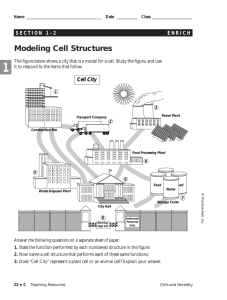
Networks
advertisement

Computers Are Your Future © 2005 Prentice-Hall, Inc. Computers Are Your Future Chapter 6 Computers Are Your Future Chapter 6 Networks: Communicating and Sharing Resources © 2005 Prentice-Hall, Inc Slide 2 Computers Are Your Future Chapter 6 What You Will Learn About Basic networking concepts The three major types of physical media Bandwidth How modems transform digital computer signals into analog signals Circuit switching and packet switching networks © 2005 Prentice-Hall, Inc Slide 3 Computers Are Your Future Chapter 6 What You Will Learn About The importance of protocols in a computer network The advantages of a network Peer-to-peer and client/server LANs The most widely used LAN protocol Ways that businesses use WANs © 2005 Prentice-Hall, Inc Slide 4 Computers Are Your Future Chapter 6 Network Fundamentals A computer network consists of two or more computers linked together to exchange data and share resources. Communications is the process of sending and receiving messages. Communications channels are the paths through which messages are passed. Communications devices transform electronic signals. © 2005 Prentice-Hall, Inc Slide 5 Computers Are Your Future Chapter 6 Physical Infrastructure Physical infrastructure refers to cables, modems, switches, and routers. Twisted-pair – Two insulated wires twisted around each other; the same type of wire as that used for telephones Types of twisted-pair technologies: Leased line (T1) Integrated Services Digital Network (ISDN) Digital Subscriber Line (DSL) Coaxial cable – Consists of an insulated center wire surrounded by a layer of braided wire; the same type of wire as that used for cable TV Fiber-optic cable – Type of fiber glass cable that transmits data in the form of light impulses; can carry more data for longer distances than other wire © 2005 Prentice-Hall, Inc Slide 6 Computers Are Your Future Chapter 6 Bandwidth Bandwidth is the amount of data that can be transmitted through a communications channel. Digital bandwidth is measured in bits per second (bps), kilobits per second (Kbps), megabits per second (Mbps), or gigabits per second (Gbps). Low bandwidth is 56 Kbps and high bandwidth is 622 Mbps. © 2005 Prentice-Hall, Inc Slide 7 Computers Are Your Future Chapter 6 Modems: From Digital to Analog and Back Modulation Analog Digital Demodulation Analog Digital Modems are devices that transform signals when sending and receiving transmissions. Modulation – Transforming digital signals to analog Demodulation – Transforming analog signals to digital © 2005 Prentice-Hall, Inc Slide 8 Computers Are Your Future Chapter 6 Modems: From Digital to Analog and Back Internal Modem External Modem Two types of modems: Internal modems – Fit into a computer’s expansion slot External modems – Connect to a port outside the system box © 2005 Prentice-Hall, Inc Slide 9 Computers Are Your Future Chapter 6 Asynchronous and Synchronous Communications Asynchronous communication is a method of networking in which bits of data are sent and received one bit at a time; each byte contains a start and stop bit. Synchronous communication requires a synchronization signal that identifies units of data. © 2005 Prentice-Hall, Inc Slide 10 Computers Are Your Future Chapter 6 Modulation Protocols Modulation protocols are communications standards that modems conform to. Data transfer rate is the rate at which two modems can exchange data. It is measured in bits per second (bps). A modulation protocol called V.90 enables modems to transfer data at 56 Kbps. © 2005 Prentice-Hall, Inc Slide 11 Computers Are Your Future Chapter 6 Cable Modems Cable modems enable computers to access the Internet by way of a cable TV connection. Data is transferred through a coaxial cable. Bandwidths range from 500 Kbps to 1 Mbps. Bandwidth is divided among the number of subscribers using it. © 2005 Prentice-Hall, Inc Slide 12 Computers Are Your Future Chapter 6 Switching and Routing Techniques Packet switching Circuit switching Networks create an endto-end circuit between the sending and receiving computers. Electronic switches establish and maintain the connection. © 2005 Prentice-Hall, Inc Outgoing messages are divided into fixed-size data units called packets. Packets are numbered and addressed to the receiving computer. Routers examine the packets and send them to their destination. Slide 13 Computers Are Your Future Chapter 6 Advantages and Disadvantages of Circuit and Packet Switching Advantages Disadvantages Circuit switching Voice and real-time transmission No delivery delays Costly A direct electrical connection between the computers is required Packet switching Efficient, less expensive, and reliable Will function if part of the network is down Delays in receiving packets Not ideal for real-time voice communication © 2005 Prentice-Hall, Inc Slide 14 Computers Are Your Future Chapter 6 Protocols Protocols are fixed, formalized standards that specify how computers can communicate over a network. suite – The total package of protocols that specify how a network functions Protocol © 2005 Prentice-Hall, Inc Slide 15 Computers Are Your Future Chapter 6 Network Layers user layer physical media receiving sending protocol user stack physical media Network architecture is the overall design of a network. The network design is divided into layers, each of which has a function separate from that of the other layers. Protocol stack – The vertical (top to bottom) arrangement of the layers; each layer is governed by its own set of protocols © 2005 Prentice-Hall, Inc Slide 16 Computers Are Your Future Chapter 6 Advantages of Networking Reduced hardware costs Users share equipment Connected people People can work together without being at the same location Groupware enables sharing of schedules and communications © 2005 Prentice-Hall, Inc Shared applications Users share software File server enables all users to work with the same application program Building information resources Users create common pools of data that can be accessed by employees Slide 17 Computers Are Your Future Chapter 6 Types of Computer Networks Local Area Network (LAN) Links computers within a building or group of buildings Wide Area Network (WAN) Links computers separated by a few miles or thousands of miles Uses direct cables, radio, or Uses long-distance infrared signals © 2005 Prentice-Hall, Inc transmission media Slide 18 Computers Are Your Future Chapter 6 Local Area Networks (LANs) Network access is controlled by a network administrator. Users can access software, data, and peripherals. LANs require special hardware and software. Computers connected to a LAN are called workstations or nodes. Types of LANs: Peer-to-peer Client-server © 2005 Prentice-Hall, Inc Slide 19 Computers Are Your Future Chapter 6 LAN Hardware and Software Networking Hardware Networking Software Network interface card Operating system that (NIC) – Provides the connection between the computer and the network Inserted into a computer’s expansion slot supports networking (Unix, Linux, Windows, Mac OS) Additional system software NIC © 2005 Prentice-Hall, Inc Slide 20 Computers Are Your Future Chapter 6 Peer-to-Peer Networks All computers on the network are treated as equal. There are no file servers. Users decide which files and peripherals to share. Peer-to peer is not suited for networks with many computers. Peer-to-peer is easy to set up. Example: home networks © 2005 Prentice-Hall, Inc Slide 21 Computers Are Your Future Chapter 6 Client-Server Networks Typical corporate networks are client-server. Client-server requires various topologies or physical layouts. The network requires file servers, networked computers (clients), and a network operating system (NOS). Clients send requests to servers for programs and data, and to access peripherals. © 2005 Prentice-Hall, Inc Slide 22 Computers Are Your Future Chapter 6 LAN Topologies The physical layout of a LAN is called its topology. Topologies resolve the problem of contention, which occurs when multiple users try to access the LAN at the same time. Collisions or corrupt data occur when different computers use the network at the same time. Bus Ring Startopology topology • • • • • • All workstations Called Contains a daisy a hubchain orare central attached wiring in a Every workstation concentrator circular arrangement is connected to a single Easy A special tocable add unit workstations of data called a Resolves token travels collisions aroundthrough the ring contention management Workstations can only transmit data Difficult when theytopossess add workstations a token © 2005 Prentice-Hall, Inc Slide 23 Computers Are Your Future Chapter 6 Wide Area Networks (WANs) WANs are similar to long-distance telephone systems. They have a local access number called a point of presence (POP). They contain long-distance trunk lines called backbones. © 2005 Prentice-Hall, Inc Slide 24 Computers Are Your Future Chapter 6 WAN Applications LAN-to-LAN WANs are used to connect LANs at two or more geographic locations. Companies use WANs to connect their branches to one network system. © 2005 Prentice-Hall, Inc Transaction Acquisition Information about transactions is instantly relayed to the corporate headquarters. Point-of-sale (POS) terminals relay transactions to central computers through WANs. Slide 25 Computers Are Your Future Chapter 6 Backbones Backbones, high-capacity transmission lines, are regional, continental, or transcontinental. Internet backbones can carry 2.5 gigabits of data per second. © 2005 Prentice-Hall, Inc Slide 26 Computers Are Your Future Chapter 6 WAN Protocols X.25 is the oldest packet switching protocol. It is used by automated teller machines and credit card authorization devices. New protocols designed for digital lines and faster data transfer rates are: Switched Multimegabit Data Service (SMDS) Asynchronous Transfer Mode (ATM) © 2005 Prentice-Hall, Inc Slide 27 Computers Are Your Future Chapter 6 Public Data Network (PDN) PDN is a for-profit data communications network. Fees are paid on a per-byte-transferred basis. They offer good security and network availability. © 2005 Prentice-Hall, Inc Slide 28 Computers Are Your Future Chapter 6 Virtual Private Network (VPN) A virtual private network consists of lines that are leased to a single company. The network is not open to the public. It is the most secure type of WAN. © 2005 Prentice-Hall, Inc Slide 29 Computers Are Your Future Chapter 6 Chapter 6 Summary • Computer networks link two or more computers to exchange data and share resources. • Two types of computer networks: Local area network (LAN) Wide area network (WAN) • Computer networks: Reduce hardware costs Enable users to share applications Provide a means to pool an organization’s data Foster teamwork • Computer networks require physical media such as telephone wire, coaxial cable, or fiber-optic cable to connect the computers. © 2005 Prentice-Hall, Inc Slide 30 Computers Are Your Future Chapter 6 Chapter 6 Summary continued • Modems transform analog and digital signals. • Network protocols enable the network to function smoothly. • Data is sent through the network by switching and routing techniques. • LAN topologies include: Bus topology Star topology Ring topology • Wide area networks are used to link computers throughout the world. © 2005 Prentice-Hall, Inc Slide 31