Hoover-Security
advertisement

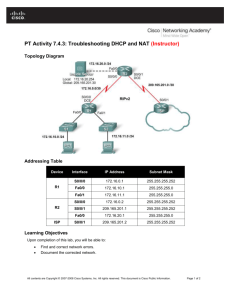
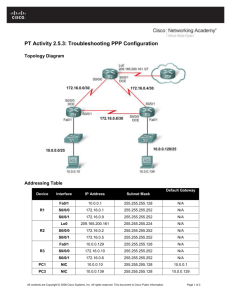
ISP Security Issues in today’s Internet It’s not a nice place anymore ... Course Number Presentation_ID © 1999, Cisco Systems, Inc. 1 The Internet Today • NetAid’s October 9th Event System architected for 60 million hits per hour, one million hits per minute, or just over 16,000 transactions per second to support 50,000,000 users over a multiday event … while under constant cyber-probes and attacks. NetAid was consistently probed and attacked through out the life of the event. It is an example of how today’s Internet networks need to be built - to ride out attacks, maintain the service, collect information on the attack, and counter the attack. Presentation_ID © 1999, Cisco Systems, Inc. 2 The ISP’s World Today Small Businesses Large Enterprises Consumers ISP Professional Office Other ISPs (the Internet) Presentation_ID © 1999, Cisco Systems, Inc. 3 The ISP’s World Today • Changing Threat User Friendly Tools make is easier for the amateur cyberpunks to do more damage E-Commerce provides a monetary motivation Direct attacks on the Internet’s core infrastructure means that the NET is not scared anymore. Source: Placeholder for Notes, etc. 14 pt., bold Presentation_ID © 1999, Cisco Systems, Inc. 4 For example - Smurfing • Newest Denial of Service attack Network-based, fills access pipes Uses ICMP echo/reply packets with broadcast networks to multiply traffic Requires the ability to send spoofed packets • Abuses “bounce-sites” to attack victims Traffic Presentation_ID © 1999, Cisco Systems, Inc. multiplied by a factor of 50 to 200 5 For example - Smurfing ICMP echo (spoofed source address of victim) Sent to IP broadcast address ICMP echo reply Internet Perpetrator Victim Presentation_ID © 1999, Cisco Systems, Inc. 6 For example - Smurfing • Perpetrator has T1 bandwidth available (typically a cracked account), and uses half of it (768 Kbps) to send spoofed packets, half to bounce site 1, half to bounce site 2 • Bounce site 1 has a switched co-location network of 80 hosts and T3 connection to net • Bounce site 2 has a switched co-location network of 100 hosts and T3 connection to net Presentation_ID © 1999, Cisco Systems, Inc. 7 For example - Smurfing • (384 Kbps * 80 hosts) = 30 Mbps outbound traffic for bounce site 1 • (384 Kbps * 100 hosts) = 37.5 Mbps outbound traffic for bounce site 2 • Victim is pounded with 67.5 Mbps (!) from half a T1! • Warning! The newest source of high speed connections are in people’s homes. How many home’s with xDSL and Cable access have any sort of security? Presentation_ID © 1999, Cisco Systems, Inc. 8 Attack Methods—WinNuke 10.1.1.1 Good By Presentation_ID © 1999, Cisco Systems, Inc. 9 Attack Methods—Crack Shareware Presentation_ID © 1999, Cisco Systems, Inc. 10 What do ISPs need to do? • ISPs need to: Protect themselves Help protect their customers from the Internet Protect the Internet from their customers Presentation_ID © 1999, Cisco Systems, Inc. 11 What do ISPs need to do? Security in a is not optional! 2) Secure Firewall, Encryption, Authentication (PIX, Cisco IOS, FW, IPSEC, TACACS+Radius) 5) Manage and Improve Network Operations and Security Professionals 1) ISP’s Security Policy 3) Monitor and Respond Intrusion Detection (i.e. NetRanger) 4) Test Vulnerability Scanning (i.e. NetSonar, SPA) Presentation_ID © 1999, Cisco Systems, Inc. 12 What do ISPs need to do? • Implement Best Common Practices (BCPs) ISP Infrastructure security ISP Network security ISP Services security • Work with Operations Groups, Standards Organisations, and Vendors on new solutions Presentation_ID © 1999, Cisco Systems, Inc. 13 BCP Examples • System Architecture Presentation_ID • Features Use AAA for staff Modular Network Design with Layered Security Turn off unnecessary features Routing Protocol MD5 Route Filters Transaction Logging (SNMP, SYSLOG, etc. ) Anti-Spoof filters or Unicast RPF Peering, Prefix, and Route Flap Filters Premises Security Rate Limiting filters on ICMP (active or scripts) © 1999, Cisco Systems, Inc. 14 Hardware Vendor’s Responsibilities The roll of the hardware vendor is to support the network’s objectives. Hence, there is a very synergistic relationship between the ISP and the hardware vendor to insure the network is resistant to security compromises. Presentation_ID © 1999, Cisco Systems, Inc. 15 Hardware Vendor’s Responsibilities • Cisco System’s Example: Operations People working directly with the ISPs Emergency Reaction Teams (i.e. PSIRT) Developers working with customers on new features Security Consultants working with customers on attacks, audits, and prosecution. Individuals tracking the hacker/phracker communities Presentation_ID © 1999, Cisco Systems, Inc. 16 For Example ... CEF Unicast RPF Routing Table: 210.210.0.0 172.19.0.0 via 172.19.66.7 is directly connected, Fddi 2/0/0 CEF Table: 210.210.0.0 172.19.66.7 172.19.0.0 attached Adjacency Table: Fddi 2/0/0 172.19.66.7 If OK, RPF passed the packet to be forwarded by CEF. Fddi 2/0/0 Fddi 2/0/0 50000603E…AAAA03000800 Customer’s Packets Data Customer’s Packets Unicast RPF IP Header In Data IP Header Out Drop Dest Addr: x.x.x.x Src Addr: 210.210.1.1 RPF Checks to see if the source address’s reverse path matches the input port. Presentation_ID © 1999, Cisco Systems, Inc. 17 For Example ... CEF Unicast RPF Routing Table: 210.210.0.0 172.19.0.0 via 172.19.66.7 is directly connected, Fddi 2/0/0 CEF Table: 210.210.0.0 172.19.66.7 172.19.0.0 attached Adjacency Table: Fddi 2/0/0 172.19.66.7 Fddi 2/0/0 Fddi 2/0/0 50000603E…AAAA03000800 Customer’s Packets Data Unicast RPF IP Header In Out Drop Dest Addr: x.x.x.x Src Addr: 144.64.21.1 RPF Checks to see if the source address’s reverse path matches the input port. Presentation_ID © 1999, Cisco Systems, Inc. If not OK, RPF drops the packet. Data IP Header Spoofed Packets 18 For More Information… URLs Referenced in the Presentation • This presentation http://www.cisco.com/public/cons/isp/document/Hoover-Security.pdf • BCPs for ISPs - Essentials IOS Features Every ISP Should Consider http://www.cisco.com/public/cons/isp/documents/ • Product Security Incident Response Team (PSIRT) http://www.cisco.com/warp/public/707/sec_incident_response.shtml • Improving Security on Cisco Routers Presentation_ID http://www.cisco.com/warp/public/707/21.html © 1999, Cisco Systems, Inc. 19 For More Information… Industry Resources • http://www.icsa.net/library Many security articles by National Computer Security Assoc., and great tutorial on firewalls • ftp://info.cert.org Published warnings and downloadable files of solutions for defeating various types of attacks that have been reported to Computer Emergency Response Team • http://www-ns.rutgers.edu/www-security/reference.html Presentation_ID Llinks to Web sites, mailing lists, standards documents, etc., related to WWW and/or Internet security © 1999, Cisco Systems, Inc. 20 Presentation_ID © 1999, Cisco Systems, Inc. 21