Cellular Access Control and Charging for Mobile Operator Wireless

Cellular Access Control and Charging for Mobile
Operator Wireless Local Area Networks
H. Haverinen, J. Mikkonen and T. Takamaki, Nokia
Wei-Jen, Lin
Advanced Network Technology Lab.
Institute of Communications Engineering
National Chung Cheng University foolfish@ant.comm.ccu.edu.tw
Outline
• Introduction
• Other Solutions
• Architecture
• Authentication Protocol
• User Identity Format
• Authentication in GSM
• Authentication and Roaming
• Subscriber Identity Privacy
• Accounting and Billing
• System Implementation
• Conclusions
Introduction
• Reusing GSM and GPRS mechanisms for user authentication, access control, subscriber management, operator roaming, and billing.
• Compatible with RADIUS 、 EAP, IEEE 802.1x and IEEE 802.11i.
• WLAN service provider is a cellular operator.
• SIM-based/RADIUS-based Authentication.
• The first public WLAN solutions only provide for internet or intranet connectivity.
Other Solutions
Reusing GPRS mobility management message. The user’s active
GPRS sessions could be transferred to WLAN.
Architecture
SS7 Network IP Network
Authentication Server
(AAA Server)
RADIUS Proxy
Charging Gateway
802.11i
802.1x with EAP/SIM
Ki / IMSI
Authentication Protocol
MAP : Mobile Application Part
MTP : Message Transfer Part
SCCP : Signaling Connection Control Part
TCAP : Transaction Capabilities Application Part
AAA Network
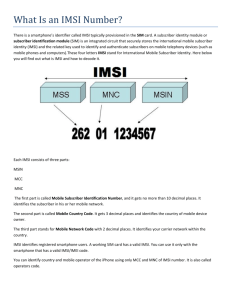
User Identity Format
Network Access Identifier (NAI) : foolfish.lin@comm.ccu
SIM-based : [Mobile Country Code][Mobile Network Code][Mobile Subscriber Identification Number]
Ki
Authentication in GSM
IMSI to E.214
AAA
Network
Authentication and Roaming
RAND
A3/A8
(nonce,Kc’,RAND) MAC’
Kc’/SRES’
(nonce,Kc,RAND)
MAC
Subscriber Identity Privacy
• GSM networks protect the privacy of the subscriber identity with temporary identities
(TMSI).
• WLAN system introduces a new type of temporary identities called pseudonyms.
• In the very first connection with an AS, the client always transmits the clear text IMSI and uses pseudonym as the username portion of the NAI in subsequent connections.
Subscriber Identity Privacy
Pseudonyms
IMSI
(Encrypted pseudonyms)
Accounting and Billing
Access
Network
Auth. Server
GTP’ proprietary / FTP
CDR : Charging Data Records
CGF : Charging Gateway Functionality
CG : Charging Gateway
BS : Billing System
GTP’ : GPRS Tunneling Protocol proprietary
System Implementation
• Nokia Operator Wireless LAN solution release 2.0
• Nokia A036 AP
– Linux OS, ARM940, Kernel 2.4.17, PoE
• AS is based on PC-Server (Compaq)
– Windows NT 4.0, RADIUS, SIM auth. Software
• 10-20 terminal auth. exchanges/sec.
– An average connection time of 30 min, 18,000-36,000 simultaneous connections.
• For redundancy and load-balancing reasons it’s recommended to have always at least two ASs in a
WLAN system.
Conclusions
• The solution is generic enough to be used on any access networks that support EAP.
• Loose coupling architecture.
• Subscriber Identity Privacy issue.