实验三、传输层、网络层、链路层协议分析
一、 传输层 TCP 协议分析
概述:在这个实验中,我们将详细的研究 TCP 保护协议的行为.我们通过从你的电脑与远
程服务器之间发送 150KB 的文件来分析 TCP 段的发送和接收. 我们将研究 TCP 的使用序
列和确认号来提供可靠的数据传输; 我们将看到 TCP 拥塞控制算法--慢启动和拥塞避免;
我们将着眼于 TCP 的接收流量控制机制. 我们也将简要考虑 TCP 连接的建立,我们将调
查您的计算机和服务器之间的 TCP 连接的性能(吞吐量和往返时间)
。
目的:以 TCP 协议为例,研究传输层协议的具体实现。包括可靠数据传输、拥塞控制实
现以及流量控制机制。
过程和细节:
1. TCP 批量传输分析
a. 打开你的 web 浏览器,进入 http://gaia.cs.umass.edu/wireshark-labs/alice.txt,复
制这篇文章 Alice in Wonderland 到你的电脑。
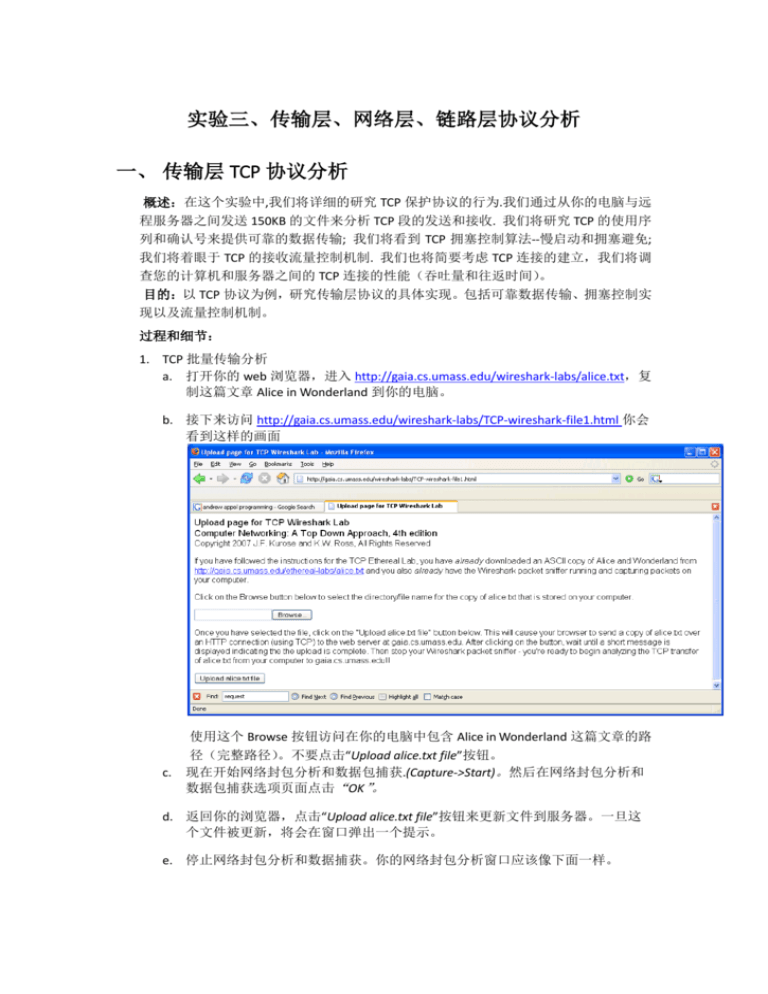
b. 接下来访问 http://gaia.cs.umass.edu/wireshark-labs/TCP-wireshark-file1.html 你会
看到这样的画面
c.
使用这个 Browse 按钮访问在你的电脑中包含 Alice in Wonderland 这篇文章的路
径(完整路径)
。不要点击“Upload alice.txt file”按钮。
现在开始网络封包分析和数据包捕获.(Capture->Start)。然后在网络封包分析和
数据包捕获选项页面点击“OK”
。
d. 返回你的浏览器,点击“Upload alice.txt file”按钮来更新文件到服务器。一旦这
个文件被更新,将会在窗口弹出一个提示。
e. 停止网络封包分析和数据捕获。你的网络封包分析窗口应该像下面一样。
2. TCP trace 分析
a. 在详细的分析 TCP 连接行为之前,先观察追踪的高级视图。可以发现主机和
gaia.cs.umass.edu 之间的一系列基于 TCP 和 HTTP 协议的交换数据。可以分辨出
看到初始的包含 SYN 报文的三次握手,以及一个 HTTP POST 报文。根据正在使
用的网络分析封包的版本,能看到从你的计算机发送到 gaia.cs.umass.edu 的一
系列“HTTP 过程”
。
b. 打开在 http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip 中的网络封包
分析获取的数据包文件 tcp-ethereal-trace-1,回答问题。
c. 在 wireshark 中设置分析的协议,选择 Analyze->Enabled Protocols. 取消 HTTP 协
议的支持,可以看到如下界面:
3. TCP 拥塞控制分析
a. 在网络封包分析的“listing of captured-packets”窗口中选一个 TCP 段,然后选择
Statistics->TCP Stream Graph-> Time-Sequence-Graph(Stevens),可以看到如下的图
片,这是在 http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip 的 tcpethereal-trace-1 跟踪的数据中创建的。
b. 根据实验数据的分析,回答问题
二、 网络层 IP 协议分析
概述:
本实验通过执行 traceroute 程序,探究 IP 协议,实现对 IP 数据报发送和接收流程的追
踪,研究分析 IP 首部各字段中的内容,了解 IP 分片的细节。
目的:
1、利用 Wireshark 工具分析 IP 协议
2、分析 IP 报文段各个字段
3、分析 IP 数据报的分片
基础知识及准备:
熟悉 IP 数据报首部各字段的含义在 Windows 下安装 Wireshark 工具和 pingplotter 工
具。
过程和细节:
1、捕获数据包
1)启动 Wireshark 开始抓包(Capture->Start)
;
2)启动 pingplotter,在“Address to Trace Window” 框中输入目的地址,将“# of times to Trace”
字段设置为 3,报文字段大小可在菜单”Edit->Advanced Options->Packet Options”中改变,初
始值设为 56 字节;然后点击 Trace 按钮,弹出如下图所示的 pingplotter 窗口;
3)等 pingplotter 停止后,依次点击 Edit->Advanced Options->Packet Options ,在 Packet Size
框中输入 2000,再依次点击 OK->Resume 按钮;
4)以同样的方式将数据包大小设为 3500 字节;
5)停止抓包。
2、查看捕获的数据包
在你捕获的数据包中,你可以看到一系列 ICMP Echo Request 报文和 ICMP TTL_exceeded
报文,如下图所示,分析这些报文,回答下列问题。
选择你的主机发送的第一个 ICMP Echo Request 报文,展开查看 IP 首部,回答后面的问
题。
3、IP 分片
单击 Time 栏,按时间先后顺序排列数据报,找到在 pingplotter 中将分组大小改为 2000
字节后的第一个 ICMP Echo Request 报文,回答后面的问题。
找到在 pingplotter 中将分组大小改为 3500 字节后的第一个 ICMP Echo Request 报文,回
答相应问题。
三、 链路层 Ethernet&ARP 协议分析
概述:
本实验将抓取并分析 Ethernet 数据帧的内容,观察 ARP 协议在现实网络中如何工作。
过程与细节:
1.
抓取 Ethernet 数据帧并进行分析:
a. 清空浏览器的缓存,启动 Wireshark 程序;
b. 键入 http://gaia.cs.umass.edu/wireshark-labs/HTTP-ethereal-lab-file3.html ;
c.
停止 Wireshark 程序,选择显示 IP 协议以下的协议,如下图;
d. 分析包含了 Http GET 数据的 Ethernet frame 的内容;
2. ARP 协议分析
a. Windows 操作系统进入 CMD 下,使用 ARP 命令,分析 ARPcache 内容;
b. MS-DOS 下键入 arp-d *命令,清除 ARPcache 内容,清除浏览器缓存;
c.
打开 Wireshark,打开浏览器;
d. 键入 http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-lab-file3.html;
e. 停止 Wireshark,更改 Wireshark 的“listing of captured packets”窗口;
实验结果检查(实验课结束前完成)
:
1. 完成 TCP 协议分析;
2. 完成 IP 协议分析;
3. 完成链路层协议分析
3. 1 人 1 组,上交实验报告;
4. 实验报告回答指导书的问题(红色标记)
附件:
Wireshark Lab: TCP v6.0
Supplement to Computer Networking: A Top-Down
Approach, 6th ed., J.F. Kurose and K.W. Ross
“Tell me and I forget. Show me and I remember. Involve me
and I understand.” Chinese proverb
© 2005-21012, J.F Kurose and K.W. Ross, All Rights
Reserved
In this lab, we’ll investigate the behavior of the celebrated TCP protocol in detail. We’ll do so by
analyzing a trace of the TCP segments sent and received in transferring a 150KB file (containing the
text of Lewis Carrol’s Alice’s Adventures in Wonderland) from your computer to a remote server.
We’ll study TCP’s use of sequence and acknowledgement numbers for providing reliable data
transfer; we’ll see TCP’s congestion control algorithm – slow start and congestion avoidance – in
action; and we’ll look at TCP’s receiver-advertised flow control mechanism. We’ll also briefly
consider TCP connection setup and we’ll investigate the performance (throughput and round-trip
time) of the TCP connection between your computer and the server.
Before beginning this lab, you’ll probably want to review sections 3.5 and 3.7 in the text1.
1. Capturing a bulk TCP transfer from your computer to a remote
server
Before beginning our exploration of TCP, we’ll need to use Wireshark to obtain a packet trace of
the TCP transfer of a file from your computer to a remote server. You’ll do so by accessing a Web
page that will allow you to enter the name of a file stored on your computer (which contains the
ASCII text of Alice in Wonderland), and then transfer the file to a Web server using the HTTP POST
method (see section 2.2.3 in the text). We’re using the POST method rather than the GET method
as we’d like to transfer a large amount of data from your computer to another computer. Of course,
1
References to figures and sections are for the 6th edition of our text, Computer Networks, A Top-down
Approach, 6th ed., J.F. Kurose and K.W. Ross, Addison-Wesley/Pearson, 2012.
we’ll be running Wireshark during this time to obtain the trace of the TCP segments sent and
received from your computer.
Do the following:
Start up your web browser. Go the http://gaia.cs.umass.edu/wireshark-labs/alice.txt and
retrieve an ASCII copy of Alice in Wonderland. Store this file somewhere on your
computer.
Next go to http://gaia.cs.umass.edu/wireshark-labs/TCP-wireshark-file1.html.
You should see a screen that looks like:
Use the Browse button in this form to enter the name of the file (full path name) on your
computer containing Alice in Wonderland (or do so manually). Don’t yet press the
“Upload alice.txt file” button.
Now start up Wireshark and begin packet capture (Capture->Start) and then press OK on
the Wireshark Packet Capture Options screen (we’ll not need to select any options here).
Returning to your browser, press the “Upload alice.txt file” button to upload the file to
the gaia.cs.umass.edu server. Once the file has been uploaded, a short congratulations
message will be displayed in your browser window.
Stop Wireshark packet capture. Your Wireshark window should look similar to the
window shown below.
If you are unable to run Wireshark on a live network connection, you can download a packet trace
file that was captured while following the steps above on one of the author’s computers2. You
may well find it valuable to download this trace even if you’ve captured your own trace and use it,
as well as your own trace, when you explore the questions below.
2. A first look at the captured trace
Before analyzing the behavior of the TCP connection in detail, let’s take a high level view of the
trace.
First, filter the packets displayed in the Wireshark window by entering “tcp” (lowercase,
no quotes, and don’t forget to press return after entering!) into the display filter
specification window towards the top of the Wireshark window.
What you should see is series of TCP and HTTP messages between your computer and
gaia.cs.umass.edu. You should see the initial three-way handshake containing a SYN message.
2
Download the zip file http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip and extract the
file tcp-ethereal-trace-1. The traces in this zip file were collected by Wireshark running on one of the
author’s computers, while performing the steps indicated in the Wireshark lab. Once you have
downloaded the trace, you can load it into Wireshark and view the trace using the File pull down menu,
choosing Open, and then selecting the tcp-ethereal-trace-1 trace file.
You should see an HTTP POST message. Depending on the version of Wireshark you are using,
you might see a series of “HTTP Continuation” messages being sent from your computer to
gaia.cs.umass.edu. Recall from our discussion in the earlier HTTP Wireshark lab, that is no such
thing as an HTTP Continuation message – this is Wireshark’s way of indicating that there are
multiple TCP segments being used to carry a single HTTP message. In more recent versions of
Wireshark, you’ll see “[TCP segment of a reassembled PDU]” in the Info column of the Wireshark
display to indicate that this TCP segment contained data that belonged to an upper layer protocol
message (in our case here, HTTP). You should also see TCP ACK segments being returned from
gaia.cs.umass.edu to your computer.
Answer the following questions, by opening the Wireshark captured packet file tcp-ethereal-trace1 in http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip (that is download the trace and
open that trace in Wireshark; see footnote 2). Whenever possible, when answering a question you
should hand in a printout of the packet(s) within the trace that you used to answer the question
asked. Annotate the printout3 to explain your answer. To print a packet, use File->Print, choose
Selected packet only, choose Packet summary line, and select the minimum amount of packet detail
that you need to answer the question.
1. What is the IP address and TCP port number used by the client computer (source) that is
transferring the file to gaia.cs.umass.edu? To answer this question, it’s probably easiest
to select an HTTP message and explore the details of the TCP packet used to carry this
HTTP message, using the “details of the selected packet header window” (refer to Figure
2 in the “Getting Started with Wireshark” Lab if you’re uncertain about the Wireshark
windows.
2. What is the IP address of gaia.cs.umass.edu? On what port number is it sending and
receiving TCP segments for this connection?
If you have been able to create your own trace, answer the following question:
3. What is the IP address and TCP port number used by your client computer (source) to
transfer the file to gaia.cs.umass.edu?
Since this lab is about TCP rather than HTTP, let’s change Wireshark’s “listing of captured packets”
window so that it shows information about the TCP segments containing the HTTP messages,
rather than about the HTTP messages. To have Wireshark do this, select Analyze->Enabled
Protocols. Then uncheck the HTTP box and select OK. You should now see a Wireshark window
that looks like:
3
What do we mean by “annotate”?
If you hand in a paper copy, please highlight where in the
printout you’ve found the answer and add some text (preferably with a colored pen) noting what you
found in what you ‘ve highlight.
highlight and annotate.
If you hand in an electronic copy, it would be great if you could also
This is what we’re looking for - a series of TCP segments sent between your computer and
gaia.cs.umass.edu. We will use the packet trace that you have captured (and/or the packet trace
tcp-ethereal-trace-1 in http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip; see earlier
footnote) to study TCP behavior in the rest of this lab.
3. TCP Basics
Answer the following questions for the TCP segments:
4. What is the sequence number of the TCP SYN segment that is used to initiate the TCP
connection between the client computer and gaia.cs.umass.edu? What is it in the
segment that identifies the segment as a SYN segment?
5. What is the sequence number of the SYNACK segment sent by gaia.cs.umass.edu to the
client computer in reply to the SYN? What is the value of the Acknowledgement field in
the SYNACK segment? How did gaia.cs.umass.edu determine that value? What is it in
the segment that identifies the segment as a SYNACK segment?
6. What is the sequence number of the TCP segment containing the HTTP POST command?
Note that in order to find the POST command, you’ll need to dig into the packet content
field at the bottom of the Wireshark window, looking for a segment with a “POST” within
its DATA field.
7. Consider the TCP segment containing the HTTP POST as the first segment in the TCP
connection. What are the sequence numbers of the first six segments in the TCP
connection (including the segment containing the HTTP POST)? At what time was each
segment sent? When was the ACK for each segment received? Given the difference
between when each TCP segment was sent, and when its acknowledgement was
received, what is the RTT value for each of the six segments? What is the
EstimatedRTT value (see Section 3.5.3, page 239 in text) after the receipt of each
ACK? Assume that the value of the EstimatedRTT is equal to the measured RTT for
the first segment, and then is computed using the EstimatedRTT equation on page
239 for all subsequent segments.
Note: Wireshark has a nice feature that allows you to plot the RTT for each of the
TCP segments sent. Select a TCP segment in the “listing of captured packets”
window that is being sent from the client to the gaia.cs.umass.edu server. Then
select: Statistics->TCP Stream Graph->Round Trip Time Graph.
8. What is the length of each of the first six TCP segments?4
9. What is the minimum amount of available buffer space advertised at the received for the
entire trace? Does the lack of receiver buffer space ever throttle the sender?
10. Are there any retransmitted segments in the trace file? What did you check for (in the
trace) in order to answer this question?
11. How much data does the receiver typically acknowledge in an ACK? Can you identify
cases where the receiver is ACKing every other received segment (see Table 3.2 on page
247 in the text).
12. What is the throughput (bytes transferred per unit time) for the TCP connection?
Explain how you calculated this value.
4. TCP congestion control in action
Let’s now examine the amount of data sent per unit time from the client to the server. Rather
than (tediously!) calculating this from the raw data in the Wireshark window, we’ll use one of
Wireshark’s TCP graphing utilities - Time-Sequence-Graph(Stevens) - to plot out data.
Select a TCP segment in the Wireshark’s “listing of captured-packets” window. Then
select the menu : Statistics->TCP Stream Graph-> Time-Sequence-Graph(Stevens). You
4
The TCP segments in the tcp-ethereal-trace-1 trace file are all less that 1460 bytes.
This is because
the computer on which the trace was gathered has an Ethernet card that limits the length of the
maximum IP packet to 1500 bytes (40 bytes of TCP/IP header data and 1460 bytes of TCP payload).
This 1500 byte value is the standard maximum length allowed by Ethernet.
If your trace indicates a
TCP length greater than 1500 bytes, and your computer is using an Ethernet connection, then
Wireshark is reporting the wrong TCP segment length; it will likely also show only one large TCP
segment rather than multiple smaller segments.
Your computer is indeed probably sending multiple
smaller segments, as indicated by the ACKs it receives.
This inconsistency in reported segment
lengths is due to the interaction between the Ethernet driver and the Wireshark software.
We
recommend that if you have this inconsistency, that you perform this lab using the provided trace file.
should see a plot that looks similar to the following plot, which was created from the
captured packets in the packet trace tcp-ethereal-trace-1 in
http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip (see earlier footnote ):
Here, each dot represents a TCP segment sent, plotting the sequence number of the
segment versus the time at which it was sent. Note that a set of dots stacked above each
other represents a series of packets that were sent back-to-back by the sender.
Answer the following questions for the TCP segments the packet trace tcp-ethereal-trace-1 in
http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip
13. Use the Time-Sequence-Graph(Stevens) plotting tool to view the sequence number
versus time plot of segments being sent from the client to the gaia.cs.umass.edu server.
Can you identify where TCP’s slowstart phase begins and ends, and where congestion
avoidance takes over? Comment on ways in which the measured data differs from the
idealized behavior of TCP that we’ve studied in the text.
14. Answer each of two questions above for the trace that you have gathered when you
transferred a file from your computer to gaia.cs.umass.edu
Wireshark Lab: IP v6.0
Supplement to Computer Networking: A Top-Down
Approach, 6th ed., J.F. Kurose and K.W. Ross
“Tell me and I forget. Show me and I remember. Involve me
and I understand.” Chinese proverb
© 2005-21012, J.F Kurose and K.W. Ross, All Rights
Reserved
In this lab, we’ll investigate the IP protocol, focusing on the IP datagram. We’ll do so by analyzing
a trace of IP datagrams sent and received by an execution of the traceroute program (the
traceroute program itself is explored in more detail in the Wireshark ICMP lab). We’ll
investigate the various fields in the IP datagram, and study IP fragmentation in detail.
Before beginning this lab, you’ll probably want to review sections 1.4.3 in the text5 and section 3.4
of RFC 2151 [ftp://ftp.rfc-editor.org/in-notes/rfc2151.txt] to update yourself on the operation of
the traceroute program. You’ll also want to read Section 4.4 in the text, and probably also
have RFC 791 [ftp://ftp.rfc-editor.org/in-notes/rfc791.txt] on hand as well, for a discussion of the
IP protocol.
1. Capturing packets from an execution of traceroute
In order to generate a trace of IP datagrams for this lab, we’ll use the traceroute program to
send datagrams of different sizes towards some destination, X. Recall that traceroute
operates by first sending one or more datagrams with the time-to-live (TTL) field in the IP header
set to 1; it then sends a series of one or more datagrams towards the same destination with a TTL
value of 2; it then sends a series of datagrams towards the same destination with a TTL value of 3;
and so on. Recall that a router must decrement the TTL in each received datagram by 1 (actually,
RFC 791 says that the router must decrement the TTL by at least one). If the TTL reaches 0, the
router returns an ICMP message (type 11 – TTL-exceeded) to the sending host. As a result of this
behavior, a datagram with a TTL of 1 (sent by the host executing traceroute) will cause the
5
References to figures and sections are for the 6th edition of our text, Computer Networks, A Top-down
Approach, 6th ed., J.F. Kurose and K.W. Ross, Addison-Wesley/Pearson, 2012.
router one hop away from the sender to send an ICMP TTL-exceeded message back to the sender;
the datagram sent with a TTL of 2 will cause the router two hops away to send an ICMP message
back to the sender; the datagram sent with a TTL of 3 will cause the router three hops away to
send an ICMP message back to the sender; and so on. In this manner, the host executing
traceroute can learn the identities of the routers between itself and destination X by looking
at the source IP addresses in the datagrams containing the ICMP TTL-exceeded messages.
We’ll want to run traceroute and have it send datagrams of various lengths.
Windows. The tracert program (used for our ICMP Wireshark lab) provided with
Windows does not allow one to change the size of the ICMP echo request (ping)
message sent by the tracert program. A nicer Windows traceroute program is
pingplotter, available both in free version and shareware versions at
http://www.pingplotter.com. Download and install pingplotter, and test it out by
performing a few traceroutes to your favorite sites. The size of the ICMP echo request
message can be explicitly set in pingplotter by selecting the menu item Edit->
Options->Packet Options and then filling in the Packet Size field. The default packet size
is 56 bytes. Once pingplotter has sent a series of packets with the increasing TTL
values, it restarts the sending process again with a TTL of 1, after waiting Trace Interval
amount of time. The value of Trace Interval and the number of intervals can be explicitly
set in pingplotter.
Linux/Unix/MacOS. With the Unix/MacOS traceroute command, the size of the
UDP datagram sent towards the destination can be explicitly set by indicating the
number of bytes in the datagram; this value is entered in the traceroute command
line immediately after the name or address of the destination. For example, to send
traceroute datagrams of 2000 bytes towards gaia.cs.umass.edu, the command
would be:
%traceroute gaia.cs.umass.edu 2000
Do the following:
Start up Wireshark and begin packet capture (Capture->Start) and then press OK on the
Wireshark Packet Capture Options screen (we’ll not need to select any options here).
If you are using a Windows platform, start up pingplotter and enter the name of a target
destination in the “Address to Trace Window.” Enter 3 in the “# of times to Trace” field,
so you don’t gather too much data. Select the menu item Edit->Advanced
Options->Packet Options and enter a value of 56 in the Packet Size field and then press
OK. Then press the Trace button. You should see a pingplotter window that looks
something like this:
Next, send a set of datagrams with a longer length, by selecting Edit->Advanced
Options->Packet Options and enter a value of 2000 in the Packet Size field and then press
OK. Then press the Resume button.
Finally, send a set of datagrams with a longer length, by selecting Edit->Advanced
Options->Packet Options and enter a value of 3500 in the Packet Size field and then press
OK. Then press the Resume button.
Stop Wireshark tracing.
If you are using a Unix or Mac platform, enter three traceroute commands, one with
a length of 56 bytes, one with a length of 2000 bytes, and one with a length of 3500
bytes.
Stop Wireshark tracing.
If you are unable to run Wireshark on a live network connection, you can download a packet trace
file that was captured while following the steps above on one of the author’s Windows computers6.
You may well find it valuable to download this trace even if you’ve captured your own trace and
use it, as well as your own trace, when you explore the questions below.
6
Download the zip file http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip and extract the
file ip-ethereal-trace-1. The traces in this zip file were collected by Wireshark running on one of the
author’s computers, while performing the steps indicated in the Wireshark lab. Once you have
downloaded the trace, you can load it into Wireshark and view the trace using the File pull down menu,
choosing Open, and then selecting the ip-ethereal-trace-1 trace file.
2. A look at the captured trace
In your trace, you should be able to see the series of ICMP Echo Request (in the case of Windows
machine) or the UDP segment (in the case of Unix) sent by your computer and the ICMP TTLexceeded messages returned to your computer by the intermediate routers. In the questions
below, we’ll assume you are using a Windows machine; the corresponding questions for the case
of a Unix machine should be clear. Whenever possible, when answering a question below you
should hand in a printout of the packet(s) within the trace that you used to answer the question
asked. When you hand in your assignment, annotate the output so that it’s clear where in the
output you’re getting the information for your answer (e.g., for our classes, we ask that students
markup paper copies with a pen, or annotate electronic copies with text in a colored font).To print
a packet, use File->Print, choose Selected packet only, choose Packet summary line, and select the
minimum amount of packet detail that you need to answer the question.
1. Select the first ICMP Echo Request message sent by your computer, and expand the
Internet Protocol part of the packet in the packet details window.
What is the IP address of your computer?
2. Within the IP packet header, what is the value in the upper layer protocol field?
3. How many bytes are in the IP header? How many bytes are in the payload of the IP
datagram? Explain how you determined the number of payload bytes.
4. Has this IP datagram been fragmented? Explain how you determined whether or not
the datagram has been fragmented.
Next, sort the traced packets according to IP source address by clicking on the Source column
header; a small downward pointing arrow should appear next to the word Source. If the arrow
points up, click on the Source column header again. Select the first ICMP Echo Request message
sent by your computer, and expand the Internet Protocol portion in the “details of selected packet
header” window. In the “listing of captured packets” window, you should see all of the
subsequent ICMP messages (perhaps with additional interspersed packets sent by other protocols
running on your computer) below this first ICMP. Use the down arrow to move through the ICMP
messages sent by your computer.
5. Which fields in the IP datagram always change from one datagram to the next within this
series of ICMP messages sent by your computer?
6. Which fields stay constant? Which of the fields must stay constant? Which fields must
change? Why?
7. Describe the pattern you see in the values in the Identification field of the IP datagram
Next (with the packets still sorted by source address) find the series of ICMP TTL-exceeded replies
sent to your computer by the nearest (first hop) router.
8. What is the value in the Identification field and the TTL field?
9. Do these values remain unchanged for all of the ICMP TTL-exceeded replies sent to your
computer by the nearest (first hop) router? Why?
Fragmentation
Sort the packet listing according to time again by clicking on the Time column.
10. Find the first ICMP Echo Request message that was sent by your computer after you
changed the Packet Size in pingplotter to be 2000. Has that message been fragmented
across more than one IP datagram? [Note: if you find your packet has not been
fragmented, you should download the zip file http://gaia.cs.umass.edu/wiresharklabs/wireshark-traces.zip and extract the ip-ethereal-trace-1packet trace. If your
computer has an Ethernet interface, a packet size of 2000 should cause fragmentation.7]
7
The packets in the ip-ethereal-trace-1 trace file in
labs/wireshark-traces.zip are all less that 1500 bytes.
http://gaia.cs.umass.edu/wiresharkThis is because the computer on which the trace
was gathered has an Ethernet card that limits the length of the maximum IP packet to 1500 bytes (40
bytes of TCP/IP header data and 1460 bytes of upper-layer protocol payload).
the standard maximum length allowed by Ethernet.
This 1500 byte value is
If your trace indicates a datagram longer 1500
bytes, and your computer is using an Ethernet connection, then Wireshark is reporting the wrong IP
datagram length; it will likely also show only one large IP datagram rather than multiple smaller
datagrams..
This inconsistency in reported lengths is due to the interaction between the Ethernet
11. Print out the first fragment of the fragmented IP datagram. What information in the IP
header indicates that the datagram been fragmented? What information in the IP
header indicates whether this is the first fragment versus a latter fragment? How long
is this IP datagram?
12. Print out the second fragment of the fragmented IP datagram. What information in the
IP header indicates that this is not the first datagram fragment? Are the more
fragments? How can you tell?
13. What fields change in the IP header between the first and second fragment?
Now find the first ICMP Echo Request message that was sent by your computer after you changed
the Packet Size in pingplotter to be 3500.
14. How many fragments were created from the original datagram?
15. What fields change in the IP header among the fragments?
driver and the Wireshark software.
We recommend that if you have this inconsistency, that you
perform this lab using the ip-ethereal-trace-1 trace file.
Wireshark Lab: Ethernet
and ARP v6.01
Supplement to Computer Networking: A Top-Down
Approach, 6th ed., J.F. Kurose and K.W. Ross
“Tell me and I forget. Show me and I remember. Involve me
and I understand.” Chinese proverb
© 2005-21012, J.F Kurose and K.W. Ross, All Rights
Reserved
In this lab, we’ll investigate the Ethernet protocol and the ARP protocol. Before beginning this
lab, you’ll probably want to review sections 5.4.1 (link-layer addressing and ARP) and 5.4.2
(Ethernet) in the text8. RFC 826 (ftp://ftp.rfc-editor.org/in-notes/std/std37.txt) contains the gory
details of the ARP protocol, which is used by an IP device to determine the IP address of a remote
interface whose Ethernet address is known.
1. Capturing and analyzing Ethernet frames
Let’s begin by capturing a set of Ethernet frames to study. Do the following9:
8
First, make sure your browser’s cache is empty. To do this under Mozilla Firefox V3,
select Tools->Clear Recent History and check the box for Cache. For Internet Explorer,
select Tools->Internet Options->Delete Files. Start up the Wireshark packet sniffer
Enter the following URL into your browser
http://gaia.cs.umass.edu/wireshark-labs/HTTP-ethereal-lab-file3.html
References to figures and sections are for the 6th edition of our text, Computer Networks, A Top-down
Approach, 6th ed., J.F. Kurose and K.W. Ross, Addison-Wesley/Pearson, 2012.
9
If you are unable to run Wireshark live on a computer, you can download the zip file
http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip and extract the file ethernet--etherealtrace-1. The traces in this zip file were collected by Wireshark running on one of the author’s computers,
while performing the steps indicated in the Wireshark lab. Once you have downloaded the trace, you
can load it into Wireshark and view the trace using the File pull down menu, choosing Open, and then
selecting the ethernet-ethereal-trace-1 trace file.
questions below.
You can then use this trace file to answer the
Your browser should display the rather lengthy US Bill of Rights. Stop Wireshark packet
capture. First, find the packet numbers (the leftmost column in the upper Wireshark
window) of the HTTP GET message that was sent from your computer to
gaia.cs.umass.edu, as well as the beginning of the HTTP response message sent to your
computer by gaia.cs.umass.edu. You should see a screen that looks something like this
(where packet 4 in the screen shot below contains the HTTP GET message)
Since this lab is about Ethernet and ARP, we’re not interested in IP or higher-layer
protocols. So let’s change Wireshark’s “listing of captured packets” window so that it
shows information only about protocols below IP. To have Wireshark do this, select
Analyze->Enabled Protocols. Then uncheck the IP box and select OK. You should now
see an Wireshark window that looks like:
In order to answer the following questions, you’ll need to look into the packet details and packet
contents windows (the middle and lower display windows in Wireshark).
Select the Ethernet frame containing the HTTP GET message. (Recall that the HTTP GET message is
carried inside of a TCP segment, which is carried inside of an IP datagram, which is carried inside
of an Ethernet frame; reread section 1.5.2 in the text if you find this encapsulation a bit confusing).
Expand the Ethernet II information in the packet details window. Note that the contents of the
Ethernet frame (header as well as payload) are displayed in the packet contents window.
Answer the following questions, based on the contents of the Ethernet frame containing the HTTP
GET message. Whenever possible, when answering a question you should hand in a printout of the
packet(s) within the trace that you used to answer the question asked. Annotate the printout10
10
What do we mean by “annotate”?
If you hand in a paper copy, please highlight where in the
printout you’ve found the answer and add some text (preferably with a colored pen) noting what you
to explain your answer. To print a packet, use File->Print, choose Selected packet only, choose
Packet summary line, and select the minimum amount of packet detail that you need to answer
the question.
What is the 48-bit Ethernet address of your computer?
What is the 48-bit destination address in the Ethernet frame? Is this the Ethernet
address of gaia.cs.umass.edu? (Hint: the answer is no). What device has this as its
Ethernet address? [Note: this is an important question, and one that students sometimes
get wrong. Re-read pages 468-469 in the text and make sure you understand the
answer here.]
Give the hexadecimal value for the two-byte Frame type field. What upper layer
protocol does this correspond to?
How many bytes from the very start of the Ethernet frame does the ASCII “G” in “GET”
appear in the Ethernet frame?
Next, answer the following questions, based on the contents of the Ethernet frame containing the
first byte of the HTTP response message.
What is the value of the Ethernet source address? Is this the address of your computer,
or of gaia.cs.umass.edu (Hint: the answer is no). What device has this as its Ethernet
address?
What is the destination address in the Ethernet frame? Is this the Ethernet address of
your computer?
Give the hexadecimal value for the two-byte Frame type field. What upper layer protocol
does this correspond to?
How many bytes from the very start of the Ethernet frame does the ASCII “O” in “OK”
(i.e., the HTTP response code) appear in the Ethernet frame?
2. The Address Resolution Protocol
In this section, we’ll observe the ARP protocol in action. We strongly recommend that you reread section 5.4.1 in the text before proceeding.
ARP Caching
Recall that the ARP protocol typically maintains a cache of IP-to-Ethernet address translation pairs
on your comnputer The arp command (in both MSDOS and Linux/Unix) is used to view and
manipulate the contents of this cache. Since the arp command and the ARP protocol have the same
name, it’s understandably easy to confuse them. But keep in mind that they are different - the arp
command is used to view and manipulate the ARP cache contents, while the ARP protocol defines
the format and meaning of the messages sent and received, and defines the actions taken on
found in what you ‘ve highlight.
highlight and annotate.
If you hand in an electronic copy, it would be great if you could also
message transmission and receipt.
Let’s take a look at the contents of the ARP cache on your computer:
MS-DOS. The arp command is in c:\windows\system32, so type either “arp” or
“c:\windows\system32\arp” in the MS-DOS command line (without quotation marks).
Linux/Unix/MacOS. The executable for the arp command can be in various places.
Popular locations are /sbin/arp (for linux) and /usr/etc/arp (for some Unix variants).
The Windows arp command with no arguments will display the contents of the ARP cache on
your computer. Run the arp command.
Write down the contents of your computer’s ARP cache. What is the meaning of each
column value?
In order to observe your computer sending and receiving ARP messages, we’ll need to clear the
ARP cache, since otherwise your computer is likely to find a needed IP-Ethernet address translation
pair in its cache and consequently not need to send out an ARP message.
MS-DOS. The MS-DOS arp –d * command will clear your ARP cache. The –d flag
indicates a deletion operation, and the * is the wildcard that says to delete all table
entries.
Linux/Unix/MacOS. The arp –d * will clear your ARP cache. In order to run this
command you’ll need root privileges. If you don’t have root privileges and can’t run
Wireshark on a Windows machine, you can skip the trace collection part of this lab and
just use the trace discussed in the earlier footnote.
Observing ARP in action
Do the following11:
Clear your ARP cache, as described above.
Next, make sure your browser’s cache is empty. To do this under Mozilla Firefox V3,
select Tools->Clear Recent History and check the box for Cache. For Internet Explorer,
select Tools->Internet Options->Delete Files.
Start up the Wireshark packet sniffer
Enter the following URL into your browser
http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-lab-file3.html
Your browser should again display the rather lengthy US Bill of Rights.
Stop Wireshark packet capture. Again, we’re not interested in IP or higher-layer
protocols, so change Wireshark’s “listing of captured packets” window so that it shows
11
The ethernet-ethereal-trace-1 trace file in http://gaia.cs.umass.edu/wireshark-labs/wireshark-
traces.zip was created using the steps below (in particular after the ARP cache had been flushed).
information only about protocols below IP. To have Wireshark do this, select
Analyze->Enabled Protocols. Then uncheck the IP box and select OK. You should now
see an Wireshark window that looks like:
In the example above, the first two frames in the trace contain ARP messages (as does
the 6th message). The screen shot above corresponds to the trace referenced in
footnote 1.
Answer the following questions:
What are the hexadecimal values for the source and destination
addresses in the Ethernet frame containing the ARP request message?
Give the hexadecimal value for the two-byte Ethernet Frame type field. What upper
layer protocol does this correspond to?
Download the ARP specification from
ftp://ftp.rfc-editor.org/in-notes/std/std37.txt. A readable, detailed discussion of ARP is
also at http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/arp.html.
1. How many bytes from the very beginning of the Ethernet frame does the ARP
opcode field begin?
2. What is the value of the opcode field within the ARP-payload part of the
Ethernet frame in which an ARP request is made?
3. Does the ARP message contain the IP address of the sender?
4. Where in the ARP request does the “question” appear – the Ethernet address of
the machine whose corresponding IP address is being queried?
Now find the ARP reply that was sent in response to the ARP request.
1. How many bytes from the very beginning of the Ethernet frame does the ARP
opcode field begin?
2. What is the value of the opcode field within the ARP-payload part of the
Ethernet frame in which an ARP response is made?
3. Where in the ARP message does the “answer” to the earlier ARP request appear
– the IP address of the machine having the Ethernet address whose
corresponding IP address is being queried?
What are the hexadecimal values for the source and destination
addresses in the Ethernet frame containing the ARP reply message?
Open the ethernet-ethereal-trace-1 trace file in
http://gaia.cs.umass.edu/wireshark-labs/wireshark-traces.zip. The first and
second ARP packets in this trace correspond to an ARP request sent by the
computer running Wireshark, and the ARP reply sent to the computer running
Wireshark by the computer with the ARP-requested Ethernet address. But
there is yet another computer on this network, as indicated by packet 6 –
another ARP request. Why is there no ARP reply (sent in response to the
ARP request in packet 6) in the packet trace?
Extra Credit
EX-1. The arp command:
arp -s InetAddr EtherAddr
allows you to manually add an entry to the ARP cache that resolves the IP
address InetAddr to the physical address EtherAddr. What would happen if,
when you manually added an entry, you entered the correct IP address, but the
wrong Ethernet address for that remote interface?
EX-2. What is the default amount of time that an entry remains in your
ARP cache before being removed. You can determine this empirically (by
monitoring the cache contents) or by looking this up in your operation system
documentation. Indicate how/where you determined this value.