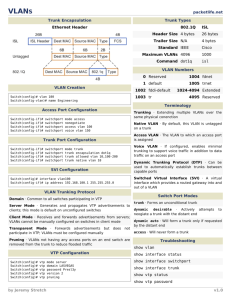
Introduction to VLANs
advertisement

Cabrillo College
CCNP – Multilayer Switching
Introduction to VLANs
Rick Graziani, Instructor
March 27, 2001
1
VLANs
Switched networks that are logically
segmented on an organizational basis
by functions, project teams, or
applications rather than on a physical or
geographical basis
2
VLANs
Can be thought of as a broadcast domain that
exists within a defined set of switches
Provide the segmentation services
traditionally provided by routers
Offer scalability, security, and improved
network management
Routers in VLAN topologies provide
broadcast filtering, security, address
summarization, and traffic flow management.
3
VLANs
What are the issues if these were only separate subnets and not
vlans? To solve this problem, normally the router would only be
attached to one subnet and the hosts on physically separate
subnets, in order to divide the broadcast domains.
4
VLANs
5
VLANs are secure
Whenever a station transmits in a shared
network such as a legacy half-duplex
10BaseT system, all stations attached to the
segment receive a copy of the frame, even if
they are not the intended recipients.
Anyone with such a network sniffer can
capture passwords, sensitive e-mail, and any
other traffic on the shared network.
6
VLANs are secure - Switches
Switches allow for microsegmentation
– Each user that connects directly to a switch
port is on his or her own segment.
• If every device has its own segment
(switchport) then only the sender and receiver
will “see” unicast traffic, unless the switch has
to flood the unicast traffic for that vlan.
• More in a moment!
VLANs contain broadcast traffic
– Only users on the same VLAN will see
broadcasts
7
Side Note - Transparent Bridging
Transparent bridging (normal switching
process) is defined in IEEE 802.1d describing
the five bridging processes of:
–
–
–
–
learning
flooding filtering
forwarding
aging
These will be discussed further in STP
8
Transparent Bridge Process - Jeff Doyle
Receive Packet
Learn source address or refresh aging timer
Is the destination a broadcast, multicast or unknown unicast?
No
Yes
Flood Packet
Are the source and destination on the same interface?
No
Yes
Filter Packet
Forward unicast to correct port
9
Transparent Bridging
Switches will flood unicast traffic out all ports if it does
not have the destination MAC address in its source
address table.
This can be especially true for large flat networks
where switches cannot contain all of the MAC
addresses.
– MAC address table can be 1,024 (or less) and
more than 16,000 addresses depending upon
vendor and model
Addresses will also age out of the source address
table which means the frames will be flooded. This
traffic may include confidential information including
passwords.
– Cisco and Bay default is 5 minutes (common)
– Why so small? Dynamic and current.
10
Changing and viewing the aging timer
Set-based
Switch_1> (enable) set cam agingtime vlan
agingtime_in_msec
Switch_1> (enable) show cam agingtime
VLAN 1 aging time = 300 sec
VLAN 2 aging time = 300 sec
IOS-based
Switch(config)# mac-address-table agingtime seconds [vlan vlan]
Switch# show mac-address-table aging-time
300
11
Show Mac-Address-Table
(Source Address Table)
Set-based
Console> (enable) show cam dynamic
* = Static Entry. + = Permanent Entry. # = System
Entry. R = Router Entry. X = Port Security Entry
VLAN Dest MAC/Route Des
[CoS] Destination Ports…
---- ---------------------- ------------------1
00-a0-c9-66-86-94
2/6 [ALL]
Total Matching CAM Entries Displayed = 1
12
Show Mac-Address-Table
(Source Address Table)
IOS-based
Switch#show mac-address-table dynamic
Non-static Address Table:
Destination Address Address Type VLAN
------------------- ------------ ---00a0.c966.8694
Dynamic
1
... Port
...-----FastEthernet0/5
13
VLANs are secure - Switches
VLANs contain broadcast, multicast
(later) and unknown unicast traffic to the
specific VLAN
14
VLANs control broadcasts
15
VLANs control broadcasts
Broadcast traffic is a necessary evil
– Routing protocols and network services typically
rely on broadcasts
– Multimedia applications may also use broadcast
frames/packets
Each VLAN is its own broadcast domain
– Traffic of any kind cannot leave a VLAN without L3
services (a router)
– Administrators can control the size of a broadcast
domain by defining the size of the VLAN
16
VLANs improve BW utilization
Bandwidth is shared in legacy Ethernet; a
switch improves BW utilization by eliminating
collisions (microsegmentation).
VLANs further improve BW utilization by
confining broadcasts and other traffic
Switches only flood ports that belong to the
source port’s VLAN.
17
VLANs decrease latency
If switches and VLANs were used here instead of
routers, Accounting users would experience less
latency.
18
When NOT to VLAN
19
Types of VLANs
When scaling VLANs in the switch block,
there are two basic methods of defining the
VLAN boundaries:
– End-to-end VLANs (no longer
recommended by Cisco due to
management and STP concerns)
– Local VLANs
20
Types of VLANs
Remember: a one-to-one correspondence
between VLANs and IP subnets is strongly
recommended!
– Typically, this results in VLANs of 254
hosts or less. (Depending upon the
subnetting scheme used.)
21
End-to-End VLANs
Users are grouped into VLANs independent
of physical location and dependent on group
or job function.
All users in a VLAN should have the same
80/20 traffic flow patterns.
As a user moves around the campus, VLAN
membership for that user should not change.
Each VLAN has a common set of security
requirements for all members.
22
End-to-End VLANs
23
Local VLANs
As many corporate networks have moved to
centralize their resources, end-to-end VLANs
became more difficult to maintain.
Users are required to use many different
resources, many of which are no longer in
their VLAN.
Because of this shift in placement and usage
of resources, VLANs are now more frequently
being created around geographic boundaries
rather than commonality boundaries.
24
Local VLANs
Can span a geographic location as large as
an entire building or as small a one switch
20/80 rule in effect with 80 percent of the
traffic remote to the user and 20 percent of
the traffic local to the user
A user must cross a L3 device in order to
reach 80 percent of the resources
– However, this design allows the network to
provide for a deterministic, consistent
method of accessing resources.
25
VLAN Types
The two common approaches to assigning
VLAN membership are:
– Static VLANs
– Dynamic VLANs
26
Static VLANs
Also referred to as port-based membership
VLAN assignments are created by assigning
ports to a VLAN
As a device enters the network, the device
automatically assumes the VLAN of the port.
– If the user changes ports and needs access to the
same VLAN, the network administrator must
manually make a port-to-VLAN assignment for the
new connection.
27
Static VLANs
28
Static VLANs
The port is assigned to a specific VLAN
independent of the user or system attached
to the port.
The port cannot send or receive from devices
in another VLAN without the intervention of a
L3 device.
– The device that is attached to the port likely has
no understanding that a VLAN exists.
– The device simply knows that it is a member of a
subnet. (ip address and subnet mask)
29
Static VLANs
Switch is responsible for identifying that the
information came from a specific VLAN and
for ensuring that the information gets to all
other members of the VLAN.
– The switch is further responsible for
ensuring that ports in a different VLAN do
not receive the information.
30
Static VLANs
This approach is quite simple, fast, and easy
to manage in that there are no complex
lookup tables required for VLAN
segmentation.
If port-to-VLAN association is done with an
application-specific integrated circuit (ASIC),
the performance is very good.
An ASIC allows the port-to-VLAN mapping to
be done at the hardware level.
31
Configuring Static VLANs
IOS-Based Switch
Switch# vlan database
Switch(vlan)# vlan vlan-num name vlan-name
Switch(config)#interface fastethernet 0
Switch(config-if)# switchport access vlan
vlan-num
32
Configuring Static VLANs
Set-Based Switch
Switch(enable) set vlan vlan-num [name name]
Switch(enable) set vlan vlan-num
mod/num_list
Switch(enable) set vlan 10 2/19-24
33
Dynamic VLANs
Created through the use of software
packages such as CiscoWorks 2000
Allow for membership based on the MAC
address of the device
As a device enters the network, the device
queries a database for VLAN membership
34
Dynamic VLANs
35
Dynamic VLANs
With a VLAN Management Policy Server
(VMPS), you can assign switch ports to
VLANs dynamically, based on the source
MAC address of the device connected to the
port.
When you move a host from a port on one
switch in the network to a port on another
switch in the network, the switch assigns the
new port to the proper VLAN for that host
dynamically.
36
Dynamic VLANs
When you enable VMPS, a MAC address-toVLAN mapping database downloads from a
Trivial File Transfer Protocol (TFTP) server
and VMPS begins to accept client requests.
– If you reset or power cycle the Catalyst
5000, 4000, 900, 3500, or 6000 Series
Switch, the VMPS database downloads
from the TFTP server automatically and
VMPS is reenabled.
37
Dynamic VLANs
VMPS opens a UDP socket to communicate
and listen to client Catalyst requests.
When the VMPS server receives a valid
request from a client Catalyst, it searches its
database for a MAC address-to-VLAN
mapping.
38
Access and Trunk Links
39
Access Links
An access link is a link on the switch that is a
member of only one VLAN.
This VLAN is referred to as the native VLAN
of the port.
– Any device that is attached to the port is
completely unaware that a VLAN exists.
40
Trunk Links
A trunk link is capable of supporting multiple
VLANs.
Trunk links are typically used to connect
switches to other switches or routers.
Switches support trunk links on both Fast
Ethernet and Gigabit Ethernet ports.
41
Access and Trunk Links
42
Trunk Links
Without trunking
With trunking
43
Trunking
A trunk is a point-to-point link that supports
several VLANs
A trunk is to saves ports when creating a link
between two devices implementing VLANs
Trunking covered in more detail in next
section
44
Trunk Links
A trunk link does not belong to a specific
VLAN.
– Acts as a conduit for VLANs between
switches and routers.
The trunk link can be configured to transport
all VLANs or to transport a limited number of
VLANs.
A trunk link may, however, have a native
VLAN.
– The native VLAN of the trunk is the VLAN
that the trunk uses if the trunk link fails for
any reason.
45
Trunk Links
In Ethernet, the switch has two methods of
identifying the VLAN that a frame belongs to:
– ISL – InterSwitch Link
• (Cisco proprietary)
– IEEE 802.1Q (standards-based)
• aka, dot1q
46
VLAN Identification
ISL - This protocol is a Cisco proprietary
encapsulation protocol for interconnecting
multiple switches; it is supported in switches
as well as routers.
Even though it’s Cisco proprietary, ISL is not
natively supported by the Catalyst 4000.
– The L3 blade does give the Cat4000s
router two ISL-capable ports (Gig 1 and
Gig 2).
47
VLAN Identification
IEEE 802.1Q - This protocol is an IEEE
standard method for identifying VLANs by
inserting a VLAN identifier into the frame
header.
This process is referred to as frame tagging.
– Note: In practice, both ISL and dot1q are
called frame tagging
48
VLAN Identification
802.10 - This standard is a Cisco proprietary
method of transporting VLAN information
inside the standard 802.10 frame (FDDI).
– The VLAN information is written to the
security association identifier (SAID)
portion of the 802.10 frame.
– This method is typically used to transport
VLANs across FDDI backbones.
49
VLAN Identification
LAN Emulation (LANE) - LANE is an ATM
Forum standard that can be used for
transporting VLANs over Asynchronous
Transfer Mode (ATM) networks.
50
VLAN Identification
Both 802.1Q and ISL do “Explicit tagging.” 802.1Q uses an
“internal tagging process” that modifies the existing Ethernet
frame with the VLAN ID. This allows 802.1Q frames to work on
both access and trunk links as it appears to be a standard
Ethernet frame. ISL uses external tagging process, where the
original frame is not altered but it is encapsulated with a new 26byte ISL header (tag). This means that only ISL aware devices
can interpret this frame.
51
ISL (Frame Encapsulation)
Ethernet Frame
1500 bytes plus 18 byte header
(1518 bytes)
Standard NIC cards and networking devices don’t understand
this giant frame. A Cisco switch must remove this
encapsulation before sending the frame out on an access link.
52
ISL
An Ethernet frame is encapsulated with a
header that transports VLAN IDs
It adds overhead to the packet as a 26-byte
header containing a 10-bit VLAN ID.
In addition, a 4-byte cyclic redundancy check
(CRC) is appended to the end of each frame.
– This CRC is in addition to any frame
checking that the Ethernet frame requires.
53
ISL - Selected fields
DA - Destination Address
The DA field of the ISL packet is a 40 bit destination address. This
address is a multicast address and is currently set to be:
0x01_00_0C_00_00. The first 40 bits of the DA field signal the
receiver that the packet is in ISL format.
TYPE - Frame Type
The TYPE field indicates the type of frame that is encapsulated and
could be used in the future to indicate alternative
encapsulations. The following TYPE codes have been defined:
Code Meaning
0000 Ethernet
0001 Token-Ring
0010 FDDI
0011 ATM
54
ISL - Selected fields
SA - Source Address
The SA field is the source address field of the ISL packet. It should
be set to the 802.3 MAC address of the switch port transmitting
the frame. It is a 48-bit value. The receiving device may ignore
the SA field of the frame.
VLAN - Virtual LAN ID
The VLAN field is the virtual LAN ID of the packet. It is a 15-bit
value that is used to distinguish frames on different VLANs. This
field is often referred to as the "color" of the packet
BPDU - BPDU and CDP Indicator
The BPDU bit is set for all bridge protocol data units that are
encapsulated by the ISL packet. The BPDUs are used by the
spanning tree algorithm to determine information about the
topology of the network.
55
ISL - Selected fields
ENCAP FRAME - Encapsulated Frame
The ENCAP FRAME is the encapsulated frame, including its own
CRC value, completely unmodified. The internal frame must have
a CRC value that is valid once the ISL encapsulation fields are
removed. The length of this field can be from 1 to 24575 bytes
long to accommodate Ethernet, Token Ring, and FDDI frames. A
receiving switch may strip off the ISL encapsulation fields and use
this ENCAP FRAME as the frame is received, associating the
appropriate VLAN and other values with the received frame as
indicated above for switching purposes.
CRC - Frame Checksum
The CRC is a standard 32-bit CRC value calculated on the entire
encapsulated frame from the DA field to the ENCAP FRAME field.
The receiving MAC will check this CRC and can discard packets
that do not have a valid CRC on them. Note that this CRC is in
addition to the one at the end of the ENCAP FRAME field.
56
802.1q
NIC cards and networking devices can understand this “baby
giant” frame (1522 bytes). However, a Cisco switch must
remove this encapsulation before sending the frame out on an
access link.
SA and DASA and
802.1q
DA
MACs
MACsTag
Type/Length
Field
Data (max 1500
bytes)
2-byte TPID
Tag Protocol Identifier
2-byte TCI
Tag Control Info (includes
VLAN ID)
CRC
New
CRC
57
802.1q
Significantly less overhead than the ISL
As opposed to the 30 bytes added by ISL,
802.1Q inserts only an additional 4 bytes into
the Ethernet frame
58
802.1q
A 4-byte tag header containing a tag protocol
identifier (TPID) and tag control information
(TCI) with the following elements:
59
802.1q
TPID
A 2-byte TPID with a fixed value of 0x8100. This value
indicates that the frame carries the 802.1Q/802.1p
tag information.
TCI
A TCI containing the following elements:
- Three-bit user priority (8 priority levels, 0 thru 7)
- One-bit canonical format (CFI indicator), 0 =
canonical, 1 = noncanonical, to signal bit order in
the encapsulated frame
(www.faqs.org/rfcs/rfc2469.html - “A Caution On
the Canonical Ordering of Link-Layer Addresses”)
- Twelve-bit VLAN identifier (VID)-Uniquely identifies
the VLAN to which the frame belongs, defining
4,096 VLANs, with 0 and 4095 reserved.
60
Trunk Links - once again...
Without trunking
With trunking
61
Trunking
Before attempting to configure a VLAN trunk
on a port, you should to determine what
encapsulation the port can support.
Set-based switches:
switch> (enable) show port capabilities
– Note: the Catalyst 4000 does not support ISL
(except the router blade)
IOS-based switches:
switch(config-if)# switchport trunk
encapsulation ?
– (only way I know)
62
Next week...
More Trunking next week, along with
VTP (VLAN Trunking Protocol)
Next few slides, review of vlan
commands
63
Creating VLANs - access ports
IOS-Based
Switch(config)# interface fastethernet mod/num
Switch(config-if)# switchport access vlan vlan-num
Remove
Switch(config-if)# no switchport access vlan vlan-num
Set-Based
Switch> (enable) set vlan vlan-num mod/num_list
Remove
Switch> (enable) clear vlan vlan-num
When you clear a VLAN, all ports assigned to that
VLAN become inactive and can be reactivated using
set vlan vlan-num state active or by assigning the
64
ports to another vlan.
Naming a VLAN
IOS-Based
Switch# vlan database (not in global config!)
Switch(vlan)# vlan vlan-num name vlan-name
Set-Based
Switch> (enable) set vlan vlan-num name vlan-name
65
Viewing VLAN information
IOS-Based
Switch# show vlan
Switch# show vlan brief
Set-Based
Switch> (enable) show vlan
Switch> (enable) show interface
66
IOS-based
CIS-2900-ServerFarm>show vlan
VLAN Name
---- -------------------------------1
default
2
VLAN0002
3
VLAN0003
4
VLAN0004
5
VLAN0005
10
VLAN0010
50
SeverFarm
1002 fddi-default
<text omitted>
Status
Ports
--------- ----------------active
active
active
active
active
active
active
Fa0/1, Fa0/2, Fa0/3, Fa0/4,
Fa0/5, Fa0/6, Fa0/7, Fa0/8,
<output omitted)
Fa0/21, Fa0/22
active
VLAN Type SAID
MTU
Parent RingNo BridgeNo Stp BrdgMode Trans1
Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ----1
enet 100001
1500 0
0
<Text omitted>
67
IOS-based
CIS-2900-ServerFarm>show vlan brief
VLAN Name
---- -------------------------------1
default
2
VLAN0002
3
VLAN0003
4
VLAN0004
5
VLAN0005
10
VLAN0010
50
SeverFarm
1002
1003
1004
1005
fddi-default
token-ring-default
fddinet-default
trnet-default
Status
Ports
--------- ----------------active
active
active
active
active
active
active
Fa0/1, Fa0/2, Fa0/3, Fa0/4,
Fa0/5, Fa0/6, Fa0/7, Fa0/8,
<output omitted)
Fa0/21, Fa0/22
active
active
active
active
68
Set-based
CIS-4003-MainSwitch> show vlan
VLAN Name
---- -------------------------------1
default
2
VLAN0002
3
VLAN0003
4
VLAN0004
5
VLAN0005
10
VLAN0010
50
SeverFarm
1002 fddi-default
1003 token-ring-default
1004 fddinet-default
1005 trnet-default
VLAN
---1
2
3
4
Type
----enet
enet
enet
enet
SAID
---------100001
100002
100003
100004
MTU
----1500
1500
1500
1500
Parent
------
RingNo
------
Status
IfIndex Mod/Ports
--------- ------- -------------active
4
2/1-12
active
9
2/13-36
active
10
2/37-40
active
11
2/41-44
active
60
active
68
active
62
2/47
active
5
active
8
active
6
active
7
BrdgNo
------
Stp
----
BrdgMode
--------
Trans1
-----0
0
0
0
Trans2
-----0
0
0
0
69
IOS-based
Switch# show running-config
!
interface FastEthernet0/1
switchport access vlan 50
!
interface FastEthernet0/2
switchport access vlan 50
!
interface FastEthernet0/3
switchport access vlan 50
!
interface FastEthernet0/4
switchport access vlan 50
70
Set-based
Switch>(enable)show config
#vtp
set vtp domain CIS-classrooms
set vlan 1 name default type ethernet mtu 1500
said 100001 state active
set vlan 50 name SeverFarm type ethernet mtu 1500
said 100050 state active
…
#module 2 : 48-port 10/100BaseTx Ethernet
set vlan 2
2/13-36
set vlan 3
2/37-40
set vlan 4
2/41-44
set vlan 10
2/48
set vlan 50
2/47
71
Trunking continued (Part II)
A trunk is a point-to-point link between:
– Two switches
– A switch and a router
Trunks carry traffic of multiple VLANs
Cisco supports one or both of these
Trunking protocols:
– IEEE 802.1Q (dot1q)
– ISL (Cisco proprietary)
72
Trunking
Cisco offers DTP and DISL which negotiates
trunking between two ends of a link and the
compatible trunking protocol (DTP).
– Dynamic Trunking Protocol (DTP) manages trunk
negotiation on a Catalyst Supervisor engine
software release 4.2 and later
• Supports both 802.1Q and ISL
– Dynamic Inter-Switch Link (DISL) was used prior
to release 4.2.
• Used only with ISL.
Set-based switches only (as far as I know)
73
DTP and DISL
Cisco also adapted its Dynamic ISL (DISL)
protocol and turned it into Dynamic Trunking
Protocol (DTP).
DISL can negotiate ISL trunking on a link
between two devices; DTP can, in addition,
negotiate the type of trunking encapsulation
(802.1q or ISL) that will be used as well.
This is an interesting feature as some Cisco
devices support only ISL or 802.1q, whereas
some are able to run both.
74
DTP Modes
When configuring a port for trunking, two parameters
can be set: the trunking mode and the
encapsulation type (if DTP is supported on that
port).
• The trunking mode defines how the port will
negotiate the set up of a trunk with its peer port.
• The encapsulation type allows the user to
specify whether 802.1q or ISL should be used
when setting up the trunk. Of course, the
parameter is only relevant if the module you are
using is able to use both.
75
Configuring Trunking
Fast Ethernet and Gigabit Ethernet
trunking modes:
– On
– Off
– Desirable
– Auto Nonegotiate
Switch(enable) set trunk mod/port
[on | off |desirable | auto | nonegotiate]
[isl | dot1q | dot10 | lane | negotiate]
vlan range
76
Trunking
Mode
DTP
frames
sent
Description
Final state (local port)
on
The local port advertises the
YES,
remote it is going to the
periodic
trunking state.
Trunking, unconditionally.
auto
The local port advertises the
YES, remote it is able to trunk but
periodic does not request to go to the
trunking state.
The port will end up in trunking
state only if the remote wants to,
that is, the remote mode is on or
desirable.
desirable
nonegotiate
off
If the port detects that the remote
The local port advertises the
is able to trunk (remote in on,
YES,
remote it is able to trunk and desirable or auto mode), it will
periodic
ask to go to the trunking state. end up in trunking state, else will
stay non-trunking.
NO
YES
Local port goes to
unconditionally trunking, with
Trunking, unconditionally.
no DTP notification to the
remote.
Disable trunking on the port.
DTP frames are only sent out
when the port is transitioning
to non-trunking.
Non trunking, unconditionally.
77
Configuring Trunking
On
This mode puts the port into permanent
trunking.
The port becomes a trunk port even if the
neighboring port does not agree to the
change.
The on state does not allow for the
negotiation of an encapsulation type.
– You must, therefore, specify the
encapsulation in the configuration
78
Configuring Trunking
Off
This mode puts the port into permanent
nontrunking mode and negotiates to convert
the link into a nontrunk link.
The port becomes a nontrunk port even if the
neighboring port does not agree to the
change.
79
Configuring Trunking
Desirable
This mode makes the port actively attempt to
convert the link to a trunk link. The port
becomes a trunk port if the neighboring port
is set to on, desirable, or auto mode.
80
Configuring Trunking
Auto
This mode makes the port willing to convert
the link to a trunk link.
The port becomes a trunk port if the
neighboring port is set to on or desirable
mode.
This is the default mode for Fast and Gigabit
Ethernet ports.
– if the default setting is left on both sides of
the trunk link, the link will not become a
trunk
– Do not want both sides to be set to Auto 81
Configuring Trunking
Nonegotiate
This mode puts the port into permanent
trunking mode but prevents the port from
generating Dynamic Trunking Protocol (DTP)
frames.
– You must configure the neighboring port
manually as a trunk port to establish a
trunk link.
82
Encapsulation Type
Encapsulation
type
ISL
dot1q
Description
Sets the port encapsulation to ISL.
Sets the port encapsulation to 802.1q.
This encapsulation is only available in auto or desirable trunking
modes.
negotiate
If the remote has a negotiate encapsulation type, the trunk will
eventually be set up with ISL.
If the remote is configured for ISL or 802.1q or only able to do
ISL or 802.1q, then the trunking encapsulation used will be the
one of the remote port.
Switch(enable) set trunk mod/port
[on | off |desirable | auto | nonegotiate]
[isl | dot1q | dot10 | lane | negotiate]
vlan range
83
Configuring Trunking
For trunking to be autonegotiated on Fast
Ethernet or Gigabit Ethernet ports, the ports
must be in the same VTP domain.
However, you can use “on” or “nonegotiate”
mode to force a port to become a trunk, even
if it is in a different domain.
84
Configuring Trunking
IOS-Based Switch
Switch(config)# interface fastethernet 0
Switch(config-if)# switchport mode [access | multi | trunk]
Switch(config-if)# switchport trunk encapsulation {isl|dot1q}
Switch(config-if)# switchport trunk allowed vlan remove vlan-list
Switch(config-if)# switchport trunk allowed vlan add vlan-list
By default, all VLANS, 1-1005 transported automatically
85
Configuring Trunking
Set-Based Switch
Switch(enable) set trunk mod/port [on | off |desirable |
auto | nonegotiate]
[isl | dot1q | dot10 | lane |
negotiate] vlan range
Switch(enable) clear trunk mod/port vlan-range
By default, all VLANS, 1-1005 transported automatically
86
87
IOS 1924 Switch
interface FastEthernet0/22
switchport access vlan 50
!
interface FastEthernet0/23
port group 1 distribution destination
switchport mode trunk
switchport trunk encapsulation dot1q
!
interface FastEthernet0/24
port group 1 distribution destination
switchport mode trunk
switchport trunk encapsulation dot1q
!
88
Catalyst 4003
set trunk 2/45 on dot1q 1-1005
set trunk 2/46 on dot1q 1-1005
set trunk 2/48 on dot1q 1-1005
(to 4003)
(to 4003)
(to Rtr)
By default, all VLANS, 1-1005 transported
automatically
89
Router
interface FastEthernet0/1.1
encapsulation dot1Q 1
ip address 172.30.1.1 255.255.255.0
ip access-group 100 in
ip helper-address 172.30.50.50
no ip directed-broadcast
!
interface FastEthernet0/1.2
encapsulation dot1Q 2
ip address 172.30.2.1 255.255.255.0
ip access-group 102 in
ip helper-address 172.30.50.255
ip helper-address 172.30.50.10
no ip directed-broadcast
90
VLAN Trunking Protocol
VTP maintains VLAN configuration
consistency across the entire network.
VTP is a messaging protocol that uses Layer
2 trunk frames to manage the addition,
deletion, and renaming of VLANs on a
network-wide basis.
Further, VTP allows you to make centralized
changes that are communicated to all other
switches in the network.
91
VTP
Create VLANs on the VTP Server
Those VLANs get sent to other client
switches
On the client switches, you can now
assign ports to those vlans.
Cannot create vlans on the client
switches like you could previously
before configuring the switch to be a
VTP client.
92
VTP Benefits
93
VTP
All switches in the same management
domain share their VLAN information with
each other, and a switch can participate in
only one VTP management domain.
Switches in different domains do not share
VTP information.
Using VTP, switches advertise:
– Management domain
– Configuration revision number
– Known VLANs and their specific parameters
94
VTP
Switches can be configured not to accept
VTP information.
These switches will forward VTP information
on trunk ports in order to ensure that other
switches receive the update, but the switches
will not modify their database, nor will the
switches send out an update indicating a
change in VLAN status.
– This is referred to as transparent mode.
95
VTP
By default, management domains are
set to a nonsecure mode, meaning that
the switches interact without using a
password.
Adding a password automatically sets
the management domain to secure
mode.
– A password must be configured on every
switch in the management domain to use
secure mode.
96
VTP
The VTP database contains a revision
number.
Each time a change is made, the switch
increments the revision number
97
VTP
A higher configuration revision number
indicates that the VLAN information that is
being sent is more current then the stored
copy.
Any time a switch receives an update that has
a higher configuration revision number, the
switch will overwrite the stored information
with the new information being sent in the
VTP update.
98
VTP Modes
Switches can operate in any one of the
following three VTP modes:
– Server
– Client
– Transparent
99
VTP Modes
Server - If you configure the switch for server
mode, you can create, modify, and delete
VLANs, and specify other configuration
parameters (such as VTP version and VTP
pruning) for the entire VTP domain.
VTP servers:
– advertise their VLAN configuration to other
switches in the same VTP domain
– synchronize the VLAN configuration with other
switches based on advertisements received over
trunk links.
– Recommended you have at least 2 VTP servers in
case one goes down
This is the default mode on the switch.
100
VTP Modes
Client - VTP clients behave the same
way as VTP servers. However, you
cannot create, change, or delete VLANs
on a VTP client.
101
VTP Modes
Transparent - VTP transparent switches do
not participate in VTP.
A VTP transparent switch does not advertise
its VLAN configuration, and does not
synchronize its VLAN configuration based on
received advertisements.
– However, in VTP Version 2, transparent switches
do forward VTP advertisements that the switches
receive out their trunk ports.
102
Configuring VTP
103
Configuring VTP
IOS-Based Switch
Switch# vlan database
Switch(vlan)# vtp domain domain-name
Switch(vlan)# vtp {server | client | transparent}
Optional:
Switch(vlan)# vtp password password
Switch(vlan)# vtp v2-mode (version2)
Example:
ALSwitch# vlan database
ALSwitch(vlan)# vtp domain corp
ALSwitch(vlan)# vtp client
104
Configuring VTP
Set-Based Switch
Switch(enable) set vtp [domain domain-name] [mode {server
| client | transparent}[password password]
Switch(enable) set vtp v2 enable (version 2)
Example:
DLSwitch(enable) set vtp domain corp
DLSwitch(enable) set vtp mode server
105
VTP Pruning
VTP pruning enhances network bandwidth
use by reducing unnecessary flooding of
traffic, such as broadcast, multicast,
unknown, and flooded unicast packets.
VTP pruning increases available bandwidth
by restricting flooded traffic to those trunk
links that the traffic must use to access the
appropriate network devices.
By default, VTP pruning is disabled.
106
VTP Pruning
107
VTP Pruning
Enabling VTP pruning on a VTP server
enables pruning for the entire management
domain.
VTP pruning takes effect several seconds
after you enable it.
By default, VLANs 2 through 1000 are
pruning eligible.
– VLAN 1 is always pruning ineligible, so traffic from
VLAN 1 cannot be pruned.
– You have the option to make specific VLANs
pruning eligible or pruning ineligible on the device.
108
Configuring VTP Pruning
IOS-Based Switch
Switch# vlan database
Switch(vlan)# vtp pruning
Remove VLANs from being pruned:
Switch(config-if)# switchport trunk pruning vlan
remove vlan-list
By default, all Vlans pruned in management domain
109
Configuring VTP Pruning
Set-Based Switch
Switch(enable) set vtp pruning enable
Optional:
Switch(enable) set vtp pruneeligible vlan-range
Switch(enable) clear vtp pruning vlan-range
By default, all Vlans pruned in management domain.
110