The 1-hour Guide to Stuxnet
Carey Nachenberg
Vice President, Symantec Fellow
Symantec Corporation
The 1-hour Guide to Stuxnet
1
This is Natanz, Iran
The 1-hour Guide to Stuxnet
2
And these are Natanz’s Centrifuges
The 1-hour Guide to Stuxnet
3
Industrial control systems are
typically controlled by a
standard PC running
industrial control software
like STEP7 from
Siemens.
Windows
Programmable
And this is how they’re controlled
PC
Logic Controller
Communications
Processors (Routers)
Frequency Converters are
responsible for converting
The PLC is a specialized Communications
AC frequencies topiece
eitherof hardware that Processors route
higher-or lower frequencies
orchestrates control commands
of
from the PLC
to operate motors.
multiple connectedto groups of mechanical
mechanical devices.
devices.
Centrifuges enrich Uranium
...
Frequency
so.it. .can be used to power
Converters
nuclear plants or weapons.
...
...
Centrifuges
The 1-hour Guide to Stuxnet
4
And this is how they’re isolated
Windows Programmable
PC
Logic Controller
Communications
Processors (Routers)
Research Network
Frequency
Converters
...
...
...
...
Centrifuges
The 1-hour Guide to Stuxnet
5
And Who
this iswants
(probably)
an IsraelitoMossad
Programmer
introduce
onto this
computer
right here
The 1-hour Guide to Stuxnet
6
So how exactly
does this:
Get onto an
“air-gapped”
network to
disrupt these:
It’s got to spread on its own…
Until it discovers the proper computers…
Where it can disrupt the centrifuges…
All while evading detection.
The 1-hour Guide to Stuxnet
7
It’s got to spread on its own…
Stuxnet uses seven distinct mechanisms to spread to new computers.
Six of these attacks targeted flaws (back doors) that were
unknown to the security industry and software vendors!
attacks
hole
Peers
update
other
Stuxnet
uses
thumb
ItItcopies
attacks
aa hole
It
password-cracks
It
itself
to
infects
SIEMENS
Windows
RPC.
peers
directly.
drives
to
bridge
the gap!
ininWindows’
print
SIEMENS
DB
software.
open
file-shares.
PLC
data
files.
spooler.
But if the centrifuges are
air-gapped from the ‘net,
Usually
we’re surprised
how
can Stuxnet
jump to
we see network?
a threat
thewhen
enrichment
targeting
one flaw...
USB drives!
The 1-hour Guide to Stuxnet
8
Spreading – A Sidebar
(the tasks themselves
are stored as globally
readable/writable XML files)
Windows has a built-in task scheduler system.
Windows Tasks
Each user can add new tasks to be run at a certain
time and with a certain permission level.
(Regular users can’t add “root” level jobs)
To prevent tampering, windows computes
a CRC32 hash for each task record and stores this in
a protected area of the computer.
Task #1:
Job: Delete
Tasktemp
#2: files
Run
Root
user
Job:as:
Clean
registry
Task10pm
#3:
Run
at:
RunJob:
as: Print
Jim (non-root)
receipts
Run
at:
6pm
Run as: Ted (non-root)
Run at: 2am
Task1 hash: 9B7CC653
Task2 hash: 11090343
Task3 hash: 40910276
The 1-hour Guide to Stuxnet
9
Spreading – A Sidebar
When it arrives on a machine, Stuxnet starts
running with non-administrator privileges.
But to do its mischief, Stuxnet needs to
run with “root” privileges.
Windows Tasks
Task #1:
So first, Stuxnet creates a new task,
Job: Delete
temp
files
Task
#2:
using the permissions of the current user.
Run
Root
user
Job:as:
Clean
registry
Task10pm
#3:
Run
at:
And of course, once Windows verifies that the job is
RunJob:
as: Print
Jim (non-root)
legitimate (the user hasn’t tried to create a rootreceipts
Run
at:
6pm
level job), it calculates the job’s hash and adds it to
Run as: Ted (non-root)
the security store.
Run at: 2am
Task #4:
Job: Run stuxnet.dll
Task1 hash: 9B7CC653
Run as: Ted (non-root)
Task2 hash: 11090343
Run at: 2pm
Task3 hash: 40910276
Task4 hash: DE9DBA76
The 1-hour Guide to Stuxnet
10
Spreading – A Sidebar
Next Stuxnet modifies the XML job file it just
added, changing its permission to “root”!
(Remember, theBut
XMLwait!
files are
writable)
The
updated job
Windows Tasks
hashclever
no longer
matches
Ah, but Stuxnetfile
is more
than that.
Task #1:
the
protected
stored
by Job: Delete temp files
Stuxnet knows how to
forge
a CRC - ithash
computes
a set
Task #2:
Windows!
Run
as:
Root
user
of values which, if appended to the file, will result in
Job:
Clean
registry
its CRC matching the original! And then it appends
Task10pm
#3:
Run
at:
as: Print
Jim (non-root)
these If
bytes
to the file!
Windows
were to process RunJob:
receipts
Task
#4:
Run
at:
6pm
the updated job file, it would Run as: Ted (non-root)
And Windows will happily run the updated job,
Job:
Run
stuxnet.dll
detect
this
and
reject
it!
Run
at:
2am
giving Stuxnet root-level privileges!
Run as: Ted
Root(non-root)
user
Run at: 2pm
Task1 hash: 9B7CC653
Task2 hash: 11090343
Task3 hash: 40910276
Task4 hash: DE9DBA76
The 1-hour Guide to Stuxnet
XQ
DE9DBA76
New hash: 66C35150
11
Until itIt’s
discovers
the proper
got to spread
on itscomputers…
own…
Stuxnet is extremely picky and only activates
its payload when it’s found an exact match.
The targeted computer must be running
STEP7 software from Siemens.
The targeted computer must be directly connected to
an S7-315 Programmable Logic Controller from Siemens.
The PLC must further be connected to at least six
CP-342-5 Network Modules from Siemens.
Each Network Module must be connected to ~31
Fararo Paya or Vacon NX frequency converters.
The 1-hour Guide to Stuxnet
…
12
Until it discovers the proper computers…
Stuxnet is extremely picky and only activates
its payload when it’s found an exact match.
What a coincidence!
Now if you do the math….
The creators of
Stuxnet must have
guessed
these
Stuxnet verifies
thatall
theofdiscovered
details.
Programmable Logic
Controller…
Is controlling at least
155 total frequency converters…
And recently we learned that Iran’s
Uranium enrichment “cascade” just happens
to use exactly 160 centrifuges.
The 1-hour Guide to Stuxnet
…
13
Until
discovers
thedown
proper
Nowit Stuxnet
gets
to computers…
business…
Stuxnet starts by downloading
malicious logic onto the PLC hardware.
The 1-hour Guide to Stuxnet
What you (probably) didn’t
realize is that the PLC uses a
totally different microchip &
computer language than
Windows PCs.
Stuxnet is the first known
threat to target an industrial
control microchip!
14
Now Stuxnet gets down to business…
And makes sure the motors are running between 807Hz and 1210Hz.
(This is coincidentally
the frequency range
required to run
centrifuges.)
(After all, whoever wrote
Stuxnet wouldn’t want it
to take out a roller
coaster or something.)
Next, Stuxnet measures the operating speed of
the frequency converters during their normal
operation for 13 days!
The 1-hour Guide to Stuxnet
15
Now Stuxnet gets down to business…
Once it’s sure, the malicious PLC logic begins its mischief!
Stuxnet raises the spin rate
to 1410Hz for 15 mins.
Then sleeps for 27 days.
Then slows the spin rate
to 2Hz for 50 mins.
Then sleeps for 27 days.
Stuxnet repeats this
process over and over.
0Hz
The 1-hour Guide to Stuxnet
1500Hz
16
Now Stuxnet gets down to business…
Why push the motors up to 1410Hz?
Well, ~1380Hz is a resonance frequency.
It is believed that operation at this frequency for even a
few seconds will result in disintegration of the enrichment tubes!
Why reduce the motors to 2Hz?
At such a low rotation rate, the vertical enrichment tubes
will begin wobbling like a top (also causing damage).
0Hz
The 1-hour Guide to Stuxnet
1500Hz
17
Now Stuxnet gets down to business…
What about Iranian failsafe systems?
(Surely by now you’re thinking that alarm
bells should have been blaring at the
enrichment plant, right?)
Maybe Stuxnet pulled a mission impossible?!?
The 1-hour Guide to Stuxnet
18
Now Stuxnet gets down to business…
And in fact, that’s exactly what Stuxnet did!
0Hz
The 1-hour Guide to Stuxnet
1500Hz
Stuxnet
Well,records
in fact, telemetry
these
readingstypically
while the
facilities
do
centrifuges
are
operating
have fail-safe controls.
normally.
They
triggerit alaunches
shutdown
And when
its
if the
frequency
goes
attack,
it sends
thisout
of the acceptable
range.
recorded
data to fool
the
fail-safe
systems!
But
worry
not…
Stuxnet
takes disables
care of
And Stuxnet
this too.kill switch
the emergency
on the PLC as well…
Just in case someone tries
to be a hero.
20
while evading
detection…
NowAll
Stuxnet
gets down
to business…
Stuxnet uses five distinct mechanisms to conceal itself.
#5
Stuxnet hides its own files on infected thumb drives using 2 “rootkits.”
The 1-hour Guide to Stuxnet
21
All while evading detection.
Stuxnet uses five distinct mechanisms to conceal itself.
#4
Stuxnet inhibits different behaviors in the presence of different
security products to avoid detection.
Launch Attack A
Launch Attack B
Launch Attack C
Launch Attack D
The 1-hour Guide to Stuxnet
Launch Attack A
Launch Attack B
Launch Attack C
Launch Attack D
Launch Attack A
Launch Attack B
Launch Attack C
Launch Attack D
22
All while evading detection.
Stuxnet uses five distinct mechanisms to conceal itself.
#3
Stuxnet completely deletes itself from USB keys after it has
spread to exactly three new machines.
The 1-hour Guide to Stuxnet
23
All while evading detection.
Stuxnet uses five distinct mechanisms to conceal itself.
#2
Stuxnet’s authors “digitally signed” it with stolen digital certificates
to make it look like it was created by well-known companies.
The two certificates
were stolen from
RealTek and Jmicron…
Realtek
The 1-hour Guide to Stuxnet
…as it turns out, both
companies are located
less than 1km apart in
the same Taiwanese
business park.
24
All while evading detection.
Stuxnet uses five distinct mechanisms to conceal itself.
#1
Stuxnet conceals its malicious “code” changes to the PLC
from operational personnel (It hides its injected logic)!
Instructions to the Centrifuges
PLC
During normal operation:
Spin at 1410hz
In case of emergency:
IGNORE OPERATOR COMMANDS
(To centrifuges)
The 1-hour Guide to Stuxnet
25
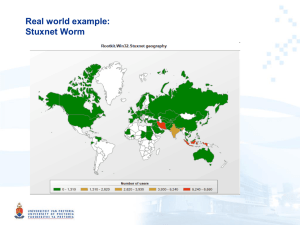
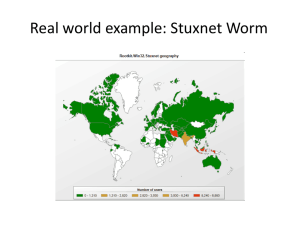
Stuxnet Epidemiology
The 1-hour Guide to Stuxnet
26
Did It Succeed?
Well, based on some clever
Symantec engineering, we’ve
got some interesting data.
Working with registrars,
Symantec took control of these
domains, forwarding all traffic
to our Symantec data centers.
Fact: Stuxnet contacts two
command-and-control servers
every time it runs to report its
status and check for commands.
Fact: As Stuxnet spreads between
computers, it keeps an internal log
of every computer it’s visited.
www.todaysfutbol.com
www.mypremierfutbol.com
The 1-hour Guide to Stuxnet
27
Stuxnet Bookkeeping
27.42.97.152
151.21.32.19
151.21.32.21
151.21.32.21
151.21.32.19
151.21.32.19
151.21.32.21
27.42.97.152
151.21.32.19
151.21.32.21
93.154.11.42
93.154.12.78
93.154.11.42
93.154.12.78
Stuxnet embeds its “visited list” inside its own body as it
spreads, enabling detailed forensics!
The 1-hour Guide to Stuxnet
28
Here’s What We Found
The 1-hour Guide to Stuxnet
29
Here’s What We Found
(These graphs show how the discovered samples spread)
The 1-hour Guide to Stuxnet
30
Here’s What We Found
Data at time of discovery (July, 2010)
The 1-hour Guide to Stuxnet
31
Here’s What We Found
Distribution of Infected Systems with Siemens Software
80.00
67.60
70.00
60.00
50.00
40.00
30.00
2.18
2.18
1.56
1.25
INDIA
4.98
TAIWAN
10.00
12.15
INDONESIA
8.10
GREAT BRITAIN
20.00
OTHERS
USA
SOUTH KOREA
IRAN
0.00
Data at time of discovery (July, 2010)
The 1-hour Guide to Stuxnet
32
Did It Succeed?
Indications are that it did!
Symantec telemetry indicates that rather than directly
trying to infiltrate Natanz…
The attackers infected five industrial companies with
potential subcontracting relationships with the plant.
These companies (likely) then unknowingly ferried the infection
into Natanz’s research and enrichment networks.
The Institute for Science and International Security writes:
“It is increasingly accepted that, in late 2009 or early 2010,
Stuxnet destroyed about 1,000 IR-1 centrifuges out of about
9,000 deployed at the site.”
The 1-hour Guide to Stuxnet
33
Whodunit?
19790509
According to Wikipedia, On May 9th, 1979 “Habib
Elghanian was executed by a firing squad in Tehran
sending shock waves through the closely knit Iranian
Jewish community. He was the first Jew and one of the
first civilians to be executed by the new Islamic
government. This prompted the mass exodus of the
once 100,000 member strong Jewish community of
Iran which continues to this day.”
June 22, 2009 4:31:47pm GMT
June 22, 2009 6:31:47pm Local
GMT + 2
The 1-hour Guide to Stuxnet
34
To Conclude
Stuxnet has signaled a fundamental
shift in the malware space.
Stuxnet proves cyber-warfare against
physical infrastructure is feasible.
Unfortunately, the same techniques can be used to
attack other physical and virtual systems.
The 1-hour Guide to Stuxnet
35
Thank you!
Copyright © 2010 Symantec Corporation. All rights reserved. Symantec and the Symantec Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in
the U.S. and other countries. Other names may be trademarks of their respective owners.
This document is provided for informational purposes only and is not intended as advertising. All warranties relating to the information in this document, either express or implied,
are disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice.
The 1-hour Guide to Stuxnet
36