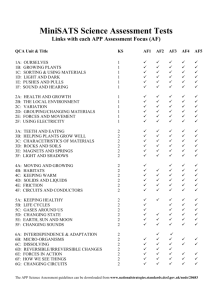
1. List 5 applications that use the Internet. e
advertisement

1. List 5 applications that use the Internet. e-mail, file transfer, remote login, WWW, file sharing (P2P systems such as E-mule, etc), skype, VoIP based applications, teleconference applications (e.g., NetMeeting, WebEx, etc.). 2. What are "stand-alone" computers? Give an example mentioned in class. Stand Alone computers are those which are unconnected from other computers. Such as a single home pc, not connected to the Internet or older-generation mainframe computers. 3. What is the main principle behind the telephone network? Explain. The main purpose was to allow for voice communication from one end user to another. This is done as a direct connection between the end users. The telephone network was designed for voice communication and as its main design principle used "circuit switching". Circuit switching networks establish a physical circuit or connection between the end points engaged in the communication. By doing so, it reserves the necessary resources to guarantee a successful call. These resources are used exclusively by the call in progress, i.e., are not shared with any other call even when the call is idle. 4. How is it different from the main principle behind the internet? Explain The internet was instead developed with the goal of providing data communication between users. It uses the principle of "packet switching", which allows several calls, or connetions, to share the same set of resources. 5. What are packets? Packets are the body of a message, as well as the encapsulation of that packet, transmitted over the internet. In the Internet, application-layer messages are broken down into smaller self-contained pieces that can be routed from the source of the message to its destination, independent of one another. 6. What were the first 3 internet applications? Email, File Transfer, Remote Login 7. What is a "killer app"? In your opinion, what is/was the internet's "killer app"? A killer app is one which is the hottest thing out there, the application which all services and providers will build up upon / make use of, in order to draw in their customers. In my opinion, the general killer app would be email, which has allowed communication on a much larger and faster scale than previously [there are many possible answers here as long as they are justified/explained; e.g., i would say that the Internet's killer app is the Web.] 8. What is the IETF? The IETF is the Internet Engineering Task Force, which is charged with providing standardized documentation to influence the design, use, and management of the Internet. 9. How are IP addresses assigned? From Wikipedia: The Internet Assigned Numbers Authority (IANA) is the entity that oversees global IP address allocation, root zone management for the Domain Name System (DNS), media types, and other Internet Protocol related assignments. It is operated by the Internet Corporation for Assigned Names and Numbers, better known as ICANN. Prior to the establishment of ICANN for this purpose, IANA was administered primarily by Jon Postel at the Information Sciences Institute at the University of Southern California, under a contract USC/ISI had with the United States Department of Defense, until ICANN was created to assume the responsibility under a United States Department of Commerce contract. IP addresses are assigned by essentially the same process depending on the scale. Externally, as seen by the world, IP addresses are assigned by the IANA, the Internet Assigned Numbers Authority, which allows for ISPs and businesses to obtain a block of IP addresses which can then be sold to and used by their respective customers. Inside of a local network, a similar situation is seen where IP Addresses are assigned by the local network administrator manually or automatically (via a protocol called DHCP). 10. What is the End to End Principle and how does it apply to the internet? The end to end principle states that whenever possible, communications protocol operations should be set up to occur at the end points of the communications system, as close to the end point as possible. This allows for the heavier weight protocols to be handled out of the main stream of the data, while the lighterweight protocols necessary to transmit the data are used by the network itself.