LN8-14
advertisement

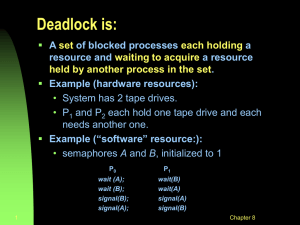
CET 386 Summer 2002 Lecture Notes Chapter 8 - Deadlocks What is deadlock? 4 necessary conditions which must hold simultaneously: mutual exclusion, hold-andwait, no preemption, circular wait Resource assignment graph: resources and processes (nodes) with assignment edges and request edges. If graph has no cycles then there is no deadlock. If there is a cycle there may be deadlock. In a system with only one instance per resource a cycle implies deadlock Methods used by OS for handling deadlock 1. Prevent/avoid 2. Recover 3. Ignore Prevention methodologies contradict one or more of the necessary conditions. I) Require that processes request all resources before starting - if can’t be granted don’t run. II) Processes only permitted to request resources when they hold none. III) If a resource request cannot be granted, halt process and take away resources held. Give back and restart when all available simultaneously. IV) If a resource request cannot be granted, take them away from some other process. V) Provide a total ordering of resources and only grant requests if up along the order. Or release ones ahead in the order. Note in I&II resource utilization may be low and starvation is possible. Note in III&IV cancels prevention condition. Note V prevents circular wait. Avoidance methodologies generally require that the OS be given advanced knowledge of resource requirements of processes and let the system manage scheduling of processes and assignment of resources so that deadlock does not occur. Usually means run a deadlock avoidance algorithm( at least once) before running a process to see deadlock could occur. If so do something else. If a system doesn’t prevent or avoid deadlock, things slow down and eventually come to a halt. At that point an administrator could kill off some or all of the processes involved or take away some resources. But which processes or resources? To find out use a deadlock detection algorithm. These are costly and time consuming (O(n2)). Recovery ideas Kill off all processes involved – drastic. Kill off one at a time till deadlock gone – select a victim – what criteria? Preempt resources – select victim. If any of the above need to rollback computations => requires prior setup. Can starvation be prevented. CH 5-7 1 CET 386 Summer 2002 Lecture Notes Chapter 9 – Memory Management Memory – an array of randomly accessible and addressable words (words does not imply any particular number of bits or bytes) Words may contain CPU instructions or data. Data or instructions are bound at various times (both before and after beginning of process execution). See Figure 9.1 [a good diagram of the various binding times]. Logical address space (what the program thinks of memory addresses). Physical address space – where the instructions/data actually are in the computer’s memory. Management of the mapping of logical to physical addresses handled by by the memory management unit. Dynamic loading is the delaying of loading (bringing into memory) of a routine until it is needed. Routine is in relocatable format until that time. Improves memory utilization. Dynamic linking involves delay of the binding of libraries until needed. Makes it easier to have shared libraries. Know overlays, swapping, backing store. Paging Frames vs pages Addresses composed of page number and offset in page Page number used as index into page table that has frame numbers (if mapped) Page tables kept in memory (usually) For hardware assist there is usually a Page-table-base-register Frequently the hardware supports a cache of the mappings kept in an associative memory frequently called a TLB (translation look-aside buffer). Know what a hit ratio is and how to compute the effective memory access time given the hit ratio. Valid bit usefulness. Multilevel page tables are … Inverted page tables are … No section 9.5 or 9.6 Chapter 10 – Virtual Memory Virtual memory is . . . Its advantages are . . . Demand paging Page fault (trap) Locality of reference and effect on paging given caches of pages and address mappings. Effective memory access time = (1-pfr)*mat+pfr*pftime CH 5-7 2 CET 386 Summer 2002 Lecture Notes Page replacement – what frame to evict if no frame available. Several possibilities – want the one with the lowest page-fault rate. Choices – FIFO [yuck], Optimal [the best – but we’ll never know enough], LRU [near optimal], second-chance [widely used, too bad – why] Belady’s anomaly Thrashing what is it and what is its cause. How can it be limited. Working set model, working set window Memory Mapped Files & Copy-On-Write/Reference Don’t do 10.7 Chapter 11 – File Systems What is a file? What are directories? What are some of the file attributes and operations on/to a file and some of the OS data structures needed to support or do the operations? Ditto directories Protection => access => access types; control via ACLs and groups File-Systems – organization and layering File allocation methods Free Space management – bit vector linked list Skip 11.5 Chapter 12 – File Systems Implementation Layering Typical data structures Mounting VFS Skip 12.3 Disk block allocation & free space management – pluses and minuses Skip 12.6 and .7 Skip most of NFS – know fundamental protocol architecture (RPC over UDP) not details CH 5-7 3 CET 386 Summer 2002 Lecture Notes Chapter 13 – I/O Systems I/O hardware see Figure 13.1 and description Understand polling and interrupts including interrupt cycle Understand DMA Application I/O Interface Character vs block Sequential vs random-access Blocking vs non-blocking Kernel I/O concepts Scheduling, buffering, caching, spooling, See figure 12.10 Lifecycle of an I/O request Skip 13.6 Chapter 14 – Mass-Storage Structure 14.1, 3, 5 only – general concepts CH 5-7 4