Active & Passive Fingerprinting of Microsoft Based
advertisement

Active & Passive Fingerprinting of
Microsoft based Operating Systems using
the ICMP Protocol
Ofir Arkin, Founder
The Sys-Security Group
http://www.sys-security.com
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
1
Ofir Arkin
Founder
http://www.sys-security.com
ofir@sys-security.com
Active Member
http://project.honeynet.org
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
2
RFCs are meant to be read
and followed…
Ofir Arkin, Black Hat Briefings 2000, Amsterdam
People don’t learn the
lesson
Ofir Arkin, Black Hat Windows 2k Security Conference, Las Vegas,
February 2001
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
3
Introduction
The ICMP Protocol may seem harmless at first glance. Its
goals and features were outlined in RFC 792 (and than
later cleared in RFCs 1122, 1256, 1349, 1812).
The ICMP protocol is being used:
• When a router or a destination host need to inform the source
host about errors in a datagram processing, and
• For probing the network with request & reply messages in order
to determine general characteristics about the network.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
4
Introduction
In terms of security, ICMP is one of the most
controversial protocols in the TCP/IP protocol suite.
The risks involved in implementing the ICMP protocol in
a network, regarding scanning, are the subject of this
presentation.
We will especially focus on Active and Passive
Fingerprinting of Microsoft Based Operating Systems
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
5
The ICMP Protocol Specifications
ICMP messages are sent in IP datagrams. Although ICMP uses IP as if it
were a higher-level protocol, ICMP is an internal part of IP, and must be
implemented in every IP module.
It is important to note that the ICMP protocol is used to provide
feedback about some errors (non-transient) in a datagram processing,
not to make IP reliable. Datagrams may still be undelivered without any
report of their loss. If a higher level protocol that uses IP needs
reliability he must implement it.
RFC 792 defines the IP protocol ID for ICMP to be 1. It also states that
the IP Type-of-Service field value and the Precedence Bits value should
be equal to zero. According to RFC 1812, Routers will use the value of 6
or 7 as their IP Precedence bits value with ICMP Error messages.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
6
Why?
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
7
The ICMP Protocol
0
4
8
4 bit
Header
Length
4 bit
Version
16
8-bit type of service
(TOS)=0
16-bit total length ( in bytes )
3 bit
Flags
16-bit identification
8-bit time to live
( TTL )
31
8-bit protocol=1
(ICMP)
13-bit Fragment Offset
16-bit header checksum
20
bytes
32-bit source IP address
32-bit destination IP address
Options ( if any )
Type
IP Data
Field
Code
Checksum
4 bytes
ICMP data (depending on the type of message)
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
8
Special Conditions with ICMP
For transient error messages no ICMP error message should be sent. For the
following conditions the ICMP protocol has strict rules of inner working which are
defined in RFC 792:
No ICMP Error messages are sent in response to ICMP Error messages to avoid
infinite repetition.
• For fragmented IP datagrams ICMP messages are only sent for errors on fragment
zero (the first fragment).
• ICMP Error messages are never sent in response to a datagram that is
to a broadcast or a multicast address.
destined
• ICMP Error messages are never sent in response to a datagram sent
as a link layer broadcast.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
9
Special Conditions with ICMP
• ICMP Error messages are never sent in response to a datagram whose
source address does not represents a unique host – the source IP
address cannot be zero, a loopback address, a broadcast address or a
multicast address.
• ICMP Error messages are never sent in response to an IGMP message
of any kind.
• When an ICMP message of unknown type is received, it must be
silently discarded.
• Routers will almost always generate ICMP messages but when it
comes to a destination host(s), the number of ICMP messages
generated is implementation dependent.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
10
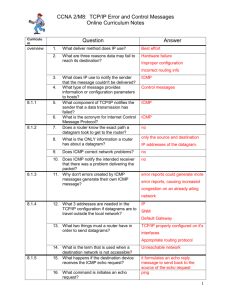
ICMP Messages
A number code, also known as the “message type”, is assigned to each
ICMP message; it specifies the type of the message.
Another number code represents a “code” for the specified ICMP type. It
acts as a sub-type, and its interpretation is dependent upon the
message type.
The ICMP protocol has two types of operations, therefore its messages
are also divided to two:
• ICMP Error Messages
• ICMP Query Messages
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
11
ICMP Messages
The Internet Assigned Numbers Authority (IANA) has a list defining the ICMP
message types that are currently registered. It also lists the RFC that defines
the ICMP message. The list is available at:
http://www.isi.edu/in-notes/iana/assignments/icmp-parameters
Error Messages
Query Messages
Destination Unreachable
Echo
Source Quench
Time Stamp
Redirect
Information
Time Exceeded
Address Mask
Parameter Problem
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
12
Active OS Fingerprinting
Finger Printing is the art of Operating System Detection.
A malicious computer attacker needs a few pieces of information before
lunching an attack. First, a target, a host detected using a host
detection method. The next piece of information would be the services
that are running on that host. This would be done with one of the Port
Scanning methods. The last piece of information would be the operating
system used by the host.
The information would allow the malicious computer attacker to identify
if the targeted host is vulnerable to a certain exploit aimed at a certain
service version running on a certain operating system.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
13
The Usage of ICMP in The Active Operating
System Fingerprinting Process
What makes the Active Fingerprinting methods, which
use the ICMP protocol unique, comparing to other
Active Fingerprinting methods?
As we will learn, using Active Fingerprinting with ICMP requires less
traffic initiation from the prober to a target host.
With some methods only one datagram is required to determine the
underlying operating system.
The methods presented were discovered during my ICMP
research.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
14
Active OS Fingerprinting
We can group the Active Fingerprinting methods that are based upon
the ICMP protocol into the following groups, which are based upon the
ICMP traffic used:
• Regular ICMP Query Messages
• Crafted ICMP Query Messages
• ICMP Error Messages
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
15
The “Who answers what?” approach
The question “Which operating system answers for what kind of ICMP Query
messages?“ help us identify certain groups of operating systems.
For example, LINUX and *BSD based operating systems with a default
configuration answer for ICMP Echo requests and for ICMP Timestamp
Requests. Until Microsoft Windows 2000 family of operating systems has been
released it was a unique combination for these two groups of operating
systems. Since the Microsoft Windows 2000 operating system family mimics
the same behavior (yes mimic), it is no longer feasible to make this particular
distinction.
Microsoft might have been thinking that this way of behavior might hide
Microsoft windows 2000 machines in the haze. As we will see with the
examples given in this presentation – I hope the guys are taking notes.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
16
The “Who answers what?” approach
Other data we might use is “Which operating systems answers for
queries aimed at the broadcast / network address of the network they
reside on?”.
For Microsoft based operating systems this information is not useful,
since Microsoft based operating system machines will not answer for any
type of ICMP message aimed at the broadcast address of the network
these machines reside on.
Using tables that map the “who answers what?” approach we can map
Ultrix, Linux, Sun Solaris, and group HPUX & AIX based machines with
some ICMP Query messages combinations.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
17
The “Who answers what?” approach
ICMP Timestamp Request aimed at the Broadcast
Address of a Network
1
Reply
No Reply
Solaris
HP-UX
LINUX Kernel 2.2.14
Other OS's
ICMP Information Request aimed at the Broadcast
Address of a Network
2
Reply
HP-UX
No Reply
Solaris
LINUX Kernel 2.2.14
ICMP Address Mask Request aimed at Specific IPs
3
Reply
Solaris
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
No Reply
LINUX Kernel 2.2.14
18
The “Who answers what?” approach
Is it a sin not to answer an ICMP Query request aimed at the broadcast
address of a network?
No.
This is not an abnormal behavior as RFC 1122 states that if we send an
ICMP ECHO request to an IP Broadcast or IP Multicast addresses it may
be silently discarded by a host.
We do not have a misbehavior … Yet.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
19
IP Time-to-Live Field
The sender sets the time to live field to a value that represents the
maximum time the datagram is allowed to travel on the Internet.
The field value is decreased at each point that the Internet header is
being processed. RFC 791 states that this field decreasement reflects
the time spent processing the datagram. The field value is measured in
units of seconds. The RFC also states that the maximum time to live
value can be set to 255 seconds, which equals 4.25 minutes. The
datagram must be discarded if this field value equals zero - before
reaching its destination.
Relating to this field as a measure to assess time is a bit misleading.
Some routers may process the datagram faster than a second, and
some may process the datagram longer than a second.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
20
IP Time-to-Live Field
The real intention is to have an upper bound to the datagrams lifetime,
so infinite loops of undelivered datagrams will not jam the Internet.
Having a bound to the datagram’s lifetime help us to prevent old
duplicates to arrive after a certain time elapsed. So when we retransmit
a piece of information which was not previously delivered we can be
assured that the older duplicate is already discarded and will not
interfere with the process.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
21
IP Time-to-Live Field Value
with ICMP
The IP TTL field value with ICMP has two separate values: one for ICMP
query messages and one for ICMP query replies.
The TTL field value helps us identify certain operating systems and
groups of operating systems. It also provides us with the simplest
means to add another check criteria when we are querying other host(s)
or listening to traffic (sniffing).
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
22
IP Time-to-Live Field Value
with ICMP
ICMP Query Replies
We can use the IP TTL field value with the ICMP Query Reply datagrams to
identify certain groups of operating systems. The method discussed in this section
is a very simple one. We send an ICMP Query request message to a host. If we
receive a reply, we would be looking at the IP TTL field value in the ICMP query
reply.
The IP Time-To-Live field value received will not be the original value assigned to
this field. The reason is that each router along the path from the targeted host to
the prober decreased this field value by one.
We can use two ways to approach this. The first one is looking at the IP TTL field
values that are usually used by operating systems and networking devices. They
are 255, 128, 64 and 32. We will use the most close to value, as the original value
assigned to the IP TTL field.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
23
IP Time-to-Live Field Value
with ICMP
ICMP Query Replies
The second approach is less accurate than the first one.
Since we already queried the targeted host, querying it again will not be that
harmful (well we hope at least). We can use the traceroute program (tracert in
Windows 2000) in order to reveal the number of hops between our system to the
target. Adding the number we calculated to the IP TTL field value should give us a
good guess about the original IP TTL value assigned to this field.
Why this is only a good guess? Because the routes taken from the target to our
host and from our host to the target may be different routes.
Again, we will have a number close enough to one of the common values used to
make a good guess about the original IP TTL field value.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
24
IP Time-to-Live Field Value
with ICMP
ICMP Query Replies
C:\>ping -n 1 www.sys-security.com
Pinging www.sys-security.com [216.230.199.48] with 32 bytes of data:
Reply from 216.230.199.48: bytes=32 time=481ms TTL=238
Ping statistics for 216.230.199.48:
Packets: Sent = 1, Received = 1, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 481ms, Maximum =
481ms, Average =
481ms
C:\>
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
25
IP Time-to-Live Field Value
with ICMP
ICMP Query Replies
C:\>tracert -h 16 www.sys-security.com
Tracing route to www.sys-security.com [216.230.199.48]
over a maximum of 16 hops:
1
100 ms
100 ms
120 ms
Haifa-mng-1 [213.8.12.7]
2
90 ms
90 ms
90 ms
3
120 ms
151 ms
200 ms
213.8.8.5
4
441 ms
450 ms
451 ms
500.Serial3-5.GW3.NYC6.ALTER.NET [157.130.253.69]
5
440 ms
451 ms
451 ms
521.ATM2-0.XR2.NYC4.ALTER.NET [152.63.24.38]
6
912 ms
460 ms
461 ms
188.ATM3-0.TR2.NYC1.ALTER.NET [146.188.179.38]
7
471 ms
480 ms
471 ms
104.at-5-1-0.TR2.CHI4.ALTER.NET [146.188.136.153]
8
470 ms
471 ms
471 ms
198.at-2-0-0.XR2.CHI2.ALTER.NET [152.63.64.229]
9
480 ms
471 ms
471 ms
0.so-2-1-0.XL2.CHI2.ALTER.NET [152.63.67.133]
10
471 ms
471 ms
470 ms
POS6/0.GW2.CHI2.ALTER.NET [152.63.64.145]
11
471 ms
481 ms
470 ms
siteprotect.customer.alter.net [157.130.119.50]
12
481 ms
490 ms
481 ms
216.230.199.48
ge037.herndon1.us.telia.net [205.164.141.1]
Trace complete.
C:\>
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
26
IP Time-to-Live Field Value
with ICMP
ICMP Query Replies
Operating System
IP TTL on ICMP Query Replies
LINUX Kernel 2.2.x
255
Kernel 2.0.x
64
*BSD, Solaris 2.x, HPUX, Irix, AIX, Ultrix, OpenVMS
255
Windows 95
32
Windows 98, 98 SE
128
Windows ME
128
Windows NT 4 WRKS SP 3
128
Windows NT 4 WRKS SP 4+
128
Windows 2000 Family
128
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
27
IP Time-to-Live Field Value
with ICMP
ICMP Query Replies
If we look at the ICMP Echo replies IP TTL field values than we can
identify few patterns:
• UNIX and UNIX-like operating systems use 255 as their IP TTL field
value with ICMP query replies.
• Compaq Tru64 v5.0 and LINUX 2.0.x are the exception, using 64 as its
IP TTL field value with ICMP query replies.
• Microsoft Windows operating system based machines are using the
value of 128.
• Microsoft Windows 95 is the only Microsoft operating system to use 32
as its IP TTL field value with ICMP query messages, making it unique
among all other operating systems as well.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
28
IP Time-to-Live Field Value
with ICMP
ICMP Query Requests
The examination of the IP TTL field value is not limited to ICMP Query
replies only. We can learn a lot from the ICMP requests aimed at our
host(s) as well.
The IP Time-To-Live field value received will not be the original value
assigned to this field. The reason is that each router along the path from
the targeted host to the prober decreased this field value by one.
We will examine the IP TTL field values that are usually used by
operating systems and networking devices. They are 255, 128, 64 and
32. We will use the most close to value, as the original value assigned to
the IP TTL field.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
29
IP Time-to-Live Field Value
with ICMP
ICMP Query Requests
Using techniques which will trace the querying target path until its
gateway may not work, and may alert the prober that we are aware of
his activities.
This method is a Passive Fingerprinting method.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
30
IP Time-to-Live Field Value
with ICMP
ICMP Query Requests
Operating System
IP TTL with ICMP Query messages
Linux 2.4.x, 2.2.x, 2.0.x
64
*BSD, Solaris 2.x, HPUX
255
Windows 95
32
Windows 98
32
Windows 98 SE
32
Windows ME
32
Windows NT 4 WRKS SP 3
32
Windows NT 4 WRKS SP 4+
32
Windows 2000 Family
128
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
31
IP Time-to-Live Field Value
with ICMP
ICMP Query Requests
The ICMP Query message type used was ICMP Echo request, which is
common on all operating systems tested using the ping utility.
• LINUX Kernel 2.0.x, 2.2.x & 2.4.x use 64 as their IP TTL Field Value with
ICMP Echo Requests.
• FreeBSD 4.1, 4.0, 3.4; Sun Solaris 2.5.1, 2.6, 2.7, 2.8; OpenBSD 2.6, 2.7,
NetBSD and HP UX 10.20 use 255 as their IP TTL field value with ICMP Echo
requests.
• Windows 95/98/98SE/ME/NT4 WRKS SP3,SP4,SP6a/NT4 Server SP4 - all
use 32 as their IP TTL field value with ICMP Echo requests.
• Microsoft Window 2000 uses 128 as its IP TTL Field Value with ICMP
Echo requests.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
32
IP Time-to-Live Field Value
with ICMP
Correlating the Information
Operating System
IP TTL value in the ECHO
Requests
IP TTL value in the ECHO
Replies
Microsoft Windows
Family
32
128
*BSD and Solaris
255
255
LINUX Kernel 2.2.x
and 2.4.x
64
255
LINUX Kernel 2.0.x
64
64
Microsoft Windows
2000
128
128
Microsoft Windows
95
33
32
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
33
Playing with the TOS Field
0
1
Precedence
2
3
4
5
6
TOS
7
MBZ
The Type of Service Byte
The “Precedence field”, which is 3-bit long, is intended to prioritize the
IP Datagram. It has eight levels of prioritization.
The second field, 4 bits long, is the “Type-of-Service” field. It is intended
to describe how the network should make tradeoffs between
throughput, delay, reliability, and cost in routing an IP Datagram.
The last field, the “MBZ” (must be zero), is unused and must be zero.
Routers and hosts ignore this last field. This field is 1 bit long.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
34
Precedence Bits Echoing
The precedence bits behavior is a problem. RFC 1122, which defines the
requirements for Internet Hosts, does not outline the way to handle the
Precedence Bits with ICMP. The RFC only statement about the
Precedence Bits is:
“The Precedence field is intended for Department of Defense
applications of the Internet protocols. The use of non-zero values in this
field is outside the scope of this document and the IP standard
specification. Vendors should consult the Defense Communication
Agency (DCA) for guidance on the IP Precedence field and its
implications for other protocol layers. However, vendors should note
that the use of precedence will most likely require that its value be
passed between protocol layers in just the same way as the TOS field is
passed“.
This does not give us something to work with.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
35
Precedence Bits Echoing
RFC 1812, Requirements for IP version 4 routers state that: “An ICMP
reply message MUST have its IP Precedence field set to the value as the
IP Precedence field in the ICMP request that provoked the reply”.
Echoing back the Precedence field value has its logic, because the TOS
field should be echoed back with an ICMP Query replies, and both the
Precedence field and the TOS field were to dictate very explicit types of
behavior with certain types of data.
As you can understand we do not have a clear ruling about this issue. I
was thinking it might be a ground for an operating system fingerprinting
method…
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
36
Precedence Bits Echoing
Most operating systems I have checked will behave as the next
behavioral example with AIX 4.3. With this example an ICMP Echo
request is sent which carries a value for the TOS field:
[root@godfather precedence_echo]# /usr/local/bin/sing -c 5 -TOS 128
y.y.y.y
SINGing to y.y.y.y (y.y.y.y): 16 data bytes
16 bytes from y.y.y.y: seq=0 ttl=239 TOS=128 time=5896.472 ms
...
--- y.y.y.y sing statistics --5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 5842.726/6011.057/6261.997 ms
[root@godfather precedence_echo]#
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
37
Precedence Bits Echoing
The Host queried is using the value used for the ICMP Echo Request
with its ICMP Echo Reply.
Some operating systems are the exception. The next example is with
Microsoft Windows 2000. The same ICMP Echo Request was sent.
[root@godfather precedence_echo]# /usr/local/bin/sing -c 5 -TOS 128
y.y.y.y
SINGing to y.y.y.y (y.y.y.y): 16 data bytes
16 bytes from y.y.y.y: seq=0 ttl=111 TOS=0 time=6261.043 ms
...
--- y.y.y.y sing statistics --5 packets transmitted, 4 packets received, 20% packet loss
round-trip min/avg/max = 6261.043/6384.440/6572.675 ms
[root@godfather precedence_echo]#
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
38
Precedence Bits Echoing
The ICMP Echo Reply will not use the value assigned to the Precedence
Bits with the ICMP Echo Request with Microsoft Windows 2000 as the
answering operating system.
Which operating systems share this behavioral pattern?
Microsoft Windows 2000 Family, and ULTRIX.
Differentiating between Microsoft Windows 2000 and Ultrix is easily
achieved if we examine the IP TTL field value. With ULTRIX the value
assigned to the ICMP Echo reply will be 255, with Microsoft Windows
2000 it will be 128.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
39
Precedence Bits Echoing
Changed Pattern with other ICMP Query Message Types
We can identify change of pattern with OpenVMS, Windows 98, 98SE, and
ME. With ICMP Echo replies they all would echo back the TOS field value,
but with ICMP Timestamp replies they will change the behavior and send
back 0x000. Since OpenVMS use 255 as its IP TTL field value, and the
Microsoft Windows based machines use 128, we can differentiate between
them and isolate OpenVMS, and the Microsoft based OSs.
Further distinction between the Microsoft operating systems can be
achieved if we will query them with ICMP Address Mask request, which only
Microsoft Windows 98/98SE will answer for. The Microsoft Windows ME will
not reply, enabling us to identify it.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
40
Precedence Bits Echoing
Changed Pattern with other ICMP Query Message Types
ICMP Echo Request
Precedence Bits !=0
1
Reply with
Precedence
Bits !=0
Reply with
Precedence
Bits =0
Windows 2000 Family
Ultrix
Other OS's
2
ICMP Timestamp Request
Precedence Bits !=0
Reply with
Precedence
Bits !=0
Other OS's
Reply with
Precedence
Bits =0
TTL=255
TTL=128
Ultrix
Windows 2000 Family
Windows 98/98SE/ME
OpenVMS
ULTRIX (identified already)
Microsoft Windows 2000 Family
(Identified Already)
TTL=255
OpenVMS
TTL=128
Windows 98/98SE/ME
3
ICMP Address Mask Request
No Reply
Windows ME
Reply
Windows 98/98SE
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
41
TOSing OSs out of the Window
The use of the Type-of-Service field with the Internet Control Message Protocol
RFC 1349 also define the usage of the Type-of-Service field with the
ICMP messages. It distinguishes between ICMP error messages
(Destination Unreachable, Source Quench, Redirect, Time Exceeded, and
Parameter Problem), ICMP query messages (Echo, Router Solicitation,
Timestamp, Information request, Address Mask request) and ICMP reply
messages (Echo reply, Router Advertisement, Timestamp reply,
Information reply, Address Mask reply).
The RFC defines simple rules to follow.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
42
TOSing OSs out of the Window
The use of the Type-of-Service field with the Internet Control Message Protocol
• An ICMP error message is always sent with the default TOS (0x00)
• An ICMP request message may be sent with any value in the TOS
field. “A mechanism to allow the user to specify the TOS value to be
used would be a useful feature in many applications that generate
ICMP request messages”.
• The RFC further specify that although ICMP request messages are
normally sent with the default TOS, there are sometimes good
reasons why they would be sent with some other TOS value.
• An ICMP reply message is sent with the same value in the TOS field as
was used in the corresponding ICMP request message.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
43
TOSing OSs out of the Window
The use of the Type-of-Service field with the Internet Control Message Protocol
Using this logic I have decided to check if certain operating systems
react correctly to an ICMP Query messages with a Type-of-Service field
value, which is different than the default (0x00).
The check out was produced with all ICMP query message types sent
with a Type-of-Service field set to a known value, than set to an
unknown value (the terms known and unknown are used here because I
was not experimenting with non-legit values, and since any value may
be sent inside this field).
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
44
TOSing OSs out of the Window
The use of the Type-of-Service field with the Internet Control Message Protocol
The following example is an ICMP Echo request sent to my FreeBSD 4.0
machine with the TOS field value set to 8 hex [which is a legit TOS
value]. The tool used was SING:
[root@godfather bin]# ./sing -echo -TOS 8 IP_Address
SINGing to IP_Address (IP_Address): 16 data bytes
16 bytes from IP_Address: icmp_seq=2 ttl=243 TOS=8 time=260.043 ms
16 bytes from IP_Address: icmp_seq=3 ttl=243 TOS=8 time=180.011 ms
16 bytes from IP_Address: icmp_seq=4 ttl=243 TOS=8 time=240.240 ms
16 bytes from IP_Address: icmp_seq=5 ttl=243 TOS=8 time=260.037 ms
16 bytes from IP_Address: icmp_seq=6 ttl=243 TOS=8 time=290.033 ms
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
45
TOSing OSs out of the Window
The use of the Type-of-Service field with the Internet Control Message Protocol
This is the second test I have produced, sending ICMP Echo request
with the Type-of-Service field value set to 10 Hex [a value that is not a
known Type-of-Service value]:
[root@godfather bin]# ./sing -echo -TOS 10 IP_Address
SINGing to IP_Address (IP_Address): 16 data bytes
16 bytes from IP_Address: icmp_seq=0 ttl=243 TOS=10 time=197.933 ms
16 bytes from IP_Address: icmp_seq=1 ttl=243 TOS=10 time=340.048 ms
16 bytes from IP_Address: icmp_seq=2 ttl=243 TOS=10 time=250.025 ms
16 bytes from IP_Address: icmp_seq=3 ttl=243 TOS=10 time=230.019 ms
16 bytes from IP_Address: icmp_seq=4 ttl=243 TOS=10 time=270.017 ms
16 bytes from IP_Address: icmp_seq=5 ttl=243 TOS=10 time=270.017 ms
16 bytes from IP_Address: icmp_seq=6 ttl=243 TOS=10 time=260.021 ms
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
46
TOSing OSs out of the Window
The use of the Type-of-Service field with the Internet Control Message Protocol
What is the Microsoft Windows 2000 Behavior with non default TOS
values within ICMP Echo Requests (Similar with Ultrix & Novell
Netware)?
[root@godfather bin]# ./sing -echo -TOS 8 Host_Address
SINGing to Host_Address (IP_Address): 16 data bytes
16 bytes from IP_Address: icmp_seq=0 ttl=113 TOS=0 time=278.813 ms
16 bytes from IP_Address: icmp_seq=1 ttl=113 TOS=0 time=239.935 ms
16 bytes from IP_Address: icmp_seq=2 ttl=113 TOS=0 time=249.937 ms
...
--- Host_Address sing statistics --5 packets transmitted, 5 packets received, 0% packet loss
round-trip min/avg/max = 229.962/249.720/278.813 ms
[root@godfather bin]#
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
47
TOSing OSs out of the Window
The use of the Type-of-Service field with the Internet Control Message Protocol
Other ICMP query message types help us to identify a unique group of
Microsoft operating systems. As a rule all operating systems except the named
Microsoft windows operating systems here, maintain a single behavior
regarding the Type-of-Service field. All would maintain the same values with
different types of ICMP requests.
We have the following Microsoft operating systems zero out (0x00) the Typeof-Service field with the replies for ICMP Timestamp requests: Microsoft
Windows 98/98SE/ME. Microsoft Windows 2000 machines would zero out the
TOS field with ICMP Timestamp replies as well.
This means that Microsoft Windows 98/98SE/ME would not zero out the Typeof-Service field value with ICMP Echo requests but will do so with ICMP
Timestamp requests.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
48
TOSing OSs out of the Window
ICMP Echo Request
TOS !=0
1
Reply with
TOS!=0
Other OS's
3
Reply with
TOS=0
Windows 2000 Family
Ultrix
Novell Netware
ICMP Timestamp Request
TOS!=0
TTL=255
Reply with
TOS!=0
TTL=128
Reply with
TOS=0
Ultrix
Other OS's
Windows 98/98SE/ME
Windows 2000 Family
Novell Netware
2
ICMP Timestamp Request
No Reply
Novell Netware
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
Reply
Windows 2000 Family
49
Using the TOS byte‘s Unused Bit
RFC 1349 states that the last field of the TOS byte, the “MBZ” (must be
zero), is unused and must be zero. The RFC also states that routers and
hosts ignore the value of this bit [remember this for later].
This is the only statement about the unused bit in the TOS Byte in the
RFCs. The RFC states: “The originator of a datagram sets this field to
Zero“.
Obviously it was meant that this field would be always zero. But what
will happen if we would set this bit with our ICMP Echo Requests? Will
this bit be zero out on reply or will it be echoed back?
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
50
Using the TOS byte‘s Unused Bit
The next example is with an ICMP Echo Request sent with the TOS bit in
the TOS Byte set, targeting a FreeBSD 4.1.1 machine:
[root@godfather /root]# /usr/local/bin/sing
SINGing to y.y.y.y (y.y.y.y): 16 data bytes
-c 2 -TOS 1 y.y.y.y
16 bytes from y.y.y.y: seq=0 ttl=233 TOS=1 time=330.461 ms
16 bytes from y.y.y.y: seq=1 ttl=233 TOS=1 time=723.300 ms
--- y.y.y.y sing statistics --2 packets transmitted, 2 packets received, 0% packet loss round-trip
min/avg/max = 330.461/526.880/723.300 ms
[root@godfather /root]#
Echoing back the Unused bit in the TOS Byte represents the behavior of
most of the operating systems I have checked this method against.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
51
Using the TOS byte‘s Unused Bit
Which operating systems are the exceptions?
The next example is with Microsoft Windows 2000 as the targeted
machine:
[root@godfather precedence_echo]# /usr/local/bin/sing -c 2 -TOS 1
y.y.y.y
SINGing to y.y.y.y (y.y.y.y): 16 data bytes
16 bytes from y.y.y.y: seq=0 ttl=111 TOS=0 time=299.188 ms
16 bytes from y.y.y.y: seq=1 ttl=111 TOS=0 time=280.321 ms
--- y.y.y.y sing statistics --2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 280.321/289.755/299.188 ms
[root@godfather precedence_echo]#
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
52
Using the TOS byte‘s Unused Bit
Another OS that behaves the same is ULTRIX:
[root@godfather precedence_echo]# /usr/local/bin/sing -c 2 -TOS 1
y.y.y.y
SINGing to y.y.y.y (y.y.y.y): 16 data bytes
16 bytes from y.y.y.y: seq=0 ttl=237 TOS=0 time=371.776 ms
--- y.y.y.y sing statistics --2 packets transmitted, 1 packets received, 50% packet loss
round-trip min/avg/max = 371.776/371.776/371.776 ms
[root@godfather precedence_echo]#
We will use, again, the IP TTL field value to differentiate between the
two operating systems.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
53
Using the TOS byte‘s Unused Bit
ICMP Echo Request
Unused Bit =1
1
Reply with
Unused Bit !=0
Reply with
Unused Bit =0
Windows 2000 Family
Ultrix
Other OS's
2
ICMP Timestamp Request
Unused Bit =1
Reply with
Unused Bit
=0
Reply with
Unused Bit !=0
Other OS's
TTL=255
TTL=128
Ultrix
Windows 2000 Family
Windows 98/98SE/ME
OpenVMS
ULTRIX (Identified Already)
Windows 2000 Family (Identified
Already)
TTL=255
OpenVMS
TTL=128
Windows 98/98SE/ME
3
ICMP Address Mask Request
No Reply
Windows ME
Reply
Windows 98/98SE
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
54
Using the TOS byte
Why This Works With Microsoft Windows 2000?
HKEY_LOCAL_MACINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parametrs
DefaultTOSValue
Key: Tcpip\Parameters
Value Type: REG_DWORD – Number
Valid Range: 0-255
Default: 0
This parameter value can be overwritten by a program using the option IP_TOS
(IPPROTO_IP level) as long as DisableUserTosSetting is not set (default is 1 –
not to allow the TOS value to be modified by a program), or by enabling the
QoS policy on the network.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
55
The DF Bit Echoing
Some operating systems, when receiving an ICMP Query message with
the DF bit set, would set the DF bit with their replies as well. Sometimes
it would be in contrast with their regular behavior, which would be not
setting the DF Bit in their replies for a regular query that comes with the
DF bit not set.
This method give us interesting results with all ICMP Query messages
and their replies.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
56
The DF Bit Echoing
DF Bit Echoing with ICMP Echo Request
1
Echo the DF Bit
Do Not Echo the DF Bit
Other OSs
LINUX based on Kernel 2.2.x, 2.4x
ULTRIX
Novell Netware
DF BIt Echoing with ICMP Address Mask Request
2
Echo the DF Bit
SUN Solaris
OpenVMS
Do Not Echo the DF Bit
Based upon the TTL Field
Windows 98/98SE
ULTRIX
DF BIt Echoing with ICMP Time Stamp Request
3
Do Not Echo the DF Bit
Echo the DF Bit
Other OSs
LINUX based on Kernel 2.2.x, 2.4.x
Microsoft Windows 98/98SE
Microsoft Windows ME
Microsoft Windows 2000 Family
ULTRIX
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
57
Using Code field values different than zero within
ICMP ECHO requests
The Ultimate “Who is a Windows Based Machine?” Test
In the next example I have sent an ICMP Echo Request with the code
field value set to 26 hex instead of 0, to a LINUX machine running with
Kernel 2.2.14.
00:21:05.238649 ppp0 > x.x.x.x > y.y.y.y: icmp: echo request (ttl
255, id 13170)
4500 0024 3372 0000 ff01 08d3 xxxx xxxx
yyyy yyyy 0826 af13 2904 0000 41e4 c339
17a4 0300
00:21:05.485617 ppp0 < y.y.y.y > x.x.x.x: icmp: echo reply (ttl 240,
id 2322)
4500 0024 0912 0000 f001 4233 yyyy yyyy
xxxx xxxx 0026 b713 2904 0000 41e4 c339
17a4 0300
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
58
Using Code field values different than zero within
ICMP ECHO requests
The Ultimate “Who is a Windows Based Machine?” Test
I have checked the behavior of my Microsoft Windows 2000 Professional
box. I have sent the same ICMP ECHO Request message to the
Microsoft Windows box:
10:03:33.860212 eth0 > localhost.localdomain > 192.168.1.1: icmp: echo request
4500 0020 3372 0000 fe01 0614 c0a8 0105
c0a8 0101 0826 d618 6102 f658 0183 c8e2
10:03:33.860689 eth0 < 192.168.1.1 > localhost.localdomain: icmp: echo reply
4500 0020 2010 0000 8001 9776 c0a8 0101
c0a8 0105 0000 de3e 6102 f658 0183 c8e2
0000 0000 0000 0000 0000 0000 0000
Microsoft Windows 4.0 Server SP4, Microsoft Windows NT 4.0
Workstation SP 6a, Microsoft Windows NT 4.0 Workstation SP3,
Microsoft Windows 95 / 98 / 98 SE / ME have produced the same
behavior as the Microsoft Windows 2000 Professional (Server &
Advanced Server).
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
59
Using Code field values different than zero within
ICMP Timestamp requests
The Non-Answering Operating Systems
ICMP Timestamp Request
1
Reply
No Reply
Windows 95
Windows NT 4 WRKS SP6a
Other OS's
ICMP Timestamp Request with CODE!=0
2
Reply
Other OS's
No Reply
Windows 98
Windows 98 SE
Windows ME
Windows 2000 Proffesional
Windows 2000 Server
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
60
DF Bit Echoing with ICMP Error Messages
Offending Packet with DF Bit Set
(data portion set to 70 bytes, for example)
1
Reply - Error
Message not
Echoing the DF Bit
Reply - Error
Message Echoing
the DF Bit
LINUX based on Kernel 2.2.x, 2.4x
ULTRIX
Novell Netware
HPUX
Windows 98/98SE/ME
Microsoft Windows NT4 Server,
SP6a
Microsoft Windows 2000 Family
Precedence
Bits value
equal 0xc0
LINUX Kernel based 2.2.x, 2.4x
Other OSs
64 bytes of the
offending packet's
data portion are
echoed back
Wrong IP ID
IP Header Checksum is zero
Original Checksum is zero
Novell Netware
Windows 98/98SE/ME
Microsoft Windows NT4 Server,
SP6a
Microsoft Windows 2000 Family
ULTRIX
HPUX
2
Offending Packet that will elicit ICMP Time Exceeded
Error Message
Reply with
Echoed IP TTL
field !=0
Windows 98/98SE/ME
Microsoft Windows NT4 Server, SP6a
Microsoft Windows 2000 Family
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
Reply with Echoed
IP TTL Field =0
Novell Netware
61
The usage of ICMP in the Passive Operating System
Fingerprinting Process
Passive Fingerprinting is a technique used to map a targeted network (and
networks and hosts communicating with it) using sniffed information
(exchanged network traffic) from that network.
Different operating systems use different implementations of the TCP/IP
stack. We can identify differences between those TCP/IP stack
implementations. Therefore differentiate between the different operating
systems using those TCP/IP stack implementations differences.
Based on the sniffed information and those differences we can identify the
various operating systems used on the sniffed network. We can also identify
some operating systems used on the network(s) and host(s) communicating
with our targeted network. We can also identify the various services available
on those host(s).
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
62
The usage of ICMP in the Passive Operating System
Fingerprinting Process
Which operating system answers for what kind of ICMP Query
messages?
Which operating system answers for special/crafted ICMP Queries and
how?
Which operating system produces what sort of ICMP Error messages?
An Analysis of ICMP Error Messages
An Analysis of ICMP Query Messages
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
63
Analysis of ICMP Query messages
The only ICMP query message type, which is implemented with all
operating systems, is the ICMP Echo request. RFC 1122 states that
every host should implement an end-user-accessible application
interface for sending ICMP Echo request query message to other hosts.
The “ping” utility is using this implementation on various operating
systems.
Since not all ICMP Query request message types are implemented on
the various operating systems it leaves us only with ICMP Echo requests
to be examined closely.
Please note: “ping” might use its own default values for several fields
within the ICMP Echo request datagram, and not the Operating
System’s.
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
64
Analysis of ICMP Query messages
The IP Portion
The TOS Byte (Precedence Bits, TOS Bits, Unused)
IP Identification
The DF Bit
The Unused Bit
IP TTL
IP Options
The ICMP Portion
ICMP Identification Number
ICMP Sequence Number
ICMP Data field (Payload)
Offset from ICMP Header
Content
Size
ICMP Echo Request Total Size
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
65
Analysis of ICMP Query messages
Linux ICMP Echo Request with “ping”:
[root@godfather sbin]# ping -c 2 y.y.y.y
PING y.y.y.y (y.y.y.y) from x.x.x.x : 56(84) bytes of data.
64 bytes from hostname (y.y.y.y): icmp_seq=0 ttl=255 time=0.1 ms
64 bytes from hostname (y.y.y.y): icmp_seq=1 ttl=255 time=0.1 ms
--- y.y.y.y ping statistics --2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 0.1/0.1/0.1 ms
[root@godfather sbin]#
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
66
Analysis of ICMP Query messages
Linux ICMP Echo Request (1) with “ping”:
08/08-11:59:55.336240 x.x.x.x -> y.y.y.y
ICMP TTL:64 TOS:0x0 ID:383
ID:15875
Seq:0
ECHO
0B CC 8F 39 3D 21 05 00 08 09 0A 0B 0C 0D 0E 0F
...9=!..........
10 11 12 13 14 15 16 17 18 19 1A 1B 1C 1D 1E 1F
................
20 21 22 23 24 25 26 27 28 29 2A 2B 2C 2D 2E 2F
!"#$%&'()*+,-./
30 31 32 33 34 35 36 37
01234567
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
67
Analysis of ICMP Query messages
Linux ICMP Echo Request (2) with “ping”:
08/08-11:59:56.337752 x.x.x.x -> y.y.y.y
ICMP TTL:64 TOS:0x0 ID:386
ID:15875
Seq:256
ECHO
0C CC 8F 39 3B 27 05 00 08 09 0A 0B 0C 0D 0E 0F
...9;'..........
10 11 12 13 14 15 16 17 18 19 1A 1B 1C 1D 1E 1F
................
20 21 22 23 24 25 26 27 28 29 2A 2B 2C 2D 2E 2F
!"#$%&'()*+,-./
30 31 32 33 34 35 36 37
01234567
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
68
Analysis of ICMP Query messages
Microsoft Windows 2000 Server ICMP Echo Request (1):
C:\>ping 192.168.1.15
Pinging 192.168.1.15 with 32 bytes of data:
Reply from 192.168.1.15: bytes=32 time<10ms TTL=255
Reply from 192.168.1.15: bytes=32 time<10ms TTL=255
Reply from 192.168.1.15: bytes=32 time<10ms TTL=255
Reply from 192.168.1.15: bytes=32 time<10ms TTL=255
Ping statistics for 192.168.1.15:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum =
0ms, Average =
0ms
C:\>
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
69
Analysis of ICMP Query messages
Microsoft Windows 2000 Server ICMP Echo Request (1):
-*> Snort! <*Version 1.6
By Martin Roesch (roesch@clark.net, www.clark.net/~roesch)
08/08-12:43:56.438090 x.x.x.x -> y.y.y.y
ICMP TTL:128 TOS:0x0 ID:279
ID:512
Seq:6144
ECHO
61 62 63 64 65 66 67 68 69 6A 6B 6C 6D 6E 6F 70
abcdefghijklmnop
71 72 73 74 75 76 77 61 62 63 64 65 66 67 68 69
qrstuvwabcdefghi
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
70
Analysis of ICMP Query messages
Microsoft Windows 2000 Server ICMP Echo Request (2):
-*> Snort! <*Version 1.6
By Martin Roesch (roesch@clark.net, www.clark.net/~roesch)
08/08-12:26:21.428181 x.x.x.x -> y.y.y.y
ICMP TTL:128 TOS:0x0 ID:280
ID:512
Seq:6400
ECHO
61 62 63 64 65 66 67 68 69 6A 6B 6C 6D 6E 6F 70
abcdefghijklmnop
71 72 73 74 75 76 77 61 62 63 64 65 66 67 68 69
qrstuvwabcdefghi
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
71
Analysis of ICMP Query messages
Microsoft Windows 2000 Server SP1 ICMP Echo Request (two
different hosts):
E:\>windump -xnvv -s 1600 icmp
windump: listening on\Device\Packet_{79C233F1-6CD7-49EB-8FA2-FA825CB1C9C3}
11:31:21.848025
x.x.x.x > y.y.y.y icmp: echo request (ttl 128, id 11071)
4500 003c 2b3f 0000 8001 b4a8 xxxx xxxx
yyyy yyyy 0800 265c 0300 2400 6162 6364
6566 6768 696a 6b6c 6d6e 6f70 7172 7374
7576 7761 6263 6465 6667 6869
11:31:22.221772 x.x.x.x > z.z.z.z icmp: echo request (ttl 128, id 11075)
4500 003c 2b43 0000 8001 b420 xxxx xxxx
zzzz zzzz 0800 255c 0300 2500 6162 6364
6566 6768 696a 6b6c 6d6e 6f70 7172 7374
7576 7761 6263 6465 6667 6869
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
72
Analysis of ICMP Query messages
Microsoft Windows NT 4 WRKS SP6a ICMP Echo Request (1):
-*> Snort! <*Version 1.6
By Martin Roesch (roesch@clark.net, www.clark.net/~roesch)
08/10-16:55:04.640085 10.0.0.117 -> 10.0.0.105
ICMP TTL:32 TOS:0x0 ID:27904
ID:256
Seq:256
ECHO
61 62 63 64 65 66 67 68 69 6A 6B 6C 6D 6E 6F 70
abcdefghijklmnop
71 72 73 74 75 76 77 61 62 63 64 65 66 67 68 69
qrstuvwabcdefghi
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
73
Analysis of ICMP Query messages
Microsoft Windows NT 4 WRKS SP6a ICMP Echo Request (2):
-*> Snort! <*Version 1.6
By Martin Roesch (roesch@clark.net, www.clark.net/~roesch)
08/10-16:55:05.637185 10.0.0.117 -> 10.0.0.105
ICMP TTL:32 TOS:0x0 ID:28160
ID:256
Seq:512
ECHO
61 62 63 64 65 66 67 68 69 6A 6B 6C 6D 6E 6F 70
abcdefghijklmnop
71 72 73 74 75 76 77 61 62 63 64 65 66 67 68 69
qrstuvwabcdefghi
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
74
Analysis of ICMP Query messages
Operating System
Gap between each IP ID values
UNIX and UNIX-like
1
Windows 95
Windows 98
256
Windows 98 SE
256
Windows ME
1
Windows NT 4 Workstation SP3
Windows NT 4 Workstation SP6a
256
Windows NT 4 Server SP4
256
Windows 2000 Family (+SP1)
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
1
75
Analysis of ICMP Query messages
Sequence
Number
Field Value
Starts with
Gap between each
sequence number
HEX / Decimal
ICMP ID Field
Value
Starts with
HEX / Decimal
Carry the same ID
number to the
same host with
another ICMP
Echo request?
Linux Kernel 2.2.x, 2.4.x
0
100 / 256
No
FreeBSD 4.1
0
100 / 256
Aix 4.1
0
1/1
Solaris 2.x
0
1/ 1
According to
other processes
in the System
According to
other processes
in the System
According to
other processes
in the System
According to
other processes
in the System
Windows 98 / 98 SE
256
100 / 256
200 / 512
Yes*
Windows ME
256
100 / 256
300 / 768
Yes*
Operating System
No
No
No
Windows 95
Windows NT 4 Workstation SP3
100 / 256
Yes*
Windows NT 4 Workstation
SP6a
256
100 / 256
100 / 256
Yes*
Windows NT 4 Server SP4
256
100 / 256
100 / 256
Yes*
Windows 2000 Family
256
100 / 256
200 / 512
Yes*
Windows 2000 Family SP1
256
100 / 256
300 / 768
Yes*
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
76
You can run but you cannot Hide
Why it is impossible to make a Microsoft based
machine undetected?
Unless you filter ICMP traffic on the Host …
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
77
Further Reading
ICMP Usage In Scanning, by Ofir Arkin,
http://www.sys-security.com.
Passive Fingerprinting with ICMP, by Ofir Arkin,
http://www.sys-security.com.
RFC 792: Internet Control Message Protocol,
http://www.ietf.org/rfc/rfc0792.txt
RFC 1122: Requirements for Internet Hosts - Communication Layers,
http://www.ietf.org/rfc/rfc1122.txt
RFC 1256: ICMP Router Discovery Messages,
http://www.ietf.org/rfc/rfc1256.txt
RFC 1349: Type of Service in the Internet Protocol Suite,
http://www.ietf.org/rfc/rfc1349.txt
RFC 1812: Requirements for IP Version 4 Routers,
http://www.ietf.org/rfc/rfc1812.txt
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
78
Tools Used in this Presentation
tcpdump – http://www.tcpdump.org
Snort written by Marty Roesch, – http://www.snort.org
HPING2 written by antirez, http://www.kyuzz.org/antirez/hping/
SING written by Alfredo Andres Omella, http://www.sourceforge.org/projects/sing
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
79
Questions?
Founder
http://www.sys-security.com
ofir@sys-security.com
Active Member
project.honeynet.org
Ofir Arkin, “Active & Passive Fingerprinting of Microsoft Based Operating
Systems using the ICMP protocol”, BlackHat Windows 2k Security
http://www.sys-security.com
80