NMDWS IT Security Initiatives 06 Project Closeout Report
advertisement
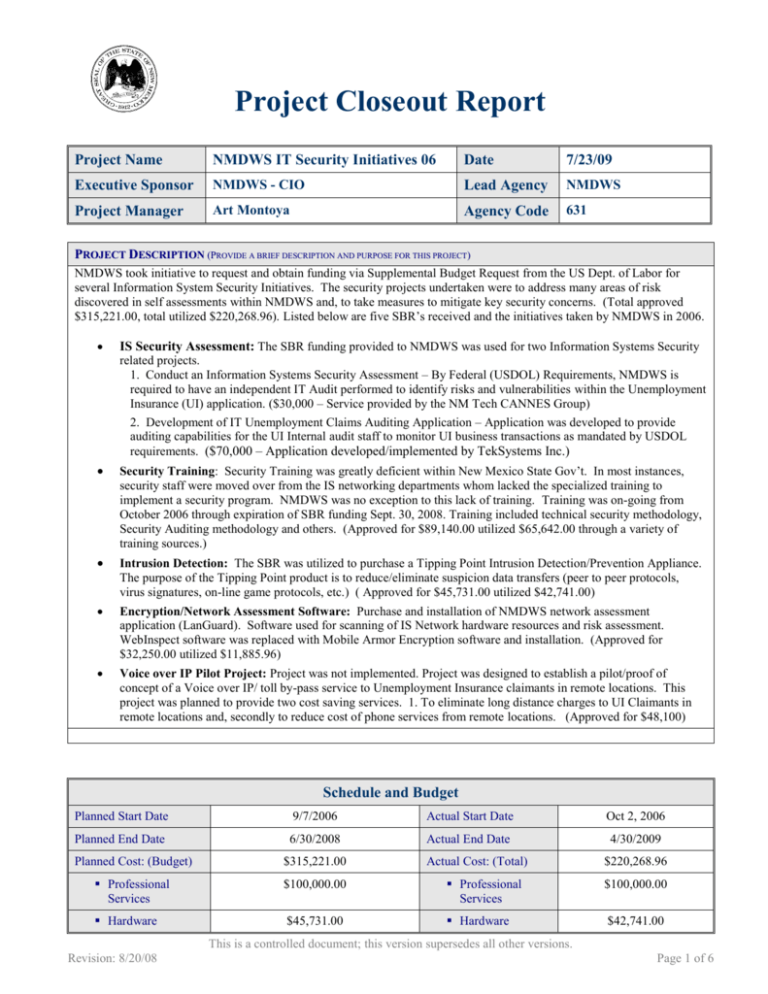
Project Closeout Report Project Name NMDWS IT Security Initiatives 06 Date 7/23/09 Executive Sponsor NMDWS - CIO Lead Agency NMDWS Project Manager Art Montoya Agency Code 631 PROJECT DESCRIPTION (PROVIDE A BRIEF DESCRIPTION AND PURPOSE FOR THIS PROJECT) NMDWS took initiative to request and obtain funding via Supplemental Budget Request from the US Dept. of Labor for several Information System Security Initiatives. The security projects undertaken were to address many areas of risk discovered in self assessments within NMDWS and, to take measures to mitigate key security concerns. (Total approved $315,221.00, total utilized $220,268.96). Listed below are five SBR’s received and the initiatives taken by NMDWS in 2006. IS Security Assessment: The SBR funding provided to NMDWS was used for two Information Systems Security related projects. 1. Conduct an Information Systems Security Assessment – By Federal (USDOL) Requirements, NMDWS is required to have an independent IT Audit performed to identify risks and vulnerabilities within the Unemployment Insurance (UI) application. ($30,000 – Service provided by the NM Tech CANNES Group) 2. Development of IT Unemployment Claims Auditing Application – Application was developed to provide auditing capabilities for the UI Internal audit staff to monitor UI business transactions as mandated by USDOL requirements. ($70,000 – Application developed/implemented by TekSystems Inc.) Security Training: Security Training was greatly deficient within New Mexico State Gov’t. In most instances, security staff were moved over from the IS networking departments whom lacked the specialized training to implement a security program. NMDWS was no exception to this lack of training. Training was on-going from October 2006 through expiration of SBR funding Sept. 30, 2008. Training included technical security methodology, Security Auditing methodology and others. (Approved for $89,140.00 utilized $65,642.00 through a variety of training sources.) Intrusion Detection: The SBR was utilized to purchase a Tipping Point Intrusion Detection/Prevention Appliance. The purpose of the Tipping Point product is to reduce/eliminate suspicion data transfers (peer to peer protocols, virus signatures, on-line game protocols, etc.) ( Approved for $45,731.00 utilized $42,741.00) Encryption/Network Assessment Software: Purchase and installation of NMDWS network assessment application (LanGuard). Software used for scanning of IS Network hardware resources and risk assessment. WebInspect software was replaced with Mobile Armor Encryption software and installation. (Approved for $32,250.00 utilized $11,885.96) Voice over IP Pilot Project: Project was not implemented. Project was designed to establish a pilot/proof of concept of a Voice over IP/ toll by-pass service to Unemployment Insurance claimants in remote locations. This project was planned to provide two cost saving services. 1. To eliminate long distance charges to UI Claimants in remote locations and, secondly to reduce cost of phone services from remote locations. (Approved for $48,100) Schedule and Budget Planned Start Date 9/7/2006 Actual Start Date Oct 2, 2006 Planned End Date 6/30/2008 Actual End Date 4/30/2009 Planned Cost: (Budget) $315,221.00 Actual Cost: (Total) $220,268.96 Professional Services $100,000.00 Professional Services $100,000.00 Hardware $45,731.00 Hardware $42,741.00 This is a controlled document; this version supersedes all other versions. Revision: 8/20/08 Page 1 of 6 Project Closeout Report Software $32,250.00 Software $11,885.96 Network $48,100.00 Network $0.00 Other $89,140.00 Other Appropriation History (Include all Funding sources, $65,642.00 e.g. Federal, State, County, Municipal laws or grants) Amount Funding Source(s) Fiscal Year 2006 $315,221.00 US Dept. of Labor Supplemental Budget Request. Scope Verification Requirements Review Yes Were the project objectives (expected outcomes) accomplished? Were all Deliverables submitted and accepted? Did the IV&V vendor verify that all deliverables met the requirements? Have all contracts been closed? Have all final payments been made (i.e., invoices paid) Has adequate knowledge transfer been completed? No Explanation/Notes X With the Exception of the Voice Over IP Pilot project. This project could not be implemented due to various problems with the UI application, the decision was made to not implement the VoIP because of the potential impact it may have created on production and secondly, VoIP project could not be implemented during peak seasons within NMDWS No IV&V required X X X X X All security Software (Languard, Mobile Armor) purchased were installed and utilized in-house. Intrusion Detection, Auditing Application is located in-house and maintained by NMDWS staff. Auditing application was developed off-site, moved to the NMDWS development and test environments and knowledge transfer was passed to NDMWS staff where application is now supported. This is a controlled document; this version supersedes all other versions. Revision: 8/20/08 Page 2 of 6 Project Closeout Report TRANSITION TO OPERATIONS: (DESCRIBE AGENCY PLAN TO MIGRATE PROJECT SOLUTION TO PRODUCTION. INCLUDE DOIT IMPACT IF DIFFERENT THAN PREVIOUS REPORT) IS Security Assessment: No migration to production necessary. Risks and Vulnerabilities were recorded and an action plan was developed and implemented to mitigate associated risks. ($30,000 – Service provided by the NM Tech CANNES Group) UI Auditing Application. Application was developed off site and was migrated into a NMDWS development environment. Application was moved into a test environment where testing was performed by NMDWS IT and business staff over a two week period. Application was moved to the production environment after testing. This application had no impact on DoIT. Security Training SBR Approved Sept. 7, 2006. Training was on-going from October 2006 through expiration of SBR funding Sept. 30, 2008. (Approved for $89,140.00 utilized $65,642.00 through a variety of training sources.) Intrusion Detection: The SBR was utilized to purchase a Tipping Point Intrusion Detection/Prevention Appliance. The purpose of the Tipping Point product is to reduce/eliminate suspicion data transfers (peer to peer protocols, virus signatures, on-line game protocols, etc.) ( Approved for $45,731.00 utilized $42,741.00) Network Assessment Applications: Purchase and installation of NMDWS network assessment application. Software used for scanning of IS Network hardware resources and risk assessment. WebInspect software was replaced with Mobile Armor Encryption software and installation. Voice over IP Pilot Project: Project was not implemented. Project was designed to establish a pilot/proof of concept of a Voice over IP/ toll by-pass service to Unemployment Insurance claimants in remote locations. This project was planned to provide two cost saving services. 1. To eliminate long distance charges to UI Claimants in remote locations and, secondly to reduce cost of phone services from remote locations. (Approved for $48,100) Maintenance/Operations Yes No Explanation/Notes Tipping Point: $ 4,768.00 Are there recurring maintenance/operational costs for the product/service? Are there any recommended enhancements or updates? Funding source for maintenance/operational costs? X per Year for Support/updates LanGuard: $ 169.98 per Year For Support/updates/licensing X UI Auditing Application requires enhancements to capture transactions due to change in business within the UI program. NMDWS Base Budget BUSINESS PERFORMANCE MEASURES (COMPLETE FOR ALL PHASES) COMMENTS: Supplemental Budget Requests for IT Security Initiatives. The funding period for the SBR’s was from Sept. 2006 to September 30, 2008. Performance Measurements are summarized on each individual Close out Report. PHASES COMPLETION DATE GOALS/OBJECTIVES AMOUNT RESULTS This is a controlled document; this version supersedes all other versions. Revision: 8/20/08 Page 3 of 6 Project Closeout Report Initiation: $ Planning: $ IS Security Assessment: NMDWS took initiative to request and obtain funding via Supplemental Budget Request from the US Dept. of Labor for several Information System Security Initiatives. Conduct an Information Systems Security Assessment ($30,000 – Service provided by the NM Tech CANNES Group) 2. Development of IT Unemployment Claims Auditing Application ($70,000 developed by TekSystems Inc.) September 2006 Certification of IT Security Initiatives $315,221 Security Training: Security (utilized $65,642.00 through a variety of training sources.) Intrusion Detection: Purchase Tipping Point Intrusion (utilized $42,741.00) Encryption/Network Assessment Software: Purchase and installation of NMDWS assessment application (LanGuard). Mobile Armor Encryption software (utilized $11,885.96) Implementation: Voice over IP Pilot Project: Not Implemented. (Approved for $48,100) This is a controlled document; this version supersedes all other versions. Revision: 8/20/08 Page 4 of 6 Project Closeout Report 07/27/2009 Close out all NMDWS 2006 SBR funding for IT Security Initiatives $0.00 All projects deliverables completed or closed with the exception of the Voice Over IP pilot project Closeout: LESSONS LEARNED Understanding and adhering to reporting requirements at State and Federal levels. Understanding project requirements, allocating resources both internal and external to keep project creep from occurring. It was difficult to allocate dedicated resources to the various projects due to staff maintaining a production environment and all other daily tasks provided to an already stretched staff. Understanding the procurement process and working with the procurement agents in a manner that does not interfere with scheduled time frames for project deliverables. IT System Analysis On this document, or as an attachment, provide a summary response, including changes, to the following IT infrastructure topics relating to this project: Describe or estimate this project’s impact on the Enterprise/DoIT infrastructure. The IS Security Initiatives had no impact on the Enterprise/DoIT infrastructure. o Hardware o Network (Include Diagram) o Software / Applications All software is installed within the NMDWS networked environment, No software or application has any impact on the enterprise network or DoIT infrastructure. o Where is this system hosted? All security initiatives are hosted within NMDWS. If not hosted at DoIT Data Center what is your strategy to host at DoIT Data Center: (When, Why?) NMDWS is working in collaboration with NM on an effort to consolidate security efforts. DoIT Migration Collaboration Summarize your collaboration with DoIT on moving this project from initialization through close (full production). Identify points of contact, dates of discussions, and results Provide Application Architecture Schematic This is a controlled document; this version supersedes all other versions. Revision: 8/20/08 Page 5 of 6 Project Closeout Report Business Continuity Strategy On this document, or as an attachment, provide a summary response, including changes, of your business Continuity Strategy. No changes were necessary for the Business Continuity Strategy within NMDWS. Presently NMDWS has a limited Business Continuity/ Disaster Recovery Plan which addresses the Critical UI application, tape backup and off-site storage. Business Continuity planning for the NMDWS is currently being addressed through the submission of a SBR through USDOL. Emergency and Disaster Management Business Resumption Operational Recovery Planning Security Strategy (Application and Data Security Process, Plan, or Standard) Project Sign Off The signatures below certify that this project has been completed in accordance to the specified budget, schedule, scope, and achieved the intended outcome. STAKEHOLDERS NAME: SIGNATURE DATE Executive Sponsor (or Designee) Lead Agency Head (or Designee) CIO IT Lead Project Manager This is a controlled document; this version supersedes all other versions. Revision: 8/20/08 Page 6 of 6