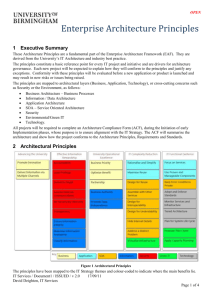
Flinders IT Standards
advertisement

Information Technology Services Flinders IT Standards Version 1.5 October 2013 Flinders IT Standards 1. 2. 3. 4. 5. 6. 7. 8. Purpose of Document ..................................................................................................................... 3 Related Documents......................................................................................................................... 4 Definition of the FITS ...................................................................................................................... 4 Systems Classification .................................................................................................................... 5 Change Control ............................................................................................................................... 5 Architectural Principles ................................................................................................................... 6 Business Architecture ..................................................................................................................... 8 Information Architecture .................................................................................................................. 8 8.1 Conceptual and Logical Data................................................................................................... 9 9. Application Architecture .................................................................................................................. 9 9.1 Presentation Architecture ........................................................................................................ 9 9.2 Database environment ........................................................................................................... 10 9.3 Adaptors ................................................................................................................................. 11 9.4 Application Development ....................................................................................................... 11 9.4.1 Application Consolidation and Key Systems ................................................................. 12 9.4.2 Methodologies ................................................................................................................ 12 9.4.3 Languages ..................................................................................................................... 12 9.4.4 Source Code Change Control and Management .......................................................... 13 9.4.5 Software Testing ............................................................................................................ 13 9.5 Application Support Services and Integration ........................................................................ 14 9.5.1 Identity Management ..................................................................................................... 14 9.5.1.1 Directory Services ...................................................................................................... 14 9.5.2 Application Integration ................................................................................................... 14 9.5.3 Business Reporting ........................................................................................................ 15 9.5.4 Collaboration Services ................................................................................................... 15 9.5.5 Web Server .................................................................................................................... 16 9.6 Desktop Applications ............................................................................................................. 16 9.7 Workstation Support Services ............................................................................................... 17 9.7.1 Remote Printing Services .............................................................................................. 17 9.7.2 Remote File Services ..................................................................................................... 17 9.7.3 Remote Management .................................................................................................... 18 9.7.4 Anti-virus, anti-spy ware and SPAM filtering services ................................................... 18 9.7.5 Systems Monitoring and Analysis .................................................................................. 19 10. Infrastructure Architecture ......................................................................................................... 19 10.1 Client Platform Architecture ............................................................................................... 19 10.2 Educational Technology Architecture ................................................................................ 20 10.3 Server Technology Architecture ........................................................................................ 21 10.3.1 Server Operating Systems ......................................................................................... 21 10.3.2 Server Hardware Vendors ......................................................................................... 22 10.3.3 Virtual Server Systems .............................................................................................. 22 10.3.4 Storage Systems........................................................................................................ 23 10.3.5 Storage Protocols ...................................................................................................... 23 10.3.6 Backup and Archiving Systems ................................................................................. 24 10.4 Network Technology Architecture ...................................................................................... 24 10.4.1 Switch and Router Equipment ................................................................................... 24 10.4.2 Wireless Access Points ............................................................................................. 25 10.4.3 Network Load Balancers ............................................................................................ 25 10.4.4 IP Telephony .............................................................................................................. 26 11. Technology Advisory Groups..................................................................................................... 28 12. Document Review and Updating ............................................................................................... 28 13. Glossary ..................................................................................................................................... 29 14. Revision History ......................................................................................................................... 31 Document1 2 of 31 1. Purpose of Document The purpose of this document is to define the Flinders IT Standards, FITS as referred to by the IT Architecture Policy. The business scenario extract below describes the typical context in which the FITS will be used. Scenario The business implements an IT solution to a business problem Actors An administrative business unit or academic faculty / department, ITS, solution vendors Steps Comments Use of the FITS 1. The business, (possibly with support from ITS), defines the requirements for the solution Typically Business Analysts would be involved in projects undertaken to define requirements. 2. The business in consultation with ITS identify solution options and build a business case. This leads to a selection of ways in which the problem may be solved – commercial-of-the-shelf, custom development etc. 3. The business and ITS decide on solution short list and assess against the environment. The FITS, specifically its policy guidelines, assists in selecting the class of solution to be adopted. Specific solutions are identified and their adherence to the environments is assessed using the FITS. Commercial off-the-shelf (COTS) product Custom internal development Custom external development Vendors may contribute to this step also. 4. The business and ITS identify the business environment in which the solution options will operate The FITS provides a framework to define the environmental constraints on the solution options 5. The business and ITS select the solution The assessments are used as input to an objective decisionmaking framework to identify the best solution. Pilot undertaken where appropriate. Refer notes below… 6. Implement the solution 7. On Flinders IT infrastructure Outside of Flinders (e.g., externally hosted) These steps have the greatest direct impacts on the ITS group (and form the justification for the FITS). Support and Maintain the solution Notes In step 5 the decision making process may result in the following types of decisions: Select a solution with best FITS conformance Select a solution which delivers very high value to the business which justifies additional ITS overhead in its maintenance – i.e., The cost benefit ratio – ITS Cost : Business benefit is skewed in favour of business benefit Select the only solution which delivers the key requirements – being aware of the impact on ITS Select the solution which best delivers business prioritised requirements amongst a selection of similar FITS impact solutions. Document1 3 of 31 2. Related Documents Relevant policies and standards are published on the Flinders University website. The following policy directly relates to this document: Flinders University Applications Acquisition, Development and Maintenance Policy (Draft) ITS policies and standards can be accessed at http://www.flinders.edu.au/ppmanual/computing/computing_home.cfm. Flinders University Policies and Procedures can be accessed at http://www.flinders.edu.au/ppmanual/ 3. Definition of the FITS Through the definition of a series of standards, the FITS describes the ITS supported architecture(s) that should be considered at each stage of the technology life cycle, including system conception, development, implementation, extension, maintenance, replacement or retirement. The FITS is based on a descriptive classification of all key elements of the architecture, including hardware, system and application software, development and management tools and technologies etc. Most of these “elements” are then classified according to the following measures: Class Element Notes Supported <product/technology> The element is preferred by ITS and represents the best match to the architectural principles To Be Supported <product/technology> The element is being considered or actively evaluated to determine its class. Candidate products/technologies cannot be implemented in a production environment until its class is confirmed as either supported or restricted. Restricted Support <product/technology> The element is required by a specific application and will be supported on that basis only. New products/technology of this class may only be used with the written permission of the Director ITS or delegate. Such usage must be justified in the business case for the system. Commodity items or specific PC applications. Not Supported <product/technology> The element is being actively phased out by ITS. New products/technologies of this class may not be introduced. Prohibited <product/technology> The element does not meet or contradicts the architectural principles. New products/technologies of this class may not be implemented and existing implementations may be targeted for replacement. Products may also be classed as prohibited due to potential security or legal issues. The exception to this is Desktop Applications (see 9.6), which is categorised into only 2 classes: Supported - Preferred Not Supported - Accepted but not supported Document1 4 of 31 4. Systems Classification Each system will be classified according to a number of criteria that describe the characteristics of the system. The characteristics relating to the classification of a key system are outlined as follows: It is used University-wide or on a Divisional basis It supports a university-wide administrative or statutory need of the University (e.g. Student Administration, Research, Human Resources, Finance) or it directly supports the delivery of teaching at least on a Divisional basis (e.g. FLO) It is used to move data between or into key systems It has a responsible Business Owner/technical support It conforms to the University’s information system architecture It runs on a Flinders approved server platform It operates within the Standard Flinders Operating Environment (SOE) It has a documented Backup strategy and Disaster Recovery Plan Where a system does not meet the above criteria, a system may still be considered for classification as key, provided adequate justification exists. Justifications may include things such as value to stakeholders, reputational risk, significant operational disruption or strategic importance. Unless specifically approved as key, Applications will be deemed to be non-key. When an additional system is introduced to Flinders, the system will be added to the inventory and assigned a classification for each criterion. A BPM modelling tool will be selected to be the primary source of information on systems classification. These criteria comprise all the elements in the FITS which describe a system (e.g. database environment, programming language etc) and additionally other criteria specified in the Applications Acquisition, Development and Maintenance Policy. The criteria that originate from the elements of the FITS are particularly relevant to The effective management and development of staff and their skills Developing plans for the consolidation, migration and retirement of systems The criteria that originate from the Applications Acquisition, Development and Maintenance Policy are particularly relevant to establishing the appropriate arrangements for that system in terms of: Implementation Maintenance Support Testing & Development Change Management 5. Change Control This document can only be changed with approval of the Director ITS. Document1 5 of 31 6. Architectural Principles The architectural principles follow the principles outlined in the Architecture Policy: IT architecture must be business driven Use of key systems in preference to the use of non-key systems Use of open standards Use of packaged and configurable solutions in preference to solutions requiring custom development of software Products for which vendor support is available Systems which are compliant with relevant legislative or regulatory requirements related to non-functional aspects such as privacy, security and resilience The following architectural principles, which are encompassed in the policy principles, provide greater context and specific application to the architectures described in this document: No. Principle Relates to AP-1 Alignment with business requirements Convergence between business needs and technical capabilities. AP-2 Focus on key systems Maximise solutions based on existing systems. Among the existing systems maximise solutions based on key systems. AP-3 Preference towards integrated solutions rather than ‘best of breed’ Integrated solutions enable greater efficiencies and improved reliability. Should minimise support costs and overheads. AP-4 Minimise the number of vendors and suppliers Reduce overheads and build strategic relationships with vendors. AP-5 Focus on secured systems and data Security of systems, information and secure access to it. AP-6 Focus on availability and reliability High levels of availability of key systems supporting critical business services. AP-7 Protecting privacy and information sharing Conform to Flinders security policies for systems being developed or extended in house, or when reviewing solutions provided by external vendors. AP-8 Use and control of authoritative data source A designated single authoritative data source for each class of information in order to ensure effective management of data and data integrity. AP-9 Encourage use of open standard technologies and platforms Prefer open standards for the building of Flinders’ information systems for increased flexibility and interoperability of solutions as well as reduced technology and business risks. AP-10 Platform independent from delivery of core functionality Provide access to the same functionality or service from a disparate set of client tools (such as web browser, PDA, desktop computer), supported by the same application component or code base. AP-11 Encourage use of purchased software instead of development Prefer commercial-off-the-shelf (COTS) applications to custom development options. Prefer re-using or extending an existing COTS application to sourcing a new one. Prefer configuration over customisation. AP-12 Use of standard platforms and software products Use the elements of Standard Operating Environment (SOE). AP-13 Sharing of resources for delivery of applications Shared usage of hardware and software resources for the delivery of application services in order to meet security, business continuity and performance requirements more efficiently. AP-14 Solutions to be built with a focus on future re-usability Maximise amount of re-usability and modularisation in solution design in order to provide better change management and to minimise maintenance costs. AP-15 Data provision devolved to end user tools where appropriate Centralise data to maintain its integrity and decentralise presentation of it to provide flexibility for the users. Document1 6 of 31 AP-16 Focus on sustainability Minimise environmental impact of technologies and solutions while balancing financial, social and efficiency concerns. AP-17 Ease of access to relevant expertise Current staffing profile and skills set and / or the availability of relevant external contractors. AP-18 Optimal use of infrastructure assets Ensure consolidation of assets and that assets are not underutilised. Document1 7 of 31 7. Business Architecture Business architecture describes the accountabilities for, and the operation of the processes, which deliver the main business activities. The business architecture is referenced by, supported by, and has interactions with the IT architecture. While ITS is not responsible for Business Architecture, ITS is responsible for Business Process Modelling. Element Description Business Process Modelling Process to model business processes, data, organisation structure, and business rules as well as IT architecture models and representations in a single repository. Class Product Notes Supported Visio Visio is used to produce technical diagrams and process maps for vendor system implementation to maintain business accessibility. Visio diagrams can be exported and imported into a BPM tool if required. Although Business Architecture resides in the Business Domain, it is essential that the Director ITS has a key role in its governance. This aids the development of compatible business and IT architectures, thus enabling the design and delivery of reliable and efficient systems, while also reducing the risk associated with managing change. Owner Director ITS Architectural Principle Reference AP-1 Process driven by business requirements. AP-8 The business process has been defined and modelled in consultation with the business and is maintained by a well-defined management process. AP-9 The business process model created in the selected BPM tool can be transferred to another BPM product. AP-11 Use of a COTS product: e.g. Visio AP-16 Aim to reduce reliance on paper within business processes. Pursue online viewing, reviewing of documents. AP-17 Aim to increase expertise available within ITS through the deployment of professional development opportunities and the allocation of resources. 8. Information Architecture Information architecture encompasses all enterprise information used within the organisation. It deals with the use of information, naming conventions to reference information and the relationship of information to business processes. Owned and primarily defined by the business, this architecture is translated to logical and physical data entities used within the IT domain. ITS defines the standard representations, using appropriate methods and associated UML model types, and supports the tool and repository. Good data modelling techniques enable accurate impact analysis of the potential introduction of new data or changes to existing elements or structures. Building and maintaining a map of the university’s descriptions and use of data is vital to support this type of activity. Document1 8 of 31 8.1 Conceptual and Logical Data Conceptual data models describe large categories of information and how they may relate to or be used by business users in terms of business objects, (e.g. forms, categories), and general entities (i.e. Local Students, International Students). Logical data models define standard business entities with related attributes instantiated as UML Class Diagrams. Logical data models are vital in ensuring business specifications of data are transferable to technical specifications and database designs Element Description Conceptual Data Modelling Conceptual data models are generally constructed during early analysis phases. They incorporate forms, large entities and technical terms for data used within the organisation. Logical Data Modelling Logical data models are generally constructed during detailed specification phases. They are often built on Conceptual Data models where refinement and consolidation of Entities, (Classes), will occur, as well as formal representations of attributes associated with classes. Class Product Notes Supported Visio Visio is currently the main tool used to represent both the conceptual and logical data models of Flinders business. 9. Application Architecture Application architecture comprises the software systems, platforms and integrations that collectively support business processes. Flinders’ application architecture is diverse with a wide variety of solutions deployed, interlinked by a number of custom integration implementations. Flinders’ applications solutions will come from the following three conceptual layers: Architectural Layer Description Presentation Architecture Provides access to information, services and applications using client tools and interfaces, such as web browsers for reporting or Portal based services and ‘thick clients’ (Finance One). This layer is mainly focused on authenticated Web delivery. Core Transactional Systems Core transactional systems provide computing and application resources to critical data entry applications underpinning the University’s core business processes and activities. Business Intelligence & Data Repositories The design and production of information is managed in the Business Intelligence & Data Repository layer where extracted information from core transactional systems is transformed into a consumable state. This layer also maintains refreshed data repositories or ‘data-marts’ which primarily support individual end user reports or services. 9.1 Presentation Architecture Support for the current suite of interfaces and products will continue. While some exceptions are granted they do not negate the need to pursue common authentication systems, single login to many services and a standard, user-friendly application interface tailored for different user groups. Element Description Presentation tool Provides access to information, services and applications using client tools and interfaces, such as web browsers for reporting or Portal based services and ‘thick clients’ (Finance One). Document1 9 of 31 Class Product Notes Supported PHP Required for presentation layer for Moodle (FLO). FLO is a COTS Learning Management System (LMS), which is externally hosted and managed by the vendor. Supported JavaScript Required for data warehouse, Service Interruption Notifications and other sundry applications. Supported .Net For Finance and Student Administration online services. Not Supported Oracle Forms Interface Currently required for the administration of applications – specifically for Human Resources and sundry applications. To be phased out. In the design and build phases of web based software development projects, user centric techniques and either story boarding or mock ups of pages and interactions should be pursued using a standard analysis and design approach. The same standards apply to all web applications whether they are developed in-house or by third parties. The University requires strict adherence to web presentation and visual design standards as found at http://www.flinders.edu.au/marketing-communications/training-and-support/onlinecommunications-support/visual-design.cfm Owner Associate Director, Applications Services Architectural Principle Reference AP-2 Focus on Key Systems. AP-10 n-tier architecture and platform independent access to functionality. AP-11 Use of a COTS product. AP-13, AP-14 Portal architecture promotes reusability and sharing of resources. AP-15 Use of centralised data and decentralised presentation principle in the portal based solution. 9.2 Database environment Oracle is the current primary relational database. Microsoft SQL Server is a major relational database getting increased use. All structured data should be stored in a centrally administered database. Any new application or development initiative must also take this into account at the conception, planning and implementation phases. Element Description Database Relational Database Management System (RDBMS) Class Product Notes Supported Oracle 11G R1/R2 Production applications. Supported SQL Server 2005/2008 R2 Production applications. Supported MySQL 5.1 Required for specific web applications. Not Supported PostgreSQL Specific applications. Document1 10 of 31 Not Supported Oracle 10G R1/R2 Production applications –phased out. Prohibited Microsoft Access1 Not suitable for mission critical applications or storage of persistent corporate data. Exception may be made for pure data push solutions where other preferred or supported databases cannot provide adequate functionality. Prohibited FileMaker Pro Not suitable for mission critical applications or storage of persistent corporate data. Owner Associate Director, Applications Services Architectural Principle Reference AP-3 Preference for integrated solutions. AP-8 Centrally controlled and managed data. AP-11 Use of a COTS product. AP-15 Central data repository. 9.3 Adaptors Database adaptors provide secure access to RDBMS where required within integration or reporting solutions. In addition they may form an abstraction layer between native RDBMS applications and staging or reporting data repositories. Element Description Database Adaptor Database adaptors used to couple RDBMS to staging or reporting repositories to support access to data. Class Product Notes Supported JDBC The Java Database Connector is generally used in Oracle Application server solutions. JDBC connectors can successfully be used for all supported Flinders RDBMS web services. Supported Web Services Web services are a standardised way of integrating Webbased applications using the XML, SOAP, WSDL and UDDI open standards over an Internet protocol backbone. Restricted Support ODBC Open Database Connectivity is used in specific client server solutions. Restricted Support Product API The use of pre-built, existing APIs while not encouraged, is acceptable for some applications where other adaptors are not supportable. 9.4 Application Development While the architectural principles encourage the use of off-the-shelf solutions rather than in-house development, ITS will be expected to undertake a certain amount of development, particularly in the maintenance of legacy key systems and the business intelligence and integration layers. By adhering to managed processes and methodologies, ITS ensures that regardless of language or chosen platform, good architectural principles are employed in all developed solutions. All software development projects are required to adhere to Flinders’ Architectural Principles as well as meeting the goals of re-usability and supportability. Adequate evidence of design and technical specification and maintenance documentation of all solutions is required, whether built by internal staff or third parties. 1 Microsoft Access is prohibited in the context of Database Environments only. Document1 11 of 31 9.4.1 Application Consolidation and Key Systems The architectural principles encourage the maximum exploitation of the University’s existing enterprise and key systems. 9.4.2 Methodologies All software development should follow one of the supported Software Development Methodologies. Element Description Software Development Methodology Standard for software specification, production, testing and deployment. Class Product Notes Supported SDLC Methodology Contained in Project Management Framework. http://www.flinders.edu.au/its/information-technologyservices/about-us/its-project-services/pmf/pmf_home.cfm Supported Agile Approaches (e.g. Scrum, Lean, Test Driven) Emphasis on communication and collaboration, functioning software, and flexibility to adapt to emerging business realities. 9.4.3 Languages The objective is to employ a limited number of languages and development environments in order to narrow the skill set to be maintained within ITS. Currently, the ongoing support of critical key application systems as well as the transition to the new standard requires a range of skills and languages. Element Description Application Development Language Languages used to develop Flinders applications Class Product Notes Supported Java Used within Oracle Application Server solutions. Supported Apex Oracle Application Express (Oracle APEX) is a declarative, rapid web application development tool for the Oracle database. It is a fully supported, no cost option available with all editions of the Oracle database. Supported PL/SQL Oracle’s procedural extension language for SQL and the Oracle relational database. Supported Perl Perl is the scripting language of choice on Linux based systems, and is essential for systems administration tasks. Supported Powershell Microsoft Powershell has replaced VB Script as the default scripting language within Microsoft environments. Systems such as Office 365 and automation of administrative tasks rely upon it. Supported .Net Microsoft’s Application Development Platform. Used for SMS and Progress Review applications. Supported PHP Required for specific web applications. Restricted Support ColdFusion Current Application Framework used for web CMS, lecture capture and important smaller systems. Prohibited Microsoft Access Document1 12 of 31 Prohibited VB Script Owner Associate Director, Applications Services Architectural Principle Reference AP-9 9.4.4 Use of standards based technologies: Java, SQL, etc. Source Code Change Control and Management Vital to the change and release management aspects of all software development projects is version control of software and documentation artefacts. All software developed for the University must have source code maintained and auditable in a suitable source code management system. Similarly scripts used for updates, upgrades or utility type functions should also be maintained in the same repository even though they may not be directly part of the software application. Element Description Source Code Change Control Repository to manage source code and track changes. Class Product Notes Supported Subversion Product built by SUN used as source repository for all Portal / Java platform code. Restricted Support MS Visual SourceSafe Used solely as a repository for historical ColdFusion Application Code as well as specification library for IS Systems and Applications Development. Owner Associate Director, Applications Services Architectural Principle Reference AP-8 Centrally controlled and managed data. AP-11 Use of a COTS product: Subversion. 9.4.5 Software Testing The University requires all internally and externally developed solutions be put through formal systems and acceptance testing based on functional and technical specification. For externally developed solutions the system and acceptance test cases together with a description of the test environments will be provided by the vendor or solution provider as part of the deliverables. This is required for maintaining the system and change management purposes after delivery of the solution to ITS. Owner Associate Director, Applications Services Architectural Principle Reference AP-8 Centrally controlled and managed test artefacts. AP-9 Use of open source open standards based solutions. AP-11 Use of a COTS product: Open STA, JIRA. Document1 13 of 31 9.5 Application Support Services and Integration 9.5.1 Identity Management Identity management comprises the identification of a user, known as authentication, and the granting of access or privileges to a set of particular services or functions, known as authorisation. Typically, users are classed in groups or levels of authorisation, which may be organised across functional or departmental areas. Staff and student access to information and systems via network resources is also specified within the domain. Access within applications forms part of identity management but typically application level authentication is only subject to the application and contributes to the issue of multiple accounts, differing levels of security adherence and poor administration and control. Single sign-on is to be pursued for application integration into the university’s supported systems as well as encouraging the use of portal delivery of application services to utilise the in-built authentication service available. Element Description Identity Management (IDM) Techniques and protocols concerned with user authentication and access to services and resources. Class Product Notes Supported MS Active Directory Required for File, Print and email authentication, applications are being actively ported to OID authentication. Restricted Support Application specific user repository To be used only when specified by business requirements and authorised by Director ITS or delegate. Restricted Support Novell eDirectory Source of authentication data (IDM). Owners Associate Directors, Applications Services / Infrastructure Services 9.5.1.1 Directory Services The Identity Management system becomes aware of a user’s identity and access privileges to enterprise applications after authenticating the end user. Directory Services manage this process by acting as a central repository for user information by incorporating data from various enterprise sources and repositories. Element Description Directory Services Provides a centralised data store for users’ identity data and all supporting data to ensure that information is properly used and shared, and that sensitive information is protected. Class Product Notes Supported Active Directory Microsoft’s directory service product. Restricted Support eDirectory Novell directory service product. Owners Associate Directors, Application Services / Infrastructure Services Architectural Principle Reference AP-5 Authorised access to systems and data. AP-8 Centrally controlled and managed authentication and authorisation. AP-9 Use of a standards based solution: eDirectory. AP-11 Use of a COTS product: eDirectory, AD. 9.5.2 Application Integration Document1 14 of 31 The integration architecture is a point-to-point solution supported on a case-by-case basis. 9.5.3 Business Reporting Reporting is included in this section as often data integrations are specifically required for report delivery. Element Description Business reporting Generation of business reports from various data sources. Class Product Notes Supported Oracle Discoverer End-user reporting tool capable of integration with Portal. Supported Oracle Business Intelligence An operational tool for management staff providing operational reporting and student information. Supported Crystal Reports General purpose reporting tool. Owner 9.5.4 Associate Director, Applications Services Collaboration Services Collaboration Services are made up of a range of service types including: services for delivery of lectures and courses, workspaces, email, calendars etc. Element Description Email, calendar, work management Tools for collaboration services. Class Product Notes Supported Microsoft Office 365 Microsoft’s messaging and collaborative software product. Supported Microsoft Outlook Supported Confluence - Wiki Team collaboration software written in Java. Supported Microsoft Entourage Email client and personal information manager developed for Mac OS. Supported Apple Mail Email program included with Mac OS X operating system. Supported Skype Voice over IP service and software application. Supported Learning Management Systems (FLO) Used to support specific student work spaces and use of email, and web technologies. Refer to section 9.1 for the specific LMS products. Supported Cisco Collaboration Suite Collaboration tools across voice, video, web conferencing, messaging, mobile applications and enterprise social software. Restricted Support Microsoft Sharepoint Pilot Sharepoint implementation. Not Supported Microsoft Live@edu Hosted collaboration services for students – being phased out. Not Supported Other mail clients Other mail clients including but not limited to: Thunderbird, Gmail, and Yahoo Mail are not supported. Owners Associate Directors, Application Services / Infrastructure Services Architectural Principle Reference AP-8 Document1 Centrally controlled and managed data. 15 of 31 9.5.5 AP-10 Platform independent collaboration service. AP-11 Use of a COTS product: LMS products. Web Server Applications are increasingly deployed via a web server or with significant application services reliant upon web servers. Element Description Web Server Server software providing services via the HTTPS protocol. Class Product Notes Supported Apache Industry standard. Supported Oracle OAS Required for ALESCO HR clients. Supported Microsoft IIS Required for Windows web applications. Supported GlassFish Open source application server. Supported WebLogic Server software application enables connection of users in a distributed computing environment. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-9 9.6 Open source, industry standard web server. Desktop Applications Refer to the Software and Standard Operating Environments Standard. The procurement of any other desktop application will be authorised by the Director, ITS or delegate on a case-by-case basis. Element Description Desktop applications Desktop applications reside on a user’s machine and can operate as standalone applications, i.e. they do not require additional components on servers or key application systems. Class Product Notes Supported Any desktop applications included in a standard operating environment. The Software and Standard Operating Environments Standard specifies the software. This includes site licensed software which is available at no additional cost. Not Supported Any other desktop application If authorised by the Director ITS or delegate, other desktop applications may be procured and installed, but such applications should be considered to be unsupported by ITS. However, support arrangements may be made with ITS, in which case the application will be added to the ‘accepted and supported’ list. Owner Associate Directors, Infrastructure Services / Client Services Architectural Principle Reference AP-12 Document1 Use of SOE systems. 16 of 31 9.7 Workstation Support Services 9.7.1 Remote Printing Services Element Description Remote printing services Configuration and management of printing services. Class Product Notes Supported MS Print Services In the normal office environment concerned with administrative or business computing tasks, printers will be setup as shared resources for a workgroup via a dedicated network point. Supported Unicard A single printing and copying system for students across the Bedford Park and metropolitan Adelaide locations. Owner Associate Directors, Infrastructure Services / Client Services Architectural Principle Reference AP-8 Use and control of authoritative data source. AP-11 Use of COTS products. AP-13 Shared usage of hardware and software resources. 9.7.2 Remote File Services Element Description File Storage Location for storage of user created files. Class Product Notes Supported MS managed file systems MS Network file system. Supported Local desktops Standard file redirection implemented to file server. Prohibited Local desktops Storing data primarily on local desktop machines is prohibited. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-5 Security and accessibility of information. AP-8 Use and control of authoritative data source. AP-11 Use of COTS products. AP-13 Shared usage of hardware and software resources. Document1 17 of 31 9.7.3 Remote Management All SOE desktops will be open for remote management using the following standards. Element Description Remote management Provides remote access to and management of desktop machines. Class Product Notes Supported Bomgar Remote support solution that allows service desk consultants to access and control systems and devices remotely, including PCs, smartphones, tablets, servers and switches. Supported Casper Suite Comprehensive platform for managing Mac OS X computers, including inventory, software distribution, settings and security. Supported MS SCCM Microsoft systems management software product for managing large groups of Windows-based computer systems. Provides remote control, patch management, software distribution, operating system deployment, network access protection, and hardware and software inventory. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-7 Protection of privacy and information sharing – Adherence to Flinders’s privacy policy is ensured to be extended to staff workstations. AP-11 Use of COTS products. AP-12 Use of SOE systems. 9.7.4 Anti-virus, anti-spy ware and SPAM filtering services All SOE desktops will be protected using anti-virus software for desktops as per SOE standards. All ITS supported servers are configured with the following server based Anti-virus tools. Element Description Anti-virus software for servers All servers will be protected using the following tools. Class Product Notes Supported MS Forefront For Windows platforms. Supported Sophos For all platforms. Email servers implement Spam filtering which supports notification to end-users. Microsoft Exchange and other supported mail clients also support configuration of local Spam rules. Element Description Spam filter for servers Software product supporting trapping and filtering of suspected Spam email based on rules and content of email received by Flinders mail servers. Class Product Notes Supported Sophos PureMessage Product supporting Flinders spam filtering rules. Blocks spam, viruses, spyware and phishing. Document1 18 of 31 Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-5 Secured systems data. AP-6 Secured availability and reliability. AP-7 Protection of privacy and information sharing – Adherence to Flinders’s privacy policy is ensured to be extended to staff workstations. AP-11 Use of COTS products. AP-12 Use of SOE systems. 9.7.5 Systems Monitoring and Analysis System monitoring tools enable the monitoring of network services or host resources and will send an alert if a problem is identified. Analysis tools enable systems administrators to find the root cause of problems quickly and locate latent systems issues before they cause downtime. Element Description Systems monitoring and analysis Software product supporting monitoring and early problem identification and the ability to find the root cause of problems quickly. Class Product Notes Supported Splunk Enables monitoring and analysis of machine generated data via a web-style interface. Supported Nagios IT infrastructure monitoring and problem identification. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-5 Secured systems data. AP-6 Secured availability and reliability. AP-11 Use of COTS products. AP-12 Use of SOE systems. 10. Infrastructure Architecture 10.1 Client Platform Architecture Client Platform Architecture relates to supported hardware and software specifications in use across Flinders. ITS supports the SOE, and all desktop, laptop on the preferred hardware list and all mobile computing devices (excluding applications support for mobile devices) on the supported mobile devices list, across the University. Desktop and Laptop standards are contained in the Hardware Recommendations available from the Desktop Technology Standard (refer to Preferred Products list: http://www.flinders.edu.au/its/computers-and-software/hardware-purchasing/preferred-products.cfm For the supported mobile devices refer to https://www.flinders.edu.au/its/help-and-support/its-clientservices/tips/mobile-device-support/mobile-device-support_home.cfm The procurement of any client hardware or software not compliant with these standards must be justified to the Director ITS or delegate, and shall be authorised on a case-by-case basis by the Director ITS or delegate. Configurations non-compliant with the SOE must be authorised on a case-by-case basis by the Director ITS or delegate. Document1 19 of 31 The procurement of all IT-related items will be undertaken in conjunction with ITS. Details of procurement processes and relevant policies and procedures are available at the policies and procedures web site, refer to: https://www.flinders.edu.au/ppmanual/finance/purchasing.cfm Owner Associate Director, Client Services Architectural Principle Reference AP-1 Solutions based on business requirements / client needs. AP-3 Preference for integrated solutions. AP-6 Focus on availability and reliability of client infrastructure. AP-11 Use of COTS products. AP-16 Selection of technologies includes sustainability criteria. 10.1.1 Application and Desktop Virtualisation Application and Desktop Virtualisation provides the user with the same user experience regardless on which device (desktop, mobile) or platform (operation system) he is on. Minimising the number of supported Application and Desktop Virtualisation Systems reduces support and maintenance costs, and provides a consistent environment which can be well managed. ITS does not support Desktop Virtualisation at the moment. Element Description Application Virtualisation systems Application Virtualization transforms applications into centrally managed services that are never installed and don’t conflict with other applications Class Product Notes Supported Citrix XenApp For running Windows applications on OS X platforms. Restricted Support MS App-V For running a Windows application on a client without conflicting with other applications Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-1 Solutions based on business requirements / client needs. AP-6 Focus on availability and reliability of client infrastructure. AP-9 Use of open standard technologies and platforms. AP-11 Use of COTS products. AP-12 Use of standard platforms and software products. 10.2 Educational Technology Architecture Educational Technology Architecture is comprised of the audio-visual components that are required to facilitate various teaching and classroom scenarios. Minimum standards for Educational Technology ensure that high quality audio-visual facilities are available for all academic staff and students, in all teaching areas at all campuses. These standards may only be installed, maintained or otherwise configured by staff from the AV Systems Group, ITS. These minimum standards are applied to the following teaching spaces: Small classroom Standard classroom Teaching computer laboratory Lecture Theatre Refer to the Audio Visual Classroom Equipment Standard: http://www.flinders.edu.au/isdfiles/documents/Audio%20visual%20services/AV%20General%20Standards%20Guidelines-ver10.pdf Document1 20 of 31 Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-1 Solutions based on business requirements / client needs. AP-6 Focus on availability and reliability of client infrastructure. AP-9 Use of open standard technologies and platforms. AP-11 Use of COTS products. AP-12 Use of standard platforms and software products. 10.3 Server Technology Architecture Server Technology Architecture is comprised of the server, storage, backup, archive, and associated infrastructure which is hosted in a secure data centre facility. Server Technology Infrastructure provides the underlying platform to support applications and systems, and is required to provide high levels of reliability, redundancy, and scalability to meet the needs of the University. 10.3.1 Server Operating Systems Server Operating Systems provide the basic management and operation functions to support applications. Minimising the number of supported Server Operating Systems reduces support and maintenance costs, and provides a consistent environment which can be well managed. Element Description Server Operating systems The operating system that will be installed on servers in order to deliver services or support applications. Class Product Notes Supported RedHat Enterprise Linux 6 For Linux platforms. Restricted Support RedHat Enterprise Linux 5 For legacy Linux applications. Not Supported RedHat Enterprise Linux 4 To be phased out as soon as possible. To Be Supported Microsoft Windows Server 2012 Pilot evaluation needs to be performed and support teams trained before being deployed. Supported Microsoft Windows Server 2008R2 For all Microsoft Windows server platforms. Restricted Support Microsoft Windows Server 2003, 2008 Legacy or existing applications only; or as part of a turnkey system provided by a vendor. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-3 Preference for integrated solutions. AP-5 Security and accessibility of information. AP-6 High level of availability and reliability. AP-9 Use of open standard technologies and platforms. AP-17 Ease of access to relevant expertise. Document1 21 of 31 10.3.2 Server Hardware Vendors Element Description Server hardware The hardware platform that will run either virtualisation software or dedicated operating systems that are supported. Class Product Notes Supported Dell Systems must be certified for the supported virtualisation technologies, have redundant power supplies and cooling, have remote management capability, and be rack mountable. Supported Cisco UCS Blade Servers Not Supported Macintosh servers No longer supported by Apple. Not Supported Macintosh desktops Apple Macintosh desktops do not have sufficient redundancy to provide server capabilities. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-4 Minimise the number of vendors and suppliers. AP-5 Focus on secured systems. AP-6 Selected systems must have high level of availability and reliability. AP-12 Use of standard platforms and conform to Flinders SOE. AP-16 Focus on sustainability. 10.3.3 Virtual Server Systems Virtual Server systems enable one physical server to run multiple operating systems in a safe, reliable manner. This maximises the utilisation of resources, minimises power consumption and data centre requirements, and provides enhanced flexibility to meet business requirements. Element Description Server virtualisation Server virtualisation platforms that can run multiple instances of supported operating systems. Class Product Notes Supported VMware Current version (N) and N-1 versions are supported. Restricted Support Microsoft HyperV HyperV systems will be migrated to VMware platforms as soon as is practical. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-1 Alignment with business requirements. AP-5 Focus on secured systems and accessibility of information. AP-6 High level of availability and reliability. AP-13 Sharing of resources for delivery of applications. AP-16 Focus on sustainability with optimal use of power and resources. Document1 22 of 31 10.3.4 Storage Systems Storage systems provide the mechanism for storing all information and data that pertains to the operation of the University. This includes data for administrative, research, and teaching systems. Element Description Storage platforms The specific technologies which comprise the storage platforms for use with University applications and systems. Class Product Notes To Be Supported Cloud storage An evaluation of cloud based storage platforms will be performed in 2013. Supported Dell Compellent University-wide storage platform. Restricted Support EMC CX3-40 Previous storage platform which provides storage for most administrative systems of the University. End of Life in January 2014. Restricted Support Direct attached arrays (CORAID, Pegasus, MD3200, others) Turn-key applications may require direct attached storage, but alternatives should be found where possible. Restricted Support Dell Equilogic Platforms purchased by faculty/school which are not scalable to an enterprise capability. Restricted Support Internal storage Internal disks will not be used due to the support overheads. Exceptions will be based on specific application requirements where SAN storage is not appropriate. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-5 Security and accessibility of information. AP-6 High level of availability and reliability. AP-8 Effective management of data and data integrity. 10.3.5 Storage Protocols Storage Protocols provide the mechanism for connecting server platforms to storage systems. Element Description Storage protocols The specific technologies which enable server platforms and storage systems to communicate together. Class Product Notes To Be Supported FCoE An evaluation of Fibre Channel over Ethernet protocols will be performed in 2013. Supported Fibre Channel 4gbs, 8gbs, and 16gbs fibre channel protocols are supported by the University server and storage systems. Supported NFS Distributed file system protocol. Supported iSCSI iSCSI is supported on smaller scale storage platforms that are purchased for specific applications which cannot leverage the university-wide storage platforms. Not Supported SCSI, USB, internal Older storage protocols will be actively phased out for server platforms. Document1 23 of 31 Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-5 Security and accessibility of information. AP-6 High level of availability and reliability. 10.3.6 Backup and Archiving Systems Backup systems enable information and data that is stored on the University storage systems to be copied and protected. The University backup system is primarily based on traditional tape backup technologies which are proven and cost effective. Element Description Backup platforms The specific technologies which comprise the storage platforms for use with University applications and systems. Class Product Notes To Be Supported Archiving An evaluation of archiving systems will be performed in 2013, including cloud/hosted solutions. Supported Quantum iScalar tape libraries Main tape drive technology used for backup purposes. Supported LTO4 and LTO5 tape drives Tape drive standard which is used within the tape libraries. Supported Symantec Netbackup Vendor solution which is used to backup all supported server platforms. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-5 Security and accessibility of information. AP-6 High level of reliability. AP-16 Focus on cost effective and sustainable approach to backup and archiving. 10.4 Network Technology Architecture Network Technology Architecture is comprised of the network devices, network topology, and network protocols which provide services across the University. The network provides access to applications and services that are required by staff and students, and enables collaboration and communication across the various Flinders University locations. Flinders will minimise the number of network equipment vendors that are necessary to provide the required services to the University. 10.4.1 Switch and Router Equipment Switches and routers enable the interconnection of computers, or connection to other network devices or to other networks. Element Description Network equipment vendor Network switches and routers will be purchased from this vendor unless they cannot supply satisfactory solutions that address business requirements. Class Product Notes Supported Cisco Default network equipment vendor. Not Supported D-Link, Netgear, Netcomm To be replaced as soon as possible. Document1 24 of 31 Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-3 Preference for integrated solutions. AP-4 Minimise number of vendors. AP-5 Security and accessibility of information. AP-6 High level of availability and reliability. AP-17 Ease of access to relevant expertise. AP-18 Optimal use of infrastructure assets. 10.4.2 Wireless Access Points Wireless access points are specially configured nodes on wireless local area networks (WLANs). They enable wireless devices to connect to a wired network using Wi-Fi, or related standards. Element Description Network equipment vendor Wireless Access Points and associated equipment. Class Product Notes Supported Cisco Default network equipment vendor. Not Supported Non-Cisco equipment To be replaced as soon as possible. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-3 Preference for integrated solutions. AP-4 Minimise number of vendors. AP-5 Security and accessibility of information. AP-6 High level of availability and reliability. AP-17 Ease of access to relevant expertise. AP-18 Optimal use of infrastructure assets. 10.4.3 Network Load Balancers Network load balancers enable the balancing of network sessions like Web, email etc. over multiple connections. This spreads out the amount of bandwidth used by each local area network (LAN) user, thus increasing the total amount of bandwidth available. Element Description Network equipment vendor Network load balancers distribute network traffic evenly between other infrastructure and applications which is accessed over the network. Class Product Supported F5 Supported Citrix Netscaler Not Supported Big-IP Document1 Notes To be replaced as soon as possible. 25 of 31 Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-3 Preference for integrated solutions. AP-4 Minimise number of vendors. AP-5 Security and accessibility of information. AP-6 High level of availability and reliability. AP-17 Ease of access to relevant expertise. AP-18 Optimal use of infrastructure assets. 10.4.4 IP Telephony IP telephony provides full-featured telephone connection over the data network. Element Description Network equipment vendor IP Telephony to ensure full functionality and inter-operability between end points. Class Product Notes Supported Cisco Default network equipment vendor. Not Supported Avaya, Mitel Mitel removed from ASMS. Owner Associate Director, Infrastructure Services Architectural Principle Reference AP-3 Preference for integrated solutions. AP-4 Minimise number of vendors. AP-6 High level of availability and reliability. AP-18 Optimal use of infrastructure assets. 10.5 Printer Device Architecture 10.5.1 Printer Device Printer Device relates to the supported hardware and driver specifications in use across Flinders. ITS supports both network multifunction printing devices and standalone network-based printers, using the IP protocol with drivers compatible on Windows 2008 R2 and later printer servers. Due to complexity requirements of Flinders University, other print manufacturers have been untested with both the Client Standard Operating System (SOE) and Tier 1 Applications (Finance System). While not prohibited, explicit approval will need to come from the Director of ITS or a specified delegate Element Description Printer Device vendor Supported Printer Hardware Class Product Notes Supported Ricoh Standalone & Multifunction Supported Kyocera Standalone & Multifunction Supported Canon Multifunction Supported HP Standalone Not Supported Sharp Any model Document1 26 of 31 Not Supported Fuji Any model Not Supported Konica Minolta Any model Not Supported Xerox Any model Prohibited Hosted-based Printer Models Owner Associate Director, Client Services Architectural Principle Reference AP-1 Alignment with business requirements. AP-4 Minimise number of vendors. AP-6 High level of availability and reliability. AP-18 Optimal use of infrastructure assets. 10.5.2 Printer Driver To optimise the efficiency and retain a level of stability on the print server, it is recommended the number of drivers in the print server drive store is kept to a minimum. For this reason,. Element Description Printer Driver Printer models must be compatible with an existing or released universal print driver, capable of providing all functionality offered by the device Class Product Notes Supported PCL 5.x Printer Command Language 5 Supported PCL 6 Printer Command Language 6 Supported PostScript PostScript Level 1,2,3 Owner Associate Director, Client Services Architectural Principle Reference AP-3 Preference for integrated solutions. AP-4 Minimise number of vendors. AP-6 High level of availability and reliability. AP-18 Optimal use of infrastructure assets. Document1 27 of 31 11. Technology Advisory Groups Flinders University Technology Advisory Groups provide advice and recommendations to the Pro Vice Chancellor, Information Services in relation to the development of University-wide IT resources, services and systems. Recommendations and advice are used to guide solutions, and to resolve issues to satisfactorily meet the administrative, research, teaching and learning needs of defined users across the University. Each group listed below is an advisory group and in no way diminishes the Director ITS’s discretion to take immediate action to protect the security of the University’s computing environment. The following Technology Advisory Groups have been established: Technology Advisory Group TAG Abbreviation Infrastructure Advisory Group IAG Enterprise Applications Reference Group Scholarly Communication and Library Advisory Group EARG SCHOLAG Educational ICT Advisory Group ETAG Role IAG provides advice on the development of the University’s ICT systems and services. EARG provides advice and recommendations to the PVC (IS) on the development and acquisition of the University’s enterprise technology systems. SCHOLAG provides advice to the University on developments in scholarly information and communication and on the development, policies and operation of the Library. ETAG provides advice on policies, strategies and priorities in the provision of ICT services that provide educational outcomes. 12. Document Review and Updating The Flinders IT Standards document is both a reference and compliance document for all initiatives involving the use of ICT, and also where third parties are seeking to provide ICT related goods or services to the University. Accordingly, it is important that the document incorporates the current standards and that where changes occur in the ICT environment, the relevant sections of the document are updated and the current version posted on the ITS web site. Action Frequency Responsibility Regular review, updating, version control and posting As required Associate Director, Application Services and Associate Director, Infrastructure Services Expert advice on changes to applications, infrastructure and client services Bi-annual or as required ITS Management Team convened by one Associate Director Document review Annual ITS Management Team convened by one Associate Director Document1 28 of 31 13. Glossary ARIS Software for business process management BPEL Business Process Execution Language: a business process modelling language that is executable BPM Business Process Modeling CMS Content Management System COTS Commercial Off the Shelf Software DAS Direct Attached Storage DRP Disaster Recovery Plan Enterprise system A very high criticality Flinders system (see the Application Classification Policy for full definition) ETL Extract, Transform, Load FITS Flinders IT Architecture Standards FLO Flinders Learning Online HTTP Hyper Text Transfer Protocol: a method used to transfer or convey information on the world wide web. It is a request/response protocol between clients and servers. IDM Identity Management IP Internet Protocol IS Information Systems ISDG Information Systems Development Group ITS The IT Services Department of Flinders JIRA A J2EE web-based bug tracking and issue tracking application Key system A critical Flinders system LDAP LMS LPR/LPD Lightweight Directory Access Protocol is an Internet protocol that email and other programs use to look up information from a server. Learning Management Systems Line Printer Remote protocol / Line Printer Daemon protocol: a set of programs which provide printer spooling and network print server functionality for Unix like systems Non-Key system A non-critical Flinders system Not Supported See section 3 OID Object identifier OIM Oracle identity management Open source describes the principles and methodologies to promote open access to the production Open Source and design process for various goods, products, resources and technical conclusions or advice. The term is most commonly applied to the source code of software that is made available to the general public with either relaxed or non-existent intellectual property restrictions. PDA Personal Digital Assistant Prohibited See section 3 RDBMS Relational Database Management System Restricted Support See section 3 SAN Storage Area Networks SMS Student Management System SOA Service-Oriented Architecture: a software architecture that uses loosely coupled software services to support the requirements of business processes and software users SOE Standard Operating Environment: see section 10.1 Supported See section 3 TAG Technology Advice Group TCP or TCP/IP Transmission Control Protocol: Using TCP, applications on networked hosts can TCP create connections to one another, over which they can exchange streams of data. The protocol guarantees reliable and in-order delivery of data from sender to receiver. To be Supported Document1 See section 3 29 of 31 UML Unified Modelling Language: in the field of software development , UML is a standardised specification language for object modelling. UPS Uninterruptible power supply VOD Video on Demand Document1 30 of 31 14. Revision History Version Issue Date Editor Sections Affected Description 1.0 5/12/2012 Ray Fallu All Final draft developed following three meetings of the FITS Working Group and subsequent review of documentation, including the addition of sections relating to server and networking technology. The Working Group comprised the following ITS staff: Rob Reddecliffe, Dean Gawler, Kevin Knox, Chris Simmons, Rick Williams, Mark Materne and Gavan Conroy 1.1 18/01/2013 Ray Fallu All Document reviewed by Nicole Fishers with a number of amendments recommended. Recommendations included a change to the title of the document to reflect the emphasis on IT Architecture Standards 1.2 6/06/2013 Ray Fallu All Complete document review undertaken by Nicole Fishers, Sally Wheldrake, Rod Walker and Peter Woolley. 1.3 22/10/2013 Nicole Fishers 1, 8.1, 9.3, 9.4.5 Minor updates from review. 1.4 25/10/13 Nicole Fishers All Updates from Sally Wheldrake and Peter Woolley 1.5 29/10/13 Nicole Fishers All Minor updates from Sascha Meier Document1 31 of 31