Rapportmall - IT-teknikerprogrammet (Linnéuniversitetet)
advertisement

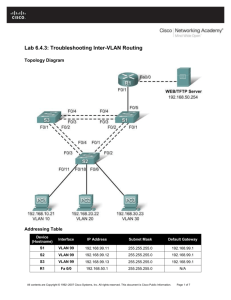
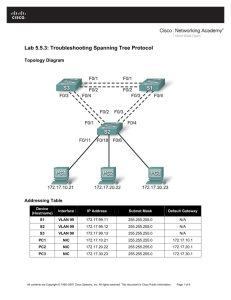
Essay Differences between STP Protocols Author: Dan Wangberg Term: HT13 Course: 1DV447 Advanced LAN Technologies 1 (18) Table of Contents Table of Contents ............................................................................................. 2 1. Problem Definition................................................................................... 3 2. Topology ...................................................................................................... 4 3. Configuration ............................................................................................... 5 3.1 About the Configuration ...................................................................... 14 4. Tests............................................................................................................ 15 5. Reflections ................................................................................................. 17 6. References .................................................................................................. 18 2 (18) 1. Problem Definition As we all know there are numerous types of STP and they all intend to fill some form of special purpose. There is also lots of information regarding the different protocols[1], but not when to actually use them. Thus when to actually use what protocol is to me yet unknown. When is MSTP better than RSTP, how many Vlans are suitable to have when using the different protocols and how fast respectively slow are they with different number of vlans. I intend to further look in to these protocols and test them to try and figure out when it is appropriate to use what type of STP. For example lets say there are three switches connected to eachother in a triangle formation. Each of the switches contains 10 vlans. What would be most suitable to use, MSTP, RSTP, PVST? There are numerous occasions and different scenarios to test, but I am hoping that I can conclude a baseline of where the different protocols are ”best”. Another example with the same topology could be if we now have two or more links between the switches, since this might make MSTP a more attractive protocol than STP. The number of Vlans could also be changed. To do this I intend to compare them with eachother. Setting up different scenarios and testing them using the different protocols. Measure the speed I get when netperfing the different Vlans, aswell as checking how long the downtime will be for failure. In order to do this three connected switches in a triangle will be required. The tests that will be conducted are as follows; Check the throughput of the links when using different protocols Check what happens when adding Vlans when the switchs is operational Forcing STP to recalculate its path and see how long it takes. Investigate how long it takes for ”cold” switches to start up and calculate their paths using different protocols Besides these practical test a theoretical analysis will be done regarding the different protocols, to see if the literature and other sources have any adequate explanations on the matter in question. These sources will lean heavily on the Cisco course material and configuration guides. 3 (18) 2. Topology The following is the topology used for conducting all the practical tests. Note that R3 is used as router on a stick for the switches while R2 and R1 is being used by other members of the group. 4 (18) 3. Configuration The following is the show running-configuration output from the different units that affect my part of the topology. R3 Building configuration... Current configuration : 1126 bytes ! version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname R3 ! boot-start-marker boot-end-marker ! ! no aaa new-model memory-size iomem 10 ! ! ip cef ! ! ! ! voice-card 0 no dspfarm ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! ! interface FastEthernet0/0 no ip address shutdown duplex auto speed auto ! interface FastEthernet0/1 no ip address 5 (18) S2 duplex auto speed auto ! interface FastEthernet0/1.10 encapsulation dot1Q 10 ip address 10.10.10.2 255.255.255.128 ! interface FastEthernet0/1.20 encapsulation dot1Q 20 ip address 10.10.10.130 255.255.255.128 ! interface FastEthernet0/1.50 encapsulation dot1Q 50 ip address 11.0.0.1 255.255.255.128 ! interface FastEthernet0/1.51 encapsulation dot1Q 51 ip address 11.0.0.129 255.255.255.128 ! interface Serial0/0/0 no ip address shutdown clock rate 125000 ! interface Serial0/0/1 no ip address shutdown clock rate 125000 ! ! ! ip http server no ip http secure-server ! ! ! ! ! control-plane ! ! ! ! ! ! ! ! ! ! line con 0 line aux 0 line vty 0 4 login ! scheduler allocate 20000 1000 ! end Show runn Building configuration... 6 (18) Current configuration : 3422 bytes ! version 12.2 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname S2 ! boot-start-marker boot-end-marker ! ! no aaa new-model system mtu routing 1500 ip subnet-zero ip routing ! ! ! ! --More-crypto pki trustpoint TP-self-signed-4185319936 enrollment selfsigned subject-name cn=IOS-Self-Signed-Certificate-4185319936 revocation-check none rsakeypair TP-self-signed-4185319936 ! ! crypto pki certificate chain TP-self-signed-4185319936 certificate self-signed 01 3082023B 308201A4 A0030201 02020101 300D0609 2A864886 F70D0101 04050030 31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274 69666963 6174652D 34313835 33313939 3336301E 170D3933 30333031 30303030 35315A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649 4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D34 31383533 31393933 3630819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281 810096B9 74AA0B44 90719192 73E137FC BF3DA694 AE2BAA91 9277277A BF716F22 3B83DA0C D2452DBF 6EF55F74 5B8AD6FB 98338C2B 5EEBB8D4 0E3FC235 BA579C2D 4AAC24BB 5C4922F9 31F0009D A4B1D64A 1F8AE764 E794A0AF A4CBE680 DE71FD18 DBE1D45F 910E0EB6 ECEDF128 8D7510ED B796E813 235A6F43 9681A11E 8700A425 EBE30203 010001A3 63306130 0F060355 1D130101 FF040530 030101FF 300E0603 551D1104 07300582 0353322E 301F0603 551D2304 18301680 14ADF22D 3752119D FA5329BC DF30E1C8 4D0FEE66 38301D06 03551D0E 04160414 ADF22D37 52119DFA 5329BCDF 30E1C84D 0FEE6638 300D0609 2A864886 F70D0101 04050003 81810042 --More-54CCB7C2 0B43AADD 0FF67A60 1C065E27 BA32FA32 D0325C9A C99A5C16 F74CC2E9 2DE103D0 85592EEC BA6C5D04 228BFFBC 722A5495 205BE050 CD695DA6 7BA7CBC2 2CA06A72 67217A03 4F0AD94D E41C54D1 C5A50A76 5BFDCC01 B4681B29 99A2A745 F4ACFB2B E12DC9A9 5207CE6B 0B770B45 99EA698D 76578260 86435B62 39AFE1 quit ! ! ! 7 (18) ! ! ! spanning-tree mode pvst spanning-tree extend system-id no spanning-tree vlan 225-1001 ! vlan internal allocation policy ascending ! ! ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 --More-switchport access vlan 10 switchport mode access ! interface FastEthernet0/3 no switchport ip address 11.0.2.1 255.255.255.128 ! interface FastEthernet0/4 no switchport ip address 11.0.2.129 255.255.255.128 ! interface FastEthernet0/5 ! interface FastEthernet0/6 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! interface FastEthernet0/9 ! interface FastEthernet0/10 ! --More-interface FastEthernet0/11 switchport access vlan 10 switchport mode access ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 switchport trunk encapsulation dot1q switchport mode trunk 8 (18) ! interface FastEthernet0/20 --More-switchport trunk encapsulation dot1q switchport mode trunk ! interface FastEthernet0/21 switchport trunk encapsulation dot1q switchport mode trunk shutdown ! interface FastEthernet0/22 switchport trunk encapsulation dot1q switchport mode trunk ! interface FastEthernet0/23 ! interface FastEthernet0/24 ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface Vlan1 no ip address ! --More-ip classless ip http server ip http secure-server ! ! ! control-plane ! ! line con 0 line vty 0 4 login line vty 5 15 login ! end S4 S2# Show runn Building configuration... Current configuration : 3412 bytes ! version 12.2 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption ! hostname S4 ! boot-start-marker boot-end-marker ! 9 (18) ! no aaa new-model system mtu routing 1500 ip subnet-zero ! ! ! ! crypto pki trustpoint TP-self-signed-3180427776 --More-enrollment selfsigned subject-name cn=IOS-Self-Signed-Certificate-3180427776 revocation-check none rsakeypair TP-self-signed-3180427776 ! ! crypto pki certificate chain TP-self-signed-3180427776 certificate self-signed 01 3082023B 308201A4 A0030201 02020101 300D0609 2A864886 F70D0101 04050030 31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274 69666963 6174652D 33313830 34323737 3736301E 170D3933 30333031 30303030 35305A17 0D323030 31303130 30303030 305A3031 312F302D 06035504 03132649 4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D33 31383034 32373737 3630819F 300D0609 2A864886 F70D0101 01050003 818D0030 81890281 8100EA53 45297063 8ECA3561 931FE18E 48C524D0 DB5277F6 9C89063D 872F134F 3592E067 7CE47A5B 3E270363 2DADEED9 837DDFF9 C92594D2 E8254DCC 94A29C31 3B56C9CF C5E2C472 0C556B80 BEEDA6FC 5779877C 60FADA37 8A776A60 AC539A62 8F58C5B3 7DC66A62 4F31EDDF 432FF044 11CEC9CF 25145523 66F90A7B B01E470C 25F70203 010001A3 63306130 0F060355 1D130101 FF040530 030101FF 300E0603 551D1104 07300582 0353342E 301F0603 551D2304 18301680 14D74982 46CCD45D 111D74AC 1FA58DE3 B7541DEB B6301D06 03551D0E 04160414 D7498246 CCD45D11 1D74AC1F A58DE3B7 541DEBB6 300D0609 2A864886 F70D0101 04050003 81810037 2E857C22 A0C49234 DFBCBFEB 656B239E 6AC8D88B BEBBE50F 2200BF82 FA3103CA --More-0D7A045D B3271FF7 C74B8702 3642C23C AE0480DA 96990D8E 1DA037EE D0A8112D 4169FD06 5D1795E5 AD019991 3737FF5F 19397715 865C550F B0B7C110 7E91C629 50FC8230 8CA8BC45 7955792D 16ED8CD7 4C8572BC 4E5A41FB 875E7BA2 809F0E quit ! ! ! ! ! spanning-tree mode pvst spanning-tree extend system-id ! vlan internal allocation policy ascending ! ! ! interface FastEthernet0/1 switchport mode trunk ! interface FastEthernet0/2 switchport access vlan 53 switchport mode access ! 10 (18) --More-interface FastEthernet0/3 switchport access vlan 52 switchport mode access ! interface FastEthernet0/4 ! interface FastEthernet0/5 switchport access vlan 50 switchport mode access ! interface FastEthernet0/6 switchport access vlan 51 switchport mode access ! interface FastEthernet0/7 switchport access vlan 52 switchport mode access ! interface FastEthernet0/8 switchport access vlan 53 switchport mode access ! interface FastEthernet0/9 --More-! interface FastEthernet0/10 ! interface FastEthernet0/11 switchport mode access ! interface FastEthernet0/12 switchport access vlan 10 switchport mode access ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 --More-switchport mode trunk ! interface FastEthernet0/20 switchport mode trunk ! interface FastEthernet0/21 ! interface FastEthernet0/22 ! interface FastEthernet0/23 switchport mode trunk ! interface FastEthernet0/24 11 (18) switchport mode trunk ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface Vlan1 no ip address no ip route-cache ! --More-ip http server ip http secure-server ! control-plane ! ! line con 0 line vty 0 4 login line vty 5 15 login ! end S5 S4# Show runn Building configuration... Current configuration : 1435 bytes ! version 12.1 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption ! hostname S5 ! ! ip subnet-zero ! ip ssh time-out 120 ip ssh authentication-retries 3 ! ! spanning-tree mode pvst no spanning-tree optimize bpdu transmission spanning-tree extend system-id no spanning-tree vlan 159-200,211-300 ! --More-! ! ! interface FastEthernet0/1 ! interface FastEthernet0/2 switchport access vlan 20 switchport mode access ! 12 (18) interface FastEthernet0/3 switchport access vlan 54 ! interface FastEthernet0/4 switchport access vlan 55 ! interface FastEthernet0/5 ! interface FastEthernet0/6 ! interface FastEthernet0/7 ! interface FastEthernet0/8 ! --More-interface FastEthernet0/9 ! interface FastEthernet0/10 ! interface FastEthernet0/11 ! interface FastEthernet0/12 ! interface FastEthernet0/13 ! interface FastEthernet0/14 ! interface FastEthernet0/15 ! interface FastEthernet0/16 ! interface FastEthernet0/17 ! interface FastEthernet0/18 ! interface FastEthernet0/19 ! interface FastEthernet0/20 --More-! interface FastEthernet0/21 switchport mode trunk ! interface FastEthernet0/22 switchport mode trunk ! interface FastEthernet0/23 switchport mode trunk ! interface FastEthernet0/24 switchport mode trunk ! interface GigabitEthernet0/1 ! interface GigabitEthernet0/2 ! interface Vlan1 no ip address no ip route-cache ! ip http server 13 (18) ! --More-line con 0 line vty 0 4 login line vty 5 15 login ! ! end S5# 3.1 About the Configuration Note that some of the configuration are used by other members of the group. Also note that during the tests the configuration is changed, however this is not attached in the essay, only explained during the tests. An example of this is the changing of STP mode or the adding and removing of VLANs. 14 (18) 4. Tests The first test conducted was to check the throughput of the network when using different STP modes. Granted, the packets are quite small and are quite similar, but I did belive that some differences would present themselfs due to various hello-timers and other things. The test was done by using netperf, a tool to check how much throughput you can get from one netperfinstance to another[2]. The test was done five times using the different protocols MSTP, Rapid PVST and PVST. This resulted in the following throughputs; PVST 91.67 91.68 91.66 91.67 91.64 STP Not supported Not supported Not supported Not supported Not supported MSTP 91.66 91.66 91.68 91.66 91.67 PVST+ 91.66 91.67 91.67 91.67 91.65 (Note that I had intended to test STP aswell but it was not supported on the switches.) The second test was to see what would happen if one were to add several vlans when having an active ping to see if the switch would drop any packages. My hypothosis here were that the cpu of the switch might be strained enough to make the network less reliable. By adding 120 vlans to the switchs while the ping was active, the cpu only reached about 30% workload. Adding more vlans was not possible as the maximum number of STP instances the switch in question could have was 128. The third test was done to see how long it would take the different protocols to recalculate their paths when the root port went down. This was done by setting up a ping between two vlans and then shutting down interface fa 0/21 which in this case was rootport and checking how many pings would be lost. The images on the next page shows the testresults. 15 (18) MSTP PVST RPVST As one can see from the tests 31 pings were lost druing the tests, regardless of protocol. The last test done was starting up the switches using the different protocols to determine which would be up and running the fastest. The time it took for the switches to boot up and sucesfully transmit a ping using the different STP were as follows; STP Not supported PVST 1.55 sec PVST+ 1.53 MSTP 1.53 This shows that the PVST+ and MSTP were a bit faster than normal PVST. 16 (18) 5. Reflections All of the tests done and all of the resarch I did indicates one thing. It does not matter at all what protocol you use. Obviously in a large network pvst+ is better than pvst due to it being a tad faster. But part from this their is actually not much thats different with these protocols. When doing the tests I first tried adding about a 1000 vlans to check the cpu workload on the switches. This was while having VTP on. This resulted in the switches complaing that they had exceeded the maxmimum number of vlans allowed. By looking up the different switches configurationguide I noticed that the Catalyst 2950 only supports 64[3] STP instances and the 3560 only supports 128[4]. This means that even though my tests showed that their were no differences in what you use, depending on the types of switches you are using it actually does matter. In a network with more than 64 vlans with 2950 switches using pvst would not work. MSTP would have to be used to circumvent this. In other words as soon as you have more vlans than the amount of stp instances your switches can handle MSTP is the better choice. However in a network were 20 vlans are presant and 3560 switches are used it would not actually matter if you used pvst or MSTP. I personally find mstp a bit easier to configure and decide where the traffic should traverse the network, but this is perfectly doable in PVST aswell, hence it is not something that negativly impacts the PVST protocol. The tests I performed could have been done using wireshark and checking the individual packets for a more extensive result than what my tests showed. However I was not intrested in exactly how many bytes of overhead the different protocols would produce. I wanted to know if there were any real reasons why one protocol would be better t use than another. My tests did not show many differences at all in the protocols. I find this as intressting as if they had shown lots of differences. Now it is clear that they are actually extremly similar and the only real thing that has to be taken into account when deciding what to use is weather or not you will have more vlans than your switches amount of viable stp instances. I do not belive that the other groupmembers impacted my tests in any way. When one person were conducting their tests the other members would have to wait, as the tests would be tainted otherwise. The topology did suffice for the tests I performed, but could have been made more extensive with more switches and more paths throughout the network. 17 (18) 6. References [1] D. Huckaby, CCNP Switch 642813: Official Certification Guide, Indianapolis: Cisco Press, 2011. [2] Netperf.com. 2014-01-09. [Online]. Available: http://www.netperf.org/netperf/ [3] Cisco.com. 2014-01-08. [Online]. Available: http://www.cisco.com/en/US/docs/switches/lan/catalyst2950/software/release /12.1_6_ea2c/configuration/guide/swgstp.html [4] Cisco.com. 2014-01-08. [Online]. Available: http://www.cisco.com/en/US/docs/switches/lan/catalyst3750x_3560x/softwar e/release/12.2_55_se/configuration/guide/swstp.html 18 (18)