Chap 8
advertisement

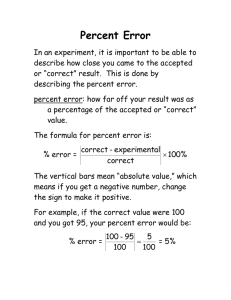
Chap 8: Administering Security Security is a combination • Technical – covered in chap 1 • Administrative • Physical controls SE571 Security in Computing Dr. Ogara 2 Security Planning Risk analysis Policy Physical control/security SE571 Security in Computing Dr. Ogara 3 Effective security planning is essential for computer organization A Security plan is a document that describes how an organization will address its security needs: • It is an official record of current security practices • Blue print for review to improve those practices SE571 Security in Computing Dr. Ogara 4 To define and implement a security plan we concentrate on three aspects as follows: Contents of security plan/what should be there? 2. Who are involved in security planning? 3. How to obtain support for a plan 1. SE571 Security in Computing Dr. Ogara 5 Security plan should address seven issues 1) 2) 3) 4) 5) 6) 7) Policy – describes the goals and are people involved willing to attain these goals? Current state – the status of security at the time of the plan Requirements – recommends ways to meet the security goals Recommended controls – mapping controls to the vulnerabilities identified in the policy and requirements Accountability – who is responsible for each security activity Timetable – when do different security functions take place? Continuing attention – specify a structure to periodically update the security plan SE571 Security in Computing Dr. Ogara 6 The Software Engineering Institute at Carnegie Mellon University has created a framework for building a security plan Identify enterprise knowledge Identify operational area knowledge Identify staff knowledge Establish security requirements Map high priority information assets to information infrastructure 6) Perform an infrastructure vulnerability evaluation 7) Develop a protection strategy 1) 2) 3) 4) 5) SE571 Security in Computing Dr. Ogara 7 Explain what should be accomplished Are functional or performance demands placed on a system to ensure a desired level of security The inputs to a security plan are shown in the diagram SE571 Security in Computing Dr. Ogara 8 Plan should identify who are responsible for implementing security requirements Different groups can be responsible for different security roles, for example, • PC Users: security of own machines • Project leaders: security of data and computations • Managers: seeing that the people they supervise implement security measures SE571 Security in Computing Dr. Ogara 9 • Database administrators: access to and integrity of data in databases • Information officers: creation and use of data, retention and proper disposal of data • Personnel staff members: security involving employees SE571 Security in Computing Dr. Ogara 10 Membership should relate to different aspects of security Planning team should respect each of the following groups: • • • • • • • Computer hardware group System administrators System programmers Application programmers Data entry personnel Physical security personnel Representative users SE571 Security in Computing Dr. Ogara 11 Ensure the security functions will be implemented and security activities carried out Three groups of people must contribute to making the plan success • The planning team • Those affected by the security recommendations • Management: using and enforcing security Organizations can use a “business continuity plan” to deal with situations having two characteristics: • Catastrophic situations: a computing capability is suddenly unavailable through fire or flood • Long duration SE571 Security in Computing Dr. Ogara 12 Effective security planning includes careful risk planning Risks can be distinguished from other events interms of : • Risk impact associated with an event • The probability (P risk) of an incidence associated with each risk. 0 =< Prisk <= 1; When Prisk = 1 we say that there is a problem Risk control – the degree to which an outcome can be changed SE571 Security in Computing Dr. Ogara 13 The effects of a risk can be quantified by multiplying the risk impact by the risk probability, yielding the risk exposure: Risk Exposure – risk impact * P risk Example: Prisk = 0.40; risk impact $10,000 (cost of cleaning the affected files) Risk Exposure = 0.4*10000 = $ 4,0000 So we can based on the calculation decide an antivirus software worth $400 is worth an investment SE571 Security in Computing Dr. Ogara 14 Three Strategies for Risk Reduction: Avoiding the risk • Change security requirements Transferring the risk • Allocate the risk to other systems, people, assets • Buy insurance to cover any financial loss Assuming the risk • Accept and control it with available resources • Prepare to deal with the loss if it happens SE571 Security in Computing Dr. Ogara 15 In addition to impact cost there is also costs associated with reducing it Risk leverage is the difference in risk exposure divided by the cost of reducing the risk Risk leverage = (risk exposure before reduction – risk exposure after reduction)/cost of risk reduction SE571 Security in Computing Dr. Ogara 16 So if the leverage value of a proposed action is not high enough then we need to find a less costly strategy The parameters in Risk Leverage equation demand the risk analysis process to identify and list all exposures in the computing system For each exposure we need to identify possible controls and their costs Finally we need to carry out a cost–benefit analysis SE571 Security in Computing Dr. Ogara 17 The basic steps of risk analysis are: 1. Identify the assets 2. Determine vulnerabilities 3. Estimate likelihood of exploitation 4. Compute expected annual loss 5. Survey applicable controls and their costs 6. Project annual savings of control SE571 Security in Computing Dr. Ogara 18 US Army – OPSEC used during Vietnam War 1) Identify critical information to be protected 2) Analyze the threats 3) Analyze the vulnerabilities 4) Asses the risks 5) Apply countermeasures SE571 Security in Computing Dr. Ogara 19 US Airforce – Operational Risk Management Procedure (AIROO) 1) Identify hazards 2) Assess hazards 3) Make risk decisions 4) Implement controls 5) Supervise SE571 Security in Computing Dr. Ogara 20 Indicating the goals of a computer security effort and the willingness of the people involved to work to achieve those goals. SE571 Security in Computing Dr. Ogara 21 Document to inform users of the objectives and constraints on using a system Purpose of policy document • Recognize sensitive information assets • Clarify security responsibilities • Promote awareness for existing staff • Provide guidelines to new employees SE571 Security in Computing Dr. Ogara 22 A security policy must address the following: • The audience – who can gets access? • Contents – which resources • Characteristics of good security policy – how? SE571 Security in Computing Dr. Ogara 23 Three groups of audience • Users • Owners • Beneficiaries (e.g. customers, clients) Audience uses the security policy in important but different ways For each policy define the degree of confidentiality, integrity, and the continuous availability in the computing resources provided to them SE571 Security in Computing Dr. Ogara 24 The risk analysis identified the assets that are to be protected These assets (computers, networks, data) should be listed in the policy document The policy should also indicate: • Who should have access to protected resources • How unauthorized people will be denied access • How that access will be ensured SE571 Security in Computing Dr. Ogara 25 Coverage – should be comprehensive ad general Durability – survive system’s growth and expansion…applicable to new situations Realism – realistic/feasible to implement Usefulness – should be concise, clear and direct SE571 Security in Computing Dr. Ogara 26 Examples: • Data sensitivity policy • U.S. Government Agency IT Security Policy • Internet Security Policy • The U.S. government Email Policy SE571 Security in Computing Dr. Ogara 27 Describes protection needed outside the computer system Physical security can be in one of this forms: • Natural disasters • Power loss • Human vandals Contingency planning is key to successful recovery: • Backups, offsite backups, network storage, etc SE571 Security in Computing Dr. Ogara 28 Describing the status of security at the time of the plan Risk analysis – a careful investigation of the system, its environment, and the things that might go wrong SE571 Security in Computing Dr. Ogara 29 Recommending ways to meet the security goals Heart of the security plan Organizational needs SE571 Security in Computing Dr. Ogara 30 Mapping controls to the vulnerabilities identified in the policy and requirements SE571 Security in Computing Dr. Ogara 31 Describing who is responsible for each security activity Personal computer Project leaders Managers Database administrators Information officers Personnel staff SE571 Security in Computing Dr. Ogara 32 Describing who is responsible for each security activity Personal computer Project leaders Managers Database administrators Information officers Personnel staff SE571 Security in Computing Dr. Ogara 33 Identifying when different security functions are to be done Show how and when the element of the plan will be performed SE571 Security in Computing Dr. Ogara 34 Specifying a structure for periodically updating the security plan SE571 Security in Computing Dr. Ogara 35