillance ended Tuesday when the Senate voted to curb the collection of millions of Americans’ phone records, the first significant retrenchment of government spying powers since the 9/11 attacks. The measure, which was signed Tuesday night by President Barack Obama, will reauthorize and reboot the provisions of the USA Patriot Act that lapsed Sunday at midnight, but it will phase out the National Security Agency’s bulk phone-records program. The bill, passed by the Senate Tuesday in a 67-32 vote, will shift storage of the phone records to telecommunications companies over six months. Supporters said the legislation marked a victory for civil liberties diminished by laws put in place in the wake of the September 2001 terror attacks. “Today the American people are now safe from the federal government’s collection of their personal data,” said Sen. Mike Lee of Utah, the bill’s chief GOP proponent in the Senate. The House approved the bill, known as the USA Freedom Act, in May. The bill will require the NSA and Federal Bureau of Investigation to obtain phone records for most counterterror investigations and other probes on a case-by-case basis from telecommunications companies. This would end the nine-year-old practice underpinned by Section 215 of the Patriot Act, which allowed the NSA to hold the telephone records of millions of Americans, regardless of any person’s background or behavior. The bulk data collection didn’t include the content of the calls themselves. The Central Intelligence Agency, the Justice Department and the White House all supported the curbs, a reflection of government officials’ shifting stance on surveillance since former NSA contractor Edward Snowden’s 2013 leaks about secretive data collection. They Say: “Deference to FISA is More Likely” The executive has jurisdiction and authority over domestic electronic intelligence gathering; data is crucial to national security issues. Furthermore, judicial deference would go to the executive, not the FISA courts. This framework for executive authority is most reasonable, complying with the Fourth Amendment. Yoo 14 – John, Emanuel Heller Professor of Law at the University of California, Berkley, Visiting Scholar at the American Enterprise Institute, J.D. from Yale University, 2014 (“The Legality of the National Security Agency’s Bulk Data Surveillance Programs,” Harv. JL & Pub. Pol'y 37 (2014): 901, Available Online to Subscribing Institutions via HeinOnline) The need for executive authority over electronic intelligence gathering becomes apparent when we consider the facts of the war against al Qaeda. In the hours and days after 9/11, members of the government thought that al Qaeda would try to crash other airliners or use a weapon of mass destruction in a major East Coast city, probably Washington, D.C. Combat air patrols began flying above New York and Washington. Suppose a plane was hijacked and would not respond to air traffic controllers. In order to protect the nation from attack, it would be reasonable for U.S. anti-terrorism personnel to intercept any radio or cell phone calls to or from the airliner, in order to discover the hijackers’ intentions, what was happening on the plane, and ultimately whether it would be necessary for the fighters to shoot down the plane. Or suppose the government had to put up a net to intercept all cellular phone calls in a city because it was searching for a terrorist cell which had yet to launch an attack. Under such circumstances, FISA should not control whether the President has the executive authority to monitor any radio or cell phone calls to or from the airliner; after all, the purpose is not to arrest and gather evidence for trial, but to prevent the nation from attack. Indeed, because the United States is in a state of war, the military can intercept the communications of the plane to see if it poses a threat, and target the enemy if necessary. This authority is not only within the President’s executive powers, but it also comports with the principle of reasonableness that guides the Fourth Amendment. 2NC/1NR – Impact Presidential Powers High The president’s power is higher than ever. Obama has become a “matchless war-powers unilateralist” – Syria, military force against ISIS, and unilateral decisions for intervention proves. Goldsmith 14 – Jack, professor at Harvard Law School and a member of the Hoover Institution Task Force on National Security and Law, served as Assistant Attorney General in the Office of Legal Counsel, from 2003-2004, in the George W. Bush Administration, 2014 (“Obama’s Breathtaking Expansion of a President’s Power To Make War,” Time, Sept. 11, Available Online at http://time.com/author/jack-goldsmith/) President Obama hoped to repeal the Bush-era authorization declaring war on al Qaeda— instead he's expanded it without bound Future historians will ask why George W. Bush sought and received express congressional authorization for his wars (against al Qaeda and Iraq) and his successor did not. They will puzzle over how Barack Obama the prudent war-powers constitutionalist transformed into a matchless war-powers unilateralist. And they will wonder why he claimed to “welcome congressional support” for his new military initiative against the Islamic State but did not insist on it in order to ensure clear political and legal legitimacy for the tough battle that promised to consume his last two years in office and define his presidency. “History has shown us time and again . . . that military action is most successful when it is authorized and supported by the Legislative branch,” candidate Barack Obama told the Boston Globe in 2007. “It is always preferable to have the informed consent of Congress prior to any military action.” President Obama has discarded these precepts. His announcement that he will expand the use of military force against the Islamic State without the need for new congressional consent marks his latest adventure in unilateralism and cements an astonishing legacy of expanding presidential war powers. The legacy began in 2011 with the seven-month air war in Libya. President Obama relied only on his Commander in Chief powers when he ordered U.S. forces to join NATO allies in thousands of air strikes that killed thousands of people and effected regime change. His lawyers argued beyond precedent that the large-scale air attacks did not amount to “War” that required congressional approval. They also blew a large hole in the War Powers Resolution based on the unconvincing claim that the Libya strikes were not “hostilities” that would have required compliance with the law. Although he backed down from his threat to invade Syria last summer, President Obama proclaimed then the power to use unilateral force for purely humanitarian ends without congressional or United Nations or NATO support. This novel theory, which removed all practical limits on presidential humanitarian intervention, became a reality in last month’s military strikes to protect civilians trapped on Mount Sinjar and in the town of Amirli. Yesterday’s announcement of a ramped-up war against the Islamic State in Iraq and possibly Syria rests on yet another novel war powers theory. The administration has said since August that air strikes in Syria were justified under his constitutional power alone. But yesterday it switched course and maintained that Congress had authorized the 2014 campaign against the Islamic State in the 2001 law that President George W. Bush sought to fight the Taliban and al Qaeda. Executive power is strong now – Syria situation proves. Posner 13 – Eric, a professor at the University of Chicago Law School, 2013 (“Obama Is Only Making His War Powers Mightier,” September 3, Available Online at http://www.slate.com/articles/news_and_politics/view_from_chicago/2013/09/obama_going _to_congress_on_syria_he_s_actually_strengthening_the_war_powers.html) President Obama’s surprise announcement that he will ask Congress for approval of a military attack on Syria is being hailed as a vindication of the rule of law and a revival of the central role of Congress in war-making, even by critics. But all of this is wrong. Far from breaking new legal ground, President Obama has reaffirmed the primacy of the executive in matters of war and peace. The war powers of the presidency remain as mighty as ever. It would have been different if the president had announced that only Congress can authorize the use of military force, as dictated by the Constitution, which gives Congress alone the power to declare war. That would have been worthy of notice, a reversal of the ascendance of executive power over Congress. But the president said no such thing. He said: “I believe I have the authority to carry out this military action without specific congressional authorization.” Secretary of State John Kerry confirmed that the president “has the right to do that”—launch a military strike—“no matter what Congress does.” Thus, the president believes that the law gives him the option to seek a congressional yes or to act on his own. He does not believe that he is bound to do the first. He has merely stated the law as countless other presidents and their lawyers have described it before him. The president’s announcement should be understood as a political move, not a legal one. His motive is both self-serving and easy to understand, and it has been all but acknowledged by the administration. If Congress now approves the war, it must share blame with the president if what happens next in Syria goes badly. If Congress rejects the war, it must share blame with the president if Bashar al-Assad gases more Syrian children. The big problem for Obama arises if Congress says no and he decides he must go ahead anyway, and then the war goes badly. He won’t have broken the law as he understands it, but he will look bad. He would be the first president ever to ask Congress for the power to make war and then to go to war after Congress said no. (In the past, presidents who expected dissent did not ask Congress for permission.) People who celebrate the president for humbly begging Congress for approval also apparently don’t realize that his understanding of the law—that it gives him the option to go to Congress— maximizes executive power vis-à-vis Congress. If the president were required to act alone, without Congress, then he would have to take the blame for failing to use force when he should and using force when he shouldn’t. If he were required to obtain congressional authorization, then Congress would be able to block him. But if he can have it either way, he can force Congress to share responsibility when he wants to and avoid it when he knows that it will stand in his way. Laundry List Executive flexibility is crucial to preserving peace, stopping nuclear proliferation, preventing terrorism, and de-escalating regional hotspots. Blomquist 10 – Robert F., Professor of Law, Valparaiso University School of Law. J.D., Cornell Law School; B.S., University of Pennsylvania, 2010 (“The Jurisprudence Of American National Security Presiprudence,” Valparaiso University Law Review (44 Val. U. L. Rev. 881) Available Online to Subscribing Institutions via Lexis-Nexis) A. Strategic Considerations of Institutional Design Coupled with Form and Function Supreme Court Justices—along with legal advocates—need to conceptualize and prioritize big theoretical matters of institutional design and form and function in the American national security tripartite constitutional system. By way of an excellent introduction to these vital issues of legal theory, the Justices should pull down from the library shelf of the sumptuous Supreme Court Library in Washington, D.C. (or more likely have a clerk do this chore) the old chestnut, The Legal Process: Basic Problems in the Making and Application of Law by the late Harvard University law professors Henry M. Hart and Albert M. Sacks.7 Among the rich insights on institutional design coupled with form and function in the American legal system that are germane to the Court’s interpretation of national security law-making and decision-making by the President are several pertinent points. First, “Hart and Sacks’ intellectual starting point was the interconnectedness of human beings, and the usefulness of law in helping us coexist peacefully together.”8 By implication, therefore, the Court should be mindful of the unique constitutional role played by the POTUS in preserving peace and should prevent imprudent judicial actions that would undermine American national security. Second, Hart and Sacks, continuing their broad insights of social theory, noted that legal communities establish “institutionalized[] procedures for the settlement of questions of group concern”9 and regularize “different procedures and personnel of different qualifications . . . appropriate for deciding different kinds of questions”10 because “every modern society differentiates among social questions, accepting one mode of decision for one kind and other modes for others—e.g., courts for ‘judicial’ decisions and legislatures for ‘legislative’ decisions”11 and, extending their conceptualization, an executive for “executive” decisions.12 Third, Professors Hart and Sacks made seminal theoretical distinctions between rules, standards, principles, and policies.13 While all four are part of “legal arrangements in an organized society,”14 and all four of these arrangements are potentially relevant in judicial review of presidential national security decisions, principles and policies15 are of special concern because of the sprawling, inchoate, and rapidly changing nature of national security threats and the imperative of hyper-energy in the Executive branch in responding to these threats.16 The Justices should also consult Professor Robert S. Summers’s masterful elaboration and amplification of the Hart and Sacks project on enhancing a flourishing legal system: the 2006 opus, Form and Function in a Legal System: A General Study. 17 The most important points that Summers makes that are relevant to judicial review of American national security presiprudence are three key considerations. First, a “conception of the overall form of the whole of a functional [legal] unit is needed to serve the founding purpose of defining, specifying, and organizing the makeup of such a unit so that it can be brought into being and can fulfill its own distinctive role”18 in synergy with other legal units to serve overarching sovereign purposes for a polity. The American constitutional system of national security law and policy should be appreciated for its genius in making the POTUS the national security sentinel with vast, but not unlimited, powers to protect the Nation from hostile, potentially catastrophic, threats. Second, “a conception of the overall form of the whole is needed for the purpose of organizing the internal unity of relations between various formal features of a functional [legal] unit and between each formal feature and the complementary components of the whole unit.”19 Thus, Supreme Court Justices should have a thick understanding of the form of national security decisionmaking conceived by the Founders to center in the POTUS; the ways the POTUS and Congress historically organized the processing of national security through institutions like the National Security Council and the House and Senate intelligence committees; and the ways the POTUS has structured national security process through such specific legal forms as Presidential Directives, National Security Decision Directives, National Security Presidential Decision Directives, Presidential Decision Directives, and National Security Policy Directives in classified, secret documents along with typically public Executive Orders.20 Third, according to Summers, “a conception of the overall form of the whole functional [legal] unit is needed to organize further the mode of operation and the instrumental capacity of the [legal] unit.”21 So, the Supreme Court should be aware that tinkering with national security decisions of the POTUS— unless clearly necessary to counterbalance an indubitable violation of the text of the Constitution—may lead to unforeseen negative second-order consequences in the ability of the POTUS (with or without the help of Congress) to preserve, protect, and defend the Nation.22 B. Geopolitical Strategic Considerations Bearing on Judicial Interpretation Before the United States Supreme Court Justices form an opinion on the legality of national security decisions by the POTUS, they should immerse themselves in judicially-noticeable facts concerning what national security expert, Bruce Berkowitz, in the subtitle of his recent book, calls the “challengers, competitors, and threats to America’s future.”23 Not that the Justices need to become experts in national security affairs,24 but every Supreme Court Justice should be aware of the following five basic national security facts and conceptions before sitting in judgment on presiprudential national security determinations. (1) “National security policy . . . is harder today because the issues that are involved are more numerous and varied. The problem of the day can change at a moment’s notice.”25 While “[y]esterday, it might have been proliferation; today, terrorism; tomorrow, hostile regional powers”26, the twenty-first century reality is that “[t]hreats are also more likely to be intertwined—proliferators use the same networks as narcotraffickers, narco-traffickers support terrorists, and terrorists align themselves with regional powers.”27 (2) “Yet, as worrisome as these immediate concerns may be, the long-term challenges are even harder to deal with, and the stakes are higher. Whereas the main Cold War threat—the Soviet Union—was brittle, most of the potential adversaries and challengers America now faces are resilient.”28 (3) “The most important task for U.S. national security today is simply to retain the strategic advantage. This term, from the world of military doctrine, refers to the overall ability of a nation to control, or at least influence, the course of events.”29 Importantly, “[w]hen you hold As further serious preparation for engaging in the jurisprudence of American national security presiprudence in hotly contested cases and controversies that may end up on their docket, our Supreme Court Justices should understand that, as Walter Russell Mead pointed out in an important essay a few years ago,35 the average American can be understood as a Jacksonian pragmatist on national security issues.36 “Americans are determined to keep the world at a distance, while not isolating ourselves from it completely. If we need to take action abroad, we want to do it on our terms.”37 Thus, recent social science survey data paints “a picture of a country whose practical people take a practical approach to knowledge about national security. Americans do not bother with the details most of the time because, for most Americans, the details do not matter most the time.”38 Indeed, since the American people “do know the outlines of the big picture and what we need to worry about [in national security affairs] so we know when we need to pay greater attention and what is at stake. This is the kind of knowledge suited to a Jacksonian.”39 Turning to how the Supreme Court should view and interpret American presidential measures to oversee national security law and policy, our Justices should consider a number of important points. First, given the robust text, tradition, intellectual history, and evolution of the institution of the POTUS as the American national security sentinel,40 and the unprecedented dangers to the United States national security after 9/11,41 national security presiprudence should be accorded wide latitude by the Court in the adjustment (and tradeoffs) of trading liberty and security.42 Second, Justices should be aware that different presidents institute changes in national security presiprudence given their unique perspective and knowledge of threats to the Nation.43 Third, Justices should be restrained in secondguessing the POTUS and his subordinate national security experts concerning both the existence and duration of national security emergencies and necessary measures to rectify them. “During emergencies, the institutional advantages of the executive are enhanced”;44 moreover, “[b]ecause of the importance of secrecy, speed, and flexibility, courts, which are slow, open, and rigid, have less to contribute to the formulation of national policy than they do during normal times.”45 Fourth, Supreme Court Justices, of course, should not give the POTUS a blank check—even during times of claimed national emergency; but, how much deference to be accorded by the Court is “always a hard question” and should be a function of “the scale and type of the emergency.”46 Fifth, the Court should be extraordinarily deferential to the POTUS and his executive subordinates regarding questions of executive determinations of the international laws of war and military tactics. As cogently explained by Professors Eric Posner and Adrian Vermeule,47 “the United States should comply with the laws of war in its battle against Al Qaeda”—and I would argue, other lawless terrorist groups like the Taliban—“only to the extent these laws are beneficial to the United States, taking into account the likely response of other states and of al Qaeda and other terrorist organizations,”48 as determined by the POTUS and his national security executive subordinates. Breaking deference destroys foreign military ops – causes diplomatic failure and intelligence breakdown/Judicial adjudication fails – decentralization, lack of expertise, and protracted decision-making. Murray 09 Kristian Murray, Judge Advocate, U.S. Army, Chief, Admin. Law, U.S. Army Central Command, Operational Command Post, Kuwait, JD from Gonzaga Law School, Spring 2009, (“NATIONAL SECURITY VEILED IN SECRECY: AN ANALYSIS OF THE STATE SECRETS PRIVILEGE IN NATIONAL SECURITY AGENCY WIRETAPPING LITIGATION”, https://www.jagcnet.army.mil/DOCLIBS/MILITARYLAWREVIEW.NSF/0/132c6b43e1e6335d 852575900049e74f/$FILE/Article%201%20%20By%20MAJ%20Kristian%20W.%20Murray.pdf) - AW 2. National Security Matters Should Be Handled by the Executive The Judiciary is not better equipped than the Executive or Congress to handle foreign policy or national security matters. The Judiciary is decentralized, has a time-consuming adjudication process, and lacks expertise in the areas of foreign policy and national security.220 Conversely, the Executive acts with a unified voice in security-related matters, has a relatively quick decision and implementation process, and possesses the requisite knowledge and expertise in national security issues. Most importantly, the Executive has a constitutional responsibility to protect the United States.221 There are ninety-four district courts, nine circuit courts, and one Supreme Court.222 Until appellate courts have adjudicated a matter, each of the district courts can have a differing opinion on a legal issue. This system works well for criminal or civil matters litigated in the respective district courts, as the courts are able to adjudicate matters relatively quickly within their jurisdictions without having to report to a higher authority. However, this decentralized system would be ineffective in adjudicating national security cases involving the invocation of the state secrets privilege. Commentators have argued that our nation’s forefathers framed the Constitution specifically to ensure that our government speaks with one voice in the context of foreign relations.223 Indeed, the district court’s ruling in ACLU v. NSA, enjoining the NSA from conducting further terrorist electronic surveillance, aptly demonstrates the danger of allowing courts to adjudicate foreign policy matters.224 If the state secrets privilege were eliminated, cases involving legitimate government security programs such as the terrorist surveillance program could be subject to lengthy and arbitrary litigation in multiple district courts. Without the privilege, it would be very difficult for our intelligence community to engage in secret operations. This would have profound national security ramifications as government intelligence could be subject to judicial activism. However, assume for the sake of argument that the Executive is running a secret program that is blatantly unconstitutional and is in violation of applicable statutes, but is important to national security. Assume also that the program originates from this country with support of private corporations, but also receives technical support from other countries such as Pakistan and India. Further, the program receives unofficial support from operatives in Iran and Saudi Arabia who secretly route information originating from those countries to the American government. If this program were to be fully exposed in a judicial forum it likely would cause major diplomatic issues, damage national security through the exposure of methods, means, and sources, and jeopardize foreign country operatives. It would also risk the possibility of private industries failing to cooperate with the government in future operations to thwart national security threats. Under these circumstances, it seems reasonable that a court would uphold the Government’s assertion of the state secrets privilege. They Say: “Surveillance Isn’t a War Power” The executive still has constitutional authority over surveillance – Vesting Clause of Article II proves. Lawson 08 – Gary, Professor, Boston University School of Law, 2008 (“WHAT LURKS BENEATH: NSA SURVEILLANCE AND EXECUTIVE POWER,” Symposium: The Role of the President in the Twenty-First Century (88 B.U. L. Rev. 375) Available Online to Subscribing Institutions via HeinOnline) My basic contention is that the President's constitutional power4 stems entirely from two provisions in the Constitution: the provision in Article 1, Section 7 which gives the President the presentment and veto power 5 and the first sentence of Article II, Section 1 which states that "[t]he executive Power shall be vested in a President of the United States of America."' 6 The second half of this statement is the eye of the storm. No one doubts that the Presentment Clause is a grant of power to the President, but the idea that the President draws power from the "Vesting Clause" of Article II rather than from the specific enumerations of presidential functions in Sections 2 and 3 of Article II - an idea that will henceforth be called "the Article II Vesting Clause thesis' 7 - is one of the most hotly debated propositions in modem constitutional law.8 The debate turns out to be remarkably one-sided upon careful consideration: the Vesting Clause grants power to the President beyond a reasonable doubt. To be sure, there are plenty of reasonable doubts about the scope and character of the power granted to the President by the Article II Vesting Clause, but the proposition that the Constitution itself grants something called "[t]he executive Power"9 to the President is a slam dunk as a matter of textual, linguistic, intratextual, and structural analysis. Once the Article II Vesting Clause is seen as a grant of power, the proper framework for evaluating the legality of presidentially-ordered surveillance of foreign communications becomes clear. Without the Article II Vesting Clause thesis, the case for the legality of the current surveillance program is dicey at best. With the Article II Vesting Clause thesis, the case for the legality of the program, while not unanswerable, is very strong, at least as a matter of original constitutional meaning.' 0 Accordingly, the Article II Vesting Clause thesis should be front and center in any discussion of the National Security Agency ("NSA") surveillance controversy for which the original meaning of the Constitution is deemed relevant. The President’s War Powers authorize covert surveillance — history abounds with examples. Yoo 14 — John Yoo, UC Berkeley Law Professor, former Deputy Assistant U.S. Attorney General in the Office of Legal Counsel at the Department of Justice under President GW Bush, 2014 (“Surveillance and executive power,” Constitution Daily, October 3rd, Available Online at http://blog.constitutioncenter.org/2014/10/surveillance-and-executive-power/, Accessed 0607-2015) As Commander-in-Chief, the President has the constitutional power and the responsibility to wage war in response to a direct attack against the United States. In the Civil War, President Lincoln undertook several actions—raised an army, withdrew money from the treasury, launched a blockade—on his own authority in response to the Confederate attack on Fort Sumter, moves that Congress and the Supreme Court later approved. During World War II, the Supreme Court similarly recognized that once war began, the President’s authority as Commander-in-Chief and Chief Executive gave him the tools necessary to effectively wage war. In the wake of the September 11 attacks, Congress agreed that “the President has authority under the Constitution to take action to deter and prevent acts of international terrorism against the United States,” which recognizes the President’s authority to use force to respond to al Qaeda, and any powers necessary and proper to that end. Even legal scholars who argue against this historical practice concede that once the United States has been attacked, the President can respond immediately with force. The ability to collect intelligence is intrinsic to the use of military force. It is inconceivable that the Constitution would vest in the President the powers of Commander-inChief and Chief Executive, give him the responsibility to protect the nation from attack, but then disable him from gathering intelligence to use the military most effectively to defeat the enemy. Every evidence of the Framers’ understanding of the Constitution is that the government would have every ability to meet a foreign danger. As James Madison wrote in The Federalist, “security against foreign danger is one of the primitive objects of civil society.” Therefore, the “powers requisite for attaining it must be effectually confided to the federal councils.” After World War II, the Supreme Court declared, “this grant of war power includes all that is necessary and proper for carrying these powers into execution.” Covert operations and electronic surveillance are clearly part of this authority. During the writing of the Constitution, some Framers believed that the President alone should manage intelligence because only he could keep secrets. Several Supreme Court cases have recognized that the President’s role as Commander-in-Chief and the sole organ of the nation in its foreign relations must include the power to collect intelligence. These authorities agree that intelligence rests with the President because its structure allows it to act with unity, secrecy, and speed. Presidents have long ordered electronic surveillance without any judicial or congressional participation. More than a year before the Pearl Harbor attacks, but with war clearly looming with the Axis powers, President Franklin Roosevelt authorized the FBI to intercept any communications, whether wholly inside the country or international, of persons “suspected of subversive activities against the Government of the United States, including suspected spies.” FDR was concerned that “fifth columns” could wreak havoc with the war effort. “It is too late to do anything about it after sabotage, assassinations and ‘fifth column’ activities are completed,” FDR wrote in his order. FDR ordered the surveillance even though a federal law at the time prohibited electronic surveillance without a warrant. Presidents continued to monitor the communications of national security threats on their own authority, even in peacetime. If Presidents in times of peace could order surveillance of spies and terrorists, executive authority is only the greater now, as hostilities continue against al Qaeda. Even if they’re right, presidential precedent treats NSA surveillance as an Article II war power. Levy 6 — Robert Levy, senior fellow in constitutional studies and chairman of the Board of Directors at the Cato Institute, director of the Institute for Justice, the Foundation for Government Accountability, J.D. and Ph.D. in business, former professor of law at Georgetown, 2006 (“Wartime Executive Power: Are Warrantless Wiretaps Legal?,” The Freeman, a publication of the Foundation for Economic Education, drawn from his testimony before the Senate Judiciary Committee, August 1st, Available Online at http://fee.org/freeman/detail/wartime-executive-power-are-warrantless-wiretaps-legal/, Accessed 05-29-2015) President Bush has authorized the National Security Agency (NSA) to eavesdrop, without obtaining a warrant, on telephone calls, e-mails, and other communications between U.S. persons in the United States and persons outside the United States. For understandable reasons, the operational details of the NSA program are secret, as are the details of the executive order that authorized the program. But Attorney General Alberto Gonzales has stated that surveillance can be triggered if an executive-branch official has reasonable grounds to believe that a communication involves a person “affiliated with al-Qaeda or part of an organization or group that is supportive of al-Qaeda.” The attorney general has declared that the President’s authority rests on the post-9/11 Authorization for Use of Military Force (AUMF) and the president’s inherent wartime powers under Article II of the U.S. Constitution, which includes authority to gather “signals intelligence” on the enemy. My conclusions, as elaborated below, are: First, the president has some latitude under the “Executive Power” and “Commander-in-Chief” Clauses of Article II, even lacking explicit congressional approval, to authorize NSA warrantless surveillance without violating Fourth Amendment protections against “unreasonable” searches. But second, if Congress has expressly prohibited such surveillance (as it has under FISA, the Foreign Intelligence Surveillance Act), then the statute binds the president unless there are grounds to conclude that the statute does not apply. Third, in the case at hand, there are no grounds for such a conclusion—that is, neither the AUMF nor the president’s inherent powers trump the express prohibition in the FISA statute. 2NC/1NR – AT: Impact Turns Security Outweighs Critics of executive power fail to recognize the security benefits of an unrestrained executive branch. Posner and Vermeule 07 – Eric A., Kirkland and Ellis Distinguished Service Professor of Law and Arthur and Esther Kane Research Chair at the University of Chicago; Adrian, John H. Watson Professor of Law at Harvard University and previously Bernard D. Meltzer Professor of Law at the University of Chicago, 2007 (Terror In The Balance Security, Liberty, And The Courts, Published by Oxford University Press, ISBN 0-19-531025, p. 55-56) Third, the critics of executive power in emergencies are usually unclear about their normative premises. Suppose that executive power increases during emergencies and that this results in abuses. In terms of the tradeoff thesis, however, such abuses are just a cost to be measured against the benefits of increased security, given the finding, reported above, that a constrained executive is associated with higher levels of terrorism.80 If the gains on the security margin exceed the costs, then the expansion of executive power improves social welfare overall, and no special opprobrium should attach to the executive’s behavior, although it would be nice to also prevent the abuses if possible. The critics treat executive abuses of civil liberties as something to be minimized, down to zero. But this is quixotic, and even if it were feasible, it would not be desirable. Some rate of abuse is inevitable once an executive branch is created, and an increase in abuses is inevitable when executive discretion expands during emergencies, but both shifts may be worth it; the critics fail to account for the gains side of the ledger.81 Granting the executive extensive powers during emergencies has many benefits, about which the critics are often silent. They Say: “Bad for CMR” The impact is non unique. Breaking deference is not the crucial internal link to CMR. Wittkopt and McCormick 04 – Eugene, Professor emeritus of Political Science at Louisiana State; James, Professor and Chair, Department of Political Science, Iowa State University, 2004 (The Domestic Sources of American Foreign Policy: Insights and Evidence, Rowan and Littlefield Publishers, ISBN: 0742525627, pg. 87 – 88) Concerns about a troublesome divide between the armed forces and the society they serve are hardly new and in fact go back to the beginning of the Republic. Writing in the 1950s, Samuel Huntington argued that the divide could best be bridged by civilian society tolerating, if not embracing, the conservative values that animate military culture. Huntington also suggested that politicians allow the armed forces a substantial degree of cultural autonomy. Countering this argument, the sociologist Morris Janowitz argued that in a democracy, military culture necessarily adapts to changes in civilian society, adjusting to the needs and dictates of its civilian masters.2 The end of the Cold War and the extraordinary changes in American foreign and defense policy that resulted have revived the debate. The contemporary heirs of Janowitz see the all volunteer military as drifting too far away from the norms of American society, thereby posing problems for civilian control. They make tour principal assertions. First, the military has grown out of step ideologically with the public, showing itself to be inordinately right-wing politically, and much more religious (and fundamentalist) than America as a whole, having a strong and almost exclusive identification with the Republican Party. Second, the military has become increasingly alienated from, disgusted with, and sometimes even explicitly hostile to, civilian culture. Third, the armed forces have resisted change, particularly the integration of women and homosexuals into their ranks, and have generally proved reluctant to carry out constabulary missions. Fourth, civilian control and military effectiveness will both suffer as the military—seeking ways to operate without effective civilian oversight and alienated from the society around it—loses the respect and support of that society. The impact is non unique and CMR is bad. (how do I tag?) Metz 15 – Steven, journalist for the World Politics Review, 2015 (“U.S. Civil-Military Relations’ Neglected Component: Congress,” World Politics Review, Feb. 13th, http://www.worldpoliticsreview.com/articles/15077/u-s-civil-military-relations-neglectedcomponent-congress) Yet as Mackubin Thomas Owens points out, “Those who neglect the congressional role in American civilmilitary relations are missing an important element.” In many ways, this is a more complicated relationship, since it lacks the clear chain of command that defines the military’s dealings with the executive. It is particularly difficult during times of shrinking defense budgets and intense partisanship. Both of these conditions exist today, creating potentially dangerous political shoals that Congress and the military are struggling to navigate. Shrinking defense budgets intensify competition among the military services and can tempt military leaders to seek congressional help to preserve their share of the money and save the programs they favor. But declining defense dollars can also exacerbate differences between the military and Congress over how to allocate the budget. In a time of austerity, the military emphasizes what it considers to be most important for it to perform its missions. Members of Congress are naturally concerned with the impact that the decisions of the services will have in their districts. These perspectives can clash. At times, in order to save jobs in members’ districts, Congress insists on funding equipment and programs that the military would rather do without . Today, for instance, the Army doesn’t want more main battle tanks, but Congress, with the encouragement of powerful defense industries, insists on keeping the tank production line open. Congress has forced the Navy to hold on to ships it wanted to retire and the Air Force to do the same with some aircraft. The military favors another round of base closures, but Congress, sensitive to the job losses this would cause, opposes the idea. At the same time, the intensely partisan climate in Washington has turned up the heat on the uneasy relationship between U.S. President Barack Obama’s administration and the military. Afghanistan was the first salvo. But what pulled Congress into the fray has been America’s conflict with the so-called Islamic State (IS). Reports have swirled that many of the military’s top leaders are unhappy with the Obama administration’s handling of the situation, particularly its resistance to the use of American ground forces. As Seth Cropsy wrote in The Wall Street Journal, “The political landscape is cleared for a contest between the president’s pledge not to use combat troops and the military’s professional opinion that defeating the enemy requires the use of well-trained and -equipped and disciplined forces on the ground.” Obama’s opponents in Congress have used this to undercut the administration. Since the military’s serving senior leaders will not openly dissent from the president’s position even in congressional testimony, Republicans have brought in well-known retired officers who can be more vocal in their opposition. A few weeks ago, Congress heard testimony from retired Marine Gen. James Mattis, who was also the former commander of the U.S. Central Command; retired Navy Adm. William Fallon, who held the same job; and retired Army Gen. John Keane, a former Army vice chief of staff who helped convince then-President George W. Bush’s administration to surge U.S. forces into Iraq in 2007. All three told Congress that the absence of a clear policy from the White House made success in Iraq and Syria unlikely. The intended message from Senate Republicans was that these retired flag officers reflected what the rest of the military thought but could not say. The most serious instance of Congress trying to drive a partisan wedge between the military and the administration came when GOP Rep. Doug Lamborn told an audience: “A lot of us are talking to the generals behind the scenes, saying, ‘Hey, if you disagree with the policy that the White House has given you, let’s have a resignation.’” Luckily, none of the military’s senior leaders heeded Lamborn’s advice, but the fact that he would suggest this openly shows how caustic today’s political climate is. As Owens noted, problems in civil-military relations seldom pit civilians against the military, but most often happen when elements of the military become part of a conflict between different factions of the civilian leadership. That is what is happening today, as the military is caught in the middle of an intense struggle between the Obama administration and its congressional opponents. The best solution would be a de-escalation of the partisan struggle and the revival of a working partnership on national security. But since that is not going to happen , at least not during the Obama administration, Congress should resist the temptation to use the military to oppose the administration’s policies no matter how much it disagrees with them. If there are members of Congress encouraging senior military leaders to openly revolt against the administration, they have crossed a red line. Responsible congressional leaders should stop their less responsible colleagues. Congress also should stop forcing the military to buy things it doesn’t want and maintain bases it doesn’t need. Members of Congress should be deeply committed to the well-being of their districts, but there are times when the national interest must take precedence. This is the only way to avoid the shoals in the congressional component of American civil-military relations. QDR non uniques the impact. Schake 14 – Kori, Ph.D., fellow at Stanford University’s Hoover Institution, 2014 (“THIS QDR IS A BUDGET DOCUMENT, NOT A STRATEGY DOCUMENT,” War on the Rocks, platform for analysis, commentary, debate and multimedia content on foreign policy and national security issues through a realist lens, Available Online at http://warontherocks.com/2014/03/this-qdr-is-a-budget-document-not-a-strategydocument/) Secretary Hagel claims that the fiscal year (FY) 2015 defense budget “matches our strategy to our resources…Our updated defense strategy,” that is. Updated because the Chairman of the Joint Chiefs of Staff memorably said the defense strategy could not be executed if a single dollar was cut from the budget, right before Congress cut about $50 billion of them. The only update in this Quadrennial Defense Review from earlier strategic guidance looks to consist of narrowing the force-sizing demand to defeat a regional adversary while “imposing unacceptable costs” on another. Otherwise it’s all the usual about the world becoming more volatile, global connectedness, building partner capacity, rebalancing to Asia without diminishing effort anywhere else, the need for “exceptional agility” in our forces and efficiencies in the defense effort. There’s lots of talk about innovation, but little evidence of it—the QDR details forces that would be cut if sequestration goes into effect, but does not explore different ways of achieving our defense objectives. Even this updated strategy is, by Hagel’s own admission, unexecutable without $115 billion more than the top line legislated in 2010 (separate from the $26 billion “Opportunity, Growth, and Security Initiative” submitted as a wish list along with the budget itself). That completely negates the $113 billion in cuts that the President’s budget “imposes.” So, they’re actually cutting nothing. The Defense Department has had three budget cycles to bring its spending into line with the law, and—even with an $80 billion annual slush fund of war operations—it has not complied. Hagel says “it would have been irresponsible not to request these additional resources.” That twists the argument: it was irresponsible not to develop a strategy consistent with available resources. This QDR has failed in its fundamental purpose. Perhaps the central issue this QDR should have addressed in detail is where to accept risk as resources become less plentiful: in what areas can we afford to reduce our margin of error, and where would unacceptable dangers be incurred? What missions ought we to stop doing and stop preparing for in order to ensure we are able to meet our highest priorities? Where do redundancies exist that can be eliminated to free up resources? The Department of Defense claimed that the QDR would initiate a serious debate about risk. While the press statements emphasize greater risk in carrying out the strategy, there’s no actual discussion in the QDR about how risk is assessed. The QDR does say we “continue to experience gaps in training and maintenance over the near term and will have a reduced margin of error in dealing with risks of uncertainty,” but does not explain how different choices might aggravate or mitigate those risks. If DOD actually wants a debate about where to accept risk—instead of simply brandishing it as a threat to budget hawks—it will need to establish a metric for evaluating risk. Secretary Hagel claims that the QDR prioritizes America’s highest security interests by focusing on three strategic pillars: defending the homeland against all threats; building security globally by projecting U.S. influence and deterring aggression; and remaining prepared to win decisively against any adversary should deterrence fail. It is difficult to discern how these three fundamental purposes of defense activity constitute priorities—they comprise the entirety of the defense effort. What program or activity could not be justified on their bases? The purpose of priorities is to allow apportionment of resources. And where is the politicking with Congress to gain adoption of this approach? The Hagel budget has zero probability of being adopted by either authorizers or appropriators on the Hill. By neglecting his own fundamental responsibility, which is to be the Department of Defense’s interface with the political processes of governance, Secretary Hagel has set the DOD up for another year of ineffectual bleating by the service chiefs that the end is nigh. It didn’t change a single vote in the past two years of sequestration and absent a serious effort, it won’t change a single vote this year. Where is the private horse-trading and, if need be, public shaming, to get Senator Kelly Ayotte off her hobby horse about the A-10s? Where is the flinty insistence that continuing the galloping pace of military entitlements is creating a hollow force? Where is the orchestration of presidential involvement to raise the political stakes? That ought not be the uniformed military’s job; and in any event, the Obama White House has selected service chiefs who demonstrably cannot deliver that kind of political heft. If Congress is to be cajoled into doing the right things, it needs to be confronted politicianto-politician. That Secretary Hagel sent the third echelon and a press statement to announce this tells us that the administration is going to mail it in, which will result in attaining neither the top line it seeks nor the latitude to implement its priorities. Hagel has failed in the essential work of gaining support for his strategy and his budget among the people with the constitutional responsibility for making it into law. This is not only bad politics, it is bad for civil-military relations because DOD’s civilian leadership is already busy blaming Congress rather than getting on with the business of effectively programming the world’s largest defense budget. The Obama administration is encouraging the uniformed military to attack the legislative branch for any shortfalls of funding they have no right to expect receiving. They Say: “Fear Clouds Effective Decision-making” The “panic thesis” is incorrect. The influence of fear and panic on decision-making during emergencies is no different than the influence of fear and panic on decision-making during normal times. Critics hold that the immediate nature of decision-making in times of crises guarantees miscalculation. However, the reality is that no national emergency requires an immediate reaction; the systems takes time to make complex judgments about the appropriate response. Posner and Vermeule 07 – Eric A., Kirkland and Ellis Distinguished Service Professor of Law and Arthur and Esther Kane Research Chair at the University of Chicago; Adrian, John H. Watson Professor of Law at Harvard University and previously Bernard D. Meltzer Professor of Law at the University of Chicago, 2007 (Terror In The Balance Security, Liberty, And The Courts, Published by Oxford University Press, ISBN 0-19-531025, p. 64-66) Suppose now that the simple view of fear is correct and that it is an unambiguously negative influence on government decisionmaking. Critics of the deferential view argue that the supposed negative effect of fear justifies skepticism about emergency policies and, therefore, about the deferential view. The problem with this argument is that it implicitly assumes that fear has more influence on decisionmaking during emergencies than on decisionmaking during normal times. This assumption is not plausible. The panic thesis holds that citizens and officials respond to terrorism and war in the same way that an individual in the jungle responds to a tiger or snake. The national response to an emergency, because it is a standard fear response, is characterized by the same circumvention of ordinary deliberative processes: (i) the response is instinctive rather than reasoned, and thus subject to error; and (ii) the error will be biased in the direction of overreaction. While the flight reaction might have been a good evolutionary strategy on the savannah, in a complex modern society the flight response is not suitable and can only interfere with judgment. Its advantage—speed—has minimal value for social decisionmaking. No national emergency requires an immediate reaction, except by trained professionals, such as soldiers or police officers, who execute policies established earlier. Instead over days, months, or years people make complex judgments about the appropriate institutional response. And the asymmetrical nature of fear guarantees that people will, during a national emergency, overweight the threat and underweight other things that people value, such as civil liberties. But if decisionmakers rarely act immediately, then the tiger story cannot bear the metaphoric weight that is placed on it. Indeed, the flight response has nothing to do with the political response to the bombing of Pearl Harbor or to the attacks on September 11. The people who were there—the citizens and soldiers beneath the bombs, the office workers in the World Trade Center and the Pentagon—no doubt felt fear, and most of them probably responded in the classic way. They experienced the standard physiological effects and (with the exception of trained soldiers and security officials) fled without stopping to think. It is also true that in the days and weeks after the attacks, many people felt fear, although not the sort that produces an irresistible urge to flee. But this kind of fear is not the kind in which cognition shuts down. Some people did have more severe mental reactions and, for example, shut themselves in their houses, but these reactions were rare. The fear is probably better described as a general anxiety or jumpiness, an anxiety that was probably shared by government officials as well as ordinary citizens.15 While, as we have noted, there is psychological research suggesting that normal cognition partly shuts down in response to an immediate threat, we are aware of no research suggesting that people who feel anxious about a medium-term or long-term threat are incapable of thinking, or thinking properly, or that they systematically overweight the threat relative to other values. Indeed, it would be surprising to find research that clearly distinguished “anxious thinking” and “calm thinking,” given that anxiety is a pervasive aspect of life. People are anxious about their children, about their health, about their job prospects, about their vacation arrangements, about walking home at night.16 So it is hard to see why anxiety about more remote threats, from terrorists or unfriendly countries with nuclear weapons, should cause the public or elected officials to place more emphasis on security than is justified and to sacrifice civil liberties unnecessarily. Quite the contrary, a standard view is that people ignore low-probability risks and that elected officials with short time horizons ignore remote ones; on this account, government will probably do too little to prevent terrorist threats, not too much. Fear generated by immediate threats, then, may cause instinctive responses that are not rational in the cognitive sense, not always desirable, and not a good basis for public policy, but it is not this kind of fear that leads to restrictions of civil liberties during wartime. The internment of Japanese Americans during World War II may have been due to racial animus, or to a mistaken assessment of the risks; it was not the direct result of panic. Indeed, there was a delay of weeks before the policy was seriously considered.17 The civil libertarians’ argument that fear produces bad policy trades on the ambiguity of the word panic, which refers both to real fear that undermines rationality and to collectively harmful outcomes that are driven by rational decisions, such as a bank panic, in which it is rational for all depositors to withdraw their funds if they believe that enough other depositors are withdrawing funds. Once we eliminate the false concern about fear, it becomes clear that the panic thesis is indistinguishable from the argument that during an emergency people are likely to make mistakes. But if the only concern is that during emergencies people make mistakes, there would be no reason to demand that the Constitution be enforced normally during emergencies. Political errors occur during emergencies and during normal times; once the panic thesis is rejected there is no reason to think that political errors occur at a higher rate during emergencies such that judicial scrutiny should be heightened, despite all of the disadvantages described in chapter 1. In sum, the panic thesis envisions decisionmakers acting immediately when in fact government policymaking moves slowly even during emergencies. Government is organized so that general policy decisions about responses to emergencies are made in advance, and the implementation of those policies during an emergency is trusted to security officials who have been trained to resist the impulse to panic. The notion of fear causing an irresistible urge to flee is a bad metaphor for an undeniable truth: during an emergency, the government does not have as much time for making decisions as it usually does, and as a result will make more errors than it usually does. But these errors will be driven by ordinary cognitive limitations and not the pressure of fear; thus, the errors will be normally distributed. It is as likely that the government will curtail civil liberties too little as too much. They Say: “Executive Power Will Snowball Out of Control” Claims of abuses in executive power are grounded in the naturalistic fallacy and the slippery slope fallacy. Furthermore, critics rely on outdated examples and fail to present a holistic analysis of executive power. Even if they are right about executive power abuses, the judiciary is not a better alternative; a litany of historical examples prove. Posner and Vermeule 07 – Eric A., Kirkland and Ellis Distinguished Service Professor of Law and Arthur and Esther Kane Research Chair at the University of Chicago; Adrian, John H. Watson Professor of Law at Harvard University and previously Bernard D. Meltzer Professor of Law at the University of Chicago, 2007 (Terror In The Balance Security, Liberty, And The Courts, Published by Oxford University Press, ISBN 0-19-531025, p. 56-57) Concerns about increasing executive power often rest on an implicit status quo bias, or naturalistic fallacy. The assumption is that the scope or level of executive power before the emergency was optimal. But this need not be so, and there is no general reason to think it will be so; consider the finding that the 7/7 attacks in London went unprevented because the United Kingdom’s intelligence services, who knew something about the plotters, had too few resources to investigate them adequately.82 Emergencies may release the polity from a sclerotic equilibrium in which executive power was too feeble to meet new challenges, as we illustrate in chapter 4. One interpretation of history is that emergencies allow presidents to obtain powers that are necessary to cope with new problems. Our original constitutional structure, with a relatively weak presidency, reflects the concerns of the eighteenth century and is not well adapted to current conditions. Finally, to the extent that the critics of executive power envision judicial review as the solution, they are whistling in the wind, especially during times of emergency. The critics envision an imperial executive, who is either backed by a sustained national majority or else has slipped the political leash, and who enjoys so much agency slack as to be heedless of the public’s preferences. In either case, it is not obvious what the critics suppose the judges will or can do about it. As we will recount in more detail in later chapters, the judges proved largely powerless to stem the tide of the New Deal, in conditions of economic emergency, or to stop Japanese internment during World War II, or to block aggressive punishment and harassment of communists during the Cold War. What is more, many of the judges had no desire to block these programs. Judges are people too and share in national political sentiments; they are also part of the political elite and will rally ’round the flag in times of emergency just as much as others do.83 Critics of executive power implicitly appeal to a slippery-slope argument: once executive power is increased to meet an emergency in a manner that is necessary and reasonable, it will unavoidably expand beyond what is necessary and reasonable. As we emphasize in chapters 4 and 5, the problem with this argument is that there is no evidence for it and no mechanism that generates such a slope. The critics focus obsessively on pathological polities like Weimar, ignoring that current well-functioning liberal democracies do not present the same conditions that led to dictatorship in 1933. More recent work in comparative politics suggests that grants of emergency powers or of decree authority to executives do not systematically end in dictatorship.84 Arguing that executive power would snowball out of control oversimplifies the equation of presidential power. Critics usually fail to distinguish the effects of “presidency as an institution” and “presidency as individuals.” Posner and Vermeule 07 – Eric A., Kirkland and Ellis Distinguished Service Professor of Law and Arthur and Esther Kane Research Chair at the University of Chicago; Adrian, John H. Watson Professor of Law at Harvard University and previously Bernard D. Meltzer Professor of Law at the University of Chicago, 2007 (Terror In The Balance Security, Liberty, And The Courts, Published by Oxford University Press, ISBN 0-19-531025, p. 54) First, the executive-despotism concern supposes that executive officials desire, above all, to maximize their power. As Daryl Levinson has emphasized, both for officials generally and for executive officials in particular, it is hardly obvious that this is so, at least in any systematic way.76 Lower-level executive officials and administrative agencies have many other possible goals or maximands, including the desire to enjoy leisure or to advance programmatic or ideological goals—goals which will usually be orthogonal to the tradeoff between security and liberty and which might even include the protection of civil liberties. The same is true for presidents: some have been power maximizers; some have not. Moreover, even with respect to power-maximizing presidents, critics fail to distinguish the man from the office. Presidents as individuals do not internalize all of the gains from expanding the power of the presidency as an institution, because those gains are shared with future presidents and senior executive officials.77 Conversely, presidents as individuals do not fully internalize harms to the institution and may thus acquiesce in limitations on executive power for partisan or personal advantage. The latter point may be more pronounced in emergencies than in normal times, because emergencies shorten the relevant time horizon; policymaking for the short run looms larger than in normal times. (We bracket for now the question of whether this is bad, an issue taken up in chapter 2.) Emergencies thus increase the divergence between the utility of individual officeholders and the institutional power of their offices, which extends into the remote future, beyond the horizon of the emergency. Critics also fail to account for political motivations. Politics can incentivize the executive branch to maximize its power. However, this does not mean politics will always push a president to test the boundaries. Critics conflate increases in executive power with aggrandizement. Posner and Vermeule 07 – Eric A., Kirkland and Ellis Distinguished Service Professor of Law and Arthur and Esther Kane Research Chair at the University of Chicago; Adrian, John H. Watson Professor of Law at Harvard University and previously Bernard D. Meltzer Professor of Law at the University of Chicago, 2007 (Terror In The Balance Security, Liberty, And The Courts, Published by Oxford University Press, ISBN 0-19-531025, p. 54-55) Second, whatever the intrinsic preferences of presidents and executive officials, politics sharply constrains their opportunities for aggrandizement,78 especially in times of emergency. The president is elected from a national constituency (ignoring the low probability that the Electoral College will make a difference). A first-term president who seeks reelection to a second term, or even a second-term president who seeks to leave a legacy, will try to appeal to the median voter, or at least to some politically engaged constituency that is unlikely to be extremist in either direction. If the national median or the political center favors increased executive authority during emergencies, then the president will push the bounds of his power, but if it does not, then he will not; there is no general reason to think that national politics will always push executive authority as far as possible, even during emergencies. Of course, during emergencies, the public will often favor increased executive power, and this may be fully sensible, given the executive’s relative decisiveness, secrecy, centralization, and other advantages over Congress and other institutions. Note, in this connection, the important finding that political constraints on the executive are associated with increased terrorism;79 shackling the executive has real security costs. The critics of executive power typically assume that executive power not only expands during emergencies, but expands too far. However, the critics supply no general reason to think this is so; they systematically conflate increases in executive power with “aggrandizement,” a normatively loaded concept which connotes an unjustified increase. We return to this point shortly. Here, the point is just that the expansion of presidential power during emergencies may reflect nothing more than the demands of the politically effective public, rather than intrinsic opportunism. The political constraints on the executive branch and the president are partisan as well as institutional. The president is the leader of a political party but is also beholden to it. The party constrains the president in various ways, and it is not necessarily in the interest of a single party to enhance the power of the executive during emergencies. For one thing, the president’s party may not win the next presidential election; for another, his party may have many other bases of power, including Congress, the judiciary, and local institutions. Expanding the president’s personal or institutional power need not be in the interests of partisan politicians who govern behind the scenes. Opposition parties, of course, have powerful incentives to criticize the expansion of presidential power during emergencies, portraying small adjustments to the legal rules as omens of a putsch. In emergencies, partisan criticism can make the political constraints on presidents even tighter than during normal times, a point we emphasize in chapter 5. Governmental decisionmaking is often more visible during emergencies than during normal times; emergency policymaking is more centralized, even within the executive branch, and more closely associated with the president; the resulting policies often present a larger target for political attack.