Introduction - Witchita State University
advertisement

Chapter 3: Wireless WANs and MANs
Introduction
The Market of Mobile Phone
Systems
The Cellular Concept
Cellular Architecture
The First-Generation Cellular
Systems
The Second-Generation
Cellular Systems
The Third-Generation Cellular
Systems
Wireless in Local Loop
Wireless ATM
IEEE 802.16 Standard
HIPERACCESS
1
The Cellular Concept
To utilize space division multiplexing the area covered by a cellular
network is divided into cells.
An idealized model of the cellular radio system consists of an array
of hexagonal cells with a base station (BS) located at the center of
each cell and a number of mobile terminals (MTs) communicate
with each other through the base station.
• Uplink channels for MTs to communication with the base station
• Downlink channels for BS to communicate with MTs.
The cells are designed for frequency reuse. Same frequency can be
reused in non-nearby cells.
A cluster is a group of cells which uses the entire radio spectrum.
• The cluster size N is the number of cells in each cluster.
• Each cell within a cluster is allocated a distinct set of frequencies (channels)
and cells labeled with a given number – i.e. co-channels reuse the same
channel set.
• As the cell size decreases, traffic carrier capacity increases, and thus cells start
2
big and split as system grows.
The Cellular Concept
Can you tell which the real tree is?
MT
BS
3
The Cellular Concept
With the shift parameters i and j defined in the figure, we see
that the number of cells in a cluster is given by N = i2 + ij + j2
and the frequency reuse distance is given by D = R 3N where
R is the radius of a cell. Examples:
N {i, j}
Reuse Distance
4 {2, 0}
3.46 R
7 {2, 1}
4.58 R
12 {2, 2}
6.00 R
Two types of interference in cellular systems:
• Co-channel interference results from the use of same frequencies in
different clusters.
• Adjacent channel interference results due to usage of adjacent frequencies
within a cluster.
4
The Cellular Concept
Advantages of cell structures:
• higher capacity, higher number of users
• Example: Assume the total bandwidth is 25 MHz and each user requires
30 KHz. A signal cell can support 25000/30 = 833 users. In a cluster of
seven cells each cell can support 833/7 = 119 users. If there are 20 cells,
then the cluster can support 883/7 x 20 = 2380 usrers.
• In general, n = k (S/N) / W where S is the total available spectrum, W is
the bandwidth needed per user, N is the cluster size, an k is the number of
cells required to cover a given area.
• S = 25 MHz, W = 30 KHz, N = 7, and k = 20, then n = 2380.
• less transmission power needed
• more robust, decentralized
• base station deals with interference, transmission area etc. locally
5
Capacity Enhancement
Cell-Splitting: To accommodate a very high density of mobile
subscribers, a cell can divided into a smaller coverage area.
• This smaller cell is called microcell. Microcells are traditionally used in
convention centers, airports and similar areas. A microcell can be further
splitted into picocells.
• The number of handoffs is increased.
Sectorization: To further reduce inter-cluster interference, each cell
is quite often sectored – i.e. directional antennas are used at the
mobile base stations.
• A cell is normally partitioned into three 120-degree sectors or six 60-degree
sectors.
• The number of handoffs is increased.
Power Control: To avoid the near-far problem, the BS must issue
power control orders to the MTs to receive a fairly constant, equal
power from all MTs, irrespective of their distance form the BS.6
Frequency planning
Frequency reuse only with a certain distance
between the base stations. Standard model
using 7 sets of frequencies.
f3
f5
f4
f2
f6
f1
f3
f5
f4
f7
f1
f2
Fixed channel allocation (FCA) – Fixed frequency assignment:
• certain frequencies are assigned to a certain cell
• problem: different traffic load in different cells
Dynamic channel allocation (DCA) – Dynamic frequency
assignment :
• base station chooses frequencies depending on the frequencies already used
in neighbor cells
• more capacity in cells with more traffic
• assignment can also be based on interference measurement
• The allocation scheme is more complex.
Hybrid channel allocation:
• Give two sets of channels to each cell: a set of local channels and a set of
borrowable channels.
7
• Allow to dynamic allocate channels but with intermediate complexity.
Frequency planning
f3
f3
f2
f1
f3
f3
f2
3 cell cluster
f3
f6
f3
f6
f5
f4
f7
f1
f3
f2
f3
f7
f2
f1
f1
f1
f3
f4
f1
f2
f3
f5
f2
f1
f2
f2
f3
f5
f2
7 cell cluster
f2
f2
f2
f1 f
f1 f
f1 f
h
h
3
3
3
h 2
h 2
g2 1 h3 g2 1 h3
g2
g1
g1
g1
g3
g3
g3
3 cell cluster
with 3 sector antennas
8
Cell Breathing
CDM systems: cell size depends on current load
Additional traffic appears as noise to other users
If the noise level is too high users drop out of cells
CDM cell shrinks with the additional user. Two
users drop out of the cell.
9
Handoffs
When a user moves from the coverage area of one BS to the
adjacent one, a handoff (handover) has to be executed to continue
the call. A handoff contains two main parts:
• Find an uplink-downlink channel pair from the new cell to carry on the call
• Drop the link form the original BS.
Issues involved in Handoffs:
• Optimal BS selection
• Ping-pong effect: The call gets bounced back and forth in the boundaries
between different cells. This should be avoided.
• Data loss
• Detection of handoff requirement: Three handoff schemes:
• Mobile-initiated: An MT monitors the signal strength and requests a
handoff when the strength drops below a threshold.
• Network-initiated handoff: The BS forces a handoff if the signals from an
MT weaken.
• Mobile-assisted handoff: An MT evaluates the signal strength and the10 BS
decides the handoff.
Handoffs
Handoff quality is measured by the following parameters (make
sure the carrier to interference ratio (C/I) doesn’t fall below the
minimum):
• Handoff delay: The signaling during a handoff causes a delay in the transfer
of an on-going call from the current cell to the new call.
• Duration of interruption: In hard handoff, the channel pair is switched from
the current cell to the new cell.
• Handoff success: The handoff strategies should maximize the handoff
success rate.
• Probability of unnecessary handoff: Unnecessary handoffs increase the
signaling overhead on the network.
Improved handoff strategies:
• Prioritization: handoffs are given priority over new call requests.
• Relative signal strength: The signal strength in the new cell is stronger than
the current one.
• Soft handoffs: A short period of time when more than one BS handles a call
can be allowed.
• Predictive handoffs: the mobility pattern can be predicted.
• Adaptive handoffs: Users may have to be shifted from micro-cell to macro11
cell.
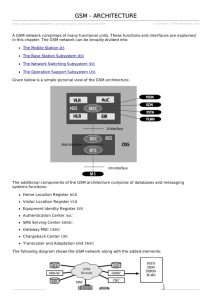
Cellular Architecture
Every cell has a Base Station (BS) to which all Mobile Terminals
(MTs) in the cell communicate.
A Base Station Controller (BSC) controls a set group of BTSs.
Together the BTS and BSC systems are known as the BSS or Base
Station System (BSS) . The BSC is vital to the BSS system in that
it ensures that subscribers can move freely from one cell to another
with no loss in signal strength
A BSC is then connected to a Mobile Switching Center (MSC).
The MSC acts as an interface between the cellular radio system
and the public switched telephone network (PSTN).
The Authentication Center (AuC) validates the MTs by verifying
their identity with the Equipment Identity Register (EIR).
The MSCs are linked through a signaling system 7 (SS7) network,
which controls setting up, managing, and releasing of telephone
calls.
12
Cellular Architecture
The SS7 protocol introduces certain nodes called Signal Transfer
Points (STPs) which help in call routing.
A MT or a mobile station (MS) reports their location to the network
periodically. Each user is permanently associated with the home
location register (HLR) in his/her subscribed cellular network.
This HLR contains the user profile consisting of the services
subscribed by the user, billing information, and location
information.
The Visitor Location Register (VLR) maintains the information
regarding roaming users in the cell. VLRs download the
information from the users’ respective HLRs.
13
Cellular Architecture
STP
HLR
VLR
EIR
GMSC
PSTN
MSC
VLR
MSC
AuC
BSC
BSC
SS7 Network
MT Mobile Terminal
BS Base Station
HLR Home Location Register
VLR Visitor Location Register
EIR Equipment Identity Register
AuC Authentication Center
MSC Mobile Switching Center
STP Signal Transfer Point
PSTN Public Switched
Telephone Network
BSC Base Station Controller
14
Mobile Phone Subscribers Worldwide
approx. 1.7 bn (2004)
1600
GSM: 1.36 bn (June,
2005)
1400
Subscribers [million]
1200
GSM total
1000
TDMA total
CDMA total
PDC total
800
Analogue total
W-CDMA
600
Total wireless
Prediction (1998)
400
200
0
1996
1997
1998
1999
2000
2001
2002
2003
2004
2005
15
year
CT0/1
AMPS
NMT
CT2
IMT-FT
DECT
IS-136
TDMA
D-AMPS
TDMA
FDMA
Development of Mobile
Telecommunication Systems
GSM
PDC
EDGE
GPRS
IMT-SC
IS-136HS
UWC-136
IMT-DS
UTRA FDD / W-CDMA
HSDPA
IMT-TC
CDMA
UTRA TDD / TD-CDMA
IMT-TC
TD-SCDMA
1G
IS-95
cdmaOne
cdma2000 1X
2G
2.5G
IMT-MC
cdma2000 1X EV-DO
1X EV-DV
(3X)
3G
16
1st-Generation Mobile Cellular Systems –
Analog Voice: AMPS
AMPS (Advanced Mobile Phone System) is the analog system
(1G) first developed and used in the U.S. Nordic mobile telephony
(NMT) is a 1G system developed in Europe.
The cellular structure uses a cluster size of seven, and each cell is
roughly 10 – 20 Km across.
The AMPS system uses FDM to separate 832 full-duplex channels.
• 832 simplex transmission channels from 824 to 849 MHz
• 832 simplex receive channels from 869 to 894 MHz
• Each simplex channel is 30 kHz wide.
These channels are divided into four categories:
•
•
•
•
Control (base to mobile) to manage the system (21 channels)
Paging (base to mobile) to alert users to calls for them
Access (bidirectional) for call setup and channel assignment
Data (bidirectional) for voice, fax, or data (45 channels)
AMPS provides a maximum data transmission rate of 10 Kbps.17
1st-Generation Cellular Systems: AMPS
AMPS Operation
• Subscriber initiates call by keying in phone number and presses send key
• MTSO verifies number and authorizes user
• MTSO issues message to user’s cell phone indicating send and receive traffic
channels
• MTSO sends ringing signal to called party
• Party answers; MTSO establishes circuit and initiates billing information
• Either party hangs up; MTSO releases circuit, frees channels, completes
billing
The problem of the first-generation systems:
• No use of encryption
• Inferior call quality
• Spectrum inefficiency
18
2nd-Generation Cellular Phone Systems
Differences between the first and second generation cellular
systems:
• Digital traffic channels – first-generation systems are almost purely analog;
second-generation systems are digital
• Encryption – all second generation systems provide encryption to prevent
eavesdropping
• Error detection and correction – second-generation digital traffic allows for
detection and correction, giving clear voice reception
• Channel access – second-generation systems allow channels to be
dynamically shared by a number of users
Examples of 2G system: Global system for mobile communications
(GSM) in Europe, digital-AMPS (DAMPS) in United States, and
personal digital cellular (PDC) in Japan.
19
GSM: Overview
GSM
• formerly: Groupe Spéciale Mobile (founded 1982)
• now: Global System for Mobile Communication
• Pan-European standard (ETSI, European Telecommunications
Standardization Institute)
• simultaneous introduction of essential services in three phases (1991, 1994,
1996) by the European telecommunication administrations (Germany: D1
and D2) seamless roaming within Europe possible
• today many providers all over the world use GSM (more than 200 countries
in Asia, Africa, Europe, Australia, America)
• more than 1.3 billion subscribers in more than 630 networks
• more than 75% of all digital mobile phones use GSM (74% total)
• over 200 million SMS per month in Germany, > 550 billion/year worldwide
(> 10% of the revenues for many operators)
[be aware: these are only rough numbers…]
Performance Characteristics of GSM
Communication: mobile, wireless communication; support for
voice and data services
Total mobility: international access, chip-card enables use of
access points of different providers
Worldwide connectivity: one number, the network handles
localization
High capacity: better frequency efficiency, smaller cells, more
customers per cell
High transmission quality: high audio quality and reliability for
wireless, uninterrupted phone calls at higher speeds (e.g., from
cars, trains)
Security functions: access control, authentication via chip-card and
PIN
21
Disadvantages of GSM
There is no perfect system!!
no end-to-end encryption of user data
no full ISDN bandwidth of 64 kbit/s to the user, no transparent Bchannel
reduced concentration while driving
electromagnetic radiation
abuse of private data possible
roaming profiles accessible
high complexity of the system
several incompatibilities within the GSM standards
22
GSM Frequency Bands
Type
Channels
Uplink [MHz]
Downlink [MHz]
GSM 850 (Americas)
128-251
824-849
869-894
GSM 900
0-124, 955-1023
876-915
921-960
classical
extended
124 channels
+49 channels
890-915
880-915
935-960
925-960
GSM 1800
512-885
1710-1785
1805-1880
GSM 1900 (Americs)
512-810
1850-1910
1930-1990
GSM-R (Rail)
955-1024, 0-124
876-915
921-960
Exclusive
69 channels
876-880
921-925
450-458
460-468
489-496
GSM 450/480
479-486
Please note: frequency ranges may vary depending on the country!
Channels at the lower/upper edge of a frequency band are typically not used 23
GSM
The cellular structure uses a cluster size of seven, and each cell is
roughly up to 35 Km across.
The modulation scheme used in GSM is Gaussian minimum shift
keying (GMSK).
The GSM uses FDM to separate 124 full-duplex channels.
•
•
•
•
The duplex channels are separated by 45 MHz.
124 simplex uplink channels from 890 to 915 MHz
124 simplex downlink channels from 935to 960 MHz
Each simplex channel is 200 kHz wide.
Each physical channel is divided into eight periodic (0.577 ms)
time slots by TDMA.
8 time slots make up a TDMA frame. 26 TDMA frames make up a
multiframe. Multiframe is grouped into superframes and
hyperframes.
24
GSM
GSM uses 124 frequency channels, each of which
uses an eight-slot TDM system
25
GSM
Each MT is assigned only one slot within each frame, the
maximum speed is around 34 Kbps (1/8 of the 270.8 Kbps
capacity of a 200 KHz GSM carrier).
Forward error correction (FEC) and encryption reduce the data
rate to around 9.6 Kbps.
A slot comprises four parts:
• Header and footer are empty space at the beginning and end of
the slot to separate a slot from its neighbors.
• Training sequence (Training) helps a receiver lock on to the
slot.
• Stealing bits (S) identify whether the slot carries data or control
information.
• Traffic carries user voice/data, control information, and error
correction.
26
GSM - TDMA/FDMA
935-960 MHz
124 channels (200 kHz)
downlink
890-915 MHz
124 channels (200 kHz)
uplink
higher GSM frame structures
time
1250-Bit GSM TDMA Frame
1
2
3
4
5
6
7
8
4.615 ms
148-Bit data frame
GSM time-slot (normal burst)
guard
space
tail
3 bits
8.25-Bit, 546.5 µs
user data
S Training S
user data
57 bits
1 26 bits 1
57 bits
guard
tail space
3
546.5 µs
577 µs
GSM hierarchy of frames
hyperframe
0
1
2
2045 2046 2047 3 h 28 min 53.76 s
...
superframe
0
1
0
2
...
1
48
...
49
24
50
6.12 s
25
multiframe
0
1
...
0
1
24
2
120 ms
25
...
48
49
50
235.4 ms
frame
0
1
...
6
7
4.615 ms
slot
burst
577 µs
28
GSM Frame
A the control channels in GSM are classified into three broad
categories:
• Broadcast control channel (BCCH) is a downlink channel that contains the
BS’s identity and channel status. All MTs monitor the BCCH to detect if they
have moved into a new cell.
• Dedicated control channel (DCCH) is used for call-setup, location updates,
and all call-management information exchange. BS uses DCCH to keep track
of all MTs in its coverage area.
• Common control channel consists of:
• the downlink paging channel is used to page any MT to alert it for an
incoming call.
• the random access channel supports ALOHA-based request from MT to
BS.
• the access grant channel on which the BS informs the MT of an allotted
duplex channel for a call.
29
GSM: Mobile Services
GSM offers
• several types of connections
• voice connections, data connections, short message service
• multi-service options (combination of basic services)
Three service domains
• Bearer Services (data)
• Telematic Services (voice)
• Supplementary Services
Bearer services
MS
TE
MT
R, S
GSM-PLMN
Um
Transit
Network
(PSTN, ISDN)
Telematic services
Source/
Destination
TE
Network
(U, S, R)
30
Bearer Services
Telecommunication services to transfer data between access points
Specification of services up to the terminal interface (OSI layers 13)
Different data rates for voice and data (original standard)
• data service (circuit switched)
• synchronous: 2.4, 4.8 or 9.6 kbit/s
• asynchronous: 300 - 1200 bit/s
• data service (packet switched)
• synchronous: 2.4, 4.8 or 9.6 kbit/s
• asynchronous: 300 - 9600 bit/s
Today: data rates of approx. 50 kbit/s possible
31
Telematic Services
Telecommunication services that enable voice communication
via mobile phones
All these basic services have to obey cellular functions, security
measurements etc.
Offered services
• mobile telephony
primary goal of GSM was to enable mobile telephony offering the
traditional bandwidth of 3.1 kHz
• Emergency number
common number throughout Europe (112); mandatory for all service
providers; free of charge; connection with the highest priority (preemption
of other connections possible)
• Multinumbering
several ISDN phone numbers per user possible
32
Telematic Services
Additional services
• Non-Voice-Teleservices
• group 3 fax
• voice mailbox (implemented in the fixed network supporting the mobile
terminals)
• electronic mail (MHS, Message Handling System, implemented in the
fixed network)
• Short Message Service (SMS)
alphanumeric data transmission to/from the mobile terminal (160
characters) using the signaling channel, thus allowing simultaneous use of
basic services and SMS
(almost ignored in the beginning now the most successful add-on!)
33
Supplementary Services
Services in addition to the basic services, cannot be offered standalone
Similar to ISDN services besides lower bandwidth due to the radio
link
May differ between different service providers, countries and
protocol versions
Important services
•
•
•
•
•
identification: forwarding of caller number
suppression of number forwarding
automatic call-back
conferencing with up to 7 participants
locking of the mobile terminal (incoming or outgoing calls)
34
Architecture of the GSM System
GSM is a PLMN (Public Land Mobile Network)
• several providers setup mobile networks following the GSM standard within
each country
• components
• MS (mobile station)
• BS (base station)
• MSC (mobile switching center)
• LR (location register)
• subsystems
• RSS (radio subsystem): covers all radio aspects
• NSS (network and switching subsystem): call forwarding, handover,
switching
• OSS (operation subsystem): management of the network
35
Architecture of the GSM System
OMC, EIR,
AUC
HLR
NSS
with OSS
VLR
MSC
GMSC
VLR
fixed network
MSC
BSC
BSC
RSS
36
Mobile Terminal: Mobile Phones, PDAs &
Communicator
The visible but smallest
part of the network!
37
Base Station: Antennas
Still visible – cause many discussions…
38
Base Station (BS)
Base Stations
Cabling
Microwave links
39
Mobile Switching Center (MSC)
Not visible, but comprise
the major part of the
network (also from an
investment point of
view…)
Management
Data bases
Switching units
Monitoring
40
Radio subsystem
The Radio Subsystem (RSS) comprises the cellular mobile network
up to the switching centers
Components
• Base Station Subsystem (BSS):
• Base Transceiver Station (BTS): radio components including sender,
receiver, antenna - if directed antennas are used one BTS can cover
several cells
• Base Station Controller (BSC): switching between BTSs, controlling
BTSs, managing of network resources, mapping of radio channels (Um)
onto terrestrial channels (A interface)
• BSS = BSC + sum(BTS) + interconnection
• Mobile Stations (MS)
41
GSM: Cellular Network
segmentation of the area into cells
possible radio coverage of the cell
cell
idealized shape of the cell
use of several carrier frequencies
not the same frequency in adjoining cells
cell sizes vary from some 100 m up to 35 km depending on user density,
geography, transceiver power etc.
hexagonal shape of cells is idealized (cells overlap, shapes depend on
geography)
if a mobile user changes cells
handover of the connection to the neighbor cell
Example Coverage of GSM Networks
(www.gsmworld.com)
T-Mobile (GSM-900/1800) Germany
AT&T (GSM-850/1900) USA
O2 (GSM-1800) Germany
Vodacom (GSM-900) South Africa
43
Base Transceiver Station and Base Station
Controller
Tasks of a BSS are distributed over BSC and BTS
BTS comprises radio specific functions
BSC is the switching center for radio channels
Functions
Management of radio channels
Frequency hopping (FH)
Management of terrestrial channels
Mapping of terrestrial onto radio channels
Channel coding and decoding
Rate adaptation
Encryption and decryption
Paging
Uplink signal measurements
Traffic measurement
Authentication
Location registry, location update
Handover management
BTS
X
X
X
X
X
X
BSC
X
X
X
X
X
X
X
X
X
X
44
Mobile Station
Terminal for the use of GSM services
A mobile station (MS) comprises several functional groups
• MT (Mobile Terminal):
• offers common functions used by all services the MS offers
• corresponds to the network termination (NT) of an ISDN access
• end-point of the radio interface (Um)
• TA (Terminal Adapter):
• terminal adaptation, hides radio specific characteristics
• TE (Terminal Equipment):
• peripheral device of the MS, offers services to a user
• does not contain GSM specific functions
• SIM (Subscriber Identity Module):
• personalization of the mobile terminal, stores user parameters
TE
TA
R
MT
S
Um
45
Network and switching subsystem (NSS)
NSS is the main component of the public mobile network GSM
• switching, mobility management, interconnection to other networks, system
control
Components
• Mobile Services Switching Center (MSC)
controls all connections via a separated network to/from a mobile terminal
within the domain of the MSC - several BSC can belong to a MSC
• Databases (important: scalability, high capacity, low delay)
• Home Location Register (HLR)
central master database containing user data, permanent and semipermanent data of all subscribers assigned to the HLR (one provider can
have several HLRs)
• Visitor Location Register (VLR)
local database for a subset of user data, including data about all user
currently in the domain of the VLR
46
Mobile Services Switching Center
The MSC (mobile switching center) plays a central role in GSM
•
•
•
•
•
switching functions
additional functions for mobility support
management of network resources
interworking functions via Gateway MSC (GMSC)
integration of several databases
Functions of a MSC
•
•
•
•
•
•
•
specific functions for paging and call forwarding
termination of SS7 (signaling system no. 7)
mobility specific signaling
location registration and forwarding of location information
provision of new services (fax, data calls)
support of short message service (SMS)
generation and forwarding of accounting and billing information
47
Operation subsystem
The OSS (Operation Subsystem) enables centralized operation,
management, and maintenance of all GSM subsystems
Components
• Authentication Center (AUC)
• generates user specific authentication parameters on request of a VLR
• authentication parameters used for authentication of mobile terminals and
encryption of user data on the air interface within the GSM system
• Equipment Identity Register (EIR)
• registers GSM mobile stations and user rights
• stolen or malfunctioning mobile stations can be locked and sometimes
even localized
• Operation and Maintenance Center (OMC)
• different control capabilities for the radio subsystem and the network
subsystem
48
Mobile Terminated Call
1: calling a GSM subscriber
2: forwarding call to GMSC
3: signal call setup to HLR
4, 5: request MSRN from VLR
6: forward responsible
calling
station
MSC to GMSC
7: forward call to
current MSC
8, 9: get current status of MS
10, 11: paging of MS
12, 13: MS answers
14, 15: security checks
16, 17: set up connection
HLR
4
5
3 6
1
PSTN
2
GMSC
10
7
VLR
8 9
14 15
MSC
10 13
16
10
BSS
BSS
BSS
11
11
11
11 12
17
MS
49
Mobile Originated Call
1, 2: connection request
3, 4: security check
5-8: check resources (free
circuit)
9-10: set up call
VLR
3 4
6
PSTN
5
GMSC
7
MSC
8
2 9
MS
1
10
BSS
50
MTC/MOC
MS
MTC
BTS
MS
MOC
BTS
paging request
channel request
channel request
immediate assignment
immediate assignment
paging response
service request
authentication request
authentication request
authentication response
authentication response
ciphering command
ciphering command
ciphering complete
ciphering complete
setup
setup
call confirmed
call confirmed
assignment command
assignment command
assignment complete
assignment complete
alerting
alerting
connect
connect
connect acknowledge
connect acknowledge
data/speech exchange
data/speech exchange
51
4 Types of Handover
1
MS
BTS
2
3
4
MS
MS
MS
BTS
BTS
BTS
BSC
BSC
BSC
MSC
MSC
52
Handover Decision
receive level
BTSold
receive level
BTSold
HO_MARGIN
MS
MS
BTSold
BTSnew
53
Handover Procedure
MS
BTSold
BSCold
measurement
measurement
report
result
MSC
HO decision
HO required
BSCnew
BTSnew
HO request
resource allocation
ch. activation
HO command
HO command
HO command
HO request ack ch. activation ack
HO access
Link establishment
clear command clear command
clear complete
HO complete
HO complete
clear complete
54
Security services
Security in GSM
• access control/authentication
• user SIM (Subscriber Identity Module): secret PIN (personal
identification number)
• SIM network: challenge response method
• confidentiality
• voice and signaling encrypted on the wireless link (after successful
authentication)
• anonymity
“secret”:
• temporary identity TMSI
• A3 and A8
(Temporary Mobile Subscriber Identity)
available via the
Internet
• newly assigned at each new location update (LUP)
• network providers
• encrypted transmission
can use stronger
3 algorithms specified in GSM
• A3 for authentication (“secret”, open interface)
• A5 for encryption (standardized)
• A8 for key generation (“secret”, open interface)
mechanisms
55
GSM - Authentication
SIM
mobile network
Ki
RAND
128 bit
AC
RAND
128 bit
RAND
Ki
128 bit
128 bit
A3
A3
SIM
SRES* 32 bit
MSC
SRES* =? SRES
SRES
SRES
32 bit
Ki: individual subscriber authentication key
32 bit
SRES
SRES: signed response
56
GSM - Key Generation and Encryption
MS with SIM
mobile network (BTS)
Ki
AC
RAND
128 bit
RAND
128 bit
RAND
128 bit
A8
cipher
key
BSS
Ki
128 bit
SIM
A8
Kc
64 bit
Kc
64 bit
data
A5
encrypted
data
SRES
data
MS
A5
57
Data Over Voice Channel
The main problems in using a voice network for data
transmission are:
• Signal distortion: Data cannot tolerate the distortion like the voice.
• Handoff error: Handoffs introduce a certain delay in transfer of the call
from one cell to another.
• Interfacing with fixed network: The cellular network should be able to
differentiate between a data call and a voice call.
To make the network recognize a data call, some possible
solutions are:
• A control message could be transmitted all along the path of the call to
indicate a data call so that voice coding can be disabled.
• A two-stage dial-up operation can be used, the cellular carrier is first
dialed, and then the MT is informed of a data call.
• A subscriber could be assigned separate subscriber numbers for each
service he/she opts for.
58
GSM Evolution of Data Services
Short Messaging Service (SMS) is a connectionless transfer of
messages, each up to 160 alphanumeric characters in length.
High-Speed Circuit-Switched Data (HSCSD) is a circuit-switched
protocol for large file transfers and multimedia data transmissions.
• Offer a data rate of 57.6 Kbps
• Increase blocking probability
General Packet Radio Service (GPRS) uses TCP/IP and X.25 to
provide a high-capacity connection (up to 171.2 Kbps) to the
Internet.
Enhanced Data Rates for GSM Evolution (EDGE) uses 8-PSK to
triple the capacity of GSM.
Cellular Digital Packet Data (CDPD) is a packet-based data
service on AMPS and IS-136 systems.
59
Data services in GSM
Data transmission standardized with only 9.6 kbit/s
• advanced coding allows 14,4 kbit/s
• not enough for Internet and multimedia applications
HSCSD (High-Speed Circuit Switched Data)
• mainly software update
• bundling of several time-slots to get higher
AIUR (Air Interface User Rate)
(e.g., 57.6 kbit/s using 4 slots, 14.4 each)
• advantage: ready to use, constant quality, simple
• disadvantage: channels blocked for voice transmission
AIUR [kbit/s]
4.8
9.6
14.4
19.2
28.8
38.4
43.2
57.6
TCH/F4.8
1
2
3
4
TCH/F9.6
TCH/F14.4
1
1
2
3
4
2
3
4
60
Data services in GSM
GPRS (General Packet Radio Service)
• packet switching
• using free slots only if data packets ready to send
(e.g., 50 kbit/s using 4 slots temporarily)
• standardization 1998, introduction 2001
• advantage: one step towards UMTS, more flexible
• disadvantage: more investment needed (new hardware)
GPRS network elements
• GSN (GPRS Support Nodes): GGSN and SGSN
• GGSN (Gateway GSN)
• interworking unit between GPRS and PDN (Packet Data Network)
• SGSN (Serving GSN)
• supports the MS (location, billing, security)
• GR (GPRS Register)
• user addresses
61
GPRS quality of service
Reliability
class
Lost SDU
probability
Duplicate
SDU
probability
1
2
3
10-9
10-4
10-2
10-9
10-5
10-5
Delay
class
1
2
3
4
Out of
sequence
SDU
probability
10-9
10-5
10-5
Corrupt SDU
probability
10-9
10-6
10-2
SDU size 128 byte
SDU size 1024 byte
mean
95 percentile
mean
95 percentile
< 0.5 s
< 1.5 s
<2s
<7s
<5s
< 25 s
< 15 s
< 75 s
< 50 s
< 250 s
< 75 s
< 375 s
unspecified
62
Examples for GPRS device classes
Class
Receiving
slots
Sending slots
Maximum number of slots
1
1
1
2
2
2
1
3
3
2
2
3
5
2
2
4
8
4
1
5
10
4
2
5
12
4
4
5
63
GPRS user data rates in kbit/s
Coding
scheme
1 slot
2 slots
3 slots
4 slots
5 slots
6 slots
7 slots
8 slots
CS-1
9.05
18.1
27.15
36.2
45.25
54.3
63.35
72.4
CS-2
13.4
26.8
40.2
53.6
67
80.4
93.8
107.2
CS-3
15.6
31.2
46.8
62.4
78
93.6
109.2
124.8
CS-4
21.4
42.8
64.2
85.6
107
128.4
149.8
171.2
64
D-AMPS
D-AMPS (Digital-AMPS) is the first digital version (2G) of
AMPS.
• It uses the 800 or 1900 MHz spectrum.
• Each simplex channel is 30 kHz wide.
• It is described in IS-54 and IS-136.
It is also known as TDMA (Time Division Multiple Access).
• Several physical channels are located by dividing one frequency channel
into several time slots.
• The advantage of TDMA is that several channels are co-located on one
carrier frequency, so there are less transmitters required.
65
D-AMPS
Digital Advanced Mobile Phone System
(a) A D-AMPS channel with three users.
(b) A D-AMPS channel with six users.
66
CDMA
CDMA (Code Division Multiple Access) is a standard using
spread spectrum transmission (2G).
• The original CDMA standard, also known as cdmaOne and still common in
cellular telephones in the U.S., offers a transmission speed of up to 14.4 Kbps
in its single channel form and up to 115 Kbps in an eight-channel form.
• It operates in the 800 and 1900 MHz bands.
• Each simplex channel is 1.25 MHz wide.
• It can carry data at rates up to 115 kbps.
Operation of CDMA:
• In CDMA, the input signals are digitized and transmitted in coded, spreadspectrum mode over a broad range of frequencies.
• In CDMA, each bit time is subdivided into m short intervals called chips.
Typically, there are 64 or 128 chips per bit.
• Each station is assigned a unique m-bit code called a chip sequence.
• To transmit a 1 bit, a station sends its chip sequence. To transmit a 0 bit, the
station sends the one’s complement of its chip sequence.
• The receiver can “tune” into this signal if it knows the chip sequence (pseudo
67
random number), tuning is done via a correlation function
CDMA – Code Division Multiple Access
(a) Binary chip sequences for four stations
(b) Bipolar chip sequences
(c) Six examples of transmissions
(d) Recovery of station C’s signal
68
CDMA
Advantages of CDMA Cellular
• Frequency diversity – frequency-dependent transmission impairments have less effect
on signal. All terminals can use the same frequency, no planning needed.
• Huge code space (e.g. 232) compared to frequency space
• Multipath resistance – chipping codes used for CDMA exhibit low cross correlation
and low autocorrelation. Interferences (e.g. white noise) is not coded.
• Privacy – privacy is inherent since spread spectrum is obtained by use of noise-like
signals
• forward error correction and encryption can be easily integrated
• Graceful degradation – system only gradually degrades as more users access the
system
Disadvantages of CDMA Cellular
• higher complexity of a receiver (receiver cannot just listen into the medium and start
receiving if there is a signal)
• Self-jamming – arriving transmissions from multiple users not aligned on chip
boundaries unless users are perfectly synchronized
• Near-far problem – signals closer to the receiver are received with less attenuation
than signals farther away. All signals should have the same strength at a receiver.
• Soft handoff – requires that the mobile acquires the new cell before it relinquishes the
old; this is more complex than hard handoff used in FDMA and TDMA schemes69
CDMA
CDMA Design Considerations
• Bandwidth – limit channel usage to 5 MHz
• Chip rate – depends on desired data rate, need for error control, and
bandwidth limitations; 3 Mbps or more is reasonable
• Multirate – advantage is that the system can flexibly support multiple
simultaneous applications from a given user and can efficiently use
available capacity by only providing the capacity required for each service
Before CDMA is adopted as the 3G standard, the CDMA debate
is as follows:
Claims
Reality
Capacity of 20 times that of AMPS
No more dropped calls
No problem of interference
Quality of speech promised at 8 Kbps
Only 3-4 times that of AMPS
40% dropped calls when loaded
Interference from existing AMPS
Had to change to 13 Kbsp
70
Access method CDMA
What is a good code for CDMA?
• A good autocorrelation (the absolute value of the inner product of a
vector multiplied by itself should be large)
• Orthogonal to other codes (Two vectors are called orthogonal if their
inner product is 0.
Examples of a good CDMA code:
• The Baker code (+1, -1, +1, +1, -1, +1, +1, +1, -1, -1, -1)
• a good autocorrelation: the inner product is large, 11.
(+1, -1, +1, +1, -1, +1, +1, +1, -1, -1, -1) (+1, -1, +1, +1, -1, +1, +1, +1, -1, -1, -1) = 11
• Orthogonal to other codes
(+1, -1, +1, +1, -1, +1, +1, +1, -1, -1, -1) (+1, +1, -1, +1, -1, -1, +1, +1, +1, -1, + 1) = 1
• used for ISDN and IEEE 802.11.
71
CDMA in Theory
Sender A
• sends Ad = 1, key Ak = 010011 (assign: ‘0’ = -1, ‘1’= +1)
• sending signal As = Ad * Ak = (-1, +1, -1, -1, +1, +1)
Sender B
• sends Bd = 0, key Bk = 110101 (assign: ‘0’ = -1, ‘1’ = +1)
• sending signal Bs = Bd * Bk = (-1, -1, +1, -1, +1, -1)
Both signals superimpose in space
• interference neglected (noise etc.)
• As + Bs = (-2, 0, 0, -2, +2, 0)
Receiver wants to receive signal from sender A
• apply key Ak bitwise (inner product)
• Ae = (-2, 0, 0, -2, +2, 0) Ak = 2 + 0 + 0 + 2 + 2 + 0 = 6
• result greater than 0, therefore, original bit was ‘1’
• receiving B
• Be = (-2, 0, 0, -2, +2, 0) Bk = -2 + 0 + 0 - 2 - 2 + 0 = -6, i.e. ‘0’
72
CDMA on signal level (1)
data A
1
0
Ad
1
key A
key
sequence A
data key
0
1
0
1
0
0
1
0
0
0
1
0
1
1
0
0
1
1
1
0
1
0
1
1
1
0
0
0
1
0
0
0
1
1
0
0
Ak
As
signal A
Real systems use much longer keys resulting in a larger distance
between single code words in code space.
73
CDMA on signal level (2)
As
signal A
data B
key B
key
sequence B
data key
signal B
1
0
Bd
0
0
0
0
1
1 0
1
0
1 0
0
0
0
1 0
1
1
1
1
1
1
0
0 1
1
0
1 0
0
0
0
1 0
1
1
1
Bk
Bs
As + Bs
74
CDMA on signal level (3)
data A
1
0
1
1
0
1
Ad
As + B s
Ak
(As + Bs)
* Ak
integrator
output
comparator
output
75
CDMA on signal level (4)
data B
1
0
0
1
0
0
Bd
As + B s
Bk
(As + Bs)
* Bk
integrator
output
comparator
output
76
CDMA on signal level (5)
As + B s
wrong
key K
(As + Bs)
*K
integrator
output
comparator
output
(0)
(0)
?
77
3rd-Generation Cellular Systems: Digital
Voice and Data
The aim of the 3G cellular system is to provide a virtual home
environment, that offers a uniform and continuous presentation of
services, independent of location and access.
From the user point of view, the 3G systems with very high-speed
wireless communications (up to 2 Mbps) plan to offer Internet
access (e-mail, Web surfing, including pages with audio and
video), telephony (voice, video, fax, etc.), and multimedia (playing
music, viewing videos, films, television, etc.) services.
Evolution to 3 G
Country
Existing 2G Standard
China
Europe
Japan
USA
USA
GSM
GSM
PDC
IS-95/cdmaOne
IS-136
3G Standard
TD-SCDMA
W-CDMA (UMTS)
W-CDMA (DoCoMo)
Cdma2000
UWC-136
78
Third-Generation Mobile Phones:
Digital Voice and Data
Factors which drives the telephony industry:
1. Data traffic exceeds voice traffic.
2. Design a lightweight portable device with versatile functions (telephone,
music player, gaming device, digital camera, Web interface, and more).
IMT-2000 (International Mobile Telecommunication-2000)
network should provide
•
•
•
•
High-quality voice transmission
Messaging (replace e-mail, fax, SMS, chat, etc.)
Multimedia (music, videos, films, TV, etc.)
Internet access (web surfing, w/multimedia.)
Proposals for IMT-2000
• UWC-136, cdma2000, WP-CDMA
• UMTS (Universal Mobile Telecommunications System) from ETSI
79
3G Standards: UMTS and IMT-2000
UMTS
• UTRA (was: UMTS, now: Universal Terrestrial Radio Access)
• Enhancements of GSM
• EDGE (Enhanced Data rates for GSM Evolution): GSM up to 384 kbit/s
• CAMEL (Customized Application for Mobile Enhanced Logic)
• VHE (virtual Home Environment)
• Fits into GMM (Global Multimedia Mobility) initiative from ETSI
• Requirements
• min. 144 kbit/s rural (goal: 384 kbit/s)
• min. 384 kbit/s suburban (goal: 512 kbit/s)
• up to 2 Mbit/s urban
80
Frequencies for IMT-2000
1850
1900
ITU allocation
(WRC 1992)
Europe
China
1950
IMT-2000
GSM DE
1800 CT
GSM
1800
Japan
T
D
D
North
America
1900
T
D
D
MSS
2000
2200
MHz
MSS
UTRA MSS
FDD
IMT-2000
MSS
cdma2000 MSS
W-CDMA
MSS
1950
2100 2150
IMT-2000
cdma2000 MSS
W-CDMA
PCS
1850
2050
MSS
UTRA MSS
FDD
IMT-2000
PHS
2000
rsv.
2050
2100 2150
MSS
2200
MHz
81
UMTS and IMT-2000
IMT-2000 family
• IMT-DS: The direct spread technology comprises wideband CDMA (WCDMA) systems. It consists of UTRA-FDD in Europe and FOMA (Freedom
of Mobile Multimedia Access in Japan developed by 3GPP (3rd Generation
Partnership Project).
• IMT-TC: The time code technology uses time-division CDMA (TDCDMA). It consists of UTRA-TDD in Europe and TD-synchronous CDMA
(TD-SCDMA) in China developed by 3GPP.
• IMT-MC: The multi-carrier technology comprises cdma2000 developed by
3GPP2.
• IMT-SC: The single carrier technology comprises the enhancement of the
US TDMA, UWC-136. It applies EDGE (Enhanced Data Rates for Global
Evolution) developed by 3GPP/UWCC.
• IMT-FT: The frequency time technology comprises an enhanced version of
DECT developed by ETSI.
82
IMT-2000 family
Interface
for Internetworking
IMT-2000
Core Network
ITU-T (Telecomm.)
GSM
(MAP)
Initial UMTS
(R99 w/ FDD)
IMT-2000
Radio Access
ITU-R
(Radiocomm.)
ANSI-41
(IS-634)
IP-Network
Flexible assignment of
Core Network and Radio Access
IMT-DS
IMT-TC
IMT-MC
IMT-SC
IMT-FT
(Direct Spread)
(Time Code)
(Multi Carrier)
(Single Carrier)
(Freq. Time)
UTRA FDD
(W-CDMA)
3GPP
UTRA TDD
(TD-CDMA);
TD-SCDMA
3GPP
cdma2000
UWC-136
(EDGE)
UWCC/3GPP
DECT
3GPP2
ETSI
The main driving forces are 3GPP (European and Japanese) and
83
3GPP2 (Qualcomm and CDMA).
GSM and UMTS Releases
GSM/EDGE Release
3G Release
Abbreviated name
Spec version
number
Freeze date
(indicative only)
Phase 2+ Release 6
Release 6
Rel-6
6.x.y
December 2004 March 2005
Phase 2+ Release 5
Release 5
Rel-5
5.x.y
March - June 2002
Phase 2+ Release 4
Release 4
Rel-4
4.x.y
March 2001
-
Release 2000
Phase 2+ Release 2000
-
-
Release 1999
R00
4.x.y
9.x.y
Renaming…
3.x.y
R99
8.x.y
March 2000
Phase 2+ Release 1999
-
Phase 2+ Release 1998
-
R98
7.x.y
early 1999
Phase 2+ Release 1997
-
R97
6.x.y
early 1998
Phase 2+ Release 1996
-
R96
5.x.y
early 1997
Phase 2
-
Ph2
4.x.y
1995
Phase 1
-
Ph1
3.x.y
1992
84
UMTS architecture (Release 99)
UTRAN (UTRA Network)
• Cell level mobility
• Radio Network Subsystem (RNS)
• Encapsulation of all radio specific tasks
UE (User Equipment)
CN (Core Network)
• Inter system handover
• Location management if there is no dedicated connection between UE and
UTRAN
Uu
UE
Iu
UTRAN
CN
85
UMTS domains and interfaces
Home
Network
Domain
Zu
Cu
USIM
Domain
Mobile
Equipment
Domain
Uu
Access
Network
Domain
Iu
Serving
Network
Domain
Yu
Transit
Network
Domain
Core Network Domain
User Equipment Domain
Infrastructure Domain
User Equipment Domain
• Assigned to a single user in order to access UMTS services
Infrastructure Domain
• Shared among all users
• Offers UMTS services to all accepted users
86
UMTS domains and interfaces
Universal Subscriber Identity Module (USIM)
• Functions for encryption and authentication of users
• Located on a SIM inserted into a mobile device
Mobile Equipment Domain
• Functions for radio transmission
• User interface for establishing/maintaining end-to-end connections
Access Network Domain
• Access network dependent functions
Core Network Domain
• Access network independent functions
• Serving Network Domain
• Network currently responsible for communication
• Home Network Domain
• Location and access network independent functions
87
UMTS FDD frame structure
Radio frame
10 ms
0
1
2
...
12
13
14
Time slot
666.7 µs
Pilot
TFCI
FBI
TPC
uplink DPCCH
2560 chips, 10 bits
666.7 µs
uplink DPDCH
Data
2560 chips, 10*2k bits (k = 0...6)
666.7 µs
Data1 TPC TFCI Data2
Pilot
downlink DPCH
DPDCH DPCCH DPDCH DPCCH
2560 chips, 10*2k bits (k = 0...7)
Slot structure NOT for user separation
but synchronisation for periodic functions!
W-CDMA
• 1920-1980 MHz uplink
• 2110-2170 MHz downlink
• chipping rate:
3.840 Mchip/s
• soft handover
• QPSK
• complex power control
(1500 power control
cycles/s)
• spreading: UL: 4-256;
DL:4-512
FBI: Feedback Information
TPC: Transmit Power Control
TFCI: Transport Format Combination Indicator
DPCCH: Dedicated Physical Control Channel
DPDCH: Dedicated Physical Data Channel
DPCH: Dedicated Physical Channel
88
Typical UTRA-FDD uplink data rates
64
144
384
User data rate [kbit/s]
12.2
(voice)
DPDCH [kbit/s]
60
240
480
960
DPCCH [kbit/s]
15
15
15
15
Spreading
64
16
8
4
89
UMTS TDD frame structure (burst type 2)
Radio frame
10 ms
666.7 µs
0
1
2
Time slot
Data
Midample
1104 chips 256 chips
2560 chips
...
Data
GP
1104 chips
12
13
14
Traffic burst
GP: guard period
96 chips
TD-CDMA
2560 chips per slot
spreading: 1-16
symmetric or asymmetric slot assignment to UL/DL (min. 1 per direction)
tight synchronisation needed
simpler power control (100-800 power control cycles/s)
90
UTRAN architecture
RNS
UE1
Node B
Iub
RNC: Radio Network Controller
RNS: Radio Network Subsystem
Iu
RNC
CN
UE2
Node B
UE3
Iur
Node B
Iub
Node B
RNC
UTRAN comprises several
RNSs
Node B can support FDD or
TDD or both
RNC is responsible for
handover decisions requiring
signalingto the UE
Cell offers FDD or TDD
Node B
RNS
91
UTRAN functions
Admission control
Congestion control
System information broadcasting
Radio channel encryption
Handover
SRNS moving
Radio network configuration
Channel quality measurements
Macro diversity
Radio carrier control
Radio resource control
Data transmission over the radio interface
Outer loop power control (FDD and TDD)
Channel coding
Access control
92
Core network: protocols
VLR
MSC
GSM-CS
backbone
RNS
GMSC
PSTN/
ISDN
GGSN
PDN (X.25),
Internet (IP)
HLR
RNS
Layer 3: IP
Layer 2: ATM
Layer 1: PDH,
SDH, SONET
UTRAN
SGSN
GPRS backbone (IP)
SS 7
CN
93
Core network: architecture
VLR
BTS
Abis
BSS
BSC
Iu
MSC
GMSC
PSTN
Node
BTSB
IuCS
AuC
EIR
HLR
GR
Node B
Iub
Node B
RNC
SGSN
GGSN
Gn
Node B
RNS
IuPS
Gi
CN
94
Core network
The Core Network (CN) and thus the Interface Iu, too, are
separated into two logical domains:
Circuit Switched Domain (CSD)
•
•
•
•
Circuit switched service incl. signaling
Resource reservation at connection setup
GSM components (MSC, GMSC, VLR)
IuCS
Packet Switched Domain (PSD)
• GPRS components (SGSN, GGSN)
• IuPS
Release 99 uses the GSM/GPRS network and adds a new radio
access!
• Helps to save a lot of money …
• Much faster deployment
• Not as flexible as newer releases (5, 6)
95
UMTS protocol stacks (user plane)
UE
Uu
UTRAN
IuCS
3G
MSC
apps. &
protocols
Circuit
switched
RLC
MAC
RLC
MAC
radio
radio
UE
Packet
switched
apps. &
protocols
IP, PPP,
…
PDCP
Uu
SAR
SAR
AAL2
AAL2
ATM
ATM
UTRAN
IuPS
3G
SGSN
Gn
IP tunnel
3G
GGSN
IP, PPP,
…
GTP
RLC
RLC
GTP
UDP/IP
MAC
MAC
AAL5
AAL5
L2
L2
radio
radio
ATM
ATM
L1
L1
PDCP
GTP
UDP/IP UDP/IP
GTP
UDP/IP
96
Support of mobility: macro diversity
Multicasting of data via several
physical channels
• Enables soft handover
• FDD mode only
UE
Node B
Uplink
Node B
RNC
CN
• simultaneous reception of UE data
at several Node Bs
• Reconstruction of data at Node B,
SRNC or DRNC
Downlink
• Simultaneous transmission of data
via different cells
• Different spreading codes in
different cells
97
Support of mobility: handover
From and to other systems (e.g., UMTS to GSM)
• This is a must as UMTS coverage will be poor in the beginning
RNS controlling the connection is called SRNS (Serving RNS)
RNS offering additional resources (e.g., for soft handover) is called
Drift RNS (DRNS)
End-to-end connections between UE and CN only via Iu at the
SRNS
• Change of SRNS requires change of Iu
• Initiated by the SRNS
• Controlled by the RNC and CN
Node B
Iub
UE
CN
SRNC
Node B
Iur
Iu
DRNC
Iub
98
Example Handover Types in UMTS/GSM
UE1
Node B1
UE2
UE3
UE4
RNC1
3G MSC1
Iu
Node B2
Iur
Iub
Node B3
RNC2
3G MSC2
BTS
BSC
2G MSC3
Abis
A
99
Breathing Cells
GSM
• Mobile device gets exclusive signal from the base station
• Number of devices in a cell does not influence cell size
UMTS
• Cell size is closely correlated to the cell capacity
• Signal-to-nose ratio determines cell capacity
• Noise is generated by interference from
• other cells
• other users of the same cell
• Interference increases noise level
• Devices at the edge of a cell cannot further increase their output power (max.
power limit) and thus drop out of the cell
no more communication possible
• Limitation of the max. number of users within a cell required
• Cell breathing complicates network planning
100
Breathing Cells: Example
101
UMTS services (originally)
Data transmission service profiles
Service Profile
High Interactive MM
High MM
Bandwidth
Transport mode
128 kbit/s Circuit switched
2 Mbit/s Packet switched
Medium MM
384 kbit/s Circuit switched
Switched Data
14.4 kbit/s Circuit switched
Simple Messaging
14.4 kbit/s Packet switched
Voice
Bidirectional, video telephone
Low coverage, max. 6 km/h
asymmetrical, MM, downloads
SMS successor, E-Mail
16 kbit/s Circuit switched
Virtual Home Environment (VHE)
• Enables access to personalized data independent of location, access network,
and device
• Network operators may offer new services without changing the network
• Service providers may offer services based on components which allow the
automatic adaptation to new networks and devices
102
• Integration of existing IN services
Example 3G Networks: Japan
FOMA (Freedom Of Mobile multimedia
Access) in Japan
Examples for FOMA phones
103
Example 3G networks: Australia
cdma2000 1xEV-DO in Melbourne/Australia
Examples for 1xEV-DO devices
104
Isle of Man – Start of UMTS in Europe as
Test
105
UMTS in Monaco
106
UMTS in Europe
Orange/UK
Vodafone/Germany
107
Some current Enhancements
GSM
• EMS/MMS
• EMS: 760 characters possible by chaining SMS, animated icons, ring
tones, was soon replaced by MMS (or simply skipped)
• MMS: transmission of images, video clips, audio
• see WAP 2.0 / chapter 10
• EDGE (Enhanced Data Rates for Global [was: GSM] Evolution)
• 8-PSK instead of GMSK, up to 384 kbit/s
• new modulation and coding schemes for GPRS EGPRS
• MCS-1 to MCS-4 uses GMSK at rates 8.8/11.2/14.8/17.6 kbit/s
• MCS-5 to MCS-9 uses 8-PSK at rates 22.4/29.6/44.8/54.4/59.2 kbit/s
UMTS
• HSDPA (High-Speed Downlink Packet Access)
• initially up to 10 Mbit/s for the downlink, later on 20 Mbit/s using MIMO(Multiple Input Multiple Output-) antennas
108
• uses 16-QAM instead of QPSK
Wireless Local Loops
Business practice of a long-distance telephone company for the
local phone service:
•
•
•
•
It must buy or lease a building for the end office.
It must fill the end office with switches.
It must run a fiber between the end office and the toll office.
It must acquire customer.
How is the new local phone company provides the last hop (local
loop) connectivity between the subscriber and PSTN?
• Buy the right to lay the new wires. Costly
• Buy/lease from other local phone company. Costly
• Use the Wireless Local Loop (WWL), also known as fixed wireless access
(FWA)
• A fixed telephone using a wireless local loop is different from a
mobile phone in three ways:
• The wireless local loop customer often wants high-speed Internet
connectivity.
• A directional antenna is needs to be installed.
• The user does not move.
109
Wireless Local Loops
A WLL system consists of:
• The BS is implemented by the base transceiver station system (BTS) and
the base station controller (BSC).
• The BTS, also called radio port (RP) or radio-transceiver unit (RTU),
performs channel coding, modulation/demodulation, and implements the
radio interface for transmission and reception of radio signals.
• A BSC, called the radio port control unit (RPCU), controls one or more
BTSs and provides them with an interface to the local exchange.
• The fixed subscriber unit (FSU) or radio subscriber unit (RSU) is the
interface between the subscriber’s wired devices and the WLL network. The
FSU performs all physical and data-link layer functions from the subscriber
end.
Cellular-based WLL systems
• Based on TDMA and CDMA.
• IS-95-based CDMA WLL, 9.6 Kbps or 14.4 Kbps
110
Wireless Local Loops
Architecture of an LMDS system.
111
A WLL Example
112
Wireless Local Loops
Cordless-based WLL systems
• Digital Enhanced Cordless Telecommunications (DECT) is a radio interface
standard developed by ETSI, operates in 1880 – 1990 MHz, ranges over
100m ~ 500m, provides120 duplex channels of 144 KHz/pair, offers 32
Kbps, and uses dynamic channel allocation.
• Personal Access Communication System (PACS) is based on TDMA and
QPSK, and supports up to 32 Kbps
• Personal Handy phone System (PHS) is developed in Japan, operates at
1900 MHz with 300 KHz per channel, and supports up to 384 Kbps.
Proprietary systems: E-TDMA of Hughes Network Systems
(HNS), Lucent’s Wireless Subscriber System, Qualcomm’s QCTel,
Lucent’s Airloop.
Broadband Wireless Access
• Local Multipoint Distribution System (LMDS) operates at 28 GHz in USA
and at 40 GHz in Europe, covers the area of 1- 2 Km, and offers up to 155
Mbps.
• Multichannel multipoint distribution service (MMDS) operates at 2.5 GHz
and at 5.8 GHz, covers the area of 45 Km, and offers up to 36 Mbps. 113
Comparison
WLL
Mobile Wireless
Wireline
Good Line of Sigth
(LOS) component
Mainly diffuse
components
No diffuse
components
Rician fading
Rayleigh fading
No fading
Narrowbeam
directed antennas
Omnidirectional
antennas
Expensive wires
High Channel reuse
Less Channel reuse
Reuse Limited by
wiring
Simple design,
constant channel
Expensive DSPs,
power control
Expensive to build
and maintain
Low in-premises
mobility only, easy
access
High mobility
allowed, easy access
Low in-premises
mobility, wiring of
distant areas
cumbersome
Weather conditions
effects
Not very reliable
Very reliable
114
Communication Satellites
Geostationary Satellites (GEO)
• VSAT (Very Small Aperture Terminals): 1-meter antennas, DirecPC
Medium-Earth Orbit Satellites (MEO)
Low-Earth Orbit Satellites (LEO)
• Iridium: Iridium Satellite LLC provides satellite voice and data services.
Iridium makes this possible through its constellation of 66 low-earth
orbiting (LEO), cross-linked satellites and 12 in-orbit spares.
• Globalstar provides affordable, dependable high quality satellite voice and
data service through its 48 satellites.
• Teledesic was a 1990s proposal to use 30 satellites to build a commercial
broadband satellite constellation for Internet services. Teledesic was
notable for gaining early funding from Craig McCaw and Bill Gates, and
for achieving allocation of Ka band frequency spectrum for nongeostationary services.
Global Positioning System (GPS) is a system of satellites and
receiving devices used to compute positions on the Earth.
115
Communication Satellites
Communication satellites and some of their properties,
including altitude above the earth, round-trip delay time
and number of satellites needed for global coverage. 116
Communication Satellites
The principal satellite bands.
117
Low-Earth Orbit Satellites
Iridium
(a) The Iridium satellites from six necklaces around the earth.
(b) 1628 moving cells cover the earth.
118
Globalstar
(a) Relaying in space: Iridium
(b) Relaying on the ground: Globalstar
119
Some History: Why wireless ATM?
Today we face two major trends in communications: broadband
multimedia and mobility.
Thus there is a strong demand for broadband wireless networks
which support advanced multimedia applications running on a
variety of terminals and in different environments.
While fixed network technologies like ATM promise to provide
differentiated Quality of Service (QoS), nowadays wireless cellular
networks (e.g., GSM, IS-54) and wireless LANs (e.g.,
HIPERLAN1 - HIgh PErformance Radio Local Area Network,
IEEE 802.11) are mainly single service networks which are not
able to meet the above mentioned future requirements.
Therefore, the wireless ATM working group of the ATM Forum is
specifying various extensions to ATM protocols in order to cope
with the user mobility and wireless access
120
Some History: Why wireless ATM?
Seamless connection to wired ATM, an integrated service highperformance network supporting different types a traffic streams.
B-ISDN (Broadband ISDN) uses ATM as backbone infrastructure
and integrates several different services in one universal system.
Mobile phones and mobile communications have an ever
increasing importance in everyday life.
Current wireless LANs do not offer adequate support for
multimedia data streams.
Merging mobile communication and ATM leads to wireless ATM
from a telecommunication provider point of view
Goal: seamless integration of mobility into B-ISDN
Problem: very high complexity of the system – never reached
products
121
ATM - Basic Principle
favored by the telecommunication industry for advanced highperformance networks, e.g., B-ISDN, as transport mechanism
statistical (asynchronous, on demand) TDM (ATDM, STDM)
cell header determines the connection the user data belongs to
mixing of different cell-rates is possible
• different bit-rates, constant or variable, feasible
interesting for data sources with varying bit-rate:
• e.g., guaranteed minimum bit-rate
• additionally bursty traffic if allowed by the network
ATM cell:
5
48
cell header
user data
connection identifier, checksum etc.
[byte]
Cell-based transmission
asynchronous, cell-based transmission as basis for ATM
continuous cell-stream
additional cells necessary for operation and maintenance of the
network (OAM cells; Operation and Maintenance)
OAM cells can be inserted after fixed intervals to create a logical
frame structure
if a station has no data to send it automatically inserts idle cells that
can be discarded at every intermediate system without further
notice
if no synchronous frame is available for the transport of cells (e.g.,
SDH or Sonet) cell boundaries have to be detected separately (e.g.,
via the checksum in the cell header)
B-ISDN protocol reference model
3 dimensional reference model
• three vertical planes (columns)
• user plane
• control plane
• management plane
management plane
layers
ATM adaptation layer
ATM layer
physical layer
planes
plane management
• physical layer
• ATM layer
• ATM adaptation layer
Out-of-Band-Signaling: user data is
transmitted separately from control
information
layer management
• three hierarchical layers
control
user
plane
plane
higher
higher
layers
layers
ATM layers
Physical layer, consisting of two sub-layers
• physical medium dependent sub-layer
• coding
• bit timing
• transmission
• transmission convergence sub-layer
• HEC (Header Error Correction) sequence generation and verification
• transmission frame adaptation, generation, and recovery
• cell delineation, cell rate decoupling
ATM layer
•
•
•
•
cell multiplexing/demultiplexing
VPI/VCI translation
cell header generation and verification
GFC (Generic Flow Control)
ATM adaptation layer (AAL)
125
ATM adaptation layer (AAL)
Provides different service classes on top of ATM based on:
• bit rate:
• constant bit rate: e.g. traditional telephone line
• variable bit rate: e.g. data communication, compressed video
• time constraints between sender and receiver:
• with time constraints: e.g. real-time applications, interactive voice and
video
• without time constraints: e.g. mail, file transfer
• mode of connection:
• connection oriented or connectionless
AAL consists of two sub-layers:
• Convergence Sublayer (CS): service dependent adaptation
• Common Part Convergence Sublayer (CPCS)
• Service Specific Convergence Sublayer (SSCS)
• Segmentation and Reassembly Sublayer (SAR)
• sub-layers can be empty
126
ATM and AAL connections
end-system A
AAL
ATM
end-system B
service dependent
AAL connections
service independent
ATM connections
physical
layer
AAL
ATM
physical
layer
ATM network
application
ATM layer:
• service independent transport of ATM cells
• multiplex and demultiplex functionality
AAL layer: support of different services
ATM Forum Wireless ATM Working Group
ATM Forum founded the Wireless ATM Working Group June 1996
(http://www.atmforum.com/)
Task: development of specifications to enable the use of ATM technology also
for wireless networks with a large coverage of current network scenarios
(private and public, local and global)
compatibility to existing ATM Forum standards important
it should be possible to easily upgrade existing ATM networks with mobility
functions and radio access
HIPERLAN/2 offers the capabilities of WATM.
Two sub-groups of work items
Radio Access Layer (RAL) Protocols
• radio access layer
• wireless media access control
• wireless data link control
• radio resource control
• handover issues
Mobile ATM Protocol Extensions
• handover signaling
• location management
• mobile routing
• traffic and QoS Control
• network management
128
WATM services
Office environment
• multimedia conferencing, online multimedia database access
Universities, schools, training centers
• distance learning, teaching
Industry
• database connection, surveillance, real-time factory management
Hospitals
• reliable, high-bandwidth network, medical images, remote monitoring
Home
• high-bandwidth interconnect of devices (TV, CD, PC, ...)
Networked vehicles
• trucks, aircraft etc. interconnect, platooning, intelligent roads
129
WATM components
WMT (Wireless Mobile ATM Terminal)
RAS (Radio Access System)
EMAS-E (End-user Mobility-supporting ATM Switch - Edge)
EMAS-N (End-user Mobility-supporting ATM Switch - Network)
M-NNI (Network-to-Network Interface with Mobility support)
LS (Location Server)
AUS (Authentication Server)
130
WATM Reference model
EMAS-N
WMT
RAS
EMAS-E
M-NNI
WMT
RAS
EMAS-N
LS
AUS
131
Application Scenarios of Wireless ATM
132
Reference Model with Further Access
Scenarios (1)
1: wireless ad-hoc ATM network
2: wireless mobile ATM terminals
3: mobile ATM terminals
4: mobile ATM switches
5: fixed ATM terminals
6: fixed wireless ATM terminals
WMT: wireless mobile terminal
WT: wireless terminal
MT: mobile terminal
T: terminal
AP: access point
EMAS: end-user mobility supporting ATM switch (-E: edge, -N: network)
NMAS: network mobility supporting ATM switch
MS: mobile ATM switch
133
Reference model with further access
scenarios (2)
WMT
1
RAS
2
WMT
EMAS
-E
RAS
ACT
EMAS
-N
WMT
EMAS
-E
MT
5
T
6
RAS
3
WT
NMAS
MS
RAS
RAS
T
4
134
WATM
Three MAC protocols:
• Fixed assignment apportions the available resource in a definite manner.
• Random assignment involves random allocation of the resource.
• Demand assignment allocates the resource based on users’ requests.
Types of handoffs
• Backward handoff: The MT decides the possibility of handoff and the
EMAS-E chooses the next BS.
• Intra AP
• Inter AP/Intra EMAS-E
• Inter EMAS-E
• Forward handoff: The MT decides on the BS to which the handoff occurs.
• Intra AP
• Inter AP/Intra EMAS-E
• Inter EMAS-E
135
User Plane Protocol Layers
fixed network segment
radio segment
MATM
terminal
WATM
terminal
adapter
RAS
EMAS
-E
EMAS
-N
ATMSwitch
fixed
end
system
user process
user
process
AAL
AAL
ATM
ATMCL
ATMCL
RAL
RAL
ATM
ATM
ATM
ATM
ATM
PHY
PHY PHY
PHY PHY
PHY PHY
PHY
136
Control Plane Protocol Layers
fixed network segment
radio segment
MATM
terminal
WATM
terminal
adapter
EMAS
-E
EMAS
-N
ATMSwitch
fixed
end
system
SIG,
M-UNI
SIG,
M-UNI,
M-PNNI
SIG,
M-PNNI
SIG,
PNNI,
UNI
SIG,
UNI
SAAL
SAAL
SAAL
SAAL
SAAL
ATM
ATM
ATM
ATM
PHY PHY
PHY
RAS
M-ATM
ATMCL
ATMCL
RAL
RAL
ATM
PHY
PHY PHY PHY PHY
137
WATM – Location Management
The requirements of an location management system:
•
•
•
•
Transparency
Security
Unambiguous identification
Scalability
Location management should address these issues:
• Addressing specifies how MTs, switches, APs, BSs are addressed.
• Location updating involves updating an MT’s address.
• Location server (LS)
• Authentication server (AuS)
• End-user mobility-supporting ATM switch (EMAS)
• Location resolution deals with obtaining the current location of an MT.
138
Comparison of 802.11 and 802.16
Similarity - Provide high-bandwidth wireless communications.
Differences
• 802.16 provides service to stationary buildings which can have multiple
computers. High quality full-duplex link is used. Higher cost is affordable.
802.11 provides service to individual mobile users.
• Longer transmission range security/privacy
• More user in each cell more spectrum is needed, operate in 10-66 GHz
absorbed by water
• QoS is made possible for all transmissions.
Physical layer
• Physical medium dependent sublayer – narrow-band radio (which means
that it contains all of its power in a very narrow portion of the radio
frequency bandwidth, prone to interference ) is used with conventional
modulation schemes.
• Transmission convergence sublayer – hide the different physical medium
139
technologies from the data link layer.
The 802.16 Protocol Stack
The 802.16 Protocol Stack.
140
The 802.16 Protocol Stack
• Data link layer
• Security layer – deal with privacy and security
• MAC sublayer common part – channel management
• Service specific convergence sublayer – integrate with both datagram
protocols (PPP, IP, and Ethernet) and ATM.
Physical media:
• 10-to-66 GHz millimeter waves travel in the straight line.
• Transfer up to 155 Mbps
• 30 miles range
The base station has multiple antennas, each pointing at a
different sector.
The signal-to-noise ratio drops sharply with distance. Three
modulation schemes are used depending on distance:
• QAM-64 (6 bits/baud)
• QAM-16 (4 bits/baud)
• QPSK (2 bits/baud)
141
The 802.16 Physical Layer
The 802.16 transmission environment.
142
Broadband Wireless
143
The 802.16 Physical Layer
Unlike equal bandwidth allocation in the cell phone system, more
bandwidth is allocated for downstream than upstream traffic.
Two schemes are used to allocate the bandwidth:
• FDD (frequency division duplex)
• TDD (time division duplex) – downstream, guard, and upstream time slots
The Hamming code is used for forward error correction.
Frames and time slots for time division duplexing.
144
The 802.16 MAC Sublayer Protocol
Base station sends out frames
Each frame includes a number of subframes, which include a
number of time slots
The first two subframes are the downstream and upstream maps,
which tell what is in which time slot.
Downstream subframes (channels) are straight forward. The base
station decides what to send
Upstream channel is more complex, due to competition.
145
The 802.16 MAC Sublayer Protocol
Four classes of service are defined and are connection-oriented:
• Constant bit rate service: transmit uncompressed voice (similar to a T1
channel). Certain time slots are dedicated to each user.
• Real-time variable bit rate service: compressed multimedia and other soft
real-time applications (bandwidth needed at each instant may vary). Polling
is used.
• Non-real-time variable bit rate service: e.g., file transfer.
• User can request a poll to send constant rate
• If a station does not respond to a poll K times, the base station put it in a
multicast group. The user will content for service.
• Best efforts service
• No polling. User compete for channel in the time slots marked inthe
upstream map for contention.
• If a request is successful, it will be noticed in the next downstream map.
146
The 802.16 MAC Sublayer Protocol
• Generic frame:
•
•
•
•
•
•
•
EC: tells whether the payroll is encrypted
Type: frame type (fragmentation)
CI: whether checksum presents (optional as FEC in physical layer)
EK: which encryption key is used
Length: complete length including header
Connection ID: which connection this frame belongs to
CRC: checksum over header only
• Bandwidth request frame: indicate bytes needed
147
The 802.16 Frame Structure
(a) A generic frame.
(b) A bandwidth request frame.
148
Comparisons among WLAN, WMAN,
WWAN
Feature
IEEE 802.11b
WLANs
IEEE 802.16
WMANs
GSM WWANs
Range
Few hundred meters
Several Km
Few tens of Km
Frequency
2.4 GHz ISM band
10-66 GHz
900 or 1800 MHz
Physical Layer
CCK, BPSK, QPSK
QAM-64, QAM-16, GMSK
QPSK
Maximum Data
Rate
11 Mbps
60-180 Mbps
9.6 Kbps/user
Medium Access CSMA/CA
TDM/TDMA
FDD/TDMA
QoS Support
DCF - No
PCF - Yes
Yes
Yes
Connectivity
DCF- Connectionless Connection oriented Connection
Oriented
PCF - Connection
Typical
Applications
Web browsing, email
Multimedia, digital
TV broadcasting
Voice
149