pptx
advertisement

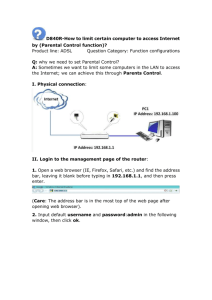
Network Architecture and Protocols IT443 – Network Security Administration Instructor: Bo Sheng Reference Textbooks Computer Networks: A Systems Approach Computer Networking: A Top Down Approach 1 Outline • Network Layers • Internet Protocol (IP) • TCP and UDP 2 Layering: A Modular Approach • Sub-divide the problem – Each layer relies on services from layer below – Each layer exports services to layer above • Interface between layers defines interaction – Hides implementation details – Layers can change without disturbing other layers Application TCP, UDP Transport Network Ethernet, DSL WiFi, … HTTP, FTP, TELNET POP/IMAP, SSH, SSL, … IP(IPv4, IPv6) Link Physical 3 Layer Encapsulation User A User B Get index.html Connection ID Source/Destination Link Address 4 4 IP Layer • Data traffic divided into packets – Each packet contains a header (with address) • Packets travel separately through network – Packet forwarding based on the header – Network nodes may store packets temporarily • Destination reconstructs the message 5 IP Layer • Packet Switching – VS. Circuit Switching • Best-effort delivery – Packets may be lost – Packets may be corrupted – Packets may be delivered out of order 6 What if the Data Doesn’t Fit? Problem: Packet size • On Ethernet, max IP packet is 1500 bytes (MTU) • Typical Web page is 10 kbytes Solution: Split the data across multiple packets ml x.ht inde GET GET index.html 7 What if the Data is Out of Order? Problem: Out of Order ml inde x.ht GET GET x.htindeml Solution: Add Sequence Numbers ml 4 inde 2 x.ht 3 GET 1 GET index.html 8 IP Packet 4-bit 8-bit 4-bit Version Header Type of Service Length (TOS) 3-bit Flags 16-bit Identification 8-bit Time to Live (TTL) 16-bit Total Length (Bytes) 8-bit Protocol 13-bit Fragment Offset 16-bit Header Checksum 20-byte header 32-bit Source IP Address 32-bit Destination IP Address Options (if any) Payload 9 Transport Protocols • Provide logical communication between application processes running on different hosts • Datagram messaging service (UDP) – No-frills extension of “best-effort” IP • Reliable, in-order delivery (TCP) 10 Using Ports to Identify Services Server host 128.2.194.242 Client host Service request for 128.2.194.242:80 (i.e., the Web server) Web server (port 80) OS Client Echo server (port 7) Service request for 128.2.194.242:7 (i.e., the echo server) Client Web server (port 80) OS Echo server (port 7) 11 Knowing What Port Number To Use • Popular applications have well-known ports – E.g., port 80 for Web and port 25 for e-mail – Well-known ports listed at http://www.iana.org • Well-known vs. ephemeral ports – Server has a well-known port (e.g., port 80) • Between 0 and 1023 – Client picks an unused ephemeral (i.e., temporary) port • Between 1024 and 65535 • Uniquely identifying the traffic between the hosts – Two IP addresses and two port numbers – Underlying transport protocol (e.g., TCP or UDP) Unreliable Message Delivery Service • User Datagram Protocol (UDP) – IP plus port numbers – Optional error checking on the packet contents SRC port DST port checksum length DATA • Lightweight communication between processes – Avoid overhead and delays of ordered, reliable delivery • For example: VoIP, video conferencing, gaming 13 Transmission Control Protocol • Communication service (socket) – Ordered, reliable byte stream – Simultaneous transmission in both directions • Key mechanisms at end hosts – – – – Retransmit lost and corrupted packets Discard duplicate packets and put packets in order Flow control to avoid overloading the receiver buffer Congestion control to adapt sending rate to network load 14 An Analogy: Talking on a Cell Phone • Alice and Bob on their cell phones – Both Alice and Bob are talking • What if Alice couldn’t understand Bob? – Bob asks Alice to repeat what she said • What if Bob hasn’t heard Alice for a while? – – – – – Is Alice just being quiet? Or, have Bob and Alice lost reception? How long should Bob just keep on talking? Maybe Alice should periodically say “uh huh” … or Bob should ask “Can you hear me now?” • Retransmission, ACK/NACK, timeout 15 TCP Support for Reliable Delivery • Checksum – – • Sequence numbers – – • Used to detect corrupted data at the receiver …leading the receiver to drop the packet Used to detect missing data ... and for putting the data back in order Retransmission – – Sender retransmits lost or corrupted data Timeout based on estimates of round-trip time 16 Establishing a TCP Connection Each host tells its ISN to the other host. • Three-way handshake to establish connection – Host A sends a SYN (open) to the host B – Host B returns a SYN acknowledgment (SYN ACK) – Host A sends an ACK to acknowledge the SYN ACK 17 TCP Header Source port Destination port Sequence number Flags: SYN FIN RST PSH URG ACK Acknowledgment HdrLen 0 Flags Advertised window Checksum Urgent pointer Options (variable) Data 18 Identifiers • Transport Layer: port number • IP Layer: IP address • Link Layer: MAC address 19 IP Suite: End Hosts vs. Routers host HTTP message HTTP router IP Ethernet interface HTTP TCP segment TCP IP packet Ethernet interface IP host TCP router IP packet SONET interface SONET interface IP IP packet Ethernet interface IP Ethernet interface 20 Outline • Addressing and Naming – IP prefix, DNS, ARP 21 Grouping Related Hosts • The Internet is an “inter-network” – Used to connect networks together, not hosts – Needs a way to address a network (i.e., group of hosts) host host ... host host host ... host LAN 2 LAN 1 router WAN router WAN router LAN = Local Area Network WAN = Wide Area Network 22 Scalability Challenge • Suppose hosts had arbitrary addresses – Then every router would need a lot of information – …to know how to direct packets toward the host 1.2.3.4 host 5.6.7.8 host ... 2.4.6.8 1.2.3.5 5.6.7.9 host host host 2.4.6.9 ... host LAN 2 LAN 1 router WAN router WAN router 1.2.3.4 1.2.3.5 forwarding table 23 IP Prefix • Divided into network & host portions (left and right) • 12.34.158.0/24 is a 24-bit prefix with 28 addresses 12 34 158 5 00001100 00100010 10011110 00000101 Network (24 bits) Host (8 bits) 24 IP Address and Subnet Mask Address 12 34 158 5 00001100 00100010 10011110 00000101 11111111 11111111 11111111 00000000 Mask 255 255 255 0 25 Scalability Improved • Number related hosts from a common subnet – 1.2.3.0/24 on the left LAN – 5.6.7.0/24 on the right LAN 1.2.3.4 1.2.3.7 host host 1.2.3.156 ... 5.6.7.8 host host 5.6.7.9 host 5.6.7.212 ... host LAN 2 LAN 1 router WAN router WAN router 1.2.3.0/24 5.6.7.0/24 forwarding table 26 Easy to Add New Hosts • No need to update the routers – E.g., adding a new host 5.6.7.213 on the right – Doesn’t require adding a new forwarding entry 1.2.3.4 1.2.3.7 host host 1.2.3.156 ... host 5.6.7.8 5.6.7.9 host host 5.6.7.212 ... host LAN 2 LAN 1 router WAN router WAN router host 5.6.7.213 1.2.3.0/24 5.6.7.0/24 forwarding table 27 Classful Addressing • In the olden days, only fixed allocation sizes – Class A: • Very large /8 blocks (e.g., MIT has 18.0.0.0/8) – Class B: • Large /16 blocks (e.g,. Princeton has 128.112.0.0/16) – Class C: • Small /24 blocks (e.g., AT&T Labs has 192.20.225.0/24) 28 Classless Inter-Domain Routing (CIDR) Use two 32-bit numbers to represent a network. Network number = IP address + Mask IP Address : 12.4.0.0 IP Mask: 255.254.0.0 00001100 00000100 00000000 00000000 Mask 11111111 11111110 00000000 00000000 Network Prefix for hosts Written as 12.4.0.0/15 29 Private Networks • Not globally delegated – 10.0.0.0/8 (255.0.0.0) – 172.16.0.0/12 (255.240.0.0) – 192.168.0.0/16 (255.255.0.0) 30 Growth History • BGP (Broader Gateway Protocol) Table Size – Autonomous systems (routing prefixes) – http://bgp.potaroo.net/as1221/bgp-active.html 31 Are 32-bit Addresses Enough? • Not all that many unique addresses – 232 = 4,294,967,296 (just over four billion) – Plus, some are reserved for special purposes – And, addresses are allocated in larger blocks • And, many devices need IP addresses – Computers, PDAs, routers, smartphones, toasters, … • Long-term solution: a larger address space – IPv6 has 128-bit addresses (2128 = 3.403 × 1038) • Short-term solutions: limping along with IPv4 – Private addresses – Network address translation (NAT) – Dynamically-assigned addresses (DHCP) 32 Naming: Domain Name System (DNS) • Properties of DNS – Hierarchical name space divided into zones – Translation of names to/from IP addresses – Distributed over a collection of DNS servers 33 DNS Root Servers • 13 root servers (see http://www.root-servers.org/) • Labeled A through M E NASA Mt View, CA F Internet Software C. Palo Alto, CA (and 17 other locations) A Verisign, Dulles, VA C Cogent, Herndon, VA (also Los Angeles) D U Maryland College Park, MD K RIPE London (also Amsterdam, Frankfurt) G US DoD Vienna, VA H ARL Aberdeen, MD I Autonomica, Stockholm J Verisign, ( 11 locations) (plus 3 other locations) m WIDE Tokyo B USC-ISI Marina del Rey, CA L ICANN Los Angeles, CA 34 Domain Name System unnamed root com edu org generic domains bar zw uk ac arpa country domains ac inaddr west east cam 12 foo my usr 34 my.east.bar.edu usr.cam.ac.uk 12.34.56.0/24 56 35 DNS Resolver and Local DNS Server Root server 3 4 Application DNS cache 5 1 10 DNS resolver DNS query 2 6 Local DNS server Top-level domain server 7 DNS response 9 8 Second-level domain server Caching based on a time-to-live (TTL) assigned by the DNS server responsible for the host name to reduce latency in DNS translation. 36 Recursive and Iterative • Recursive query – Ask server to get answer for you – E.g., request 2 and response 9 • Iterative query – Ask server who to ask next – E.g., all other request-response pairs 37 DNS Caching • Performing all these queries take time – And all this before the actual communication takes place – E.g., 1-second latency before starting Web download • Caching can substantially reduce overhead – The top-level servers very rarely change – Popular sites (e.g., www.cnn.com) visited often – Local DNS server often has the information cached • How DNS caching works – DNS servers cache responses to queries – Responses include a “time to live” (TTL) field – Server deletes the cached entry after TTL expires 38 Negative Caching • Remember things that don’t work – Misspellings like www.cnn.comm and www.cnnn.com – These can take a long time to fail the first time – Good to remember that they don’t work – … so the failure takes less time the next time around 39 Address Translation • MAC (or LAN or physical or Ethernet) address: – function: get frame from one interface to another physically-connected interface (same network) – 48 bit MAC address (for most LANs) • burned in NIC ROM, also sometimes software settable • Analogy: – MAC address: like Social Security Number – IP address: like postal address 40 ARP: Address Resolution Protocol • Each IP node (host, router) on LAN has ARP table • ARP table: IP/MAC address mappings for some LAN nodes < IP address; MAC address; TTL> – TTL (Time To Live): time after which address mapping will be forgotten (typically 20 min) • First time (A→B): A broadcasts an ARP query packet, containing B's IP address – destination MAC address = FF-FF-FF-FF-FF-FF – all machines on LAN receive ARP query 41 Addressing: routing to another LAN walkthrough: send datagram from A to B via R. –focus on addressing - at both IP (datagram) and MAC layer (frame) B A R 111.111.111.111 74-29-9C-E8-FF-55 222.222.222.222 49-BD-D2-C7-56-2A 222.222.222.220 1A-23-F9-CD-06-9B 111.111.111.112 CC-49-DE-D0-AB-7D 111.111.111.110 E6-E9-00-17-BB-4B Data Link Layer 222.222.222.221 88-B2-2F-54-1A-0F 5-42 A creates IP datagram with IP source A, destination B A creates link-layer frame with R's MAC address as dest, frame contains A-to-B IP datagram MAC src: 74-29-9C-E8-FF-55 MAC dest: E6-E9-00-17-BB-4B IP src: 111.111.111.111 IP dest: 222.222.222.222 IP Eth Phy B A R 111.111.111.111 74-29-9C-E8-FF-55 222.222.222.222 49-BD-D2-C7-56-2A 222.222.222.220 1A-23-F9-CD-06-9B 111.111.111.112 CC-49-DE-D0-AB-7D 111.111.111.110 E6-E9-00-17-BB-4B Data Link Layer 222.222.222.221 88-B2-2F-54-1A-0F 5-43 frame sent from A to R frame received at R, datagram removed, passed up to IP MAC src: 74-29-9C-E8-FF-55 MAC dest: E6-E9-00-17-BB-4B IP src: 111.111.111.111 IP dest: 222.222.222.222 IP Eth Phy IP Eth Phy B A R 111.111.111.111 74-29-9C-E8-FF-55 222.222.222.222 49-BD-D2-C7-56-2A 222.222.222.220 1A-23-F9-CD-06-9B 111.111.111.112 CC-49-DE-D0-AB-7D 111.111.111.110 E6-E9-00-17-BB-4B Data Link Layer 222.222.222.221 88-B2-2F-54-1A-0F 5-44 R forwards datagram with IP source A, destination B R creates link-layer frame with B's MAC address as dest, frame contains A-to-B IP datagram MAC src: 1A-23-F9-CD-06-9B MAC dest: 49-BD-D2-C7-56-2A IP src: 111.111.111.111 IP dest: 222.222.222.222 IP Eth Phy IP Eth Phy B A R 111.111.111.111 74-29-9C-E8-FF-55 222.222.222.222 49-BD-D2-C7-56-2A 222.222.222.220 1A-23-F9-CD-06-9B 111.111.111.112 CC-49-DE-D0-AB-7D 111.111.111.110 E6-E9-00-17-BB-4B Data Link Layer 222.222.222.221 88-B2-2F-54-1A-0F 5-45 R forwards datagram with IP source A, destination B R creates link-layer frame with B's MAC address as dest, frame contains A-to-B IP datagram MAC src: 1A-23-F9-CD-06-9B MAC dest: 49-BD-D2-C7-56-2A IP src: 111.111.111.111 IP dest: 222.222.222.222 IP Eth Phy IP Eth Phy B A R 111.111.111.111 74-29-9C-E8-FF-55 222.222.222.222 49-BD-D2-C7-56-2A 222.222.222.220 1A-23-F9-CD-06-9B 111.111.111.112 CC-49-DE-D0-AB-7D 111.111.111.110 E6-E9-00-17-BB-4B Data Link Layer 222.222.222.221 88-B2-2F-54-1A-0F 5-46 R forwards datagram with IP source A, destination B R creates link-layer frame with B's MAC address as dest, frame contains A-to-B IP datagram MAC src: 1A-23-F9-CD-06-9B MAC dest: 49-BD-D2-C7-56-2A IP src: 111.111.111.111 IP dest: 222.222.222.222 IP Eth Phy B A R 111.111.111.111 74-29-9C-E8-FF-55 222.222.222.222 49-BD-D2-C7-56-2A 222.222.222.220 1A-23-F9-CD-06-9B 111.111.111.112 CC-49-DE-D0-AB-7D 111.111.111.110 E6-E9-00-17-BB-4B Data Link Layer 222.222.222.221 88-B2-2F-54-1A-0F 5-47