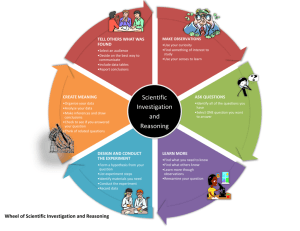
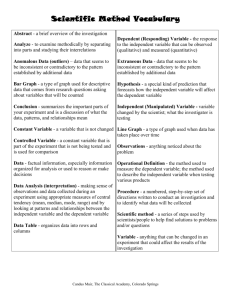
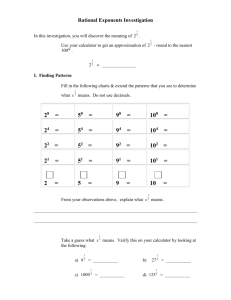
Document Management A plan for managing all aspects of the
advertisement

Document Management A plan for managing all aspects of the documentary evidence uncovered in the investigation must be developed as early as possible. This is particularly true if the suspected wrongdoing involves a complex trail of financial transactions. In most cases, establishing a document management plan will be one of the first steps in the investigation. That way the members of the investigative team will be able to decide which documents will best achieve the strategic goals of the investigation. Any document management plan should provide for the following: Document Security A key priority in document management is to preserve the integrity of all evidence. Most fraud evidence is in the form of working papers, correspondence, and original documents, such as bank statements, checks, customer records, accounting documents like inventory records and ledgers, corporate taxation returns, and computer information. Original documents should be secured as soon as they are seized and stored in locked cabinets or safes accessible only to members of the investigating team. If several keys to these cabinets or safes are in circulation, the locks must be changed. Documents are likely targets for destruction by arson or theft and, therefore, may need to be stored off-site. The documents can also be copied and inventoried, which will also aid in the identification of any documents that have not yet been obtained. The search for additional evidence will be an ongoing task, so an up-to-date inventory of all seized documents is a great help. To help maintain a high level of confidentiality, all working notes and correspondence generated by the investigating team should also be kept in a secure place. Doing everything possible to keep the investigation confidential is important because it helps to protect the reputation of the suspected person. In addition, confidentiality helps ensure that the investigation proceeds unhindered and allows counsel to develop a strategy for any anticipated legal action. Any information about the investigation that is generated or stored on a computer should also be safe-guarded. There's no point in locking physical documents in a cabinet each evening if the investigators' computers holding information about the investigation remain accessible to everyone in the office. It's a good idea to use password protection for all of the investigators' computer files related to the investigation. Using a personal computer that can be locked away each night is an even better solution. A regular back-up of all investigation files should be made and stored in a separate secure location. In addition to securing computerized information about the investigation generated by the investigators, computer evidence linking the suspect to the crime must also be safeguarded. Computer records are often crucial to the successful completion of an investigation, and the first step to securing such records is to make absolutely certain that the suspected person does not retain access to computer information. This would involve changing the passwords on all relevant files, including network files and modem facilities. Care should be taken, however, to guard against any action that might cause undue damage to the suspected individual's reputation. In most companies, regular employees will need to retain daily access to the information contained in the organization's computer system. So that the information necessary to the investigation will remain unaltered and available to the investigators, a back-up of all relevant computer systems should be made, and a duplicate copy of the back-up should be stored with the original documents. Continuity of Evidence It's always a good idea to assume that any document related to the case will be used in court. To be admissible, the document must be genuine and in the same condition it was in when seized. The site from which each document was seized should be recorded, and no marking, stapling, or hole-punching of the original documents should occur. In addition, a clear chain of custody for each document must be demonstrated. All original documents must be uniquely identified, copied, inventoried, and stored in a secure place. If an important document lies around in somebody's in-tray for several days, its authenticity may be challenged. Destruction of Obsolete Documents It might seem obvious, but all discarded or otherwise obsolete documents related to the investigation should be destroyed by shredding. They should never be simply dropped in a wastepaper basket. It can be painfully embarrassing to see the details of a confidential memo or report splashed across the front page of the local newspaper. This kind of carelessness can also lose cases, provoke lawsuits, and end careers. Document Database A simple investigation can often involve hundreds of documents. In more complex cases, investigators may be working with several thousand pieces of evidence. The key in all cases is to file each document in an organized way so that information can be readily located as needed. A manual document management system might serve the purpose in a small investigation; however, a computerized database system is usually more efficient and effective. The system should be selected based on the anticipated number of documents, the interrelationship of the various documents, and the complexity of the investigation. The benefits of any document management database should obviously be weighed against the costs, which will include database development, data input, and ongoing database maintenance. To help make a final choice, the search, retrieval and display, and database access requirements will need to be determined in advance. Another option worth considering is transferring entire documents into machine-readable form using document imaging. Setting Up the Database The first step in setting up a document database is to identify the types of documents involved, the key documents, and any generic document terms that can be used to standardize referencing. Next, a general index of the documents should be created. For smaller investigations, a flat file database, such as a spreadsheet, might be used to list all relevant documents and where they are filed. However, more complex investigations involving large numbers of transactions, funds tracing, or the identification of relationships between companies or individuals will most likely require the use of a relational database, which can create links between two or more pieces of information. The Chronological Database One useful relational database is the chronological database, which is particularly valuable at the start of an investigation when it's hard to determine which documents will be relevant. A basic chronological database will help the investigating team compile a timeline of events, people, companies, and places associated with the alleged wrongdoing. By sorting the recorded information so that the date and time of movements of funds can be identified, a sophisticated chronological database can even help investigators establish links between transactions in different locations and currencies. Final Reports The final aspect of document management is compiling everything in some type of report. Investigators must communicate their findings so that a reader or listener will understand the information and how the investigators reached each conclusion. Not every investigation calls for a formal final report, however. Sometimes an affidavit, an oral report, or a reporting letter will do the job. Regardless of the actual format, any time litigation is anticipated the report should be reviewed by legal counsel to ensure that it is appropriate for court presentation. In cases that involve the presentation of many documents at a trial, legal counsel should be consulted to help investigators prepare a document brief for the convenience of the court. This should contain unmarked copies of all the original documents that may be presented as exhibits. It's not an exhibit itself, but a document brief can save valuable time when the judge and jury need to refer to various original documents during the trial. Final Precautions Although investigation preparation and document management are essential strategies in fraud investigations, the internal auditor must be aware of other actions that can help to achieve an effective inquiry. For example, maintaining good communication among all members of the investigating team will be critical. During an investigation, no investigator ever wants to get into a situation where he or she is working in the dark. Ideally, the investigator in charge of evidence collection should participate in all meetings related to the assignment. When the president meets with the security officer or the general counsel meets with another member of the team without the investigator's knowledge, for example, problems can occur. Such communication breakdowns can sometimes cause the entire investigation to drift off strategy.