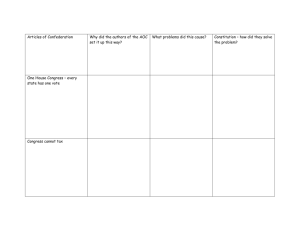
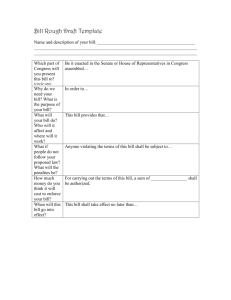
Links to Neg Args - UMKC Summer Debate Institute
advertisement

Inherency/Status Quo The FBI is currently using guidelines for NSLs Bendix et al in 2013 (William Bendix, Assistant Professor of Political Science at Keene State College; Paul Quirk, a former research associate at Brookings Institution, is Phil Lind Chair in U.S. Politics and Representation at the University of British Columbia., “Institutional Failure in Surveillance Policymaking: Deliberating the Patriot Act” Brookings.edu, Number 60; 6/13, 15 pgs., Website, 6/28/15, http://www.brookings.edu/~/media/research/files/papers/2013/07/29%20surveillance%20policymaking%20patri ot%20act%20bendix%20quirk/bendix%20quirk_patriot%20act_v14.pdf) It is debatable whether the U.S. government, overall, has struck a defensible balance between enhancing security and protecting civil liberties. We have seen the implementation of expansive surveillance programs, and we have reason to believe that other important surveillance operations remain classified and undisclosed.39 It is even possible that the executive has withheld eavesdropping activities from Congress. But if recent accounts by Intelligence members are accurate, we have also seen that agents follow multiple court procedures— first by seeking judicial approval to seize records and then by obtaining separate, highly targeted approval to examine records. Most of the very few members of Congress who have closely monitored the FISA process believe that it includes reasonable safeguards. Still, the policymaking system has been overly secretive, dominated by the executive, and slow to identify gaps in privacy protections. We suggest both changes to the Patriot Act and, more important, changes to the institutional arrangements for making decisions on surveillance policy. The FBI is curtailing its use of NSL’s Nakashima in 2011 (Ellen. "FBI Heads to Court More Often to Obtain Data on Personal Internet Usage." The Washington Post. The Washington Post, 26 Oct. 2011. Web. 29 June 2015.) The FBI is increasingly going to court to get personal e-mail and Internet usage information as service providers balk at disclosing customer data without a judge's orders. Investigators once routinely used administrative subpoenas, called national security letters, seeking information about who sent and received email and what Web sites individuals visited. The letters can be issued by FBI field offices on their own authority, and they obligate the recipients to keep the requests secret. But more recently, many service providers receiving national security letters have limited the information they give to customers' names, addresses, length of service and phone billing records. "Beginning in late 2009, certain electronic communications service providers no longer honored" more expansive requests, FBI officials wrote in August, in response to questions from the Senate Judiciary Committee. This marked a shift from comments made last year by Obama administration officials, who asserted then that most service providers were disclosing sufficient information when presented with national security letters. Investigators seeking more expansive information over the past two years have turned to court orders called business record requests . In the first three months of this year, more than 80 percent of all business record requests were for Internet records that would previously have been obtained through national security letters, the FBI said. The FBI made more than four times as many business records requests in 2010 than in 2009: 96 compared with 21, according to Justice Department reports. In response to concerns expressed by administration officials, Judiciary Committee Chairman Patrick J. Leahy (D-Vt.) has introduced a measure that would establish that the FBI can use national security letters to obtain "dialing, routing, addressing and signaling information." It would not include the content of an e-mail or other communications, the administration has said. The administration, which last year contemplated legislation to expand the authority of national security letters, has not taken a formal position on the Leahy measure, officials said. But the FBI has told Congress that the number of business record orders will continue to grow unless a legal change gives the agency more routine access to customer data. Civil liberties groups said Leahy's measure, included in a bill to modernize the Electronic Communications Privacy Act, would expand the government's authority to obtain substantial data about the private communications of individuals without court oversight. "Our view is data like e-mail 'to-from' information is so sensitive that it ought to be available only with a court order," said Greg Nojeim, senior counsel at the Center for Democracy and Technology. Privacy advocates said they support requiring the FBI to use court orders to seek the data. "This is an example of how the system should work," said American Civil Liberties Union legislative counsel Michelle Richardson. Business record requests are also known as Section 215 orders, after a provision in the Patriot Act, the law passed after the Sept. 11, 2001, terrorist attacks. The provision allows the government to obtain "any tangible thing" if officials can show reasonable grounds that it would be relevant to an authorized terrorism or espionage investigation. The ACLU and the Electronic Frontier Foundation on Wednesday plan to separately sue the government to force disclosure of its interpretation of Section 215. The groups are following the lead of Sen. Ron Wyden (D-Ore.), who has accused the administration of inappropriately withholding information about the law's use. On Oct. 19, Assistant Attorney General Ronald Weich wrote to Wyden, saying the government has briefed Congress on the classified uses of Section 215. "We do not believe the Executive Branch is operating pursuant to 'secret law,' " Weich wrote. An NSL is very similar to a grand jury subpoenas and NSLs have to be disclosed to congress currently Hinnen 2011 (“Statement of Todd Hinnen, Acting Assistant Attorney General for National Security, Before the House Judiciary Subcommittee on Crime, Terrorism and Homeland Security” March 30, 2011 http://www.justice.gov/nsd/justice-news-1) A national security letter is effectively an administrative subpoena, issued by a federal agency, requiring the production of certain limited types of information held by third-party custodians. NSLs are used during national security investigations in much the same way as grand jury subpoenas are used during routine criminal investigations. NSLs and grand jury subpoenas allow investigators to acquire the sort of very basic information that can be used as building blocks of an investigation; documents like telephone toll records, and banking and credit records. Unlike grand jury subpoenas, however, NSL authorities are limited to only certain types of records and are found in several distinct statutes, each of which has specific rules governing its use, the types of records that can be obtained, and the nature of the certification that must be provided. And, unlike most grand jury subpoenas, the NSL statutes all contain nondisclosure provisions, which, upon certification from a specified government official, restrict the recipient’s right to disclose the NSL. Finally, also unlike grand jury subpoenas, the government must report to Congress specific information regarding its use of NSLs. Case Advantages Human Rights Not Modeled US has A Cruel Record of Human Rights Carter 2012 (Jimmy Carter, the 39th President of the United States, 6-24-2012, "America’s Shameful Human Rights Record," New York Times, http://www.nytimes.com/2012/06/25/opinion/americasshameful-human-rights-record.html?_r= 0/30/15)TA THE United States is abandoning its role as the global champion of human rights. Revelations that top officials are targeting people to be assassinated abroad, including American citizens, are only the most recent, disturbing proof of how far our nation’s violation of human rights has extended. This development began after the terrorist attacks of Sept. 11, 2001, and has been sanctioned and escalated by bipartisan executive and legislative actions, without dissent from the general public. As a result, our country can no longer speak with moral authority on these critical issues. While the country has made mistakes in the past, the widespread abuse of human rights over the last decade has been a dramatic change from the past. With leadership from the United States, the Universal Declaration of Human Rights was adopted in 1948 as “the foundation of freedom, justice and peace in the world.” This was a bold and clear commitment that power would no longer serve as a cover to oppress or injure people, and it established equal rights of all people to life, liberty, security of person, equal protection of the law and freedom from torture, arbitrary detention or forced exile. The declaration has been invoked by human rights activists and the international community to replace most of the world’s dictatorships with democracies and to promote the rule of law in domestic and global affairs. It is disturbing that, instead of strengthening these principles, our government’s counterterrorism policies are now clearly violating at least 10 of the declaration’s 30 articles, including the prohibition against “cruel, inhuman or degrading treatment or punishment.” Recent legislation has made legal the president’s right to detain a person indefinitely on suspicion of affiliation with terrorist organizations or “associated forces,” a broad, vague power that can be abused without meaningful oversight from the courts or Congress (the law is currently being blocked by a federal judge). This law violates the right to freedom of expression and to be presumed innocent until proved guilty, two other rights enshrined in the declaration. In addition to American citizens’ being targeted for assassination or indefinite detention, recent laws have canceled the restraints in the Foreign Intelligence Surveillance Act of 1978 to allow unprecedented violations of our rights to privacy through warrantless wiretapping and government mining of our electronic communications. Popular state laws permit detaining individuals because of their appearance, where they worship or with whom they associate. The American Constitution is losing its influence – it is outdated, difficult to amend, and guarantees few rights Liptak 2012, Adam Liptak (Supreme Court correspondant of the NY Times) Feb 6, 2012, “We the People loses Appeal with People Around the World”, NY Times, The Constitution has seen better days. Sure, it is the nation’s founding document and sacred text. And it is the oldest written national constitution still in force anywhere in the world. But its influence is waning. In 1987, on the Constitution’s bicentennial, Time magazine calculated that “of the 170 countries that exist today, more than 160 have written charters modeled directly or indirectly on the U.S. version.” A quarter-century later, the picture looks very different. “The U.S. Constitution appears to be losing its appeal as a model for constitutional drafters elsewhere,” according to a new study by David S. Law of Washington University in St. Louis and Mila Versteeg of the University of Virginia. The study, to be published in June in The New York University Law Review, bristles with data. Its authors coded and analyzed the provisions of 729 constitutions adopted by 188 countries from 1946 to 2006, and they considered 237 variables regarding various rights and ways to enforce them. Occupy activists tested a float made with a copy of the Constitution in California. Credit Jae C. Hong/Associated Press “Among the world’s democracies,” Professors Law and Versteeg concluded, “constitutional similarity to the United States has clearly gone into free fall. Over the 1960s and 1970s, democratic constitutions as a whole became more similar to the U.S. Constitution, only to reverse course in the 1980s and 1990s.” “The turn of the twenty-first century, however, saw the beginning of a steep plunge that continues through the most recent years for which we have data, to the point that the constitutions of the world’s democracies are, on average, less similar to the U.S. Constitution now than they were at the end of World War II.” There are lots of possible reasons. The United States Constitution is terse and old, and it guarantees relatively few rights. The commitment of some members of the Supreme Court to interpreting the Constitution according to its original meaning in the 18th century may send the signal that it is of little current use to, say, a new African nation. And the Constitution’s waning influence may be part of a general decline in American power and prestige. In an interview, Professor Law identified a central reason for the trend: the availability of newer, sexier and more powerful operating systems in the constitutional marketplace. “Nobody wants to copy Windows 3.1,” he said. In a television interview during a visit to Egypt last week, Justice Ruth Bader Ginsburg of the Supreme Court seemed to agree. “I would not look to the United States Constitution if I were drafting a constitution in the year 2012,” she said. She recommended, instead, the South African Constitution, the Canadian Charter of Rights and Freedoms or the European Convention on Human Rights. The rights guaranteed by the American Constitution are parsimonious by international standards, and they are frozen in amber. As Sanford Levinson wrote in 2006 in “Our Undemocratic Constitution,” “the U.S. Constitution is the most difficult to amend of any constitution currently existing in the world today.” (Yugoslavia used to hold that title, but Yugoslavia did not work out.) Other nations routinely trade in their constitutions wholesale, replacing them on average every 19 years. By odd coincidence, Thomas Jefferson, in a 1789 letter to James Madison, once said that every constitution “naturally expires at the end of 19 years” because “the earth belongs always to the living generation.” These days, the overlap between the rights guaranteed by the Constitution and those most popular around the world is spotty. Americans recognize rights not widely protected, including ones to a speedy and public trial, and are outliers in prohibiting government establishment of religion. But the Constitution is out of step with the rest of the world in failing to protect, at least in so many words, a right to travel, the presumption of innocence and entitlement to food, education and health care. It has its idiosyncrasies. Only 2 percent of the world’s constitutions protect, as the Second Amendment does, a right to bear arms. (Its brothers in arms are Guatemala and Mexico.) Many foreign judges say they have become less likely to cite decisions of the United States Supreme Court, in part because of what they consider its parochialism. “America is in danger, I think, of becoming something of a legal backwater,” Justice Michael Kirby of the High Court of Australia said in a 2001 interview. He said that he looked instead to India, South Africa and New Zealand. Mr. Barak, for his part, identified a new constitutional superpower: “Canadian law,” he wrote, “serves as a source of inspiration for many countries around the world.” The new study also suggests that the Canadian Charter of Rights and Freedoms, adopted in 1982, may now be more influential than its American counterpart. The Canadian Charter is both more expansive and less absolute. It guarantees equal rights for women and disabled people, allows affirmative action and requires that those arrested be informed of their rights. On the other hand, it balances those rights against “such reasonable limits” as “can be demonstrably justified in a free and democratic society.” There are, of course, limits to empirical research based on coding and counting, and there is more to a constitution than its words, as Justice Antonin Scalia told the Senate Judiciary Committee in October. “Every banana republic in the world has a bill of rights,” he said. “The bill of rights of the former evil empire, the Union of Soviet Socialist Republics, was much better than ours,” he said, adding: “We guarantee freedom of speech and of the press. Big deal. They guaranteed freedom of speech, of the press, of street demonstrations and protests, and anyone who is caught trying to suppress criticism of the government will be called to account. Whoa, that is wonderful stuff!” “Of course,” Justice Scalia continued, “it’s just words on paper, what our framers would have called a ‘parchment guarantee.’ ” US has bad human rights now – 348 abuses found by the UN Dakwar 05/15 (Jamil Dakwar, Director, ACLU Human Rights Program, MAY 15, 2015”UN Issues Scathing Assessment of US Human Rights Record”, https://www.aclu.org/blog/speak-freely/un-issuesscathing-assessment-us-human-rights-record) The U.N. Human Rights Council adopted a scathing report today, consisting of 348 recommendations that address myriad human rights violations in the United States. The report came out as a part of a mechanism called the Universal Periodic Review (UPR), which examines the human rights record of all U.N. member states. The council questioned the United States on its record earlier this week. Although many of these recommendations in the report are redundant or too general to offer tangible solutions to the human rights situation in the U.S., they echo many of the concerns raised by U.S. civil society groups like the ACLU, who attended the review and offered concrete recommendations to reverse policies that are inconsistent with international human rights principles. For example, the report adopted a recommendation made by Sweden to "halt the detention of immigrant families and children, seek alternatives to detention and end use of detention for reason of deterrence." The report also adopted several recommendations calling on the Obama administration to independently investigate allegations of torture documented in the recent Senate torture report and provide reparations to victims. Denmark, for instance, recommended that the United States "further ensure that all victims of torture and ill-treatment — whether still in US custody or not — obtain redress and have an enforceable right to fair and adequate compensation and as full rehabilitation as possible, including medical and psychological assistance." In addition, the report included many fitting recommendations to address police brutality and excessive use of force as well as ending racial profiling against minorities and immigrants. Mexico recommended that the U.S. "adopt measures at the federal level to prevent and punish excessive use of force by law enforcement officials against members of ethnic and racial minorities, including unarmed persons, which disproportionately affect Afro American and undocumented migrants." Ireland, for its part, directly touched on the broken trust between American law enforcement and communities of color and recommended that the U.S. "continue to vigorously investigate recent cases of alleged police-led human rights abuses against African-Americans and seek to build improved relations and trust between U.S. law enforcement and all communities around the U.S." While in some areas, like LGBT rights and freedom of speech, the United States' human rights record fares far better than other parts of the world, in many areas — including national security, criminal justice, social and economic rights, and immigration policy — the U.S. has an abysmal record compared to other liberal democracies. This report sends a strong message of no-confidence in the U.S. human rights record. It clearly demonstrates that the United States has a long way to go to live up to its human rights obligations and commitments. This will be the last major human rights review for the Obama administration, and it offers a critical opportunity to shape the president's human rights legacy, especially in the areas of racial justice, national security, and immigrants' rights. The Obama administration has until September to respond to the 348 recommendations. At that time, the administration will make a direct commitment to the world by deciding which of the 348 will be accepted and implemented over the next four years, and which will be rejected. While many of the recommendations fall outside the constitutional powers of the executive branch — such as treaty ratification and legislative actions on the national, state, and local levels — the Obama administration should use its executive powers to their fullest extent to effectuate U.S. human rights obligations. The U.S. record for implementing U.N. recommendations has thus far been very disappointing, but if President Obama really cares about his human rights legacy, he should direct his administration to adopt a plan of action with concrete benchmarks and effective implementation mechanisms that will ensure that the U.S. indeed learns from its shortcomings and genuinely seeks to create a more perfect union. The world will be watching. HRs Violated Frequently Human rights are violated all the time while governments stand by Gummow, 2013 Gummow, Jodie. "14 Shocking Global Human Rights Violations of 2013." AlterNet. Alternet, 26 Dec. 2013. Web. 30 June 2015. From rampant violence and sexual abuse against women, to the commission of crimes against humanity by dictators, 2013 was a year filled with pervasive human rights violations worldwide. Government response to the atrocities was disappointing, marked by lack of transparency and accountability, blatant malevolence and a disregard for human life. Yet, international human rights advocates remained tenacious, inciting massive protests and public condemnation in an effort to demand an end to the culture of impunity. Here are some of most outrageous travesties of justice that captured our attention and had us up in arms this year. 1. Unsafe labor conditions in Bangladesh led to world’s worst garment industry tragedy as thousands died in horrific building collapse. On April 24, the Rana Plaza factory in Dhaka, Bangladesh, which housed six factories that produce clothing for Western brands, collapsed, killing over 1000 factory workers and injuring over 2500 people. While the owners of the factory came under fire for ignoring previous warnings of cracks in the wall, many pointed the blame at global corporations like Walmart and the Gap for exploiting workers for cheap labor and failing to provide adequate fire and building safeguards in factories where their products are made. Worldwide protests ensued with a view to putting pressure on major retailers to sign a legally binding accord aimed at improving labor conditions in Bangladesh, which to date has 100 signatories. 2. Egypt’s epidemic of violence and sexual abuse resulted in more than 600 deaths and 91 women assaulted in four days of riots at Tahrir Square. On the first anniversary of the election of President Mohamed Morsi on June 30, thousands of Egyptians took to the streets in Tahrir Square in Cairo demanding the dictator’s resignation. During the four days of protests, at least 91 women were attacked and sexually assaulted by mobs, while government leaders and police stood by and failed to intervene. Some women required extensive medical surgery after being subjected to brutal gang rapes and sexual assault with sharp objects. After the protests, survivors came forward to tell their stories and demand better protections for women. While the protests led to the end of Morsi’s presidency, the government downplayed the violence, prompting international calls to improve law enforcement and bring perpetrators to justice. These actions proved fruitless, as security forces again came under fire in August for using live ammunition against citizens resulting in 638 deaths. 3. Burma committed ethnic cleansing against thousands of Rohingya Muslims; 28 children hacked to death and mass graves uncovered. Burma’s quasi-civilian government was accused of committing crimes against humanity in the Rakhine State for forcibly displacing more than 125,000 Rohingya Muslims, the religious minority. A Human Rights Watch report revealed that authorities denied tens of thousands of stateless Muslims access to humanitarian aid, destroyed mosques, conducted mass arrests and issued a public statement promoting ethnic cleansing. Security forces stood aside and directly assisted Arakanese mobs in attacking and killing Muslim communities. In October, at least 70 Rohingya were killed in a day-long massacre in which 28 children hacked to death. Four mass gravesites were uncovered. The persecution stems from a long internal conflict in Burma essentially emanating from an arbitrary citizenship law passed in 1982 which denies Burmese citizenship to Rohingya on discriminatory ethnic grounds. In recent times, lack of rule of law has led to thousands of Rohingya fleeing the country. 4.North Korea’s large-scale human rights abuses revealed: 120,000 prisoners held in gulags, citizens starved and publicly executed by firing squad. North Korea’s appalling human rights record is no secret. Following the death of Kim Jong-il in 2011, any hope of improvement in the country was short-lived with the appointment of successor, Kim Jong-un. The young dictator quickly became more ruthless than his father, inflicting mass atrocities against his population. In September, a UN investigation revealed shocking evidence from defectors who compared life in DPRK to that of the German-run concentration camps in WWII. Prisoners in the gulags lucky enough to escape described atrocities including witnessing a woman forced to drown her own baby in a bucket. 120,000 people are still thought to be held in gulags. Public executions by firing squad have also continued at unprecedented levels under Jong-un’s rule, including the execution of the dictator’s own uncle and former girlfriend. The Security Council has been criticized for failing to refer the matter to the International Criminal Court, a move that seems unlikely given North Korea’s long alliance with China. 5. A chemical weapons attack in Syria. Syria’s ongoing civil war, which in almost three years has claimed the lives of approximately 100,000 people, continued full, force and throttle. In August, Syrian government forces under ruthless leader Bashar al-Assad were suspected of launching chemical weapon attacks on two Damascus suburbs, killing hundreds of civilians including children. Following the attack, an influx of disturbing and emotionally wrenching video footage infiltrated social media. In September, Russia and the United States announced an agreement that would lead to the abolition of Syria’s chemical weapons. The Organization for the Prohibition of Chemical Weapons was subsequently tasked with ensuring all chemical weapons and equipment in Syria be destroyed by mid-2014, though many remain skeptical about Assad’s compliance with the order. 6. Uganda, India and Russia passed draconian laws against homosexuality. While there were increasing wins for gay rights around the globe this year, including a number of U.S. states, LGBT rights took a major step back in other parts of the world. Uganda abolished the death penalty as punishment for having gay sex, but it passed an anti-gay law punishing “aggravated homosexuality” with life imprisonment. The new provision drew international criticism by gay rights activists, particularly after Uganda’s parliament expressed that the anti-gay law was a “Christmas gift” to all Ugandans. Meanwhile, India’s Supreme Court reinstated a ban against homosexuality, making gay sex a criminal offense, prompting human rights groups to file a petition seeking a review of the decision on the grounds that the law is unconstitutional. Russia’s anti-gay laws also came under fire for a bill that banned propaganda of “nontraditional sexual relations." 7. Turkey's Islamic fundamentalist regime attacked secular groups for peacefully assembling. Once considered the most modernized and advanced Islamic nation after founding father President Ataturk created a secular state, a number of civil rights violations in 2013 have led to fears that Turkey’s conservative government is heading toward Islamic fundamentalism. This summer, Turkish authorities were accused of using excessive police violence to put down an environmental sit-in over government plans to build a barracks in Gezi Park. During the demonstration, police used live ammunition, tear gas, water cannons and plastic bullets to suppress the masses. Authorities were also accused of sexually abusing female demonstrators and severely beating protestors, leaving more than 8000 people injured. The actions have outraged Turkey’s secular population. Protestors viewed the move as another indicator of the authoritarian propensities of Turkish Prime Minister Recep Tayyip Erdogan and his Islamist party. 8. Qatar’s construction sector rife with migrant worker abuse leading up to World Cup preparation. This year, the International Trade Union Confederation found that as a result of the construction frenzy surrounding the 2022 World Cup, 12 laborers would die each week unless the Doha government made urgent labor reforms. Half a million extra workers from countries like Nepal, India and Sri Lanka are expected to arrive to work in an effort to complete infrastructure in time for the World Cup kickoff. However, the ITUC said the annual death toll could rise to 600 people a year as construction workers are subjected to harsh and dangerous work conditions daily. A comparable study revealed that 44 migrant construction workers from Nepal died in the summer working in exploitive conditions, with workers describing forced labor conditions where they work in 122 degree heat and live in squalor. 9. Forced sterilization for disabled underage girls in Australia sparked outrage as attempts to reform the laws failed. The involuntary sterilization of disabled people in Australia remains lawful after the Senate ruled that it would not ban the procedure in 2013. Disabled girls are sterilized to manage menstruation and the risks associated with sexual exploitation, which human rights groups argue is a form of violence against women. Australian families are able to apply for court orders to allow involuntary sterilization of their disabled children. A court previously ruled that it was in the best interests of an 11-year-old girl who suffered a neurological disorder to have a hysterectomy, which caused a media storm. Human rights groups argued that fertility is a basic human right and that sterilization is not a substitute for proper education about family planning and support during menstruation. The Human Rights Commission said “one sterilization, one forced or coerced is one too many.” 10. Afghanistan attempted to reintroduce public stoning for adulterers; women were forced to undergo vaginal examinations to prove virginity. Women’s rights suffered a massive blow in Afghanistan in 2013. Cases of violence against women grew by 28 percent and females continued to be treated as second-class citizens. President Hamid Karzai backed away from government plans to implement a controversial law reintroducing public stoning as punishment for adultery after the draft law was leaked causing international outrage. Women’s rights groups condemned invasive vaginal examinations women are forced to undergo to ascertain “virginity” every time a girl is arrested on a morality charge. As the 2014 deadline to withdraw combat action in Afghanistan approaches, activists fear that the removal of soldiers will trigger further deterioration of the chaotic human rights situation in the country, particularly for women. 11. Israel’s mistreatment of Palestinian children resulted in 700 child detentions. The precarious situation in the Middle East between Palestinians and Israelis led to a number of gross human rights violations committed by Israeli soldiers against Palestinian children. A UNICEF report revealed that in the second quarter of 2013, 700 Palestinian children aged 12-17 were arrested and subjected to solitary confinement, threats of death and sexual assault by Israeli military and police in the occupied West Bank. In November, an Israeli Defense Force soldier on a Ukraine game show nonchalantly discussed killing Palestinian toddlers as young as 3 years old. A 12-year-old Palestinian boy was paralyzed after he was shot and seriously injured by an Israeli solider as he attempted to retrieve his school bag, and a 14-year-old Palestinian girl died en route to hospital this month as a result of tightened Israeli security at Israeli-controlled checkpoints, prompting public outrage. 12. New wave of repression against civil society swept Saudi Arabia as women continued to protest against de facto ban on driving. With more than 40,000 political prisoners in detention and democracy silenced by threats of intimidation and arrests, 2013 was one of the worst years for human rights in Saudi Arabia, according to activists. In addition, women faced major oppression. While women will now be allowed to vote in 2015, Saudi females are still not allowed to drive, despite the fact there is no express law making it illegal. In protest this October, women in Saudi Arabia defied the de facto ban on driving by getting behind the wheel in a brave display of civil disobedience, as part of their Women2Drive campaign. The move prompted threats of punishment by the government and resulted in the detention of 14 women. 13. South Sudan declared a humanitarian crisis with bloody massacres, 100,000 refugees, discovery of mass graves and violent attacks on U.N peacekeepers. Post-independence, South Sudan was stricken with internal conflict in 2013 resulting in extrajudicial killings and numerous human rights atrocities. While Sudan’s north is home to mainly Arabic-speaking Muslims, South Sudan has no dominant culture. Instead, it is home to some 200 ethnic groups, each with its own beliefs and language. In a recent spate of ethnically motivated violence between the two largest ethnic groups, the Dinkas and Nuers, security forces shot and killed more than 200 people in the capital Juba. Almost 100,000 people have been displaced as a result of the violence. In reponse, the Security Council doubled UN peacekeeping troops to bolster its mission to protect civilians. The United Nations compound was raided earlier this year killing Indian peacekeepers. This week alone, the UN discovered 75 bodies in mass graves, evidence of ethnic killings taking place. 14. French military intervention in Mali led to catastrophic escalation of retaliatory ethnic violence fueled by poverty and famine. The security situation in Mali made headlines in 2013 following French intervention, which arguably exacerbated conditions in the wartorn country. The ongoing armed conflict led to appalling human rights violations fraught with a lack of government accountability. In June, UN investigation revealed countless cases of extrajudicial executions, torture and enforced disappearances of civilians carried out by both Tuareg rebels and the army. Soldiers were accused of torturing Tuaregs while French-led forces attempted to oust Islamist militants. The precarious situation was further aggravated by pervasive food insecurity and extreme poverty throughout Africa’s Sahel region, which stretches from the Atlantic Ocean to the Red Sea. According to the United Nations the United States is failing in 25 human rights issues Hudson 2014 Hudson, Adam. "UN Human Rights Committee Finds US in Violation on 25 Counts." Truthout. Truth Out, 4 Apr. 2014. Web. 30 June 2015. While President Obama told the country to "look forward, not backward" when it came to Bush's torture program, the United Nations has taken a different route. Recently, the UN Human Rights Committee issued a report excoriating the United States for its human rights violations. It focuses on violations of the International Covenant on Civil and Political Rights, to which the country is party. The report mentions 25 human rights issues where the United States is failing. This piece will focus on a few of those issues Guantanamo, NSA surveillance, accountability for Bush-era human rights violations, drone strikes, racism in the prison system, racial profiling, police violence, and criminalization of the homeless. Accountability for Bush-Era Crimes; Torture The UN committee expressed concerned with "the limited number of investigations, prosecutions and convictions of members of the Armed Forces and other agents of the US government, including private contractors" for "unlawful killingsin its international operations" and "torture" in CIA black sites during the Bush years. It welcomed the closing of the CIA black sites, but criticized the "meagre number of criminal charges brought against low-level operatives" for abuses carried out under the CIA's rendition, interrogation and detention program. The committee also found fault with the fact that many details of the CIA's torture program "remain secret, thereby creating barriers to accountability and redress for victims." In response to the 9/11 terrorist attacks, the Bush administration jettisoned the Constitution and international law and openly embraced the use of torture against suspected terrorists captured overseas. The CIA tortured people in secret prisons around the world known as "black sites." Torture was sanctioned from the top down. Then-President George W. Bush, Vice President Dick Cheney, Defense Secretary Donald Rumsfeld, National Security Advisor Condoleezza Rice, lawyers and many others in the executive branch played roles in crafting nifty ways to justify, approve and implement the use of torture. Rather than be held accountable, the top-level government officials responsible for authorizing torture and other crimes have been given comfort in the public sphere. Condoleezza Rice returned to Stanford University as a political science professor. John Yoo, who authored the torture memos, is a law professor at UC Berkeley. Jose Rodriguez, a former CIA officer in the Bush administration, vigorously defends torture in his autobiography and interviews. George W. Bush, Dick Cheney and Donald Rumsfeld are able to rest comfortably in retirement and continue to defend their records. Of the report's 25 issues, four looked at racial disparities within the United States' criminal justice system and law enforcement practices. In the Guantanamo military commissions, evidence of torture is concealed. A "protective order" restricts what defense lawyers and the accused can say about how the defendants were treated in CIA black sites, including details of torture, because that information is classified. Defense lawyers have been fighting for declassification of those details, as they are mitigating evidence. The potential release of portions of the Senate Intelligence Committee's report on the CIA torture program could tip the scale the defense attorneys' favor. "There is every reason to believe the SSCI [Senate Select Committee on Intelligence] Report contains information about the CIA's torture of Mr. al Baluchi," said defense attorney James Connell, who represents Ammar al-Baluchi, one of the five 9/11 defendants, in a press statement. "The SSCI knows the truth of what happened, and the military commission considering whether to execute Mr. al Baluchi should know too." Racism in the Prison System; Racial Profiling; Police Brutality Of the report's 25 issues, four looked at racial disparities within the United States' criminal justice system and law enforcement practices. It denounced the "racial disparities at different stages in the criminal justice system, sentencing disparities and the overrepresentation of individuals belonging to racial and ethnic minorities in prisons and jails." The committee condemned racial profiling by police and FBI/NYPD surveillance of Muslims - but it did welcome plans to reform New York City's "stop and frisk" program. It also denounced the continuing use of the death penalty and "racial disparities in its imposition that affects disproportionately African Americans." Finally, it expressed concern at "the still high number of fatal shootings by certain police forces" and "reports of excessive use of force by certain law enforcement officers including the deadly use of tasers, which have a disparate impact on African Americans, and the use of lethal force by Customs and Border Protection (CBP) officers at the US-Mexico border." The United States contains the largest prison population in the world, holding over 2.4 million people in domestic jails and prisons, immigration detention centers, military prisons, civil commitment centers and juvenile correctional facilities. Its prison population is even larger than those of authoritarian governments like China and Russia, which, respectively, hold 1,640,000 and 681,600 prisoners, according to the International Centre for Prison Studies. More than 60 percent of the US prison population are people of color. African Americans, while 13 percent of the national population, constitute nearly 40 percent of the prison population. Moreover, one in every three black males can expect to go to prison in their lifetime, compared to one in every six Latino males, and one in every 17 white males. Thus, black men are six times more likely to be incarcerated than white men. Even though whites and blacks use drugs at roughly the same rates, African Americans are more likely to be imprisoned for drug-related offenses than whites. Every 28 hours, a black person is killed by a police officer, security guard, or self-appointed vigilante, according to a report by the Malcolm X Grassroots Movement. Recently in New York City, NYPD brutalized two teenage AfricanAmerican girls at a Chinese restaurant in Brooklyn. A 16-year-old girl's face was slammed against the floor, while police threw the 15-year-old through the restaurant's window, shattering it as a result. The incident started when police ordered everyone to leave the restaurant, but one of the girls refused. While police violence against people of color has long existed, the militarization of American police exacerbates this trend. This trend began when Richard Nixon inaugurated the War on Drugs in the 1970s. Then in 1981, President Ronald Reagan signed the Military Cooperation with Civilian Law Enforcement Agencies Act, which provided civilian police agencies with military equipment, training, advice and access to military research and facilities. When 9/11 hit, police militarization kicked into overdrive with the creation of the Department of Homeland Security, which has given police still greater access military equipment like armored personnel carriers and high-powered weapons for anti-terrorism purposes. Now police look, act and think like the military, with dangerous consequences for the communities they serve. Among the report's suggestions to curb excessive police violence were better reporting of incidents, accountability for perpetrators, and "ensuring compliance with the 1990 UN Basic Principles on the Use of Force and Firearms by Law Enforcement Officers". The Basic Principles include a number of provisions, including "Law enforcement officials, in carrying out their duty, shall, as far as possible, apply non-violent means before resorting to the use of force and firearms" and "Governments shall ensure that arbitrary or abusive use of force and firearms by law enforcement officials is punished as a criminal offence under their law." Drone Strikes, Assassination To execute its perpetual global war on terrorism, the Bush administration favored large-scale, conventional land invasions and occupations, as in Iraq and Afghanistan. Obama has moved away from such operations and embraced seemingly lighter tactics of irregular warfare to continue the perpetual war, while making it less visible to Americans. Extrajudicial killing and drone strikes are the most notable methods, but others include air strikes, cruise missile attacks, cyberwarfare, special operations, and proxy wars. These tactics have meant more use of the military's Joint Special Operations Command (JSOC) and the paramilitary branch of the CIA. Both the CIA and JSOC carry out drone strikes and sometimes collaborate in joint operations. The CIA, not the military, is legally mandated to launch covert operations, which are classified and unacknowledged by the US government. However, JSOC performs essentially the same operations, particularly extrajudicial killings. Thus, transferring control of the drone program from the CIA to the military would make little difference. The UN report criticized the United States' assassination program and drone strikes. It expressed concerned with the "lack of transparency regarding the criteria for drone strikes, including the legal justification for specific attacks, and the lack of accountability for the loss of life resulting from such attacks." The United States' position for justifying its extrajudicial killing operations is that it is engaged in an armed conflict with al-Qaeda, the Taliban and "associated forces" - a term the Obama administration created to refer to co-belligerents with al-Qaeda - and that the war is in accordance with the nation's inherent right to self-defense against a terrorist enemy. However, the committee took issue with the United States' position, particularly its "very broad approach to the definition and the geographical scope of an armed conflict, including the end of hostilities." A May 2010 report by Philip Alston, former UN special rapporteur on extrajudicial, summary or arbitrary executions, notes that, under international law, states cannot wage war against non-state actors, such as international terrorist groups like al-Qaeda, because of their nebulous character and loose affiliations. The committee's report also took issue with "the unclear interpretation of what constitutes an 'imminent threat' and who is a combatant or civilian taking a direct part in hostilities, the unclear position on the nexus that should exist between any particular use of lethal force and any specific theatre of hostilities, as well as the precautionary measures taken to avoid civilian casualties in practice." So far, US drone strikes and other covert operations have killed between 2,700 and nearly 5,000 people. Under international law, self-defense against an "imminent" threat is "necessity of that self-defense is instant, overwhelming, and leaving no choice of means, and no moment for deliberation." However, the Obama administrationcompletely obliterated this meaning. In a16-page white paper leaked to NBC News, the Obama administration believes that whether "an operational leader present an 'imminent' threat of violent attack against the United States does not require the United States to have clear evidence that a specific attack on U.S. persons and interest will take place in the immediate future." Thus, a "high-level official could conclude, for example, that an individual poses an 'imminent threat' of violent attack against the United States where he is an operational leader of al-Qa'ida or an associated force and is personally and continually involved in planning terrorist attacks against the United States" without any proof of an actual plot against the U.S. Thus, in Obama-lingo, the word "imminent" means the complete opposite of what it is in the English language. There is no due process in the assassination program, either. President Obama and his advisors decide who will be killed by a drone strike in a secret internal executive branch process that occurs every Tuesday. Even American citizens are fair game for the assassination program. In fact, four US citizens have been killed by drone strikes, including a 16-year-old boy. A database called the "disposition matrix" adds names to kill or capture lists, ensuring the assassination program will continue no matter who is in office. Targeting for drone strikes is not based on human intelligence but, rather, signals intelligence, particularly metadata analysis and cellphone tracking. According to a report by The Intercept, the NSA geolocates a SIM card or mobile phone of a suspected terrorist, which helps the CIA and JSOC to track an individual to kill or capture in a night raid or drone strike. However, it is very common for people in places like Yemen or Pakistan, to hold multiple SIM cards, give their phones, with the SIM cards in them, to children, friends, and family, and for groups like the Taliban to randomly distribute SIM cards among their units to confuse trackers. As a result, since this methodology targets SIM cards rather than real people, civilians are regularly killed by mistake. As with the word "imminent," the Obama administration utilizes its own warped definitions of "civilian" and "combatant." As The New York Times reported in May 2012, the Obama administration "counts all military-age males in a strike zone as combatants . . . unless there is explicit intelligence posthumously proving them innocent." Despite claims to the contrary, drone strikes kill a significant number of civilians and inflict serious human suffering. So far, US drone strikes and other covert operations have killed between 2,700 and nearly 5,000 people, including 500 to more than 1,100 civilians in Pakistan, Yemen and Somalia, according to the Bureau of Investigative Journalism's figures. Many of those deaths occurred under Obama's watch, with drone strikes killing at least 2,400 people during his five years in office. Only 2 percent of those killed by drone strikes in Pakistan are high-level militants, while most are low-level fighters and civilians. In addition to causing physical harm, drone strikes terrorize and traumatize communities that constantly live under them. Drone strikes have lulled in Pakistan due to peace talks between the Pakistani government and Pakistan Taliban, which collapsed on February 17. The last US drone strike in Pakistan happened on Christmas Day 2013. In Yemen, drone strikes have continued. Several US drone strikes in Yemen occurred during the first 12 days of March. Last November, six months after President Obama laid out new rules for US drone strikes, a TBIJ analysis showed that "covert drone strikes in Yemen and Pakistan have killed more people than in the six months before the speech." It also was recently reported that the Obama administration is debating whether to kill a US citizen in Pakistan who is suspected of "actively plotting terrorist attacks," according to The New York Times. It is very likely these operations will continue. The Pentagon's 2015 budget proposal, taking sequestration into account, spends $0.4 billion less than 2014 at $495.6 billion, shrinks the Army down to between 440,000 to 450,000 troops from the post-9/11 peak of 570,000, and protects money for cyberwarfare and special operations forces. Cyber operations are allocated $5.1 billion in the proposal, while US Special Operations Command gets $7.7 billion, which is 10 percent more than in 2014, and a force of 69,700 personnel. While President Obama promised to take the United States off a "permanent war footing," his administration's policies tell a different story. The Obama administration is reconfiguring, rather than halting, America's "permanent war footing." Guantanamo, Indefinite Detention President Obama recommitted himself to closing the prison in Guantanamo last year, but has made little progress, which the UN report noted. The committee said it "regrets that no timeline for closure of the facility has been provided." It also expressed concern that "detainees held in Guantanamo Bay and in military facilities in Afghanistan are not dealt with within the ordinary criminal justice system after a protracted period of over a decade in some cases." The report called on the United States to expedite the transfer of prisoners out of Guantanamo, close the prison, "end the system of administrative detention without charge or trial" and "ensure that any criminal cases against detainees held in Guantanamo and military facilities in Afghanistan are dealt with within the criminal justice system rather than military commissions and that those detainees are afforded fair trial guarantees." Indefinite detention violates international human rights law, but has been embraced by Obama ever since he stepped into the White House. Currently, 154 men remain held in the prison at Guantanamo Bay. Of those, 76 are cleared for release; around four dozen will remain in indefinite detention; 20 can be "realistically prosecuted," according to chief prosecutor Brig. Gen. Mark Martins' estimate; six are being tried in military commissions and two are serving sentences after being convicted in the commissions. President Obama promised to close Guantanamo right when he stepped into office. However, he has yet to fulfill that promise. Congressional obstructionism, especially from the Republican Party, has stalled his plans. For a long time, Congress blocked funding for transferring Guantanamo prisoners. Recently, though, Congress easedthose restrictions, making it easier to transfer prisoners to other countries, but not to the United States. While the Obama administration is working to close the prison at Guantanamo, it maintains the policy of indefinite detention without trial, designating nearly four dozen Guantanamo prisoners for forever imprisonment. Obama's original plan to close Guantanamo was to open a prison in Illinois to hold Guantanamo detainees, many indefinitely. While soon killed, this plan would have effectively moved the system of indefinite detention from Guantanamo to US soil. Now the Obama administration is considering opening a prison in Yemen to hold the remaining Guantanamo prisoners, many of whom are Yemeni. Indefinite detention violates international human rights law, but has been embraced by Obama ever since he stepped into the White House. The 2012 National Defense Authorization Act (NDAA) that Obama signed into law contains sections that allow for the indefinite detention of US citizens on American soil. NSA Surveillance Notably, the UN report denounced the NSA's mass surveillance "both within and outside the United States through the bulk phone metadata program (Section 215 of the PATRIOT Act) and, in particular, the surveillance under Section 702 of Amendments to the Foreign Intelligence Surveillance Act (FISA) conducted through PRISM (collection of the contents of communications from US-based companies) and UPSTREAM (tapping of fiber-optic cables in the country that carry internet traffic) programs and their adverse impact on the right to privacy. "The report also criticized the secrecy of "judicial interpretations of FISA and rulings of the Foreign Intelligence Surveillance Court (FISC)," which prevent the public from knowing the laws and legal interpretations that impact them. Promises of "oversight" obviously did not persuade the committee, either, as it said "the current system of oversight of the activities of the NSA fails to effectively protect the rights of those affected," and "those affected have no access to effective remedies in case of abuse." Continuing NSA leaks, provided by former intelligence contractor Edward Snowden last year, have revealed the depth of the United States' massive surveillance system. The bulk collection of phone metadata is probably the most well-known program. Recently, President Obama proposed ending the bulk phone metadata collection program. But the NSA's surveillance system extends far beyond phone metadata. In a program called PRISM, the NSA collects user data, such as search history and message content, sent through internet communication services like Google, Yahoo!, Facebook and Skype. Major tech companies have denied knowledge of the program, but the NSA claims those companies knew and provided full assistance. The NSA uses a back door in surveillance law to monitor the communications of American citizens without a warrant. As mentioned earlier, the NSA is also involved in the drone program through the collection of signals intelligence. Additionally, much of NSA surveillance is used for economic espionage. With the help of Australian intelligence, the NSA spied on communications between the Indonesian government and an American law firm representing it during trade talks. Indonesia and the United States have long been in trade disputes, such as over Indonesia's shrimp exports and a US ban on the sale of Indonesian clove cigarettes. It is highly unlikely Obama's reforms will curb these abuses. Criminalizing the Homeless The plight of homeless people is rarely held up as a pressing human rights issue. But, in the UN report, it is. The committee expressed concern "about reports of criminalization of people living on the street for everyday activities such as eating, sleeping, sitting in particular areas etc." It also "notes that such criminalization raises concerns of discrimination and cruel, inhuman, or degrading treatment." For evidence of such criminalization and of "cruel, inhuman, or degrading treatment," look no further than to the liberal, historically countercultural city of San Francisco. The city that smugly prides itself on progressivism has a sit-lie ordinance that forbids people from sitting or lying on public sidewalks between 7 AM and 11 PM. It particularly hurts and targets homeless people. In the same city, homeless people are washed away. Street cleaners from the San Francisco Department of Public Works regularly spray their high-powered hoses at homeless people sleeping on the streets. Recently, in Albuquerque, New Mexico, police shot and killed a homeless man. His crime? Illegal camping . . . in the Albuquerque foothills. Albuquerque police went to arrest 38-year-old James Boyd, who was sleeping in a campsite he set up. After arguing with police for three hours, Boyd was apparently about to leave and picked up his belongings. As he started walking down the hill, police shot a flash-bang device at Boyd. Disoriented, he dropped his bags, appeared to take out a knife, and then police fired multiple bean-bag rounds at Boyd. The man fell to the ground, hitting his head on a rock, his blood spattered on it. Officers yelled at him, telling Boyd to drop his knife. When Boyd didn't answer, police fired more bean-bag rounds and sicced their dog on him. Boyd was later taken to a hospital and pronounced dead a day later. In addition to stun guns and bean bags, officers shot six live rounds at Boyd. The shooting prompted an FBI investigation, which is ongoing, and a protest in Albuquerque that was met with intense police violence as officers fired tear gas into the crowd. Clean Your Own Backyard The UN report elevates the suffering inflicted by US domestic and foreign policies to the realm of international human rights. To be tortured, spied on, unjustly imprisoned, put in solitary confinement, indefinitely detained, extrajudicially killed by the state, racially profiled, deprived of a home and criminalized for being homeless is to have one's basic human rights violated and dignity as a human demolished. That's why there are international laws to protect those rights - laws with which the United States and every nation-state are bound to comply. Even as the United States commonly condemns other countries for their human rights abuses, it has yet to clean its own house. Human rights are continuing to be broken even now. United Nations Human Rights in 2015 (Office of the High Commissioner for Human Rights, “Human Rights Council opens twenty-eight session”, United Nations Human Rights, http://www.ohchr.org/EN/NewsEvents/Pages/DisplayNews.aspx?NewsID=15630&LangID=E) BAN KI-MOON, United Nations Secretary-General, in a video message, said that the world faced serious human rights violations from discrimination, inequality and violent extremism and the challenge was to keep those from occurring. The United Nations had the mandate and tools in place to act preventively and the biggest challenge to using those tools was the lack of political consensus between Member States. The United Nations Secretary-General appealed to the Human Rights Council to support the work of local human rights actors who were the only guarantee of national sovereignty, and looked at Member States to generate that most needed shift in the ways of working. The United States has poor human rights standards – social and economic failures NESRI, no date (National Economic and Social Rights Initiative, “Human rights in the United States: Beginning at Home” http://www.nesri.org/human-rights/human-rights-in-the-united-states) Human Rights in the United States: Beginning at Home Introduction In recent history, the United States government and many organizations in the United States have often talked about human rights as if they were only relevant to abuses in other countries, and claims of human rights violations were leveled by, not at, the U.S. government. Although human rights documents and treaties claimed to discuss universal rights obligations that applied to all countries, the prevailing wisdom was that people in the United States did not need human rights standards or international scrutiny to protect their rights. Yet, many Americans have always believed that the struggle for human rights is profoundly relevant to the United States. One of the earliest uses of the term “human rights” is attributed to Frederick Douglas when he referred to the fundamental rights of enslaved African-Americans at the time when the United States did not recognize their humanity or their rights. Indeed, the idea that all individuals have fundamental rights rooted in the concept of human dignity and that the international arena might provide support in domestic rights struggles has often resonated with marginalized and disenfranchised people. So it was no surprise that U.S. rights organizations, including the NAACP and the American Jewish Congress, played a crucial role in the birth of the modern human rights movement. Both groups helped to ensure that human rights were included in the UN Charter which founded the United Nations. Despite fierce resistance from adversaries of human rights, such as avowed segregationists or more recently advocates of U.S. exceptionalism, who successfully delayed human rights advocacy within the United States for decades, there has been a growing domestic human rights movement that is committed to the long term vision of ensuring the full range of human rights for all within or at our borders. This movement - comprised of community organizers, academics and scholars, lawyers, artists, web activists, policy advocates, economists, educators and many others - is multi-issue covering the span of civil, political, economic, social and cultural rights. It is ambitious in its breadth and scope and audacious in its aspirations. There are many voices that still argue that rights such as health care or housing are only commodities that serve market interests. The human rights movement, however, is a platform for voices who argue, intensely and passionately, that this view cannot and must not prevail. Economic and Social Rights in the United States: Six Rights, One Promise The U.S. government has rarely recognized the relevance of human rights standards within the United States, or recognized that human rights obligations include obligations to protect basic economic and social rights. Few people would hesitate to condemn poor education systems, inadequate health care infrastructure, hunger, scores of families suffering from abject poverty and homelessness, wages that do not support a dignified life, and widespread economic insecurity. Nor would anyone plausibly deny that all of these are sharply evident in the United States. Yet, successive U.S. administrations have explicitly resisted the notion that every person has fundamental economic and social rights to be free from such conditions and failed to reform our legal, political, and economic system to meet people's needs and protect people from the structural inequalities that amount to a systemic assault on human dignity. Historically, the United States played an important role in the development of the Universal Declaration of Human Rights which embraced economic and social rights, including the right to housing, education, decent work, social security, food and health care (later expanded to the right to health more broadly within the UN system). In fact, the international economic and social rights framework was deeply influenced by President Franklin D. Roosevelt’s “Four Freedoms” agenda, which included freedom from want. But this visionary promise represented by these six rights is long overdue. While every U.S. state recognizes a basic right to education, there are still deep inequities in education and too many children face degraded school environments that push them out of schools. (see NESRI's work with the Dignity in Schools Campaign). Health care, food, housing and access to decent work (or in the event of unemployment or disability basic social security) are still not recognized as basic rights leading to irrational and damaging policy choices that leave scores of families unable to meet their fundamental needs. This landscape calls for revisiting why the United States has denied economic and social rights to its people, and for a change in our vision of basic rights, government responsibility and our collective commitment to meeting the fundamental needs of all. The Call for Economic and Social Rights: A Revolution of Values Economic and social rights are a natural, and in fact necessary, outgrowth of U.S. founding ideals of equality, freedom and human dignity. Social movement leaders have often recognized this relationship. Around the time of his launching the Poor People’s Campaign, Rev. Dr. Martin Luther King Jr. spoke to this stating: “We read one day. We hold these truths to be self-evident that all men are created equal.That they endowed by their Creator with certain inalienable rights. That among these, are life, liberty, and the pursuit of happiness. But if a man doesn’t have job or an income, he has neither life, nor liberty and the possibility for the pursuit of happiness. He merely exists.” —Martin Luther King, Jr. (March 1968) Issuing a dramatic challenge, Dr. King called for a Bill of Economic Rights and recognized that: “We have moved from the era of civil rights to the era of human rights, an era where we are called upon to raise certain basic questions about the whole society. We have been in a reform movement… But after Selma and the voting rights bill, we moved into a new era, which must be the era of revolution. We must recognize that we can’t solve our problem now until there is a radical redistribution of economic and political power… this means a revolution of values and other things. We must see now that the evils of racism, economic exploitation and militarism are all tied together…you can’t really get rid of one without getting rid of the others… the whole structure of American life must be changed. America is a hypocritical nation and [we] must put [our] own house in order.” —Martin Luther King, Jr. (May 1967) Bringing economic and social rights home is a central part of putting our house in order and living up to our ideals. Neither charity nor temporary policy shifts will protect the basic dignity and equality of the ever larger number of people within the United States who are being pushed out to the margins of our increasingly harsh economy. Moreover, lack of resources is not the cause of any of these harms imposed on individuals, families and communities. Even in this economic downturn, the United States has the capacity to meet the needs of all its people. We do not really face a housing crisis. Instead, we face a policy crisis evidenced by the fact that while we have so many people without homes, we continue to allow an ever increasing number of homes to go empty without people. Irrational and unjust policy choices impact almost every economic and social rights issue facing people in the United States today. Recognizing basic economic and social rights defends both the poor and middle class against the interests that threaten access to these fundamental needs and human dignity. Privacy Most Americans believe that NSA surveillance it warranted Cohen in 2013 (Jon Cohen; Cohen is polling director for Capital Insight, Washington Post Media’s independent polling group, “Most Americans back NSA tracking phone records, prioritize probes over privacy”, Washington Post 6/10/13, Website, 7/2/15, http://www.washingtonpost.com/politics/most-americans-support-nsatracking-phone-records-prioritize-investigations-over-privacy/2013/06/10/51e721d6-d204-11e2-9f1a1a7cdee20287_story.html A large majority of Americans say the federal government should focus on investigating possible terrorist threats even if personal privacy is compromised, and most support the blanket tracking of telephone records in an effort to uncover terrorist activity, according to a new Washington Post-Pew Research Center poll. Fully 45 percent of all Americans say the government should be able to go further than it is, saying that it should be able to monitor everyone’s online activity if doing so would prevent terrorist attacks. A slender majority, 52 percent, say no such broad-based monitoring should occur. The new survey comes amid recent revelations of the National Security Agency’s extensive collection of telecommunications data to facilitate terrorism investigations. Overall, 56 percent of Americans consider the NSA’s accessing of telephone call records of millions of Americans through secret court orders “acceptable,” while 41 percent call the practice “unacceptable.” In 2006, when news broke of the NSA’s monitoring of telephone and e-mail communications without court approval, there was a closer divide on the practice — 51 percent to 47 percent. General priorities also are similar to what they were in 2006: Sixty-two percent of Americans now say it’s more important for the government to investigate terrorist threats, even if those investigations intrude on personal privacy, while 34 percent say privacy should be the focus, regardless of the effect on such investigations. Constitutionality Third party information does not fall under the fourth amendment Moore in 2009 (Trevor, studying political science at Brigham Young University, “PRIVACY vs. THE PUBLIC Good: NATIONAL SECURITY LETTERS AND THE FOURTH AMENDMENT”, Vol. 23, https://ojs.lib.byu.edu/spc/index.php/PrelawReview/article/viewFile/13600/13478) In United States v. Miller, the government accused Mitch Miller of operating a distillery without the proper license and of engaging in tax fraud.9 the government's case was based in part on bank records obtained by a grand jury subpoena. An appellate court ruled that the records should have been suppressed.10 The Supreme Court reversed the decision, saying, The depositor takes the risk, in revealing his affairs to another, that the information will be conveyed by that person to the Government. This Court has held repeatedly that the Fourth Amendment does not prohibit the obtaining of information revealed to a third party and conveyed by him to Government authorities, even if the information is revealed on the assumption that it will be used only for a limited purpose and the confidence placed in the third party will not be betrayed.1 The collection of Meta data without a warrant is constitutional in the Smith vs Maryland decision Ombres in 2015 (Devon, J.D. 2006 from Stetson University College of Law; L.L.M. 2013 from American University Washington College of Law, NSA DOMESTIC SURVEILLANCE FROM THE PATRIOT ACT TO THE FREEDOM ACT: THE UNDERLYING HISTORY, CONSTITUTIONAL BASIS, AND THE EFFORTS AT REFORM, Seton Hall Legislative Journal, 2015,) There is little doubt that the collection of content data, absent probable cause, violates the Fourth Amendment as an unreasonable search. n28 However, whether the mass collection of domestic metadata violates the Fourth Amendment is a question that is still being wrestled with due to the historical approval of the Third Party Doctrine ("TPD") arising from the seminal opinion of Smith v. Maryland. n29 In Smith, a PR was used to assist in a conviction of a burglary. n30 The Supreme Court held that using a PR did not constitute an unreasonable search because individuals are aware that phone companies maintain permanent records of dialed phone numbers, thereby abrogating any expectation of privacy. n31 As Smith has not been overruled, it maintains its standing as a guiding principle under stare decisis and is being utilized, at least in part, as a basis for conducting domestic surveillance as discussed below. The FISC cites directly to the Smith reasoning, in a heavily redacted [*34] opinion/order, in noting that there is no reasonable expectation of privacy in the collection of metadata. n32 The FISC notes that Congress relaxed requirements to collect "non-content addressing information through [PR] and [TT] devices" through the PATRIOT Act and FISA Amendments and that "such information is not protected by the Fourth Amendment." n33 Like phone calls under Smith, the FISC held that email users, due to the same reasoning, also do not have an expectation of privacy. n34 The FISC recognized the need for only a relevance standard, rather than reasonable suspicion, in approving the government's requests for widespread surveillance. n35 The FISC analogizes the low hit rate in obtaining actionable information through dragnet metadata collection to DUI checkpoints and drug testing students in justifying suspicionless searches. n36 Further, great deference must be given to the government officials who have a unique understanding of these situations, and they do not need to act in the least intrusive means available. n37 In so approving of the bulk collection of metadata, the court provided: analogous to suspicionless searches and seizures that have upheld under the Fourth Amendment in that the Government's need is compelling and immediate, the intrusion on individual privacy interests is limited, and bulk collection appears to be a reasonably effective means of monitoring (redacted) related operatives ... . In these circumstances, the certification of relevance is consistent with the fact that only a very small proportion of the huge volume of information collected will be directly relevant to the FBI's (redacted) [*35] investigations. NSLs do not violate the 4th Amendment – third party information is not protected under administrative subpoenas Moore in 2009 (Trevor Moore, “Privacy vs. the Public Good: National Security Letters and the Fourth Amendment”, BYU PreLaw Review Vol. 23, 2009, https://ojs.lib.byu.edu/spc/index.php/PrelawReview/article/viewFile/13600/13478) Because NSLs deal exclusively with information which is kept in the hands of third parties, the question that must be answered is whether or not the Fourth Amendment protects information revealed to third parties. In general, access to information that is protected by statute but not by the Fourth Amendment is obtained through a subpoena. Many agencies have the power to issue administrative subpoenas. An administrative subpoena is an official order compelling an individual to provide a government administrative agency with information. In contrast, to obtain information or items protected by the Fourth Amendment, the government must have a warrant signed by a judge allowing them limited access to an individual's papers and belongings. Warrants and subpoenas are similar in the fact that they allow the government to gain access to private information. A major difference between the two is that a warrant is obtained through judicial authority and grants access to information protected by the Fourth Amendment, whereas subpoenas do not need judicial authority, and they request information not protected by the Fourth Amendment. For example, the FBI uses NSLs to request copies of transactional and personal records from communications providers, financial institutions, consumer credit agencies, and travel agencies. 8 These letters require businesses to supply the FBI with transaction information pertaining to persons involved in a current investigation. Showing that information held by third parties is not protected by the Fourth Amendment will logically show that NSLs do not violate Fourth Amendment protection, making NSLs comparable to administrative subpoenas in function. With present national security threats, the need for increased intelligence by law enforcement is greater than it has ever been. To prevent future attacks, government agencies must have quick access to information that so that criminals may be apprehended before they strike. NSLs aid law enforcement agencies by providing them with information that can lead to sufficient evidence for a search warrant. Legal precedent has shown that information held by third parties is not protected under the Fourth Amendment. Furthermore, subjecting NSLs to Justice Harlan's test shows again that the kind of information requested by NSLs is not included within the scope of the Fourth Amendment. Determining that NSLs do not violate Fourth Amendment rights leads us to treat NSLs no differently than other administrative subpoenas. Treating NSLs as administrative subpoenas demonstrates that there is adequate oversight involved for the type of information being requested. The use of NSLs by government agencies is in accordance with the laws of the United States. National Security Turn NSL Comparatively better NSL’s are better than alternatives OIG in 2014 (Office of the Inspector General. Oversight and Review Division “A Review of the Federal Bureau of Investigation’s Use of National Security Letters: Assessment of Progress in Implementing Recommendations and Examination of Use in 2007 through 2009” US Department of Justice. August 2014) FBI personnel told us that in cases that have a criminal nexus the FBI can use a grand jury subpoena to obtain information that is substantially similar to the information obtained through an NSL. [Omitted text]. Personnel identified other alternatives for text]. They told us that these alternatives were less effective than NSLs because the techniques require more resources and can produce information that is not as complete or reliable as NSL-derived information. They also stated that these techniques create a greater risk of premature exposure of the investigation. Two FBI employees also said that [Omitted text] may unnecessarily intrude on a potentially innocent person's privacy and can harm his or her reputation in the community. We interviewed two field supervisors on cyberterrorism squads who told us that in cyber intrusion investigations there is often no alternative to an NSL because the only lead in the case is [Omitted text] those instances, [Omitted text] can only be accomplished with [Omitted text]. determining [Omitted NSL key to National Security NSLs only affect a small amount of people but are integral to national security Hinnen in 2011 (Todd Hinnen “Statement of Todd Hinnen, Acting Assistant Attorney General for National Security, Before the House Judiciary Subcommittee on Crime, Terrorism and Homeland Security” March 30, 2011 http://www.justice.gov/nsd/justice-news-1) I would like to conclude my remarks by emphasizing how important NSLs are to our national security. NSLs are an indispensable investigative tool, and have often been described as the “building blocks” of national security investigations. NSLs contribute significantly to the FBI’s ability to carry out its national security responsibilities by directly supporting its counterterrorism, counterintelligence, and intelligence missions. As reported in the Department’s last annual report on NSL usage, excluding requests for subscriber information (i.e., an NSL issued to ascertain the subscriber associated with a particular telephone or email address), in 2009, the FBI made 14,788 NSL requests for information concerning 6,114 different United States persons. In 2008, the FBI made 24,744 NSL requests (excluding requests for subscriber information) pertaining to 7,225 United States persons. These numbers reflect the importance of these tools to the FBI, but also reflect the fact that the FBI uses NSLs to obtain information regarding a very small portion of the American population. NSLs are issued by the FBI in national security cases for a variety of investigative reasons. They are used in counterintelligence cases in which individuals are suspected of attempting to steal our nation’s secrets, including espionage cases. They are used extensively in terrorism cases to help correctly identify international terrorists and thwart future attacks in the United States. As an investigative tool, NSLs are integral to determining whether, how, and by whom our nation is being put at risk. So, while I cannot discuss specific investigative techniques that were used in specific investigations, NSLs were used in most cases, if not every major case, in which the FBI has disrupted terrorist plots against the homeland or identified spies working to obtain classified United States Government information. These tools have helped keep our nation safe, while safeguarding the civil liberties of all Americans. NSLs are key to safety and security – people falsely demonize domestic surveillance programs Carafono in 2007 (James Jay Carafono (PhD, Vice President for the Kathryn and Shelby Cullom Davis Institute for National Security and Foreign Policy), January 18, 2007, “Don’t demonize security”, http://www.heritage.org/research/commentary/2007/01/dont-demonize-security) First, find a legitimate domestic surveillance program. Make sure it's one most Americans ignore - the more obscure, the better. It doesn't matter if the courts have ruled it constitutional. It doesn't matter if it helps fight crime or protect national security. Next, find an "expert" to denounce the program as an unnecessary expansion of executive authority. Rail about the potential for abuse (even when there's no evidence of actual abuse). Argue that the program could be a threat, even if it hasn't, in fact, been misused. Finally, stimulate the "Luddite response" - a fear of technology. Rant about how the information age is destroying any hope of privacy. More information and technology equals power. And with more power comes more abuse. Combining these ingredients is guaranteed to shock sensibilities and spark congressional hearings. It's been done many times, starting with the tools authorized in the Patriot Act to fight terrorism, like delayed-notification warrants. U.S. military Here's the recipe for a scary, post-9/11 news story about liberties vs. security: domestic investigations are the latest intelligence and law enforcement tool to receive the treatment. A spate of recent news reports revealed that the armed forces use "national security" letters to request business records, such as phone and bank data. It sounds scary, but it shouldn't. The military has a legitimate, limited mission to conduct intelligence inside the United States. It is written into law and funded by Congress. National security letters are perfectly legal, and the Defense Department is authorized to issue them. Requesting business records is a common intelligence and law enforcement practice and does not in many cases require a warrant. Finally, there is a domestic security threat to worry about. On 9/11, there was an attack on American soil, and others have been plotted since then. Keeping America safe, free and prosperous requires both liberty and order. Protecting the safety and freedom of Americans is not served well by simply demonizing security NSL key to FISA NSLs are necessary to support FISA applications Wells in 2015 (Desirae L. Wells, “NATIONAL SECURITY LETTERS: WHY REFORM IS NECESSARY”, LexisNexis.com, Yeshiva University 2012, 18 pgs., Database, 6/28/15, http://www.lexisnexis.com.proxy.library.umkc.edu/hottopics/lnacademic/) The passage of the Patriot Act caused NSLs to be the subject of much debate and controversy. There are two main opposing viewpoints. The chief viewpoint of advocates of NSLs, mainly the FBI, is that NSLs are a necessary and highly effective counter terrorism and counterintelligence tool needed in this Post 9/11 era. As outlined in Part I, NSLs have a long history and in fact predate 9/11. Historically, the [*222] scope of NSLs was limited to mundane business records, n23 and the Supreme Court in Smith v. Maryland has already stated that federal authorities do not need a warrant for these records since because no reasonable expectation of privacy may exist in records that have been exposed to third parties. n24 They also contend that evidence is routinely obtained in police and grand jury investigations with no signoffs from high level officials who could be held accountable, whereas in NSLs you at least have an FBI official formally affirming the letter's necessity. NSLs, it is argued, are the necessary first step to support Foreign Intelligence Surveillance Act applications for electronic surveillance, physical searches or pen registers/trap and trace orders n25. Similarly, often the target of an NSL is not necessarily the main target of an investigation and an NSL thus serves as a key tool in allowing the FBI to follow leads. n26 In sum, supporters argue that NSLs are a vital tool in the ongoing effort to keep Americans safe. Democracy Alt cause to Demo Collapse Inequality makes democratic collapse inevitable Peebles ‘14. [Graham Peebles, 4/18/14, Counter Punch News, “Inequality and the Inevitable Collapse] http://www.counterpunch.org/2014/04/18/inequality-and-the-inevitable-collapse/ Inequality has far-reaching social effects and erodes democracy. Grossly unequal societies have greater levels of alcohol and drug addiction, more crime, lower mortality rates, higher child pregnancies and lower literacy levels than less unequal countries. Political influence/control is an added bonus for the rich; as for the rest, well they get to vote, but have little or no influence over government policy and overwhelmingly distrust politicians. With dire poverty, as experienced by the 3.5 billion living somehow, goes lack of education, vulnerability and exploitation, all of which discolours democracy. Inequality is the plague of our times, a divisive epidemic caused by the unjust economic system – ‘Neo-Liberalism’, or market fundamentalism – which saturates the world. A system which, Noam Chomsky says, is “so dysfunctional that it cannot put eager hands to needed work,” as would happen “if the economy were designed to serve human need rather than create wealth beyond avarice for the privileged few.” It’s hard, he says, “to think of a more serious indictment of a socio-economic system.” The ‘dysfunctional’ socially unjust system has facilitated “very high concentrations of wealth, and with it political power, which yields [favourably skewed] legislation, which drives the cycle forward.” Based as it is on competition, this ‘dysfunctional’ model breeds insecurity and stress, encourages separation and division leading to social tension and a lack of trust. A recent survey found that in America – where inequality is ‘off the scale’ – only 15% admitted trusting their neighbours, whereas in more equitable societies the number is closer to 60%. At: Exec Power u/mines Demo Executive overreach/power in the fight against terrorism is key/constitiutional- Article II does not clarify Edelson in 2013 (Chris, “Emergency Presidential Power: From The Drafting Of The Constitution To The War on Terror,” by Chris Edelson, University of Wisconsin Press) Americans understandably think of the U.S. Constitution as a document that defines (among other things) the scope of presidential power in war and peace, calm and crisis. If you follow political debate about constitutional interpretation, which focuses on distinctions between “activism” and “strict construction,” the process of defining presidential power would seem easy: just turn to Article II of the Constitution, which addresses executive power, and see what it has to say. Reality, it turns out, is more complicated. As one scholar notes, “the text and history of Article II fail to offer decisive guidance regarding presidential power.” When presidents want to take action, it is not always clear whether the Constitution provides the authority they desire. Some presidents are reluctant to act without clear constitutional or statutory authorization, but most presidents have not viewed their authority as restricted to the plain text of the Constitution or the explicit approval of Congress. When asked to review presidential actions, the Supreme Court has been unable to develop a “magical formula” to define the scope and limits of presidential authority. One area of special difficulty is the question of presidential authority to respond to national security threats: what powers do presidents have to respond to emergencies like war, rebellion, or the threat of terrorist attack? Article II makes no express provision for such emergency presidential power—in fact, what emergency power the Constitution does provide seems to be assigned to Congress by Article I. Presidents may and often do cite congressional authority as a basis for responding to threats to national security. When congressional authority is lacking, however, presidents often claim the right to take unilateral action. During crises, “presidents generally have not hesitated to do whatever, in their view, needed to be done.” Faced with a document that does not provide clear instructions and faced with crises that demand or seem to demand immediate action, presidents have found ways to justify actions not expressly authorized by the Constitution or statute. The central problem this book addresses is this: given that the Constitution does not expressly provide for emergency presidential power in the absence of congressional authorization but presidents, in practice, do independently exercise such power, how do we define its scope and limits? In answering this question, I consider actions taken by each branch of the federal government. Presidents often do whatever they believe is necessary, but Congress and the courts do not always agree with them. All three branches of the federal government can and do play a role in defining emergency power. I will frequently use excerpts from Supreme Court opinions as guideposts for assessing the nature of emergency power—not because the Supreme Court necessarily has the last word on the matter but because the court has, since Marbury v. Madison, identified its duty as “say[ing] what the law is.”6 Court opinions highlight some of the central issues involved in assessing emergency presidential power, and they tell us what the justices think about these issues—including when the court thinks presidents have acted appropriately and when presidents have exceeded their authority. That does not mean the court always provides the right answers or even asks the right questions, but these opinions offer a useful window into the ongoing debate and discussion. As noted and as is discussed in detail throughout this book, presidents have historically exercised power beyond what is expressly assigned to the executive branch by the text of the Constitution—often to the satisfaction of Congress, the courts, and the people. That does not mean, however, that all justifications for such actions are equally valid. For instance, presidents, members of Congress, judges, and scholars have recognized implied emergency presidential power that is linked to express powers and limited by contrary provisions of the Constitution. On the other hand, arguments for inherent executive power, unmoored from and unlimited by the Constitution, are far more controversial. This book aims to consider the strengths and weaknesses of different justifications offered for presidential power during war or other national security crises. I refer to this as emergency presidential power because presidents often assert authority to take unilateral action when necessary to protect national security, especially when there is no time for deliberation and/or, in their view, Congress is not equipped to respond. Most observers agree that the president has at least some unilateral ability to take action necessary to respond to crisis, even though the Constitution is silent on the matter. However, there is disagreement as to the scope of such power. Advocates for broad presidential power argue that the president has “plenary” or absolute power when it comes to defending the nation—that decisions in this context are for the president alone to make. Others conclude that presidents can initially act independently when they believe it is necessary to defend the nation; however, their actions must be retroactively approved by Congress and are subject to review by the courts. Some arguments, of course, are more persuasive than others, and one’s conclusion about which argument is best may depend on constitutional text, court precedent, congressional action, and past presidential practice, as well as context— the specific reason why presidential authority is claimed in different cases. This book presents and explains the various arguments offered for specific presidential actions while offering different ways to consider the questions at stake but ultimately leaves it to you to decide which arguments are best and how emergency presidential power should be defined. One may reasonably ask if, in the end, presidents do whatever they believe is necessary, why it matters how they justify their actions. First, presidents may act unilaterally, but, unless they achieve permanent dictatorial power, ultimately they must persuade others—Congress, the courts, the press, the people—that their actions are justified. As we will see, presidents have sometimes been able to do so, but not always. The justifications presidents offer for their actions are also important because they may be cited as precedent in the future. Lincoln’s decision to order a naval blockade of the Confederacy is cited as support for broad presidential authority with regard to deployment of the military in the context of the war on terror. Franklin D. Roosevelt’s decision to try captured Nazi saboteurs before a military tribunal is improperly cited as precedent for the decision to do the same with suspected terrorists. The challenge for the Framers of the Constitution and for Americans today is to balance competing considerations. After the failure of the Articles of Confederation, which did not provide for an executive, the Framers realized it was necessary to create the presidency. The new president would have to have enough power to carry out the responsibilities assigned to the office and to resist encroachment from the other branches of the federal government, but there would also have to be limits on presidential power. The president would not be a king, as Alexander Hamilton explained in the Federalist Papers.10 Unlike the eighteenth-century British monarch, the American president would share war power and power over foreign affairs with Congress, as part of the system of checks and balances the Framers developed. In the twenty-first century, this balancing continues. As Supreme Court Justice David Souter put it, “the Constitution embodies the desire of the American people, like most people, to have things both ways. We want order and security, and we want liberty.” Defining the scope and limits of emergency presidential power requires Americans to balance liberty and security, to make sure the president has enough authority to deal with threats to national security without taking on so much power that the system of checks and balances fails and liberty suffers. Some of the discussion so far may seem fairly abstract, but the reward of unraveling the mysteries of emergency presidential power is that we can begin to arrive at answers—or at least possible answers—to specific questions we face today. Can the president decide to hold suspected terrorists indefinitely without charges? If suspected terrorists are prosecuted, can presidents order their trial before military tribunals instead of civilian courts? Was the Bush administration justified in authorizing waterboarding? If the president decides that the best way to prevent future terrorist attacks is by secretly listening to millions of telephone conversations and reading millions of e-mails, can he (or, at some point, she) order these actions? Was President Obama justified in authorizing the killing, without trial or hearing, of a U.S. citizen who was a suspected terrorist? This book addresses each of these questions. Since the question of emergency presidential power begins with the Constitution itself, we start by considering how the Framers understood that power, to the extent that such inquiry produces useful guidance. We then examine how presidents have actually exercised and justified emergency power and what role Congress and the Supreme Court have played in defining such power. As we will see, emergency presidential power is not a new idea. However, the way in which it is used in the twenty-first century, especially in the context of the war on terror, presents new challenges. If, in the past, one way to limit presidential power was by publicly debating the justifications presidents gave for using emergency power, what happens when power is exercised in secret, with justifications initially provided only in classified memoranda? If one way to limit emergency power is to require that it be temporary, that it be used only for as long as a particular crisis demands, what happens when crisis is open ended, when Americans find themselves in a war against terrorism that has no clear end point? Defining the scope and limits of emergency presidential power becomes especially important, though also more difficult. Although we begin by considering how power has been defined and used historically, the ultimate goal is to develop a framework for emergency presidential power that meets the challenges of our time. The President has full power over National Security- Keeps checks and balances Meese III in 2011 (Edwin Meese III, ambassador for Heritage, “Who Is Responsible for America’s Security?”, 7/19/11, http://www.heritage.org/research/reports/2011/08/who-is-responsible-foramerica-s-security, 7/1/15) With the memory of the War for Independence still fresh and the fledging nation facing constant threat from foreign powers and Indian tribes, the Framers saw national security as the highest calling of the federal government that they would create.[1] The Articles of Confederation had proved inadequate as they created a weak and ineffectual government. The world’s naval powers were fearsome but despotic, unworthy examples for this great experiment in freedom and democratic self-rule. So the Framers turned to the lessons of history and reason. The balance they struck remains, like our Constitution, unique. The Constitution vests the President of the United States with the full “executive power” of the federal government. He is named the “commander in chief of the Army and Navy of the United States, and of the militia of the several states, when called into the actual service of the United States.” So does the Constitution place paramount authority for national security in a single executive. At: Democratic Peace Theory Democratic peace theory is a myth- it’s the spread of social capitalism that generates the conditions for stability Mousseau, Michael in 2012 The Democratic Peace Unraveled: It’ s the Economy, THE DEMOCRATIC PEACE UNRAVELED: IT’S THE ECONOMY, http://www.econstor.eu/bitstream/10419/108587/1/erf_wp_1207.pdf This article has sought to address the controversy of whether the capitalist peace can explain the democratic peace. Whether or not a capitalist peace can account for the democratic peace depends on whether capitalism can account for democracy as well as peace (Blalock 1979:468474; Ray 2003). There are two kinds of capitalist peace theories: free-market models link smaller government with peace (Weede 1996; Gartzke et al. 2001; McDonald 2009); the social-market model links impersonal economy with peace (Mousseau 2000). Among these, only the socialmarket model has been both theorized to account for both democracy and peace (ibid.) and shown to account for the democratic peace (Mousseau 2009; Choi 2011; Dafoe 2011). Some have pointed out several ways that the results of Mousseau (2009) may not pose a challenge to the democratic peace, and this article was aimed at examining these arguments. First, a new continuous measure of impersonal economy was introduced, solving the perfect prediction problem that results from the binary measure for social-market capitalism in analyses of fatal disputes. Second, all militarized conflicts, not just fatal ones, were examined in crucial tests, to see if the new binary maximum measure of democracy (Polity +10), put forward by Dafoe (2011), can save the democratic peace hypothesis. Third, tests included control for differences along the democracy-autocracy dimension. Finally, the robustness of the social-market economic peace was examined with consideration of measures of free-market capitalism. The results for democracy are clear and clean: once ―capitalist‖ impersonal economy is taken into account, there is no evidence of causation from democracy to peace; it is far more likely that impersonal economy accounts for both democracy and peace. The use of the highest +10 measure of democracy does not save the democratic peace hypothesis; and democracy remains insignificant with consideration of regime differences. All data and measures are conventional to studies of interstate conflict processes, and the most likely cause of democracy’s insignificance is consideration of impersonal economy, since key models are identical in every other way. Nor can the social-market peace be explained by trade or wealth; and the free-market theories of capitalist peace, size of public sector (McDonald 2009) and capital openness (Gartzke et al. 2001; Gartzke 2007), do not survive rigorous testing or the consideration of impersonal economy at standard levels of significance. The results of this study must be made clear: there is no scientific justification for inferring or this study any evidence, direct or indirect, of causation from democracy to peace. Furthermore, democracy is not merely insignificant: standard measures of democracy were shown to have positive impacts on the odds of militarized conflict in every model that controlled for contract flows, with the positive implying from impact of binary (Polity >+6) democracy even reaching significance when regime difference is considered. Deference/SOP Answers Judicial Deference Good The Judicial Branch agrees to the notion of executive overreach and its necessity in national security instances Luban in 2008 (David is a professor of Law and Philosophy at the University of Chicago; “On the Commander-In-Chief Power” Published: 2008 PG: 478-479; http://scholarship.law.georgetown.edu/facpub/598/) Perhaps the best-known example of the former argument appeared in the 2002 torture memo by the Justice Department’s Office of Legal Counsel (“OLC”), leaked in 2004 just weeks after Abu Ghraib. In OLC’s words: Any effort by Congress to regulate the interrogation of battlefield combatants would violate the Constitution’s sole vesting of the Commander-in-Chief authority in the President. . . . Congress can no more interfere with the President’s conduct of the interrogation of enemy combatants than it can dictate strategic or tactical decisions on the battlefield. Thus, federal statutes making torture a felony would be unconstitutional if applied to interrogations authorized by the commander in chief. Although the torture memo was withdrawn in the face of scandal, the opinion OLC substituted for it carefully refrained from commenting on its override argument, neither endorsing it nor repudiating it. But an earlier OLC opinion from September 25, 2001, which was never withdrawn, also asserts that the president has “plenary constitutional power to take such military actions as he deems necessary and appropriate . . . .” Commenting on the War Powers Resolution and Joint Resolution passed by Congress in the wake of 9/11, that OLC opinion added: “Neither statute, however, can place any limits on the President’s determinations as to any terrorist threat, the amount of military force to be used in response, or the method, timing, and nature of the response. These decisions, under our Constitution, are for the President alone to make.” Thus, the commander in chief override argument still appears to be the Justice Department’s official position even after withdrawing the torture memo. Its theory appears to underlie signing statements the president has attached to legislation, declaring that he will construe provisions consistent with his constitutional authority as commander in chief, by which he evidently means that he reserves the right to disregard restrictions that in his opinion impinge on his commander in chief authority. Justices must respect and give precedent to the executive branch during times of national security especially against terrorist groups Blomquist in 2010 (Robert F. is a professor of law; “The Jurisprudence of American National Security” Volume 44 Number 3, Published Spring 2010; http://scholar.valpo.edu/vulr/vol44/iss3/6/) Turning to how the Supreme Court should view and interpret American presidential measures to oversee national security law and policy, our Justices should consider a number of important points. First, given the robust text, tradition, intellectual history, and evolution of the institution of the POTUS as the American national security sentinel, and the unprecedented dangers to the United States national security after 9/11, national security presiprudence should be accorded wide latitude by the Court in the adjustment (and tradeoffs) of trading liberty and security. Second, Justices should be aware that different presidents institute changes in national security presiprudence given their unique perspective and knowledge of threats to the Nation. Third, Justices should be restrained in second-guessing the POTUS and his subordinate national security experts concerning both the existence and duration of national security emergencies and necessary measures to rectify them. “During emergencies, the institutional advantages of the executive are enhanced”; moreover, “[b]ecause of the importance of secrecy, speed, and flexibility, courts, which are slow, open, and rigid, have less to contribute to the formulation of national policy than they do during normal times.” Fourth, Supreme Court Justices, of course, should not give the POTUS a blank check—even during times of claimed national emergency; but, how much deference to be accorded by the Court is “always a hard question” and should be a function of “the scale and type of the emergency.” Fifth, the Court should be extraordinarily deferential to the POTUS and his executive subordinates regarding questions of executive determinations of the international laws of war and military tactics. As cogently explained by Professors Eric Posner and Adrian Vermeule, “the United States should comply with the laws of war in its battle against Al Qaeda”—and I would argue, other lawless terrorist groups like the Taliban—“only to the extent these laws are beneficial to the United States, taking into account the likely response of other states and of al Qaeda and other terrorist organizations,” as determined by the POTUS and his national security executive subordinates. Judicial overview of military operation in order to prevent military adventurism hurts the inherent checks on all branches and downplays the importance of the Executive Branch Sulmasy and Yoo in 2007 (John Yoo and Sulmasy are both professors of law; “Katz and the War on Terrorism”, 41 U.C. Davis L. Rev. 1219 2007, Page: 1252-1254 http://scholarship.law.berkeley.edu/facpubs/967/) Presidential leadership has always included control over the goals and means of military campaigns. As the Supreme Court has observed, the President has the authority "to employ [the armed forces] in the manner he may deem most effectual to harass and conquer and subdue the enemy. “Lincoln did not seek authorization from Congress over whether to defend Washington, D.C.; FDR did not ask Congress whether he should make the war in Europe a priority over the war in the Pacific; Truman did not seek legislative permission to drop nuclear bombs on Japan. Many of the wars fought since World War I, ranging from Korea to Panama to Kosovo, never received any congressional authorization. While Presidents should not ignore congressional leaders, a wise President, acting within his constitutional authority, will consult with them at the politically appropriate moment. The Constitution does not force the President to get a letter from Congress or seek permission from the judiciary every time he makes an important decision about wartime strategy or tactics. Nor is Congress defenseless. It has total control over funding and the size and equipment of the military. If it does not agree with a war or a strategy, it can cut off funds, reduce the size of units, or refuse to provide material for it.'89 War would be impossible without Congress's cooperation, or at least acquiescence.'9° This is even more true in the age of modern warfare, which requires material, high technology weapons systems, and massive armed forces dependent upon constant congressional budgetary support.'9 Some critics now assert the judiciary ought to review military operations in order to prevent military adventurism, to check the executive, and to foster political consensus. This neglects the need for executive action during time of imminent foreign threat, and downplays the checks inherent in the other branches' administrative impediments, such as delay, inflexibility, and lack of secrecy. World War II demonstrated that unfettered presidential initiative has been critical to the protection of American national security. When Europe plunged into war, Congress enacted a series of Neutrality Acts designed to keep the United States out of the conflict. In 1940 and 1941, FDR recognized that America's security would be threatened by German control of Europe, and he and his advisers gradually attempted to bring the United States to the assistance of Great Britain and the Soviet Union. He was not required, nor was it thought prudent, to seek judicial blessings or congressional authorization when acting to prevent "potential" attacks on the United States. In fact, FDR stretched his authority to cooperate closely with Great Britain in protecting convoys in the North Atlantic, and providing the British with fifty "obsolete" destroyers, among other things. American pressure on Japan to withdraw from China helped trigger the Pacific War, without which American entry into World War II might have been delayed by at least another year, if not longer. Legislative Deference Good Wars unpredictability requires the executive branch, the legislative branch is to slow to respond effectively Sulmasy and Yoo in 2007 (John Yoo and Sulmasy are both professors of law; “Katz and the War on Terrorism”, 41 U.C. Davis L. Rev. 1219 2007, Page: 1234 http://scholarship.law.berkeley.edu/facpubs/967/) War's unpredictability and unique nature demands decisive and often secret action. Philosopher John Locke first observed that a constitution ought to give the foreign affairs power to the executive because foreign threats "are much less capable to be directed by antecedent, standing, positive laws," and the executive can act to protect "security and interest of the public. Legislatures were too slow and their members too numerous to respond effectively to unforeseen situations. As Locke noted, "Many things there are, which the Law can by no means provide for, and those must necessarily be left to the discretion of him, that has the Executive Power in his hands, to be ordered by him, as the public good and advantage shall require...” Executive key- National Defense The Executive Branch is the best at national defense and Katz doesn’t apply nor should it to the Executive branch in times of National security Sulmasy and Yoo in 2007 (John Yoo and Sulmasy are both professors of law; “Katz and the War on Terrorism”, 41 U.C. Davis L. Rev. 1219 2007, Page: 1258 http://scholarship.law.berkeley.edu/facpubs/967/) Katz should remain a vital part of the law enforcement system as a provision of judicial oversight over surveillance activities to detect crime. However, such judicial involvement has not, nor should it, extend to the conduct of surveillance to combat national security threats. Forty years ago, the threats of al Qaeda and international terror were not part of the American consciousness. Unfortunately, since September 11, the United States is now painfully aware that the landscape of national security has changed. The Founders created a flexible executive, embodied in Article II of the Constitution, to respond to just such threats. As Justice White anticipated in Katz, the need for rapid decision-making and intelligence gathering are best employed by the Executive Branch. Applying Katz to anti-terrorism surveillance can do nothing more than hinder, rather than promote, measures necessary to protect the national security of the United States. The executive branch has undisputed say in times of war this includes matters of terrorism and surveillance Sulmasy and Yoo in 2007 (John Yoo and Sulmasy are both professors of law; “Katz and the War on Terrorism”, 41 U.C. Davis L. Rev. 1219 2007, Page: 1246 - 1247 http://scholarship.law.berkeley.edu/facpubs/967/) FISA and the criminal justice warrant system sacrifice speed and breadth of information in favor of individualized suspicion, while providing a path for using evidence in a civilian criminal prosecution. If the President chooses to rely on his constitutional authority alone to conduct warrantless searches, then he should generally only use the information for military purposes. As General Hayden stated in 2005, the primary objective of the NSA program is to "detect and prevent" possible al Qaeda attacks on the United States, whether another attack like September 11, or a bomb in apartment buildings, bridges, transportation hubs such as airports, or a nuclear, biological, or chemical attack. These are not hypotheticals; they are all al Qaeda plots, some of which intelligence and law enforcement agencies have already stopped. The President will want to use such information to deploy military, intelligence, and law enforcement personnel to stop the attack. Intercepting enemy communications has long been part of waging war; indeed, it is critical to victory. Gathering intelligence has long been understood as a legitimate aspect of conducting war. The military cannot successfully attack or defend unless it knows the location of the enemy. America has a long history of conducting intelligence operations to obtain information on the enemy. General George Washington used spies extensively during the Revolutionary War, and as President established a secret fund for spying that existed until the creation of the Central Intelligence Agency ("CIA")."' President Abraham Lincoln personally hired spies during the Civil War, a practice the Supreme Court upheld. In both World Wars I and II, Presidents ordered the interception of electronic communications leaving the United States. Some of America's greatest wartime intelligence successes have involved Signals Intelligence ("SIGINT"), most notably the breaking of Japanese diplomatic and naval codes during World War II, which allowed the U.S. Navy to anticipate the attack on Midway Island. SIGINT is even more important in this war than in wars of the last century. The primary way to stop al Qaeda attacks is to find and stop its operatives by intercepting their electronic communications, entering or leaving the country. As commander-in-chief, the President has the constitutional power and the responsibility to wage war in response to a direct attack against the United States. In the Civil War, President Lincoln undertook several actions: raised an army, withdrew money from the treasury, and launched a blockade on his own authority in response to the Confederate attack on Fort Sumter. Congress and the Supreme Court approved Lincoln's actions ex post. During World War II, the Supreme Court similarly recognized that once war began, the President's authority as commander-in-chief and chief executive gave him the tools necessary to effectively wage war. In the wake of the September 11 attacks, Congress agreed that "the President has authority under the Constitution to take action to deter and prevent acts of international terrorism against the United States," which recognizes the President's authority to use force to respond to al Qaeda, and any powers necessary and proper to that end. Even legal scholars who argue against this historical practice concede that once the United States has been attacked, the President can independently respond with force. The ability to collect intelligence is intrinsic to the use of military force. It is even more so now while fighting al Qaeda, a covert group that relies extensively on electronic communication in and outside of the United States to plan their attacks. It is inconceivable that the Constitution would vest in the President the power of commander-in-chief and chief executive, give him the responsibility to protect the nation from attack, but then disable him by preventing him from gathering intelligence crucial to defeating the enemy. Evidence of the Framers' original understanding of the Constitution is that the government would have complete ability to face a foreign danger. As James Madison wrote in The Federalist, "security against foreign danger is one of the primitive objects of civil society." Therefore, the "powers requisite for attaining it must be effectually confided to the federal councils. “As the Supreme Court declared after World War II, "this grant of war power includes all that is necessary and proper for carrying these powers into execution."' Courts have recognized the executive branches authority to conduct warrantless searches as well as the executive is better suited to protect the nation Sulmasy and Yoo in 2007 (John Yoo and Sulmasy are both professors of law; “Katz and the War on Terrorism”, 41 U.C. Davis L. Rev. 1219 2007, Page: 1239 http://scholarship.law.berkeley.edu/facpubs/967/) In light of FISA's statutory structure, it is clear that both FISA and the Act's amendments are a compromise. Under the current interpretation of the Fourth Amendment, the government can conduct surveillance without a warrant to identify foreign threats to national security. FISA is a compromise in that it requires the executive to go to a court to get a warrant; in the past, the Executive Branch could engage in a search for national security reasons without having to get a judge's permission. Courts have recognized that the Executive Branch has the authority to conduct warrantless searches for foreign intelligence purposes, so long as they are reasonable under the Fourth Amendment. This deferential approach recognizes that because the executive can more fully assess the requirements of national security than can the courts, and because the President has a constitutional duty to protect national security, courts should not attempt to constrain his authority to conduct warrantless intelligence searches. The FISA process is simply a process, agreed upon by the President and Congress, for national security searches, but it is not the constitutional baseline for such a process. Exec Good/Needed Executive power good – Contains many advantages over courts Ku et al in 2006 (Julian, Associate Professor of Law at Hofstra University School of Law, “Hamdan v. Rumsfeld: The Functional Case for Foreign Affairs Deference to the Executive Branch”, Berkeley Law Scholarship Repository, http://scholarship.law.berkeley.edu/cgi/viewcontent.cgi?article=1508&context=facpubs) The doctrines requiring judicial deference to executive interpretations of laws affecting foreign affairs, especially during wartime, have a solid and undisputed formal pedigree. But these doctrines also have a strong functional basis. The executive branch has strong institutional advantages over courts in the interpretation of laws relating to the conduct of war. Courts are poorly positioned, from the standpoint of institutional competence, to resolve ambiguities in statutes, treaties, and customary international law that govern the conduct of national policy in times of war. Courts lack expertise and access to crucial information when acting in these areas. Perhaps most importantly, courts lack the flexibility to adjust or revise decisions when the factual context for its decision has changed. In all of these circumstances, the Executive has greater (although not infallible) abilities to resolve ambiguities in the interpretation of these laws. Deference !- Terror Enemies will exploit the legal system to undermine public support for US war efforts Smith in 2010 (Terence Terrorists employ "lawfare", Harrisburg Conservative Examiner, http://www.examiner.com/article/terrorists-employ-lawfare) In an essay entitled, “Law and Military Interventions: Preserving Humanitarian Values in 21st Century Conflicts," Col. Charles J. Dunlap, USAF has coined the term “lawfare” to describe terrorists’ efforts to use the U.S. legal system against us while waging acts of terror against our citizens. Dunlap wrote his essay in 2001, using examples from the then-ongoing nation-building efforts in the former Yugoslavia, but the intervening decade has, if anything, continued to validate those lessons.¶ Dunlap defines “lawfare” as “"a cynical manipulation of the rule of law and the humanitarian values it represents. Rather than seeking battlefield victories, per se, challengers try to destroy the will to fight by undermining the public support that is indispensable when democracies like the U.S. conduct military interventions." The term “will to fight” is borrowed from the writings of the great 19th century military theoretician Carl von Clausewitz, who identified “centers of gravity” as those elements in the enemy’s organizational structure that can be attacked and exploited to sap their desire to continue the battle and thus be used to defeat them. The American center of gravity, then, is its legal system, which terrorists hope to exploit by forcing the U.S. to conduct show trials that will make at least some segments of our society doubt we should even be fighting this battle.¶ Plan destroys deference in a crucial area – the war on terror demands a strong commander and chief (Luban 08) (DAVID LUBAN, University Professor and Professor of Law and Philosophy, Georgetown University, “ON THE COMMANDER IN CHIEF POWER” SOUTHERN CALIFORNIA LAW REVIEW [Vol. 81:477 2008] http://scholarship.law.georgetown.edu/cgi/viewcontent.cgi?article=1597&context=facpub) These are arguments about the president and the Congress.11 What ¶ about the president and the judiciary? Here, claims about the commander in ¶ chief’s power characteristically assume a different form. They are claims ¶ that courts lack competence to secondguess military commanders, and ¶ therefore courts should defer to wartime decisions by the commander in chief. In this form, the argument played a role in several decisions early in ¶ the war on terror, in which U.S. citizens who had been captured, then ¶ classified by the executive branch as enemy combatants, sought to ¶ challenge their detention. The district court in Padilla v. Bush, like the ¶ circuit court and Supreme Court in Hamdi, deferred to the executive branch ¶ determination that Jose Padilla and Yaser Hamdi were unlawful enemy ¶ combatants, because (in the Supreme Court’s words), “our Constitution ¶ recognizes that core strategic matters of warmaking belong in the hands of ¶ those who are best positioned . . . for making them.”12 In the same way, the ¶ U.S. District Judge determining that John Walker Lindh (a U.S. national ¶ who belonged to the Taliban) was unprotected by the Geneva Conventions ¶ wrote: “It is important to recognize that the deference . . . is appropriately ¶ accorded . . . to the President’s application of the treaty to the facts in issue. ¶ Again, this is warranted given the President’s special competency in, and ¶ constitutional responsibility for . . . the conduct of overseas military ¶ operations.”13¶ And not just overseas military operations, because the Global War on ¶ Terror (“GWOT”) is unlike other wars. We fight it wherever the terrorists ¶ are, and the terrorists might be anywhere. They pick the battlefield, so the ¶ battlefield potentially encompasses the entire Earth. It follows that the ¶ commander in chief power, and the nearly unreviewable authority it ¶ encompasses, knows no geographical limits. For example, Padilla was ¶ arrested in a Chicago airport, yet the government subsequently asserted that ¶ this was not an ordinary criminal arrest of a U.S. citizen in the United ¶ States governed by constitutional criminal procedure.14 It was a wartime ¶ capture of an unlawful enemy combatant who could be held ¶ incommunicado for years in order to interrogate him and render him ¶ militarily harmless. What made it a battlefield capture was a determination ¶ by the commander in chief that Padilla, although a U.S. citizen, was also an ¶ enemy combatant on a military mission.15 Combining the authority of a ¶ battlefield commander with the expansive definition of the battlefield in the ¶ GWOT creates a vast scope of plenary power for the president. All of this ¶ purportedly follows from the constitutional designation of the president as commander in chief, combined with the bitter realities of the GWOT. ¶ Furthermore, the president’s decisions can fall under the commander ¶ in chief power even if they do not look like military decisions. Padilla, for ¶ example, was arrested by law enforcement officials, not captured by the ¶ military, and the conclusion about his enemy combatant status was drawn ¶ by civilian officials in the Pentagon.16 Determining what legal category ¶ applies to Padilla looks like a judicial job, not a military job. However, ¶ Judge Mukasey wrote in Padilla v. Bush that deference to the commander ¶ in chief¶ is due not because judges are not personally able to decide whether facts ¶ have been established by competent evidence, or whether those facts are ¶ sufficient to warrant a particular conclusion by a preponderance of ¶ evidence, or by clear and convincing evidence, or beyond a reasonable ¶ doubt. Indeed, if there is any task suited to what should be the job skills ¶ of judges, deciding such issues is it. Rather, deference is due because of ¶ a principle captured in another “statement of Justice Jackson—that we ¶ decide difficult cases presented to us by virtue of our commissions, not ¶ our competence.”17¶ Current executive power is insufficient in the war on terrorism-Obama should circumvent Congress Benen on 2/13/15 (Steve; in 2009, The Atlantic named Benen one of the top 50 most influential political commentators in the United States. His background includes writing for The American Prospect, the Huffington Post, and The New York Daily News.; “GOP flips the script, endorses executive overreach”; MSNBC; www.msnbc.com/rachel-maddow-show/gop-flips-the-script-endorses-executiveoverreach) The good news is, six months after President Obama launched a military offensive against ISIS targets in the Middle East, Congress is starting to debate the U.S. mission. The bad news is, the debate is off to a ridiculous start. President Barack Obama should be asking for more power to wage war against Islamic State extremists, some Republicans on the U.S. House Foreign Affairs committee said. […] While Republicans have repeatedly accused Obama of executive overreach in areas such as immigration, several lawmakers at the hearing questioned why he wasn’t seeking broader authority this time. You’ve probably heard that the GOP is outraged by the White House’s proposed Authorization for the Use of Military Force (AUMF), but it’s important to understand why. About a year ago, the Republican condemnation of President Obama shifted – “he doesn’t lead enough” was out, “he leads too much” was in. The more Obama’s policy agenda succeeded in practical terms, the more the GOP argued the president is a lawless, out-of-control tyrannical dictator, hell bent on limitless power without regard for the Constitution. This week, however, Republicans are disgusted by Obama’s lack of executive overreach. GOP lawmakers are suddenly convinced the tyrannical dictator needs even more sweeping powers to act unilaterally in matters of life and death. House Speaker John Boehner (R-Ohio), who occasionally pretends to believe his party’s talking points, expressed dismay yesterday that the president’s AUMF would “tie his hands even further.” Congress’ top lawmaker apparently hopes for a more diminished role for Congress. This isn’t so much an example of Republicans temporarily putting aside their principles for the sake of convenience. Rather, it’s fresh evidence that the principles themselves have always been a mirage. Republicans think Obama must stop acting like a dictator and start working with Congress as the Constitution intended – unless we’re talking about wars, in which case Obama should go ahead and circumvent Congress as much as possible. Republicans think higher deficits are an economic scourge – unless deficit financing advances conservative policy goals, in which case budget shortfalls are better left ignored. Republicans think government spending is inherently wasteful and counter-productive – unless the investments are directed at their state and/or their policy priorities, in which case government spending is great. Republicans think the big federal government shouldn’t interfere with local decision making – unless the residents of the District of Columbia make a decision the right disagrees with. Republicans think Congress should take a leading role in economic policy – unless we’re talking about trade authority, in which case it’s time to curtail Congress’ influence and empower the lawless White House to do as it pleases. We’re talking about leaders of principle – weak, malleable, and ultimately hollow principles. The point, of course, is that Republican principles aren’t to be taken seriously. Indeed, Republicans don’t take them seriously. When Obama takes executive action on immigration and the GOP goes berserk, it has nothing to do with “overreach” and everything to do with Republican opposition to immigration. The same can be said for executive actions on the minimum wage. And health care. And the environment. And on and on. Fealty to separation of powers and checks and balances is nice, but GOP lawmakers have made clear that when it comes to the issues they care about, sweeping, unilateral actions from the White House are just fine. And so, as the debate over authorizing the mission against ISIS continues, expect to see congressional Republicans stress one point above all others: extending as much unilateral power as possible to the executive, the usual anti-Obama talking points notwithstanding. Exec Good- War Executive branch key for action in international conflict Gonzales in 2015 (Alberto, Former Counsel to the President and the United States Attorney General under the George W. Bush Administration, “ADVISING THE PRESIDENT: THE GROWING SCOPE OF EXECUTIVE POWER TO PROTECT AMERICA”, Harvard Journal of Law and Public Policy, http://web.b.ebscohost.com.proxy.library.umkc.edu/ehost/pdfviewer/pdfviewer?sid=f2b846ca-ef7d4681-867e-4479b4210cf0%40sessionmgr112&vid=9&hid=128) When the Framers drafted the Constitution, the most dangerous threats were crude cannons and muskets. The initial balance between executive accountability and flexibility was created in this milieu.17 The world has changed since then, as has the magnitude of the threats to U.S. interests. Based upon my experiences and study, I believe the Framers intended for the executive branch to be able to act with speed and agility to respond to threats and crises.18 Today the ability to act rapidly is more necessary than ever. Article I of the Constitution grants Congress power to “provide for the common Defence and general Welfare of the United States;21 . . . declare War, grant Letters of Marque and Reprisal, and make Rules concerning Captures on Land and Water; 22 raise and support Armies;23 . . . provide and maintain a Navy”24 among other specific duties. Article II grants the President the power as the “Commander in Chief of the Army and Navy of the United States, and of the Militia of the several States, when called into the actual Service of the United States.”25 Cases within the highest power are usually decided in favor of the executive, as the President’s constitutional authority is supported statutorily.158 Some may question whether the courts even have the necessary expertise to judge the president’s national security actions. One scholar argues: Courts and commentators have emphasized the lack of judicial competence in evaluating questions about the conduct of war. As compared to courts, the executive branch has more experience and better access to information about war. It also needs to act at times with dispatch, secrecy, and “unity of plan,” all of which may counsel against interference by the courts.166 From this observation, it may be best for the courts to defer to the executive before action is taken. Exec Good- k 2 National Security Executive branch key to assessing national security Ku et al in 2006 (Julian, Associate Professor of Law at Hofstra University School of Law, “Hamdan v. Rumsfeld: The Functional Case for Foreign Affairs Deference to the Executive Branch”, Berkeley Law Scholarship Repository, http://scholarship.law.berkeley.edu/cgi/viewcontent.cgi?article=1508&context=facpubs) By contrast, the executive branch itself collects a wide variety of information through its own institutional experts and a wide global network of contacts without the necessity of strict rules of evidentiary exclusion. While this information may be presented to the executive branch at any time, a court generally cannot account for new information except in the context of a new case." Courts also cannot update statutory mandates to reflect new information, but instead must continue to enforce policies even when they are no longer appropriate. For instance, once the political branches have enacted a statute or approved a treaty, the courts cannot alter or refuse to execute those laws, even if the original circumstances that gave rise to the statute or treaty have changed or even if the national interest would be harmed.72 Indeed, unlike courts, the executive branch is designed to develop specialized competence. In the area of foreign policy, the executive branch is composed of large bureaucracies solely focused on designing and implementing foreign policy. More broadly, the U.S. executive branch, which is largely responsible for directing U.S. state practice with respect to the law of war, is likely to have more expertise, information, and ability when assessing the effect of rejecting or accepting conspiracy as a war crime or the right to be privy to evidence on larger U.S. efforts to develop the law of war. The President is the one to respond to National Security Threats- National Security comes first in order to preserve Liberty Meese III in 2011 (Edwin Meese III, ambassador for Heritage, “Who Is Responsible for America’s Security?”, 7/19/11, http://www.heritage.org/research/reports/2011/08/who-is-responsible-foramerica-s-security, 7/1/15) Though the Framers could never have imagined the events of September 11, 2001, or the terrorist forces that have made America their enemy, they built a republic that could endure and defeat all external threats and prosper. The war on terrorism, being fought against an enemy with few assets and dead aim on soft targets, has only increased the importance of swiftness and secrecy. The President has the power, and bears the responsibility, to make tough decisions at a moment’s notice—whether to trust fresh but uncertain intelligence, bomb an al-Qaeda safe house, target a terrorist for drone attack, or arrest a terror suspect. These decisions are not subject to legislative check or veto. Nor, in an age where a rogue state or stateless terrorist group may threaten the lives of million of Americans, could they be, if the safety of the nation is to be maintained. National security comes first; without it, life and liberty are threatened and happiness is an impossibility. Therefore, as James Madison wrote: “Security against foreign danger is one of the primitive objects of civil society. It is an avowed and essential object of the American Union.” Protecting the nation requires a unity of purpose and faculty, and it cannot be devolved to a committee or Congress. The Framers recognized as much, and their wisdom is our strength. The President, first and foremost, is responsible for ensuring America’s national security. Solvency Rollback bad Reverting to Earlier versions of NSL’s would lead to previous laws that disallowed the recipient the ability to seek advice Doyle in 2011 (Charles Doyle Senior Specialist in American Public Law; National Security Letters: Proposals in the 112th Congress; Congressional Research Service, Published June 30, 2011; http://fas.org/sgp/crs/intel/R41619.pdf) In the USA PATRIOT Improvement and Reauthorization Act, Congress addressed the issue in three ways. First, it amended the federal obstruction of justice statute to outlaw unjustified disclosures. Second, it amended the NSL statutes to make it clear that a recipient remained free to seek the advice of counsel before complying. These amendments, unlike the obstruction of justice amendment, would disappear should the NSL statutes return to their earlier versions. Congress’s third response, however, would mitigate impact of the disappearance. Third, Congress created a nonexpiring statutory section for review of NSLs, 18 U.S.C. 3511. Congressional Oversight Fails Institutional barriers prevent effective congressional oversight- they will continue to defer Carpenter, 2014 Carpenter, Zoe. "Can Congress Oversee the NSA?" The Nation. The Nation, 30 Jan. 2014. Web. 1 July 2015. “The men and women of America’s intelligence agencies are overwhelmingly dedicated professionals,” Ron Wyden said on Wednesday, before proceeding to excoriate their bosses in front of the Senate Intelligence Committee. Addressing Director of Intelligence James Clapper, CIA Director John Brennan and FBI Director James Comey, Wyden continued, “They deserve to have leadership that is trusted by the American people. Unfortunately, that trust has been seriously undermined by senior officials’ reckless reliance on secret interpretations of the law and battered by years of misleading and deceptive statements that senior officials made to the American people. These statements did not protect sources and methods that were useful in fighting terror. Instead, they hid bad policy choices and violation of the liberties of the American people.’ With the future of the surveillance programs disclosed by Edward Snowden still uncertain, the ball is very much in Congress’s court. Specifically, in the Intelligence And Judiciary Committees, which have critical oversight roles over the National Security Agency and others. The stakes are higher than the individual programs revealed by Snowden, however. In question is Congress’s ability to act as an effective watchdog over an expanding national security state. Wednesday’s hearing nicely showcased the two major hurdles to congressional oversight. The first, as Wyden argued, is senior intelligence officials. The second is the congressional committees, which face an institutional mismatch with the intelligence community and whose members often seem more committed to protecting, rather than scrutinizing, the agencies they are tasked with overseeing. First, a brief history. After revelations about abuses by the CIA and other agencies in the 1970s, Congress struck what Stephen Vladeck, a professor of law at American University, calls a “grand bargain,” to accommodate the paradoxical need to submit secret programs to democratic oversight. New legal constraints on intelligence activities would be enforced not in public but instead behind the veil by the intelligence committees and the Foreign Intelligence Surveillance Court (also known as the FISA court). As Colorado Senator Mark Udall said at the Intelligence Committee hearing, “This committee was created to address a severe breach of trust that developed when it was revealed that the CIA was conducting unlawful domestic searches.” The Snowden leaks indicate the bargain has broken down. “In essence, the delicate balance Congress sought to strike thirty-five years ago now appears to be tipped, rather decisively, in favor of the intelligence community,” Vladeck explained in an e-mail. Intelligence officials have done some of that tipping themselves, by withholding information from the public and lawmakers. On Wednesday, Wyden said the committee had been “stonewalled” by intelligence officials; indeed, none of his questions received direct answers, although Wyden did receive promises from officials to get back to him by specific deadlines. Wyden also cited several incidents in which officials had given inaccurate testimony in public hearings. Last March, for example, James Clapper told Wyden that the NSA did “not wittingly” collect data on American citizens, a claim we now know from the Snowden leaks to be false. In some cases, officials may not be telling legislators anything at all. “There are certain things that the committees are simply not going to find out about unless they’re briefed,” said Representative Adam Schiff, a California Democrat on the House Intelligence Committee. According to law, the executive branch must keep the intelligence committees “fully and currently informed” of any intelligence activity, including significant anticipated activity. But recent history suggests that even committee chairs have not been kept abreast. Senator Dianne Feinstein, who chairs the Senate Intelligence Committee and has become one of the NSA’s closest congressional allies, has admitted that her committee “was not satisfactorily informed” about certain surveillance activities, in particular the tapping of German chancellor Angela Merkel’s cell phone. The reauthorization of Section 215 of the Patriot Act, which the NSA says provides legal grounds for collecting Americans’ phone records in bulk, presents another case in which Congress appears to have had insufficient information to determine whether intelligence activities were lawful. In a report released last Friday, the Privacy and Civil Liberties Oversight Board explained that the FISC did not articulate the legal basis for bulk collection until last August—years after Congress extended Section 215 in 2010 and 2011. This indicates that lawmakers may not have been properly informed of how the statute was being applied when they extended it. Ultimately, the board argued that Section 215 is not written in a way that justifies bulk data collection at all, but it said that even if the language were ambiguous, One explanation for is the institutional mismatch between the intelligence community and the congressional committees. “The intelligence committees are small, the staff is small, the agencies themselves are behemoth,” said Schiff. In the House, members are not permitted to have their own staff on the committee, and some have described feeling inadequately prepared to question intelligence officials. “You don’t have any idea what kind of some members of Congress “may have been prohibited from reading” critical documents before voting to maintain Section 215. these gaps things are going on. So you have to start just spitting off random questions: Does the government have a moon base? Does the government have a talking bear? Does the government have a cyborg army?” Representative Justin Amash said in October at a conference hosted by the Cato Institute. The administration says Congress is duly informed, while other lawmakers have suggested it’s their colleagues’ own fault if they aren’t up to speed. Clapper reaffirmed promises of greater transparency on Wednesday, but critics remain skeptical. “I don’t think this culture of misinformation is going to be easily fixed,” Wyden warned. Representative Schiff told me that he expects the mismatch in resources to continue to impact the committees’ oversight ability. “I’d like to see our capacities augmented in the intelligence committee, but at a time of dwindling legislative budgets, I’m not sure whether that will take place,” he said. Congress could reassert some of its own authority by including more members in the group briefed on significant intelligence activity, for example; by shortening the authorization period for laws like the Patriot Act to spur more frequent debate; by imposing a rule of lenity on the FISA court, so that the administration would have to receive congressional approval in ambiguous cases, thus preventing the FISA court from creating its own novel interpretations of law; and by making sure FISA judges hear adversarial opinions from civil liberties and technology experts. Whether Congress has the will to strengthen its own hand is the big question. The fact that the chairman of the House Intelligence Committee, Mike Rogers, believes that “you can’t have your privacy violated if you don’t know your privacy is violated” does not exactly inspire confidence. These questions about oversight can and should be separated from the debate about the legality and effectiveness of individual surveillance programs. “It may well be, at the end of the day, that the programs the committees are overseeing are legal, but meaningful oversight presupposes that the overseers will be the last, not the first, to reach that conclusion,” said Vladeck. The decision about whether the government or anyone else may continue to sweep up and search our phone records is important. Without addressing broader oversight issues, however, we may barely scratch the surface of a much-needed conversation about balance of power in the post-9/11 era Congressional oversight has been counterproductive. Van Wangenen, 2008 James S. "A Review of Congressional Oversight." Central Intelliegence Agency. The CIA, 27 June 2008. Web. 1 July 2015. *Updated in 2008. Originally published in 2007. Permanent, continuing, day-to-day Congressional oversight of the US Intelligence Community (IC) marked its 20th anniversary in May 1996. Two decades earlier, Senate Resolution 400 established the Senate Select Committee on Intelligence (SSCI) following revelations of "intelligence abuses." In July 1997, the SSCI's House counterpart, the House Permanent Select Committee on Intelligence (HPSCI), will celebrate its 20th birthday. During this time, the IC's missions, responsibilities, capabilities, size, and management have experienced dramatic changes. The Congressional oversight committees have played a significant role in shaping these changes and continue to do so. Some individuals within the Community have argued, with a certain amount of justification, that Congressional oversight has been intrusive, meddling, short-sighted, and counterproductive; has involved micromanagement on a grand scale; and has served to drag the IC into the political cockpit of partisan politics from which it had previously been immune. Others tend to view Congressional oversight as being, on balance and after a somewhat rocky start in the late 1970s, a decided plus for the Community by providing loci for Congressional advocacy and support for intelligence and by providing rigorous review and questioning of intelligence activities and budgets. Perhaps, in looking back at what Congressional oversight has and has not been, we will be better able to discern the future of oversight by the Congress. First, it is important to dispel the popular notion that Congressional oversight started with the establishment of the SSCI and the HPSCI. That notion is not accurate. Before their establishment, however, oversight was certainly not intense or much of an inconvenience to the agencies that carried out intelligence activities. The Revolutionary War Experience It is somewhat ironic that at the beginning of the republic, intelligence operations were conducted by the forebearer of today's Congress--the Continental Congress. During the Revolutionary War, the Second Continental Congress not only functioned as the government of the 13 rebellious colonies, but also planned, directed, and carried out intelligence activities in support of the war effort. Secret committees of the Congress were formed for this purpose, and covert actions, use of secret writing, codes and ciphers, protection of sources, compartmentation, propaganda, and deception all were in the "bag of tricks" used by these "legislative intelligence officers." (Thomas Paine, the author of Common Sense, was fired from the staff of a secret committee for leaking information on France's covert assistance to the colonies.) Agents employed by the Continental Congress succeeded in obtaining covert aid for the war effort from France and Spain and, following the Battle of Saratoga, the open entry of those countries into the war against the British. Other agents on the Congressional payroll scoured European capitals for intelligence as well as indications and warning of impending events such as the plan by King George III to send German troops (lumped together by the colonists as "Hessians") to America to put down the rebellion. The Continental Congress was alerted to this plan, and Thomas Jefferson alluded to the use of "Foreign Mercenaries" as part of his indictment of King George contained in the Declaration of Independence. [Top of page] Establishing a Secret Fund At the conclusion of the war, and following a turbulent decade under the weak and ineffective Articles of Confederation, the new United States adopted the Constitution and elected George Washington as its first President. One of the first things he did was to request the Congress to appropriate for his use a "secret fund," contained in the budget of the Department of State and innocuously called the "Contingency Fund for the Conduct of Foreign Intercourse." This fund was a pot of money available to the President for clandestine intelligence purposes. By the third year of Washington's presidency, the fund amounted to 12 percent of the national budget. Expenditure of money from the fund was done on the signature of the President, with no further accounting required. (This practice established the precedent for a similar provision contained in the CIA Act of 1949.) The secret fund was used for numerous intelligence operations by our early presidents, including: Funding negotiations (bribes) with Napoleon Bonaparte to try to get him to coerce Spain into ceding East and West Florida to the United States. Later, when these "negotiations" failed to bear fruit, the fund was used to promote revolution in the Floridas, and this prompted Spain to see the wisdom in such a territorial transaction. Funding the Lewis and Clark and the Zebulon Pike expeditions, which in part were intelligence missions with the goal of entering territories of foreign governments with which the United States was at peace, in order to locate and map their fortifications. President James Madison used the secret fund to enlist gangsters for intelligence purposes. The pirate Jean Laffite and his men were paid to scout, spy, and sometimes fight for Gen. Andrew Jackson during the War of 1812. [Top of page] Early Attempts at Oversight From time to time during the early years of the republic, members of Congress tried to obtain an accounting of expenditures made from the President's secret intelligence fund as well as to effect oversight of the activities it was used to finance. In one debate over this issue, Senator John Forsyth, later to become Secretary of State, declared: The experience of the Articles of Confederation having shown the necessity of secret confidential agencies in foreign countries, very early in the progress of the Federal Government, a fund was set apart, to be expended at the discretion of the President, on his responsibility only, for all purposes to which a secret service fund should or could be applied to the public benefit. For spies, if the gentleman pleases.... Later, some opposition members of Congress suspected President James Polk was using the secret fund for agents provocateurs in Mexico and California for the purpose of fomenting "incidents" designed to provoke a war with Mexico and thus ensure that Texas and California would become part of the United States. A Congressional demand was made that Polk surrender to the Congress all accounts of payments from the fund. Polk refused, stating: The experience of every nation on earth has demonstrated that emergencies may arise in which it becomes absolutely necessary for the public safety or the public good to make expenditures, the very subject of which would be defeated by publicity. In no nation is the application of such funds to be made public. In time of war or impending danger, the situation of the country will make it necessary to employ individuals for the purpose of obtaining information or rendering other important services who could never be prevailed upon to act if they entertained the least apprehension that their names or their agency would in any contingency be revealed. [Top of page] Period of Benign Neglect President Polk's defiant stance regarding Congressional oversight effectively staved off significant oversight by the legislative branch for more than a century. It was not until after World War II and enactment of the National Security Act of 1947 that the Congress again tried to oversee US intelligence activities. With the establishment of the CIA as the nation's first permanent, statutory, and national intelligence entity, each house of the Congress assigned oversight responsibility over this new executive branch capability to its respective Armed Services Committee and Appropriations Defense Subcommittee. In actual practice, awareness of CIA's and other intelligence agencies' activities was limited largely to the chairmen and ranking minority members of those committees/subcommittees. Staff cognizance was generally restricted to one or two senior staff members of each of the oversight bodies whose principal job was to make certain that the needs of the intelligence agencies were included in the annual Defense Department budget. Oversight, such as it was, was typically worked out by the Director of Central Intelligence and a few senior members of the Congress, with little involvement of the Congress as a whole. While occasional proposals were put forth during the 1950s and 1960s to conduct more robust oversight by establishing select intelligence committees, none of these pro posals was ever seriously considered. Most members of Congress tended to agree with the view expressed by Senator Leverett Saltonstall, who stated in 1956: It is not a question of reluctance on the part of CIA officials to speak to us. Instead, it is a question of our reluctance, if you will, to seek information and knowledge on subjects which I personally, as a member of Congress and as a citizen, would rather not have.... Another member commented several years later that: I have found little hesitation on the part of the Congress to support and to finance our intelligence work with all its secrecy. This hands-off view of oversight continued to be the accepted modus operandi of the Congressional oversight bodies for over a quarter of a century following the creation of the CIA in 1947. Congressional historians refer to it as an "era of trust" or as the "period of benign neglect." As the 1970s approached, however, ominous clouds started to appear. [Top of page] Getting Tough By the early years of the 1970s, the unpopular war in Southeast Asia and the unfolding Watergate scandal brought the era of minimal oversight to a screeching halt. The Congress was determined to rein in the Nixon administration and to ascertain the extent to which the nation's intelligence agencies had been involved in questionable, if not outright illegal, activities. A series of troubling revelations started to appear in the press concerning intelligence activities. The dam broke on 22 December 1974, when The New York Times published a lengthy article by Seymour Hersh detailing operations engaged in by the CIA over the years that had been dubbed the "family jewels." Covert action programs involving assassination attempts against foreign leaders and covert attempts to subvert foreign governments were reported for the first time. In addition, the article discussed efforts by intelligence agencies to collect information on the political activities of US citizens. These revelations convinced many Senators and Representatives that the Congress itself had been too lax, trusting, and naive in carrying out its oversight responsibilities. (Many of the so-called family jewels had been briefed to some members on the existing oversight panels, but in the highly charged atmosphere of the Watergate period they tended to opt for selective amnesia when asked if they had known about these activities.) The first legislative response was enactment in 1974 of the Hughes-Ryan Amendment to the Foreign Assistance Act of 1961. This amendment addressed the question of CIA covert actions and prohibited the use of appropriated funds for their conduct unless and until the President "finds" that each such operation is important to the national security and submits this Finding to the appropriate Congressional committees--a total of six committees. (This grew to eight committees after the House and Senate intelligence committees were established.) The following year, Congress actually terminated funding for a covert program--the secret military support of the UNITA faction in the Angolan civil war. In early 1975, additional disclosures surfaced regarding CIA domestic spying operations and the COINTEL program of the FBI to undermine the activities of the civil rights and anti-Vietnam war protest movements. These further revelations convinced the Congress that it could not rely solely on the presidentially chartered Rockefeller Commission to investigate illegal abuses, both foreign and domestic, committed by US intelligence agencies. Each house of the Congress proceeded to establish its own special investigating committee. In the Senate, this committee became known as the Church committee, named for its chairman, Senator Frank Church of Idaho. The House committee was the Pike committee, after its chairman, Representative Otis Pike of New York. During 1975 and the first half of 1976, the country was rocked by an almost daily stream of disclosures from these committees documenting a pattern of misconduct by the nation's intelligence agencies. These disclosures concerned fairly widespread abuse of the civil rights of American citizens; activities that violated applicable laws and executive branch policies; and clandestine operations overseas that seemed to conflict with US values. At the same time, however, these investigations served to educate committee members about the valuable contributions the intelligence agencies had made in protecting national security and about the significant capabilities they possessed. As shocked as these members were over the abuses, they were equally impressed by the abilities of the Intelligence Community (IC) and did not want to advocate any action that would remedy the former but destroy the latter. They did, however, want to establish a mechanism to ensure that henceforth the intelligence agencies would have effective Congressional supervision, accountability, and oversight. Consequently, both the Church and Pike committee final reports (1) recommended the establishment of new, follow-on, permanent committees in their respective houses of Congress to provide continuing oversight and to consider such additional legislation as might be deemed necessary. These recommendations led to the establishment of the SSCI on 19 May 1976 and the HPSCI on 14 July 1977. The HPSCI was established more than a year after the SSCI because the House of Representatives was so disgusted with the leaking of the Pike committee report that it was not certain it wanted a permanent intelligence committee. The first few years of the new oversight committees were somewhat rocky as they fought for turf with more established committees, principally the Armed Services and Appropriations Committees, which had previously been responsible for Congressional oversight of intelligence. They also battled the Carter administration over the issue of charter legislation for each of the intelligence agencies. Essentially, this proposed legislation would have defined in law precisely the mission of each intelligence agency and the activities each could and could not undertake. The executive branch opposed such definitive legislation, and it eventually succeeded in preventing its enactment. In 1978, however, the oversight committees did enact the first Intelligence Authorization Act, which gave them the ultimate oversight hammer--control of the IC's purse strings. [Top of page] Cooperation and Legislation In these early years, the committees slowly distanced themselves from the Church and Pike committees to become Congressional advocates for intelligence. The Soviet invasion of Afghanistan and the Iranian seizure of American hostages in Tehran helped persuade the public and the Congress that too tight a rein on the intelligence agencies could be disastrous. As a result of this changed outlook, the proposals for intelligence charters died. Congressional oversight, following the landslide victory of Ronald Reagan in the election of 1980, changed gears from trying to control the intelligence agencies to seeking to assist them in carrying out their responsibilities. Congressional oversight, which had gone from benign neglect in the 1950s, 1960s, and early 1970s to oversight based on suspicion, doubt, and micromanagement in the late 1970s, entered an era of cooperation in the 1980s. In fairly rapid succession, the oversight committees either drafted or assisted other Congressional committees with concurrent jurisdiction in drafting a series of legislative initiatives which, upon becoming law, proved to be of great assistance to the IC. First came the Foreign Intelligence Surveillance Act, which requires that a court order be obtained from a special court established by the Act for all electronic surveillance for intelligence purposes within the United States. (In 1994, this Act was expanded to impose the same court order procedure for physical surveillance for intelligence purposes.) Next came the Classified Information Procedure Act, which established statutory procedures for the handling of classified information in Federal criminal proceedings. The Intelligence Oversight Act of 1980 amended the Hughes-Ryan Amendment to require notice of covert actions only to the two intelligence committees; the requirement to notify six other committees was eliminated. In 1982, the Intelligence Identities Protection Act became law, making it a crime to reveal the identity of intelligence agents. This was followed by the enactment in 1984 of the CIA Information Act, which exempted certain CIA operational files from requirements of the Freedom of Information Act. [Top of page] Renewed Tension The spirit of cooperation between the Congressional oversight committees and the IC was sorely tested during the first administration of President Ronald Reagan. The oversight committees, particularly the HPSCI, became increasingly alarmed over the role US intelligence agencies were playing in the implementation of the administration's Central American policy. The issue of greatest concern was the CIA's support to the Contra rebels in Nicaragua. Ultimately, a series of funding restrictions were enacted (the Boland amendments) that put limits on aid to the Contras. The second Reagan administration produced the so-called Iran-Contra affair, which the oversight committees viewed as the most serious breakdown of the trust between the executive branch and the Congress since the oversight committees were established. In late 1986, the committees learned that a covert action Finding had been approved 10 months earlier authorizing arms sales to Iran in an effort to secure the release of Americans being held hostage in Lebanon. This Finding had specifically ordered that the oversight committees not be notified. It was then revealed that proceeds from the arms sales were used to provide assistance to the Contras that appeared to violate the Boland amendments. During the course of their investigations, the committees learned that some administration officials and IC personnel had considered the idea of using excess funds from the Iranian arms sales to fund covert action programs, thus completely avoiding the Congressional oversight process. A special prosecutor was appointed to investigate violations of applicable laws, and the oversight committees tried to enact legislation to force the President to notify the committees of all covert actions within 48 hours. Several legislative attempts were made to achieve this, and, in 1990, such a provision was included in the Intelligence Authorization Bill for fiscal year 1991. President Bush vetoed the bill, principally because it contained this provision. The committees were unable to secure a veto override, and they ended the dispute by agreeing to accept notification "in a timely fashion." But the issue remains far from resolved, and some future incident could easily revive it. [Top of page] Reorganization In January 1990, the chairmen of both intelligence oversight committees introduced far-reaching bills to reorganize the IC. During the first half of 1992, the two committees held extensive public hearings on these proposals. By fall, and after several months of negotiations with the Bush administration, the committees attached "The IntelligenceOrganization Act of 1992" to the fiscal year 1992 Intelligence Authorization Act. This new legislation did not represent a radical departure from the status quo. Essentially, it merely enshrined into law what Director of Central Intelligence (DCI) Robert Gates had already accomplished in restructuring the IC. It did, however, represent a significant change in the legal framework for US intelligence activities. In amending the National Security Act of 1947, this new statute: Recognized the DCI as the statutory adviser to the National Security Council. Established the National Intelligence Council as the highest authority for developing and publishing intelligence analysis. Gave the DCI responsibility for establishing priorities for US Government intelligence-gathering and for coordinating all HUMINT collection. Gave the DCI approval authority for the budgets of the intelligence agencies. Defined the composition of the IC for the first time. The Intelligence Organization Act of 1992 represented the first successful effort by the Congress since the National Security Act of 1947 to enact organizational legislation for the IC. In the Intelligence Authorization Act for fiscal year 1995, the oversight committees included a provision mandating a Presidential Commission to review the roles and missions of US intelligence agencies in the post-Cold War era. This commission, chaired by former Defense Sectretary Les Aspin and, after his death, by another former Defense Secretary, Harold Brown, met its charge of producing a report to the President and the Congress by 1 March 1996. The Congressional oversight committees will play a central role in transforming any of the Commission's recommendations into law in the event it is necessary to amend or replace existing statutes, such as the National Security Act of 1947 and the CIA Act of 1949. [Top of page] The Balance Sheet At this point, no other major legislative initiatives appear to be on the horizon. The two oversight committees continue to exercise oversight and to use their fiscal control to obtain the intelligence agencies' compliance when necessary. Year in and year out, however, the committees authorize and the appropriations committees appropriate the bulk of the budget requested by the DCI. Changes made by the committees really amount to nibbling at the margins. In addition, the oversight committees have not been at all reluctant to increase funding for programs and capabilities they perceive to be important. In several instances over the years, the committees have actually pushed the IC and the administrations into larger and more expensive programs involving technical collection systems, HUMINT, and certain covert action operations. Today, Congressional oversight is accepted and recognized as a fact of life. The top echelons of the IC are replete with former professional staffers of the intelligence committees, and the committees themselves continue to draw staff expertise from the Community. While the Congressional oversight committees are among the harshest critics of the intelligence agencies, they are also their strongest defenders. Congress has repeatedly failed at oversight of the executive branch Strand and Lang, 2011 Strand, Mark, and Tim Lang. "Executive Oversight: Congress’ Oft-Neglected Job." The Sausage Factory. The Congressional Institute, 28 Nov. 2011. Web. 1 July 2015. Congressional oversight is an effort of the legislative branch to examine the activities of the executive branch. This is perhaps the simplest definition of “Congressional oversight”. Walter Oleszek, writing for the Congressional Research Service in Congressional Oversight: An Overview, notes that political scientists have many definitions for the term; however, it’s probably not necessary to delve into the various nuances differentiating them. Whatever your definition, a key point to remember is that this process is one of the most important legislative checks on Presidential power. Members of Congress might investigate the administration for a number of reasons. First and foremost, legislators will exercise oversight to verify whether the President has “[taken] Care that the Laws be faithfully executed”, a task given to him in the Constitution (Article 2, Section 3). In other words, they do this so they can ensure that he is acting in a manner consistent with their commands as manifested in law. A similar reason for investigating the executive branch is to gauge how efficiently and effectively the administration is governing. A President and a department might be gung-ho about a program, but still not run it very well, so the oversight authority can serve as a corrective to poor governance. When the legislature engages in oversight, it says, “We, the Congress, want to know what you, the President, are doing with the money we appropriated to you.” But oversight uncovers more than simply administrative inefficiency. Congress can unearth corruption and criminality when it investigates the executive branch. Whatever the reason, Congressional oversight is a powerful mechanism for fostering good governance by the administration. In the first known example of Congressional oversight, President George Washington was rather indignant about Congress questioning him over his Administration’s treaty negotiations with the Creek Indians. Also, as we note in Surviving Inside Congress, the legislature decided “to flex its oversight muscle early, instructing the executive departments it had just created to report back to it on various matters under the Executive’s jurisdiction”. Since the first Congress, the legislature’s oversight activities have not slackened. Congress has even established two committees to spearhead oversight initiatives. The Committee on Government Oversight and Reform is primarily responsible for this task in the House. The Committee website notes that it does produce bills on certain matters, but that is of secondary importance: “Our primary responsibility…is oversight of virtually everything the government does”. Likewise, its Senate counterpart, the Committee on Homeland Security and Governmental Affairs, lists “studying the efficiency, economy, and effectiveness of all agencies and departments of the Government” as one of its functions. Although these two committees are specifically engaged in oversight activities, every committee in both Chambers may actively review executive activities on the subject matters falling under its jurisdiction. Most major committees even have oversight subcommittees and hire investigative specialists for the task. Government oversight, then, is a responsibility of every Member of Congress in every Congress. If all the Members of Congress did exercise all their oversight prerogatives, committees might be meeting 24 hours a day, seven days a week. That’s an exaggeration perhaps, but Congress has many tools at its disposal, including the power to subpoena witnesses. First and foremost, committees may conduct hearings and investigations, which are opportunities for lawmakers to invite (or compel, via subpoena) administration officials or other witnesses to testify about an issue. The terms hearing and investigation are very similar, but Oleszek notes they are often distinguished by using the former term to denote a meeting that is convened to gauge how well the administration is governing, but the latter has a negative connotation, used when the session is to see whether officials have engaged in illegal activities or whether they were grossly incompetent. In hearings and investigations, Members of Congress take initiative in overseeing the government, but they have also empowered others to take on this role too. For instance, the government has established offices of inspectors general (IGs) in almost 70 federal departments or other bureaus. These officers are charged with investigating their agencies to improve efficiency and uncover criminal activity. Twice a year, the IGs must submit reports, including recommendations, to the heads of their organizations, who must then send them to Congress within a month. If an IG unearths something urgent, he must immediately alert his superior, who must then inform Congress within a week. In addition to these offices’ individual bodies, Congress has also established the Government Accountability Office (GAO), a whole agency dedicated to oversight. Its purpose is to “advise Congress and the heads of executive agencies about ways to make government more efficient, effective, ethical, equitable and responsive”. Committees may request that the GAO undertake an investigation, or legislation may require it; the head of the GAO, the Comptroller General, may also commission such projects. Congress can even compel the executive branch to participate in oversight activities by including, in authorizing legislation, provisions requiring that administration officials report back on progress on implementing the law. Although Congress has established a number of ways to exercise its oversight authority, the legislature sometimes neglects to do so. When one party controls both the White House and one or both Chambers of Congress, legislators from the President’s party are generally less aggressive in fulfilling their supervisory duties – at least in public. Oversight concerns are more likely to be voiced in meetings or by private correspondence. As we note in Surviving Inside Congress, “family fights are not good politics ”. Like many instances of selfinterest, this happens under both parties. Before the 2010 election, the minority staff of the Oversight Committee issued a report, A Constitutional Obligation: Congressional Oversight of the Executive Branch, which extensively criticized Democrats for alleged inaction during the period of united government. “Congress’ chief watchdog committee has failed repeatedly to conduct meaningful and sustained investigations”, they write. On the flip side, the Democrats charged that the Republicans neglected oversight as well. “During the last five years [2001-2006], the Republican-controlled Congress has failed to meet this constitutional oversight responsibility. On issue after issue, the Congress has failed to conduct meaningful investigations of significant allegations of wrongdoing by the Bush Administration”, the Democratic minority staff wrote in a January 2006 report entitled Congressional Oversight of the Bush Administration. Now that we are in a period of divided government, you can bet there will be significant investigations for the remainder of the 112th Congress. Republican Representative Darrell Issa, Chairman of the House Committee on Government Reform, began this session with guns blazing. After the election, there was a flurry of news articles and commentaries on Chairman Issa’s choices of subjects of investigations, but you could argue that he was not being entirely partisan. During an interview on CNN’s State of the Union, Issa argued that providing the President billions of dollars for dispersal, through the Troubled Asset Relief Program (TARP) and the American Recovery and Reinvestment Act of 2009 (the “stimulus bill” passed at the beginning of Obama’s term), has a “corrupting effect” on an administration. In the interview, when challenged that TARP was signed by Republican President George Bush, he maintained that the money should not have been provided to him either. (Chairman Issa voted against the legislation that created TARP.) Further, he also emphasized the role of the Oversight Committee in promoting government efficiency. “But remember the focus of our committee…has been consistently about looking for waste, fraud and abuse. That’s the vast majority of what we do”, he said. Although Chairman Issa described the role of his Committee as ensuring government efficiency, one of his latest initiatives is not obviously related to maximizing the use of taxpayer dollars. Rather, he and his Senate counterparts have been examining the Department of Justice’s Operation Fast and Furious program – a foolhardy attempt on the part of the Obama Administration to discover the location of the leaders of Mexican drug cartels. In this program, government agents allowed firearms to “walk” to Mexico – to cross the southern border illegally – in the hope that they could trace them to drug lords. Not only was the government unable to keep tabs on at least 1,500 of these guns, but at least one was also linked to the death of American border patrol agent Brian Terry, whose murder prompted a public investigation of the program. Gaining intelligence that could lead to the capture and destruction of cartels that bring drugs into the United States and that have wreaked havoc in Mexico is, of course, a worthy goal and a legitimate government function – it’s just that those responsible did not consider the unintended consequences of this operation. At issue in the investigation is who is at fault for the repercussions associated with Operation Fast and Furious. Additionally, a Department of Justice official sent a letter to Senator Chuck Grassley (R-IA) that falsely claimed that the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) attempted to stop illegally purchased guns from being taken to Mexico. Chairman Issa recently sent a letter to the official requiring that he release documentation so Congress might know whether the falsehood was unintentional or not. It’s not clear how the Fast and Furious investigation will turn out. If it uncovers some gross flaw on the part of the administration, it’s a win for democracy. If not, the Obama Administration will accuse the investigators of partisanship – generally the last refuge of any administration being investigated and a common risk when different parties control Congress and the White House. Even if the Administration makes its case, most Americans really wouldn’t want to curtail Congress’ oversight powers, since we expect accountability from the Presidency. Congress, moreover, has been happy to foster executive transparency and efficiency by developing and deploying the various tools at its disposal. Without them, who knows what would happen? That’s the point: We’d have no idea, and that’s how cover-ups happen. Recent congressional oversight has been effective only 20% of the time – the other 80% is just political nonsense and bickering Bassetti, 2015 Bassettii, Victoria. "How to Fix Congressional Oversight." Brennan Center for Justice. The Brennan Center for Justice, 15 Jan. 2015. Web. 1 July 2015. It was an unseasonably warm, overcast March day in 2012, when Energy Secretary Steven Chu exited a House office building after his testimony before the House Oversight and Government Reform Committee. He was probably exhausted as he headed for his car. With three edgy hours of Q&A with Rep. Darrell Issa (R-Calif.) and others finally over, what the Nobel Prize winner did not suspect was that he was being followed stealthily by Republican staffers. They snapped a picture of him getting into an SUV. Then Issa blasted Chu: “#hypocrisy,” he tweeted. Chu, it seemed, was riding in a gas guzzler. Issa was being more than just rude. He was also wrong. Chu’s car was a flex vehicle that also ran on ethanol. And it was the car assigned to him for security reasons. Perhaps Chu should have expected the tail and the personal attack. Earlier that month, Issa had threatened unnecessarily to subpoena him to testify. Issa rarely pretended that his energy hearings were open inquiries to uncover the facts. His Committee, after all, regularly gave its hearings conclusory titles like “How Obama’s Green Energy Agenda is Killing Jobs.” Reserving judgment was not the Committee’s operating procedure. Welcome to 21st century congressional oversight, an unpredictable blend of partisan hackery, prosaic toil, and rare but extraordinary work (the Senate Intelligence Committee’s torture report). As a new Congress dawns, it’s time to gear up for two years of “investigatory-pallooza,” as one former agency head appointed by President Obama called it. It’s inevitable, as we near a presidential election with a partisan split between the legislative and executive branches. It’s also highly doubtful that much of this forthcoming congressional oversight will be productive. Congress far too often engages in oversight that is “lackadaisical” and caught up in the “gotcha cycle,” the former agency head added. "Some hearings are worthwhile and uncover useful information, but others amount to an all-day exercise in congressional preening," said Ron Weich, a former DOJ official and now dean of the University of Baltimore School of Law. Worse, a fair amount of it is "mere harassment," he noted. So much so that another agency chief once turned to one of his aides during an oversight hearing and asked, “Why would anyone take this job again?” One former high-ranking Department of Justice official said that during his time at the agency 20 percent of the oversight was effective; 40 percent was a wash; and 40 percent was political nonsense. The failure of Congress to conduct comprehensive and effective oversight is shameful. With federal government spending at more than 23 percent of the gross domestic product and employing more than 2.5 million people, who doesn’t think that someone needs to mind the store? “Independent review is always valuable,” said Weich, who guided DOJ through the Fast and Furious hearings. Worse, the type of oversight Congress conducts today is often counterproductive. It wastes valuable time, leads to minimal improvements, and inhibits good government. A former Department of Energy official told me that the agency’s staff was amazed at the “intensity of all the investigations” in the first four years of the Obama Administration. They felt beleaguered, even as they continued to do their jobs. But it hurt morale and made people excessively sensitive about internal communications. Congress could conduct oversight seriously if it wanted to. One important first step would be to institutionalize the responsibility and to incentivize a bipartisan approach. Last year, I proposed that each Senate Committee be required to appoint a non-partisan Oversight staff director (with dedicated resources) and that Committee funding be withheld until that appointment was certified by both the Republican and Democratic heads of the Committee. Why is this so important? It’s a corrective to two of the main barriers to good oversight: lack of knowledge and lack of reward. Most members of Congress “actually have no idea how the government functions,” a former high-ranking DOJ official from the Bush Administration said. Moreover, “political actors rarely get remembered for their oversight. They don’t get votes from conducting effective oversight,” he added. Put professional staff and funding in place to help do the job, and we might see a bit of a course correction. But there is more Congress could do. A lot of it involves exercising self-control. There are no rules to enforce good judgment but here’s a quick checklist: Remember the Goal: “The easiest but least useful form of oversight is Monday morning quarterbacking of an agency screw up. It’s hard to look at a tactical failure and decide it will inform substantive changes to the law,” said the former Bush Administration DOJ official. Take Your Time: “It’s never a quick hit. If all you’re doing is sending a letter to send a press release, that’s not good oversight,” Weich said. Instead, when a committee takes its time and really gathers the evidence, subsequent recommendations have legitimacy. Follow the Golden Rule: Do unto others as you would have them do unto you. Most members would “never tolerate routine communications between members and staff being subject to public exposure,” Weich said. When oversight is reduced to an effort to find an ill-considered phrase buried deep in piles of emails, you know effective oversight is not the goal. Avoid the Cliches: You know there’s bad oversight ahead when members and staff start appending “gate” or “scam” to every investigation. It’s even worse when they start asking questions like “What did he know and when did he know it?” Make it Bipartisan: When an inquiry was launched by both a Democrat and a Republican, we “took a good long look”, Weich, the former DOJ official, said. That doesn’t mean that investigations launched with the support of only one party inevitably are going to be partisan attacks. “Partisan things can have a good productive result,” the Republican DOJ source said. But when oversight starts off bi-partisan, the odds of productive hearings increase significantly. As with much in our dysfunctional Congress, most of these solutions can be found only in that ineffable territory we call good judgment. Today, many members of Congress seem afraid to enter that land. Too many partisan forces drive them off. We can only hope that a mild structural reform—the mandate that each committee hire unified, bi-partisan oversight staff—might help nurture a glimmer of wisdom. After all, from small acorns…. Congress is ineffective at oversight of the FBI and CIA- limited expertise and weak budgetary power Zegart, 2011 Amy B. "The Domestic Politics of Irrational Intelligence Oversight." Political Science Quarterly 126.1 (2011): 1-2. Serial Solutions. Web. 1 July 2015. Nine years after September 11, the least-reformed part of America’s intelligence system is not the Central Intelligence Agency (CIA) or the Federal Bureau of Investigation (FBI), but the U.S. Congress. Although the House and Senate enacted sweeping changes to the executive branch, including restructuring intelligence agencies under a new Director of National Intelligence and creating the Department of Homeland Security, Congress has been largely unable to reform itself. In 2004, the 9/11 Commission called congressional oversight “dysfunctional,” and warned that fixing oversight weaknesses would be both essential to American national security and exceedingly difficult to achieve.1One year later, the Commission’s report card gave efforts to improve intelligence oversight a “D.”2 By 2007, Lee Hamilton, who served as the Commission’s Vice Chairman and earlier as Chairman of the House Permanent Select Committee on Intelligence, was angry. Testifying before the Senate Select Committee on Intelligence, he delivered an ominous warning: To me, the strong point simply is that the Senate of the United States and the House of the United States is [sic] not doing its job. And because you’re not doing the job, the country is not as safe as it ought to be….Youʼre dealing here with the national security of the United States, and the Senate and the House ought to have the deep down feeling that weʼve got to get this thing right. Hamiltonʼs words prompted vigorous nods of agreement across the aisle, but never made headlines or produced major changes.4Instead, even the Committee’s own reform centerpiece—consolidating appropriations andauthorization powers—quickly and quietly died. In May 2009, House Speaker Nancy Pelosi declared that oversight had become so feckless, the only way tochange the intelligence policies of the George W. Bush administration was to oust Republicans at the polls .5In January 2010, the Commission on the Prevention of Weapons of Mass Destruction Proliferation and Terrorism con-cluded that congressional intelligence and homeland security reform efforts were still failing.6Although Congress later that year managed to pass anintelligence authorization bill for the first time since 2004, several key over-sight measures were stripped or watered down.This article examines the roots of weak intelligence o versight. SinceSeptember 11, most explanations have focused on the Bush administrationand the exte nt to which executive branch officials withheld information fromCongress about secret and controversial programs such as the National Secu-rity Agencyʼs warrantless wiretapping, the CIAʼs use of harsh interrogationmethods, and the establishment of CIA blac k sites to detain suspected ter-rorists abroad.7Executive branch secrecy, how ever, is not the entire s tory.Congress also has struggled for years to bolster its own intelligence oversightcapabilities, with limited success. What former Senate Intelligence Committee Chairman John D. Rockefeller, IV has called the “long and sordid his-tory” of congressional oversight weaknesses began before September 11 and continues today.8Below, I argue that Congress’s enduring oversight troubles stem largely from two institutional deficiencies: limited expertise and weak budgetary power over the intelligence community. This is no accident. In both areas, electoral incen-tives and internal congressional turf battles have led Congress to tie its ownhands. The result is an intelligence oversight system that is rationally designedto serve the reelection interests of individual legislators and protect congressio-nal committee prerogatives but poorly designed to serve the national interest.Part one discusses the importance of oversight, the elusiveness of a goodworking definition of it, and why faltering intelligence oversight is a reasonable Turn- Strengthens Surveillance No ‘reform’ will actually change anything about the US surveillance system. Actually strengthens surveillance and delays real solvency Greenwald 14 Glenn Greenwald is a journalist, constitutional lawyer, and author of four New York Times best-selling books on politics and law. “CONGRESS IS IRRELEVANT ON MASS SURVEILLANCE. HERE’S WHAT MATTERS INSTEAD.” At The Intercept on CONGRESS IS IRRELEVANT ON MASS SURVEILLANCE. HERE’S WHAT MATTERS INSTEAD. Accessed 6/29/15 at https://firstlook.org/theintercept/2014/11/19/irrelevance-u-s-congressstopping-nsas-mass-surveillance/ All of that illustrates what is, to me, the most important point from all of this: the last place one should look to impose limits on the powers of the U.S. government is . . . the U.S. government. Governments don’t walk around trying to figure out how to limit their own power, and that’s particularly true of empires. The entire system in D.C. is designed at its core to prevent real reform. This Congress is not going to enact anything resembling fundamental limits on the NSA’s powers of mass surveillance. Even if it somehow did, this White House would never sign it. Even if all that miraculously happened, the fact that the U.S. intelligence community and National Security State operates with no limits and no oversight means they’d easily co-opt the entire reform process. That’s what happened after the eavesdropping scandals of the mid-1970s led to the establishment of congressional intelligence committees and a special FISA “oversight” court—the committees were instantly captured by putting in charge supreme servants of the intelligence community like Senators Dianne Feinstein and Chambliss, and Congressmen Mike Rogers and “Dutch” Ruppersberger, while the court quickly became a rubber stamp with subservient judges who operate in total secrecy. Ever since the Snowden reporting began and public opinion (in both the U.S. and globally) began radically changing, the White House’s strategy has been obvious. It’s vintage Obama: Enact something that is called “reform”—so that he can give a pretty speech telling the world that he heard and responded to their concerns—but that in actuality changes almost nothing, thus strengthening the very system he can pretend he “changed.” That’s the same tactic as Silicon Valley, which also supported this bill: Be able to point to something called “reform” so they can trick hundreds of millions of current and future users around the world into believing that their communications are now safe if they use Facebook, Google, Skype and the rest. Circumvention The Government will inevitably get information from Silicon Valley and congressional action is irrelevant Greenwald 14 Glenn Greenwald is a journalist, constitutional lawyer, and author of four New York Times best-selling books on politics and law. “CONGRESS IS IRRELEVANT ON MASS SURVEILLANCE. HERE’S WHAT MATTERS INSTEAD.” At The Intercept on CONGRESS IS IRRELEVANT ON MASS SURVEILLANCE. HERE’S WHAT MATTERS INSTEAD. Accessed 6/29/15 at https://firstlook.org/theintercept/2014/11/19/irrelevance-u-s-congressstopping-nsas-mass-surveillance/ So let Saxby Chambliss and Susan Collins and Marco Rubio scream into their insular void about ISIS and 9/11 and terrorism. Let Barack Obama, Dianne Feinstein and Nancy Pelosi deceitfully march under a “reform” banner as they do everything possible to protect the NSA from any real limits. Let the NSA and other national security officials sit smugly in the knowledge that none of the political branches in D.C. can meaningfully limit them even if they wanted to (which they don’t). The changes from the Snowden disclosures are found far from the Kabuki theater of the D.C. political class, and they are unquestionably significant. That does not mean the battle is inevitably won: The U.S. remains the most powerful government on earth, has all sorts of ways to continue to induce the complicity of big Silicon Valley firms, and is not going to cede dominion over the internet easily. But the battle is underway and the forces of reform are formidable— not because of anything the U.S. congress is doing, but despite it. Links to Neg Args Terrorism DA Links NSLs are needed to prevent terror attacks Stimson and Grossman in 2008 (Charles D. Stimson is Senior Legal Fellow, and Andrew M. Grossman is Senior Legal Policy Analyst, in the Center for Legal and Judicial Studies at The Heritage Foundation “National Security Letters: Three Important Facts” The Heritage Foundation, March 14, 2008 http://www.heritage.org/research/reports/2008/03/national-security-letters-three-important-facts) Congress authorized the FBI to use NSLs in counterterrorism and counterintelligence investigations. Both OIG reports related to the FBI's use of NSLs unequivocally state that NSLs are an indispensable tool in national security investigations. Law enforcement officials, working closely with the intelligence community, need the tools contained within those authorized NSLs to keep Americans safe and to prevent future terrorist attacks. As the latest OIG report highlights, FBI Director Robert Mueller has made it a top priority to reduce the accidental misuse of NSLs, and the Department of Justice has made significant progress in doing so since the issuance of the 2007 OIG report. Although the report notes the significant progress the Department has made in the past 12 months, it is too early to tell how effective the new systems and controls will be in achieving the ultimate goal of eliminating all inadvertent misuses of NSLs. Every aspect of NSL’s help in counterterror and counterintelligence operations Stimson and Grossman in 2008 (Charles D. Stimson is Senior Legal Fellow, and Andrew M. Grossman is Senior Legal Policy Analyst, in the Center for Legal and Judicial Studies at The Heritage Foundation “National Security Letters: Three Important Facts” The Heritage Foundation, March 14, 2008 http://www.heritage.org/research/reports/2008/03/national-security-letters-three-important-facts) As noted in each of the two OIG reports, NSLs have proven to be invaluable tools in counterterrorism and counterintelligence investigations. According to the FBI, the principal uses of NSLs are to: Establish evidence to support FISA applications for electronic surveillance, physical searches, or pen register/trap and trace orders; Assess communication or financial links between investigative subjects or others; Collect information sufficient to fully develop national security investigations; Generate leads for other field divisions, Joint Terrorism Task Forces, and other federal agencies or to pass to foreign governments; Develop analytical products for distribution within the FBI; Develop information that is provided to law enforcement authorities for use in criminal proceedings; Collect information sufficient to eliminate concerns about investigative subjects and thereby close national security investigations; and Corroborate information derived from other investigative techniques. [12] Information obtained from each type of NSL has allowed investigators to crack cases, especially in the realms of counterterrorism and counterintelligence. A brief examination of the success stories outlined in the OIG reports under each type of NSL proves the point. The following examples, excerpted from the OIG report, show how counterterrorism and counterintelligence investigations are supported through the lawful use of NSLs: The NSLs have helped the FBI combat terrorism Sinnar in 2013 (Shirin Sinnar; Assistant Professor of Law at Stanford Law School, “Protecting Rights from Within? Inspectors General and National Security Oversight”, LexisNexis.com, 65 Stan. L. Rev. 1027, 2013; The Board of Trustees of Leland Stanford Junior University, 49 pgs., Database, 6/28/15, http://www.lexisnexis.com.proxy.library.umkc.edu/hottopics/lnacademic/) Despite these trenchant critiques, the IG investigations supported the FBI's position in several respects. Most importantly, the IG concluded that the information obtained from NSLs had "contributed significantly" to terrorism investigations n108 and that the Patriot Act's changes to the law, according to agency [*1046] officials, made NSLs more useful. n109 The IG also concluded that in most cases where the FBI had violated the law, it could have legally obtained the same information. n110 Secrecy is necessary to fight the war on terror Marsden ‘15(Rachel Marsden, Rachel Marsden is a columnist, political strategist and former Fox News host, February 2, 2015 “Rachel Marsden: Intelligence Agencies must be able to fight terrorism in secret” http://www.chicagotribune.com/news/columnists/sns-201502031330--tms--amvoicesctnavb20150203-20150203-column.html) PARIS -- Does anyone else miss the days when intelligence agencies were permitted to operate covertly and it was considered totally acceptable that they do so? It seems to be increasingly the case that Western countries are perceived as less than democratic if their traditionally covert operations aren't fully transparent to the public. It's one thing for wrongdoing to be exposed and debated, but the bar for what constitutes "wrongdoing" by intelligence agencies has been lowered so drastically that it has become prohibitive. It's being publicly defined by the loudest whiners who believe in transparency at all costs. Whether or not critics realize it, transparency makes intelligence work ineffective. They're called "secret services" for a reason. Yet anyone who argues in favor of keeping them "secret" these days is considered a statist or an enemy of freedom instead of someone who realizes their inherent value in a democracy. Pursuant to last October's terrorist attack on Canadian Parliament, Prime Minister Stephen Harper has introduced new legislation that would, among other things, authorize the Canadian Security Intelligence Service to remove suspected terrorists from flights or interfere with their banking transactions. The new legislation would also increase the sharing of national security information across federal agencies. In response, top-secret-intelligence leaker turned Russian resident Edward Snowden told Toronto students via video this week that Canada is setting up a "new secret police." Snowden could stand to learn a thing or two from his Russian hosts and their world-class counterterrorism operatives, who managed to quietly kill Islamic terrorist leader Doku Umarov of the North Caucasus after he took credit for orchestrating pre-Olympic civilian bombings. Snowden was joined by journalist Glenn Greenwald, who pointed out how rare terrorist attacks are in Canada. And why might that be? Perhaps it's because of the good work of the intelligence services. How is the lack of terrorism in Canada a valid argument against the secret services being dedicated to stopping it? Would critics prefer that the intelligence services stand down in the face of "new secret police" labeling? Would citizens prefer to find out just how effective intelligence agencies have been by seeing whether there's an increase in terrorism after the agencies have been handcuffed? If there are any cases of "secret police" action, no doubt the Snowdens and Greenwalds will be there to tell us about it. But why preemptively predict malfeasance or attribute malice? Transparency is the nemesis of operational security -- even for the enemy. Perhaps the only good thing about Islamic State terrorists trying to set up a caliphate is that it moves what has largely been an ideological ghost-war against terrorism without geographic boundaries back into the realm of a definable battlefield. Likewise, the Islamic State propaganda and recruitment machine that operates over social media allows for the group's methods and tactics to be readily viewed, researched and assessed so that their vulnerabilities can be exploited. There are two fronts on which terrorism has to be defeated: Enemy combatants must be stopped on foreign soil, and domestic sleeper cells must be wiped out. In both cases, operational secrecy is the key to eradication. The Washington Post recently ran a story detailing a successful secret counterterrorism operation in which the CIA and Israel's Mossad cooperated in the assassination of Hezbollah commander Imad Mughniyah with a car bomb in Damascus, Syria, in 2008. Mughniyah was believed to have helped plot terrorist operations against the U.S. and Israel dating back to the 1980s, including the bombings of the U.S. Marines barracks and the U.S. Embassy in Beirut, Lebanon, in 1983, and the hijacking of TWA Flight 847 in 1985. More recently, Mughniyah had been deemed a threat to U.S. troops operating in Iraq. So Mughniyah was quietly snuffed out. The operation was a total success -- right up until it was splayed out in the Washington Post because someone apparently couldn't keep the details a secret. The only difference between that operation and targeted drone strikes is that drones carry out the same sort of assassinations even more publicly -- and we're worse off as a result. A lack of discretion in counterterrorism matters, whether it's highly visible drone kills or the ridiculous idea of trying enemy combatants captured on a foreign battlefield in Western courts of law, means that you're soliciting a counterproductive reaction and attention to your modus operandi. So let the secret services do their job -- in secret. The opportunity to point fingers at a legitimate screw-up will always exist. Circumvention Links Exigent Letters The FBI was found during a Report to be circumventing requirements and in some instances issuing searches without first issuing NSLs Doyle in 2015 (Charles Doyle, Senior Specialist in American Public Law, Published January 22, 2015; National Security Letters proposals in the 113th congress Page: 6; http://www.fas.org/sgp/crs/intel/R43322.pdf) The Fair Credit Reporting Act NSL statutes, 15 U.S.C. 1681u (FCRAu) and 1681v (FCRAv) can be even more illuminating: “The supervisor of a counterterrorism squad told us that the FCRA NSLs enable the FBI to see ‘how their investigative subjects conduct their day-to-day activities, how they get their money, and whether they are engaged in white collar crime that could be relevant to their investigations.’” Overall, the report notes that the FBI used the information gleaned from NSLs for a variety of purposes, “to determine if further investigation is warranted; to generate leads for other field offices, Joint Terrorism Task Forces, or other federal agencies; and to corroborate information developed from other investigative techniques.” Moreover, information supplied in response to NSLs provides the grist of FBI analytical intelligence reports and various FBI databases. The report was somewhat critical, however, of the FBI’s initial performance: [W]e found that the FBI used NSLs in violation of applicable NSL statutes, Attorney General Guidelines, and internal FBI policies. In addition, we found that the FBI circumvented the requirements of the ECPA NSL statute when it issued at least 739 “exigent letters” to obtain telephone toll billing records and subscriber information from three telephone companies without first issuing NSLs. Moreover, in a few other instances, the FBI sought or obtained telephone toll billing records in the absence of a national security investigation, when it sought and obtained consumer full credit reports in a counterintelligence investigation, and when it sought and obtained financial records and telephone toll billing records without first issuing NSLs. The FBI Circumvents NSL’s by using exigent letters guts solvency Doyle in 2015 (Charles Doyle, Senior Specialist in American Public Law, Published January 22, 2015; National Security Letters proposals in the 113th congress Page: 8-9; http://www.fas.org/sgp/crs/intel/R43322.pdf) The third IG Report examined the FBI’s use of exigent letters and other informal means of acquiring communication service providers’ customer records rather than relying on NSL authority during the period from 2003 to 2007. The IG’s Office discovered that “the FBI’s use of exigent letters became so casual, routine, and unsupervised that employees of all three communications service providers sometimes generated exigent letters for FBI personnel to sign and return to them.” Some of the informality was apparently the product of proximity. In order to facilitate cooperation, communications providers had assigned employees to FBI offices. In addition to a relaxed exigent letter process, the on-site feature gave rise to a practice of sneak peeks, that is, of providing the FBI with “a preview of the available information for a targeted phone number, without documentation of any justification for the request.” “In fact, at times the service providers’ employees simply invited FBI personnel to view the telephone records on their computer screens. One senior FBI counterterrorism official described the culture of casual requests for telephone records by observing, ‘It [was] like having the ATM in your living room.’” Not surprisingly, the IG’s review found widespread use by the FBI of exigent letters and other informal requests for telephone records. These other requests were made ... without first providing legal process or even exigent letters. The FBI also obtained telephone records through improper ‘sneak peeks,’ community of interest █████, and hot-number ████ Many of these practices violated FBI guidelines, Department policy, and the ECPA statute. In addition, we found that t he FBI also made inaccurate statements to the FISA Court related to its use of exigent letters. Although critical of the FBI’s initial response and recommending further steps to prevent reoccurrence, the IG’s Report concluded that “the FBI took appropriate action to stop the use of exigent letters and to address the problems created by their use.” The FBI uses exigent letters in replacement of NSL’s and they also circumvent ECPA IG in 2010 (U.S Department of Justice, Office of the Inspector General; A Review of the Federal Bureau of Investigations Use of Exigent Letters and Other Informal Requests for Telephone Records, Page 2; Published January 2010; https://oig.justice.gov/special/s1001r.pdf) In our first NSL report, we described how the FBI issued at least 739 so--called "exigent letters" between March 11, 2003, and December 16, 2005. These letters were signed by personnel in the FBI Counterterrorism Division's (CTD) Communications Exploitation Section (CXS) who were not authorized to sign NSLs, including two Assistant Section Chiefs, Unit Chiefs assigned to the CXS's Communications Analysis Unit (CAU), Supervisory Special Agents (SSA), Intelligence and an Intelligence Operations Specialist. We determined that the 739 exigent letters requested information relating to approximately 3,000 telephone numbers. The overwhelming majority of the letters requested production of telephone records, allegedly "due to exigent circumstances," and also stated that subpoenas requesting the information had been submitted to a U.S. Attorney's Office for processing and would be served formally as expeditiously as possible. We concluded that by using exigent letters to acquire information from three communications service providers prior to serving NSLs or other legal process, the FBI circumvented the requirements of the Electronic Communications Privacy Act (ECPA) NSL statute and violated the Attorney General's Guidelines for FBI National Security Investigations and Foreign Intelligence Collection (NSI Guidelines), and internal FBI policy. We also found that there were factual misstatements in the letters. While almost all exigent letters stated that subpoenas requesting the information had been submitted to a U.S. Attorney's Office and would be served on the providers, in fact subpoenas were not issued in many instances and in other instances had not been requested. Moreover, we developed information that exigent letters sometimes were used in non-exigent circumstances. We also found that the FBI was unable to later establish that some of the exigent letter requests were made in connection with the required open preliminary or full investigations conducted pursuant to the Attorney General's NSI Guidelines or that the records requested were relevant to those investigations. 215 Orders/Subpoena Subjecting NSLs to judicial approval would lead to abandonment in favor of 215 orders and subpoenas Sanchez in 2014 (Julian a senior fellow at Cato; “Can We Do without National Security Letters?”, published Thursday, January 9, 2014 at 8:15 AM Date Accessed 6/29/15; http://justsecurity.org/5351/national-security-letters/) One of the more radical recommendations included in the report from President Obama’s Surveillance Review Group is the proposal to require judicial approval for National Security Letters, which can be used to compel the production (under gag) of an array of financial and communications records, and at present can be issued on the say-so of the Special Agent in Charge of any of the FBI’s 56 field offices. Though this recommendation has attracted relatively little public comment, it is unsurprising to read in a recent article in the Los Angeles Times that it “has sparked the most push-back from national security officials.” Though the review group does proposal amounts to the de facto elimination of NSLs, whose distinctive feature is precisely the absence of any advance judicial approval. Without that feature—especially following a 2008 OLC memo limiting their applicability to electronic communications transactional records—they would be a conspicuously inferior form of 215 order, requiring the same process, but applicable only to a more limited domain of records. Deprived of that key selling point, agents would almost certainly abandon NSLs in favor of 215 orders and conventional grand jury subpoenas. not frame it in these terms, their Congress will continuously find ways to get around the law – Section 215 proves Vladeck June ’15 (Stephen Vladeck june, June 1, 2015. Foreign Policy, “Forget the Patriot Act – Here Are the Privacy Violations You Should Be Worried About” http://foreignpolicy.com/2015/06/01/section215-patriot-act-expires-surveillance-continues-fisa-court-metadata/) Forget the Patriot Act – Here Are the Privacy Violations You Should Be Worried About The ongoing debate over U.S. surveillance programs seemingly came to a head last night, when the Senate failed to extend controversial Section 215 of the USA Patriot Act, which expired at midnight. As we learned from Edward Snowden two years ago, Section 215 was the provision that the government secretly claimed provided authority for the bulk collection of Americans’ phone records — their telephone “metadata.” And although the government’s less-than-obvious interpretation of that statute was accepted by judges sitting on the largely secret Foreign Intelligence Surveillance Act (FISA) Court, it has since been repudiated by two different federal courts, one on the grounds that Congress had not in fact approved such a program and one on the grounds that, even if it had, such warrantless, suspicionless surveillance violates the Fourth Amendment to the U.S. Constitution. For those reasons, and a host of others, the debate over what Congress should do with Section 215 as its sunset approached grew only more heated ahead of the deadline, provoking bitter disputes over the legal wisdom and practical necessity of the phone records program. Some privacy and civil liberties groups, joined by libertarian politicians such as Sen. Rand Paul (R-Ky.), supported outright expiration of the provision, arguing that the phone records program was both unnecessary and unconstitutional. At the other end of the spectrum, hardline conservatives, led by Senate Majority Leader Mitch McConnell (R-Ky.), backed a straight “reauthorization,” which would allow the program to continue for as much as two additional years before further reconsideration. The Obama administration, along with a number of more moderate members of Congress, took more of a middle road, calling for the fairly modest reforms provided by the USA Freedom Act, which would replace the phone records program with a somewhat less open-ended (and somewhat better regulated) series of authorities for the government to obtain and review similar data — and which the House of Representatives overwhelmingly passed on May 13. But whatever the merits of the competing sides in this debate, the larger problem is that this conversation has missed the forest for a very small — and largely irrelevant — tree. In fact, from the perspective of individual privacy rights, the phone records program is much less problematic than the government’s other authorities to conduct mass surveillance under Executive Order 12333 and the 2008 FISA Amendments Act. And so, in focusing on how to “fix” Section 215, we’ve given short shrift to the far more significant problems raised by these other authorities — and, just as importantly, the broader lessons we should be taking away from the surveillance reform conversation that Snowden started. To understand the significance of these other authorities, it’ll help to describe their aims: Executive Order 12333, issued in 1981, is directed at the overseas interception of communications — both metadata and content — of non-citizens outside the United States, who, under a 1990 Supreme Court decision, categorically lack Fourth Amendment rights. The 2008 FISA Amendments Act was enacted to close a loophole that new technology had helped to create, where non-citizens outside the United States were nevertheless communicating through servers or other telecommunications infrastructure located stateside, which the government could not surveil under the executive order. Ordinarily, the government needs a warrant before collecting the content of domestic communications, one based upon a judge’s determination that there’s good reason to believe a particular individual either is engaged in the commission of a crime or is an agent of a foreign power. But Executive Order 12333 and the 2008 FISA statute, by focusing on individuals who fall outside the Fourth Amendment, capitalize on the lack of constitutionally required individualized assessments and instead allow the government to engage in bulk collection of such information — as if it were using an industrial vacuum cleaner to pick up individual particles of dirt. It’s easy to see how these authorities could cause diplomatic headaches (as, for example, with the contretemps surrounding U.S. surveillance of German Chancellor Angela Merkel’s cell phone). But most commentators have assumed that, at least legally, the validity of these programs turns on their overseas focus. After all, if the government is only targeting the communications of non-citizens outside the United States, what could possibly be the constitutional objection? The answer, we now know, has everything to do with technology. Although the government is only allowed to “target” non-citizens outside the United States, it is inevitable, given how it collects information under both of these regimes, that the communications of U.S. citizens and non-citizens lawfully present in the United States will also be collected, albeit “incidentally,” as the government puts it. After all, when thousands of unrelated emails and other electronic communications are bundled together in a packet that travels through an Internet switch that’s physically located in the United States (for the 2008 statute) or overseas (for Executive Order 12333), it’s simply not possible for the government to only collect the communications between non-U.S. citizens and leave the others untouched, any more so than it’s possible for a vacuum to segregate particles of dirt. To be sure, the U.S. government doesn’t dispute that it routinely collects the communications of U.S. citizens. Instead, it has argued that any potential for abuse is mitigated by so-called “minimization requirements” — procedural rules that require the relevant intelligence agency to take steps to avoid the improper retention and use of communications collected under these authorities. The government’s defense, as we’ve come to learn, is flawed in two vital respects: First, as several since-disclosed opinions from the FISA Court have made clear, the government’s minimization requirements under the 2008 statute were often too skimpy, allowing the retention and use of information that both the statute and the Fourth Amendment prohibit. Second — and perhaps more importantly — even where the minimization rules were legally sufficient, there have been numerous instances in which government officials violated them, with the FISA Court only discovering the abuses after they were voluntarily reported by Justice Department lawyers. As a result, the government collected and retained a large volume of communications by U.S. citizens that neither Congress nor the Constitution allowed it to acquire. More alarmingly, with regard to collection under Executive Order 12333, there isn’t any similar judicial review (or meaningful congressional oversight), which means that it has entirely been up to the government to police itself. As State Department whistleblower John Napier Tye explained last summer, there is every reason to doubt that such internal accountability has provided a sufficient check. In his words, “Executive Order 12333 contains nothing to prevent the NSA from collecting and storing all … communications … provided that such collection occurs outside the United States in the course of a lawful foreign intelligence investigation.” To put the matter bluntly, whereas the Section 215 debate has addressed whether the government can collect our phone records, Executive Order 12333 and the 2008 FISA Amendments Act allow the government to collect a lot of what we’re actually saying, whether on the phone, in our emails, or even to our search engines. There is no question that, from a privacy perspective, these programs are far more pernicious than what’s been pegged to Section 215.There is no question that, from a privacy perspective, these programs are far more pernicious than what’s been pegged to Section 215. There is also no question that such collection raises even graver constitutional questions than the phone records program. Whereas there is an open debate over our expectation of privacy in the metadata we voluntarily provide to our phone companies, there’s no doubt that we have an expectation of privacy in the content of our private communications. Why, then, has all the fuss been around Section 215 and the phone records program, while the far more troubling surveillance authorities provided by Executive Order 12333 and the 2008 FISA Amendments Act have flown under the radar? Part of it may be because of the complexities described above. After all, it’s easy for people on the street to understand what it means when the government is collecting our phone records; it’s not nearly as obvious why we should be bothered by violations of minimization requirements. Part of it may also have to do with the government’s perceived intent. Maybe it seems more troubling when the government is intentionally collecting our phone records, as opposed to “incidentally” (albeit knowingly) collecting the contents of our communications. And technology may play a role, too; how many senders of emails know where the server is located on which the message is ultimately stored? If we don’t realize how easily our communications might get bundled with those of non-citizens outside the United States, we might not be worried about surveillance targeted at them. But whatever the reason for our myopic focus on Section 215, it has not only obscured the larger privacy concerns raised by these other authorities, but also the deeper lessons we should have taken away from Snowden’s revelations. However much we might tolerate, or even embrace, the need for secret government surveillance programs, it is all-but-inevitable that those programs will be stretched to — and beyond — their legal limits. That’s why it’s important not only to place substantive limits upon the government’s surveillance authorities, but also to ensure that they are subject to meaningful external oversight and accountability as well. And that’s why the denouement of Section 215 debate has been so disappointing. This should have been a conversation not just about the full range of government surveillance powers, including Executive Order 12333 and the 2008 FISA Amendments Act, but also about the role of the FISA Court and of congressional oversight in supervising those authorities. Instead, it devolved into an over-heated debate over an over-emphasized program. Congress has tended to a paper cut, while it ignored the internal bleeding. Not only does the expiration of Section 215 have no effect on the substance of other surveillance authorities, it also has no effect on their oversight and accountability. Reaching some degree of closure with regard to the phone records program may leave many with the impression that America has concluded a meaningful and productive national debate over surveillance reform. We haven’t. And although the 2008 FISA Amendments Act is also set to expire — on December 31, 2017 — the debate over Section 215 leaves little reason to believe that we’ll have it then, either. The FBI will circumvent policies and has many methods of domestic surveillance Lendman in 2015 (Stephen, a writer for sleuth journal Published June 10 2015 Accessed 6/29/15; “Unconstitutional Mass FBI Aerial Surveillance”; http://www.thesleuthjournal.com/unconstitutional-mass-fbiaerial-surveillance/) Free and open societies don’t spy on their citizens. They don’t invent phony threats as justification. America is a belligerent nation waging endless wars of aggression against invented enemies. Fear-mongering is rife. It’s done to rape, ravage and destroy one country after another. It’s a tactic used to scare people to believe they’re safer by sacrificing fundamental freedoms. Mass surveillance is a defining rogue state characteristic. Post-9/11, government-usurped authority turned America into a police state. Big Brother watches everyone. Tuesday Senate passage of the USA Freedom Act (the renamed Patriot Act) changed little. Government intrusion into the private lives of its citizens remains largely unchanged. The only good news is that USAF slightly rolled back its intrusiveness instead of giving spy agencies more powers. History shows restrictions imposed are easily circumvented or ignored. A separate article discusses systematic FBI misuse of Patriot Act authority. Bureau secrecy and cover-up make it impossible to know the full extent of its lawlessness. It operates ad libitum with minimum oversight and accountability. One On June 2, AP reported “(s)cores of low-flying planes circling American cities…” “They’re “part of a civilian air force operated by the FBI and obscured behind fictitious companies…” It’s not secret. It’s been reported before. In July 2013, the agency admitted using drones for domestic surveillance numerous times without court authorized warrants or other forms of oversight. At the time, deputy director Stephen D. Kelly said “(t)he FBI uses UAVs in very limited circumstances to conduct surveillance when there is a specific operational need.” “Since late 2006, the FBI has conducted surveillance using UAVs in eight criminal cases and two national security cases.” Former FBI director Robert Meuller admitted spying on US citizens with no “operational guidelines.” Warrantless spying by any example is its mass surveillance of US citizens by drones and other aircraft. means threatens everyone. No probable cause is needed. No restraints are imposed. Constitutional protections are circumvented. Once a program is established, it takes on a life of its own. In AP identified at least 50 FBI aircraft conducting more than 100 flights over urban and rural areas in 11 states. It cited a 2009 budget document indicating 115 planes, including 90 Cessna aircraft. FBI aerial spying is longstanding. Today, drones and other aircraft are equipped with high-tech cameras for close-up visual surveillance as well as technology able to monitor thousands of cell phones – a blatant breach of privacy. According to Senate the last decade, FBI aerial spying expanded to “civilian air force” level. In April alone, Judiciary Committee chairman Charles Grassley (R. IA): “It’s important that federal law enforcement personnel have the tools they need to find and catch criminals.” “But whenever an operation may also monitor the activities of Americans who are not the intended target, we must make darn sure that safeguards are in place to protect the civil liberties of innocent Americans.” No safeguards whatever exist – nor does Congress back up high-minded rhetoric with effective policies protecting the public from abusive government practices. Rogue agencies like the FBI, NSA, CIA, DEA and Homeland Security operate by their own rules – easily circumventing weak and ineffective restraints on their authority. Congressional inaction effectively rubber-stamps them. It permits unaccountable police state practices no free society would tolerate. AP learned the FBI uses at least 13 fake companies to conceal its activities – including FVX Research, KQM Aviation, NBR Aviation and PXW Services. ACLU policy analyst Jay Stanley called its flights significant if they’re “maintaining a fleet of aircraft whose purpose is to circle over American cities, especially with” today’s sophisticated surveillance technology. Details the FBI confirmed concur with published reports since at least 2003 about suspicious-looking planes overflying US cities being government ones. The Drug Enforcement Agency (DEA) and US Marshals Service have their own aerial surveillance programs using sophisticated technology, much like the FBI’s. Basic information about these programs are secret. Heavily redacted Justice Department Inspector General documents alone inadequately explain what the public has a right to know. They’re spied on – by the FBI, NSA, CIA, DEA, Homeland Security and other rogue government agencies, especially post-9/11. Spies “R” us defines US policy. America is a total surveillance society unfit to live in. Big Brother watches everyone intrusively – in blatant breach of fundamental constitutional protections. Fabricated national security threats justify the unjustifiable. The so-called “war on terror” is phony. The war OF terror by Washington on its citizens is real. Unconstitutional spying today in America is pervasive. It’s institutionalized. Privacy rights no longer matter. Fundamental freedoms are being trampled. They’re disappearing in plain sight.