Chp. 7a Review - Cisco Networking Academy
advertisement
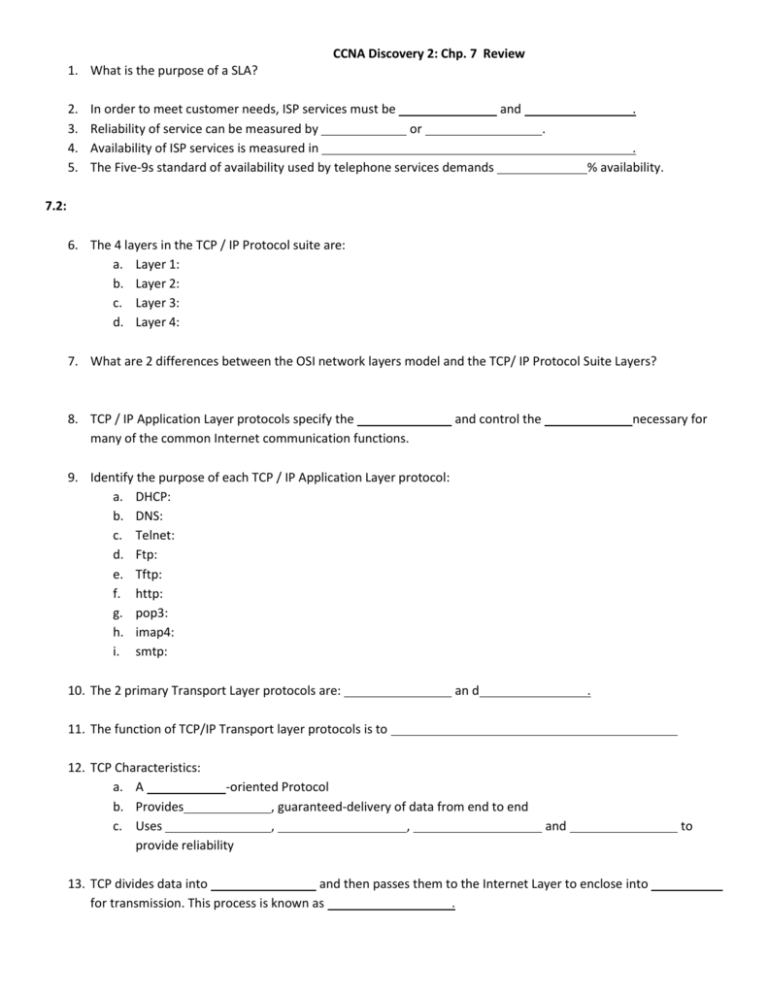
CCNA Discovery 2: Chp. 7 Review 1. What is the purpose of a SLA? 2. 3. 4. 5. In order to meet customer needs, ISP services must be and Reliability of service can be measured by or Availability of ISP services is measured in The Five-9s standard of availability used by telephone services demands . . . % availability. 7.2: 6. The 4 layers in the TCP / IP Protocol suite are: a. Layer 1: b. Layer 2: c. Layer 3: d. Layer 4: 7. What are 2 differences between the OSI network layers model and the TCP/ IP Protocol Suite Layers? 8. TCP / IP Application Layer protocols specify the many of the common Internet communication functions. and control the necessary for 9. Identify the purpose of each TCP / IP Application Layer protocol: a. DHCP: b. DNS: c. Telnet: d. Ftp: e. Tftp: f. http: g. pop3: h. imap4: i. smtp: 10. The 2 primary Transport Layer protocols are: an d . 11. The function of TCP/IP Transport layer protocols is to 12. TCP Characteristics: a. A -oriented Protocol b. Provides , guaranteed-delivery of data from end to end c. Uses , , provide reliability and 13. TCP divides data into and then passes them to the Internet Layer to enclose into for transmission. This process is known as . to 14. TCP adds a to each segment to ensure that the data has all been received and can be reordered at the destination host. 15. Applications that use TCP require the source and destination host to exchange information to set up a connection. This process is called a . 16. The 3 parts of a TCP 3-Way Handshake are: a. SYN: b. SYN-ACK: c. ACK: 17. In a TCP communication session, transmitted packets must be they will be . 18. UDP Characteristics: a. An unreliable, low b. Considered a c. Does not provide d. Used by applications such as: within a specific time period or data delivery protocol , best Transport Layer protocol , guaranteed , or , DHCP, , SNMP, , and RIP 19. Data transmitted with TCP will require more error-checking and delivery verification processes that must occur. , than that sent with UDP, due to the 20. Port Numbers are used to differentiate between 21. For Destination Port Numbers, server processes are usually statically assigned to . numbers from 22. Common Default Destination Port Numbers: a. HTTP: Port b. SMTP Email servers: Port c. FTP: Ports and d. Telnet: Port 23. ports allow clients to identify the requesting client application. They are dynamically assigned from the port range to 24. The combination of the Transport Layer port number and the Network Layer IP address of a host that uniquely identifies a particular application process is called a . 25. The combination of the source and destination IP addresses and port numbers, which identifies a specific conversation between two hosts is called a . CCNA Discovery 2: Chp. 7b Review 7.3: 1. In the early days of the Internet, host names and IP addresses were managed through the use of a single . This file contained mappings of and for every device connected to the early Internet. 2. DNS relies on a hierarchy of to store and maintain records of to IP address mappings. 3. Briefly describe the 3 components of DNS: a. Resource records and domain namespace: b. Domain name system servers: c. Resolvers: 4. DNS servers maintain records about how to reach the have records that point to the second-level domain servers. domain servers, which in turn 5. A FQDN (fully qualified domain name) is 6. When a DNS server receives a request for a name translation that is not within its DNS zone, what will it do? 7. What are the 2 ways a DNS client can dynamically update its DNS records? 8. What is a DNS Zone? 9. Identify the 4 different DNS Zone Types: a. Forward lookup zone: b. Reverse lookup zone: c. Primary zone: d. Secondary zone: 10. What command is used to do a reverse DNS lookup? 11. Identify the characteristics of the 2 types of DNS Servers: a. ISP DNS Server: i. A -only server ii. Forwards all name resolution requests to a . iii. Stores a large of resolved requests, but does not store any b. Local DNS Server: i. Responsible for name-to-IP mappings for all ii. Forwards all external name resolution requests to the server or a 12. To provide reliability of service and redundancy, a registered domain name requires a minimum of server 7.4: 13. specifies a request/response protocol for displaying html-formatted web pages. Client requests and server replies in http are sent in , so it is an insecure protocol. 14. For secure communication across the Internet, information. It adds and is used for accessing or posting web server to the http protocol. 15. What 3 pieces of information does a URL identify? a. b. c. 16. A allows clients to make indirect network connections to other network services. 3 reasons for using a proxy server are: a. Increases of subsequent requests due to caching b. Increases by intercepting and blocking viruses and malicious content c. Provides of unsuitable or undesirable web content 17. FTP is a protocol that uses TCP to allow transfer of files between a client and server. 18. FTP requires connections to exist between the client and server: a. PI: sends and commands between the server and client: connection stays open until b. DTP: transfer between the client and server: connection closes 19. Ftp uses 2 ports. The client and server use port transferring data. for control information and port for 20. Identify the 2 types of data transfer Modes available in FTP a. In a connection , the CLIENT initiates the Data-Transfer Connection. The server forwards its IP address and a random port number to the FTP client so it can initiate a data transfer connection to port 20 on the server. b. In a connection, the SERVER initiates the Data-Transfer Connection. The client sends a request to the server’s control port (Port 21) using a random local port and then the server initiates a connection to the client’s data port from its own data port (Port 20) 21. ISPs typically ONLY support data connections to their FTP servers because do not allow external hosts to initiate a connection to an internal client. 22. Email uses a often method of sending, storing, and retrieving messages across a network. 23. Identify each email protocol by its function: a. : protocol used to send email between clients and servers or between servers b. : protocol used by a client to retrieve email from a mail server by downloading it to the client c. : protocol used by a client to retrieve email from a mail server by making a local copy of the email on the client