Misbehavior Assumptions
advertisement
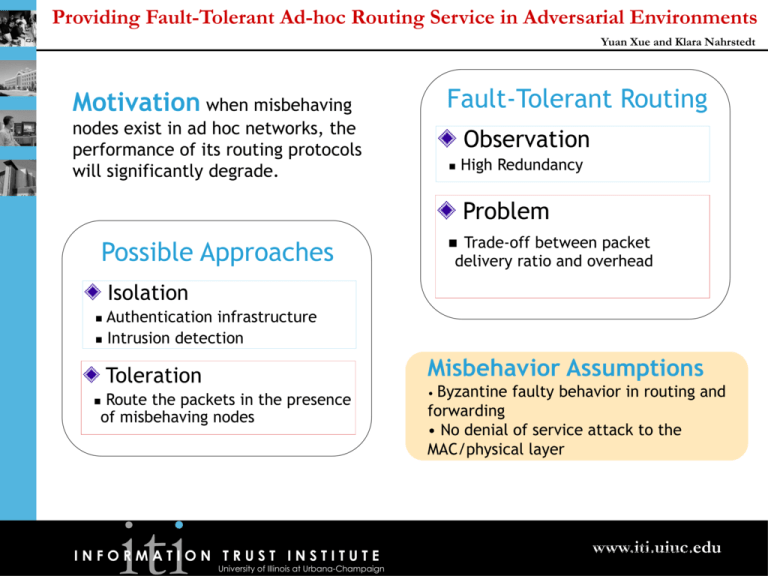
Providing Fault-Tolerant Ad-hoc Routing Service in Adversarial Environments Yuan Xue and Klara Nahrstedt Fault-Tolerant Routing Motivation when misbehaving nodes exist in ad hoc networks, the performance of its routing protocols will significantly degrade. Observation High Redundancy Problem Trade-off between packet delivery ratio and overhead Possible Approaches Isolation Authentication infrastructure Intrusion detection Misbehavior Assumptions Toleration Route the packets in the presence of misbehaving nodes INFORMATION TRUST INSTITUTE University of Illinois at Urbana-Champaign Byzantine faulty behavior in routing and forwarding • No denial of service attack to the MAC/physical layer • www.iti.uiuc.edu I: percentage that network has a “good” path II: percentage that DSR route protocol discovers a “good” path III:percentage that DSR uses a “good” path Providing Fault-Tolerant Ad-hoc Routing Service in Adversarial Environments Yuan Xue and Klara Nahrstedt Method end-to-end performance measurement Security Assumptions • Source and destination are well-behaved nodes • Priori trust relationship between source and destination Strategies Assume bad, until confirmed good Assume good, until confirmed bad Assured FT routing Algorithm Start with all available paths Refine the route progressively Drop unnecessary path Confirm a good path Best-effort FT Routing Algorithm Start with the shortest path Hypothesis test Discard the bad path Proceed with next shortest path Property Property Lower bound on packet delivery ratio Upper bound on overhead INFORMATION TRUST INSTITUTE University of Illinois at Urbana-Champaign Upper Bound on false positive probability Lower Bound on packet delivery ratio www.iti.uiuc.edu Providing Fault-Tolerant Ad-hoc Routing Service in Adversarial Environments Yuan Xue and Klara Nahrstedt 1.1 Results Greatly improved packet delivery ratio Controlled Overhead Packet delivery ratio 1 0.9 0.8 0.7 DSR AFTR BFTR Multipath 0.6 0.5 0.4 0 10 20 30 40 percent of misbehaving nodes Conclusion Fault tolerant routing is an efficient and effective approach to address the problem of misbehaving nodes in ad hoc networks Acknowledgement • ONR MURI CU fund • Professor Nitin Vaidya and Pradeep Kyasanur for their comments and helpful suggestions INFORMATION TRUST INSTITUTE University of Illinois at Urbana-Champaign www.iti.uiuc.edu