6.8 Network Security Operations Administration
advertisement

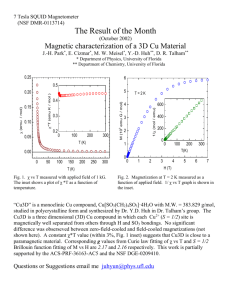
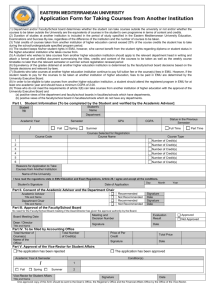
Policy Chapter Name Networking Chapter Number 6.8 Effective Date Date of Last Revision 03/13/2015 07/12/2015 Title Network Security, Operations, and Administration 1.0 Purpose This policy describes security, operational, and administrative requirements placed on wired and wireless (WiFi) users of, and network equipment connected to, the EMU network. 2.0 Scope This policy applies to any person connecting or managing a device connected to the EMU Network. 3.0 Policy Authority The Division of Information Technology (IT) is assigned operational and administrative responsibility for the EMU enterprise network. In order to assure that the enterprise network remains a resource that meets the needs of all end-users, the security practices, management practices and design standards shall be defined and managed by IT. IT shall create the standards, procedures and guidelines necessary to maintain the security, operational resiliency and long-term manageability of the network. The Director of Network and Systems may grant written exceptions to some aspects of this policy in limited instances as defined below. Tampering with, altering or moving any EMU network component is prohibited unless prior written approval is obtained from the Director of Network and System Services. Accessing a restricted space such as a network communications room without prior authorization is prohibited. Any such activity found without prior approval shall be reported to EMU Police to determine whether a crime has occurred and shall also be reported to the appropriate University office for disciplinary action when the probable culprit is identified. IT reserves the right to disconnect or impose service limits on any device, user or network equipment in the interest of minimizing network performance issues, security issues or achieving other academic/business requirements. Except in cases of abuse, IT will work with affected users to resolve issues and restore normal services to the extent possible. Clients, Devices, and Network Equipment IT may scan any device connected to the EMU network for security vulnerabilities and compliance with EMU security requirements. Devices that are not in compliance or that suffer from significant vulnerabilities may be blocked from accessing the EMU network until vulnerabilities are resolved or mitigated. All devices connected to the EMU network shall be subject to the policies, standards and procedures of IT. For EMU-managed devices connected to the EMU network, IT may force any configuration changes required to maintain network operations and security such as password changes, application of software patches, anti-malware updates or required alteration of network configurations. Any device, whether EMU-managed or personally-owned, that does not meet security or operational standards may be disconnected and/or blocked from accessing the EMU network until the device is brought into compliance. Similarly, any device deemed to present any significant security risk may be disconnected and/or blocked from accessing the EMU network until such risk is resolved or effectively mitigated. IT Policy Form Version 3.0 Page 1 of 3 IT has the responsibility for determining which network equipment meets service requirements. Departments or offices may not extend the EMU-provided network by connecting switches, routers or access points that are not approved by IT in advance. Unless a written exception is granted, use of such network-extending devices is prohibited. Wireless (WiFi) Communications IT provides University Wireless (WiFi) network services in most campus buildings. All EMU WiFi installations must be reviewed and must be approved by IT. WiFi users must be authenticated so that users are identifiable. Creation of new personal or departmental WiFi networks is prohibited unless authorized in writing by the Director of Network and Systems. In some cases, IT may opt to authorize personal or departmental WiFi network exceptions where the University-provided service is inadequate to meet operational requirements. Exceptions may be granted at the sole discretion of IT where enhanced WiFi is not yet available or other instances where the Director of Network and Systems deems deviation from this policy is required to maintain efficient operations. IT shall determine the standards, security requirements and technical/product specifications that all personal or departmental WiFi networks must meet to qualify for any such exception. To the extent possible, only University provided WiFi SSID names should be broadcast to minimize unauthorized or inadvertent connections. All WiFi devices must adhere to current IT standards and security practices. Devices may not conflict with or cause interference to the EMU WiFi system. IT may take any action deemed necessary including disconnection to stop significant interference with the EMU WiFi network where such interference is impacting the security or performance of the EMU WiFi system. Network Access in Public Spaces Network access in public spaces must be secure and is subject to IT policies, standards and procedures. The department or office responsible for managing the public space shall also be responsible for assuring that network access in that space is secure. Any network connections that are used in public spaces or for public access must be configured to be logically outside of the University firewall and on the “public” network. Network Engineering shall assist departments with requests to configure network access in a public space or for public use. Network access in public spaces should use authentication and logging to track individual usage. In the event of a subpoena or court order affecting a device in any public space, the department or office responsible for the public space shall be the network provider/administrator that must comply with the terms of the legal document. Network Communications Rooms Network communication rooms house equipment that delivers life-safety and other security related services. IT is responsible for managing and securing network data communications rooms. Network data communications rooms shall be secured using a lock and key or an ID card reader. IT may use video monitoring, environmental monitoring and other technologies to maintain the security of network communications rooms. Only employees authorized by the IT Director of Network and Systems Services may enter network communications rooms. Tampering with or disabling security cameras or environmental monitoring systems is strictly prohibited. Unauthorized access and tampering/disabling network equipment will be reported to the University’s CIO and EMU Police for possible disciplinary action and/or criminal charges. Structured Cabling IT is responsible for managing all EMU-owned structured cabling resources that service the EMU network including fiber optic cabling within and between buildings and all copper cabling used for Ethernet services. In consultation with EMU Physical Plant, IT shall be responsible for determining data network construction standards and for selecting and managing vendors that are approved to provide structured cabling installation services at the University. IT Policy Page 2 of 3 Approved vendors shall install all structured cabling in compliance with EMU installation standards, including approved mitigation of existing health and safety hazards. Cabling not installed by an approved installer may be disconnected or otherwise removed. If significant costs are incurred to correct unapproved cabling, the department hosting the unapproved cabling may be billed for the services required to correct the issue. 4.0 Responsibility for Implementation The Director of Network and Systems Services is responsible for implementing this policy. 5.0 Enforcement Any employee found to violate federal or State of Michigan laws, EMU policies, procedures or standards of conduct, will be subject to disciplinary action under University policy. Any student found to violate federal or State of Michigan laws, EMU policies, procedures or standards of conduct, will be subject to disciplinary action under EMU’s Student Code of Conduct. Any suspected violation of state or federal laws will be reported to the appropriate legal authority for investigation. The University reserves the right to protect its electronic resources from threats of immediate harm. This may include activities such as disconnecting an offending computer system from the campus network, terminating a running job on a computer system, or taking other action. 6.0 Definitions Term Enterprise Network or EMU Network Device conflict Network communication rooms Interference SSID Definition The EMU Enterprise Network consists of the total infrastructure used to deliver network services to EMU users. The enterprise network infrastructure includes the following components: • wired connections • wireless (WiFi) connections • virtual private network (VPN) connections • data network equipment (such as routers, switches, and access points) • fiber optic cabling • copper data cabling • data network communications rooms Device conflict occurs when a network-attached device is configured using the same name, channel assignments or other configuration items of an existing network-attached device. This is especially evident with devices that interfere with the operation of the EMU WiFi system. A restricted-access room designated to hold EMU network infrastructure hardware and structured cabling. WiFi devices may cause interference when mis-configured or when configured inconsistently with EMU WiFi services. The name of a wireless network (e.g. EMU-Wireless or EMU-Wireless-Secure) 7.0 Revision History Description IT Policy Committee First Review – To replace 6.1, 6.2, 6.3, 6.4 IT Policy Committee Second Review CIO approval IT Policy Approval Date 04/30/15 05/14/15 07/12/15 Page 3 of 3