1 - RGPV question paper
advertisement

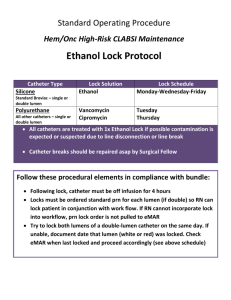
1. An Area holding a group of recods which are addressed jointly is called as a (a) block (b) Bucket c) extent d)data set 2. the concept of locking can be used to solve the problem of (a) lost update (b) uncommitted dependency (c) inconsistent data (d) deadlock 3. the entity-relationship model comes under (a) object based logical model (b) record based logical model (c) physical data model (d) none of the above 4. if every non-key attribute is functionally dependent on the primary key, then the relation will be in (a) First normal form (b) second normal form (c) third normal form (d) fourth normal form 5. the column of a table is referred to as the (a) tuple (b) attribute (c) entity (d) degree. 6. The data flow model of an application mainly shows (a) the underlying data and the relationships among them (b) Processing requirements and the flow of data (c) Decision and control information (d) Communication network structure. 7. Which of the following statement is/are correct (a) the word virtual means that the item in question appears to exist to the programmer but is actually not (b) transparent data appears to exist to the programmer but in fact does not exist (c) virtual data is handled by paging concept (d) transparent data appears not to exist but in fact does exist. 8. Choose the correct statement(s) (a) A file having two dimensional layout of data elements is called as a flat file. (b) The index table where files are stored in reverse order is called as the inverted list (c) uniquely defined primary key always consists of a single field (d) All of the above. 9. In airline reservation system, the entities are date, flight number, place of departure, destination, type of plane and seats available. The primary key is (a) flight number (b) flight number + place of departure (c) flight number + date (d) flight number + destination. 10. Data management is a discipline that focuses on a. the management of end users. b. the proper generation, storage, and retrieval of data. c. the help items to be used by end users. d. the proper generation, storage, and retrieval of information. 11. DBMSs are important because a. we need good ways of managing such data. b. they contain a query language that makes it possible to produce ad hoc queries. c. they help create an environment for end users to have access to more data. d.All of the above e.None of the above 12. Which of the following could be defined as a field in a database? a.Customer_Name b.Address c.Phone_Number d.all of the above 13. All fields for a specific entity can be grouped together as a(n) a.object. b.element. c.table. d.database. 14. A relational database is a group of a.common fields. b.field values. c.records. d.related tables. 15.A relational database data is organized as a.a collection of records. b.a collection of common fields. c.elements. d.tables. 16. DBMS allows you to extrapolate information from your data by using a a.query language. b.table generator. c.report generator. d.wizard. 17.Most DBMS are referred to as _____________database management systems. a.elemental b.linked c.hierarchical d.relational 18. A primary key a. consists of only one field. b.has the same value for all records. c.must contain a unique value for each record within the table. d.is defined automatically. 19. A foreign key must a.be numeric. b.be unique. c.be defined in all tables within the database. d.match the field value of a primary key in a related table. 20. The Access DBMS allows you to create database structures containing a. table relationships. b. tables. c. fields. d.all of the above 21. The Hierarchical database model is based on a. tree structure. b.lack of a parent segment. c. lack of a child segment. d. none of the above 22. An ad hoc query is a. a pre-scheduled question. b. a spur of the moment question. c. a pre-planned question. d. none of the above 23. John is working in the customer table and needs to know what customers are located in Florida. To find the information he would a. create a new table. b. create a new form. c. create a new query. d. utilize the Database Wizard. 24. Nulls, if used improperly, can create problems because they can represent: a. An unknown attribute value. b. A known, but missing, attribute value. c. A "not applicable" condition. d. All of the above e. None of the above 25. Assumes transaction a holds a shared loack R. if transaction b also requests for a shared lock on R. a. it will result in a deadlock situation. b. It will immediately be granted. c. It will immediately be rejected. d. It will be granted as soon as it is released by A. 26. The referential integrity rule requires that a. every null foreign key value must reference an existing primary key value. B. it makes it possible for an attribute to have a corresponding value. c. every non-null foreign key value must reference an existing primary key value. d. it makes it possible to delete a row in one table whose primary key does not have a matching foreign key value in another table. 27. Each table must have a. a primary key. b. a secondary key. c. a foreign key. d. a logical key. 28. A Relational operator that yields values from all rows in a table is known as a a. difference. b. product. c. select. d. project. 29. A Relational operator that yields all values from selected attributes is known as a a. difference. b. product. c. select. d. project. e. join. 30. A Relational operator that allows for the combination of information from two or more tables is known as a a. select. b. project. c. product. d. difference. e. join. 31. In a relationship, when a primary key from one table is also defined in a second table, the field is referred as a ____________in the second table. a. combined key b. redundant field c. primary key d. foreign key 32. A Relational operator that yields all possible pairs of rows from two tables is known as a a. union. b. intersect. c. difference. d. product. e. project. 33. It might take more than a single attribute to define functional dependence; that is, a key may be composed of more than one attribute. A multi-attribute key is known as a _____ key. a. primary b. super c. composite d. foreign 34. Within a table, the primary key must be unique so that it will identify each row. When this is the case, the table is said to exhibit ___________. a. referential integrity. b. entity integrity. c. enforced integrity. d. all of the above 35. When designing a new database, it is a good idea to a. avoid data redundancy. b. include redundant fields. c. include a common field in all tables. d. use composite keys. 36. Database designers employ data models as communications tools to facilitate the interaction among a. the designers. b. the applications programmers. c. the users. d. all of the above. 37. The conceptual model represents a _____________ view of the data. a. single b. simple c. partial d. global 38. A relationship is an association between a. objects. b. entities. c. databases. d. fields. 39. Cardinality expresses __________ number of entity occurrences associated with one occurrences of the related entity. a. an undetermined b. the specific c. a pre-determined d. a programmed 40. Normalization stages are a. 1NF. b. 2NF. c. 3NF. d. all of the above. e. none of the above. 41. A table that is in 2NF and contains no transitive dependencies is said to be in a. 1NF. b. 2NF. c. 3NF. d. 4NF. e. BCNF. 42. The SQL command that lets you insert data into a table, one row at a time, is a. insert. b. select. c. commit. d. update. e. rollback. 43. The SQL command that lets you save your work to disk, is a. insert. b. select. c. commit. d. update. e. rollback. 44. The SQL command that lets you list the table contents is a. insert. b. select. c. commit. d. update. e. rollback. 45. The SQL command that enables you to make changes in the data is a. insert. b. select. c. commit. d. update. e. rollback. 46. To list all the contents of a PRODUCT table you would use a. LIST * FROM PRODUCT; b. SELECT * FROM PRODUCT; c. DISPLAY * FROM PRODUCT; d. SELECT ALL FROM PRODUCT; 47. When making corrections you would use the following command a. CHANGE PRODUCT SET P_INDATE = '01/18/2002' WHERE P_CODE = '13-Q2/P2'; b. ROLLBACK PRODUCT SET P_INDATE = '01/18/2002' WHERE P_CODE = '13-Q2/P2'; c. EDIT PRODUCT SET P_INDATE = '01/18/2002' WHERE P_CODE = '13-Q2/P2'; d. UPDATE PRODUCT SET P_INDATE = '01/18/2002' WHERE P_CODE = '13-Q2/P2'; 48. To remove the value 2238/QPD from the product table you must use the following command a. DELETE FROM PRODUCT WHERE P_CODE = '2238/QPD'; b. REMOVE FROM PRODUCT WHERE P_CODE = '2238/QPD'; c. ERASE FROM PRODUCT WHERE P_CODE = '2238/QPD'; d. ROLLBACK FROM PRODUCT WHERE P_CODE = '2238/QPD'; 49. To select partial table contents you must use the command a. SELECT <column(s)> FROM <Table name> WHERE <item>; b. LIST <column(s)> FROM <Table name> WHERE <Conditions>; c. SELECT <column(s)> FROM <Table name> WHERE <Conditions>; 50. You want the contents of the PRODUCT table listed by P_Price in ascending order listing P_CODE, P_DESCRIPT, P_INDATE, and P_PRICE. The command will be a. SELECT P_CODE, P_DESCRIPT, P_INDATE, P_PRICE FROM PRODUCT SEQUENCE BY P_PRICE; b. SELECT P_CODE, P_DESCRIPT, P_INDATE, P_PRICE FROM PRODUCT LIST BY P_PRICE; c. SELECT P_CODE, P_DESCRIPT, P_INDATE, P_PRICE FROM PRODUCT ORDER BY P_PRICE; d. SELECT P_CODE, P_DESCRIPT, P_INDATE, P_PRICE FROM PRODUCT ASCENDING BY P_PRICE; 51. The basic SQL aggregate function that gives the number or rows containing not null values for the given column is a. COUNT b. MIN c. MAX d. SUM e. AVG 52. The basic SQL aggregate function that gives the total of all values for a selected attribute in a given column is a. COUNT b. MIN c. MAX d. SUM e. AVG 53.The basic SQL aggregate function that gives the arithmetic mean for the specific column is a. COUNT b. MIN c. MAX d. SUM e. AVG 54. A lock that prevents the use of any tables in the database from one transaction while another transaction is being processed is called a a. database-level lock. b. table-level lock. c. page-level lock. d. row-level lock. e. field-level lock. 55. A lock that locks the entire table preventing access to any row by a transaction while another transaction is using the table is referred to as a a. database-level lock. b. table-level lock. c. page-level lock. d. row-level lock. e. field-level lock. 56. A lock that allows concurrent transactions to access different rows of the same table is known as a a. database-level lock. b. table-level lock. c. page-level lock. d. row-level lock. e. field-level lock. 57. A lock that has only two stages (0 & 1) is known as a(n) a. shared lock. b. exclusive lock. c. binary lock. d. two-phase locking. e. deadlocks. 58. A condition that occurs when two transactions wait for each other to unlock data is known as a(n) a. shared lock. b. exclusive lock. c. binary lock. d. two-phase lock. e. deadlocks. 59. A consistent database is one in which a. No users are simultaneously updating the same tables. b. No users are simultaneously viewing the same tables. c. No foreign keys have null values. d. All data integrity constraints are satisfied. e. All of the above. 60. The _____ rule specifies that an entity can be a member of only one subtype at a time. A) removal B) exclusion C) disjoint D) inclusion E) overlapping 61. For the following diagram, which answer is true? A) Each employee can supervise 1 to many employees. B) Each employee can manage many departments. C) Each employee works in one department. D) A and B E) A and C 62. A relationship between the instances of a single entity type is called a(n) _____ relationship. A. Binary B. Tertiary C. Primary D. Ternary E. unary 63. An attribute or attributes that uniquely identify each row in a relation is called a(n) A) field pointer. B) column. C) primary key. D) foreign key. E) duplicate key. 64. Data modeling may be the most important part of the systems development process because a) data characteristics are important in the design of programs and other systems components. b) The data in a system are generally more complex than processes, and play a central role in development. c) Data are less stable than processes. d) A and B. e) B and C. 65. A database is an organized collection of _____ related data. a) not b) badly c) physically d) logically e) none of the above 66. Disadvantages of traditional file processing systems include a) reduced data duplication. b) program-data dependence. c) limited data sharing. d) B and C. e) A and B. 67. In the following diagram, which of the answers below is true? a) Each patient has one or more patient histories. b) Each patient has one and only one visit. c) Each patient history belongs to one and only one patient. d) A and B e) A and C 68. A(n) _____ specifies the number of instances of one entity that can be associated with the each instance of another entity. a) maximum b) cardinality constraint c) limit d) counter constraint e) degree 69. According to the figure, which of the following are subtypes of patient? a) responsible physician bB) bed c) outpatient d) all of the above eE) none of the above 70. Duplication of data in files may cause a) data integrity problems. b) data items with the same names used for different purposes. c) data items with different names in different files. d) A and C eE) all of the above. 71. Which of the following is NOT an advantage of database systems? a) better data quality b) program-data independence c redundant data d) standards enforcement e) reduced program maintenance 72. If a relation scheme is in BCNF, then it is also in a) first normal form. b) second normal form c) third normal form d) all of the above e) B and C 73. Which of the following is NOT a function of a DBMS? a) data storage, retrieval, and update. b) logical data dependence. c) recovery services. d) integrity services. e) concurrency control. 74. A group of associated fields is called a _______. a) record b) field c) attribute d) table 75. The database oriented approach _______ the redundancy of data compared to the file oriented approach a) reduces b) increases c) None of the above 76. The database oriented approach does not support multiple views of the same data. a) True b) False 77. What type of database is described as an electronic repository? a) A database used to store, sort and manipulate information b) A database used to store vast quantities of information that can be searched for relevant information c) A database management system d) An older database system 78. What is one function of a database management system (DBMS)? a) Ensuring usability b) Identifying what a user needs c) Deciding what to do with legacy systems d) Preventing errors arising, while enabling multiple, simultaneous users 79. Which of the following is not one of the three stages in planning a database? a) Backup and recovery b) Implementation c) Establishing requirements d) Designing the database 80. Which database structure consists of a set of two or more related tables with a minimum of one shared field between them? a) Hierarchical b) Network c) Object-oriented d) Relational 81. When considering database usability issues, what does information density refer to? a) The amount of data appearing on the screen b) Information enabling the user to identify their location in the database c) The type of relationship between two entities d) Prompts or text boxes with reminders or alerts 82. What is data integrity? a) The inability to view a database because of system problems b) Data being unavailable because it is being used by another user c) Maintaining consistency of the data in a database d) Preventing disclosure of information that causes harm 83. What are constraint rules? a) Rules governing how the data may exist in the database b) A program that trawls through the database looking for inconsistencies c) Rules that limit the actions that particular users can perform d) A program that regularly archives old data 84. What is a logical data model? a) A item about which information is stored in the database b) The model that focuses on representing the data as it exists in the real world c) The models that identify the data that different groups will need and will eventually translate into forms and reports d) Characteristics attached to each entity 85. Guidelines for creating tables in a relational database include which of the following? a) Only one table in the database needs a primary key b) The primary key need not be unique c) Attributes may appear in several tables d) Data must be atomic 86. What is an inference attack? a) Incorrect information in a database b) Partial disclosure of information to an unauthorised individual c) Trying to obtain information from a database by making connections between seemingly unrelated data d) A security measure that alerts the database administrator that a breach of confidentiality has occurred 87. Which of the following schemes are used to ensuring atomicity? a) Log with deferred modification. b) Log with immediate modification. c) Shadow paging. d) None of the above. 88. Generally speaking, for a weak entity set to be meaningful it must be part of a a) one-to-one relationship. b) One-to-many relationship. c) Many-to-many relationship. d) None of the above. 89. Who is the following is more concerned about the conceptual level of the DBMS/ a) DBA. b) The end user c) system programmer d) client 90. The emp-salary should not be greater than rs. 2000. this is a) integrity constraint. b) Referential constraint. c) Over-defined constraint. d) Feasible constraint. 91. The set of permitted values for each attribute is called its a) attribute set. b) attribute range c) domain d) group. 92. E-R model technique is a a) top-down approach b) bottom-up approach c) left-right approach d) none of the above. 93. consider the following set of functional dependencies on the scheme (A, B, C) A BC BC AB ABC The cannonical cover for this set is a) A BC and BC b) A BC and ABC c) A BC and AB d) A B and BC 94. STUDENT and COURSE ENROLLED, is an example of a) one-to-one relationship. b) One-to-many relationship. c) Many-to-one relationship. d) Many-to-many relationship. 95. In an E-R diagram ellipses represent. a) entity sets b) relationship among entity sets. c) attributes. d) lisk between attributes and entity set. 96. What operator performs pattern matching? a) LIKE operator. b) AND operation. c) Is operator. d) None of the above. 97. EXISTS, SOME, ANY are operators in SQL. A) True B) False 98. Which is the subset of SQL commands used to manipulate Oracle Database structures, including tables? a) Data manipulation language (DML) b) Data control language (DCL) c) Data Definition Language (DDL) d) None of the above. 99. Tables derived from the ERD a) Are totally unnormalised b) Are always in 1NF c) Can be further denormalised d) May have multi-valued attributes 100. In mapping of ERD to DFD a) entities in ERD should correspond to an existing entity/store in DFD b) entity in DFD is converted to attributes of an entity in ERD c) relations in ERD has 1 to 1 correspondence to processes in DFD d) relationships in ERD has 1 to 1 correspondence to flows in DFD 1. b 6. b 11.d 16. a. 21. a 26. c 31. d 36. d 41. c 46. b 51. a 56. d 61.e 66. d 71. c 76. a 81. a 86. c 91. c 96. a 2. a,b,c 7.a,b,c 12. d 17.d 22. b 27. a 32. d 37.d 42.a 47. d 52. d 57.c 62. e 67.e 72. c 77. b 82. c 87. a,b,c 92. a 97.a ANSWER 3. a 8.a 13.c 18.c 23.c 28.c 33.c 38.b 43.c 48. a 53. e 58. e 63. c 68. b 73.b 78. d 83. a 88.b 93. a 98.c 4.c 9.c 14.d 19.d 24.d 29.d 34. b 39. b 44.b 49. c 54. a 59. a 64. d 69.c 74. a 79. a 84.b 89.a 94.d 99.b 5.b 10.b 15.d 20. d 25.a 30.e 35.a 40.d 15.d 50.c 55.b 60.b 65. d 70. d 75. a 80. d 85.d 90.a 95.c 100. a