Advanced EIGRP Configuration Lab Activity
advertisement

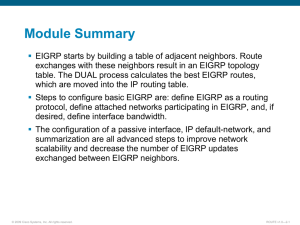
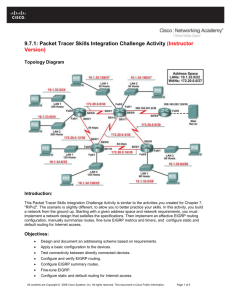
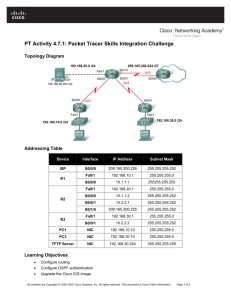
Lab 2: Advanced EIGRP Configuration Activity Objective Start with configurations from Lab 1. In this activity, you will use the correct commands, tools, and steps to configure and verify EIGRP authentication and some filtering. After completing this activity, you will be able to meet these objectives: Select the required tools and commands to configure basic EIGRP authentication Implement the identified EIGRP solution to configure basic EIGRP authentication in the provided network according to the implementation plan, using Cisco IOS commands and applications in the correct order to the selected devices and portions of the network Verify the implementation according to the verification plan, using the appropriate show and debug commands and applications to verify the correct operation, and document implementation, operation, and maintenance Step 1: Configure EIGRP Authentication First, you will configure EIGRP authentication over the LAN interfaces between the routers in your pod. The authentication should use a safe password exchange. Passwords that will be used to authenticate the routers should never expire. Once the authentication configuration on the LAN interfaces is done, you must verify if the proper key chain is defined on each pod’s routers, and that the correct keys are used, which never expire. A successful configuration results in a neighbor relationship being formed over the LAN interfaces, and you can see all of the networks advertised by the EIGRP routing process in the IP routing table of every router in the pod. After a successful LAN authentication, you will configure EIGRP authentication over the WAN interfaces between the routers in your pod. The authentication should use a safe password exchange. Passwords that are used to authenticate the routers should never expire. Use a different password for the WAN interfaces than you used for LAN. Once the authentication configuration on the WAN interfaces is done, you must verify if the proper key chain is defined on each pod router and that correct keys are used, which never expire. A successful configuration results in a neighbor relationship being formed over the WAN interfaces, and you can see all of the networks advertised by the EIGRP routing process in the IP routing table of every router in the pod. Step 2: Configure Route Filtering On R1 configure filters so that the route for 128.213.113.0/24 is not announced to R2. It should still be announced to R3. After filter in place how long before route expires on R2? Does R2 still have a route for 128.213.113.0/24? On R1 configure filters so that it will not accept a route for 128.213.40.0/24/24 from R2. It should still accept the route from R3. After filter in place how long before route expires on R1? Does R1 still have a route for 128.213.40.0/24? Remove all filters on R1 after you complete, test, and verify this step. Step 3: External EIGRP On R3 and R4 reconfigure EIGRP so that they are in AS 13 in addition to AS 113. Put interfaces facing R1/R2 into AS 113, all others into 13. Take necessary steps so that all routes are in all routing tables as before – what is required to do this? Note the differences in routing table – you know have internal and external EIGRP. How are external EIGRP routes treated differently from internal EIGRP? Step 4: BGP Configure a simple BGP neighbor relationship between R3 (BGP AS 113) and R5. Ensure BGP comes up. Configure R3 to redistribute all internal and external EIGRP routes into BGP and announce to R5. Verify R5 getting routes via BGP without any summarization. Configure R5 to announce default to R3 via BGP. There are a few different ways to accomplish this, no single right answer. Step 5: Basic IPv6 Configure IPv6 addresses on R1, R2, R3, R4. Overlay 2620:0:1000::/48 on 128.213.0.0/16 using /64 subnets. For example on R1 128.213.105.1 will have an IPv6 address of 2620:0:1000:0105::1/64. R3 128.213.130.1/27 will have an IPv6 address of 2620:0:1000:0130::1/64. Do not configure any routing at this point but ensure you can ping across directly connected subnets.