The Filesystem
advertisement

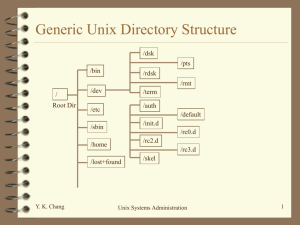
UNIX File System By Vishal Desai Introduction • Basic purpose of file system: Represent and organize the system resources. • But UNIX File System also maps processes, serial ports, interprocess communication channels. • This leads to a very convenient way of mapping these objects but leads to monstrous file systems. Basic Constituents File system consists of the following: Namespace: A way of naming and arranging things in a hierarchy. An API: Set of system calls for manipulating nodes. Security Model: Protection mechanism to enable sharing. Implementation: Code that ties the logical model to the actual disk. Basic Constituents Cont’d • UNIX file systems define an abstract kernel-level interface that accommodates several different back ends. • Some portions of a file tree are handled by traditional disk based implementation; others are fielded by separate drivers within the kernel. E.g. NFS. • A complicated factor in UNIX file systems is that they tend to support more than one type of disk-based file systems. Pathnames • The file system is a single hierarchy. • It starts at directory /. It continues through an arbitrary number of subdirectories. • / is also called as the root directory. • List of directory to be traversed to locate a file forms the pathname. • Pathnames can be either absolute or relative. • No restriction on depth of file system. • However, each component of a pathname can not be more than 255 characters in length. • Also a single path can not be more than 1023 characters. To access a file with pathname longer than this, we must “cd” to an intermediate directory and use a relative pathname. Pathnames Cont’d • No restrictions on naming of files except they are limited in length and must not contain the “/” character or nulls. • The space character is supported. • You just need to quote the file name containing spaces. • E.g. % more “My file.txt” would preserve My file.txt as a single argument to more. Mounting • A file tree refers to the overall layout of the file system. • Different file systems are attached with the mount command. • Mount maps a directory within the file tree to the root of the new file system. This is called the mount point. • The previous contents of the mount point become inaccessible. • However mount points are empty directories. E.g. # mount /dev/sd1c /users. Mounting Cont’d • A list of file systems that is customarily mounted is kept in the /etc/fstab, /etc/vfstab, or /etc/checklist file. • The information in this file allows file systems to be checked (fsck –p) and mounted (mount –a) at the time of booting. • Also in order to mount a file system manually, the location of the file system to be mounted is looked up in this file. Unmounting • File systems are detached with the unmount command. • In order to unmount a file system: 1) It must not be busy. 2) No files or process should be open or running. 3) If a file system contains executable programs, they must not be running. Some Syntactic Details About Unmounting • Some operating systems allow forced unmounting of a file system. E.g. 1) FreeBSD: unmount –f. 2) Solaris 8: unmount –f. 3) Earlier versions of Solaris: It is possible to achieve the same effects as unmount –f by a two step process as follows. a) lockfs –h <dir> to “hardlock” the file system. b) Then unmount it normally. Syntactic Details Cont’d • To find out why a file system is busy you can run the fuser -c <dir> command. • This will display the process ID of every process that is using the file system in anyway. • E.g. % fuser -c /usr /usr: 157tom 315ctom • The letter codes besides the PIDs show what’s being done. E.g. “c” is for a process that has a current directory on the file system, “o” for an open file, “t” for a running program, “m” for a mapped file (shared libraries usually) and “r” for a process whose root directory is on the file system. Syntactic Details Cont’d • To determine exactly what the offending processes are run ps with a list of the PIDs returned by fuser. • E.g. From the above example % ps -fp “157 315” UID PID PPID C STIME TTY TIME CMD root 490 0 Oct 14 ? 0:00 /usr/bin/X11/xdm 1 0 Jun 27 ? 5:26 /usr/sbin/named 157 lp 315 Organization of the File Tree • Root file system contains the root directory and a minimal set of files and subdirectories. • File containing the kernel called unix or vmunix resides in either the root directory or in /kernel or /stand. • • • • /dev is for device files. /etc is for critical system files. /sbin and /bin are for important utilities. /tmp is for temporary files. Organization of the File Tree Cont’d • Some systems keep shared libraries and the C preprocessor in the /lib directory. Others have moved this into /usr/lib. • /usr contains most of the user programs and online manuals etc. • /var provides a home for spool directories, log files, accounting information etc. • Home directories of users should be kept on different file systems and mounted beneath /usr. File Types • • • • • • • Regular Files. Directories. Character Device Files. Block Device Files. UNIX domain sockets. Named pipes (FIFOs). Symbolic links. A few systems do not support UNIX domain sockets and named pipes. File Attributes • Every file has a set of 9 permission bits that control who can read, write and execute the contents of the file. • Together with 3 other bits that affect the operation of executable programs, these bits constitute the file’s “mode”. • These 12 bits together with 4 bits of file type information are stored as a 16-bit word. • The 4 file type bits are set when the file is first created and can’t be changed, but the 12 bits can be changed by the owner of the file or the superuser by using the chmod command. File Attributes Cont’d • The setuid and setgid bits: Bits with octal values 4000 and 2000. They allow programs to access files and processes that would be otherwise off-limits to the user that runs them. • The sticky bit: octal value 1000. Mostly obsolete and is ignored by the kernel. If this bit is set though, most UNIX systems don’t allow you to delete them. You have to be superuser or the owner to do so. • The permission bits: Remaining 9 bits are permission bits. UNIX doesn’t allow for separate permissions for separate users. There are sets of permissions for the owner, group owner and everyone else.