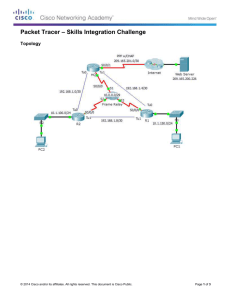
Windows Server Pro: Manage and Administer Objectives
advertisement

TestOut Windows Server Pro: Manage and Administer – English 3.1.x LESSON PLAN Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Table of Contents Course Overview .................................................................................................. 4 Course Introduction for Instructors ........................................................................ 5 Section 1.1: Active Directory Overview ................................................................. 7 Section 1.2: Speeding Up Authentication .............................................................. 8 Section 1.3: Single Master Operations Roles (FSMO) .......................................... 9 Section 1.4: Read Only Domain Controllers (RODCs) ........................................ 11 Section 1.5: Virtual Domain Controllers .............................................................. 13 Section 1.6: Service Accounts ............................................................................ 14 Section 1.7: Maintaining Active Directory ............................................................ 16 Section 1.8: Restoring Active Directory ............................................................... 18 Section 2.1: Group Policy Foundation ................................................................. 20 Section 2.2: Administrative Templates ................................................................ 23 Section 2.3: Folder Redirection ........................................................................... 25 Section 2.4: Software Deployment ...................................................................... 26 Section 2.5: Security Settings ............................................................................. 28 Section 2.6: Password and Account Policies ...................................................... 30 Section 2.7: Advanced Auditing .......................................................................... 32 Section 2.8: Preferences ..................................................................................... 34 Section 2.9: Group Policy Management .............................................................. 36 Section 2.10: Management Delegation ............................................................... 38 Section 3.1: File Server Resource Manager ....................................................... 39 Section 3.2: Distributed File System ................................................................... 41 Section 3.3: Distributed File System Replication................................................. 43 Section 3.4: File Encryption ................................................................................ 45 Section 3.5: Disk Encryption ............................................................................... 47 Section 4.1: DNS Name Resolution .................................................................... 49 Section 4.2: DNS Forwarding and Delegation .................................................... 50 Section 4.3: DNS Zone ....................................................................................... 52 Section 4.4: DNS Zone Management ................................................................. 54 Section 4.5: DNS Records .................................................................................. 56 Section 4.6: DNS Options ................................................................................... 58 Section 5.1: Routing............................................................................................ 60 Section 5.2: Network Address Translation (NAT)................................................ 62 Section 5.3: Virtual Private Networks (VPN) ....................................................... 63 Section 5.4: Network Policy Server ..................................................................... 65 Section 5.5: RADIUS .......................................................................................... 67 Section 5.6: Network Access Protection ............................................................. 69 Section 5.7: DirectAccess ................................................................................... 71 Section 6.1: Windows Software Update Services (WSUS) ................................. 73 Section 6.2: Windows Deployment Services (WDS) ........................................... 76 Section 6.3: WDS Image Management ............................................................... 78 Section 6.4: Performance Monitor....................................................................... 80 Section 6.5: Event Viewer ................................................................................... 82 Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 6.6: Network Monitor .............................................................................. 84 Windows Server Pro: Manage and Administer Practice Exams .......................... 85 Microsoft 70-411 Practice Exams ....................................................................... 86 Appendix A: Approximate Time for the Course ................................................... 87 Appendix B: Exam 70-411: Administering Windows Server 2012 Objectives ..... 90 Appendix C: Windows Server Pro: Manage and Administer Objectives ............. 96 Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Course Overview This course prepares students for TestOut’s Windows Server Pro: Manage and Administer exam and Microsoft’s 70-411 certification exam. Module 1 – Active Directory This module teaches the students details about using Active Directory. This will include authentication, FSMO, RODCs, and maintaining and restoring Active Directory. Module 2 – Group Policy In this module students will learn about creating, configuring and managing GPOs. Module 3 – File Services This module teaches students about controlling and organizing file resources and protecting access to data. Module 4 – DNS This module examines name resolution, resolving queries for records, creating and managing DNS zones, and creating DNS records. Module 5 – Remote Access Management In this module students will learn concepts about managing remote access. This includes understanding and configuring routers, securing communications over an untrusted network, authorizing remote clients and protecting access to a network. Module 6 – Server Management This module discusses management of server such as, updating software, deploying operating systems, and monitoring server, logs, and network traffic. Practice Exams In Practice Exams students will have the opportunity to test themselves and verify that they understand the concepts and are ready to take the certification exam. The practice exams contain examples of the types of questions that a student will find on the actual exam: Microsoft 70-411 Practice Exams Windows Server Pro: Manage and Administer Practice Exams Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Course Introduction for Instructors This course provides students with the knowledge to become industry certified as a Windows professional. It prepares the student for the following exams: Microsoft’s 70-411: Administering Windows Server 2012 TestOut’s Windows Server Pro: Manage and Administer Microsoft’s 70-411: Administering Windows 2012 certification measures the students’ ability to administer, configure, and manage Windows Server 2012 operating system. The following knowledge domains are addressed: Deploy, manage, and maintain servers Configure file and print services Configure network services and access Configure a network policy server infrastructure Configure and manage Active Directory Configure and manage Group Policy Note: MS 70-411 objectives are listed in Appendix B: 70-411: Administering Windows Server 2012 Objectives TestOut’s Windows Server Pro: Manage & Administer certification measures the students’ ability to perform real-world job skills using the Windows Server 2012 operating system. The following knowledge domains are addressed: Active Directory Management Group Policy Configuration File Services Management DNS Configuration Routing Configuration Routing and Remote Access Configuration Deployment Management Note: TestOut’s Windows Server Pro: Manage & Administer objectives are listed in Appendix C: Windows Server Pro: Manage and Administer Objectives The section introductions in LabSim and the lesson plans list the objectives that are met for each of the exams in that section. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. The following icons are placed in front of lesson items in LabSim to help students quickly recognize the items in each section: = Demonstration = Exam = Lab/Simulation = Text lesson or fact sheet = Video The video and demonstration icons are used throughout the lesson plans to help instructors differentiate between the timing for the videos and demonstrations. In the lesson plans the Total Time for each section is calculated by adding the approximate time for each section which is calculated using the following elements: Video/demo times Approximate time to read the text lesson (the length of each text lesson is taken into consideration) Simulations (5 minutes is assigned per simulation. This is the amount of time it would take for a knowledgeable student to complete the lab activity. Plan that the new students will take much longer than this depending upon their knowledge level and computer experience.) Questions (1 minute per question) Note: Appendix A: Approximate Time for the Course contains the approximate time for each section which are totaled for the entire course. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 1.1: Active Directory Overview Summary This section provides an overview of Active Directory. Concepts covered include: Active Directory: o Centralized database o Contains user account and security information o Hierarchical framework with the following components: Domain Object Organization Unit (OU) Generic Containers Trees and Forests Domain Controller Sites and Subnets o NTDS.dit database file: Data table Link table Security descriptor (SD) Lecture Focus Questions: Why is DNS important for Active Directory? What is the purpose of the schema? What are the advantages of using organizational units over generic containers? What is the difference between a tree and a forest? How can you tell when a new domain starts a new tree? How does a site differ from a domain? Video/Demo 1.1.1 Overview of Active Directory Time 8:13 Number of Exam Questions 7 questions Total Time About 20 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 1.2: Speeding Up Authentication Summary This section provides information about speeding up authentication in the case of multiple-domain and multiple-site design. Features to improve performance in these situations include: Global Catalog Universal Group Membership Caching (UGMC) Global Catalog vs UGMC Lightweight Directory Access Protocol (LDAP) Students will learn how to: Add or remove the global catalog from a domain controller. Enable Universal Group Membership Caching for a site. Windows Server Pro: Manage and Administer Exam Objectives: 1.0 Active Directory Management. o Implement Global Catalog Servers o Implement Universal Group Membership Caching (UGMC) 70-411 Exam Objectives: 502. Configure Domain Controllers. o Configure Universal Group Membership Caching (UGMC) Lecture Focus Questions: What are the advantages of having more than one Global Catalog server? Why does a single domain network not need a Global Catalog server? What is the function of Universal Group Membership caching? When should Universal Group Membership caching be implemented? When would you use global catalog servers instead? Video/Demo 1.2.1 Authentication Overview 1.2.2 Global Catalog Servers and UGMC Total Time 4:47 2:23 7:10 Lab/Activity Configure Global Catalog Servers Enable Universal Group Membership Caching Number of Exam Questions 8 questions Total Time About 30 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 1.3: Single Master Operations Roles (FSMO) Summary This section provides details about Single Master Operations Roles (FSMO). Students will learn about: The role of operations master roles Operation roles at the forest levels: o Schema master o Domain naming master Operation roles at the domain levels: o Relative ID (RID) Master o Primary Domain Controller (PDC) Emulator o Infrastructure Master Considerations about using operations master roles Recommendations when designing operations master roles placement Managing operations master role placement Tools to manage operations master role placement: o MMC Snap-in Management Tool o Ntdsutil.exe Details about the standby operations master Students will learn how to: Transfer operation master roles among domain controllers. Troubleshoot operation master roles to diagnose network problems. Seize an operation master role in the case of a failed role operations master. Windows Server Pro: Manage and Administer Exam Objectives: 1.0 Active Directory Management. o Manage Flexible Single-Master Operation (FSMO) roles 70-411 Exam Objectives: 502. Configure Domain Controllers. o Transfer and seize operations masters Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: What is the purpose of an operation master role server? What is the function of a PDC emulator? What does the infrastructure master do? Which operations master roles are located at the forest level? How many of these roles are there in a forest? How many domain operations masters are in a forest? You are installing a new domain controller in a new domain in an existing forest. How many operation master roles will that server hold? What might happen if the RID master becomes unavailable? Which role(s) should be placed on a global catalog server? Which roles should not? What is the difference between transferring a role and seizing a role? Video/Demo 1.3.1 Overview of FSMO Roles 1.3.2 FSMO Role Transfer/Failure 1.3.3 Viewing FSMO Roles 1.3.5 Transferring FSMO Roles 1.3.6 Seizing FSMO Roles Total Time 10:00 2:38 4:11 4:18 4:41 25:48 Lab/Activity Transfer RID and PDC Masters Transfer the Infrastructure Master Troubleshoot Operations Masters Number of Exam Questions 7 questions Total Time About 55 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 1.4: Read Only Domain Controllers (RODCs) Summary This section provides information about deploying Read Only Domain Controllers (RODCs). Details covered include: Features of RODCs: o Administrator role separation o Unidirectional replication o Read-only data o Password replication o DNS Server service Installing RODC Students will learn how to: Pre-create RODC accounts in Active Directory. Install an RODC. Windows Server Pro: Manage and Administer Exam Objectives: 1.0 Active Directory Management. o Implement a Read Only Domain Controller (RODC) 70-411 Exam Objectives: 502. Configure Domain Controllers. o Install and configure a read-only domain controller (RODC) Lecture Focus Questions: What is the purpose of administrator role separation? How does unidirectional replication protect your network? How does using an RODC allow for domain logon in the event of a WAN link failure? How do DNS zones work differently on an RODC? What are the forest functional level requirements for installing an RODC? Which operating system versions must run on the PDC emulator? Which permissions do you need to install an RODC? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Video/Demo 1.4.1 Read Only Domain Controllers (RODCs) 1.4.3 Pre-creating the RODC Account Total Time 6:46 7:19 14:05 Lab/Activity Create RODC Accounts Number of Exam Questions 6 questions Total Time About 30 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 1.5: Virtual Domain Controllers Summary This section discusses creating virtual domain controllers. Details covered include: Issues concerning creating a snapshot of a Virtual Domain Controller and later reverting back to earlier snapshots o Update Sequence Number (USN) rollback o VM-Generation-ID System requirements: o Supported hypervisors o Supported guest operating systems Virtual Domain Controller Cloning System prerequisites before cloning a virtual domain controller: o Supported hypervisors o Supported guest operating systems o PDC Emulator The basic steps for cloning a virtual domain controller 70-411 Exam Objectives: 502. Configure Domain Controllers. o Configure Domain Controller cloning Lecture Focus Questions: Which versions of the Windows operating system support VMGeneration-ID identifiers? Why is the VM-Generation-ID stored in two different locations? What is the advantage of creating a new virtual domain controller by cloning an existing virtual domain controller? Which group must the computer object for the domain controller be a member of to be cloned? Video/Demo 1.5.1 Domain Controller Cloning Time 7:41 Number of Exam Questions 6 questions Total Time About 20 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 1.6: Service Accounts Summary This section examines using service accounts to allow an application or service to interact with the operating system. Concepts covered include: Categories of service accounts: o Built-in local user account o Domain user account o Managed service account o Virtual account o Group managed service account Requirements to use managed or virtual accounts Common service account cmdlets: o New-ADServiceAccount o Get-ADServiceAccount o Set-ADServiceAccount o Remove-ADServiceAccount o Install-ADServiceAccount Considerations when using group managed service accounts Students will learn how to: Create a service account. Create a managed service account and a group managed service account. 70-411 Exam Objectives: 501 Configure service authentication. o Create and configure Service Accounts o Create and configure Group Managed Service Accounts o Create and configure Managed Service Accounts o Configure Kerberos delegation o Manage Service Principal Names (SPNs) o Configure virtual accounts Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: What are the differences between a managed service account and a virtual service account? Which operating system is required to manage a service with a managed service account? Which Windows PowerShell cmdlet will create a new managed service account? If you have a domain controller running Windows Server 2003, how can you still use a virtual account? Video/Demo Time 1.6.1 Overview of Service Accounts 2:55 1.6.2 Kerberos Delegation 2:33 1.6.3 Creating Service Accounts 10:32 1.6.4 Creating Managed Service Accounts 5:13 1.6.5 Creating Group Managed Service Accounts 7:43 1.6.6 Configuring Virtual Accounts 1:25 Total 30:21 Number of Exam Questions 8 questions Total Time About 45 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 1.7: Maintaining Active Directory Summary In this section students will learn details about maintaining Active Directory. Concepts covered include: Considerations when performing a system state backup Using the Group Policy Management console to back up and restore only Group Policy data Steps to make and use snapshots of the Active Directory database Tasks that can be performed from the command using the NTDSUtil command o Changing the recovery mode password o Cleaning the metadata o Manually compacting the database o Manually moving the database and log files Students will learn how to: Back up Active Directory and the SYSVOL. Create and mount an Active Directory snapshot. Use the NTDSUtil command to manage and optimize Active Directory from the command line. Windows Server Pro: Manage and Administer Exam Objectives: 1.0 Active Directory Management. o Backup Active Directory 70-411 Exam Objectives: 503 Maintain Active Directory. o Back up Active Directory and SYSVOL o Manage Active Directory offline o Optimize an Active Directory database o Clean up metadata o Configure Active Directory snapshots Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: Which backup type should you perform if you want to protect Active Directory? What are the requirements for performing a system state backup? When using the dsamain command with the /dbpath option to expose a snapshot through an LDAP server, why can't you use port 389? Which port should you use? Using NTDSUtil, which tasks can you perform to manage the Active Directory? Video/Demo 1.7.1 Backing up Active Directory 1.7.2 Backing up AD and the SYSVOL 1.7.4 Managing AD Snapshots 1.7.7 Active Directory Maintenance 1.7.8 Using NTDSUtil Total Time 2:10 2:36 7:51 4:17 12:25 29:19 Lab/Activity Back up Active Directory Number of Exam Questions 8 questions Total Time About 50 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 1.8: Restoring Active Directory Summary This section discusses methods of restoring Active Directory. Details include: Active Directory Recycle Bin: o Requirements o Enabling the Recycle Bin Steps to enable the Recycle Bin in an existing forest Considerations when using the Recycle Bin to restore delete Active Directory objects Types of restoration available when restoring Active Directory: o Nonauthoritative o Authoritative Methods for performing a domain controller restore: o Reinstalling Active Directory o Nonauthoritative system state restore o Authoritative system state restore o Critical volume or Bare metal recovery Set the Burflags registry settings at the domain controller to perform a restore to all replicas in the domain: o D2 performs a nonauthoritative restore o D4 performs an authoritative restore Methods to restore lost Active Directory data: o LostAndFound container o Nonauthoritative restore o Authoritative restore o Active Directory Recycle Bin o Database snapshot Warning and solution of a problem where group membership will not be restored when you restore Active Directory objects with an authoritative restore Students will learn how to: Use the AD Recycle Bin to recover AD deleted objects. Use the Administrative Center to recover a user. Use the PowerShell command to recover a user. Perform an authoritative restore using NTDSUtil. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 70-411 Exam Objectives: 503 Maintain Active Directory. o Perform object- and container-level recovery o Perform Active Directory restore o Configure and restore objects by using the Active Directory Recycle Bin Lecture Focus Questions: What is the difference between an authoritative and a nonauthoritative restore? Why might group membership not be restored with an authoritative restore? When would this problem exist and how can you overcome it? Which forest functional level is required for the Active Directory Recycle Bin? What are the differences when a deleted object lifetime expires versus when a recycled object lifetime expires? Video/Demo 1.8.1 Restoring Active Directory 1.8.2 Active Directory Recycle Bin 1.8.4 AD Restore Total Time 6:56 6:28 10:00 23:24 Number of Exam Questions 12 questions Total Time About 45 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.1: Group Policy Foundation Summary This section discusses creating and managing Group Policy objects. Details include: GPO settings: o Undefined o Defined Considerations when you configure GPO settings Intervals that Windows refreshes the effective Group Policy settings Gpupdate command switches to manually refresh group policy settings: o No switch o /force o /target:user o /target:computer o /boot o /logoff Group Policy inheritance: o The order in which GPOs are applied o Effective GPO settings o Categories: Computer policies User policies Methods to customize how GPO settings are applied: o Block inheritance o Enforced o GPO Permissions o Disabling a GPO link o Disabling a part of the GPO o WMI filtering o Loopback processing o Slow link detection o Group Policy caching o Account policies Guidelines when you use GPOs to deploy GPOs Students will learn how to: Create and link Group Policy objects. Modify and control Group Policy processing order. Control how group policies are processed by configuring Group Policy slow link detection and loopback processing. Troubleshoot Group Policy from a workstation using gpresult and RSOP. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Troubleshoot Group Policy from a server using Group Policy Modeling and Group Policy Results. Block inheritance to domain controllers and member servers. Windows Server Pro: Manage and Administer Exam Objectives: 2.0 Group Policy Configuration. o Manage Group Policy processing order 70-411 Exam Objectives: 601 Configure Group Policy processing. o Configure processing order and precedence o Configure blocking of inheritance o Configure enforced policies o Configure security filtering and WMI filtering o Configure loopback processing o Configure and manage slow-link processing o Configure client-side extension (CSE) behavior Lecture Focus Questions: What is the difference between deleting a GPO and deleting a GPO link? What is an undefined GPO setting? How does this affect the effective settings for a user or computer? When are Group Policy settings refreshed? How do you manually refresh Group Policy settings? What will determine the effective Group Policy setting when an individual setting is configured in two different GPOs? When are computer policies enforced? User policies enforced? How do you prevent inheritance from being blocked for a specific GPO? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Video/Demo 2.1.1 Group Policy Processing Order 2.1.2 Linking GPOs 2.1.3 Modifying GPO Processing Order 2.1.4 Modifying GPO Processing Order 2.1.5 Loopback Processing and Slow Link Detection 2.1.6 Loopback Processing and Slow Link Detection 2.1.7 Configuring Group Policy Caching 2.1.9 Troubleshooting Group Policy Total Time 4:51 4:04 4:34 8:54 2:25 8:16 3:54 8:51 45:49 Lab/Activity Control GPO Inheritance Configure GPO Permissions Number of Exam Questions 10 questions Total Time About 70 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.2: Administrative Templates Summary This section discusses using Administrative Templates. Concepts covered include: Prior to Windows Server 2008, the Administrative Template format was .adm files The process to work with .adm files Older adm file format has been replaced on Windows Server 2008 (and later) by the following: o .admx files o .adml files ADMX files are saved on the local computer in the %systemroot%\PolicyDefinitions folder The central storage location for .admx and .adml files on a domain controller is SYSVOL\domain_name\Policies\PolicyDefinitions folder Students will learn how to: Import custom Administrative Templates. Use the ADMX Migrator to convert older .adm Administrative Templates to the new .admx format. Configure property filters for Administrative Templates. Create a Central Store to share .admx files with multiple computers. Windows Server Pro: Manage and Administer Exam Objectives: 1.0 Group Policy Configuration. o Create custom administrative templates by importing GPOs 70-411 Exam Objectives: 602 Configure Group Policy settings. o Configure settings including software installation, folder redirection, scripts, and administrative template settings o Import security templates o Import custom administrative template file o Convert administrative templates using ADMX Migrator o Configure property filters for administrative templates Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: What is the Administrative Template central store and where is it located? What are the advantages of the .admx file format? What is the function of .adml files? Video/Demo 2.2.1 Custom Administrative Templates 2.2.2 Importing Custom Administrative Templates 2.2.4 Converting Administrative Templates 2.2.5 Configuring Property Filters 2.2.6 Central Stores 2.2.7 Creating a Central Store 2.2.8 Exploring Admin Template Settings Total Time 1:50 3:58 4:06 2:18 1:45 3:52 6:48 24:37 Lab/Activity Import a GPO Number of Exam Questions 6 questions Total Time About 35 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.3: Folder Redirection Summary In this section students will learn the benefits of folder redirection and how to configure folder redirection. Students will learn how to: Configure folder redirection to move the contents of the Documents folder to a new location. 70-411 Exam Objectives: 602 Configure Group Policy settings. o Configure settings including software installation, folder redirection, scripts, and administrative template settings Lecture Focus Questions: Why would you choose to use folder redirection? What is the difference between basic redirection and advanced redirection? A folder that has been redirected appears to be on the local system, but where is it actually stored? Video/Demo 2.3.1 Folder Redirection 2.3.2 Configuring Folder Redirection Total Time 1:52 3:59 5:51 Number of Exam Questions 5 questions Total Time About 10 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.4: Software Deployment Summary In this section students will learn about the software deployment lifecycle. Details in this section include: Steps in the software deployment lifecycle: o Plan o Deploy o Manage (Upgrade) o Remove Guidelines when you manage software distribution Students will learn how to: Assign and publish software installer packages. Configure software installation packages to customize deployment and removal. Windows Server Pro: Manage and Administer Exam Objectives: 2.0 Group Policy Configuration. o Deploy software using Group Policy 70-411 Exam Objectives: 602 Configure Group Policy settings. o Configure settings including software installation, folder redirection, scripts, and administrative template settings Lecture Focus Questions: What is the difference between assigned and published software? Why should you use the UNC path to an installer package rather than the local path? What does it mean when a user or computer is outside of the scope of management for a software installation package? What happens to the software when this condition exists? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Video/Demo 2.4.1 Software Deployment 2.4.2 Deploying Software with a GPO Total Time 2:43 14:38 17:21 Lab/Activity Assign Software Deploy Software 1 Deploy Software 2 Number of Exam Questions 14 questions Total Time About 50 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.5: Security Settings Summary This section examines the following common GPO security setting categories: Account Policies Local Policies/Audit Policy Local Policies/User Rights Assignment Local Policies/Security Options Windows Firewall with Advanced Security Network List Manager Policies Public Key Policies Software Restriction Policies Application Control Policies IP Security Policies Advanced Audit Policy Configuration Event Log Restricted Groups System Services Registry File System Wireless Network Students will learn how to: Configure, save, and import a security template. Windows Server Pro: Manage and Administer Exam Objectives: 2.0 Group Policy Configuration. o Implement the following GPO policies: Security Advanced audit 70-411 Exam Objectives: 602. Configure Group Policy settings. o Import security templates Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: What is the difference between a user right and a security option? Under what conditions are Account Policies in effect? What are some of the User Rights Assignments you might consider using? What is the function of the Network List Manager Policies? Video/Demo 2.5.1 Security Options 2.5.2 Creating Security Templates Total Time 1:43 10:10 11:53 Lab/Activity Configure Security Options Number of Exam Questions 7 questions Total Time About 30 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.6: Password and Account Policies Summary This section covers password and account policies. Concepts covered include: Password Policy: o Enforce password history o Maximum password age o Minimum password age o Minimum password length o Password must meet complexity requirements o Store passwords using reversible encryption Account Lockout Policy: o Account lockout duration o Account lockout threshold o Reset account lockout after Considerations when managing account policies Kerberos policies: o Enforce user logon restrictions o Maximum lifetime for service ticket o Maximum lifetime for user ticket o Maximum lifetime for user ticket renewal o Maximum tolerance for computer clock synchronization The role of granular password policies Facts about granular password policies Using ADSI Edit to create a PSO Managing granular passwords using Active Directory Administrative Center Students will learn how to: Configure and manage Account Policy settings. Use ADSI Edit to configure granular password policy settings. Windows Server Pro: Manage and Administer Exam Objectives: 2.0 Group Policy Configuration. o Implement the following GPO policies: Account Fine-grained password 70-411 Exam Objectives: 504. Configure account policies. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. o o o o o o Configure domain user password policy Configure and apply Password Settings Objects (PSOs) Delegate password settings management Configure local user password policy Configure account lockout settings Configure Kerberos policy settings Lecture Focus Questions: Users in a network have to change their passwords every 30 days, but many users have reported that they simply enter the same password to make the change. Which policy can you configure to prevent this? What is the effect of setting the minimum password age account policy to 5 days? How can you prevent users from creating passwords like desk, mom, chair, or office? What is the effect of setting the account lockout policy to 0? What happens when you configure the Account Policies settings in a GPO linked to an OU? How can you configure different account policy settings for different users? Which object types can you associate with a granular password policy? A user has a granular password policy applied directly to the user account, and a different policy applied to a group of which the user is a member. Which policy will be in effect? Video/Demo Time 2.6.1 Password Policies 2.6.2 Configuring Domain User Password Policy 2.6.3 Configuring Account Lockout 2.6.4 Configuring Local Password Policies 2.6.5 Configuring Kerberos Policy Settings 2.6.8 Creating a Fine-grained Password Policy Total 2:09 4:30 2:18 3:11 6:47 9:25 28:20 Lab/Activity Configure Account Policies Create a Fine-grained Password Policy Number of Exam Questions 14 questions Total Time About 60 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.7: Advanced Auditing Summary This section provides information about 53 new auditing capabilities that have been integrated with Group Policy. Concepts covered include: Details about the advanced audit policy configuration Categories of the 53 new auditing policy settings: o Account Logon o Account Management o Detailed Tracking o DS Access o Logon/Logoff o Object Access o Policy Change o Privilege Use o System o Global Object Access Auditing Students will learn how to: Use Group Policy to enforce auditing and secure audit logs. Windows Server Pro: Manage and Administer Exam Objectives: 2.0 Group Policy Configuration. o Implement the following GPO policies: Advanced audit 70-411 Exam Objectives: 204. Configure advanced audit policies. o Implement auditing using Group Policy and AuditPol.exe o Create expression-based audit policies o Create removable device audit policies Lecture Focus Questions: What is the difference between auditing for success and auditing for failure? How can you configure auditing to track changes to Active Directory objects? What is the result of excessive auditing? Why should you design periodic reviews of audit logs? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Video/Demo 2.7.1 Advanced Audit Policies 2.7.2 Auditing Folder Access Total Time 7:22 14:46 22:08 Lab/Activity Configure Advanced Auditing Configure Removable Device Auditing Number of Exam Questions 12 questions Total Time About 45 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.8: Preferences Summary This section discusses using Group Policy preferences to configure, deploy, and manage operating system and application settings that you cannot manage using Group Policy settings. Details covered include: Comparison of characteristics of Group Policy preferences to Group Policy settings Facts about Group Policy preferences Group Policy preferences: o Drive maps o Environment o Files Folders o Ini Files o Network shares o Registry o Shortcuts o Devices o Folder options o Internet settings o Local users and groups o Network options o Power options o Printers o Regional options o Scheduled tasks o Services o Start menu Students will learn how to: Configure Group Policy preferences in a GPO. Deploy shortcuts in a GPO. Windows Server Pro: Manage and Administer Exam Objectives: 2.0 Group Policy Configuration. o Configure Group Policy Preferences Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 70-411 Exam Objectives: 604 Configure Group Policy preferences. o Configure Group Policy Preferences (GPP) settings including printers, network drive mappings, power options, custom registry settings, Control Panel settings, Internet Explorer settings, file and folder deployment, and shortcut deployment. o Configure item-level targeting Lecture Focus Questions: What is the main difference between Group Policy preferences and Group Policy settings? Which types of applications and operating system features does Group Policy preferences support? How do you configure Group Policy preferences? What are the operating system prerequisites for applying Group Policy preferences? Video/Demo 2.8.1 Group Policy Preferences 2.8.2 Configuring Group Policy Preferences Total Time 1:58 7:47 9:45 Lab/Activity Configure Internet Explorer Settings in a GPO Configure Power Options in a GPO Deploy Desktop Shortcuts in a GPO Number of Exam Questions 6 questions Total Time About 35 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.9: Group Policy Management Summary This section examines management of Group Policy objects. Concepts covered include: Considerations when you manage Group policy objects Methods to create another GPO from an existing GPO: o Copy o Backup and Import o Starter GPO Using cmdlets in the Group Policy module for Windows PowerShell to manage domain-based GPOs Common GPO management cmdlets include: o New-GPO o Copy-GPO o Get-GPO o Backup-GPO o Remove-GPO o Rename-GPO o Restore-GPO o Import-GPO o New-GPLink o Set-GPLink o Remove-GPLink o New-GPStarterGPO The dcgpofix command switches to restore the default group Policy objects to their original state: o /target:dc o /target:domain o /target:both o /ignoreschema Using the Remote Group Policy update Updating Group Policy using the Group Policy Management console Students will learn how to: Back up and restore a GPO. Create and configure a migration table to migrate domain-specific settings. Restore default GPOs to what they were initially when Active Directory was installed. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Windows Server Pro: Manage and Administer Exam Objectives: 2.0 Group Policy Configuration. o Backup and restore GPOs 70-411 Exam Objectives: 603. Manage Group Policy objects (GPOs). o Back up, import, copy, and restore GPOs o Create and configure Migration Table o Reset default GPOs o Force Group Policy update Lecture Focus Questions: What is the difference between deleting a GPO and deleting a GPO link? How can you copy a GPO from one domain to another? How can you copy starter GPOs? Which tools can you use to manage GPOs and GPO links? When moving GPOs from one domain to another, how do you handle settings that are domain-specific and cannot be copied directly? Video/Demo 2.9.1 Group Policy Management 2.9.2 Managing GPOs 2.9.5 Migration Tables 2.9.6 Configuring Migration Tables 2.9.7 GPO Default Setting 2.9.8 Resetting GPO Defaults 2.9.9 Forcing Group Policy Updates Total Time 1:26 5:14 1:10 4:26 1:31 3:18 1:15 18:20 Lab/Activity Back Up a GPO Restore a GPO Number of Exam Questions 9 questions Total Time About 40 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 2.10: Management Delegation Summary This section examines delegating out Group Policy management. Students will learn how to: Create a GPO and delegate the management of particular tasks for all GPOs to a specified group. Use the Delegation of Control Wizard to delegate common administrative tasks. Windows Server Pro: Manage and Administer Exam Objectives: 2.0 Group Policy Configuration. o Delegate GPO management 70-411 Exam Objectives: 603. Manage Group Policy objects (GPOs). o Delegate Group Policy management Lecture Focus Questions: What is the two-step procedure required to delegate Group Policy object management? Which tools are required to complete a delegation of management? Video/Demo Time 2.10.1 GPO Management Delegation 2.10.2 Delegating GPO Management 2.10.4 Delegating Password Management 1:07 4:30 4:24 Total 10:01 Lab/Activity Delegate GPO Creation Delegate Administrative Control Number of Exam Questions 6 questions Total Time About 25 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 3.1: File Server Resource Manager Summary This section provides details of using the File Server Resource Manager to allow administrators to understand, control, and manage the quantity and type of data stored on their servers. Concepts covered include: FSRM is installed as a role service of the File Services role Key FSRM features: o Quotas o Notifications o File Screening o Storage Reports o File Classification o File Management Methods for configuring quotas for Windows Server: o NTFS Disk Quotas o FSRM Folder and Volume Quotas Students will learn how to: Configure volume and folder quotas. Create quota templates. Configure file screens and file screen exceptions. Generate FSRM reports for both quotas and overall file system use. Schedule FSRM reports. Windows Server Pro: Manage and Administer Exam Objectives: 3.0 File Services Management. o Configure FSRM quotas o Configure FSRM file screens 70-411 Exam Objectives: 202 Configure File Server Resource Manager (FSRM). o Install the FSRM role o Configure quotas o Configure file screens o Configure reports Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: What are the primary differences between disk quotas with NTFS and quotas implemented through FSRM? How does a soft quota differ from a hard quota? How do quota templates facilitate quota management? What is the difference between a quota and a file screen? How is an active file screen more restrictive than a passive file screen? How can you automatically assign classification information to files? What can you accomplish with the file expiration task? Video/Demo 3.1.1 File Server Resource Manager (FSRM) 3.1.2 Installing FSRM 3.1.4 FSRM Quotas 3.1.6 File Screens 3.1.8 Configuring Reports Total Time 2:49 1:07 4:59 4:41 3:32 17:08 Lab/Activity Add Role Services for FSRM Configure FSRM Quotas Configure FSRM File Screens Number of Exam Questions 15 questions Total Time About 50 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 3.2: Distributed File System Summary This section discusses using the Distributed File System (DFS) to provide a way to logically organize shared folders on multiple servers into a single logical folder hierarchy called a namespace. Concepts covered include: DFS Namespaces include the following components: o Namespace o Namespace server o Namespace root o Folder Namespace types and criteria: o Stand-alone o Domain-based Considerations when managing DFS Namespaces Students will learn how to: Create a DFS namespace with folders and targets. Add role services as required to support DFS and the appropriate replication method. Windows Server Pro: Manage and Administer Exam Objectives: 3.0 File Services Management. o Implement DFS replication 70-411 Exam Objectives: 201. Configure Distributed File System (DFS). o Install and configure DFS namespaces Lecture Focus Questions: What is the difference between the namespace root and a folder within DFS? If you have multiple namespace servers, which namespace type should you implement? Which namespace type and mode would you choose to support accessbased enumeration? If you have a single namespace server and that server fails, what happens to client access for folders within the DFS structure? Why? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. How can you prevent users from adding or changing files in a replicated folder? Video/Demo 3.2.1 DFS Namespaces and Replication 3.2.2 Installing a DFS Namespace Total Time 4:54 4:38 9:32 Lab/Activity Add Role Services for DFS and Create a Namespace Number of Exam Questions 6 questions Total Time About 25 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 3.3: Distributed File System Replication Summary This section discusses using the Distributed File System replication to increase fault tolerance and improve access. Concepts covered include: Components that DFS replication uses to control replications: o Replication group o Replicated folder o Connection Considerations when configuring DFS Cloning the DFS database in Windows Server 2012 R2 Recovering a corrupted database using DFS Replication in Windows Server 2012 R2 Optimization strategies for DFS: o Fault tolerance o Referrals o Remote Differential Compression (RDC) o Polling o Staging o Single-master Students will learn how to: Configure DFS replication of folder targets. Create and configure a replication schedule. Manage and optimize DFS by configuring staging and fault tolerance. Windows Server Pro: Manage and Administer Exam Objectives: 3.0 File Services Management. o Implement DFS replication 70-411 Exam Objectives: 201. Configure Distributed File System (DFS). o Configure DFS Replication Targets o Configure Replication Scheduling o Configure Remote Differential Compression settings o Configure staging o Configure fault tolerance Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: When can you add a failover cluster to a DFS replication group? How does Remote Differential Compression conserve bandwidth? Adam, Bob, and Curt access different copies of a replicated folder and modify the same file simultaneously. When each of them saves the file, which file becomes the authoritative copy? What happens to the other copies of this file? Video/Demo 3.3.1 Staging and Fault Tolerance 3.3.2 Configuring DFS Replication Targets 3.3.3 Cloning the DFS Database 3.3.5 Optimizing DFS Total Time 12:00 6:53 10:58 10:00 39:51 Number of Exam Questions 9 questions Total Time About 55 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 3.4: File Encryption Summary In this section students will learn about protecting data through file and disk encryption. Concepts covered include: Components of EFS: o Encryption Process o Access to Encrypted Data o EFS-Related Group Policy o Encrypted Data Management o Remote Storage o Certificate Management Students will learn how to: Encrypt or decrypt a file or folder. Add authorized users to allow encrypted file access. Designate DRAs for file recovery. Configure EFS settings in Group Policy. Windows Server Pro: Manage and Administer Exam Objectives: 3.0 File Services Management. o Encrypt files and folders with EFS 70-411 Exam Objectives: 203. Configure file and disk encryption. o Configure the EFS recovery agent o Manage EFS and Bitlocker certificates including backup and restore Lecture Focus Questions: What is the importance of the DRA in the encryption process? Which users have access to encrypted files and folders? What is the relationship between encryption and compression? What is the significance of encrypting the pagefile? How does Rekeywiz affect your encryption deployment? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Video/Demo 3.4.1 Overview of EFS 3.4.2 EFS Recovery Agents 3.4.3 Encrypting a Folder 3.4.4 Designating an EFS Recovery Agent 3.4.5 Managing EFS Certificates Total Time 2:25 2:38 8:38 11:49 6:31 32:01 Lab/Activity Encrypt a Folder Number of Exam Questions 11 questions Total Time About 50 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 3.5: Disk Encryption Summary In this section students will learn about using BitLocker to protect unauthorized data access on lost, stole or otherwise compromised systems. Concepts covered include: BitLocker key is required to access the contents of the encrypted volume BitLocker uses integrity checking BitLocker is only available on: o Windows Vista Ultimate and Enterprise editions o Windows 7 Ultimate and Enterprise editions o Windows 8 Professional and Enterprise editions o Windows Server 2008 or Windows Server 2008 R2 o Windows Server 2012 BitLocker is not installed by default BitLocker To Go Components of BitLocker: o BitLocker partition o Trusted Platform Module (TPM) o Non-TPM device support How BitLocker differs from the Encrypting File System (EFS) Security components of a BitLocker configuration: o TPM owner password o Recovery key o PIN o Startup key o Data volume key o Data Recovery Agent o Network Unlock BitLocker modes which determine the security level: o TPM-only o TPM with startup key o TPM with PIN o TPM with PIN and startup key o Without a TPM How to configure and manage BitLocker Students will learn how to: Generate recovery keys and create a BitLocker DRA. Configure BitLocker on a computer with a TPM. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Windows Server Pro: Manage and Administer Exam Objectives: 3.0 File Services Management. o Encrypt the server hard disk with BitLocker 70-411 Exam Objectives: 203. Configure file and disk encryption. o Configure BitLocker encryption o Configure the Network Unlock feature o Configure BitLocker policies o Manage EFS and BitLocker certificates including backup and restore Lecture Focus Questions: When implementing BitLocker, why is it a good idea to run a system check before encrypting the drive? What is the difference in function between BitLocker and BitLocker To Go? When using BitLocker, what are the requirements of the Trusted Platform Module? How can you implement BitLocker without a TPM? What would happen if BitLocker were enabled, and the USB flash device which holds the key were to be lost? Video/Demo 3.5.1 BitLocker Disk Encryption 3.5.2 Configuring BitLocker Encryption Total Time 11:35 11:40 23:15 Lab/Activity Configure BitLocker with a TPM Number of Exam Questions 15 questions Total Time About 50 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 4.1: DNS Name Resolution Summary This section provides details of how DNS Name Resolution maps logical host names to IP addresses. Concepts covered include: A DNS server holds a database of hostnames and their corresponding IP addresses HOSTS file Components of the DNS hierarchy: o .dot domain (also called the root domain) o Top Level Domains (TLDs) (.com, .edu, .gov) o Second-level and additional domains o Hosts Fully Qualified Domain Name (FQDN) DNS is a distributed database Caching-only DNS DNS name resolution process for the client DNS name resolution process for the server Lecture Focus Questions: What is the purpose of DNS? How does an FQDN identify a host? What is the difference between a DNS server and a caching-only DNS server? What is the difference between forwarding and recursion? Video/Demo 4.1.1 Fully Qualified Domain Names 4.1.3 Name Resolution Total Time 3:20 8:17 11:37 Number of Exam Questions 11 questions Total Time About 25 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 4.2: DNS Forwarding and Delegation Summary This section provides details of using DNS forwarding and delegation to resolve queries for records. Concepts covered include: The role of a forwarder Methods to control the server’s use of forwarders: o Secondary zone o Stub zone o Conditional forwarder o Disable recursion Reasons to perform zone delegation Process to delegate a zone Students will learn how to: Create a root zone. Use DNS Manager to setup forwarding and conditional forwarding to resolve names. Create a delegation to enable name resolution. Windows Server Pro: Manage and Administer Exam Objectives: 4.0 DNS Configuration. o Configure DNS forwarders o Create DNS delegations 70-411 Exam Objectives: 301. Configure DNS zones. o Configure zone and conditional forwards o Configure zone and conditional forward storage in Active Directory o Configure zone delegation Lecture Focus Questions: What is the role of a forwarder? What could be a disadvantage of using secondary zones? Under what circumstances would you choose to set up conditional forwarding? When should you set up zone delegation? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Video/Demo 4.2.1 Configuring Forwarding and Root Hints 4.2.4 Creating a Delegation Total Time 9:46 4:43 14:29 Lab/Activity Configure Forwarders Delegate Domains Number of Exam Questions 7 questions Total Time About 35 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 4.3: DNS Zone Summary This section discusses provides the basic information about creating and using DNS zones. Concepts covered include: Types of DNS zones: o Primary o Secondary o Active Directory-integrated o Stub Zones are classified as one of two types: o Forward lookup zone o Reverse lookup zone Details about zone transfers Tools to update of zone data: o DNS console o Dnscmd command An Active Directory-integrated zone stores DNS information in Active Directory rather than a zone file Students will learn how to: Create a standard primary zone and a standard secondary zone. Create a stub zone to refer requests over to the authoritative server. Create a Primary forward lookup zone and configure it to allow zone transfers to any server. Configure a reverse lookup zone. Create a new zone and configure the zone to be stored in Active Directory. Windows Server Pro: Manage and Administer Exam Objectives: 4.0 DNS Configuration. o Create the following types of DNS zones Primary Secondary Stub Reverse-lookup Active Directory-integrated Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 70-411 Exam Objectives: 301. Configure DNS zones. o Configure primary and secondary zones o Configure stub zones Lecture Focus Questions: What is the difference between the name resolution of a forward lookup zone and a reverse lookup zone? What are the advantages of using an Active Directory-integrated zone? What are the main difference between a primary zone and a secondary zone? Which tools can you use to manually force an update of zone data? Which type of DNS server can host an Active Directory-integrated zone? What is the function of the Start of Authority (SOA) record? Video/Demo 4.3.1 Forward and Reverse Lookup Zones 4.3.2 Standard DNS Zones 4.3.3 AD Integrated Zones 4.3.6 Creating a New Zone Total Time 2:05 5:57 5:37 11:29 25:08 Lab/Activity Create Standard Zones Create a Reverse Lookup Zone Create an Active Directory-integrated Zone Number of Exam Questions 8 questions Total Time About 55 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 4.4: DNS Zone Management Summary This section discusses management of DNS zones. Concepts covered include: Details about configuring DNS zones Zone data is replicated based on the replication scope: o All domain controllers in this domain o All DNS servers in this domain o All DNS servers in this forest o Application partition Reverse Zone Name Format for: o IPv4 o IPv6 Students will learn how to: Change an existing zone to a different zone type. Configure the properties of an existing zone as needed. Disable zone transfers for a specified zone. Enable Dynamic DNS to minimize DNS administration. Windows Server Pro: Manage and Administer Exam Objectives: 4.0 DNS Configuration. o Manage zone transfers 70-411 Exam Objectives: 302. Configure DNS records. o Configure zone scavenging o Configure record options including Tim to Live (TTL) and weight o Configure secure dynamic updates Lecture Focus Questions: How does replicating DNS information to all domain controllers in the domain affect network traffic versus replicating to all DNS servers in the forest? Which type of zone would you create if you wanted to use secure dynamic updates? What is the purpose of PTR records? What is the zone name format for the reverse lookup network of 1375:2614:DDAB:EE21? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Video/Demo 4.4.1 Configuring Zone Properties Time 7:24 Lab/Activity Disable Zone Transfers Configure a Partner DNS Solution Enable Dynamic DNS Updates Troubleshoot Dynamic DNS Number of Exam Questions 15 questions Total Time About 45 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 4.5: DNS Records Summary This section discusses DNS records which store entries for hostnames, IP addresses, and other information in the zone database. Details include: Common resource records: o SOA (Start of Authority) o NS (Name Server) o A (Host Address) o AAAA (Quad-A) o MX (Mail Exchanger) o CNAME (Canonical Name) o DNAME (Domain Alias) o SRV (Service Locator) o PTR (Pointer) o WINS and WINS-R Resource Records Considerations when managing resource records Using the dnscmd command to add a DNS record Students will learn how to: Create and configure an MX record to identify email servers. Configure the priority and weight of a SRV record to regulate the traffic to the records. Create A records and PTR records for hosts. Create CNAME records to be used as aliases to allow clients to access an intranet website. Use ping to troubleshoot DNS problems. Windows Server Pro: Manage and Administer Exam Objectives: 4.0 DNS Configuration. o Manage dynamic DNS updates 70-411 Exam Objectives: 302. Configure DNS records. o Create and configure DNS Resource Records (RR) including A, AAAA, PTR, SOA, NS, SRV, CNAME, and MX records Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: What information does an SOA record contain? What is the difference between an A and a quad-A record? How is the DNAME record similar to a CNAME record? Which are the most common DNS records? Video/Demo 4.5.1 DNS Record Types 4.5.2 Creating Common Records Total Time 6:19 9:44 16:03 Lab/Activity Create Host Records Create CNAME Records Troubleshoot DNS Records Number of Exam Questions 15 questions Total Time About 50 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 4.6: DNS Options Summary In this section students will learn about different DNS options that can be configured or controlled. Concepts covered in this section include: DNS Manager tabs to configure DNS server properties: o Interfaces o Forwarders o Root Hints o Debug Logging o Event Logging o Monitoring o Security o Advanced Configure DNS Round Robin Debug logging options to configure debug logging: o Packet direction o Packet contents o Transport protocol o Packet type o Other options o File path and name o Maximum size (bytes) Stale records and Time to Live (TTL) value Scavenging is controlled through a combination of DNS server and zone properties: o Zone properties No-refresh interval Refresh interval o DNS server properties: Scavenge Stale Resource Records Enable automatic scavenging of stale records o Considerations when configuring scavenging Students will learn how to: Enable DNS round robin on a DNS server. Enable scavenging of stale records on a DNS server. Enable scavenging of stale records and aging on Active Directory zones. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Windows Server Pro: Manage and Administer Exam Objectives: 4.0 DNS Configuration. o Manage dynamic DNS updates Create DNS records Configure DNS Round Robin Configure DNS aging and scavenging 70-411 Exam Objectives: 302. Configure DNS records. o Configure record options including Time to Live (TTL) and weight o Configure round robin o Configure secure dynamic updates Lecture Focus Questions: How do stale records affect DNS server performance? When is a DNS record considered stale? How does the no-refresh interval affect scavenging? When should you activate debug logging? For what period of time? Where do you enable scavenging? Video/Demo 4.6.1 DNS Server Properties 4.6.2 Exploring DNS Server Properties Total Time 0:33 6:21 6:54 Lab/Activity Configure DNS Round Robin Configure DNS Aging and Scavenging Number of Exam Questions 9 questions Total Time About 35 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 5.1: Routing Summary This section discusses routing. The following details are covered: The role of routers Static route Route metric Default route Persistent route Managing routing table entries: o View the IPv4 or IPv6 routing table o Add an IPv4 static route o Change a route o Add an IPv6 static route o Delete a route Considerations when creating routes Characteristics of RIP Features of RIP that can be configured: o Packet Protocol o Authentication o Route Filters o Neighbors o Timers o Clean-up Updates o VLSM Students will learn how to: Install Routing and Remote Access on a server and configure it to function as a router. Enable LAN routing on a server using the Configure and Enable Routing and Remote Access wizard. Using metrics, configure static routes on a server with subnets to make additional networks accessible. Configure RIP by adding the RIP protocol and adding interfaces to run RIP. Windows Server Pro: Manage and Administer Exam Objectives: 5.0 Routing and Remote Access Configuration. o Configure LAN routing Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 70-411 Exam Objectives: 303. Configure VPN and routing. o Install and configure the Remote Access role Configure routing Lecture Focus Questions: Which role do you install on a Windows server to get the routing component? What is the purpose of a default route? Under what circumstances can you most effectively use static routes? Which switch used with route add allows you to make a route permanent? Which routes are automatically added to the routing table when routing is enabled? Which routing protocols does Windows Server 2012 support? What is the difference between RIP version 2 and RIP? Why has RIP version 2 become the standard? What is Silent RIP and how does it affect learning and sharing routes? What affect does configuring neighbors have on RIP broadcasts and multicasts? What is route summarization? Video/Demo Time 5.1.1 Routing and Remote Access 5.1.2 Installing RRAS 5.1.4 Routing 5.1.5 Configuring Routing 2:02 3:07 7:48 17:00 Total 29:57 Lab/Activity Add Role Services for Routing and Remote Access Enable LAN Routing Add Static Routes Configure RIP Routing Number of Exam Questions 6 questions Total Time About 65 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 5.2: Network Address Translation (NAT) Summary This section discusses the role of NAT and configuring a NAT router. Students will learn how to: Configure a server as a NAT router. Configure a NAT router to provide DHCP and DNS proxy services. Windows Server Pro: Manage and Administer Exam Objectives: 5.0 Routing and Remote Access Configuration. o Configure Network Address Translation (NAT) routing 70-411 Exam Objectives: 303. Configure VPN and routing. o Install and configure the Remote Access role o Configure routing Lecture Focus Questions: What does a NAT router do? What are the address ranges you can use when deploying NAT? How can NAT provide security for a private network? Video/Demo Time 5.2.1 NAT 5.2.2 Implementing NAT 3:18 15:17 Total 18:35 Lab/Activity Configure NAT Number of Exam Questions 6 questions Total Time About 30 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 5.3: Virtual Private Networks (VPN) Summary This section discusses using a Virtual Private Network (VPN) to support secured communications over an untrusted network. VPN protocols that are supported: o Point-to-Point Tunneling protocol (PPTP) o Layer Two Tunneling Protocol (L2TP) o Secure Socket Tunneling Protocol (SSTP) o Internet Key Exchange 2 (IKEv2) Comparison of authentication protocols: o Password Authentication Protocol (PAP) o Challenge Handshake Authentication Protocol (CHAP) o Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2) o Extensible Authentication Protocol-Transport Layer Security (EAPTLS) Configuration tasks to configure a VPN Server: o Enable remote access o Configure ports o Configure addressing o Configure network policies The role of Web Application Proxy Settings used for VPN connections on Windows clients: o General o Options o Security o Networking o Sharing The role of VPN Reconnect Students will learn how to: Configure a server as a VPN remote access server. Windows Server Pro: Manage and Administer Exam Objectives: 5.0 Routing and Remote Access Configuration. o Configure a VPN server Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 70-411 Exam Objectives: 303. Configure VPN and routing. o Configure VPN settings o Configure remote dial-in settings for users o Configure routing o Configure Web Application proxy in pass-through mode Lecture Focus Questions: Which VPN protocols does Windows support? Which authentication protocols support smart card use? What makes CHAP vulnerable to security breaches? What type of security environments use EAP? Video/Demo Time 5.3.1 VPN 5.3.4 Configuring VPN 5.3.5 Configuring Web Application Proxy 5:43 20:39 11:38 Total 38:00 Lab/Activity Configure a VPN Server Number of Exam Questions 15 questions Total Time About 65 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 5.4: Network Policy Server Summary This section discusses using the Network Policy Server for authorization of remote clients. Concepts covered include: The role of authorization Components of a network policy: o Conditions o Constraints o Permissions o Settings The process used for authentication when a remote access connection is requested Students will learn how to: Create and configure a connection request policy with conditions, permissions, authentications, and constraints. Create and save NPS templates that can be used later when configuring other features of NPS. Windows Server Pro: Manage and Administer Exam Objectives: 5.0 Routing and Remote Access Configuration. o Create Network Policy Server (NPS) policies 70-411 Exam Objectives: 402. Configure NPS policies. o Configure connection request policies o Configure network policies for VPN clients (multilink and bandwidth allocation, IP filters, encryption, IP addressing) o Manage NPS templates o Import and export NPS policies Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: What is the difference between authorization and authentication? What is the difference between constraints and conditions? How are they similar? What happens to a connection that matches the policy conditions but not the policy constraints? How many other policies will be checked in this scenario? Where does the server find the permissions for a connection? What must occur before settings are applied? Video/Demo 5.4.1 NPS Policies for VPN Clients 5.4.3 Exploring NPS Policies for VPN Clients 5.4.6 Using NPS Templates Total Time 3:49 11:53 3:12 18:54 Lab/Activity Create a Network Access Policy 1 Create a Network Access Policy 2 Number of Exam Questions 8 questions Total Time About 40 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 5.5: RADIUS Summary This section examines using network policies stored on a RADIUS server to authenticate remote access clients from multiple servers. Concepts covered include: Components of a RADIUS solution: o Remote access clients o RADIUS client o RADIUS server o RADIUS proxy o Remote RADIUS server group o Network policies o Connection request policies o RADIUS Accounting o NPS templates o User account databases o RADIUS messages Configuration components and tasks to configure a RADIUS solution: o RADIUS server o RADIUS client o Remote access client o RADIUS proxy o RADIUS Accounting Best practices for configuring NPS for RADIUS RADIUS Accounting o Types of events to log on the RADIUS server: Accounting requests Authentication requests Periodic status information logs o Types of logging that can be configured: Local file logging SQL server logging Students will learn how to: Configure a remote access server as a RADIUS client. Configure a RADIUS server. Configure a RADIUS proxy by configuring Remote RADIUS Server groups and Connection Request policies. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Windows Server Pro: Manage and Administer Exam Objectives: 5.0 Routing and Remote Access Configuration. o Configure a RADIUS authentication solution o Implement a RADIUS proxy server 70-411 Exam Objectives: 401. Configure Network Policy Server (NPS). o Configure multiple RADIUS server infrastructures o Configure a RADIUS server o Configure RADIUS clients o Manage RADIUS templates o Configure RADIUS accounting o Configure certificates Lecture Focus Questions: When using a RADIUS solution, where are network access policies configured? What is the difference between a RADIUS client and a remote access client? Why would you implement a RADIUS proxy? What is the difference between a RADIUS client and a RADIUS proxy? What is the difference between a connection request policy and a network access policy? How does the RADIUS proxy use the remote RADIUS server group when processing authentication requests? Video/Demo Time 5.5.1 RADIUS Concepts 5:58 5.5.2 Configuring RADIUS Clients 7:28 5.5.3 Configuring RADIUS Accounting 2:44 5.5.4 Configuring a Multi-server RADIUS Infrastructure 4:29 5.5.5 Configuring Connection Request Policies 10:07 Total 30:46 Lab/Activity Configure a RADIUS Solution Configure a RADIUS Proxy Number of Exam Questions 10 questions Total Time About 60 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 5.6: Network Access Protection Summary This section discusses using Network Access Protection (NAP) to allow administrators to regulate network access or communication based on a computer’s compliance with health requirement policies. Concepts covered include: Features of NAP o Health state validation o Health policy compliance o Limited access network Components that comprise the NAP system: o NAP Client o NAP Server o Enforcement Server (ES) o Remediation Server Steps to configure the NAP server Steps to configure the client computer Configuration steps for the following enforcement points: o DHCP o VPN o 802.1x o Remote Desktop Gateway o IPsec Students will learn how to: Configure a DHCP server as an enforcement point. Configure SHV settings, remediation server groups, health policies, and network policies for NAP. Enable NAP enforcement on a client computer. Windows Server Pro: Manage and Administer Exam Objectives: 5.0 Routing and Remote Access Configuration. o Implement a Network Access Protection (NAP) by creating the following policies: Security Health Validator Health Network Connection Request 70-411 Exam Objectives: Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 403. Configure Network Access Protection (NAP). o Configure System Health Validators (SHVs) o Configure health policies o Configure NAP enforcement using DHCP and VPN o Configure isolation and remediation of non-compliant computers using DHCP and VPN o Configure NAP client settings Lecture Focus Questions: Why is a non-compliant computer not necessarily an immediate security threat? What happens to a computer that receives a limited access health state validation? What functions are performed by the System Health Validator (SHV)? Which NAP component do you modify to identify the health checks that should be performed? How do remediation servers and auto-remediation help clients become compliant? Which type of communication occurs in the boundary network when using IPsec enforcement? Video/Demo Time 5.6.1 Overview of NAP 10:10 5.6.3 Configuring NAP Enforcement using DHCP 14:08 5.6.4 Configuring Auto-remediation 0:58 5.6.5 Configuring NAP Enforcement using VPN 12:31 Total 37:47 Lab/Activity Configure a System Health Validator Number of Exam Questions 13 questions Total Time About 65 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 5.7: DirectAccess Summary This section discusses using DirectAccess to connect through an Internet connection to a corporate intranet. Details covered include: How DirectAccess works DirectAccess connection methods: o Full enterprise network access (end-to-edge) o Selected server access (modified end-to-edge) o End-to-end The process that DirectAccess clients use to connect to intranet resources DirectAccess requirements: o Infrastructure o Server o Client DirectAccess configuration components: o Server o Client side Students will learn how to: Prepare a server with the server requirements to set up DirectAccess. Build the infrastructure for DirectAccess by configuring DNS and certificates to support DirectAccess. Deploy DirectAccess by identifying remote clients, defining the remote access server, setting up the infrastructure servers, and identifying internal application servers. 70-411 Exam Objectives: 304. Configure DirectAccess. o Implement server requirements o Implement client configuration o Configure DNS for DirectAccess o Configure certificates for DirectAccess Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Lecture Focus Questions: What are the advantages of using DirectAccess to access corporate file servers? What is the difference between full enterprise network access and selected server access? What are the requirements for a DirectAccess server? How does the client's IP address configuration affect how the client sends traffic to the DirectAccess server? Video/Demo 5.7.1 DirectAccess Overview 5.7.3 DirectAccess Requirements 5.7.4 Implementing Server Requirements for DirectAccess 5.7.5 Configuring DNS for DirectAccess 5.7.6 Configuring Certificates for DirectAccess 5.7.7 Configuring DirectAccess Total Time 7:34 6:34 7:15 2:33 12:12 6:55 43:03 Number of Exam Questions 11 questions Total Time About 65 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 6.1: Windows Software Update Services (WSUS) Summary This section examines using the Windows Software Update Services (WSUS) to update software. Details covered include: WSUS advantages Components of WSUS: o Microsoft Update o Windows Server Update Services (WSUS) server o Automatic Updates WSUS deployment scenarios: o Single WSUS server o Multiple independent servers o Multiple synchronized servers o Disconnected WSUS server Products that Microsoft Update and WSUS support updating: o Windows operating systems o Exchange Server o SQL Server o Microsoft Office Control updates based on the following criteria: o Product family (such as operating system version or product o Update classification (such as critical updates or drivers) o Language Considerations for configuring WSUS on the server: o Installation o Configure the server o Approve updates o Add downstream servers Automatic Update policies: o Configure Automatic Updates o Specify Intranet Microsoft Update Service Location o Enable Client-Side Targeting o Reschedule Automatic Updates Scheduled Installations o No Auto-Restart with Logged On Users for Scheduled Automatic Updates Installations o Automatic Updates Detection Frequency o Allow Automatic Updates Immediate Installation o Re-prompt for Restart with Scheduled Installation o Allow Non-administrators to Receive Update Notifications o Do Not Display ‘Install Updates and Shut Down’ Option in Shut Down Windows Dialog Box Settings in the Configure Automatic Updates policy: o Download Option Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Automatic Notification o Installation Option Automatic (Scheduled) Notification Targeting provides different updates based on group membership Groups are created on the WSUS server through the console Client computers are assigned to a group with: o Server-side targeting o Client-side targeting Facts to be aware of when using computer groups Students will learn how to: Install WSUS and configure a WSUS server to download updates from Microsoft Update. Synchronize and approve updates. Run reports to view client and update information. Control client update behavior through Group Policy. Create computer groups for targeting, and manually modify group membership. Enable client-side targeting on the WSUS server. Configure client-side targeting through Group Policy. Windows Server Pro: Manage and Administer Exam Objectives: 6.0 Deployment Manager. o Configure a WSUS server o Control access to WSUS updates using the following: Computer groups Client-side targeting 70-411 Exam Objectives: 102. Implement patch management. o Install and configure the Windows Server update Services (WSUS) role o Configure group policies for updates o Configure client-side targeting o Configure WSUS synchronization o Configure WSUS groups o Manage patch management in mixed environments Lecture Focus Questions: How do clients receive updates in the absence of WSUS? What are the disadvantages that this method poses for your network? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. When should you deploy multiple, independent WSUS servers? How is this configuration similar to a single WSUS server? How would you deploy WSUS when an Internet connection is not allowed for an isolated network? What is the difference between synchronizing updates, downloading updates, and approving updates? By default, how often does the client check for updates? Which policy allows you to have clients check more frequently? Which policy points clients to your WSUS server instead of the Microsoft Update Web site? When using client-side targeting, how do you identify the computer group for a specific computer? How does this differ from server-side targeting? Video/Demo 6.1.1 WSUS Overview and Concepts 6.1.3 Installing WSUS 6.1.4 Configuring WSUS 6.1.7 WSUS GPOs and Groups 6.1.8 Configuring WSUS Group Policies Total Time 5:42 5:32 10:06 2:48 5:43 29:51 Lab/Activity Configure a Downstream Server Configure Computer Groups Configure Client-side Targeting Number of Exam Questions 10 questions Total Time About 65 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 6.2: Windows Deployment Services (WDS) Summary This section discusses using the Windows Deployment Services (WDS) to enable the deployment of Windows operating systems to client and server computers. Details covered include: Types of WDS images: o Install Image o Boot Image o Capture Boot Image o Discover Boot Image Condition under which WDS can be used to deploy virtual hard disk images Server and network requirements for Windows Deployment Services Clients requirements for using WDS to install a Windows operating system Prestaging a computer account Managing computer accounts used by WDS PXE response methods: o Do not respond to any client computer o Respond only to known client computers o Respond to all (known and unknown) client computers Methods to control how computer accounts are created Students will learn how to: Add the Windows Deployment Services server role and install the Deployment Server and Transport Server role services. Configure and manage settings for the WDS server. Prestage computer accounts to control which computers will respond to WDS servers. Windows Server Pro: Manage and Administer Exam Objectives: 6.0 Deployment Manager. o Install and configure a WDS server o Create WDS images 70-411 Exam Objectives: 101. Deploy and manage server images. o Install the Windows Deployment Services (WDS) role o Configure and manage boot, install, and discover images Lecture Focus Questions: Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Which operating systems can be deployed with Windows Deployment Services (WDS)? When would you use a discover boot image? When would you use a capture boot image? Why doesn't this boot image run on a WDS client that needs to install the operating system? How do you enable a non-PXE client to use WDS to install an operating system? How would you deploy a .VHD image using WDS? Video/Demo 6.2.1 WDS Overview 6.2.2 Imaging Concepts 6.2.4 Installing WDS 6.2.5 Configuring WDS Total Time 3:58 4:33 1:09 6:47 16:27 Lab/Activity Configure a WDS Server Pre-stage Computer Accounts Number of Exam Questions 9 questions Total Time About 45 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 6.3: WDS Image Management Summary This section discusses management of WDS images. Details covered include: Considerations when configuring multicasting with WDS Use the WDS console to view and manage multicast transmission that are in progress Tools to manage WDS images o Windows Preinstallation Environment (WinPE) o System Preparation Tool (Sysprep) o Deployment Image Servicing and Management (DISM.exe) o ImageX o Windows System Image Manager (Windows SIM) o WDSUtil Windows PowerShell cmdlets to perform common tasks in WDS Facts about WDS images Students will learn how to: Configure WDS server properties for multicast. Configure WDS multicast transmissions. Create image groups and add install images. Add boot images to WDS. Windows Server Pro: Manage and Administer Exam Objectives: 6.0 Deployment Manager. o Create WDS images o Control access to images o Deploy images to clients 70-411 Exam Objectives: 101. Deploy and manage server images. o Update images with patches, hotfixes, and drivers o Install features for offline images o Configure driver groups and packages Lecture Focus Questions: How does multicasting differ from unicasting? How does auto-cast differ from scheduled-casting? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. You have enabled scheduled-casting without a start condition. What must you do for a client to obtain an image using multicasting? What is the difference between deleting and deactivating a multicast transmission? Which two ways can you force a client currently using multicast to use unicast to complete the installation? How do you split a multicast transmission so that faster clients are not slowed down by slower clients? What are the differences between Sysprep, ImageX, and DISM? When can you use each tool? Which tasks can only be performed by one tool? Which type of boot image can you use to deploy a 64-bit install image? What is the relationship between a .wim file and a .rwm file? What is the advantage of dynamic driver provisioning? Video/Demo 6.3.1 Managing Images 6.3.3 Updating Images with Features Total Time 10:30 13:43 24:13 Lab/Activity Create WDS Images Create a Multicast Transmission Number of Exam Questions 10 questions Total Time About 50 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 6.4: Performance Monitor Summary This section discusses Performance Monitor and the other tools that can be used to monitor the reliability and performance of a Windows Server 2012 system: Task Manager Resource Monitor Reliability Monitor Performance Monitor Data Collector Sets Students will learn how to: Use Performance Monitor to create a data collector and configure the settings. Use Performance Monitor to set alerts that will be triggered when a condition is met. Use Task Manager, Resource Monitor and Performance Monitor to monitor real-time performance. 70-411 Exam Objectives: 103. Monitor servers. o Configure Data Collector Sets (DCS) o Configure alerts o Monitor real-time performance o Monitor virtual machines (VMs) o Schedule performance monitoring Lecture Focus Questions: Which tool uses the System Stability Index number? What would a System Stability Index number of 2 indicate? What is the main difference between Task Manager and Resource Monitor when it comes to monitoring the server? Performance Monitor uses objects and counters to track performance. What is the difference between an object and a counter? Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Video/Demo 6.4.1 Overview of Server Monitoring 6.4.2 Performance Monitor (DCS) 6.4.3 Performance Monitor (Alerts) 6.4.4 Real-time Performance Monitoring Total Time 4:24 8:43 4:26 4:57 22:30 Number of Exam Questions 13 questions Total Time About 40 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 6.5: Event Viewer Summary This section discusses using Event Viewer to view and manage local and remote logs. Details covered include: Common event logs include: o Application o Security o System o Setup o ForwardedEvents Features available with event logs: o Log size o Save events o Filter events o Custom views o Attach a Task o Event Log Online Help Computers running the following versions of Windows can be configured as collector systems: o Windows Server 2003 R2 or later o Windows Vista or later Computers running the following versions of Windows can be configured as source systems: o Windows XP with SP2 or later o Windows Server 2003 with SP1 or later Event subscriptions use the following services: o Windows Remote Management (WinRM) o Windows Event Collector (Wecsvc) Subscription type and source computers: o Collector initiated o Source computer initiated Delivery optimization options: o Normal o Minimize bandwidth o Minimize latency o Custom Configuring subscription types: o Collector initiated o Source initiated Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Students will learn how to: View events to gather information, such as Event ID, Log Name, User, and Computer. Create event filters and custom views. Search and save logs. Attach tasks to events or to logs. Configure subscriptions to pull events from remote machines. 70-411 Exam Objectives: 103. Monitor servers. o Monitor events o Configure event subscriptions o Configure network monitoring Lecture Focus Questions: Which log do you view to troubleshoot errors during a software installation? What options do you have for a log file that has reached its designated capacity? What happens to the data in a log that you save that has a filter on it? How does a custom view differ from adding a filter to a log? How can you combine events from multiple logs into a single report? What tasks can you attach to an event or log? What is the purpose of the Event Log Online Help link inside each event? What two services are required to configure event subscriptions? Where do you go to view events collected from remote computers collected using event subscriptions? Video/Demo 6.5.1 Event Viewer and Event Subscriptions 6.5.2 Exploring Event Viewer 6.5.4 Configuring Event Subscriptions Total Time 4:34 6:57 6:47 18:18 Number of Exam Questions 12 questions Total Time About 35 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Section 6.6: Network Monitor Summary This section discusses using Network Monitor to capture, view, and analyze network traffic. Details covered include: System Requirements o Supported operating systems o Hardware requirements Capture Filter o Display filter o Capture filter Aliases Conversations Parsers Command line Students will learn how to: Configure Network Monitor to capture packets. Configure and remove capture and display filters. Configure conversations to group data by type. Configure aliases to replace IP addresses with names. 70-411 Exam Objectives: 103. Monitor servers. o Configure network monitoring Lecture Focus Questions: What are the differences between display filters and capture filters? What is the difference between capturing in promiscuous mode and capturing without promiscuous mode? When will using promiscuous mode not result in significant differences in the data captured? How can aliases make troubleshooting easier? What permissions do you need to run Network Monitor? Video/Demo 6.6.1 Network Monitoring Time 6:28 Number of Exam Questions 7 questions Total Time About 15 minutes Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Windows Server Pro: Manage and Administer Practice Exams Summary This section provides information to help prepare students to take the Windows Server Pro: Manage and Administer certification exam. Students will have the opportunity of testing their mastery of the concepts presented in this course to reaffirm that they are ready for the certification exam. Students will typically take about 5-10 minutes (depending upon the complexity and their level of knowledge) to complete each simulation question in the following practice exams. There is no time limit on the amount of time a student can take to complete the practice exams for the following domains. Objective 1: Active Directory Management (7 simulation questions) Objective 2: Group Policy Configuration (18 simulation question) Objective 3: File Services Management (6 simulation questions) Objective 4: DNS Configuration (14 simulation questions) Objective 5: Routing and Remote Access Configuration (11 simulation questions) Objective 6: Deployment Management (7 simulation questions) The Windows Server Pro: Manage and Administer Certification Practice Exam consists of 15 simulation questions that are randomly selected from the above practice exams. Each time the Certification Practice Exam is accessed different questions may be presented. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Microsoft 70-411 Practice Exams Summary This section provides information to help prepare students to take the MS 70-411 exam and to register for the exam. Students will have the opportunity of testing their mastery of the concepts presented in this course to reaffirm that they are ready for the certification exam. Students will typically take about 1 minute to complete each question in the following practice exams. There is no time limit on the amount of time a student can take to complete the practice exams for the following domains. Objective 100. Deploy, Manage, and Maintain Servers (61 questions) Objective 200. Configure File and Print Services (69 questions) Objective 300. Configure Network Services and Access (110 questions) Objective 400. Configure a Network Policy Server Infrastructure (31 questions) Objective 500. Configure and Manage Active Directory (76 questions) Objective 600. Configure and Manage Group Policy (63 questions) The Microsoft 70-411 Certification Practice Exam consists of 60 questions that are randomly selected from the above practice exams. Each time the Certification Practice Exam is accessed different questions may be presented. The Certification Practice Exam has a time limit of 2 hours. A passing score of 95% should verify that the student has mastered the concepts and is ready to take the real certification exam. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Appendix A: Approximate Time for the Course The total time for the LabSim Windows Server Pro: Manage and Administer course is approximately 44 hours and 30 minutes. The time is calculated by adding the approximate time for each section which is calculated using the following elements: Video/demo times Approximate time to read the text lesson (the length of each text lesson is taken into consideration) Simulations (5 minutes assigned per simulation, of course many students may take longer depending upon their knowledge level and experience) Questions (1 minute per question) The breakdown for this course is as follows: Module Sections Time Minute HR:MM 20 30 55 30 20 45 50 45 295 4:55 70 35 10 50 30 60 45 35 40 25 400 6:40 1.0 Active Directory 1.1 Active Directory Overview 1.2 Speeding Up Authentication 1.3 Single Master Operations Roles (FSMO) 1.4 Read Only Domain Controllers (RODCs) 1.5 Virtual Domain Controllers 1.6 Service Accounts 1.7 Maintaining Active Directory 1.8 Restoring Active Directory 2.0 Group Policy 2.1 Group Policy Foundation 2.2 Administrative Templates 2.3 Folder Redirection 2.4 Software Deployment 2.5 Security Settings 2.6 Password and Account Policies 2.7 Advanced Auditing 2.8 Preferences 2.9 Group Policy Management 2.10 Management Delegation Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 3.0 File Services 3.1 File Server Resource Manager 3.2 Distributed File System (DFS) 3.3 Distributed File System Replication 3.4 File Encryption 3.5 Disk Encryption 50 25 55 50 50 220 3:50 4.1 DNS Name Resolution 4.2 DNS Forwarding and Delegation 4.3 DNS Zones 4.4 DNS Zone Management 4.5 DNS Records 4.6 DNS Options 25 35 55 45 50 35 245 4:05 65 30 65 40 60 65 65 390 6:30 65 45 50 40 35 15 250 4:10 390 6:30 4.0 DNS 5.0 Remote Access Management 5.1 Routing 5.2 Network Address Translation (NAT) 5.3 Virtual Private Networks (VPN) 5.4 Network Policy Server 5.5 RADIUS 5.6 Network Access Protection 5.7 DirectAccess 6.0 Server Management 6.1 Windows Software Update Services (WSUS) 6.2 Windows Deployment Services (WDS) 6.3 WDS Image Management 6.4 Performance Monitor 6.5 Event Viewer 6.6 Network Monitor Windows Server Pro: Manage & Administer Certification Practice Exam 100. Active Directory Management (7 questions) 200. Group Policy Configuration (18 questions) 300. File Services Management (6 questions) 400. DNS Configuration (14 questions) 35 90 30 70 500. Routing and Remote Access Configuration (11 questions) 600. Deployment Management (7 questions) Certification Practice Exam (15 questions) 55 35 75 Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Microsoft 70-411 Practice Exams 100. Deploy, Manage, and Maintain Servers (61 questions) 200. Configure File and Print Services (69 questions) 61 69 300. Configure Network Service and Access, (110 questions) 110 400. Configure a Network Policy Server Infrastructure (31 questions) 31 500. Configure and Manage Active Directory (76 questions) 76 600. Configure and Manage Group Policy (63 questions) Certification Practice Exam (60 questions) 63 60 Total Time 470 7:50 2660 44:30 Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Appendix B: Exam 70-411: Administering Windows Server 2012 Objectives The Windows Exam 70-411: Administering Windows Server 2012 certification exam covers the following objectives. In the spread sheet below the column to the right lists the sections where the information is located in the course: # Objective 100 Deploy, Manage, and Maintain Servers (17 percent) 101 Deploy and manage server images This objective may include but is not limited to: Module.Section 6.2, 6.3 Install the Windows Deployment Services (WDS) role Configure and manage boot, install, and discover images Update images with patches, hotfixes, and drivers Install features for offline images Configure driver groups and packages 102 Implement patch management This objective may include but is not limited to: 6.1 Install and configure the Windows Server Update Services (WSUS) role Configure group policies for updates Configure client-side targeting Configure WSUS synchronization Configure WSUS groups Manage patch management in mixed environments 103 Monitor servers This objective may include but is not limited to: 6.4, 6.5, 6.6 Configure Data Collector Sets (DCS) Configure alerts Monitor real-time performance Monitor virtual machines (VMs) Monitor events Configure event subscriptions Configure network monitoring Schedule performance monitoring 200 Configure File and Print Services (15 percent) Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 201 Configure Distributed File System (DFS) This objective may include but is not limited to: 3.2, 3.3 Install and configure DFS namespaces Configure DFS Replication Targets Configure Replication Scheduling Configure Remote Differential Compression settings Configure staging Configure fault tolerance 202 Configure File Server Resource Manager (FSRM) This objective may include but is not limited to: 3.1 Install the FSRM role Configure quotas Configure file screens Configure reports 203 Configure file and disk encryption This objective may include but is not limited to: 3.4, 3.5 Configure BitLocker encryption Configure the Network Unlock feature Configure BitLocker policies Configure the EFS recovery agent Manage EFS and BitLocker certificates including backup and restore 204 Configure advanced audit policies This objective may include but is not limited to: 2.7 Implement auditing using Group Policy and AuditPol.exe Create expression-based audit policies Create removable device audit policies Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 300 Configure Network Services and Access (17 percent) 301 Configure DNS zones This objective may include but is not limited to: 4.2, 4.3 Configure primary and secondary zones Configure stub zones Configure conditional forwards Configure zone and conditional forward storage in Active Directory Configure zone delegation Configure zone transfer settings Configure notify settings 302 Configure DNS records This objective may include but is not limited to: 4.4, 4.5, 4.6 Create and configure DNS Resource Records (RR) including A, AAAA, PTR, SOA, NS, SRV, CNAME, and MX records Configure zone scavenging Configure record options including Time To Live (TTL) and weight Configure round robin Configure secure dynamic updates 303 Configure VPN and routing This objective may include but is not limited to: 5.1, 5.2, 5.3 Install and configure the Remote Access role Implement Network Address Translation (NAT) Configure VPN settings Configure remote dial-in settings for users Configure routing Configure Web Application Proxy in pass-through mode 304 Configure DirectAccess This objective may include but is not limited to: 5.7 Implement server requirements Implement client configuration Configure DNS for DirectAccess Configure certificates for DirectAccess 400 Configure a Network Policy Server Infrastructure (14 percent) Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 401 Configure Network Policy Server (NPS) This objective may include but is not limited to: 5.5 Configure multiple RADIUS server infrastructures Configure a RADIUS server, including RADIUS proxy Configure RADIUS clients Configure NPS templates Configure RADIUS accounting Configure certificates 402 Configure NPS policies This objective may include but is not limited to: 5.4 Configure connection request policies Configure network policies for VPN clients (multilink and bandwidth allocation, IP filters, encryption, IP addressing) Manage NPS templates Import and export NPS policies 403 Configure Network Access Protection (NAP) This objective may include but is not limited to: 5.6 Configure System Health Validators (SHVs) Configure health policies Configure NAP enforcement using DHCP and VPN Configure isolation and remediation of non-compliant computers using DHCP and VPN Configure NAP client settings 500 Configure and Manage Active Directory (19 percent) 501 Configure service authentication This objective may include but is not limited to: 1.6 Create and configure Service Accounts Create and configure Group Managed Service Accounts Create and configure Managed Service Accounts Configure Kerberos delegation Manage Service Principal Names (SPNs) Configure virtual accounts 502 Configure Domain Controllers This objective may include but is not limited to: 1.2, 1.3, 1.4, 1.5 Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Configure Universal Group Membership Caching (UGMC) Transfer and seize operations masters Install and configure a read-only domain controller (RODC) Configure Domain Controller cloning 503 Maintain Active Directory This objective may include but is not limited to: 1.7, 1.8 Back up Active Directory and SYSVOL Manage Active Directory offline Optimize an Active Directory database Clean up metadata Configure Active Directory snapshots Perform object- and container-level recovery Perform Active Directory restore Configure and restore objects by using the Active Directory Recycle Bin 504 Configure account policies This objective may include but is not limited to: 2.6 Configure domain user password policy Configure and apply Password Settings Objects (PSOs) Delegate password settings management Configure local user password policy Configure account lockout settings Configure Kerberos policy settings 600 Configure and Manage Group Policy (18 percent) 601 Configure Group Policy processing This objective may include but is not limited to: 2.1, 2.9 Configure processing order and precedence Configure blocking of inheritance Configure enforced policies Configure security filtering and WMI filtering Configure loopback processing Configure and manage slow-link processing Configure client-side extension (CSE) behavior Force Group Policy update Configure and manage slow-link processing and Group Policy caching. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 602 Configure Group Policy settings This objective may include but is not limited to: 2.2, 2.3, 2.4, 2.5 Configure settings including software installation, folder redirection, scripts, and administrative template settings Import security templates Import custom administrative template file Convert administrative templates using ADMX Migrator Configure property filters for administrative templates 603 Manage Group Policy objects (GPOs) This objective may include but is not limited to: 2.9, 2.10 Back up, import, copy, and restore GPOs Create and configure Migration Table Reset default GPOs Delegate Group Policy management 604 Configure Group Policy preferences This objective may include but is not limited to: 2.8 Configure Group Policy Preferences (GPP) settings including printers, network drive mappings, power options, custom registry settings, Control Panel settings, Internet Explorer settings, file and folder deployment, and shortcut deployment Configure item-level targeting Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. Appendix C: Windows Server Pro: Manage and Administer Objectives The Windows Server Pro: Manage and Administer certification exam covers the following objectives. In the spread sheet below the column to the right lists the sections where the information is located in the course: # 1.0 Objective Module.Section Active Directory Management 1.2, 1.3, 1.4, 1.7 Implement Global Catalog Servers. Implement Universal Group Membership Caching (UGMC). Manage Flexible Single-Master Operation (FSMO) roles. Implement a Read Only Domain Controller (RODC). Backup Active Directory. 2.0 Group Policy Configuration Manage the Group Policy processing order. Create custom administrative templates by importing GPOs. Deploy software using Group Policy. Implement the following GPO policies: o Security o Account o Fine-grained password o Advanced audit Configure Group Policy preferences. Backup and restore GPOs. Delegate GPO management. 3.0 File Services Management 2.1, 2.2, 2.4 2.5, 2.6, 2.7 2.8, 2.9, 2.10 3.1, 3.2, 3.3 3.4, 3.5 Configure FSRM quotas. Configure FSRM file screens. Implement DFS replication. Encrypt files and folders with EFS. Encrypt the server hard disk with BitLocker. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them. 4.0 DNS Configuration 4.2, 4.3, 4.4 4.5, 4.6 Configure DNS forwarders. Create DNS delegations. Create the following types of DNS zones: o Primary o Secondary o Stub o Reverse-lookup o Active Directory-integrated Manage zone transfers. Manage dynamic DNS updates. Create DNS records. Configure DNS Round Robin. Configure DNS aging and scavenging. 5.0 Routing and Remote Access Configuration 5.1, 5.2, 5.3 5.4, 5.5, 5.6 Configure LAN routing. Configure Network Address Translation (NAT) routing. Configure a VPN server. Create Network Policy Server (NPS) policies. Configure a RADIUS authentication solution. Implement a RADIUS proxy server. Implement Network Access Protection (NAP) by creating the following policies: o Security Health Validator o Health o Network o Connection Request 6.0 Deployment Management 6.1, 6.2, 6.3 Configure a WSUS server. Control access to WSUS updates using the following: o Computer groups o Client-side targeting Install and configure a WDS server. Create WDS images. Control access to images. Deploy images to clients. Copyright © 2015 TestOut Corporation. CompTIA, A+, Network+, Security+, Linux+ and related trademarks and trade names are the trademarks of CompTIA. Microsoft, MCITP, MSCA, MCTS, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. (ISC)2 and SSCP are the trademarks of (ISC)2. TestOut has no affiliation with any of these companies and the products and services advertised herein are not endorsed by any of them.