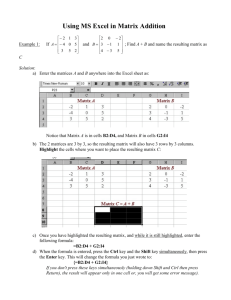
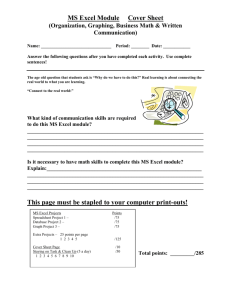
click here to view
advertisement

S NO EMERGING COMPUTER TECHNOLOGY QUESTIONS 1 Vijaya bank IS policies applies to ANSWER OPTION 1 Employees of Vijaya bank In excel to Average the contents of C1,C2,C3,C4,C5 the formula used is ANSWER OPTION 2 Non employees of Vijaya bank ANSWER OPTION 3 Vendors working with Vijaya bank ANSWER OPTION 4 All of the above 4 AVERAGE(C1:C5) AVERAGE(C1,C5) AVG(C1,C4) 2 Ans 3 Mobile Banking Launched in our Bank: August --2009 September --2009 October--2009 November -2009 2 4 What is the menu in Finacle to register Mobile Banking? SMSREG MPAYREG CUMM OAAC 2 5 is the sign we use to activate the formula in excel ? = = ++ None of these 1 6 .……… is the result produced by a computer. Data Memory Output Input 3 7 .A ……… computer (also referred to as a laptop), is a small,lightweight personal computer that incorporates the screen, the keyboard, storage, and processing components into a single portable unit. Notebook Journal Diary Briefcase 1 8 what is =A1/A2 Divide the content of A2 by A1 Divide the content of A1 by A2 Multiply the content of A1 with A2 None of these 2 9 ____ are attempts by individuals to obtain confidential information from you by falsifying their identity. Farming Phishing Computer Viruses Spyware 2 10 _______ is a two way communication device? Mouse Modem Keyboard Monitor 2 11 _______ is called brain of a Computer? DVD Hardisk CPU Monitor 3 12 ________ is the forgery of an e-mail header so that the message appears to have originated from someone or somewhere other than the actual source Spam Email Spoofing Scam None of these 2 13 _________ is not a programming language COBOL C MSDOS Java 3 14 _________ stops your computer accessing specified internet sites Antivirus Firewall Worms None of these 2 15 ……. is a widely implemented model for managing a company's interactions with customers, clients, and sales prospects Customer relationship management (CRM) Internet Banking ISO Mobile Banking 1 16 …….. is a popular wireless network technology used mainly with mobile phones MPEG 3G JPEG IEE 2 17 1 KB is? 1024 bits 1023 bits 1000 bits None of these 1 18 1024 bytes equals 1 kb 2 mb 1 gb 1 tb 1 19 2G & 3G refers to ___________ Technology Mobile Radio frequency Next Generation None 1 20 A __________ is an action that Outlook automatically performs on e-mails based on the conditions that you specify Rules and Alerts Signature Certificates Categorize 1 21 A ……… computer (also referred to as a laptop), is a small, lightweight personal computer that incorporates the screen, the keyboard, storage, and processing components into a single portable unit. Notebook Journal Diary Briefcase 1 22 A ……… is a device that not only provides surge protection, but also furnishes your computer with battery backup power during a power outage. Surge strip USB UPS Battery strip 3 23 A Cell in Excel is identified by the Cell Number Value Address None of these 3 24 A computer ……… is a set of program instructions that can attach itself to a file, reproduce itself, and spread to other files. Worm Virus Trojan horse Phishing scam 2 25 A computer can not boot if it does not have a? Loader Compiler Operating System Assembler 3 Modular Modem module None 2 Disk Copy file copy Backup None 3 26 27 A contraction of the terms modulation and demodulation A copy of a file or disk you make for archiving purposes 28 A directory within a directory is called— Mini Directory Junior Directory Part Directory Sub Directory 4 29 A disaster recovery site of our bank is located in Mumbai Delhi Bangalore Mangalore 1 different seismic zone safe and secure infrastructure preferably with outsourced management 3 Analyst Programmer 1 30 A disaster recovery site should normally be located in a different city in another state far off from the coastal area and DC 31 A person who used his or her expertise to gain access to other people's computers to get information illegally or do damage is a Hacker Spammer 32 A piece of computer information made up of eight bits TB Byte MB None 2 33 A Pixel is A computer program that draws picture a Laptop The smallest resolvable part of a picture None of these 3 34 A portion of memory where the Mac temporarily stores information Clipboard Temp file memory space None 1 35 A protocol for fast communication and file transfer across a network Ethernet Dotnet FTP None 1 36 a system malfunction in which the computer stops working and has to be restarted. HW failure Crash Down None 2 37 A website main page is called ____________ ? Home page Link Window None 1 38 A Word in a web page, that when clicked, opens another document Anchor Hyperlink URL Reference 2 39 Ability of an operating system to control the activities of multiple programs at the same time. Multi tasking Streamlining Multiuser Simulcasting 1 40 According to IS policy what is the preferred inactive time duration after which the system gets locked? 2 min 1 min 5 min 10 min 3 41 Address Labels can be generated through MS word EXCEL LABEL None of these 1 42 Aligning the text in a page by distributing the contents evenly in MS Word is called Left Alignment Right Alignment Centre Alignment Justification 4 43 All formula in excel start with % + = None of the above 3 44 All the deleted files go to_______ Recycle Bin Task Bar Tool Bar My Computer 1 45 Among the following which should NOT have a public interface Internet Router Database server Firewall VPN Concentrator 2 46 An ……. is a computer network that uses Internet Protocol technology to share information, operational systems, or computing services within an organization. Internet Intranet Website None of these 2 47 An add-on component to your computer Sub-Computer Addoncomp Peripherals None 3 48 An attack on a website that changes the visual appearance of the site or a webpage, causing reputational damage to the organization. Web hacking Website defacement Hacktivism Interent hacking 2 49 An attack or an external event that exploits a vulnerability in the system and may eventually cause risk to the information asset is Disaster Threat Vulnerability Risk 2 50 An e-mail address typically consists of a user ID followed by the ……… sign and the name of the e-mail server that manages the user’s electronic post office box. @ # & * 1 51 An example of an input device is Printer Mouse Monitor None of these 2 52 An input device used with Windows in which you point and click to make a selection. Keyboard Pen Mouse Printer 3 53 An internal weakness in the system or any form of susceptibility which may be exploited by an external event in the form of an attack Risk Threat Attack Vulnerability 4 54 An unsolocited email is called as __________? Scam Spam Cam Hidden Mails 2 55 Anti-virus software can only protect your computer against ____________ viruses All Known New None 2 56 Antivirus software used by our bank MacFee Semantec Apple KasperSky 2 57 Any computer in which a software is installed without its knowledge, that puts the computer under the control of malicious attacker used to send DoS attacks and indulge in malicious attacks is Botnet Trojan Horse Zombies virus 3 58 Any criminal activity or an offence committed with the help of a computer or an electronic gadget or internet is Computer Crime Cyber Crime Internet Crime Electronic Crime 2 59 As per PCIDSS which of the following digits of card number can be stored First 4 digits and last 6 digits First 4 digits and last 4 digits First 6 digits and last 4 digits First 6 digits and last 6 digits 3 60 As per Vijaya bank asset classification , all the information assets are grouped into 5 Categories 6 Categories 7 Categories 8 Categories 3 61 Asset valuation is done based on the business impact on the loss of which of the following Confidentiality Integrity Availability All of the above 4 62 ATM Means Automated Teller Machine Any Time Money Asynchronous Transfer Mode All Time Money 1 63 Attachements which can be sent through email Word file Excel files Pictures All of these 4 64 Bank has procured the Treasury Management Solution from Wipro Infosys TCS D2K Tech 3 65 Being at hand when needed to the rightful person is Authorization Availability Integrity Accessibility 2 66 Blue Tooth Technology allows Landline phone to mobile phone communication Signal transmission on mobile phones only Wireless communication between equipments Satellite television communication 3 67 By default MS word documents will be saved into a folder called ________? Desktop My Documents Windows All of the above 2 68 By default the Microsoft Word document will be saved into a folder called Desktop My Documents C drive Personal Folder 2 69 Can customer open a fixed deposit through net banking Yes, e-deposits only No Yes, special deposits i.e., Vijaya 555, etc., only Contact help desk at Head Office 1 70 Can net banking facility enabled to joint account holder where the mode of operation is either or survivor? yes (separate net banking to each user) No Can given only to primary account holder None of these 1 71 CD-ROM stands for Compactable Read Only Memory Compact Data Read Only Memory Compactable Disk Read Only Memory Compact Disk Read Only Memory 4 72 Changing of data before or during entry into the computer system. Examples include forging or counterfeiting documents used for data entry and exchanging valid disks and tapes with modified replacements. Web jacking Forgery Data diddling Salami attack 3 73 Computers connected throughout the world Internet Intranet Compunet None 1 74 Connectting different computers in an organised manner within an office buliding can be termed as? MAN WAN ANN LAN 4 75 Core Banking System Data base is on which platform? MySQL Microsoft SQL Server Oracle SQLite 3 76 Ctrl + H is short cut for ? Open Insert Dialog box activating Insert Hyper Link Tab Open Find Dialog box Open Find and Replace Dialog box Open Goto Dialog box 3 77 CTS stands for Cheque Tracking System Cheque Truncation System 78 Daily cap for fund transfer through Mobile Banking: ############ Cheque Transaction System # ########## Cheque Transmission System # All of the above 79 DC in the case of Core Banking Solution stands for Deputy Commissioner Demand Centre Data Center Data Communication 3 80 Deleted files can be retireved from Recycle Bin Explorer Directory Start Button 1 81 Demings Cycle sequence is check act plan and do Act check do and plan Plan do check and act Check do plan and act 3 82 Device which allows your computer to connect to another computer via a phone line Server Modem Jack None of these 2 83 Digital Signature used in Hard copy of documents Documents submitted in electronic form Both a and b None of these 2 84 Dot-matrix is a type of Printer PC Modem Router 1 85 Duplication & distribution of copyrighted software Duplicity Piracy Freedistribute None 2 86 Emails can be send through our corporate email system to Any where Within Bank Within India None of these 1 25,000 2 2 87 Ensuring that authorized users have access to information and associated assets when required Security Integrity Availability Confidentiality 3 88 Example for social network sites Facebook Linkedin Orkut All 4 89 Excel is Spread sheet Word processor Email client OS 1 90 Expand BCP Business Continuity Plan Business Completion Plan Bangalore College of Pharmacy Bangalore College for Planning 1 91 Expand CIO Common Information Officer Chief Indian Officer Company Information Officer Chief Information Officer 4 92 Expand HIPS Hardware Inclusion Plan System Host Intrusion Prevention System Host Inclusion Plan System Hardware Intrusion Prevention System 2 93 Expand ISM with respect to Information Security Indian Security Management Information Security Manager Indian Security Manager 3 Incident Security Management System Information Security Management System 4 Information Security Organization Indian Security Organization 2 Natted Inclusion Plan System Natted Intrusion Prevention System 1 None of these 1 None 2 International Security Management Information Security Management Solution Information Server Management System International Standard for Organization 94 Expand ISMS 95 Expand ISO Indian Standard for Organization 96 Expand NIPS Network Intrusion Prevention System Network Inclusion Plan System 97 Expand PIN Personal Identification Number Private Industry Network 98 Expand RAM? Read Only Memory Random Access Memory Private Identification Number Real Access Memory Uniform Resource Locator virtual private network User Resource Locator video private network United Resource Locator voice private network Filtering based on cell color is available in Excel 2000 Excel 2003 102 Finacle, the corebanking solution implemented by vijaya bank is developed by Tata Consultancy Services Infosys 103 Floppy Disk is a 104 Following is NOT a Mobile Banking Feature 105 For installing any software, user should Primary Storage Device BALANCE ENQUERY Directly download from the Internet Secondary Storage Device TEMPLE DONATION Get approval from department Head 106 For Mail Merge preferred application is MS Access MS Excel MS Word 107 Full form of IMPS Immediate Payment Service International Mobile Payment Service Instate Mobile Payment Service Indian Mobile Payment Service 1 108 Full form of IMPS INTERBANK MOBILE PAYMENT SERVICE IMMEDIATE PAYMENT SERVICE BOTH None of the above 2 109 Functional Key F2 is used in excel to Delete a sheet Edit a cell Save a sheet None of these 2 110 GIF and JPEG files are examples of ? Microsoft word files Images Audio files Video files 2 111 Gmail used for Operating System word processing spread sheet sending e-mails 4 112 Google Word processor Messenger Search Engine None of these 3 113 Govt Business is being handled in our bank through ………….system Finacle GBM CPSMS Vnet 2 99 Expand URL 100 Expand VPN 101 None of these 1 None of these 1 Excel 2007 None of these 3 Wipro Microsoft 2 Cache memory None of these 2 TAX PAYMENT IMPS 3 Directly install the software None of the above None of the above 2 3 114 Grammatical errors found in programming are called ____________ errors Syntax Grammatical Virus All of the above 1 115 GUI stands for Graphical User Interface Graph Use Interface Graphical Universal Interface None of these 1 116 Highlighted words that take you to another web page Hyperlink Highlight Shiftpage None 1 117 History of all computer transactions normally in chronological order is called System trail Audit trail End of day routine Transactions summary 2 118 How do we manage Logs centrally in our organization? What is the system/solution installed for this? Biometric mechanism Stored in respective servers/PCs Security Operations Center with and SIEM tool. Additional Hard disks provided for storage 3 119 How frequently should you change your System Password as per Password Policy Once in 45 days Once in 15 days Once in 30 days Never 1 120 How frequently should you to change your password as per password policy once in month once in 15 days As and when required Never 1 121 How government cheques are identified? Cheques with 7 digit account number and a 3 digit transaction code Cheques with 6 digit account number and transaction code in the range 20-27 and 49 Both None 3 122 How many sheets are there in Excel Workbook by default 2 123 How many times in a day Free Buzz facility can be used by a customer? Only once in a day 3 Twice in a day 4 Three times in a day 5 Unlimited with nominal subscription. 2 3 124 Ideally you should use different____________ for each site with access to financial information. connections Username Password None 3 125 IE and Firefox used in computer are called _________ Operating System Browser Database None 2 126 IMPS is a…………. service 24X7 24X5 12X7 None of these 1 127 In finacle the User profile gets deleted when the user enters the wrong passoword 2 times 3 times 5 times None of these 2 128 In Mobile Banking total number of transactions allowed per day for fund transfer? Maximum 2 Maximum 3 Maximum 4 Maximum 5 2 129 In order to multiply items in Excel you would use: * X ^ None of these 1 130 In order to multiply numbers in Excel the symbol used is ________? @ X * None 3 131 In the case of Mobile Technology who is the service provider Telecom SPs Mobile companies Airtel None 1 132 In windows, the option available to view the recently accessed documents is Programs Accessories Run Documents 4 133 Information Security Qualities/attributes are Certified Internal Auditor Central Intelligence Agency Confidentiality (C), Integrity (I) and Availability (A). Crime Investigation Agency 3 134 Intel is a company manufacturing DVD Micro Chips None 3 135 Internet is LAN MAN None of these 1 TV Network of Networks 11 Domains 39 Control objectives and 133 controls 11 domains 39 control objectives and 130 controls 12 domains 39 control objectives and 133 controls 2 136 ISO/IEC 27001 has 13 domains 45 control objectives and 133 controls 137 IT & IS policies of the Bank are approved by General Manager DIT Chariman and Managing Director Executive Director Board of Directors 4 138 It is a requisite for maintaining the privacy of the people whose personal information that organization holds. Confidentiality Availability Security Integrity 1 139 It means that data cannot be created, changed or deleted without authorization Confidentiality Integrity Availability Security 2 140 JPG file refers to Picture Diagram letter None 1 141 Key used for Capturing the screen on the computer Print Screen F4 Pause Break F10 1 142 Keys to be used for switching between different screens in the computer Tab + Shift Alt + Ctrl Alt + Enter Tab + Alt 4 143 Landscape is A font style Paper size Page layout Page orientation 4 144 Latest released version of Windows Windows 7 Windos XP Window Vista Windows 98 1 145 Latest version of Windows available in the market is ______ ? Windows-98 Windows-8 Windows-7 Windows Vista 2 146 Linux is Graphics System Operating System Drawing system Processing system 2 147 MICR stands for Magnetic Ink Character Recognition Magnetic Ink Code Reader Magnetic Ink Character Reader Magnetic Ink Code Recognition 1 148 Microsoft Powerpoint document has a file extension of ? DOC OR DOCX XLS OR XLSX PPT OR PPTX TXT 3 149 Mobile Banking Features: BALANCE ENQUERY TEMPLE DONATION TAX PAYMENT Both 1 &2 3 150 Most of the inexpensive personal computer does not have any disk or diskette drive. What is the name of such computes? Home computers Diskless computers Dedicated computer General computer 1 151 Most viruses spread through _________________ downloads Internet only Email only Email and Internet None 3 152 MS Office contains Note pad, excel Word, excel, power point only word only excel 2 153 MS Word 2003 allows creation of ___ type of documents by default? .doc .txt .aspx none of the above 1 154 No confidential information should be stored on desktops - this covers which section of IS Policy Clear Desktop policy Clean Desk Policy Internet Policy None 1 155 Nothing can keep your data safer than ___________ it up. Backing Zipping Copying None 1 156 NPCI initiated mobile banking technology IMPS IMMS MPIS None 1 on first page on last page on alternate page every page 4 Nanosecond Millisecond Billisecond None 1 Can be viewed all operative accounts of the customer Can be viewed all types of accounts of the customer No account can be viewed. 2 157 158 on which page the header or the footer is printed by default ? One billionth of a second. 159 One of the features of V-epassbook+ is correct? Can be viewed only one operative account of customer 160 One of the most talked latest server technology Desktop compute Cloud computing Word processing None 2 161 Oracle is a Relational Database Word processor Input Device Central Processing Unit/Processor 1 162 OS stands for Operating System Outstanding System Operating Software None of these 1 163 Our Bank's DIT, DC & DRC have been certified with which of the following certifications ISO 22000:2005 ISO: 26000 : 2008 ISO/IEC 90001:2008 ISO/IEC 27001:2005 4 164 Our data centre is situated at Bangalore Mumbai Delhi Kokotta 1 165 Our DR site is situated at Bangalore Mumbai Delhi Kokotta 2 166 Our Mobile banking product is known as V-Mobile V-Net I-Net None of these 1 167 Owner of all IT assets of DIT, DC & DR is General Manager DIT General ManagerRMD General Manager GAD General ManagerPersonnel 1 168 Page number property is in which menu View Insert Page Layout None of these 2 169 Personnel Department computerisation is ensured through-------------- Software HMRS HRMS PIPS None of these 2 170 Personnel who design, develop and maintain a software is Programmer Analyst DBA None 1 171 Portrait and Landscape in MS Word are called Font Types Page Orientation File Types Page Area 2 172 Printer is An Input Device An Output device Both 1 and 2 None of these 2 173 Property of the file can be viewed by ________ clicking the file Right Left Front None of these 1 174 Protecting the data from unauthorized access is called data inaccessibility data encryption data security data validity 3 175 RAM is a Volatile memory Non Volatile Memory Secondary Storage Device None of these 1 176 RAM stands for Random Access Memory Read Access Memory Read Arithmatic Memory Random Arithmatic Memory 1 177 RUPAY Card is being issued by VISA NPCI MASTER CARD MASTERO 2 178 Security requirements for entities processing, storing and/or transmitting Card Holder Data should comply PCI DSS ISO: 26000 : 2008 ISO-IEC 90001:2008 ISO-IEC 27001:2005 1 179 Select a valid email-id format abcd@vijayabank. co.in a%vijayabank www.vijayabank.c om a!vijayabank.co m 1 180 Servers are computers that provide resources to other computers connected to a Client Network Super Computer Mainframe 2 181 Set of instructions used to control the functioning of the computer is called the Human ware Hardware Software None of these 3 182 Short cut key for selecting all in a file. CTRL+A SHIFT+A ALT+A none of the above 1 183 Shortcut key for printing a document in MS Office is ________? Cntrl+P Cntrl+C Cntrl+Z None 1 184 Shortcut key to undo the last action in MS Office applications is ______ ? Cntrl+C Cntrl+H Cntrl+P Cntrl+Z 4 185 Software used to compress files Word Excel Acrobat reader Winzip 4 186 Software which supports Fee Collection that brings CASA to bank V-FeeHive V-Premises V-Adalath None of the above 1 187 Spaces allowed in email id Yes No Sometimes None of these 2 188 Spend anytime anywhere throguh mobile Mobile Banking Mobile money SMS money None 1 189 Stealing someones identity in which someone pretends to be someone else by assuming that persons identity Identity theft Individual theft Personality theft Individual fraud 1 190 Tagging of personal transactions is a feature of VNet Banking Mobile Banking v-ePassbook+ None of the above 3 191 The act of attempting to acquire information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by masquerading as a trustworthy entity in an electronic communication is known as Phishing Pharming Vishing Piggy backing 1 192 The Bank is having Debit Card of VISA MASTER CARD MASTERO Both VISA and MASTER CARD 1 193 The cell in excel labeled F5 refers to row F column 5 column F row 5 functions available in cells Function key F4 2 194 The Cell in Excel where data is currently entered is called as Active Cell Current Cell Local Cell Work Area 1 195 The cell in excel where the 3rd Column and 2nd Row cross has the cell address? C2 2C B3 3B 1 196 The data processed by a computer is termed Data Database Information None of these 3 197 The desktop contains small graphics called ..... icons logos windows pictures 1 198 The difference between memory and storage is that memory is …. and storage is … Slow, Fast Temporary, Permanent Permanent, Temporary Fast, Slow 2 199 The difference between memory and storage is that memory is …. and storage is … Slow, Fast Temporary, Permanent Permanent, Temporary None 2 200 The existing version of IS Policy in our Bank is Version 1.0 Version 2.0 Version 3.0 Version 4.0 3 201 The facility in excel to prevent the unwanted data in a sheet by specifying what information can be changed Hide Unhide Protect sheet Unprotect Sheet 3 202 The fastest among the below mentioned printers is Dot Matrix Printer Line Printer Laser Printer None of these 3 203 The following customers can avail V-net banking facility under Retail user category? Individual Trust account Joint Account Pvt.Limited 1 204 The full form of ALPM is Automatic Logic Processing Manager Auto ledger Post Machine Advanced Ledger Posting Machine None of these 3 205 The full form of ASCII is American standard for information interchange 1 The full form of DVD is Digital Video Drive Automatic standard for information interchange Digital Versatile Disk None of these 206 Association Standard for information Interchange Digital Volatile Disk None of these 3 207 The full form of IP is Internet Packet Intergrated Packet Internet Protocol None of these 3 208 The full form of LCD is Light Cathode Display Strong query language 2 The full form of SQL is Liquid Crystal Display Specified Query Langauage None of these 209 Light Crystal Display Structured query language None of these 1 210 The full form of VOIP IS Video over IP Voice Over IP Voice Outside IP None of these 2 211 The functional key used in finacle to navigate to the next screen is F5 F6 F4 None of these 2 212 The functional key used in finacle to navigate to the previous screen is F5 F3 F4 None of these 2 213 The green wave underline in MS Word document indicates Grammer error Spelling errors Address block None of these 1 214 The ICTM menu option in finacle is used for Both A and B Outwardclearing Lodgement Inward Clearing logement None of these 3 215 The input device that is most likely to be used to play computer game is the Joystick Keyboard Touch Screen Mouse 1 216 The instructions that tell a computer how to carry out the processing tasks are called as Programs Processors Input devices Memory modules 1 217 The intersection of a row and a column in excel is called: Data. a field. a cell. an equation. 3 218 The key combination used to reboot a computer is Alt + Ctrl + A Ctrl + Alt + Delete Delete button None of these 2 219 The mails already sent from Outlook will be available in __________ folder? Outbox Sent items Inbox None 2 220 The maximum amount of data that may be lost when service is restored after a disaster and when recovery is made like restoring backup and tolerable point upto which data is not recovered is Recovery Point Objective Recovery Time Objective Recollection point objective Real time Objective 1 221 The menu option in finacle used for customer creation is SALUP CUMM OAAC ACM 2 222 The menu option in finacle used to see the transaction details of an account is ACLI ACM OAAC CUMM 1 223 The menu option used in finacle for Account Creation is ACLI ACM OAAC TM 3 224 the most popular operating system is.................. Google Facebook Microsoft windows Linux 3 225 The name given to a sequence of a instructions in a computer language,to get the desired result is? A program A decesion table A pseudocode An algorithm 1 226 The number of function keys in a keyboard is # ####### 2 227 The number system which uses only 0 and 1s is called None of these 2 # 10 Hexadecimal Numbersystem ########### # Binary number System ########## Octadecimal Number system # 228 229 The number used to identify a computer in a network is called The number used to identify a computer in a network is called Process ID SYSID IP Address None of the above 3 System Address SYSID Process Id IP Address 4 230 The number used to identify a computer in a network is called ___________? Serial No. Server Address Mail Address IP Address 4 231 The option used in Microsoft word to view the print layout of a document before printing Print Preview Slide Show View None of these 1 232 The option used in word to save the current file in a different name is Save Save As Open New 2 233 The option used to resend a mail available in sent items to a different email-id Reply Forward Followup None of these 2 234 The option used to view all the drives available in a computer My documents My computer Recycle Bin Desktop 2 235 The performance of a hard drive or other storage device - how long it takes to locate a file. Access time Perfomance indicator HWP time None 1 236 The process of identifying specific rows and columns so that so that certain columns and rows are always visible on the screen iscalled freezing locking selecting fixing 1 237 The processes of starting or restarting a computer system by loading instructions from a secondary storage device into the computer memory is called Duping Booting Padding All of above 2 238 The red wave underline in MS Word document indicates Grammer error Spelling errors Address block None of these 2 239 240 the smallest piece of information used by the computer. The smallest piece of information used by the computer. Bit Byte MB GB 1 Bit Byte MB KB 1 241 The software developed by Microsoft for creating presentations is MS word MS Outlook MS Powerpoint MS SQL 3 242 The software provided by microsoft for sending and receiving mails. MS word MS Outlook MS Windows None of these 2 243 The symbol used for multiplication in Excel is & * % None of these 2 244 The symbol used to activate formula in an Excel cell is @ = ! & 2 245 The term is a combination of "voice" and phishing Phishing Pharming Vishing Piggy backing 3 246 The three types of data found in a spreadsheet in excel is data, words, numbers equations, data, numbers words, numbers, labels numbers, formulas, labels 4 The tolerable time limit as planned by the organization within 247 which the data must be recovered in case of disaster Recollection Time Objective Recovery Point Objective Real time objective Recovery Time Objective 4 248 The use of computer work stations to send and receive messages is known as electronic funds transfer electronic message switching electronic mail electronic publishing 3 249 This input device will allow the user to move the pointer on the screen Mouse Speaker Icon Output 1 250 This part allows the user to hear information from the computer Monitor Router Mouse Speaker 4 251 This part allows the user to hear information from the computer Monitor Software Input Speaker 4 252 Thumb Drives are used to__________ Data Store Mail Forward None 1 253 Time during which a job is processed by the computer is Processing time Down time Real time None 1 254 Time taken to process a job by the computer is Processing time Down time Real time None 1 255 256 TM is the menu option used in finacle for Transaction Posting TM is the menu option used in finacle for Transaction Posting 257 To assess the size of a file view the _____________ by right clicking on it. 258 To find the sum of cells A1,A2,A3,A4 the formula to be used is TRUE FALSE TRUE FALSE properties size 0 #NAME? 1 None of these 1 characteristic None of these 1 ########## #### A and B ##### Download application from our bank site/ Google play stores only A only 3 259 To get the v-e passbook+ facility, customer has to do SMS registration with mobile number 260 To guard against Virus/ malware you need to have Spyware Monitor Spreadsheet 261 To quickly print a file, Press .... Ctrl+P Ctrl+S Ctrl+N Antivirus software Ctrl+Z 262 To transfer data from one computer to another. Transferin Transferout Download None 3 263 To UNDO a recent task the key-combinations used are Ctrl+H Ctrl+Z Ctrl+B Ctrl+V 2 264 To undo your last action in MS-Office Control P Control S Control N Control Z 4 4 4 1 265 Two Factor Authentication for accessing Core Banking Solution in our Bank BioMetric Authentication Solution IRIS Scanner Speech Recognition All of the above 1 266 URL stands for Uniform Region Locator Uniform Resource Locator Uniform Resource Locator Uniform Research Locator 2 267 Usually .PDF is the extension for the files created in MS Word MS Excel Acrobat None of these 3 268 Virtual Resources Under Seize means Virus Virtual Vresource None 1 269 VIRUS stands for Very Important Resource Under Search Vital Information Resource Under Siege Verify Interchange Result Until Source Very Important Record User Searched 2 270 Vnet Banking users are Corporate Retail Both None of these 3 271 Voice Communication through intranet within our bank is being done through IP Phone Telephone Mobile PC 1 272 VPN means Virtual Private Network Video Private Network Voice Private Network None of these 1 273 WAN stands for Wap Area Network Wide Area Network Wide Array Net Wireless Area Network 2 274 We have a) Acceptable usage of Assets b) Not supposed to create chain mail c) Not supposed to access sites which are not there in approved list of websites Internet Access Policy E-mail Access Policy None Internet Access Policy & E-mail Access Policy 4 275 Websites used for messaging, posting photos etc and networking are called E-Commerce Site Social Networking sites WebMail Sites None of these 2 276 What are small pictures that represent an individual application or groups of applications? Icons Menu boxes Option boxes Scroll bars 1 277 What are the different modes to enable the retail customer V-Net banking. Through Branch (CFTM/FVTM) Self user Creation (Online) Through ATM Both (a) and (b) 4 278 What are the different ways to register our customer for mobile Banking? ATM FINACLE BOTH None of the above 3 279 What does CISO stand for Central Information Security Officer Chief Investigation Security Officer Chief Information Security Officer Central Investigation Security Officer 3 280 What does D-DOS stand for Denial of Service Detected Denial of Service Denial of Distributed Service Distributed Denial of Service 4 281 What is a Database Base Data Organized collection of Data Non Organized collection of Data None of these 2 282 What is a tablet Type of computer Gazet None 1 283 What is IMPS Immediate Payment Service Instate State Mobile Payment Service None of these 1 284 What is Intranet we can access it anywhere both a and b None of these 1 285 What is ipad Server Desktop Laptop 1 286 what is ISDN integrated services digital network industry standard digital network None of these 2 we can access it within organization A tablet computer india software data network Related to medicine International Mobile Payment Service e-file sent along with an email message Sending same formate letter to all people Annexure sent along with letter Both a and b None of these 1 Sending Different formate letter to all people Sending different formate letter to different people All the above 1 A Printer A Sound format A Scanner 3 Pending to follow Paper to follow Paper to file 3 Private Industry Network Public Industry Network None of these 1 CD ROM None of these 1 Subnet Area Network None 2 URL IP Address None of the above 3 5 Lakh for Retail and 15 lakh for corporate 1 lakh for Retail and 2 lakh for corporate Transaction facility not available through net banking Unlimited (any amount) 1 What is the DRC Drill schedule? Twice in a year once in a year once in a month Once in a quarter 4 297 What is the extension of a MS Excel 2007 file xls xlsx xlss None of these 2 298 What is the full form of ROM Read only memory Request of Memory Request on Memory None of these 3 299 What is the Inactive Time duration after which the systems get locked? 2 min 1 min 5 min 10 mon 2 300 What is the menu in Finacle to register Mobile Banking? SMSREG MPAYREG CUMM Both 1 &2 2 287 what is mail attachment 288 What is mail merge 289 What is MP3 ? 290 What is p2f with respect to CTS 291 what is PIN 292 What is RAM? Computer Memory 293 What is SAN? Service Area Network Secondary Storage Device Storage area Network 294 What is the address given to a computer connected to a network called? Process ID 295 What is the DEFAULT Funds Transfer limit in net banking 296 A Mouse Presentation to follow Personal Identification Number 301 what is the minimum limit for doing a RTGS transaction 2,00,000 1,00,000 3,00,000 4,00,000 1 302 What is the name of the software that allows us to browse through web pages called ? Browser Mail Client FTP Client Messenger 1 303 What is the suffix of all official email-ids of Vijaya Bank vijayabank.com vijayabank.org vijayabank.co.in None of these 3 304 What is the url of Vijaya bank Website www.vijayabank.o rg www.vijayabank.in None of these 2 305 What is the use of bookmarks ? To correct the spellings. www.vijayabank.c om To jump to a specific location in the document To ignore spelling mistakes To save alignments as it is 2 306 What security controls are in place to safe guard the data? Physical Security IT Security Physical Security & IT Security None 3 307 What should be the strength of your passwords? Minimum 5 char, alphanumeric Minimum 8 char, alphanumeric Minimum 10 char, alphanumeric Minimum 7 char, alphanumeric 2 308 309 310 What would be the result of =SUM(G16,300), if G16=50? What would be the result of =SUM(G16,400), if G16=50? What would be the result of =SUM(G16,900), if G16=50? 311 When user has to leave their desk, he/she has to 312 When was the last DR drill conducted 1500 250 350 6 3 1500 250 450 6 3 1500 250 950 6 3 Log off from all applications 14-Feb Lock the desktop using CTRL-ALTDEL 13-Nov Ensure the screen saver with password is turned on 13-Jun All of the above 13-Sep 4 1 313 When writing a document, you can use the ……… feature to find an appropriate word or an alternative word if you find yourself stuck for the right word. 314 When you empty your recycle bin, the files can NEVER be recovered. 315 Whether customer can do fund transfers through v-e passbook+facility? Yes Rs.5000/- per day Yes, on submission of request to the branch Only A is correct Fund cannot be transferred. 4 316 Whether customer can view Credit Card statement through net banking. Yes, Unbilled transactions only. Yes, billed transactions only. Credit card statement cannot be viewed Both (a) and (b) 1 317 Which among following is correct extension of word files ? xls doc ppt dcw 2 318 Which device connects your computer to the Internet? Telephone table Modem Hard drive CD rom 2 319 Which formula can add all the numeric values in a range of cells, ignoring those which are not numeric, and place the result in a different cell? =SUM() =AVERAGE() None of these 1 320 Which is bigger among KB,MB,GB and TB (kilo byte,mega byte, giga byte, tera byte) KB MB TB GB 3 321 which is bigger amoung KB,MB and GB (kilo byte,mega byte giga byte) kb mb gb None of these 3 322 Which is not a font style Calibri Superscript Times New Roman Verdana 2 323 Which is not an input device? Web camera Mouse Printer Keyboard 3 Dictionary TRUE Word finder Encyclopedia FALS E #NAM E? Thesaurus None 1 1 324 Which key is used when selecting a group of files? ALT CTRL ESC TAB 2 325 Which Media can normally store more data? CD-ROM Hard Disk ROM RAM 2 326 Which menu contains the commands that allow you to rename or delete a file? Disk File Options Window 2 327 Which of the below is not a type of live communication Instance Messaging IRC E-mail Chat 3 328 Which of the Card varient works on the principle "pay now use later" Debit Card Credit Card Prepaid Card Rupay Card 3 329 Which of the following area is not covered in RBI guidelines for Information security IT services outsourcing Cyber frauds Customer education Credit Risk management 4 330 Which of the following can you use to add times to the slides in a presentation? Slide show menu Rehearse timings button Slide transition button All of the above 2 331 Which of the following companies developed MS Office Novel Infosys Microsoft Lotus 3 332 Which of the following features are available through V-NET banking for the customers, who are maintaining both the operative and PPF account with us? Transfer of funds only Both the accounts can be viewed only Either A or B Both (a) and (b) 4 333 Which of the following is among the following companies are ATM manufacturer NCR Microsoft Google Oracle 1 334 Which of the following is an information asset Desktop loan document Internet All the above 4 335 Which of the following is an input device? Speakers Mouse Monitor Printer 2 336 Which of the following is not a software security control User authentication User access privilege Biometric authentication Data and input validation 3 337 Which of the following is not an option of edit menu? Cut Copy Paste Page setup 4 338 Which of the following is used to measure hard drive capacity? bps Gigahertz Gigabyte dpi 3 339 Which of the following standard is relevant to Business Continuity Management. ISO 27001 ISO 22301 PCI DSS IT Act 2 340 Which of the following will not advance the slides in a slide show view? The esc key The space bar The enter key The mouse button 1 341 Which one is Biomatric type of security IRIS Password ID card None 1 342 Which one is not an input device Keyboard Mouse Printer Webcam 3 343 Which one of the flowing service provider offers USSD based Mobile Banking BSNL/MTNL VIDAFONE AIRTEL BPL 1 344 Which one of the following is not a operating system Linux Windows XP Macintosh MS Office 4 345 Which one of these are mode of connectivity VSAT RF CDMA All 4 346 Which one of this is Card Not Present Transaction ATM Withdrawal POS Transaction None 3 347 Which option is not available In Mobile Banking “Request to Bank” REQUEST FOR NEW ACCOUNT REQUEST FOR LOAN ACCOUNT Ticket booking throguh Internet BOTH are not avialable None of the above 3 348 Which part does the processing? We sometimes call it the "brain" of the computer. Motherboard CPU ALU OS 2 349 Which part of the computer helps to store information ? Disk drive Keyboard Monitor Printer 1 350 Which two websites are search engines? Google and Ask Google and Hotmail Facebook and Orkut None of the above 1 351 While working with Ms-Dos which command transfers a specific file from one disk to another? Copy Diskcopy Time Rename 1 352 Who is our Bank's CISO Deputy General Manager – DIT Deputy General Manager – RMD General Manager RMD General Manager-DIT 2 353 Who is the ISM in your organization? Chief Manager Data center Chief Manager – IT Security Chief Manager RMD Chief Manager TMD 2 354 Who is the service provider for Mobile Banking in Vijaya Bank? FSS TCS WIPRO both 1 & 2 1 355 Writing program in natural language independent of programming software for others to know the flow is called Pseudo code Schema management coding development Low level design of software 1 356 WWW stands for World Wide Web World wide internet Website None of these 1 357 You can undo the task using keys Ctrl+H Ctrl+Z Ctrl+B Ctrl+V 2