1-CCNA BRYPHIL - BryPhil Technology
advertisement

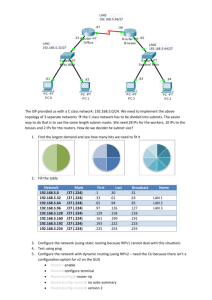
Jan 9, 2015 Tools Hardware; - Router - Switch - Laptop/PC - Console cable - Ethernet Cable (Cat5(e)/Cat6) Software; - CIOS - Packet Tracer ICONS What is a Router? A router is a device that forwards data/voice packets along networks. A router is a device that routes network traffic What is a Switch? A switch serves as a controller, enabling networked devices to talk to each other Managed Unmanaged Device and Port/Interface Identification Exercise 1. 1. 2. 3. 4. Identify a router Identify a switch Identify all interfaces on your router and switch Identify all cables and connectors. Exercise 2 1. Install any terminal of your choice (Putty, secureCRT, Teraterm) 2. Configure serial line connection settings i. Speed = 9600 ii. Data bits = 8 iii. Stop bits = 1 iv. Parity = None v. Flow Control = XON/XOFF 3. Power on devices. 4. Examine the boot process. Packet Tracer The language. - Computers only understand the language of zeros and ones. Binary Understanding IP Addressing Understanding IP Addressing IP Address: A logical numeric address that is assigned to every single computer, printer, switch, router or any other device that is part of a TCP/IP-based network Subnet: A separate and identifiable portion of an organization's network, typically arranged on one floor, building or geographical location Subnet Mask: A 32-bit number used to differentiate the network component of an IP address by dividing the IP address into a network address and host address Network Interface Card (NIC): A computer hardware component that allows a computer to connect to a network Understanding IP Addressing DHCP: Dynamic Host Configuration Protocol (DHCP) is a network protocol that enables a server to automatically assign an IP address to a computer from a defined range of numbers (i.e., a scope) configured for a given network TFTP: Trivial File Transfer Protocol (TFTP) is a simple, lock-step, file transfer protocol which allows a client to get from or put a file onto a remote host. DMARC: The separation point between carrier equipment and CPE. DNS (Domain Name System) A system used on the Internet for translating names of network nodes into addresses. HTTP (Hypertext Transfer Protocol) The protocol used by web browsers and web servers to transfer files, such as text and graphic files. Understanding IP Addressing HTTPS (Hypertext Transfer Protocol Secure) The protocol used by web browsers and web servers to transfer files, such as text and graphic files securely. Port Number A field in a TCP or UDP header that identifies the application that either sent or should receive the data inside the data segment. Common ports include: 80, 443, 110, 21, 3389, 25, 5060 RAM (Random-access Memory) A type of volatile memory that can be read and written by a microprocessor. Understanding IP Addressing NVRAM (Non-Volatile Random-access Memory) A type of non volatile memory that can be read and written by a microprocessor and retains information when powered off. Routing Protocol A protocol that accomplishes routing through the implementation of a specific routing algorithm. Examples include the Interior Gateway Routing Protocol (IGRP), the Open Shortest Path First (OSPF) protocol, and the Routing Information Protocol (RIP). Subnetting. Classful IP Addressing. Subnetting. Subnet Mask based on Class Converting Decimals to Binary . 13 12 11 10 Bits 24 n 2 23 22 21 20 2 raised to bit value 32 16 8 4 2 1 Actuals 224 240 248 252 254 255 Subnet Mask 17 16 15 14 27 26 25 128 64 128 192 1 0 1 0 1 0 1 1 Exercise: Convert 171 to binary n 2 Converting Decimals to Binary . Converting Decimals to Binary . Exercise 2. 1.Question 1: Convert 255 from decimal to binary. 2.Question 2: Convert 187 from decimal to binary. 3.Question 5: Convert 241 from binary to decimal. 4. Question 3: Convert 223 from decimal to binary. 5. Question 4: Convert 240 from decimal to binary. Converting Decimals to Binary . Converting Decimals to Binary . Cisco Devices/ IOS Open Systems Interconnection model (OSI) is a conceptual model that characterizes and standardizes the internal functions of a communication system by partitioning it into abstraction layers. 7. 6. 5. 4. 3. 2. 1. Application Presentation Session Transport Network Data link Physical 7. 6. 5. 4. 3. 2. 1. Anyway Packets Stupid Those Need Don’t People Please Do Not Tell Sales People Anything Physical (Layer 1) It provides the hardware means of sending and receiving data on a carrier, including defining cables, cards and physical aspects. e.g RJ45 Please Do Not Tell Sales People Anything Data Link (Layer 2) At this layer, data packets are encoded and decoded into bits. It furnishes transmission protocol knowledge and management and handles errors in the physical layer, flow control and frame synchronization. The data link layer is divided into two sub layers: The Media Access Control (MAC) layer and the Logical Link Control (LLC) layer. The MAC sub layer controls how a computer on the network gains access to the data and permission to transmit it. The LLC layer controls frame synchronization, flow control and error checking. e.g. PPP, FDDI, ATM, IEEE 802.5/ 802.2, IEEE 802.3/802.2, HDLC Please Do Not Tell Sales People Anything Network (Layer 3) This layer provides switching and routing technologies, creating logical paths, known as virtual circuits, for transmitting data from node to node. Routing and forwarding are functions of this layer, as well as addressing, internetworking, error handling, e.g. AppleTalk, IP, Please Do Not Tell Sales People Anything Transport (Layer 4) This layer provides transparent transfer of data between end systems, or hosts, and is responsible for end-to-end error recovery and flow control. It ensures complete data transfer. e.g SPX, TCP, UDP. Please Do Not Tell Sales People Anything Session (Layer 5) This layer establishes, manages and terminates connections between applications. The session layer sets up, coordinates, and terminates conversations, exchanges, and dialogues between the applications at each end. It deals with session and connection coordination. - e.g. RPC, SQL. Please Do Not Tell Sales People Anything Presentation (Layer 6) This layer provides independence from differences in data representation by translating from application to network format, and vice versa. The presentation layer works to transform data into the form that the application layer can accept. This layer formats and encrypts data to be sent across a network, providing freedom from compatibility problems. TIFF, GIF, JPEG, MPEG, MIDI. Please Do Not Tell Sales People Anything Application (Layer 7) This layer supports application and end-user processes. Communication partners are identified, quality of service is identified, user authentication and privacy are considered, and any constraints on data syntax are identified. file transfers, e-mail, and other network software services. Telnet and FTP are applications that exist entirely in the application e.g. browsers, NFS, SNMP, Telnet, HTTP, FTP Please Do Not Tell Sales People Anything 3:1 1:1 1:1 2:1 Please Do Not Tell Sales People Anything Please Do Not Tell Sales People Anything Please Do Not Tell Sales People Anything Please Do Not Tell Sales People Anything Which of the following correctly describe steps in the OSI data encapsulation process? (Choose two) A. The transport layer divides a data stream into segments and may add reliability and flow control information. B. The data link layer adds physical source and destination addresses and an FCS to the segment. C. Packets are created when the network layer encapsulates a frame with source and destination host addresses and protocol-related control information. D. Packets are created when the network layer adds Layer 3 addresses and control information to a segment. E. The presentation layer translates bits into voltages for transmission across the physical link. Please Do Not Tell Sales People Anything A network administrator is verifying the configuration of a newly installed host by establishing an FTP connection to a remote server. What is the highest layer of the protocol stack that the network administrator is using for this operation? A. application B. presentation C. session D. transport E. internet F. data link Please Do Not Tell Sales People Anything A receiving host computes the checksum on a frame and determines that the frame is damaged. The frame is then discarded. At which OSI layer did this happen? A. session B. network C. physical D. data link E. transport Please Do Not Tell Sales People Anything At which layer of the OSI model is RSTP used to prevent loops? A. data link B. network C. physical D. transport Please Do Not Tell Sales People Anything Please Do Not Tell Sales People Anything Routers are Computers Routers are at the Center of every Network What is a Router? Main Function Is to router or forward packets destined for local and remote network by determining best path What is a Router? Routers are Computers CPU RAM ROM Operating system CPU RAM ROM Flash memory NVRAM Cisco Devices/ IOS CPU The CPU executes operating system instructions such as 1. System initialization 2. Routing Functions 3. Network interface Control RAM Stores information or instructions needed to be executed such as 1. 2. 3. 4. Operating system (Copied to RAM during bootup) Running Configuration IP Routing Tables ARP Cache (Maps IP addresses to MAC addresses) ROM Read only memory is permanent storage. Cisco devices use ROM to store 1. Bootstrap instructions 2. Basic diagnostics software 3. A scaled down version of IOS Flash Memory This is non volatile computer memory that can be electronically erased and reprogrammed. It is used as a permanent storage of the; 1. Operating system (CIOS) NVRAM This is also non volatile Random Access Memory which is used to store 1. The start-up configuration file. The Boot Process The Boot Process The Boot Process The Boot Process A Cisco router is booting and has just completed the POST process. It is now ready to find and load an IOS image. What function does the router perform next? A. It checks the configuration register B. It attempts to boot from a TFTP server C. It loads the first image file in flash memory D. It inspects the configuration file in NVRAM for boot instructions CLI Configuration and Addressing-Basic Router Configuration User EXEC Mode The default command mode for the CLI is user EXEC mode. the user EXEC commands allow you to connect to remote devices, perform basic tests, and list system information. Router>. Privileged EXEC Mode Privileged EXEC mode is password protected, and allows the use of all EXEC mode commands available on the system. Router# . Global Configuration Mode Global configuration commands generally apply to features that affect the system as a whole, rather than just one protocol or interface. Router(config)# . ROM Monitor Mode, and Setup Mode (ignore) Basic Router Configuration When configuring a router, certain basic tasks are performed. Including the following 1. Name the router. 2. Setting password. 3. Configuring interfaces. 4. Configuring a banner. 5. Saving changes on a router. 6. Verifying basic configuration and router operations. Appendix 1A A network administrator needs to allow only one Telnet connection to a router. Which set of commands will accomplish this task? A. access-list 1 permit 192.168.1.0 0.0.0.255 line vty 0 4 login password cisco access-class 1 B. enable password secret line vty 0 login password cisco C. line vty 1 login password cisco D. line vty 0 4 login password cisco Subnet Mask / # of Host Routers are at the Center of every Network Subnet Mask / # of Host n 2 Subnets = n Host = 2 -2 n= # of borrowed bits Subnet Mask / # of Host 16 hosts < 25 – 2 (we need to borrow 5 bits -> /27) 11 hosts < 24 – 2 (borrow 4 bits -> /28) 5 hosts < 23 – 2 (borrow 3 bits -> /29) Subnet Mask / # of Host Convert the following binary to decimal--01101101. 225 109 1101 112 Subnet Mask / # of Host What address Class does 172.16.33.1/24 belong to? Class A Class B Class C Class D Subnet Mask / # of Host When calculating usable hosts per subnet, the following formula is used 2^bits - 2. For what reason is two subtracted? (choose two) Broadcast Multicast Unicast Network Subnet Mask / # of Host Your organization is designing a Wide Area Network. Locations have varying numbers of hosts. The largest network will have no more than 55 hosts. What subnet mask accomplishes the goal and maximizes the number of subnets that may be created? A: 255.255.255.192 B: /25 C: 255.255.255.224 D: /27 Subnet Mask / # of Host What are two ways to represent a network mask that would allow 14 hosts? A: /14 B: 255.255.255.240 C: 255.255.14.0 D: /28 Subnet Mask / # of Host Based on 1.1.1.0/24, the IP address would be: Class A Class B Class C Class D Subnet Mask / # of Host How many hosts can be located on a network, where the IPv4 netmask is 27 bits? A: 27 B: 30 C: 32 D: 5 Appendix 1B-1 Appendix 1B Cisco Discovery Protocol CDP CDP is primarily used to obtain protocol addresses of direct neighboring devices and discover the platform of those devices Command Router(config)# cdp run Purpose Enables CDP on the system. Router(config)# no cdp run Disables CDP on the system. Router(config-if)# cdp enable Enables CDP on an interface. Router(config-if)# no cdp enable Disables CDP on an interface. Router# show cdp neighbour Collision & Broadcast domain A collision domain is, as the name implies, a part of a network where packet collisions can occur. A collision occurs when two devices send a packet at the same time on the shared network segment. The packets collide and both devices must send the packets again, which reduces network efficiency. HUB and SWITCHES A broadcast domain is a domain in which a broadcast is forwarded. A broadcast domain contains all devices that can reach each other at the data link layer (OSI layer 2) by using broadcast. All ports on a hub or a switch are by default in the same broadcast domain. All ports on a router are in the different broadcast domains and routers don't forward broadcasts from one broadcast domain to another. ROUTER ICONS Routing Protocols RIP 1. Routing protocols enable routers to know where to forward packets. 2. Information about where a router should send specific packets are stored in the ROUTING TABLE. Types of routes. 1. Connected Routes 2. Static Routes 3. Dynamics routes. Routes 1.Routing tables store information about other destinations subnets (Subnet number and subnet mask) 2.They contain the direction which tells the router what other routers or host to send packets next(Outgoing interface and nexthop router Learning Connected Routes Subnets to which routers interfaces are connected are called DIRECTLY CONNECTED ROUTES. A router adds a directly connected route for each interface that has been configured with an IP address, and its up and working to its database. Next Hop Next Hop Next Hop LAB Static Route Administrative distance Administrative distance is the feature that routers use in order to select the best path when there are two or more different routes to the same destination from two different routing protocols. Administrative distance defines the reliability of a routing protocol. Each Routing Protocol has its default administrative distance. Administrative distance The Default Administrative distance for RIP is 120 Routing Information Protocol (RIP) • Routing Protocols exchange routing table information • Therefore, they learn routing information about IP subnets from their neighboring routers • They advertise routing information with their neighboring routers • If more than one route exist for each subnet, they chose the best route. (HOW DO THEY DO THIS?) • If a link fails (topology changes) they react by advertising that some routes have failed and pick a new currently best route (Convergence) Routing Information Protocol (RIP) All routing protocols use a metric A metric simply determines how good each route is. Hop-count tells the router how many more routers a packet has to traverse to get to its destination. Next Hop Refer to the exhibit, Host A pings interface S0/0 on router 3, what is the TTL value for that ping ? A. 253 B. 252 C. 255 D. 254 Next Hop Refer to the exhibit, Host A pings interface S0/0 on router 3, what is the TTL value for that ping ? Refer to the exhibit. A network administrator attempts to ping Host2 from Host1 and receives the results that are shown. What is a possible problem? A. The link between Host1 and Switch1 is down. B. TCP/IP is not functioning on Host1 C. The link between Router1 and Router2 is down. D. The default gateway on Host1 is incorrect. E. Interface Fa0/0 on Router1 is shutdown. F. The link between Switch1 and Router1 is down. LAB RIP Configuring RIP v2 on a Network. BryPhil#configure terminal BryPhil(config)#router rip BryPhil(config-router)#version 2 BryPhil(config-router)#no auto summary BryPhil(config-router)#network 192.168.1.0 BryPhil(config-router)#network 192.168.2.0 BryPhil(config-router)#network 172.16.1.0 BryPhil(config-router)#network 172.16.2.0 BryPhil(config-router)#end BryPhil#copy run start LAB RIP Review HINT A network administrator is verifying the configuration of a newly installed host by establishing an FTP connection to a remote server. What is the highest layer of the protocol stack that the network administrator is using for this operation? A. Application B. Presentation C. Session D. Transport E. Internet F. Data link Routing Protocol OSPF RIP v1 RIPv2 OSPF Distance Vector Classful Hop-count Slow Convergence Distance Vector Classless Hop-Count Slow Convergence Less CPU Less complex Link-State Classless Bandwidth/Cost Fast Convergence Less CPU Less complex More CPU More complex More OSPF OSPF Cost Calculation and Path Determination OSPF Cost Calculation and Path Determination OSPF Cost Calculation and Path Determination Link-state Routing Process 1. R1; Ethernet network 10.1.0.0/16; Cost 2 2. R1 -> R2; Serial point-to-point network; 10.2.0.0/16; Cost 20 3. R1 -> R3; Serial point-to-point network; 10.3.0.0/16; Cost 5 4. R1 -> R4; Serial point-to-point network; 10.4.0.0/16; Cost 20 Routers in other areas learn that this route is down, but this is done with a type of LSP that does not cause them to rerun their SPF algorithm. Routers in other areas can update their routing tables directly Route source - Identifies how the route was learned. Destination network - Identifies the address of the remote network. Administrative distance - Identifies the trustworthiness of the route source. Metric - Identifies the value assigned to reach the remote network. Lower values indicate preferred routes. Next hop - Identifies the IPv4 address of the next router to forward the packet to. Route timestamp - Identifies from when the route was last heard. Outgoing interface - Identifies the exit interface to use to forward a packet toward the final destination. Router(config)# router ospf process_ID Router(config-router)# network IP_address wildcard_mask area_# R4(config)#router ospf 4 R4(config-router)#network X.X.X.X xxx.xxx.xxx.xxx area 0 R4(config-router)#network X.X.X.X xxx.xxx.xxx.xxx area 0 R4(config-router)# X.X.X.X = IP Address xxx.xxx.xxx.xxx = wild card mask