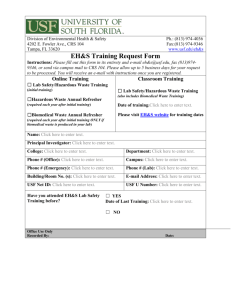
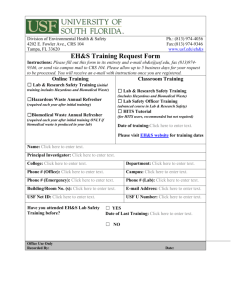
Louis de la Parte Florida Mental Health Institute
advertisement

USF IT Security HIPAA Practice Ensuring IT Security: Policies, Training &Technology All USF workforce members utilizing/ coming in contact with HIPAA Protected Health Information (PHI) must complete this training program and pass the security quiz at the end of Part 4. The purpose of this training is to provide USF faculty & staff information on: – USF data security requirements & procedures – The Privacy Rule of the Health Insurance Portability and Accountability Act (HIPAA) – The HITECH provisions of the ARRA Act Part 1 General Network Information and Security Procedures Accessing the USF Network USF Computer Network USF employees work on computers that are linked through a network that connects all computers at the University. The network allows users to share computing resources and increases efficiency for all computer users. A log-in ID and a secure password are needed to allow you to access this system. USF Computer Network With an ID and password, you are able to: Use email Access shared files & information stored in databases Use hardware such as printers and scanners Use software such as web browsers & virus protection programs. Secure Log-in ID The USF Information Technologies (IT) Office will help you establish a log-in ID that will be a unique identifier linking you to all of your computer transactions. Secure Log-in ID Like a fingerprint, your ID can be traced for all authorized and unauthorized activities conducted on the USF network. Secure Password You will need to establish a secure password to ensure that you and only you can access your network account and files. Your secure password should NEVER be shared with others, including co-workers or family members. Secure Password To maximize security, passwords must be at least eight characters long and contain 3 of the following 4 types of characters: upper case letters, lower case letters, numbers; or special characters such as ! # &. Example: GoBulls2! Please don’t select this as your own password – make up one yourself! Password Aging All users will be asked to change their network password every 6 months. When it is time to change your password, you will be notified with a pop-up message when logging in. If you do not change your password in a timely manner, your account will be temporarily locked. Appropriate Use All USF users sign a statement agreeing to use the USF computers and network only to conduct activities related to the mission and business purposes of the University. Closing Accounts All USF computer accounts are automatically closed when employment ends. Some transitional services (such as auto-forwarding of e-mail messages) may be offered as allowed by USF policy. USF Network Security General Network Security It is very important to protect all computer users at USF from loss or corruption of files and data on the network. Network security is maintained through procedures and technical tools designed to prevent negative events like viruses, intrusion, and data loss. These negative events have the potential to harm everyone connected within our computer network. What is a computer virus? A computer virus is a bit of computer programming code that instructs the computer to do something you did not intend for it to do. The virus is usually invisible to the user until AFTER it has attached itself to the computer. How do you get a computer virus? Most computer viruses enter a computer from program or file “downloads” (for example, email attachments) or from transfers from external disks (floppies, USB drives). Although all USF PCs have a virus protection program installed, we all must be VERY CAREFUL about what we download to our computers. Are viruses dangerous? Some viruses are simply a nuisance, but others can seriously harm the network and permanently damage computers and data. The cost of restoring the system after a virus attack is very high in both time and money. How do viruses work? Some viruses open pathways or holes in the system to provide access for later intrusion into the network. Some viruses and intrusions are more damaging than others, but all of them represent a hole in the security of the network. An intruder may not be interested in what is on your computer, but may be searching for an unprotected point of access to the network. A virus may even send sensitive information from your computer to another unauthorized location. USF E-mail Policies Access to E-mail USF and the University has established an electronic mail (e-mail) system to improve communication and facilitate the important work at USF. E-mail may be accessed directly from USF network computers, or remotely from other locations (e.g. home computer) through the USF web-server, using a login ID and secure password. Appropriate Use All communications using the USF e-mail system should be courteous and professional and should comply with USF anti-harassment policies, i.e., unwelcome, offensive or otherwise inappropriate messages are prohibited. The USF e-mail system may not be used for: – lobbying activities – political or religious causes – private, commercial ventures E-mail Messages are Public Records All e-mail created, transmitted, and stored in the USF e-mail system are the property of USF and become part of the public record of the University. Your e-mail messages may be released by the University upon receipt of a public records request. If you don’t want to read about it in the newspaper, don’t put it in email. E-mail Monitoring USF reserves the right to review, audit, intercept, access, and disclose email. However, your email will be treated as confidential and will be accessed only when necessary. Remote Access Remote Access For PC users, remote access to the USF Network for purposes other than email is provided through a Microsoft Remote Desktop Gateway server located on campus. This enables a secure encrypted connection directly to your USF desktop computer. Macintosh users, and others with special requirements, may request the use of the GoToMyPC remote access software. GoToMyPC also uses encryption to transfer information in a secure manner. An application to establish a GoToMyPC account may be obtained from the CBCS Administrative Office. What is encryption? Encryption is the conversion of data into a form that cannot be easily understood by unauthorized people. An encrypted computer will require you to enter one additional password as the PC or laptop boots up. Laptop Security All USF owned laptops (i.e., those that have a USF Property barcode tag) must have their entire hard disk drive encrypted. Laptops will be encrypted by the IT staff during the initial setup of all new purchases. Why is laptop encryption required? Because of the portability of laptops, the chances of a lost or stolen laptop are higher than an office-based work station. Thus, laptop encryption is used to protect our confidential data. If only it had been encrypted… A thief who stole a laptop from UC Berkeley might have walked off with more than a computer. The thief wandered into a building and snatched the laptop off a desk. The laptop contained personal data, on more than 100,000 UC Berkeley alumni or applicants, such as their Social Security numbers, birth dates and addresses. The school had to notify ALL 100,000 consumers who might have had their data compromised, some whom had graduated as long ago as 1976! •Adapted from article by: • MICHAEL LIEDTKE, AP Business Writer What do I do if my laptop is stolen or lost? Immediately contact the IT Office at USF and report the loss. The IT staff will help you secure sensitive data, investigate and document the loss, and report the incident to the proper authorities. Adding New Equipment to the Network If you purchase new computer equipment and want it connected to the USF network, it must comply with USF standards and be approved prior to purchase by the IT department. If you purchase new equipment.. •Contact the IT Office at USF for additional information or go to the policy section of the IT website: •USF IT Security Policies and Standards Part 2 USF Security Policies and Procedures Part 2 of this training program provides an overview of USF computer security policies and procedures. Basic Principles Faculty and staff at USF often use sensitive and confidential data to conduct research and evaluation studies. Data security is not only an obligation of individual researchers, but also of the University, it’s Colleges and Institutes as academic entities. Potential Dangers Because USF stores confidential information, our data systems must be protected against: Internet hackers Access by unauthorized users Improper printing or distribution of protected electronic information Inappropriate use or access by employees Other threats to protected information Risk Assessment To enhance the security of our data, USF systematically monitors its network for intrusions, security incidents, and inappropriate activity. USF also conducts periodic audits of all PC’s and network devices. Security Infrastructure Our security infrastructure includes: clear policies and procedures secure facilities and equipment shared responsibility for information security among faculty and staff Information Security The USF security infrastructure includes the: – Information Security Officer (ISO) – Information Security Coordinator (ISC) – Information Security Relationship Manager – Data Network Committee – Information Security Liaison to the Dean Information Security Officer Our ISO, Dennis Guillette, has primary responsibility and authority for the security of the USF Information Systems. Information Security Coordinator Steve Gammon is the IT Security Coordinator. He works with the ISO to carry out the information security policies and procedures. USF IT Relationship Manager Alex Campoe acts as the Relationship Manager between USF IT and CBCS for all issues needing escalation between the two entities Data Network Committee (DNC) The DNC strives to provide reasonable data access for research, while ensuring protection of sensitive information against security breaches. The DNC includes faculty and staff from all USF units. PSRDC Director Charles Dion chairs the Data Network Committee. Dean’s Office Liaison Dr. Catherine Batsche, Associate Dean, serves as the Dean’s liaison to the Data Network Committee. Part 3 Basic Information for All Employees What is HIPAA? HIPAA stands for the Health Insurance Portability and Accountability Act. Congress passed HIPAA in 1996 to make health insurance eligibility “portable” from one employer to the next when employees change jobs or have a change in family status. Congress passed HITECH in 2009 significantly affected HIPAA, including changes to security and privacy rules, increased enforcement and more severe penalties HIPAA establishes a civil right to the protection of personal health information through the U.S. Department of Health and Human Services. Health Information is any information created or received that relates to the past, present, or future physical or mental health of an individual. What is Protected Health Information? Protected Health Information (PHI) is any information that contains data that may be used to directly or indirectly identify an individual. Elements that can make Health Information identifiable: Name Address/geographic info Telephone # Email address Finger or voice prints Social Security # Vehicle I.D./device serial # Health plan # Certificate/license # Names of relatives Name of employer Fax number Birthdate; other dates Photo image/x-rays Internet IP address Web URL Medical record # Account # Does USF Have PHI data? Yes, we house private information for individuals receiving services through Medicaid, Medicare, as well as mental health and substance abuse services. These data sets contain names, Social Security numbers, addresses, patient ID numbers, and other identifiers and are protected health information. PHI is protected in any form: database or computer files email conversations documents hand-written notes student logs Can PHI be used in research? Yes. PHI may be used for research with the express authorization of the individual or through other measures designed to protect the privacy of the individual. What is the impact on USF? USF must provide as good, or better, security for sensitive data than the agencies and providers from whom we obtain the data. Non-compliance with HIPAA can result in: Civil penalties with fines up to $100/violation Criminal penalties with 1 to 10 years in jail and $50,000 - $250,000 fine for wrongful disclosure. Breach Notification Breach generally is the unauthorized acquisition, access, use or disclosure of PHI. Breach Notification – must provide notice, via first class mail, to the affected person(s) within 60 days of the breach. In any case in which 500 or more persons are affected by a breach, notice to major media outlets must occur. How does USF protect PHI data? Information security is the key to protecting PHI data. USF has developed: 1. policies and procedures on Information Technology & Security 2. training activities for employees 3. secure technology enhancements and risk assessment procedures. Policies USF has security policies addressing: Data procurement and use Data access and security Security incident reporting Regular review of systems activity For more information on specific policies, please contact USF IT or go to the policy webpage: USF Policies and Standards USF Training We provide training through mandatory, periodic, basic training for all USF faculty and staff on security procedures and through specialized training for USF faculty and staff who use data that are subject to HIPAA guidelines. USF Technology Security USF has implemented several technological enhancements to address security concerns. USF Technology Security We have installed a Firewall to protect our network. A firewall is computer hardware and/or software that limit access to a computer network from an outside source. Firewalls are used to prevent computer hackers from getting into computer systems. USF Technology Security Restructured the USF computer network to increase security Implemented the use of Microsoft’s Remote Desktop Gateway or the GoToMyPC software for external data access to HIPAA ePHI Part 4 Protected Data Who can be an Authorized User ? An authorized user is a person who has: – completed this USF training module; – received permission to use the sensitive data (including collecting such data themselves); – been approved by the DNC to use the USF secure data servers. Becoming an Authorized User To become an authorized user, submit an application to the ISO. The form may be obtained from USF IT. A complete application will include supporting documentation of appropriate training as shown on next slide. Application Documentation 1. The certificate indicating that the applicant has completed the training on Human Subjects/Institutional Review Board (IRB) procedures required by the USF Division of Research Compliance. 2. A certificate from the IT Department indicating that this USF training on data security and HIPAA guidelines has been completed (may be submitted electronically) 3. If applicable, a signed Data Confidentiality Procedures agreement from the source from which the data were received (e.g., DCF, AHCA) What is a Data Custodian? The custodian of the data set is an authorized user who has primary responsibility for: – Developing the data use agreement with the source – Approving the scientific use of the data – Communicating with the IT Office regarding the storage of data on a secure server – Ensuring that individuals who access data are appropriate co-investigators and have the approval of the data source (e.g., AHCA) to use these data. All research data at USF, including data from active projects and archived data from inactive projects, are potentially subject to the regulation. Three categories of data are subject to regulation: Protected Health Information (see previous section) Sensitive, personally identified data Non-sensitive or de-identified data Sensitive, Personally Identified Data Sensitive, personally identified data are: Any research data (such as demographic characteristics) that contain information that might allow an individual’s identity to become known to others (who do not have authorization to see the data). In brief, sensitive data is all non-PHI data that allows the identification of participants Non-sensitive or de-identified data Non-sensitive or de-identified research data is any data where all identifiers have been removed or individual persons/entities cannot be identified. Non-sensitive or de-identified data should be secured in a manner that the data owner or investigator determines is reasonable and appropriate. Protecting Data at USF Any data obtained or maintained by USF faculty or staff that include sensitive and/or PHI data, should be protected from unauthorized disclosure. It is recommended that all such data be stored on USF secure data servers. Any data not stored on an USF secure server should be stored according to the Generally Accepted System Security Principles (GASSP) of the International Information Security Foundation. Sharing data with other users… If the source of the sensitive data asks you to provide or share sensitive data with specific individuals, specific procedures must be used (continued on next slide). – The request from the source should be in writing (or via confirmed e-mail) and kept on file – The request should be specific as to what data sets are to be given the person – The person who will gain access to the data must complete the process to become an authorized user – No authorized user can allow anyone else to access or use data without following credentialing/approval by DNC. Archived Data If you have data that are no longer needed: Determine if the data can be destroyed or deleted from server (this should comply with any data use agreements); Maintain documentation on file that the PI has removed the data from his/her PC or other form of data storage and secured it appropriately. Paper Copies of Data If you print copies of sensitive/PHI data, the printed documents should never leave the USF premises and should be secured promptly. Non-secured printouts should be shredded – never discarded or recycled. Notification of Data Acquisition The department chair or other designated authority should notify the ISO when a research project that will use sensitive data is approved at the departmental level. Any USF investigator acquiring sensitive data should send a brief description of the data to the ISO. The investigator may request that the data be kept on a Data Server under high security. The investigator may also choose to keep sensitive, primary data (data collected by the researcher for a specific research project) outside of a secure data server providing that the researcher demonstrates adequate proof of security. That proof must be filed with the ISO. Data Access by Non-Authorized Users All disclosures of sensitive/PHI data to non-authorized users must be approved by the custodian, with notice provided to the ISO. Project Closure Custodians for sensitive data sets should inform the ISO and the IT department when: Projects have ended and the data can be archived Computers are to be removed from the network and inactivated We hope this training program has increased your understanding of the importance of utilizing secure procedures in your job. All employees will need to complete a short quiz to reinforce your knowledge of critical security procedures. Please proceed to the security quiz. Click on the following link, print and complete the quiz, and send it to the USF IT Office. HIPAA Quiz