Hardcore Defacement Statistics Presented by Brian Martin / Matt
advertisement

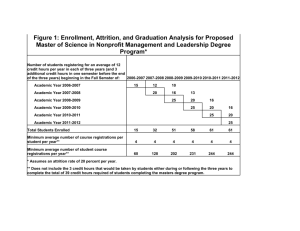
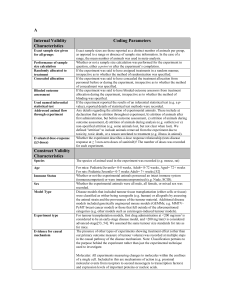
Feds, Felons and Flakes: Reflections on the Attrition Mirror Presented by Brian Martin / Matt Dickerson Slides by Dale Coddington Copyright 2000. attrition.org Staff Introduction This Talk Will Cover: The attrition mirror How we operate Defacement information and statistics Random other babble Copyright 2000. attrition.org Staff Who We Are attrition.org Staff Brian Martin a.k.a. Jericho Brian Martin has been involved in computers since the early 80's. His experience spans from first generation home computers to large scale servers powering the most current business applications today. Working in the computer security industry for the past five years, he has provided security audit and penetration assessment for foreign banks, Fortune 500 companies, Department of Defense and more. He has provided training and consultation for the Federal Bureau of Investigations, Defense Criminal Investigative Services, and the National Security Agency. In recent months, Brian's articles focusing on security issues have been widely circulated on the Internet, corporate newsletters, and print magazines. Copyright 2000. attrition.org Staff Who We Are attrition.org Staff Matt Dickerson a.k.a. Munge Matt Dickerson has worked as an economist and statistician providing legal consulting for Fortune 500 companies and universities since 1996. While his experience with computers began in the late 1980's, his interest in the Unix Operating System coincided with his statistical programming on the Unix platform in the mid-1990's. Since then, he has provided administrative, technical, and training support for diverse Unix platforms for the professional, manufacturing, and banking industries. Copyright 2000. attrition.org Staff Who We Are attrition.org Staff Dale Coddington a.k.a. Punkis Dale Coddington is a Systems Security Engineer with eEye Digital Security, a computer security products and consulting company located in sunny Southern California. In the past Dale has conducted consulting and training courses at several NASA Centers, State of Washington, Naval Justice Center, the U.S. Department of Justice, and several Japanese Corporations. In 1999 Dale was appointed one of two technical consultants by the Defense Team of Kevin Mitnick. Copyright 2000. attrition.org Staff Modus Operandi Qualification of Statistics The statistics and information presented here are based on data collected since November 1998 Attrition began actively mirroring defaced sites in January 1999 Mirrors on the attrition site date back to 1995 Data before January ‘99 is believed to be accurate but is not 100% confirmed Copyright 2000. attrition.org Staff The “Root” of the Problem How are These Sites Being Defaced? Unix: – – – Remote buffer overflows Sniffer / trusted path attacks Poorly-coded CGI’s Windows NT: – – – – RDS / MSADC IISHack MS Front Page misconfigurations Other misc. CGI/Web exploits Copyright 2000. attrition.org Staff Defacements Speculation: Why are More NT Boxes Defaced? Compare the knowledge required to navigate the hacked system: NT : Must know basic DOS Commands. – echo "i 0wn j00" >> c:\inetpub\index.html Unix : Must know basic Unix commands – – – In many cases defacers lack the common skill to even find the main web page on a system: find / -type f -name index.html –print vi /path/to/index.html (wait vi is too hard to use) Copyright 2000. attrition.org Staff Why Me? Why Are These Sites Being Defaced? Tagging, electronic graffiti One-upmanship - who can hit the biggest site The ‘gov/mil’ phenomenon Delusions that what they are doing is impressive or cool It's trendy - like baggy pants, it just won't go away. “Hacktivism” (95% convenient excuse) Copyright 2000. attrition.org Staff The Fine Art of Mirroring The Steps Mail comes in (hacked@attrition.org) Goes to six people on attrition (and mirrored off site) Staff verifies the defacement (lynx, Netscape, etc) Run a custom mirror utility 'aget' Copyright 2000. attrition.org Staff The Fine Art of Mirroring What aget Does aget Version 4.5 - 866 lines of shell script – – – – – – – check to see if it has been mirrored, avoid duplication use Netcraft (www.netcraft.com/whats/), NMAP (www.insecure.org), and lynx to verify the Operating System of the defaced site If NMAP OS fingerprint is unknown, mail it to Fyodor Do a NIC lookup based on the country/TLD Take traceroute to record upstream provider(s) Check to see if previously defaced Check for hidden comments in HTML, DOS signature, etc. Copyright 2000. attrition.org Staff The Fine Art of Mirroring What aget Does (Continued) – – – Mail CERT based on country, mail NIPC (heh) Mail NIC contacts Mail attrition defaced* mail lists http://www.attrition.org/security/lists.html – Form letter clearly explaining this is a third party notification of a security incident on the remote machine – this is just a warning that a site has been defaced, no other information is given Copyright 2000. attrition.org Staff Stop Hacking My %^&&* Box! "Defaced Site Administrative Response" 80 – 90% – Friendly, appreciative, asking us for help, thanking for notification 10 – 20% – Hostile responses, threats, insults, blame us Copyright 2000. attrition.org Staff Stop Hacking My %^&&* Box! Responses CERT – – Recent addition. CERT originally asked to be removed from notification utility When challenged on why they exist in the first place, they agreed to receive notifications Copyright 2000. attrition.org Staff Stop Hacking My %^&&* Box! Responses NIPC – – Forwarded notifications on to “the appropriate people” approximately 20% of the time – some replies state they do not fall under infrastructure threats No response for other 80% of notifications Copyright 2000. attrition.org Staff Feds Us Federal Agency / Law Enforcement Mirror Utilization FBI Connecticut Office – – – – Issued a single 2703(d) subpoena requesting information on ‘flipz’ and ‘fuqraq’ Attrition Responded and charged $16.00 for administrative fees $16.00 is the extent of income from federal agencies in all of attrition’s history Copyright 2000. attrition.org Staff Feds Us Federal Agency / Law Enforcement Mirror Utilization FBI Mirror Printouts – – – Several raid victims have verified that printouts from the attrition.org mirror were used during those raids “Did you hack this site?” Copyright 2000. attrition.org Staff Forensics and Mirrors (Not Profiling) Most defacements are sloppy Leave a nice forensics trail Many patterns in defacement activity – – Easy to match one person operating under different names Indications groups/individuals talk before choosing targets (wave of .edu, wave of .br, wave of...) Copyright 2000. attrition.org Staff Linking (Public) Obvious signs – Broken Image – pathed to local drive where HTML was created - few geniuses pathed to c:\microsoft\office\john\doe\ or similar paths that included their real name Meta tags – signatures (graphics or text) Generators, meta names, and more Greets, misspellings, language, more Copyright 2000. attrition.org Staff Linking (Private) Mail to us is more candid, more verbose Defacers use Hotmail and other freemail sites w/ X-Originating-IP – – (grep, quote how many times we see x-originating) (uniq, how many unique x-originating IPs have we seen) In some mail the defacer takes credit – – Other times a 'friend' is reporting the hack Occasionally arbitrary third party reports it (usually on high profile, high traffic sites). Copyright 2000. attrition.org Staff Linking Analysis Looking at all of the above, it is trivial to link different names and group members to each other Several defacers change name and style for a variety of reasons – A quick check at the forensics/footprints of their work will reveal a substantial amount Copyright 2000. attrition.org Staff Mail Woes Roughly 33% of mail to hacked@ are false reports Sites are not defaced, do not answer, or show no signs of intrusions Infrequently, we receive mail of a defacement before it happens – Typically a minute or less before defacement. Either way, it obligates us and potentially makes us liable if we do not report the crime before it occurs Copyright 2000. attrition.org Staff Blame Us (Everyone Else Does) We are often accused of encouraging defacements – This is far from the truth Odds are we have berated and insulted most defacers for their activities - we've questioned them, encouraged them to STOP, etc. We are not the only mirror. If we close up shop, the other mirrors will pick up our role. This isn't a good idea because we do it better Copyright 2000. attrition.org Staff Disclaimer (Of Course) Conclusions based on the mirror or statistics must be looked at carefully: Example: Saying "defacements are increasing“ – – Yes. there are more defacements today than yesterday in general No. roughly the same percentage compared to servers deployed (?) Example: Saying "XX OS is more secure“ – No. it is likely the OS has not been audited/tested as much as many other OS’s. You must factor if the OS is open source, how long it has been deployed, etc. Copyright 2000. attrition.org Staff Why Our Mirror is Better (The Fine Art of Shameless Self Promotion) All of our information is public (and free) We notify sites of the intrusions as we learn about them We provide mail lists to keep you informed of defacements We collect more information about the site We provide breakouts by group, TLD, organization We provide comprehensive statistics Copyright 2000. attrition.org Staff 20 Most Active Groups Including Ties 20) 20) 19) 18) 17) 17) 17) 16) 16) group hacks kpz mozy p4riah keeblerelves ehw fuqrag teaminfinity hip ytcracker 40 40 41 43 43 43 43 44 44 Copyright 2000. attrition.org Staff days active 185 211 108 138 101 74 112 233 299 in years 0.51 0.58 0.30 0.38 0.28 0.20 0.31 0.64 0.82 20 Most Active Groups Including Ties group 16) 15) 14) 13) 13) 12) 11) 10) 9) 8) 7) 6) v00d00 kryptek pentaguard fuby artech teamecho hv2k levelseven ph33rtheb33r crimeboys mcm4nus acidklown hacks 44 46 47 54 54 59 60 64 67 83 86 93 Copyright 2000. attrition.org Staff days active 183 191 503 289 166 54 226 233 214 156 100 273 in years 0.50 0.52 1.38 0.79 0.45 0.15 0.62 0.64 0.59 0.43 0.27 0.75 20 Most Active Groups Including Ties group 5) 4) 3) 2) 1) dhc pakistanhc gh antichrist forpaxe hacks 98 100 115 142 154 Copyright 2000. attrition.org Staff days active 271 272 268 163 196 in years 0.74 0.74 0.73 0.45 0.54 20 Longest Running Groups group 20) 19) 18) 17) 16) 15) 14) 13) 12) 11) x rat maverick c0rvus xessor mod ez|ne ch0jin kingstr0ke lou days active in years 312 334 338 359 377 379 389 390 403 419 Copyright 2000. attrition.org Staff 0.85 0.91 0.93 0.98 1.03 1.04 1.07 1.07 1.10 1.15 hacks 4 10 3 12 12 2 3 2 4 15 20 Longest Running Groups group 10) 9) 8) 7) 6) 5) 4) 3) 2) 1) druhy viper sploit rewted snow pentaguard xploit rootworm h4g1s adm days active 432 443 495 498 498 503 531 549 693 811 Copyright 2000. attrition.org Staff in years 1.18 1.21 1.36 1.36 1.36 1.38 1.45 1.50 1.90 2.22 hacks 6 3 16 7 3 47 3 21 5 3 Defacement Counts and Percentages Generic Domains Breakout Defacements Percent International Organizations (int) 11 0.17 Non-Profit Organizations (org) 473 7.20 U.S. Commercial (com) 2749 41.83 U.S. Educational Institutions (edu) 324 4.93 U.S. Government (gov) 198 3.01 Further stats available at www.attrition.org/mirror/attrition/country.html Copyright 2000. attrition.org Staff Defacement Counts and Percentages Country Domains Breakout Defacements Percent Brazil (br) 359 5.46 United States (us) 236 3.59 United Kingdom (uk) 155 2.36 Mexico (mx) 109 1.66 Thailand (th) 5 0.08 Copyright 2000. attrition.org Staff 1999 vs. 2000 Daily Cumulative Total Comparison Copyright 2000. attrition.org Staff Defacements per Day January 1999 - July 2000 : Linear Regression Copyright 2000. attrition.org Staff Defacements per Day January 1999 - July 2000 Copyright 2000. attrition.org Staff Monthly Totals January 1999 - July 2000 Copyright 2000. attrition.org Staff Histogram of Defacements per Day January 1999 - June 2000 Copyright 2000. attrition.org Staff OS Totals by Month Yellow: NT, White: Linux, Orange: BSD, Green: Solaris, Purple: All Other Copyright 2000. attrition.org Staff 29-Day Moving Average All Yellow: NT, Green: Solaris, White: Linux, Orange: BSD, Purple: All Other Copyright 2000. attrition.org Staff Daily Cumulative Totals All Copyright 2000. attrition.org Staff Overall OS Shares Copyright 2000. attrition.org Staff Holiday Attacks After selecting 11 holidays per year, we found that while the average was greater than for nonholidays, the holiday average was not significantly different from the non-holiday average, though there were two holidays that when examined individually were significantly greater than nonholidays: new years eve, 1999 and July 4th, 2000. Defacement activity is not statistically different on holidays than non-holidays Copyright 2000. attrition.org Staff The Future Faster updates of the main mirror page with defacements in real-time The introduction of dynamically generated pages via user-defined queries against our defacement database(s) Never before seen on attrition.org, user interaction with actual pages With the introduction of the SQL database(s), more breakouts pertaining to each defacement mirrored Copyright 2000. attrition.org Staff References Attrition Mirror http://www.attrition.org/mirror Statistics / Graphs http://www.attrition.org/mirror/attrition/stats.html Updated Slide Presentation http://www.attrition.org/mirror/presentation.ppt Copyright 2000. attrition.org Staff Fin Contact Information • Brian Martin jericho@attrition.org • Matt Dickerson munge@attrition.org • Dale Coddington punkis@attrition.org Copyright 2000. attrition.org Staff