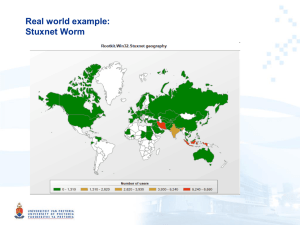
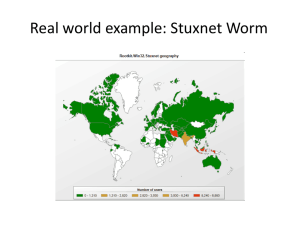
Stuxnet
advertisement

Stuxnet Burns Hudson Kevin Smith Background • • • • • • Spread on Microsoft Windows Developed June 2009 Spreading began late 2009/early 2010 Discovered in July 2010 o Microsoft out-of-band patch released August 2010 - .lnk exploit o More patches with the September 'Patch Tuesday' - print spooler exploit Around half a megabyte C, C++, and other object oriented languages What the news says it was • • • • • Iranian centrifuge destroyer! o It's one goal was to destroy the Iranian nuclear program Developed by the United States and Israel Contributed to the Gulf oil leak 'Mission: Impossible'-like virus It will kill your unborn children o Assuming they are born in a hospital using PLC machines What it really was • Malware that spread on networks to infect systems running WinCC and PCS 7 SCADA • Took advantage of the fact that PLCs are usually unsecured o They are behind firewalls and run by other computers that ARE secured • Once inside, had the ability to reprogram PLC controlling machinery o Gave the possibility of altering how machinery being controlled will run *PLC: Programmable Logic Controller How it did it • • • • • USB drive for initial infection, then spread on network .lnk file exploit o As soon as the shortcut is displayed, exploit is run Windows vulnerabilities o EoP Task scheduler o MS08-067 (Conficker) - Already patched!!!! (but not on these systems) o Printspooler exploit o Used at least 4 previously undiscovered vulnerabilities Searched for WinCC and PCS 7 SCADA management programs o Tried default Siemens passwords to gain access o If access is granted, PLC software could be reprogrammed Used stolen signed digital certificates o looked like genuine software to antivirus scanners *EoP: Elevation of Privileges How it did it (cont.) • • Installed a RPC server Self-updating o Machines check on other machines running Stuxnet and do a version check o Newer versions automatically push their version onto the other machines o Older versions automatically request newer version to be pushed If central server goes down, updates still spread *RPC: Remote Procedure Call What a story! I mean theory... "As the story goes, the Stuxnet worm was designed and released by a government--the U.S. and Israel are the most common suspects--specifically to attack the Bushehr nuclear power plant in Iran. How could anyone not report that? It combines computer attacks, nuclear power, spy agencies and a country that's a pariah to much of the world. The only problem with the story is that it's almost entirely speculation." - Bruce Schneier What we "know" it does: • Infects windows • Looks for Siemens SIMATIC WinCC/Step 7 controller software • Reads and changes bits in the PLC • Spreads through network/USB • Various updating mechanisms What a story! I mean theory... The media focuses on these types of quotes: • The Stuxnet worm is a "groundbreaking" piece of malware so devious in its use of unpatched vulnerabilities, so sophisticated in its multipronged approach, that the security researchers who tore it apart believe it may be the work of state-backed professionals. • "I'd call it groundbreaking," said Roel Schouwenberg, a senior antivirus researcher at Kaspersky Lab. In comparison, other notable attacks, like the one dubbed Aurora that hacked Google's network and those of dozens of other major companies, were child's play. • But it gets worse. Since reverse engineering chunks of Stuxnet's massive code, senior US cyber security experts confirm what Mr. Langner, the German researcher, told the Monitor: Stuxnet is essentially a precision, military-grade cyber missile deployed early last year to seek out and destroy one real-world target of high importance – a target still unknown. What a story! I mean theory... Once you pop you just can't stop: • • • The word "myrtus" appears in the worm: o an artifact that the compiler left, possibly by accident. o refers to Queen Esther, also known as Hadassah; she saved the Persian Jews from genocide in the 4th century B.C. "Hadassah" means "myrtle" in Hebrew. Sets a registry value of "19790509": o a date o refers to the date Persian Jew Habib Elghanain was executed in Tehran for spying for Israel. The hex 0xDEADF007 appears in the worm: o Symantec suggests it may mean Dead Fool or Dead Foot, a term referring to an airplane engine failure. o "This suggests failure of the targeted system is a possible aim, though whether Stuxnet aims to simply halt the system or blow it up remains unknown." What a story! I mean theory... These markers COULD: • • • Point to Israel as the author. Point to being deliberately planted by someone who wanted to frame Israel Point to being deliberately planted by Israel, who wanted us to think they were planted by someone who wanted to frame Israel. When do you stop? • Deepwater Horizon did have some Siemens PLC systems on it! • Did stuxnet contribute to the Gulf of Mexico oil spill?!?! Stuxnet's Authors: • extremely careful to not leave any traces What a story! I mean theory... • • • We don't know who wrote Stuxnet. o Government o Individual o Research Group We don't know why. o Criminal worm to demonstrate capability o Research efforts o Social/Political We don't know what the target is, or if Stuxnet reached it. o control alarm systems o access controls on doors o motors o conveyor belts o pumps o chemical plants o oil refineries o pipelines o nuclear power plants!?!?! What a story! I mean theory... Stuxnet is sophisticated. It is fun to speculate its purposes. But we do not know the author's true intentions. Questions? Sources http://www.networkworld.com/news/2010/091610-is-stuxnet-the-best-malware.html?page=2 http://www.computerworld.com/s/article/9179618/Iran_was_prime_target_of_SCADA_worm http://www.computerworld.com/s/article/9185419/Siemens_Stuxnet_worm_hit_industrial_systems http://www.symantec.com/connect/blogs/stuxnet-p2p-component http://blogs.technet.com/b/mmpc/archive/2010/07/30/stuxnet-malicious-lnks-and-then-there-was-sality.aspx http://www.internetnews.com/security/article.php/3903541/Patch+Tuesday+Fixes+Another+Stuxnet+Vulner ability.htm http://www.abc.net.au/science/articles/2011/11/01/3353334.htm http://www.schneier.com/blog/archives/2010/10/stuxnet.html http://www.schneier.com/blog/archives/2010/09/the_stuxnet_wor.html http://www.wired.com/threatlevel/2010/10/stuxnet-deconstructed/