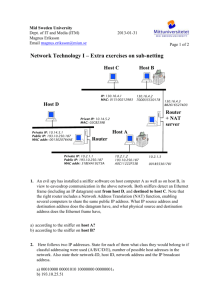
Inter-networking
advertisement

Computer Networks Introduction A computer network is a group of computers which are connected together to allow communication between them. Computers connected to a network are known as stations. All of the computers connected to a network must be identified by unique addresses. Two types of addresses, MAC addresses and IP addresses, are used for this purpose. LANs and WANs Computer networks are classified as being either Local Area Networks (LANs) or Wide Area Networks (WANs). Important properties of LANs and WANs are : Properties of LANs Located entirely on one site. Baseband operation. Fast transmission of data. Lower error rates. Properties of WANs Located on several sites in different areas. Broadband operation. Slow transmission of data. Higher error rates. 1. Advantages of connecting a group of computers together using a LAN instead of using them as stand alone machines are : Sharing of expensive resources such as printers reduces cost. Files stored on a file server can be accessed and used from any station. Access to a centralised database of information is possible. Email can be used to communicate between computers. 2. Disadvantages of connecting a group of computers together using a LAN instead of using them as stand alone machines are : The initial outlay on network interface cards, cables etc. can be expensive. The failure of a network cable or server might cause the whole network to stop functioning. Viruses could be transmitted over the network. Unless appropriate security measures are taken it could be easier to steal or destroy data stored on a networked computer. -- Page 1 -- Topology The topology of a network is the theoretical arrangement of the interconnections between the components on the network. This can be thought of as the geographical layout of the components. There are two topologies that you need to know about. They are Bus and Star. Topology 1 : Bus This used to be the most common topology due to its low cost and easy setup. All of the stations in a bus network are connected together by one main cable. The main cable has terminators at each end. Stations can be connected to the main cable using “T pieces” or by sockets and drop leads. Advantages and Disadvantages Advantages Disadvantages This is the cheapest type of network to If the cable is broken at any point none of the connected cable as all of the stations are simply stations will be able to use the network. connected to one long cable. As the number of computers connected to the network increases the effective rate of data transmission slow It is easy to add and remove stations to/from the network. significantly. This is because the number of collisions increases rapidly (see below). Access Method The method that is used to determine when a station can transmit data on a bus network is known as Carrier Sense Multiple Access / Collision Detection of CSMA/CD for short. It works like this : Each station that has data to send monitors the traffic on the network and waits until no other stations are sending data. When a station with data to send detects that there is no traffic on the network it will start to send its data. There are two possible outcomes when the station starts to send : Data Sent Successfully If no other stations attempt to send data at the same time then the data will be sent successfully. Once the other stations detect that a station is transmitting they will wait until it finishes before attempting to send. Collision Occurs Often (especially on large networks) several stations will have been waiting to send data and they will all start transmitting at the same time. To overcome this problem, as a station sends data, it listens to the data that is actually going round the network. If this differs from the data that it is sending then two stations must have started transmitting at the same time. All the stations that are transmitting will detect this “collision” and will immediately stop sending. The stations that were sending then each wait a random time interval before trying to send again. Waiting a random time reduces the likelihood that they will all start sending at the same time again and cause another collision. -- Page 2 -- Ethernet : An Example of a Bus Network Ethernet is the most common standard for data transmission of LANs. It was originally based on a bus network using the CSMA/CD system but nowadays it usually makes use of switched instead. Currently, standard Ethernet can transmit data at 100Mbs and faster Gigabit Ethernet (1000Mbps) is now available but is more expensive. Topology 2 : Star In a star network each station that is part of the network is connected directly by its own cable to a central device. In a server based network this would usually be the file server but more commonly it is some type of switch (see later). All communication takes place via the central device. Advantages and Disadvantages Advantages Disadvantages If a cable breaks, only the one station that is If the central device fails then none of the connected to the central device by that cable is stations on the network can communicate. unable to use the network. It is expensive to cable a start network as each station must have its own cable which The network can transmit data quickly even when many stations are connected as each runs back to the central device. station has its own dedicated cable to connect it to the central device. All data must pass through the central device. This makes it easy to monitor network traffic and enforce security measures. Access Method Because each computer has its own dedicated cable connected to the central device there is no need for an access method such as CSMA/CD or token passing to determine which station can send data at a particular time. Any station can transmit data down its own cable at any time. The speed at which data can be transmitted will depend upon the speed at which the central device can receive and (when required) forward messages to their destination. -- Page 3 -- Hybrid Topologies : Switched Ethernet Network engineers who produce networks to be used in the real world have attempted to create hybrid topologies which can achieve most of the advantages of the standard bus and ring without all of the disadvantages. One method of doing this is to use an enhanced Ethernet system that incorporates devices known a switches. This produces a network that is a mixture of a bus and a star topology: Backbone S C C S C C S C C C C S = Switch C = Computer The switches are connected together using one main cable. This is usually known as the network backbone and is effectively a bus. No stations are connected directly to the backbone. Instead the individual stations are each connected to a nearby switch by a dedicated cable. The portion of the network between the switch and the stations is like a star topology. A switch is a device which has many sockets to allow many stations to be connected through it to a network backbone. Usually switches have 16 or 24 sockets. A switch will also have a special socket to allow it to connect to the network backbone. In a typical office environment the backbone cable would run through the entire building. Each room that had computers in it would have one switch connected to the backbone cable and all of the stations in the room would be connected to the switch. Inside a switch, a buffer is used to temporarily store packets of data as they are received down cables from stations. The switch then forwards these packets to the correct destination station by retransmitting them down the correct cable (and only this cable, once it has learnt which computers are plugged into which socket). Because packets are only sent down the cables that they need to be, collisions do not occur. The main advantages of using an Ethernet system with switches instead of a standard star or bus topology are : The efficiency of the network is improved as no collisions occur, so no bandwidth is wasted on lost packets, and more stations can be added to the network than could be added to a standard bus topology. It is cheaper to cable than a star system because only one main cable is required. The individual cables that connect each station to the network only have to run a short distance to a nearby switch. They do not all have to run a long distance to one central device. It is more reliable than a bus system. If a cable connecting a station to a switch breaks then only that one station will be affected. All of the other stations will continue to be able to use the network (Note however that if the main backbone cable fails none of the computers will be able to use the network). -- Page 4 -- Inter-networking Inter-networking is the connecting together of different networks (which may be owned and used by the same or different groups of users) to allow data to be transmitted between them. The Internet is the biggest example of inter-networking of networks. Two networks that are connected together to form a bigger network are known as subnets or segments. Bridges A bridge is a device that is used to connect together two segments of a network, passing data between the segments as required. A bridge monitors the data that is being sent on the two segments that it connects. If data is being sent from a station on one segment to a station on the other segment then the bridge will copy the data from the source segment to the destination segment so that it can reach the destination station. On the other hand, data sent between two stations on the same segment will not be copied to another segment by a bridge. Bridges can only be used to connect together two network segments that use the same protocol. Segment 1 Segment 2 Segment 3 Bridge Bridge This means that several communications can take place simultaneously on a network that has been segmented with bridges : If two stations on segment 1 are communicating with each other then, at the same time, two stations on segment 2 could also be communicating with each other. However, if a station on segment 1 is communicating with a station on segment 2 then no other communication can take place on either of these segments at the same time. The main advantage of dividing a network up into segments using bridges is that the capacity (bandwidth) of the network will be increased because several communications can take place at the same time (at most one per segment). On a non-segmented network only one communication can take place at a time. The greater the number of computers that are connected to a network, the greater the advantages are of segmenting it, as traffic on each segment will reduce and so the number of collisions will reduce dramatically. Two further advantages of segmentation are: The network becomes more reliable as the failure of a cable in one segment will usually only affect that segment; computers on other segments will continue to be able to communicate as normal. The network becomes more secure as packets are only transmitted within one segment, unless they are destined for a computer on another segment. This means that it is not possible to attempt to hack all transmissions from any point on the network. To get the maximum advantage from using bridges it is important that not too much data needs to be passed from one segment to another. Therefore careful planning about where to divide networks up into segments and place bridges is required. -- Page 5 -- Gateway A gateway is a device that (like a bridge) allows two networks to be connected together. However, unlike a bridge a gateway can be used to link together two networks that use different protocols. If a packet of data needs to be passed from one network to another, a gateway will convert the data in the packet from the protocol used on the source network to the protocol used on the destination network. Router A router is a device that identifies the destination that a packet of data is being transmitted to and chooses an appropriate route to send the packet down to get it closer to its destination. If a packet of data is being sent a long distance, possibly across several networks, then it is likely that it will pass through many routers en route to its destination. The route that a packet will take across a network can be determined entirely when the packet is first transmitted. However it is more common for the route to be determined dynamically as the packet travels. i.e. each router that the packet arrives at will decide which route to retransmit it on. A router will use the information in the destination address that the packet contains to decide how to route it. This shows an example WAN connected by routers. It is a packet switched system. Router Router Source Router Destination Router = Available channel = Actual route taken by a packet Router A router must use an algorithm to determine which route to send a packet along. Possible objectives that this routing algorithm could aim to achieve are : To ensure that transmitted data arrives at its destination as quickly as possible. To balance the amount of traffic travelling down different possible routes to avoid congestion building up. To send the data as cheaply as possible. -- Page 6 -- Local and International Routing This section explains how packets of data are routed from one computer to another across the Internet. Two types of address are used in the routing process: IP addresses and MAC addresses. You will need to understand how IP addresses are made up of a Host ID and a Subnet ID to understand the routing process. Subnets and Subnet Masks IP Address Format: Host ID and Subnet ID IP addresses are split into two parts: A Subnet ID (also known as Network ID) and a Host ID. The Subnet ID is at the left hand end of the IP address and the Host ID is at the right hand end. The Subnet ID identifies which subnet the computer with that IP address is on, and the Host ID is a unique number for that computer within the subnet. Here is an example of how an IP address could be split up: 203 . 87 . 43 . 18 Subnet ID Host ID If the IP address was split up in this way, all computers on the subnet would have IP addresses that begin with 203.87.43. This would leave one byte (so 256 possible values) for the Host ID, which would place an upper limit on the number of the computers that could be on the subnet. You might reasonably assume that this would be 256, but two values are reserved for special purposes, so if the IP address is split like this, 254 computers can be on the subnet. The split between the Subnet ID and Host ID does not have to be in the position shown in the above example. Another possibility would be: 203 . 87 . 43 . 18 Subnet ID Host ID In this second example, all computers on the subnet would have IP addresses that begin with 203.87. As two bytes are now left for the Host ID, more computers could be on this subnet than in the first example but there are practical reasons why this is less common than the first case - mostly because it makes sense to logically divide a network up into small segments to aid management. Subnet Masks The network manager decided how the IP address should be split between Subnet ID and Host ID by setting a Subnet Mask on all of the computers. The Subnet Mask is logically ANDed with an IP address to extract the Subnet ID from the IP address. Example 1: Subnet Mask is 255.255.255.0 This Subnet Mask indicates the first three bytes of the IP address are the Subnet ID and the remaining byte is the Host ID. ANDing the IP address 203.87.43.18 with 255.255.255.0 gives the result 203.87.43.0 which reveals the subnet ID as being 203.87.43. -- Page 7 -- Example 2: Subnet Mask is 255.255.0.0 This Subnet Mask indicates the first two bytes of the IP address are the Subnet ID and the remaining two bytes are the Host ID. ANDing the IP address 203.87.43.18 with 255.255.0.0 gives the result 203.87.0.0 which reveals the subnet ID as being 203.87. Routable and Non-Routable IP Addresses For the IP addressing system to work, it is important that every device connected to the Internet has a unique IP address. Packets could not be routed using IP addresses if more than one device had the same IP address. But there are problems with this concept: There are only 4 billion IP addresses available under the IPv4 scheme, and because of the hierarchical organisation of them, the actual number that can be used is really less than this. IPv6 is being introduced to address this upper limit. How can we ensure that every device is given a unique address when these are set in software? e.g. when you add a new computer to your home network, how do you know it does not have the same IP address as another computer in Mali? The answer to this is that, really, not all IP addresses are unique. In fact, there are two classes of IP address: Routable IP Addresses: These are unique. They are allocated internationally in a hierarchical manner. For example, a certain range of IP addresses will be allocated to the UK, then of these an organisation in the UK will allocate a certain range to BT, a certain range to Virgin etc. When your home router connects to the Internet, your ISP's DHCP system will allocate it a routable IP address which will be unique. Non-routable IP Addresses: These are not unique. Specific ranges of IP addresses are reserved as being non-routable. The most commonly used on of these blocks begins with 192.168. If you connect a device to a home router it will be allocated an IP address beginning with 192.168. This will be unique on your home network, but worldwide there will be many devices with the same IP address. So, if for example you open a web page on the Internet, how does the web server know where to send the web page back to? The simple answer is that this request will be registered as having come from your router, which does have a unique Routable IP address so the web page will be sent to your router, and it will keep track of which computer on your network requested the page and will send the page back to that specific computer. Key differences between routable and non-routable IP addresses: Routable Globally unique. Allocated globally using a hierarchical system. Used by devices connected directly to the Internet. Non-Routable Many computers will have the same address. Not allocated centrally. Can only be used by devices that are not connected to Internet or a connected through another device like a router. -- Page 8 -- The Routing Process Two different types of address are used when routing data: IP addresses are used to route packets of data across the Internet. e.g. 192.168.2.7 MAC addresses are used to identify the destination computer to send a packet to on an individual network subnet. e.g. 00-B0-D0-86-BB-F7 Step 1: Local Routing on the Subnet Two distinct addresses are used to identify computers on a subnet. They are: IP address: This is a software address that can be set manually on a computer or allocated automatically to a compute by a DHCP server. The IP address can be changed. MAC address: This a hardware address set on the network card in the computer. It cannot be easily altered and every networkable hardware device has a unique MAC address. The first step that a computer that has data to send must take is to check whether or not the computer that it sending the data to is on the same subnet. To do this it uses its own IP address, the IP address of the destination computer and also a Subnet Mask. The Subnet Mask is logically ANDed with the IP address of both the source computer and the destination computer. If the result of both these operations is the same, then the two computers are on the same subnet. Otherwise, they are not. Example 1: Computer 192.168.2.4 wants to send data to computer 192.168.2.3. The subnet mask is 255.255.255.0. 192.168.2.4 and 255.255.255.0 = 192.168.2.0 192.168.2.3 and 255.255.255.0 = 192.168.2.0 Both the results are 192.168.2.0 so both these computers are on the same subnet. Example 2: Computer 192.168.2.4 wants to send data to computer 203.27.4.37. The subnet mask is 255.255.255.0. 192.168.2.4 and 255.255.255.0 = 192.168.2.0 203.27.4.37 and 255.255.255.0 = 203.27.4.0 As 192.168.2.0 and 203.27.4.0 are not the same, the destination computer is on a different subnet. If the destination computer is on the same subnet as the source, then the source computer sends the packet of data to the MAC address of the destination computer. If it is not, the source computer sends the packet of data to the MAC address of the router or gateway that connects that subnet to other subnets or the Internet. -- Page 9 -- Step 2: Routing across the Internet The first thing that a router in a home/office will do when it receives a packet of data to send to another subnet is to determine if this is another subnet within the home/office or if it is on the Internet. The router will then either forward the packet to another internal router, or forward it onto the Internet. Routers on the Internet are ordered in a hierarchical manner and the IP address is used to determine what route a packet should be passed down. A packet may pass through many routers on the way to its destination. When a packet is received by a router, the router will forward it to the next router that it knows about that is nearer to the destination than it is. The router will not determine the entire course the packet will take, just the next step of its path (known as a hop). Routers automatically build tables that identify the routers that they are connected to, and which paths lead on from these routers, which are known as routing tables. Extended Example: You send an email to a person in New York. On your subnet, the IP address of the destination computer (the email server of the person in New York) is ANDed with your subnet mask, as is your own computer's IP address. The results of these two AND operations are the subnet IDs of the source and destination networks. These are compared by your computer and are different, so your computer sends the packets that make up the email to the MAC address of you home router. Your home router looks at the IP address of the destination computer and determines that this is an address on the Internet. So, it forwards it to the router that it is connected to at your ISP. The ISP looks at the IP address of the destination and determines that this is not another computer on its own network, so it forwards it to a router that connects it to the a national network. Then a router on the national network identifies that the packet is addressed to an IP address in America, so it forwards it to a router than connects to a trans-Atlantic connection. At the other end of this connection, a router receives it and identifies that the destination IP address is of a computer in New York. It forwards it to a router in New York. In New York, the router recognises from the IP address the ISP of the person the email is to and forwards the packet to a router at this ISP. The router at the ISP recognises from the subnet ID in the IP address that the computer the data is being sent to (the email server) is on its network, so it now looks up the MAC address of the email server and sends the data directly to that. -- Page 10 -- Server Based and Peer-to-Peer Networking One of the most important reasons for connecting computers to a network is to let the computers on the network share expensive resources such as file storage space and printers. Access to these resources must be managed in some way. This can be achieved using either a server based network or a peer-to-peer network. Server Based Networks The most common type of network used in a business or school environment is a server based network. On a server based network access to shared resources like storage devices and printers is obtained through special server computers. Two different types of computer are connected to a server based network: Server : A computer which provides services to other computers on the network. For example, a file server will allow users to save and load files, a printer server will let users send documents to a shared printer. Client : A computer which uses the resources provided by servers. A typical network will have a small number of servers (possibly just one) but many clients. Client Client Client A large server based network may have more than one file or printer server connected to it. Other types of sever include email, web and database servers. Peer-to-Peer Networks Peer-to-peer networks do not have special computers which are used as servers. Instead any computer on the network can share its resources with other computers and can also access resources that are shared from any other computer. Each computer on the network can be viewed as having equal status. Peer-to-peer networks are cheaper to set up and easier to manage than server based networks. They are however less secure. Because of this peer-to-peer networks are used mainly by small companies who trust their employees and do not have the necessary technical staff to maintain a server based network. -- Page 11 -- Comparison of Server Based and Peer-to-Peer Networks Comparison Server Based Storage/Printers Access to storage devices and printers is through dedicated computers known as servers. Security Security is controlled by a central servers. Users must log on before they can access network resources. Reliance Number of Users Because access to resources is via servers, if a server fails the computers on the network will not be able to access resources connected to it. Dedicated server computers need to be purchased, so set up costs can be expensive. Suitable for large numbers of users who must be managed. Typical Use In a company, school etc. Cost -- Page 12 -- Peer-to-Peer Any computer can access storage devices and printers connected to any other computer. There is little security. Users of individual computers may be able to make local resources secure using passwords but there is no central control of security. No reliance on central servers. If a station fails, only the resources connected to it can not be accessed. Resources on other stations remain available. No dedicated servers are required, so set up costs are low. Suitable for small numbers of users who can all be trusted not to interfere with each others work etc. At home. Thin Client Computing In a thin-client network stations connect to a central server on which all processing takes place. Workstations themselves have very little processing power and no hard disk storage. Their primary purpose is to communicate key presses and mouse movements to the central server and to display the results of the processing on a monitor. This is the opposite of a thick (or fat) client machine on which the processing is done locally. As (almost) all processing is completed on the server, the server must have a fast processing capacity, a lot of RAM and a large amount of secondary storage space. Also, as the clients must communicate with the server after each key press, thin clients require greater network bandwidth than thick clients so faster network cabling and switches will be required. Comparison of thin client and thick/fat client Comparison Hardware Network Cost Updates Security Speed Thin client Each client has a low power processor, very little RAM and no secondary storage. The server must have fast (multiple) processors, a lot of RAM and lots of secondary storage. A fast network is required as there is a lot of communication with the server. As processing is done on servers, it is only these that need to be regularly updated; this can lead to saving as opposed to regularly replacing all workstations Updates only need to be made on the server, saving time and ensuring that all workstations access the same version of the software As security is centrally controlled it can help to make system more secure. Thin-client is not suitable for applications such as gaming and video editing or other applications with a high bandwidth requirement. Thick/Fat client Each client does its own processing and storage, so required adequate processor, RAM and hard disk drive. A slower network is adequate as communication with server only takes place at certain times e.g. when logging on, loading a file. All workstations may need replacing to keep up with the increased demands of new programmes. Updates need to be made to each work station. This can be time consuming and can lead to inconsistencies if workstations are missed. Elements of security are workstation based, leading to possible security breaches. As processing is done locally demanding applications can be run without the need to pass data over the network. -- Page 13 -- Web Services Web 2.0 is the concept that the pages on the world wide web can be interactive and can, therefore, be used to deliver content such as software to users through their web browsers. Software as a Service (SaaS) uses these principles to deploy software to users over the internet. Applications are hosted on servers and customers access these across the internet. Examples include Google Docs and Office 365 which let you run applications such as a word processor over the Internet in your web browser. Documents produced are saved on servers in "the cloud". Advantages of SaaS 1. No need to upgrade software or install patches. 2. Lower hardware requirements for computers as the processing is done on web server. 3. No one-off purchase cost. 4. Software can be used from anywhere there is an Internet connection, e.g. at home as well as the office. 5. Software can be used on any platform e.g. Windows, Mac, Tablet device. Disadvantages of Saas 1. Reliance on Internet - an unreliable Internet connection may mean software is inaccessible. 2. Slow connection speed may make software difficult 3. to use. 4. Concern over security of saved documents. 5. Reliance on the company that develops the software to keep providing the service. 6. May be an ongoing cost to pay for using the software. Ajax is a group of tools used to aid creating interactive web applications. It can be used to retrieve data from part of a page and without having to refresh the whole page. -- Page 14 -- Wireless Networking Wireless networking allows devices to be added easily to any point of a network without the need for running cables. Wireless networking is often preferred to running cables as it allows computers to be used in many places and even moved during used, and avoids the difficult / costly /messy process of laying cables. Wireless networks are however almost always slower and less reliable than wired networks. The two main standards for wireless networking are Wi-Fi and Bluetooth. Wi-Fi The Wi-Fi standard incorporates several standards including 802.11a, 802.11g and 802.11n. Wireless networks are typically slower than those connected using cable; they are also more vulnerable as the radio broadcasts can be intercepted. Users of Wi-Fi should take important steps to make their connections more secure. Suitable steps include: Use of WEP/WPA2 security protocols which ensure strong encryption of transmitted data. Use of Extensible Authentication Protocol/EAP. Setting up an approved list of devices so that only devices with a MAC address in the list are allowed to connect. Disabling the broadcast of a Wireless Access Point's SSID (identity) so that it cannot be seen if searched for. Instead, you must type its name in to connect to it. Bluetooth Bluetooth is a wireless protocol, most commonly used to transmit data between devices such as mobile phones and headsets, printers, cameras and video games consoles. Unlike Wi-Fi, Bluetooth is not intended for general networking purposes, but only for connecting together individual devices or small groups of devices. Comparison of Wi-Fi and Bluetooth Comparison Speed Range Number of Connections Wi-Fi Depends on the standard in use. The fastest is 802.11n which has a theoretical maximum speed of 600Mbit/s but this is affected by distance and interference so not really achieved. Indoors, approximately 70m but affected by walls etc. No limit in specification, will depend upon configuration of network, but hundreds. Bluetooth Speed has changed as the specification has but is currently around 3Mbit/s which is slow. There are different classes of Bluetooth device, most have a range of 1 to 10m. Typically 8 devices can communicate together in a piconet as addresses are 3-bit values. Faster speed, increased range and higher number of devices that can be connected means that Wi-Fi is better suited to general networking than Bluetooth. -- Page 15 --