The Top 10 Internet Security Vulnerabilities
advertisement

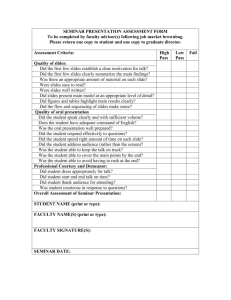
The Top 10/20 Internet Security Vulnerabilities – A Primer Randy Marchany VA Tech Computing Center Blacksburg, VA 24060 marchany@vt.edu ITTIP Seminar Copyright 2001 R.C.Marchany 1 Introduction This presentation is designed to give you a brief overview of the top 10 most critical Internet Security threats. These aren’t the only threats….just the most common at the moment. Hopefully, we’ll eliminate these threats and create a new list next year. The Top 10 and Top 20 documents are in Appendix A of this presentation. ITTIP Seminar Copyright 2001 R.C.Marchany 2 Introduction We’ll review the original Top 10 list first We’ll review the new items in the Top 20 We’ll also provide a list of common ports to filter or monitor. ITTIP Seminar Copyright 2001 R.C.Marchany 3 Why Are We Vulnerable? Computer systems and programs have become more complex in the past 25 years. Quality control hasn’t been able to keep up due to market pressures, programming skill deficiencies, etc. Most of these programs/systems are based on code that was never intended to be “production” quality.They were “proof of concept” programs that became the basis of production systems. ITTIP Seminar Copyright 2001 R.C.Marchany 4 So Many Systems, Not Enough Time….. 2.3 million hosts are connected to the Net each month. There aren’t 2.3 million sysadmins. Something has to give…. Unfortunately, it’s the sysadmin. Not enough training, too many conflicting demands on their time. The Prime Directive: Keep the system up! Patch the system? When I have time…. ITTIP Seminar Copyright 2001 R.C.Marchany 5 Hacking = Rocket Science? Not! Any good hacker can write the attack tool. The real skill is making so easy to use that a CEO could launch the attack. There are lots of hacker WWW sites where you can get these tools. These sites try to outdo each other by designing the best, baddest, userfriendly site. ITTIP Seminar Copyright 2001 R.C.Marchany 6 Why Are the Attacks Successful? We didn’t close all the doors because we’re too busy doing “real” stuff. If the hackers got caught, we didn’t punish them. It would be too embarrassing to admit we got hit. Our Incident Response Plans were inadequate. ITTIP Seminar Copyright 2001 R.C.Marchany 7 Why Are the Attacks Successful? The attack designers studied (cased) the target code carefully. A lot of attacks are based on Buffer Overflows. ITTIP Seminar Example: a program expects 80 input characters max. You give it 5000 characters. How does the code handle it? Copyright 2001 R.C.Marchany 8 Some Pointers About the Lists Each item in the list is divided into 4 parts A description of the vulnerability The systems affected by the vulnerability A CVE number identifying the vulnerability Some suggested corrections ITTIP Seminar Copyright 2001 R.C.Marchany 9 Some Pointers about the Lists What’s a CVE number? CVE = Common Vulnerabilities & Exposures reference number that is used to uniquely identify a vulnerability. It’s like the Dewey Decimal #’s that are used in the library. You can go to any library and find the same book using the same Dewey catalog number CVE’s does the same for vulnerabilities. ITTIP Seminar Copyright 2001 R.C.Marchany 10 Some More Pointers about the Lists Ports to block/monitor at the firewall are provided at the end of the Top 20 list. Remember this only works for EXTERNAL attacks. Internal attacks need additional security measures. ITTIP Seminar Copyright 2001 R.C.Marchany 11 Some More Pointers about the Lists Automated Scanning for the Top 20 SARA – freeware scanning tool designed specifically for this. See http://www.cisecurity.org Commercial scanners are becoming available. Links to ICAT Vulnerability Index Each entry is linked to the NIST ICAT indexing service. ICAT entries contain a short description of the vulnerability and other info. ITTIP Seminar Copyright 2001 R.C.Marchany 12 Item #1: BIND All Internet systems have a hostname and an IP address. Every home is known by its address and who lives in it. “hey, is that Randy’s house?” “Yeah, it’s at 24 Main St.” “Randy’s house” = hostname “24 Main St.” = IP address BIND (Berkeley Internet Domain) maps hostnames to IP addresses. It’s the set of “phone books” of the Internet. ITTIP Seminar Copyright 2001 R.C.Marchany 13 Item #1: BIND Every network needs a couple of systems that run BIND. They’re called nameservers. Old versions of BIND have security holes.The nameservers aren’t always up-to-date. They were when they were installed but that was years ago. It works so why fix it? Right? Wrong! ITTIP Seminar Copyright 2001 R.C.Marchany 14 Item #1: BIND The Danger: Hackers get full control of the nameserver and can use it for anything they want. A Solution Make sure your version is higher than BIND 8.2.2 patch level 5 ITTIP Seminar Copyright 2001 R.C.Marchany 15 Item #2: CGI Scripts CGI = Common Gateway Interface It’s the language that programmers use to display and read your input to a WWW based form. Not everyone knows how to use it so WWW server vendors supply examples. The examples have security holes in them. Some CGI programmers haven’t checked their code. ITTIP Seminar Copyright 2001 R.C.Marchany 16 The Second Item – CGI Scripts All Web servers could be affected by this “feature”. The Danger Your WWW pages could be changed a la DOJ, CIA, FBI, Valujet. Your WWW server could be used to attack other sites A Solution Remove unsafe CGI scripts from the WWW server ITTIP Seminar Copyright 2001 R.C.Marchany 17 Item #3: Remote Procedure Calls (RPC) RPC allows a computer to run a program on another computer. It’s used by computers that share files between them. Many client – server systems depend on the use of RPC calls. Unix systems (Solaris, AIX, HP-UX, Linux, Tru64, Irix) were primarily affected but any computer that uses the RPC subsystem is vulnerable ITTIP Seminar Copyright 2001 R.C.Marchany 18 Item #3: Remote Procedure Calls (RPC) The Danger: Older versions of RPC have security weaknesses that allow hackers to gain full control of your computer(s). A Solution Disable the RPC services if you don’t use them Install the latest vendor patches ITTIP Seminar Copyright 2001 R.C.Marchany 19 Item #4: Microsoft Internet Information Server (IIS) Windows NT and Windows 2000 Web servers use IIS to support web services. IIS has a component called Remote Data Services (RDS) that could allow a hacker to run remote commands with administrator privileges. Code Red, NIMDA ITTIP Seminar Copyright 2001 R.C.Marchany 20 Item #4: Microsoft Internet Information Server (IIS) The Danger: A hacker can run commands on another system without having to access it directly. A Solution: Read the Microsoft technical bulletins that describe how to fix the problem ITTIP Seminar Copyright 2001 R.C.Marchany 21 Item #5: Sendmail Weakness Sendmail is one of the original Internet email programs. It was a graduate programming project that was never designed to work in a “production” environment. It became the defacto standard. Pre-version 8.10 had security problems Some vendors still ship Sendmail v5.65! Most vendors shipped their systems with these older versions. ITTIP Seminar Copyright 2001 R.C.Marchany 22 Item #5: Sendmail Weakness The 1988 Internet Worm exploited a problem in sendmail.There are a lot of systems that still run that version of sendmail. Why? It works! The Danger: Hackers can run commands on your systems without ever logging into your system. Hackers can take over your machine. A Solution: Update to the latest version of sendmail ITTIP Seminar Copyright 2001 R.C.Marchany 23 Item #6: sadmind and mountd Sadmind is used by Solaris applications to run distributed sysadmin operations. It executes the request on the server from a client program. Sounds like RPC? It is. Mountd controls file sharing across the network using NFS. This is the program that “attaches” a remote disk to your computer. ITTIP Seminar Copyright 2001 R.C.Marchany 24 Item #6: sadmind and mountd The Danger: Hackers can cause these programs to give them access to root. They can take over your machine. This was one of the primary ways hackers used to set up the systems used in the recent DDOS attacks against Yahoo, CNN and other sites. A Solution: Install the latest vendor patches for sadmind and mountd. ITTIP Seminar Copyright 2001 R.C.Marchany 25 Item #7: Global File Sharing You can share files between computers using tools like Network Neighborhood (Windows), AppleShare(Macintosh) or NFS(Unix). By default, the access is read-write. ITTIP Seminar Copyright 2001 R.C.Marchany 26 Item #7: Global File Sharing Anyone on the same network could access your files. In the old days, the network was small but now the network is the Internet so anyone anywhere in the world could access your files if you let them. The problem is that you don’t always know that you’re letting them. ITTIP Seminar Copyright 2001 R.C.Marchany 27 Item #7: Global File Sharing This is a real danger to homes that have direct connect modems. The Danger: People can get access to your personal data, for example, your checking account data (if you use MSMoney), your email, etc. A Solution: Make sure you know what you’re sharing. Make sure you know who’s sharing the data with you. ITTIP Seminar Copyright 2001 R.C.Marchany 28 Item #8: User Accounts with No Passwords Some systems come with demo or guest accounts with no passwords or well known passwords. The initial/default password for VMS system manager account, SYSTEM was MANAGER. The initial password for the Field Service account, FIELD, was SERVICE. ITTIP Seminar Copyright 2001 R.C.Marchany 29 Item #8: User Accounts with No Passwords People forgot to change these passwords. The first thing hackers do is check to see if the defaults passwords were changed. Why waste a lot of effort if the door is unlocked? ITTIP Seminar Copyright 2001 R.C.Marchany 30 Item #8: User Accounts with No Passwords The Danger: Someone can get complete control of your system. Someone can get access to your system via a general accounts and then run exploit tools on your systems to get full control of your system. A Solution: Change your root, administrator passwords before the systems goes into production. Run a password checking program to discover who has weak passwords on your system. Do it before the hackers do! ITTIP Seminar Copyright 2001 R.C.Marchany 31 Item #9: IMAP, POP Vulnerabilities IMAP and POP are two common email protocols that provide additional features to email users. They allow users to access their email accounts from anywhere on the Internet. ITTIP Seminar Copyright 2001 R.C.Marchany 32 Item #9: IMAP, POP Vulnerabilities Firewalls usually allow email using these services to pass through the firewall. Quality control of the software is inconsistent most of the time. ITTIP Seminar Copyright 2001 R.C.Marchany 33 Item#9: IMAP, POP Vulnerabilities The Danger: Hackers can gain access to your internal network if they can subvert IMAP or POP mail server systems. If successful, they gain complete control of your system. A Solution: Make sure you’ve installed the latest patches. Run the services on your mail servers only. ITTIP Seminar Copyright 2001 R.C.Marchany 34 Item #10: SNMP Vulnerabilities Simple Network Management Protocol (SNMP) is used by network managers to monitor the status, performance and availability of the network. The Net Mgrs can remotely manage their routers, printers, systems using SNMP. ITTIP Seminar Copyright 2001 R.C.Marchany 35 Item #10: SNMP Vulnerabilities SNMP has very weak authentication. Its default “password” is “private”. Everyone knows this. ITTIP Seminar Copyright 2001 R.C.Marchany 36 Item #10: SNMP Vulnerabilities The Danger: Hackers can gain control of network devices such as routers. They could shut them down. They can map your network w/o your knowledge. A Solution: Pick strong community strings (passwords) for your SNMP devices. Make the MIBs read only. ITTIP Seminar Copyright 2001 R.C.Marchany 37 Summary Most of the successful system and network attacks exploit a small set of vulnerabilities. The Top 10 list briefly describes this set of vulnerabilities and gives you references to learning more about them. More importantly, it gives you some suggested fixes for the problem. Our individual security depends on our mutual security. ITTIP Seminar Copyright 2001 R.C.Marchany 38 The SANS/FBI Top 20 List If we had fixed the top 10, there wouldn’t be a top 20. ITTIP Seminar Copyright 2001 R.C.Marchany 39 Top 20 List Organization Vulnerabilities that affect all systems Unix/Linux Windows Mac Mainframes Windows Vulnerabilities Unix Vulnerabilities ITTIP Seminar Copyright 2001 R.C.Marchany 40 Top 20 Summary General – Affects all Systems G1: Default OS Installations G2: Accounts with Weak or No Passwords G3: Non-existent or Incomplete Backups G4: Large Number of Open Ports G5: Incorrect Ingress/Egress Packet Filtering G6: Non-existent or Incomplete Logging G7: Vulnerable CGI Programs ITTIP Seminar Copyright 2001 R.C.Marchany 41 Top 20 Summary Windows W1: Unicode Vulnerability W2: ISAPI Extension Buffer Overflows W3: IIS RDS Exploit W4: Unprotected NETBIOS Shares W5: Null Sessions W6: Weak Hashing in SAM (LM Hash) ITTIP Seminar Copyright 2001 R.C.Marchany 42 Top 20 Summary Unix U1: RPC buffer Overflows U2: Sendmail Vulnerabilities U3: BIND U4: R Commands U5: LPD Buffer Overflow U6: sadmind mountd Buffer Overflow U7: Default SNMP ITTIP Seminar Copyright 2001 R.C.Marchany 43 G1: Default OS Installations OS and application installs are not configured for security Vendor Philosophy Better to enable all functions than require the user to turn them on individually. Convenience vs. Security: Who wins? ITTIP Seminar Copyright 2001 R.C.Marchany 44 G1: Default OS Installations System Impacted All Unix, Linux, Windows, MacOS are vulnerable to some degree. Windows, SGI are more open than normal. ITTIP Seminar Copyright 2001 R.C.Marchany 45 G1: Default OS Installations Are you vulnerable? If you use default vendor installation programs then you are vulnerable. Extra extra service/tool installed that is not needed is another window into your system. ITTIP Seminar Copyright 2001 R.C.Marchany 46 G1: Default OS Installations How to protect? Remove unnecessary software/services asap. Install minimum then add. This can be automated using Minimum Installation guidelines. Use the CIS Security Benchmark tools for your OS. ITTIP Seminar Copyright 2001 R.C.Marchany 47 G3: Non-existent, Incomplete Backups Recovery from an incidents requires up-todate backup. Have you verified the backups actually work? Offsite? 9/11 proved this. How long does it take to RESTORE the data? What is the data xfer rate of your tape drives? Systems Impacted Any critical system ITTIP Seminar Copyright 2001 R.C.Marchany 48 G3: Non-existent, Incomplete Backups Am I vulnerable? Check backup procedures. Is the backup interval acceptable? Are the systems being backup up according to procedure? Off site storage? Procedures? Restoration tested and verified? ITTIP Seminar Copyright 2001 R.C.Marchany 49 G3: Non-existent, Incomplete Backups How to Protect Daily backups Monthly backups should be verified. ITTIP Seminar Copyright 2001 R.C.Marchany 50 G4: Large Number of Open Ports The more ports open, the more ways to get into the system. Related to Default OS install vulnerability. Systems Impacted Any system that used a vendor default installation program. ITTIP Seminar Copyright 2001 R.C.Marchany 51 G4: Large Number of Open Ports Am I vulnerable? Use netstat command to list open ports. Run a port scanner (nmap, Nessus) against your system. Match open ports to legitimate services provided by the machine. If no match, then it’s an unnecessary service. ITTIP Seminar Copyright 2001 R.C.Marchany 52 G4: Large Number of Open Ports How to protect myself Unix: modify /etc/inetd.conf Windows NT/2000 : use fport from www.foundstone.com to list the ports. Windows XP: netstat –o command ITTIP Seminar Copyright 2001 R.C.Marchany 53 G5: Incorrect Ingress/Egress Router Filters Description IP spoofing hides the attacker. Numerous attacks (Smurf, mail forgery) use this technique. Systems Impacted Unix, Windows, Mac, Routers ITTIP Seminar Copyright 2001 R.C.Marchany 54 G5: Incorrect Ingress/Egress Router Filters Am I vulnerable? Send a spoofed packet and see if it’s blocked and logged. ITTIP Seminar Copyright 2001 R.C.Marchany 55 G5: Incorrect Ingress/Egress Router Filters How to Protect Incoming packets must not have SRC of your internal network. It must have a DST of your internal network. Outbound packets must have a SRC of your internal network. Outbound packets must not have a DST of your internal net. No packet should have SRC/DST of a private address or address listed in RFC1918.. Block any source routed packet with IP options set ITTIP Seminar Copyright 2001 R.C.Marchany 56 G6: Non-existent, Incomplete Logging Description You can’t detect an attack if you don’t know what’s going on your network. Logs are business records! Systems Impacted All system and network devices ITTIP Seminar Copyright 2001 R.C.Marchany 57 G6: Non-existent, Incomplete Logging Am I vulnerable? Are there logs for the critical assets? How to Protect? Set up local and central logging. Save on CD or other Read-Only device. ITTIP Seminar Copyright 2001 R.C.Marchany 58 W1: Unicode – Web Server Traversal Description Unicode provides a unique number for every character regardless of the the platform, program or language. You can send IIS a carefully constructed URL with an invalid Unicode sequence that will let an attacker see any file anywhere on the system. You can run programs as well. ITTIP Seminar Copyright 2001 R.C.Marchany 59 W1: Unicode – Web Server Traversal Systems Impacted Windows NT 4.0 with IIS 4.0 Windows 2000 server with IIS 5.0 with no SP2 CVE-2000-0884 ITTIP Seminar Copyright 2001 R.C.Marchany 60 W1: Unicode – Web Server Traversal Am I vulnerable? Unpatched version of IIS? Yes! Did you install MS00-057, MS00-078, MS00-086, MS00-026, MS00-044, SP2? Yes, then ok. ITTIP Seminar Copyright 2001 R.C.Marchany 61 W1: Unicode – Web Server Traversal Enter: http://victim/scripts/..%c0%af../winnt/sys tem32/cmd.exe?/c+dir+c:\ If you removed scripts dir, then it’ll fail. Replace scripts with whatever you named your script directory. ITTIP Seminar Copyright 2001 R.C.Marchany 62 W1: Unicode – Web Server Traversal How to Protect Install latest Microsoft patches. See http://www.microsoft.com/technet/security/b ulletin/MS00-78.asp Install IIS lockdown tool if you want. Don’t use IIS for critical functions, IMHO. ITTIP Seminar Copyright 2001 R.C.Marchany 63 W2: ISAPI Extension Buffer Overflows Description Several ISAPI extensions are installed by default when you install IIS. This allows developers to extend IIS by using DLLs. Several DLLs, idq.dll, have errors that allow buffer overflow attacks. This lets an attacker take full control of your IIS server. ITTIP Seminar Copyright 2001 R.C.Marchany 64 W2: ISAPI Extension Buffer Overflows Systems Impacted Windows 2000 running Index Server 2.0, Indexing Service Windows 2000 server, Adv. Server, Server Data Center Edition, Professional ITTIP Seminar Copyright 2001 R.C.Marchany 65 W2: ISAPI Extension Buffer Overflows Am I vulnerable? SP2 installed? No, then you are. Installed MS01-023, MS01-033, MS01044, MS01-033, MS01-044, NT4.0 Security Roll-up Package? Yes, then ok. How to Fix Install latest patches from Microsoft. Unmap unnecessary ISAPI extensions ITTIP Seminar Copyright 2001 R.C.Marchany 66 W5: Null Session Connections Description Null Session (anonymous login) lets you get info over the net about shares, etc. When 1 machine needs something from another, it uses the local SYSTEM (LocalSystem, W2K) account to open a null session to the remote system. Hackers can use Null logins to gain access to SYSTEM. This has no password. ITTIP Seminar Copyright 2001 R.C.Marchany 67 W5: Null Session Connections Systems Impacted Windows NT 4.0, Windows 2000 Am I vulnerable? Go to http://grc.com and click on the ShieldsUP link to see your system’s SMB exposure. ITTIP Seminar Copyright 2001 R.C.Marchany 68 W5: Null Session Connections How to Protect Needed for Domain Controllers Block TCP/UDP 139, 445 on the network Never allow Internet users to access any internal DC. ITTIP Seminar Copyright 2001 R.C.Marchany 69 W6: Weak Hashing in SAM Description LAN Manager passwords have very weak encryption. LM passwords are truncated to 14 characters, padded with spaces to 14 characters, converted to all Upper case, split into 2 seven character pieces. Crackers only have to do 2 upper case seven characters passwords. ITTIP Seminar Copyright 2001 R.C.Marchany 70 W6: Weak Hashing in SAM Systems Impacted Windows NT, Windows 2000 Am I vulnerable? Running default installation of NT or W2K? Yes because LM is created by default. ITTIP Seminar Copyright 2001 R.C.Marchany 71 W6: Weak Hashing in SAM How to Protect? Disable LAN Manager Use NTLMv2 (version 2 LM) Read Technet article “ How to Disable LM Authentication on Windows NT [Q147706] ITTIP Seminar Copyright 2001 R.C.Marchany 72 U4: R Commands Description If a user logins from a trusted system, then no password is needed to gain access to your system. rlogin, rsh, rcp Used by Network Appliance vendors with no concept of security. Systems Impacted Any Unix/Linux system ITTIP Seminar Copyright 2001 R.C.Marchany 73 U4: R Commands Am I vulnerable? Look for .rhosts, /etc/hosts.equiv files. If there, then yes. How to Protect Disable r-command in /etc/inetd.conf. Fire any one who wants to use it for they have no concept of security. ITTIP Seminar Copyright 2001 R.C.Marchany 74 U5: LPD Description The in.lpd program provides local printer services for Unix users. It listens on port 515 for incoming requests but has a buffer overflow vulnerability allowing root access. Systems Impacted Solaris 2.6-8 Linux ITTIP Seminar Copyright 2001 R.C.Marchany 75 U5:LPD Am I vulnerable? Are you running unpatched version of lpd? Yes, then you are. How to Protect Install latest Solaris or Linux patches. Disable print service in /etc/inetd.conf Block access to port 515 Install TCP Wrappers, Portsentry ITTIP Seminar Copyright 2001 R.C.Marchany 76 Common Vulnerable Ports Common ports probed/attacked Block or log all access to these ports as necessary. Login services telnet: 23/tcp FTP: 21/tcp NetBIOS: 139/tcp Ssh: 22/tcp r-commands: 512-514/tcp RPC/NFS Portmap/rpcbind: 111/tcp/udp NFS: 2049/tcp/udp lockd: 4045/tcp/udp ITTIP Seminar Copyright 2001 R.C.Marchany 77 Common Vulnerable Ports NetBIOS: 135/tcp/udp, 137/udp, 138/udp, 139/tcp, 445/tcp/udp X-Windows: 6000-6255/tcp DNS: 53/udp, LDAP: 389/tcp/udp Mail SMTP: 25/tcp POP: 109/tcp, 110/tcp IMAP: 143/tcp WWW HTTP: 80/’tcp SSL:443/tcp ITTIP Seminar Copyright 2001 R.C.Marchany 78 Common Vulnerable Ports Small Services Miscellaneous Ports < 20/tcp/udp, Time: 37/tcp/udp TFTP: 69/udp finger: 79/tcp NNTP: 119/tcp NTP: 123/tcp LPD: 515/tcp syslog: 514/udp SNMP: 161/tcp/udp, 162/tcp/udp BGP: 179/tcp SOCKS: 1080/tcp ICMP: Block incoming echo requests, outgoing echo reply, time exceeded, destination unreachable. This breaks ping. ITTIP Seminar Copyright 2001 R.C.Marchany 79 Summary You won’t eliminate all of your exposure by closing these 20 holes. Constant vigilance and awareness is the best defense. The consequences of failure could drive your company out of business. There’ll be another top 20 items to inspect in the future but at least we got rid of these items. ITTIP Seminar Copyright 2001 R.C.Marchany 80