NetworkExecutiveBriefing
advertisement

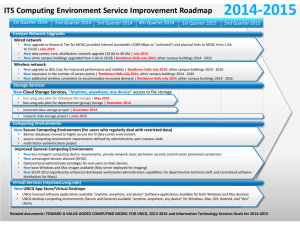
Network Refresh Technology Briefing December 1, 2006 ITS Systems and Networks and Technology Planning and Security Today’s Topics Why should you care about Network Refresh? What are the key issues that drive and affect Network Refresh? How do we compare to our peers on these issues? What are the goals, benefits and weaknesses of the new network design and why will UNCG be better off as a result? What is the implementation plan? Why should you care about Network Refresh? The services we offer as a higher education institution are dependent on the campus data network. If the network doesn’t work, our critical services don’t either. What is the UNCG Campus Data Network? The data network infrastructure SUPPORTS – 300 enterprise application servers – 7,200 computing devices – 18,000 faculty, staff and students computing needs TRANSPORTS – 1,200 – 1,600 Gigabytes of data daily TRAVERSES – 650 Ethernet switches – 200 wiring closets – 73 buildings – 24,000 access ports Today, we depend on our campus network to support • Academic computing services • Administrative Computing Services • Student Housing (RESNET) computing services • Human safety related devices • Remote access for campus services • Web services How UNCG uses its network UNCG faculty, staff and students create or modify about 2.5 TB of data every day, which is equivalent to approximately a quarter of the total contents of the Library of Congress. We collectively use the campus network to transport 63GB of data per hour, or 1,521GB of data per day, which is equivalent to approximately 250,000 books. EMAIL: 750,000 and 1,000,000 incoming internet email messages daily UNCGENIE: 1.1GB of data transported per hour, 29GB of data daily NETWORK PRINTING: Since the Fall semester began, 616,996 sheets have been printed When UNCG uses the network Campus network traffic generated outside of the University’s traditional hours of operation comprises 46% of the total volume of traffic on the network. Traffic during regular hours of operation 8am – 5pm, M – F 54% Traffic during off-hours 5pm – 8am, M – Th Friday at 5pm – Monday at 8am 46% Impact of the Network on the Classroom 24x7 Web hits on the Blackboard server in a typical 24-hour period: Total hits, on and off campus: 2,508,885 On-campus only: Off-campus only: 1,219,934 1,288,951 49% 51% 8 AM to 5 PM (on and off campus): On-campus only: Off-campus only: 1,387,590 780,681 606,909 55% 56% 44% Off hours (on and off campus): On-campus only: Off-campus only: 1,121,295 439,253 682,042 45% 39% 61% The Network is not only a strategic asset, but also a strategic differentiator “All students want to be — expect to be, demand to be —connected to the internet, each other, and all capabilities of the university 24/7.” Campus Technology Whitepaper: THE CIO’S DILEMMA... AND SOME SOLUTIONS How UNCG residential students use the campus network Significant activity: 24 x 7 Peak activity: noon - midnight What will UNCG’s campus data network needs be tomorrow? As a Carnegie Foundation research university with “high research activity”, these and other new research initiatives will shape our future network service requirements: • • • • • Joint School of Nanoscience and Nanoengineering North Carolina Research Campus at Kannapolis Chemistry Department Geography Department Greensboro Center for Innovative Development What are the key issues that drive and affect Network Refresh? The need to refresh is driven by equipment age which affects: • Support • Services that can be offered • Security The cost of refresh is affected by: • How much intelligent switching is implemented • Network speed • Length of the refresh cycle The need to refresh is driven by equipment age The industry standard lifespan of network equipment is 3 - 5 years. 2005 Data Storage Devices Management Software Desktops Servers Network Equipment Phone Systems 0% 20% Every 3 Years or Less Every 7 Years 40% 60% 80% 100% Every 5 Years Every 10 Years or More Product Replacement— Avg. Useful Life, Yankee Group Enterprise Survey, Nov. 2005. What does it mean for network equipment to become “end of life”? “end of life” means • hardware spares/replacements not available • software upgrades not available • technical support not available At end of life, equipment vendors no longer offer replacement parts, software upgrades or technical support As network equipment becomes “end of life”, we lose our ability to: • Support the network effectively • Offer services that meet campus needs • Defend ourselves effectively against security threats Effective July 2007, 48% of UNCG’s building switching is end of life. Would it be cost effective for us to support Windows 98 as our primary desktop OS today? Diminishing ability to support the network effectively 52% of the 231 total enterprise level service outages at UNCG between 4/1/2006 and 10/31/2006 resulted from network outages Diminishing ability to offer services that meet campus needs Client Needs Example 1 Spring/Summer 2005: Financial Aid office required a network communications solution that enabled them to setup stations in the Elliott Center quickly that had access to restricted data. Current Solution: In the current environment the solution we offered was one of registering each computer in Elliot using NetReg and then install and configure VPN to access the secure data. It works, but it’s not a good solution from the user’s perspective. Preferred Solution after Refresh: The next generation of the network will allow us to implement identity-based networking. With this service, users will authenticate based on who they are (rather than what machine they are using or where they are on campus) and be free to roam around campus with full secure access to the data and services they are supposed to see from any location, without additional requirements for machine registration or VPN software. Wherever you are, login and compute just like you are sitting at your desk – no assistance required. Diminishing ability to offer services that meet campus needs Clients Needs Example 2 2006: Chemistry department contacted ITS with a request to enhance building network security and performance in order to meet current research needs. Current Solution: An add-on firewall solution was deployed to address building security needs. No solution is available today to address high performance computing needs. Preferred Solution after Refresh: Quick turnaround of an integrated firewall solution to provide the enhanced level of building security that research projects require and Gigabit access ports to allow in-building high performance computing. Diminishing ability to defend ourselves effectively against security threats We all are aware of our institutional requirements to be compliant with state and federal regulations for handling restricted data. Equally important, is our ability to combat security threats that become increasingly more sophisticated every day. In 2006, there are hundreds of tools that we know about that can be easily obtained by an average person and used maliciously to compromise restricted data and networks. There are hundreds more that we don’t know about. The following demonstration is one example of many possible scenarios. One example of an attack Don’t Try This Yourself http://its.uncg.edu/Policy_Manual/Acceptable_Use/ C. Unacceptable Use i. Prohibited System and Network Activities Executing any form of network monitoring which will intercept data not intended for the employee's host. Authorized ITS employees are permitted to monitor network traffic data as part of their normal job duties. Man in the middle attack There are many different types of attacks and the one I'm showing today is called man in the middle. There are a variety of ways to perform this attack. We will be performing what is called arp poisoning to get all machines in this building to send this computer all their data. The software I'm using (ettercap) is easily downloaded and has been available since 1/25/01. However, Dug Song's "dsniff" does the same thing and predates this by a couple of years with a release date of Fri Dec 17, 1999 THE BAD NEWS: This attack is easy to do. The computer host firewall will not prevent this attack or detect it. SSL encryption will not prevent this attack. THE GOOD NEWS: New network equipment finally prevents this attack. This attack allows us to see: • • • • • • • • all usernames and passwords all email being read/sent all instant messages all network phone calls all websites being viewed all print jobs all files being saved to Novell everything The cost of network refresh is affected by How much intelligent switching is implemented: Extending security out to the edge of the network can increase costs significantly! Network speed: 1 Gigabit vs. 10 Gigabit. Choosing 10 Gigabit speeds can increase costs significantly! Length of the refresh cycle: Choosing a 3 year versus 5 year refresh cycle can increase costs significantly! Building intelligence out to the edge of the network BUILDING ACCESS NETWORK 600 + building switches $$$$ Premium: Intelligent switching present in core, distribution and building access DISTRIBUTION NETWORK 8 distribution switches Adequate: Intelligent switching present in core and distribution CORE NETWORK 2 core switches Less than adequate: Intelligent switching present in core only $$ UNCG chose a moderate, middle-ground solution BUILDING ACCESS NETWORK Building intelligence out to the building layer would have been a very expensive “premium” choice. Additional benefit to end users: contain outages at the workgroup level within a building. DISTRIBUTION NETWORK UNCG Chose this configuration: Intelligent switching present in core and distribution Contain outages at building level. CORE NETWORK Intelligent switching present UNCG chose a moderate, middle-ground solution Network speed: UNCG chose a 1 GB network speed at less than half the cost of the 10 GB solution. 1 GB speeds will more than support our current network usage. Length of the refresh cycle: UNCG chose a four year refresh cycle for our core and distribution equipment and a five year refresh cycle on our building access equipment, which effectively trimmed 1/3rd off of the bottom line cost of the project. The overall solution is built to scale such that if pockets of higher performance are required, they can be seamlessly accommodated. How does our network strategy compare to those of our peers? Network Refresh issues are not unique to UNCG In 2005, the EDUCAUSE Center for Applied Research (ECAR) published a comprehensive national study that provides a detailed insight into how higher education approaches IT networking, titled “Information Technology Networking in Higher Education: Campus Commodity and Competitive Differentiator”. Senior IT leaders from 517 institutions responded to the survey. 98% of the national study respondents report that leadership “views the campus network as an essential resource”. 66.7% of the national study respondents said their institution’s spending on data networking increased during the past three years and 74.6% anticipate this trend will continue. 2005 Data 79.5% of the national study respondents report that “the most frequent funding source for central networking upgrades and improvements” is an annual data networking budget. 2005 Data National study respondents reported that their institutions plan to invest most in network components and software (64.4%) and wireless networking (60.5%) over the next three years. 2005 Data How UNCG’s refresh strategy compares locally The following information comes from peer to peer conversations between UNCG networking staff and Networking staff at UNCC and ECU. This information has not been confirmed by detailed on-site study. How UNCG’s refresh strategy compares locally UNC Charlotte East Carolina UNCG Intelligent switching: Distribution layer Building access layer Distribution layer Network speed: Gigabit Gigabit Gigabit Reported length of refresh cycle: 3 year high end and intermediate 3 year high end and intermediate 4 year high end and intermediate 4 year network mgmt hardware 3 year network mgmt hardware 4 year network mgmt hardware 5 year building access 5 year building access 5 year building access One-time money One-time money Annual ITS allocation + TBD Reported funding source: What are the goals, benefits and weaknesses of the new network design? Brief History of the Campus Network • • 1999 – 2002: – Large project to install fiber optics, and shift to Cisco Systems Ethernet based technology. – 100 Mbps to buildings – 10 Mbps switched to desktops – 622 Mbps NCREN/Internet speed – Time span: Windows 95 -> Windows 98 2003 – 2006: – 1000 Mbps (1Gbps) to buildings – 10/100 Mbps switched to desktops – 2,400 Mbps (2.4 Gbps) NREN/Internet speed – Various Security Solutions • Intrusion Prevention • Firewall around data center • Email Anti-Virus / Anti-Spam – Time span: Windows 98 -> Windows XP Today’s Network Campus Bldg Campus Bldg Campus Bldg Campus Bldg McNutt Router Bryan Router Forney Router Jackson Router Campus Bldg IPS Sniffer Server monitoring/analysis IPS NCREN Internet Sniffer Server monitoring/analysis Data Center Firewall (Active) Data Center Firewall (Standby) Forney Data Ctr Router Bryan Data Ctr Router Today’s Network - Weaknesses • Causes of network failure – Software defects in (bugs) switches / routers – Hardware failure – Security related events • Particularly those involving unusual traffic conditions (DDoS) such as the infamous Sobig, Blaster and Welchia. – Human failure / misunderstanding – Growth challenges Security Considerations • Targets of software hacking exploits: – Network Infrastructure • • • • Routers Switches Firewalls Intrusion Prevention Systems – Applications • Desktop computers • Application Servers • Its all software whether application level or network level device! The security landscape is changing • SANS TOP-20 Critical Vulnerabilities for 2005: “This SANS Top-20 2005 is a marked deviation from the previous Top-20 lists. In addition to Windows and UNIX categories, we have also included Cross-Platform Applications and Networking Products. The change reflects the dynamic nature of the evolving threat landscape and the vulnerabilities that attackers target.” • SANS TOP-20 Critical Vulnerabilities for 2006: “This announcement comes in the midst of an explosion in cyber crime, driven in part by a surge in the number of online criminals in Asian countries along with continuing growth in attacks from Eastern European countries. The surge is so great that several banks have reported 400 to 500 percent increases in losses to cyber fraud from 2005 to 2006.” Design Choices and Goals • Increase/improve – – – – Reliability, Redundancy Configuration Flexibility Performance Security • Provide client-facing communications security – Admin clients and academic where needed. • Provide Identity Based Network Service / Network Admission Control • Maintain open access academic networks. • Prepare for possible voice support (VoIP). • Prepare for IPV6 and Internet2 support. New Design Overview Building Access Voice and Wireless ready Building Distribution Campus Distribution Core WAN Resnet Services Distribution Server Farm Metro Ethernet Services Access Internet Limitations of Design for 2007 - 2011 • Access layer switches are over-subscribed – 1 Gigabit access ports – 1 Gigabit uplink ports between switches • Very high performance needs can potentially overwhelm a building network. • Layer 2 only networking in buildings • Workstation peer to peer traffic will frequently come back to a distribution area if crossing layer 3 routed boundary. • Limited “in-building” network customization if need to keep traffic localized. • Potential network failure can be contained to a building level only. Key Technology Areas • Multi-Protocol Label Switching (MPLS) and Virtual Routing / Forwarding (VRF) – BENEFITS: • Network virtualization • Creation of distinct closed user communities (CUG) • Identity Based Network Service (IBNS), 802.1X, Network Admission Control (NAC) – BENEFITS: • Increased mobility. • Vulnerability remediation. • Quality of Service (QoS) – BENEFIT: Selective network traffic prioritization • Firewall Services Module – BENEFIT: Communications security / risk mitigation • Intrusion Prevention Systems – BENEFIT: Communications security / risk mitigation New Design Benefits Why will UNCG be better off as a result? • Benefits of new network design / implementation – Security • Further reducing risk of data exposure • Targeting security implementation to risk areas • Enabling IBNS / NAC / Networked Virtual Organization (NVO) – Performance • Implementing quality of service (QoS) traffic protection • Increasing access port speed to 1 gigabit per second – Reliability • Redundantly connected buildings throughout • Designed for reduced failure domains. What is the Implementation Plan? Five-Year Implementation Plan Overview FIRST OBJECTIVE: Develop the Test Environment October 2006 – March 2007: Networks is currently building a test lab at DSINet. During the initial lab phase, Networks will be working with key technical clients across campus to define THE NEW CORE AND DISTRIBUTION NETWORK (12/8/06 - 2/26/07) – – – – – – – – – NETWORK VIRTUALIZATION IDENTITY BASED NETWORKING FIREWALL SERVICE MODULE NETWORK TOPOLOGY QUALITY OF SERVICE INFRASTRUCTURE SERVICES PROBES/TRAFFIC ANALYSIS DIRECTORY SERVICES GUEST USER THE NEW ACCESS / BUILDING NETWORK (1/16/07 - 3/26/07) – – – – – NETWORK TOPOLOGY L2 / VLAN SEGMENTATION QUALITY OF SERVICE VOIP COMPATIBILITY ACCESS PORT SECURITY FEATURES Five-Year Implementation Plan Overview SECOND OBJECTIVE: Actively Engage Clients October 2006 – March 2007: Engage key clients across the University to participate as formal members of the Network Refresh Project, helping to define the evolution of the campus network and its associated services, build understanding among client groups for this critical work and test potential solutions with client applications. ACADEMIC NEEDS Open academic network High Performance Computing Guest access BUSINESS NEEDS Highly secure restricted business network Specialty networks (HVAC controls,…) Mobility for transaction processing - “mobile road shows” for events like SOAR Vendor Access Five-Year Implementation Plan Overview OVERVIEW: Annual schedule and deliverables Goals for Winter 2006 – Winter 2007 Upgrade the Core Network to a “Core + Distribution” design in accordance with best practices (Network Refresh Project: PM – Natsu Carr) Upgrade some Buildings to current technology (Network Refresh Project: PM – Natsu Carr) Upgrade the Server Farm to current technology (Data Center Relocation Project: PM – Natsu Carr) Five-Year Implementation Plan Overview YEAR 1: Annual schedule and deliverables February 2007 – May 2007: Two core and four distribution routers, along with three new building networks will be deployed (pending full funding of non-recurring portion). YEAR 1 DEPLOYMENT (2/12/07 - 5/14/07) • • • • • • • • “Deployment Kickoff" CORE AND DISTRIBUTION: Install and test routers MOSSMAN: Install and test switches GRAY HOME: Install and test switches POLICE STATION: Install and test switches Install, test, accept security components Conduct user acceptance testing Provide user acceptance / sign off Five-Year Implementation Plan Overview YEARS 2 – 5: Annual schedule and deliverables Year 2: Remainder of Core Network, Server Farm, Enhanced Security, more buildings,… Years 3 – 4: more buildings,… Year 5: core and more buildings,… Year 6: do it again! Five-Year Implementation Plan Overview Campus-wide Communications: December Technical Briefing (Donna Heath/John Gale/Joff Thyer/Chris Roys) December IT Professionals Roundtable (Chris Roys/Joff Thyer) Quarterly Technical Professionals Meeting (Brad Lytle/Chris Roys) Project Meetings Project Webpages Questions?