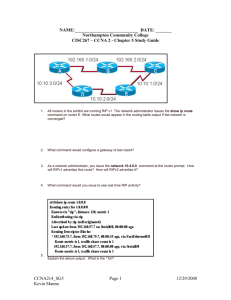
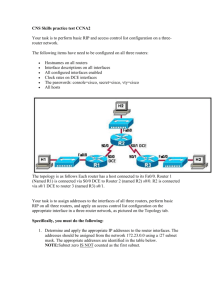
CCNA DUMPS - Asim Patel's Site
advertisement

The Building Scalable Cisco Certification exam is a qualifying exam for the CCNA certifications. The exam will certify that the successful candidate has important knowledge and skills necessary to use advanced IP addressing and routing in implementing scalability for Cisco routers connected to LANs and WANs. The exam covers topics on Advanced IP Addressing, Routing Principles, Configuring the EIGRP, Configuring the Open Shortest Path First Protocol, Configuring IS-IS, Manipulating Routing Updates, and configuring basic BGP. We provide CCNA sample questions that help test your preparedness for taking the actual cisco certification exam. CCNA 640-801 sample questions help in consolidating your concepts, preparation and also as exam cram. Each CCNA sample question is based on respective vendors published exam objectives and designed to help attain cisco certification. 1. Given the the following network diagram, assume that port 1 through 3 are assigned to VLAN 1 and ports 4 through 6 are assigned to VLAN 2 on each switch. The switches are interconnected over a trunked link. Which of the following conditions would verify VLAN and trunk operation? (choose 3) A. B. C. D. E. A. Host 1-1 can ping Host 1-2 B. Host 1-1 can ping Host 4-2 C. Host 1-1 can not ping Host 1-2 D. Host 4-1 can not ping Host 1-2 E. Host 4-1 can ping Host 4-2 Answer :A, D, E 2. By looking at the configuration, Which additional command must be issued on the Branch router before interesting traffic will be sent to the Remote router? Hostname: Branch Hostname: Remote PH# 123-6000, 123-6001 PH# 123-8000, 123-8001 SPID1: 32055512360001 SPID1: 32055512380001 SPID2: 32055512360002 SPID2: 32055512380002 isdn switch-type basic ni username Remote password cisco interface bri0 ip address 10.1.1.1 255.255.255.0 encapsulation ppp ppp authentication chap isdn spid1 41055512360001 isdn spid2 41055512360002 dialer map ip 10.1.1.2 name Remote 1238001 dialer-list 1 protocol ip permit A. B. C. D. (config-if)# dialer-group 1 (config-if)# dialer-list 1 (config-if)# dialer map 1 (config-if)# dialer-route 1 Answer : A Explanation :The "dialer-group #" command tells the access-list (used with the dialer-list # command), which interface to activate when it finds interesting traffic. The numbers at end of each command must match. 3. You are the network administrator of the RouterSim global software Company. You receive a call from a user who is unable to reach a server at a remote site. After further review you discover the following info: Local PC 190.0.3.35/24 Default Gateway 190.0.3.1 Remote Server 190.0.5.250/24 You then conduct the following tests from the offending local PC: Ping 127.0.0.1 - Unsuccessful Ping 190.0.3.35 - Successful Ping 190.0.3.1 - Unsuccessful Ping 190.0.5.250 - Unsuccessful Which of the following problems would create the test results listed above? A. B. C. D. TCP/IP not correctly installed Local physical layer problem NIC not functioning Remote physical layer problem Answer : A Explanation :If you cannot ping the loopback address of 127.0.0.1, then something is wrong with the IP configuration of the host. 4. Choose three reasons why the networking industry uses a layered model. (Choose 3) A. Allow changes in one layer to occur without changing other layers B. To get Gigabit speeds on LANs C. Clarify what general functions is to be done rather than how to do it D. To create filter tables on LANs E. Order network troubleshooting steps Answer :A, C, E Explanation : The reasons to use a layer model are: 6. Clarify what general function is to be done rather than how to do it. 7. Reduce the complexity of networking into more manageable sublayers. 8. Enable interoperability using standard interfaces. 9. Allow changes in one layer to occur without changing other layers. 10. Speed up network industry progress by allowing specialization. 11. Allow for shortcut explanations to facilitate protocol comparisons. 12. Order network troubleshooting steps. 13. Facilitate systematic troubleshooting. 5. What is a disadvantage to using bridges in your network? . Filters by MAC address A. Stops broadcast storms B. Doesn't stop broadcast storms C. Can only use up to 4 bridges in any LAN Answer : C Explanation : Even though the 5-4-3 rule specifies you can only have 4 bridges in a network, that is not really a disadvantage. The disadvantage to bridging is that it filters by MAC address and cannot create separate networks like a router can. This means that if a broadcast storm was to take place a bridge will forward the frames. 6. Two routers Rtr1 and Rtr2 are both configured with RIP only. What will be the result when Rtr1 receives a routing update that contains a higher cost path to a network already in its routing table? . The update information will replace the existing routing table entry. A. The update information will be added to the existing routing table. B. The existing routing table entry will be deleted from the routing table and all routers will exchange routing updates to reach convergence. C. The update will be ignored and no further action will be taken. Answer :E 7. What switching method examines the destination MAC address as the frame is being received and then begins forwarding the frame prior to receiving the entire frame? . Modified Cut Through A. Store and Forward B. Cut Through C. Fragment Free Answer :C Next » 640-801 8. Which PPP authentication methods will you use when configuring PPP on an interface of a Cisco router? (Select two options.) A. SSL B. SLIP C. PAP D. LAPB E. CHAP F. VNP Answer :C, E Explanation :Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP) authenticate the endpoints on either end of a point-to-point serial link. Chap is the preferred method today because the identifying codes flowing over the link are created using a MD5 one-way hash, which is more secure that the clear-text passwords sent by PAP. 9. If NVRAM lacks boot system commands, where does the router look for the Cisco IOS by default? A. ROM B. RAM C. Flash D. Bootstrap E. Startup-.config Answer :C Explanation :Flash memory - Either an EEPROM or a PCMCIA card, Flash memory stores fully functional IOS images and is the default location where the router gets its IOS at boot time. Flash memory also can be used to store any other files, including configuration files. 10. You need to troubleshoot a Cisco router at the Toronto office of How2Pass Inc. The router loses its configuration each time it is rebooted. You study the output displayed in the exhibit. What is the cause of the problem? Exhibit: ----- output omitted ---Cisco 2620 (MPC860) processor (revision 0x200) with 16384/2048K bytes of memory. Processor board ID JAD05076EF6 (3878188963) M860 processor: part number 0, mask 49 Bridging software. X.25 software, Version 3.0.0. 2 Ethernet/IEEE 802.3 interface(s) 2 Serial(sync/async) network interface(s) 2 Low speed serial(sync/async) network interface(s) 32K bytes of non-volatile configuration memory. 16384K bytes of processor board System flash (Read/Write) Configuration register is 0x2142 A. B. C. D. E. There is insufficient RAM for the IOS image The configuration register is misconfigured There is insufficient flash memory NVRAM failed POST There is insufficient NVRAM B 11. If an Ethernet port on router was assigned an IP address of 172.16.112.1/20, what is the maximum number of hosts allowed on this subnet? A. 2046 B. 8190 C. 4094 D. 4096 E. 1024 Answer :C 12. The Frame Relay circuit between router A and router B is experiencing congestion. Which type of notification are used to alleviate the congestion? (Choose three) A. B. C. D. E. DE BECN DLCI 100 is Down CIR FECN Answer :D, B & A 13. At which OSI layer does data translation and code formatting occur? A. Network B. Physical C. Data link D. Transport E. Session F. Presentation Answer :F 14. Which one of the following is a reason to use a hardware address? A. To transmit a packet from one local device to another local device. B. To transmit a frame from one interface to another interface. C. To obtain a vendor code/serial number from the user. D. To transmit data from one local device to remote device across Internet. E. To contain logical information about a device to use an end-to-end transmission. Answer :B 640-801 15. Which wireless data communication type has a high data rate but is limited to very short distances? A. Infrared B. Broadband Personal Communication Service (PCS) C. Narrowband D. Spread spectrum Answer :A 16. Ethernet networks are broadcast domains and collision domains. How the hosts on an Ethernet network will know when to resume transmissions after a collision has occurred? (Choose all that apply) A. The router on the segment will signal that the collision has cleared. B. The jam signal indicates that the collision has been cleared. C. The hosts will attempt to resume transmission after a time delay has expired. D. The destination host sends a request to the source for retransmission. E. An electrical pulse indicates that the collision has cleared. Answer :C 17. Which command must be entered when connecting two routers without external DCE devices via a serial link? A. Serial up. B. Dte rate. C. Dce rate. D. Clock rate. E. Line protocol up. Answer :D 18. How2Pass Router Simulation. Please read the instructions and problem statement carefully. Complete your configuration and press the Done button when finished. Answer : Troubleshooting In the simulation, click Host D, a dialog box will appear, select the Cisco Terminal option and press the OK button, to establish a terminal session to the router Kenan. Press ‹Enter› key to enter the User EXEC mode. Enter the privileged EXEC mode by typing enable at the Kenan> prompt and then the password how2pass at the Password: prompt. The privileged EXEC mode prompt, Kenan#, will be displayed. Issue the command show running-config (abbreviated as sh runn), read the output carefully to find any missing or wrong configuration. Whenever you see the prompt --More-- at the bottom of a page, you can press spacebar to see the next output page. Notice the running-config entries for interface serial1. It has wrong IP address and subnet mask. Notice the word shutdown below Serial1. To confirm this, issue show interface serial 1 command. The output confirms that the interface is shutdown. This simulation also supports ping, show ip protocol and show ip route commands for effective debugging. Do the configuration shown below and ping to a remote ip address. Save your configuration using copy running-config startup-config (abbreviated as copy runn start) command. Now press the Done button. Configuration Required Kenan#config t Enter configuration commands, one per line. End with CNTL/Z. Kenan(config)#int s1 Kenan(config-if)#ip address 192.168.69.2 255.255.255.0 Kenan(config-if)#no shutdown %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial1, changed state to up %LINK-3-UPDOWN: Interface Serial1 changed state to up Kenan(config-if)#^z %SYS-5-CONFIG_I: Configured from console by console Kenan#ping 192.168.59.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.69.1, timeout is 2 seconds: ! ! ! ! ! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/4 ms Kenan#copy runn start Destination filename [startup-config]? Building configuration... 19. Which of the following will configure a static route on Router A to network 180.18.30.0/24 with an administrative distance of 90? A. B. C. D. E. Router(config)# ip route 90 180.18.30.0 255.255.255.0 182.18.20.2 Router(config)# ip route 180.18.30.0 255.255.255.0 182.18.20.2 90 Router(config)# ip route 180.18.30.1 255.255.255.0 182.18.20.1 90 Router(config)# ip route 180.18.20.1 255.255.255.0 182.18.30.0 90 Router(config)# ip route 90 180.18.20.1 255.255.255.0 182.18.20.2 Answer :B 20. What is a trunk link? A. A link that is only part of one VLAN and is referred to as the native VLAN of the port B. A link that can carry multiple VLANs C. A switch port connected to the Internet D. Data and voice capability on the same interface Answer :B 640-801 21. What is the purpose of Inverse ARP? A. It is used to map a known DLCI to an IP address B. It is used to map a known DLCI to a MAC address C. It is used to map a known IP address to a MAC address D. It is used to map a known MAC address to an IP address E. It is used to map a known MAC address to DLCI Answer :A 22. You want to configure a router for load balancing across 4 unequal cost paths on your network. Which of the following routing protocols can you use? (Choose two) A. RIP v1 B. RIP v2 C. OSPF D. IGRP E. EIGRP F. VLSM Answer :D & E 23. At what layer data is split into segments A. Transport B. LAN C. Session D. Data Link Answer :A 24. Host A is communicating with the server. What will be the source MAC address of the frames received by Host A from the server? A. The MAC address of Host A. B. The MAC address of the server network interface. C. The MAC address of router interface E1. D. The MAC address of router interface E0. Answer :D 25. What does the concept route aggregation mean when one talks about using variable subnet masking? A. Combining routes to multiple networks into one supernet. B. Deleting unusable addresses through the creation of many subnets. C. Calculating the available host addresses in the AS. D. Reclaiming unused space by means of changing the subnet size. Answer :A 26. What PPP protocol provides dynamic addressing, authentication, and multilink? A. HDLC B. LCP C. NCP D. X.25 Answer :B 27. Study the network topology exhibit carefully, in particular the two switches SW1, SW2, and the router RT3. Which statements are true in this scenario? (Select two) A. The hosts on the 192.168.1.0 network form one collision domain, and the hosts on the 192.168.2.0 network form a second collision domain. B. Each host is in a separate collision domain. C. All the devices in both networks will receive a broadcast to 255.255.255.255 sent by host A. D. Only the devices in network 192.168.1.0 will receive a broadcast to 255.255.255.255 sent by host A. E. All the devices on both networks are members of the same collision domain. Answer :D & B 28. What switching method examines the destination MAC address as the frame is being received and then begins forwarding the frame prior to receiving the entire frame? A. Fragment Free B. Store and Forward C. Modified Cut Through D. Cut Through Answer :D 640-801 29. Please drag the appropriate options to the correct targets. After completing the question press the push button below the question to save your response. Answer: 1:E,2:A,3:F Explanation: LAPD - provides the data link protocol that allows delivery of messages across that D-channel to the local switch. LAPB - Protocol and is designed primarily to satisfy the signaling requirements of ISDN basic access. It is defined by ITU-T Recommendations Q.920 and Q.921. TE1 - ISDN -capable four-wire cable. Understands signaling and 2B=D. Uses an S reference point. ITU.T.430 - Defines connectors, encoding, framing, and reference points. TE2 - Equipment that does not understand ISDN protocols and specifications (no ISDN awareness). Uses an R reference point, typically an RS-232 or V.35 cable, to connect to a TA. NT1 - CPE equipment in North America. Connects with a U reference point (twowire) to the telco. 30. Which routing protocol would allow a network administrator scalability, VLSM support and minimize overhead if the network administrator wants to merge different networks all using routers from multiple vendors? A. OSPF B. VTP C. EIGRP D. RIP E. IGRP Answer :A 31. You work as network administrator at Brain dump. Your trainee is configuring a router with both physical and logical interfaces. He asks you what factor determines the OSPF router ID. What should you tell him? A. The lowest IP address of any interface. B. The highest IP address of any interface. C. The highest IP address of any logical interface. D. The middle IP address of any logical interface. E. The lowest IP address of any physical interface. F. The highest IP address of any physical interface. G. The lowest IP address of any logical interface. Answer :F Explanation: The OSPF topology database includes information about routers and the subnets, or links, to which they are attached. To identify the routers in the neighbor table’s topology database, OSPF uses a router ID (RID) for each router. A router’s OSPF RID is that router’s highest IP address on a physical interface when OSPF starts running. Note: The OSPF router ID is a 32-bit IP address selected at the beginning of the OSPF process. Thehighest IP address configured on the router is the router ID. If a loopback address is configured, then it is the router ID. In case of multiple loopback addresses, the highest loopback address is the router ID. Once the router ID is elected it doesn't change unless the IP address is removed or OSPF restarts. 32. Which of the following routes will be used to forward data in a situation where a routing table contains static, RIP, and IGRP routes destined to the same network with each set to its default administrative distance? A. The IGRP route B. The static route C. The RIP route D. All three will load balance. Answer :B Explanation:To decide which route to use, IOS uses a concept called Administrative Distance. Administrative distance is a number that denotes how believable an entire routing protocol is on a single router. The lower the number, the better, or more believable the routing protocol. Route Type Administrative Distance o o o Static 1 IGRP 100 RIP 120 33. When you consider half-duplex and full-duplex Ethernet, what are unique for half-duplex Ethernet? (Select two options.) . Half-duplex Ethernet operates in a shared collision domain. A. Half-duplex Ethernet operates in an exclusive broadcast domain. B. Half-duplex Ethernet has efficient throughput. C. Half-duplex Ethernet has lower effective throughput. D. Half-duplex Ethernet operates in an exclusive collision domain. Answer :A, D Explanation:A single device could not be sending a frame and receiving a frame at the same time because it would mean that a collision was occurring. So, devices simply chose not to send a frame while receiving a frame. That logic is called half-duplex logic. Ethernet switches allow multiple frames to be sent over different ports at the same time. Additionally, if only one device is connected to a switch port, there is never a possibility that a collision could occur. So, LAN switches with only one device cabled to each port of the switch allow the use of full-duplex operation. Full duplex means that an Ethernet card can send and receive concurrently. 34. What Channel is provided by ISDN BRI? . 2B+1D A. 30B+1D B. 23B+1D C. 2D+1B Answer :A 35. Which of the following describe the process identifier that is used to run OSPF on a router? (Choose two) . It is globally significant. A. It is an optional parameter required only if multiple OSPF processes are running on the router. B. All routers in the same OSPF area must have the same process ID if they are to exchange routing information. C. It is needed to identify a unique instance of an OSPF database. D. It is locally significant. Answer :D & E 640-801 36. What is the maximum number of hops that OSPF allows before marking a network as unreachable? A. 15 B. 16 C. 255 D. Unlimited E. 99 Answer :D 37. Which routing protocol would allow a network administrator scalability, VLSM support and minimize overhead if the network administrator wants to merge different networks all using routers from multiple vendors? A. VTP B. RIP C. IGRP D. EIGRP E. OSPF Answer :E 38. Two routers Rtr1 and Rtr2 are both configured with RIP only. What will be the result when Rtr1 receives a routing update that contains a higher cost path to a network already in its routing table? A. The update information will replace the existing routing table entry. B. The update information will be added to the existing routing table. C. The existing routing table entry will be deleted from the routing table and all routers will exchange routing updates to reach convergence. D. The update will be ignored and no further action will be taken. Answer :E 39. The following exhibit shows the Braindumps.biz WAN. Study it carefully: What are the broadcast addresses of the subnets in the Braindumps network? (Select three options). A. 172.16.82.255 B. 172.16.95.255 C. 172.16.64.255 D. 172.16.32.255 E. 172.16.47.255 F. 172.16.79.255 Answer :B, E, F Explanation:The subnets in the network are subnetted Class B addresses. A /20 subnet mask means that the subnet addresses increment by 16. For example: 172.16.16.0, 172.16.32.0, 172.16.48.0, 172.16.64.0 etc. The broadcast address is the last IP address before the next subnet address. B: The switch IP address (172.16.82.90) is in the 172.16.80.0 subnet. 172.16.95.255 is the broadcast address for the 172.16.80.0 subnet. E: 172.16.47.255 is the broadcast address for the 172.16.32.0 subnet. F: 172.16.79.255 is the broadcast address for the 172.16.64.0 subnet. 40. You are a network administrator at Braindumps. The Braindumps network is illustrated in the following exhibit. Study it carefully: Routers Braindumps1 and Braindumps2 are connected through their social interfaces, however, they cannot communicate. You ascertain that Braindumps1 has the correct configuration. Can you identify the fault on router Braindumps2? A. B. C. D. E. F. Link reliability is insufficient IPCP is not open Incorrect subnet mask Incompatible encapsulation Bandwidth allocation is too low Incomplete IP address Answer :D Explanation :HDLC and PPP Configuration HDLC and PPP configuration is straightforward. You just need to be sure to configure the same WAN data-link protocol on each end of the serial link. Otherwise, the routers will misinterpret the incoming frames, because each WAN data-link protocol uses a different frame format. Other than configuring some optional features that are all you need to 640-801 41. The exhibit displays the partial contents of an encapsulation header. Which of the following are true of the network traffic represented in this diagram? (Select three) A. B. C. D. E. This is traffic from an FTP server. This is a UDP header. The last PDU received in this session had a sequence number of 292735. This is an OSI layer 4 header. This is traffic from a Telnet client. Answer :D, A &C 42. What does the concept route aggregation mean when one talks about using variable subnet masking? A. Reclaiming unused space by means of changing the subnet size. B. Combining routes to multiple networks into one supernet. C. Calculating the available host addresses in the AS. D. Deleting unusable addresses through the creation of many subnets. Answer :B 43. What OSI layer is FRAME-RELAY mapped to? A. Network B. Transport C. Data Link D. Physical Answer :C 44. What is the basic characteristic of switches and hubs? A. B. C. D. E. Hubs cannot filter frames. Using hubs is costly with regard to bandwidth availability. Switches do and can not forward broadcasts. Switches are more efficient than hubs in processing frames. Switches increase the number of collision domains in the network. Answer :E Explanation:Switches increases the number of collisions domains in the network. Switches that are configured with VLANs will reduce the size of the collision domains by increasing the number of collision domains in a network, but making them smaller than that of one big, flat network. 640-801 45. You are a Cisco certified expert. You have been contracted by the Braindumps Pro chain to fix a problem that was caused by a MCP certified technician who could not complete the configuration of the routers. This Braindumps Pro chain has three stores and wanted to maintain their bicycle repair business in a centralized manner through network connectivity. They then asked the local MCP certified technician to configure the routers, but the technician failed to establish connectivity among the routers. The routers are named Braindumps1, Braindumps2, and Braindumps3, respectively. Identify the faults(s) and make the appropriate change(s) to rectify the configuration of the routers. The MCP technician configured the routers with the specification that follows: The routers are named Brain dump1, Brain dump2, and Brain dump3. RIP is the routing protocol Clocking is provided on the serial 0 interfaces The password on each router is "Brain dump" The subnet mask on all interfaces is the default mask. The IP addresses are listed in chart below. Brain dump1 E0 192.168.27.1 E1 192.168.29.1 S0 192.168.31.1 Secret password: Brain dump Brain dump2 E0 192.168.35.1 S0 192.168.33.1 S1 192.168.31.2 Secret password: Brain dump Brain dump3 E0 192.168.37.1 S1 192.168.33.2 Secret password: Brain dump To configure the router click on the host icon that is connected to the router by a serial cable. Answer : Click on Host 2: Router Brain dump1: Brain dump1 enable Password: Brain dump Brain dump1 # config terminal Brain dump1 (config) # interface ethernet 0 Brain dump1 (config-if) # ip address 192.168.27.1 255.255.255.0 Brain dump1 (config-if) # no shutdown Brain dump1 (config-if) # exit Brain dump1 (config) # interface ethernet 1 Brain dump1 (config-if) # ip address 192.168.29.1 255.255.255.0 Brain dump1 (config-if) # no shutdown Brain dump1 (config-if) # exit Brain dump1 (config) # interface serial 0 Brain dump1 (config-if) # ip address 192.168.31.1 255.255.255.0 Brain dump3 (config-if) # clock rate 64000 Brain dump1 (config-if) # no shutdown Brain dump1 (config-if) # exit. Brain dump1 (config) # router rip Brain dump1 (config-router) # network 192.168.27.0 Brain dump1 (config-router) # network 192.168.29.0 Brain dump1 (config-router) # network 192.168-31.0 Brain dump1 (config-router) # Ctrl-Z Brain dump1 # copy running-config startup-config Click on Host 4 Router Brain dump2: Brain dump2 enable Password: Brain dump Brain dump2 # config t Brain dump2 (config) # interface ethernet 0 Brain dump2 (config-if) # ip address 192.168.35.1 255.255.255.0 Brain dump2 (config-if) # no shutdown Brain dump2 (config-if) # exit Brain dump2 (config) # interface serial 0 Brain dump2 (config-if) # ip address 192.168.33.1 255.255.255.0 Brain dump2 (config-if) # clock rate 64000 Brain dump2 (config-if) # no shutdown Brain dump2 (config-if) # exit Brain dump2 (config) # interface serial 1 Brain dump2 (config-if) # ip address 192.168.31.2 255.255.255.0 Brain dump2 (config-if) # no shutdown Brain dump2 (config-if) # exit Brain dump2 (config) # router rip Brain dump2 (config-router) # network 192.168.35.0 Brain dump2 (config-router) # network 192.168.33.0 Brain dump2 (config-router) # network 192.168.31.0 Brain dump2 (config-router) # Ctrl-Z Brain dump2 # copy running-config startup-config Router Brain dump3: Click on Host6 Brain dump3 enable Password: Brain dump Brain dump3 # config t Brain dump3 (config) # interface ethernet 0 Brain dump3 (config-if) # ip address 192.168.37.1 255.255.255.0. Brain dump3 (config-if) # no shutdown Brain dump3 (config-if) # exit Brain dump3 (config) # interface serial 1 Brain dump3 (config-if) # ip address 192.168.33.2 255.255.255.0 Brain dump3 (config-if) # no shutdown Brain dump3 (config-if) # exit Brain dump3 (config) # router rip Brain dump3 (config-router) # network 192.168.33.0 Brain dump3 (config-router) # network 192.168.37.0 Brain dump3 (config-router) # Ctrl-Z Brain dump3 # copy running-config startup-config 640-801 46. You are a systems administrator at Braindumps and you've just acquired a new Class C IP network. Which of one of the subnet masks below is capable of providing one useful subnet for each of the above departments (support, financial, sales & development) while still allowing enough usable host addresses for each departments needs? A. B. C. D. E. F. 255.255.255.128 255.255.255.192 255.255.255.224 255.255.255.240 255.255.255.248 255.255.255.252 Answer :C Explanation:The network currently consists of 5 networks and another network will be acquired. That gives us atotal of 6 networks. This requires that we use 3 bits for the network address. Using the formula 2n-2 we get 6. This also leaves us with 5 bits for hosts, which gives us 30 hosts. 47. You are a network administrator at Braindumps. You need to troubleshoot the Braindumps network shown in the exhibit. Study the Exhibit carefully: The host, EX1, is connected to the Braindumps1 LAN, but it cannot get access to resources on any ofthe other networks. The host's configuration is as follows: Host address: 192.168.5.45 Subnet mask: 255.255.255.240 Default gateway: 192.168.5.32 Which of the following is the cause of this problem? A. B. C. D. The default gateway is a subnetwork address. The default gateway is on a different subnet address as the host. The IP address of the host is on a different subnet. The host subnet mask is incompatible to the subnet mask of the attached router interface. Answer :A Explanation:The range of the subnet used in this question is 192.168.166.32 to 192.168.166.47.192.168.166.32 is the network address and 192.168.166.47 is the broadcast. This leaving a usable host address range of 192.168.166.33 to 192.168.166.46. The default gateway for the host should be 192.168.166.33. 48. Which of the following are benefits of segmenting a network with a router? (Select all that apply) A. Broadcasts are not forwarded across the router. B. All broadcasts are completely eliminated. C. Adding a router to the network decreases latency. D. Filtering can occur based on Layer 3 information. E. Routers are more efficient than switches and will process the data more quickly. F. None of the above. Answer :A, D 49. Which of the following about Routing Protocols is correct? (choose all that apply) A. RIP 2 is a Distance Vector Protocol B. The RIP 1 uses bandwidth and delay as the metric C. RIP 1 uses subnet mask D. The holdown timer value for RIP is 240 sec E. The Update timer value of IGRP is 90 sec Answer :A & E 50. What command is used to delete the configuration stored in NVRAM? A. erase startup-config B. erase running-config C. delete nvram D. erase nvram Answer :A 640-801 51. You are a network administrator at Braindumps. The Braindumps network is illustrated in the following exhibit. Study it carefully: You want to prevent users on the Research Network and the Internet from accessing the Braindumps Support server, but you want to allow all other Braindumps users access to the server. You create an access control list (ACL) called research block. The ACL contains the following statements: deny 172.16.102.0 0.0.0.255 172.16.104.255 0.0.0.0 permit 172.16.0.0 0.0.255.255 172.16.104.252 0.0.0.0 Which of the following commands sequences will place this list to meet these requirements? A. Brain dump1 (config)# interface e0 Brain dump1 (config-if)# ip access-group research block in B. Brain dump1 (config)# interface s0 Brain dump1 (config-if)# ip access-group research block out C. Brain dump2 (config)# interface s0 Brain dump2 (config-if)# ip access-group research block out D. Brain dump2 (config)# interface s1 Brain dump2 (config-if)# ip access-group research block in E. Brain dump3 (config)# interface s1 Brain dump3 (config-if)# ip access-group research block in F. Brain dump3 (config)# interface e0 Brain dump3 (config-if)# ip access-group research block out Answer :F Explanation:To enable the ACL on an interface and define the direction of packets to which the ACL is applied, the ip access-group command is used. When referring to a router, these terms have the following meanings. o Out - Traffic that has already been through the router and is leaving the interface; the source Would be where it's been (on the other side of the router) and the destination is where it's Going. o In - Traffic that is arriving on the interface and which will go through the router; the source would Be where it's been and the destination is where it's going (on the other side of the router). 52. You are a network administrator at Braindumps. You are troubleshooting a router problem. You issue the show ip route command on one of the routers. The output from the command is shown in the following exhibit: Router Brain dump# Show in ip route. What does [120/3] represent? . 120 is the bandwidth allocation and 3 is the routing process number. A. 120 is the administrative distance and 3 is the metric for that route. B. 120 is the value of the update timer and 3 is the number of updates received. C. 120 is the UDP port for forwarding traffic and 3 is the number of bridges. Answer :B Explanation:To decide which route to use, IOS uses a concept called Administrative Distance. Administrativedistance is a number that denotes how believable an entire routing protocol is on a single router. The lower the number, the better, or more believable the routing protocol. Route Type Administrative Distance Route Type Administrative Distance o o o o o Connected 0 EIGRP 90 IGRP 100 OSPF 110 RIP 120 For RIP, the metric is the hop count, so in this case the route is 3 hops away. 640-801 53. Which of the following belong to the ISDN TE2 function group? (Choose two) A. a router serial interface B. an ISDN phone C. a router ISDN BRI "U" interface D. a standard pc E. an ISDN terminal adapter Answer :A & D 54. Which protocol is used to look up an IP address from a known Ethernet address? A. TCP B. RARP C. ARP D. IP Answer :B 55. What could be the rationale behind using passive-interface command when configuring a router? A. Allows interfaces to share common IP addresses. B. Allows an interface to remain up without the aid of keepalives. C. Allows a router to send routing and not receive updates via that interface. D. Allows a routing protocol to forward updates that is missing its IP address. E. Allows a router to receive routing updates on an interface but not send updates via that interface. Answer :E Explanation:The passive-interface command is used to control the advertisement of routing information. The command enables the suppression of routing updates over some interfaces while allowing updates to be exchanged normally over other interfaces. For any interface specified as passive, no routing information will be sent. Routing information received on that interface will be accepted and processed by the router. This is often useful for DDR links such as ISDN. « Previous || Next » The Building Scalable Cisco Certification exam is a qualifying exam for the CCNA certifications. The exam will certify that the successful candidate has important knowledge and skills necessary to use advanced IP addressing and routing in implementing scalability for Cisco routers connected to LANs and WANs. The exam covers topics on Advanced IP Addressing, Routing Principles, Configuring the EIGRP, Configuring the Open Shortest Path First Protocol, Configuring IS-IS, Manipulating Routing Updates, and configuring basic BGP. We provide CCNA sample questions that help test your preparedness for taking the actual cisco certification exam. CCNA 640-801 sample questions help in consolidating your concepts, preparation and also as exam cram. Each CCNA sample question is based on respective vendors published exam objectives and designed to help attain cisco certification. 1. Which of the following about Routing Protocols is correct? (choose all that apply) A. RIP 2 is a Distance Vector Protocol B. The RIP 1 uses bandwidth and delay as the metric C. RIP 1 uses subnet mask D. The holdown timer value for RIP is 240 sec E. The Update timer value of IGRP is 90 sec Answer :A & E 2. What command is used to delete the configuration stored in NVRAM? A. erase startup-config B. erase running-config C. delete nvram D. erase nvram Answer :A 3. What is the maximum number of hops that OSPF allows before marking a network as unreachable? A. 15 B. 16 C. 255 D. Unlimited E. 99 Answer :D 4. Which routing protocol would allow a network administrator scalability, VLSM support and minimize overhead if the network administrator wants to merge different networks all using routers from multiple vendors? A. VTP B. RIP C. IGRP D. EIGRP E. OSPF Answer :E 5. Two routers Rtr1 and Rtr2 are both configured with RIP only. What will be the result when Rtr1 receives a routing update that contains a higher cost path to a network already in its routing table? A. The update information will replace the existing routing table entry. B. The update information will be added to the existing routing table. C. The existing routing table entry will be deleted from the routing table and all routers will exchange routing updates to reach convergence. D. The update will be ignored and no further action will be taken. Answer :E 6. Two routers Rtr1 and Rtr2 are both configured with RIP only. What will be the result when Rtr1 receives a routing update that contains a higher cost path to a network already in its routing table? A. The update information will replace the existing routing table entry. B. The update information will be added to the existing routing table. C. The existing routing table entry will be deleted from the routing table and all routers will exchange routing updates to reach convergence. D. The update will be ignored and no further action will be taken. Answer :E 7. What switching method examines the destination MAC address as the frame is being received and then begins forwarding the frame prior to receiving the entire frame? A. Modified Cut Through B. Store and Forward C. Cut Through D. Fragment Free Answer :C 8. Which of the following belong to the ISDN TE2 function group? (Choose two) A. a router serial interface B. an ISDN phone C. a router ISDN BRI "U" interface D. a standard pc E. an ISDN terminal adapter Answer :A & D 9. Which protocol is used to look up an IP address from a known Ethernet address? A. TCP B. RARP C. ARP D. IP Answer :B 10. You need to troubleshoot a Cisco router at the Toronto office of How2Pass Inc. The router loses its configuration each time it is rebooted. You study the output displayed in the exhibit. What is the cause of the problem? Exhibit: ----- output omitted ---Cisco 2620 (MPC860) processor (revision 0x200) with 16384/2048K bytes of memory. Processor board ID JAD05076EF6 (3878188963) M860 processor: part number 0, mask 49 Bridging software. X.25 software, Version 3.0.0. 2 Ethernet/IEEE 802.3 interface(s) 2 Serial(sync/async) network interface(s) 2 Low speed serial(sync/async) network interface(s) 32K bytes of non-volatile configuration memory. 16384K bytes of processor board System flash (Read/Write) Configuration register is 0x2142 A. B. C. D. E. B There is insufficient RAM for the IOS image The configuration register is misconfigured There is insufficient flash memory NVRAM failed POST There is insufficient NVRAM 11. If an Ethernet port on router was assigned an IP address of 172.16.112.1/20, what is the maximum number of hosts allowed on this subnet? A. 2046 B. 8190 C. 4094 D. 4096 E. 1024 Answer :C 12. The Frame Relay circuit between router A and router B is experiencing congestion. Which type of notification are used to alleviate the congestion? (Choose three) A. B. C. D. E. DE BECN DLCI 100 is Down CIR FECN Answer :D, B & A 13. At which OSI layer does data translation and code formatting occur? A. Network B. Physical C. Data link D. Transport E. Session F. Presentation Answer :F 14. Which one of the following is a reason to use a hardware address? A. To transmit a packet from one local device to another local device. B. To transmit a frame from one interface to another interface. C. To obtain a vendor code/serial number from the user. D. To transmit data from one local device to remote device across Internet. E. To contain logical information about a device to use an end-to-end transmission. Answer :B 15. Which wireless data communication type has a high data rate but is limited to very short distances? A. B. C. D. Infrared Broadband Personal Communication Service (PCS) Narrowband Spread spectrum Answer :A 16. Ethernet networks are broadcast domains and collision domains. How the hosts on an Ethernet network will know when to resume transmissions after a collision has occurred? (Choose all that apply) A. The router on the segment will signal that the collision has cleared. B. The jam signal indicates that the collision has been cleared. C. The hosts will attempt to resume transmission after a time delay has expired. D. The destination host sends a request to the source for retransmission. E. An electrical pulse indicates that the collision has cleared. Answer :C 17. Which command must be entered when connecting two routers without external DCE devices via a serial link? A. Serial up. B. Dte rate. C. Dce rate. D. Clock rate. E. Line protocol up. Answer :D 18. How2Pass Router Simulation. Please read the instructions and problem statement carefully. Complete your configuration and press the Done button when finished. Answer : Troubleshooting In the simulation, click Host D, a dialog box will appear, select the Cisco Terminal option and press the OK button, to establish a terminal session to the router Kenan. Press ‹Enter› key to enter the User EXEC mode. Enter the privileged EXEC mode by typing enable at the Kenan> prompt and then the password how2pass at the Password: prompt. The privileged EXEC mode prompt, Kenan#, will be displayed. Issue the command show running-config (abbreviated as sh runn), read the output carefully to find any missing or wrong configuration. Whenever you see the prompt --More-- at the bottom of a page, you can press spacebar to see the next output page. Notice the running-config entries for interface serial1. It has wrong IP address and subnet mask. Notice the word shutdown below Serial1. To confirm this, issue show interface serial 1 command. The output confirms that the interface is shutdown. This simulation also supports ping, show ip protocol and show ip route commands for effective debugging. Do the configuration shown below and ping to a remote ip address. Save your configuration using copy running-config startup-config (abbreviated as copy runn start) command. Now press the Done button. Configuration Required Kenan#config t Enter configuration commands, one per line. End with CNTL/Z. Kenan(config)#int s1 Kenan(config-if)#ip address 192.168.69.2 255.255.255.0 Kenan(config-if)#no shutdown %LINEPROTO-5-UPDOWN: Line protocol on Interface Serial1, changed state to up %LINK-3-UPDOWN: Interface Serial1 changed state to up Kenan(config-if)#^z %SYS-5-CONFIG_I: Configured from console by console Kenan#ping 192.168.59.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.69.1, timeout is 2 seconds: ! ! ! ! ! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/4 ms Kenan#copy runn start Destination filename [startup-config]? Building configuration... 19. Which of the following will configure a static route on Router A to network 180.18.30.0/24 with an administrative distance of 90? A. B. C. D. E. Router(config)# ip route 90 180.18.30.0 255.255.255.0 182.18.20.2 Router(config)# ip route 180.18.30.0 255.255.255.0 182.18.20.2 90 Router(config)# ip route 180.18.30.1 255.255.255.0 182.18.20.1 90 Router(config)# ip route 180.18.20.1 255.255.255.0 182.18.30.0 90 Router(config)# ip route 90 180.18.20.1 255.255.255.0 182.18.20.2 Answer :B 20. What is a trunk link? A. A link that is only part of one VLAN and is referred to as the native VLAN of the port B. A link that can carry multiple VLANs C. A switch port connected to the Internet D. Data and voice capability on the same interface Answer :B 21. What does the concept route aggregation mean when one talks about using variable subnet masking? A. Combining routes to multiple networks into one supernet. B. Deleting unusable addresses through the creation of many subnets. C. Calculating the available host addresses in the AS. D. Reclaiming unused space by means of changing the subnet size. Answer :A 22. What PPP protocol provides dynamic addressing, authentication, and multilink? A. HDLC B. LCP C. NCP D. X.25 Answer :B 23. Study the network topology exhibit carefully, in particular the two switches SW1, SW2, and the router RT3. Which statements are true in this scenario? (Select two) A. The hosts on the 192.168.1.0 network form one collision domain, and the hosts on the 192.168.2.0 network form a second collision domain. B. Each host is in a separate collision domain. C. All the devices in both networks will receive a broadcast to 255.255.255.255 sent by host A. D. Only the devices in network 192.168.1.0 will receive a broadcast to 255.255.255.255 sent by host A. E. All the devices on both networks are members of the same collision domain. Answer :D & B 24. What is the purpose of Inverse ARP? A. It is used to map a known DLCI to an IP address B. It is used to map a known DLCI to a MAC address C. It is used to map a known IP address to a MAC address D. It is used to map a known MAC address to an IP address E. It is used to map a known MAC address to DLCI Answer :A 25. You want to configure a router for load balancing across 4 unequal cost paths on your network. Which of the following routing protocols can you use? (Choose two) A. RIP v1 B. RIP v2 C. OSPF D. IGRP E. EIGRP F. VLSM Answer :D & E 26. At what layer data is split into segments A. Transport B. LAN C. Session D. Data Link Answer :A 27. Host A is communicating with the server. What will be the source MAC address of the frames received by Host A from the server? A. The MAC address of Host A. B. The MAC address of the server network interface. C. The MAC address of router interface E1. D. The MAC address of router interface E0. Answer :D 28. What switching method examines the destination MAC address as the frame is being received and then begins forwarding the frame prior to receiving the entire frame? A. Fragment Free B. Store and Forward C. Modified Cut Through D. Cut Through Answer :D 29. The exhibit displays the partial contents of an encapsulation header. Which of the following are true of the network traffic represented in this diagram? (Select three) A. B. C. D. E. This is traffic from an FTP server. This is a UDP header. The last PDU received in this session had a sequence number of 292735. This is an OSI layer 4 header. This is traffic from a Telnet client. Answer :D, A &C 30. What does the concept route aggregation mean when one talks about using variable subnet masking? A. Reclaiming unused space by means of changing the subnet size. B. Combining routes to multiple networks into one supernet. C. Calculating the available host addresses in the AS. D. Deleting unusable addresses through the creation of many subnets. Answer :B 31. What OSI layer is FRAME-RELAY mapped to? A. Network B. Transport C. Data Link D. Physical Answer :C 32. Please drag the appropriate options to the correct targets. After completing the question press the push button below the question to save your response. Answer: 1:E,2:A,3:F Explanation: LAPD - provides the data link protocol that allows delivery of messages across that D-channel to the local switch. LAPB - Protocol and is designed primarily to satisfy the signaling requirements of ISDN basic access. It is defined by ITU-T Recommendations Q.920 and Q.921. TE1 - ISDN -capable four-wire cable. Understands signaling and 2B=D. Uses an S reference point. ITU.T.430 - Defines connectors, encoding, framing, and reference points. TE2 - Equipment that does not understand ISDN protocols and specifications (no ISDN awareness). Uses an R reference point, typically an RS-232 or V.35 cable, to connect to a TA. NT1 - CPE equipment in North America. Connects with a U reference point (twowire) to the telco. 33. Which routing protocol would allow a network administrator scalability, VLSM support and minimize overhead if the network administrator wants to merge different networks all using routers from multiple vendors? A. OSPF B. VTP C. EIGRP D. RIP E. IGRP Answer :A 34. What Channel is provided by ISDN BRI? A. 2B+1D B. 30B+1D C. 23B+1D D. 2D+1B Answer :A 35. Which of the following describe the process identifier that is used to run OSPF on a router? (Choose two) A. It is globally significant. B. It is an optional parameter required only if multiple OSPF processes are running on the router. C. All routers in the same OSPF area must have the same process ID if they are to exchange routing information. D. It is needed to identify a unique instance of an OSPF database. E. It is locally significant. Answer :D & E 36. Given the the following network diagram, assume that port 1 through 3 are assigned to VLAN 1 and ports 4 through 6 are assigned to VLAN 2 on each switch. The switches are interconnected over a trunked link. Which of the following conditions would verify VLAN and trunk operation? (choose 3) A. A. Host 1-1 can ping Host 1-2 B. B. Host 1-1 can ping Host 4-2 C. C. Host 1-1 can not ping Host 1-2 D. D. Host 4-1 can not ping Host 1-2 E. E. Host 4-1 can ping Host 4-2 Answer :A, D, E 37. By looking at the configuration, Which additional command must be issued on the Branch router before interesting traffic will be sent to the Remote router? Hostname: Branch Hostname: Remote PH# 123-6000, 123-6001 PH# 123-8000, 123-8001 SPID1: 32055512360001 SPID1: 32055512380001 SPID2: 32055512360002 SPID2: 32055512380002 isdn switch-type basic ni username Remote password cisco interface bri0 ip address 10.1.1.1 255.255.255.0 encapsulation ppp ppp authentication chap isdn spid1 41055512360001 isdn spid2 41055512360002 dialer map ip 10.1.1.2 name Remote 1238001 dialer-list 1 protocol ip permit A. B. C. D. (config-if)# dialer-group 1 (config-if)# dialer-list 1 (config-if)# dialer map 1 (config-if)# dialer-route 1 Answer : A Explanation :The "dialer-group #" command tells the access-list (used with the dialer-list # command), which interface to activate when it finds interesting traffic. The numbers at end of each command must match. 38. You are the network administrator of the RouterSim global software Company. You receive a call from a user who is unable to reach a server at a remote site. After further review you discover the following info: Local PC 190.0.3.35/24 Default Gateway 190.0.3.1 Remote Server 190.0.5.250/24 You then conduct the following tests from the offending local PC: Ping 127.0.0.1 - Unsuccessful Ping 190.0.3.35 - Successful Ping 190.0.3.1 - Unsuccessful Ping 190.0.5.250 - Unsuccessful Which of the following problems would create the test results listed above? A. B. C. D. TCP/IP not correctly installed Local physical layer problem NIC not functioning Remote physical layer problem Answer : A Explanation :If you cannot ping the loopback address of 127.0.0.1, then something is wrong with the IP configuration of the host. 39. Choose three reasons why the networking industry uses a layered model. (Choose 3) A. Allow changes in one layer to occur without changing other layers B. To get Gigabit speeds on LANs C. Clarify what general functions is to be done rather than how to do it D. To create filter tables on LANs E. Order network troubleshooting steps Answer :A, C, E Explanation : The reasons to use a layer model are: 6. Clarify what general function is to be done rather than how to do it. 7. Reduce the complexity of networking into more manageable sublayers. 8. Enable interoperability using standard interfaces. 9. Allow changes in one layer to occur without changing other layers. 10. Speed up network industry progress by allowing specialization. 11. Allow for shortcut explanations to facilitate protocol comparisons. 12. Order network troubleshooting steps. 13. Facilitate systematic troubleshooting. 40. What is a disadvantage to using bridges in your network? . Filters by MAC address A. Stops broadcast storms B. Doesn't stop broadcast storms C. Can only use up to 4 bridges in any LAN Answer : C Explanation : Even though the 5-4-3 rule specifies you can only have 4 bridges in a network, that is not really a disadvantage. The disadvantage to bridging is that it filters by MAC address and cannot create separate networks like a router can. This means that if a broadcast storm was to take place a bridge will forward the frames. « Previous || Next » 41. You work as network administrator at Brain dump. Your trainee is configuring a router with both physical and logical interfaces. He asks you what factor determines the OSPF router ID. What should you tell him? A. The lowest IP address of any interface. B. The highest IP address of any interface. C. The highest IP address of any logical interface. D. The middle IP address of any logical interface. E. The lowest IP address of any physical interface. F. The highest IP address of any physical interface. G. The lowest IP address of any logical interface. Answer :F Explanation: The OSPF topology database includes information about routers and the subnets, or links, to which they are attached. To identify the routers in the neighbor table’s topology database, OSPF uses a router ID (RID) for each router. A router’s OSPF RID is that router’s highest IP address on a physical interface when OSPF starts running. Note: The OSPF router ID is a 32-bit IP address selected at the beginning of the OSPF process. Thehighest IP address configured on the router is the router ID. If a loopback address is configured, then it is the router ID. In case of multiple loopback addresses, the highest loopback address is the router ID. Once the router ID is elected it doesn't change unless the IP address is removed or OSPF restarts. 42. Which of the following routes will be used to forward data in a situation where a routing table contains static, RIP, and IGRP routes destined to the same network with each set to its default administrative distance? A. The IGRP route B. The static route C. The RIP route D. All three will load balance. Answer :B Explanation:To decide which route to use, IOS uses a concept called Administrative Distance. Administrative distance is a number that denotes how believable an entire routing protocol is on a single router. The lower the number, the better, or more believable the routing protocol. Route Type Administrative Distance o o o Static 1 IGRP 100 RIP 120 43. What is the basic characteristic of switches and hubs? . Hubs cannot filter frames. A. Using hubs is costly with regard to bandwidth availability. B. Switches do and can not forward broadcasts. C. Switches are more efficient than hubs in processing frames. D. Switches increase the number of collision domains in the network. Answer :E Explanation:Switches increases the number of collisions domains in the network. Switches that are configured with VLANs will reduce the size of the collision domains by increasing the number of collision domains in a network, but making them smaller than that of one big, flat network. 44. When you consider half-duplex and full-duplex Ethernet, what are unique for half-duplex Ethernet? (Select two options.) . Half-duplex Ethernet operates in a shared collision domain. A. Half-duplex Ethernet operates in an exclusive broadcast domain. B. Half-duplex Ethernet has efficient throughput. C. Half-duplex Ethernet has lower effective throughput. D. Half-duplex Ethernet operates in an exclusive collision domain. Answer :A, D Explanation:A single device could not be sending a frame and receiving a frame at the same time because it would mean that a collision was occurring. So, devices simply chose not to send a frame while receiving a frame. That logic is called half-duplex logic. Ethernet switches allow multiple frames to be sent over different ports at the same time. Additionally, if only one device is connected to a switch port, there is never a possibility that a collision could occur. So, LAN switches with only one device cabled to each port of the switch allow the use of full-duplex operation. Full duplex means that an Ethernet card can send and receive concurrently. 45. You are a Cisco certified expert. You have been contracted by the Braindumps Pro chain to fix a problem that was caused by a MCP certified technician who could not complete the configuration of the routers. This Braindumps Pro chain has three stores and wanted to maintain their bicycle repair business in a centralized manner through network connectivity. They then asked the local MCP certified technician to configure the routers, but the technician failed to establish connectivity among the routers. The routers are named Braindumps1, Braindumps2, and Braindumps3, respectively. Identify the faults(s) and make the appropriate change(s) to rectify the configuration of the routers. The MCP technician configured the routers with the specification that follows: o o o o o o The routers are named Brain dump1, Brain dump2, and Brain dump3. RIP is the routing protocol Clocking is provided on the serial 0 interfaces The password on each router is "Brain dump" The subnet mask on all interfaces is the default mask. The IP addresses are listed in chart below. Brain dump1 E0 192.168.27.1 E1 192.168.29.1 S0 192.168.31.1 Secret password: Brain dump Brain dump2 E0 192.168.35.1 S0 192.168.33.1 S1 192.168.31.2 Secret password: Brain dump Brain dump3 E0 192.168.37.1 S1 192.168.33.2 Secret password: Brain dump To configure the router click on the host icon that is connected to the router by a serial cable. Answer : Click on Host 2: Router Brain dump1: Brain dump1 enable Password: Brain dump Brain dump1 # config terminal Brain dump1 (config) # interface ethernet 0 Brain dump1 (config-if) # ip address 192.168.27.1 255.255.255.0 Brain dump1 (config-if) # no shutdown Brain dump1 (config-if) # exit Brain dump1 (config) # interface ethernet 1 Brain dump1 (config-if) # ip address 192.168.29.1 255.255.255.0 Brain dump1 (config-if) # no shutdown Brain dump1 (config-if) # exit Brain dump1 (config) # interface serial 0 Brain dump1 (config-if) # ip address 192.168.31.1 255.255.255.0 Brain dump3 (config-if) # clock rate 64000 Brain dump1 (config-if) # no shutdown Brain dump1 (config-if) # exit. Brain dump1 (config) # router rip Brain dump1 (config-router) # network 192.168.27.0 Brain dump1 (config-router) # network 192.168.29.0 Brain dump1 (config-router) # network 192.168-31.0 Brain dump1 (config-router) # Ctrl-Z Brain dump1 # copy running-config startup-config Click on Host 4 Router Brain dump2: Brain dump2 enable Password: Brain dump Brain dump2 # config t Brain dump2 (config) # interface ethernet 0 Brain dump2 (config-if) # ip address 192.168.35.1 255.255.255.0 Brain dump2 (config-if) # no shutdown Brain dump2 (config-if) # exit Brain dump2 (config) # interface serial 0 Brain dump2 (config-if) # ip address 192.168.33.1 255.255.255.0 Brain dump2 (config-if) # clock rate 64000 Brain dump2 (config-if) # no shutdown Brain dump2 (config-if) # exit Brain dump2 (config) # interface serial 1 Brain dump2 (config-if) # ip address 192.168.31.2 255.255.255.0 Brain dump2 (config-if) # no shutdown Brain dump2 (config-if) # exit Brain dump2 (config) # router rip Brain dump2 (config-router) # network 192.168.35.0 Brain dump2 (config-router) # network 192.168.33.0 Brain dump2 (config-router) # network 192.168.31.0 Brain dump2 (config-router) # Ctrl-Z Brain dump2 # copy running-config startup-config Router Brain dump3: Click on Host6 Brain dump3 enable Password: Brain dump Brain dump3 # config t Brain dump3 (config) # interface ethernet 0 Brain dump3 (config-if) # ip address 192.168.37.1 255.255.255.0. Brain dump3 (config-if) # no shutdown Brain dump3 (config-if) # exit Brain dump3 (config) # interface serial 1 Brain dump3 (config-if) # ip address 192.168.33.2 255.255.255.0 Brain dump3 (config-if) # no shutdown Brain dump3 (config-if) # exit Brain dump3 (config) # router rip Brain dump3 (config-router) # network 192.168.33.0 Brain dump3 (config-router) # network 192.168.37.0 Brain dump3 (config-router) # Ctrl-Z Brain dump3 # copy running-config startup-config 46. The following exhibit shows the Braindumps.biz WAN. Study it carefully: What are the broadcast addresses of the subnets in the Braindumps network? (Select three options). A. 172.16.82.255 B. 172.16.95.255 C. 172.16.64.255 D. 172.16.32.255 E. 172.16.47.255 F. 172.16.79.255 Answer :B, E, F Explanation:The subnets in the network are subnetted Class B addresses. A /20 subnet mask means that the subnet addresses increment by 16. For example: 172.16.16.0, 172.16.32.0, 172.16.48.0, 172.16.64.0 etc. The broadcast address is the last IP address before the next subnet address. B: The switch IP address (172.16.82.90) is in the 172.16.80.0 subnet. 172.16.95.255 is the broadcast address for the 172.16.80.0 subnet. E: 172.16.47.255 is the broadcast address for the 172.16.32.0 subnet. F: 172.16.79.255 is the broadcast address for the 172.16.64.0 subnet. 47. You are a network administrator at Braindumps. The Braindumps network is illustrated in the following exhibit. Study it carefully: Routers Braindumps1 and Braindumps2 are connected through their social interfaces, however, they cannot communicate. You ascertain that Braindumps1 has the correct configuration. Can you identify the fault on router Braindumps2? A. B. C. D. E. F. Link reliability is insufficient IPCP is not open Incorrect subnet mask Incompatible encapsulation Bandwidth allocation is too low Incomplete IP address Answer :D Explanation :HDLC and PPP Configuration HDLC and PPP configuration is straightforward. You just need to be sure to configure the same WAN data-link protocol on each end of the serial link. Otherwise, the routers will misinterpret the incoming frames, because each WAN data-link protocol uses a different frame format. Other than configuring some optional features that are all you need to do. 48. You are a network administrator at Braindumps. The Braindumps network is illustrated in the following exhibit. Study it carefully: You want to prevent users on the Research Network and the Internet from accessing the Braindumps Support server, but you want to allow all other Braindumps users access to the server. You create an access control list (ACL) called research block. The ACL contains the following statements: deny 172.16.102.0 0.0.0.255 172.16.104.255 0.0.0.0 permit 172.16.0.0 0.0.255.255 172.16.104.252 0.0.0.0 Which of the following commands sequences will place this list to meet these requirements? A. Brain dump1 (config)# interface e0 Brain dump1 (config-if)# ip access-group research block in B. Brain dump1 (config)# interface s0 Brain dump1 (config-if)# ip access-group research block out C. Brain dump2 (config)# interface s0 Brain dump2 (config-if)# ip access-group research block out D. Brain dump2 (config)# interface s1 Brain dump2 (config-if)# ip access-group research block in E. Brain dump3 (config)# interface s1 Brain dump3 (config-if)# ip access-group research block in F. Brain dump3 (config)# interface e0 Brain dump3 (config-if)# ip access-group research block out Answer :F Explanation:To enable the ACL on an interface and define the direction of packets to which the ACL is applied, the ip access-group command is used. When referring to a router, these terms have the following meanings. o Out - Traffic that has already been through the router and is leaving the interface; the source Would be where it's been (on the other side of the router) and the destination is where it's Going. o In - Traffic that is arriving on the interface and which will go through the router; the source would Be where it's been and the destination is where it's going (on the other side of the router). 49. You are a network administrator at Braindumps. You are troubleshooting a router problem. You issue the show ip route command on one of the routers. The output from the command is shown in the following exhibit: Router Brain dump# Show in ip route. What does [120/3] represent? . 120 is the bandwidth allocation and 3 is the routing process number. A. 120 is the administrative distance and 3 is the metric for that route. B. 120 is the value of the update timer and 3 is the number of updates received. C. 120 is the UDP port for forwarding traffic and 3 is the number of bridges. Answer :B Explanation:To decide which route to use, IOS uses a concept called Administrative Distance. Administrativedistance is a number that denotes how believable an entire routing protocol is on a single router. The lower the number, the better, or more believable the routing protocol. Route Type Administrative Distance Route Type Administrative Distance o o o o o Connected 0 EIGRP 90 IGRP 100 OSPF 110 RIP 120 For RIP, the metric is the hop count, so in this case the route is 3 hops away. 50. Which PPP authentication methods will you use when configuring PPP on an interface of a Cisco router? (Select two options.) A. SSL B. SLIP C. PAP D. LAPB E. CHAP F. VNP Answer :C, E Explanation :Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP) authenticate the endpoints on either end of a point-to-point serial link. Chap is the preferred method today because the identifying codes flowing over the link are created using a MD5 one-way hash, which is more secure that the clear-text passwords sent by PAP. 51. If NVRAM lacks boot system commands, where does the router look for the Cisco IOS by default? A. ROM B. RAM C. Flash D. Bootstrap E. Startup-.config Answer :C Explanation :Flash memory - Either an EEPROM or a PCMCIA card, Flash memory stores fully functional IOS images and is the default location where the router gets its IOS at boot time. Flash memory also can be used to store any other files, including configuration files. 52. What could be the rationale behind using passive-interface command when configuring a router? A. Allows interfaces to share common IP addresses. B. Allows an interface to remain up without the aid of keepalives. C. Allows a router to send routing and not receive updates via that interface. D. Allows a routing protocol to forward updates that is missing its IP address. E. Allows a router to receive routing updates on an interface but not send updates via that interface. Answer :E Explanation:The passive-interface command is used to control the advertisement of routing information. The command enables the suppression of routing updates over some interfaces while allowing updates to be exchanged normally over other interfaces. For any interface specified as passive, no routing information will be sent. Routing information received on that interface will be accepted and processed by the router. This is often useful for DDR links such as ISDN. 53. You are a systems administrator at Braindumps and you've just acquired a new Class C IP network. Which of one of the subnet masks below is capable of providing one useful subnet for each of the above departments (support, financial, sales & development) while still allowing enough usable host addresses for each departments needs? A. B. C. D. E. F. 255.255.255.128 255.255.255.192 255.255.255.224 255.255.255.240 255.255.255.248 255.255.255.252 Answer :C Explanation:The network currently consists of 5 networks and another network will be acquired. That gives us atotal of 6 networks. This requires that we use 3 bits for the network address. Using the formula 2n-2 we get 6. This also leaves us with 5 bits for hosts, which gives us 30 hosts. 54. You are a network administrator at Braindumps. You need to troubleshoot the Braindumps network shown in the exhibit. Study the Exhibit carefully: The host, EX1, is connected to the Braindumps1 LAN, but it cannot get access to resources on any ofthe other networks. The host's configuration is as follows: Host address: 192.168.5.45 Subnet mask: 255.255.255.240 Default gateway: 192.168.5.32 Which of the following is the cause of this problem? A. The default gateway is a subnetwork address. B. The default gateway is on a different subnet address as the host. C. The IP address of the host is on a different subnet. D. The host subnet mask is incompatible to the subnet mask of the attached router interface. Answer :A Explanation:The range of the subnet used in this question is 192.168.166.32 to 192.168.166.47.192.168.166.32 is the network address and 192.168.166.47 is the broadcast. This leaving a usable host address range of 192.168.166.33 to 192.168.166.46. The default gateway for the host should be 192.168.166.33. 55. Which of the following are benefits of segmenting a network with a router? (Select all that apply) A. Broadcasts are not forwarded across the router. B. All broadcasts are completely eliminated. C. Adding a router to the network decreases latency. D. Filtering can occur based on Layer 3 information. E. Routers are more efficient than switches and will process the data more quickly. F. None of the above. Answer :A, D