Minutes of meeting - the Law Society's governance website
advertisement

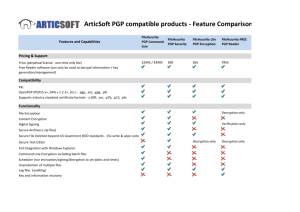
MINUTES ELECTRONIC LAW COMMITTEE 10.30am 21 April 2005 BREAMS ROOM, THE LAW SOCIETY Kenneth Byass, Nicholas Bohm, Steve Kelway, Julian Boardman-Weston, Denis Cameron (telelink) 1. Apologies Robert Bond 2. Minutes of last E-Law Committee Meeting and Matters Arising. The minutes of the last meeting were agreed. 3. Security for e-Conveyancing Nicholas outlined the Land Registry’s document authentication prototype pilot to the committee. He explained that it applied to elodgement — which not that many were using — and that only those participating in the pilot could sign digitally. 4. Security consultancy for the smaller firm Dr Simon Davey (ICT consultant) explained some of the security risks faced by SMEs and the voluntary sector. He said that just over 80% of charities were using anti-virus software but that only 55% installed a firewall. He emphasised the need to install a firewall particularly when using an ASDL (broadband) internet connection. He also pointed out that anti-virus software needed to be updated daily to remain effective and often this did not happen. Password protection was also of serious concern. A recent experiment at Waterloo railway station had exposed the willingness of commuters to divulge their passwords to researchers conducting a bogus survey (with the aim of seeing if they could secure passwords). Even if passwords were not voluntarily disclosed, easily guessable or attached to computers with 'stick-it' notes, most were susceptible to dictionary attacks. He pointed out that many types of fraud were not prevented by the use of a digital signature and suggested that users should be aware that the loss of a PGP private key could mean loss of access to encrypted documents. A range of support could be offered to small law firms. Tailored guidance. An issue was 'have it perfect or have it by Thursday'. For the small firm, his advice would be 'keep it simple'. Approved suppliers for small firms. How does a small firm identify value for money from a prospective IT supplier? One way might be to have, for instance, a directory of IT consultants who had passed competency checks. Engage through understanding. Help to increase small firms' understanding of the business and technical environment within which IT security measures had to be taken. Create the right climate. Within the voluntary sector this had meant creating bodies that were only now getting fully up-tospeed with ICT. He concluded by suggesting that promoting security to small firms was a matter of engaging their interest or their fear. The Committee explored the question of how to engage small firms. In particular, how was it possible to get a small firm interested in the IT security problem if: (a) it did not have specialist IT staff and (b) its finances were extremely tight? Discussion ensued about awareness raising and the possibility that some parts of the profession might never take proper IT security precautions unless they were compelled to do so. There was further discussion about what practical advice — in the form of guidelines — might be offered by the Society to the profession. The e-mail guidelines were one example. Were there others? 5. Commercial products for e-mail security Sebastian Stoughton outlined his company's e-mail security product for law firms. He proposed that the biggest e-mail risk faced by law firms was sending an e-mail to the wrong person; the problem was compounded by not being able to recall an e-mail once it had been sent. He cited a firm that had lost £6m by sending an e-mail to the wrong 'John Smith'. He also suggested that most lawyers and their clients simply did not realise just how insecure e-mail is. If they did, he felt sure they would apply security measures of the kind offered by Legal eSafe. The Legal eSafe product addresses the problems of misdirection and insecurity through a web-based e-mail solution. Some of its characteristics were that it did not require a change of existing e-mail addresses, clients required no special software, if messages had not been picked up their recall was guaranteed, messages were time and date stamped and it could be used in hostile environments — that is, it left no record on the browser after use. Product security was based on the Secure Software Layer (SSL) protocol. 6. Jon Penney (Intellect – Certified PGP Solution Partner) Jon outlined the basic principles of symmetric and asymmetric encryption explaining that the former was much faster (by a factor of 1e4) than the latter but that obviously key distribution was a problem. PGP as a hybrid cryptosystem solved this problem by using asymmetric encryption for key distribution and symmetric encryption for ensuing communications. He then gave a brief history of PGP from its publication by Phil Zimmerman in 1991 to the foundation of the new PGP Corporation in 2002. Jon then explained the PGP vision (pervasiveness, use of PKI infrastructure to deliver benefits that PKI cannot and Open Standards) and he took the committee through a number of PGP products including PGP command line, PGP desktop and PGP universal. He said that PGP 9.0 was due to be released shortly. 7. Proposal to form an E-Law Security Working Group The committee engaged in broad discussion on the presentations they had seen. They concluded that online security can be achieved in a number of ways but that a practical way forward - particularly in relation to the Land Registry's current authentication pilot - might be the formation of a working group. This would explore options to meet the profession’s security needs and might, in due course, lead to the publication of a consultation paper. 8. AOB and Next Meeting The next scheduled meeting of the E-Law Committee would be on 30 June.