Target Enumeration A. nmap

Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
Target Enumeration
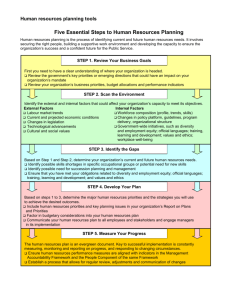
The objective of the target enumeration process is to find and collect information on services available in target machines. The output of a target enumeration process may include:
● Status of the ports in targets
● Services running on the targets
● Versions of the services
● Topology of the target network
Before starting the activities, use the ifconfig command to figure out the IP address of your
Backtrack VM. The examples in this document are provided for the network 192.168.2.0. It would be faster if you try the commands in your local network.
At the end of this document, you will be asked to complete the second part of the project.
Therefore, it is recommended to try sample Nmap command as you read the document.
A. nmap
Nmap is one of most comprehensive port scanners widely used by the security community.
Nmap can be used for discovering targets, scanning open ports, OS fingerprinting, network route detection, as well as for vulnerability detection. Nmap has many options which may overwhelm a novice user. To display all options, simply type nmap in the commandline as follows: root@bt:~#nmap
A basic port scan of the host 192.168.2.1 can be performed as follows: root@bt:~#nmap 192.168.2.1
The following picture shows the result of this port scan. The host has two ports open (22 for ssh service and 80 for http service), and the remaining 998 ports are closed. If these ports are not required to be open for a proper function of the host, they should be closed. Otherwise, they could be exploited by attackers.
1 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
All IP addresses in the network 192.168.2.0 can be scanned as follows: root@bt:~#nmap 192.168.2.0/24 or root@bt:~#nmap 192.168.2.1254
The result of this scan shows that three hosts are alive in the network, and two of them have all ports closed.
2 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
Port Scan States
Nmap recognizes six port states: open, closed, filtered, unfiltered, open/filtered, or closed/filtered.
open: A port is accessible and an application is actively accepting connection associations on this port. Finding open ports is often the primary goal of port scanning. Each open port is an avenue for attack. As attackers are likely to exploit open ports, network security administrators must protect them while making sure that legitimate users can access the services.
closed: A closed port is accessible (it receives and responds to Nmap probe packets), but there is no application listening on it. They can be helpful in showing that a host is up on an IP address
(host discovery, or ping scanning) and as part of OS detection. Because closed ports are reachable, it may be worth scanning later in case some open up. Administrators may want to consider blocking such ports with a firewall. Then, they would appear in the filtered state as discussed next.
filtered: Nmap cannot determine whether the port is open because packet filtering prevents its probes from reaching the port. The filtering could be from a dedicated firewall device, router rules, or hostbased firewall software. These ports frustrate attackers because they provide so little information.
unfiltered: A port is accessible, but Nmap is unable to determine whether it is open or closed.
Only the ACK scan, which is used to map firewall rulesets, classifies ports into this state.
Scanning unfiltered ports with other scan types such as Window scan, SYN scan, or FIN scan, may help resolve whether the port is open.
open|filtered: Nmap places ports in this state when it is unable to determine whether a port is open or filtered. This occurs for scan types in which open ports give no response. The lack of response could also mean that a packet filter dropped the probe or any response it elicited.
closed|filtered: This state is used when Nmap is unable to determine whether a port is closed or filtered.
Port Scan Types
Nmap has many port scan type options. Port scan type options are of the form s , where same time.
sS (TCP SYN scan): SYN scan is the default and most popular scan type. It can be
3 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks performed quickly, scanning thousands of ports per second on a fast network not hampered by restrictive firewalls. It is also relatively unobtrusive and stealthy since it never completes TCP connections.
root@bt:~#nmap sS 192.168.2.1
sT (TCP connect scan): TCP connect scan is the default TCP scan type when SYN scan is not an option. In this option, Nmap will try to complete the threeway handshake with each target port. If the connection is successful, the port is considered open.
root@bt:~#nmap sT 192.168.2.1
sU (UDP scan): Some services run on UDP ports (e.g., DHCP, DNS, video streaming). UDP scans tend to take a very long time (several hours to scan all 65,536 ports). Therefore, penetration testers are likely to ignore them. The UDP ports of the host 192.168.2.1 is scanned as follows:
root@bt:~#nmap sU 192.168.2.1
The result of this scan is given below. The UDP scan of the host reveals that the host runs a
DHCP server (port 67), which does not appear on the earlier scans.
sN; sF; sX (TCP NULL, FIN, and Xmas scans): These scan send no or a limited number of bits while scanning. Therefore, these scan types can pass through certain nonstateful firewalls and packet filtering routers and they are a little more stealthy than even a SYN scan.
sA (TCP ACK scan): This scan type is used to map out firewall rulesets, determining whether they are stateful or not and which ports are filtered. For example, the following scan reveals that the host 192.168.2.1 does not use any firewall rules to block ports (all 1000 ports are unfiltered).
root@bt:~#nmap sA 192.168.2.1
4 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
Port Specifications
By default, Nmap scans the most common 1,000 ports. It is also possible to specify which ports are scanned using p <port ranges> flag. For example, the following command scans only port
80 in the network 192.168.2.0.
root@bt:~#nmap sN p 80 192.168.2.0/24
The same command can also be written as follows: root@bt:~#nmap sN p http 192.168.2.0/24
The following command would scan UDP ports 67 and 137, as well as the TCP ports between
21 and 30 and port 80 of the host 192.168.2.1
root@bt:~#nmap p U:67,137, T:2130,80 192.168.2.1
The result of this scan is given below. Notice that the state of all specified ports are displayed in the scan result.
5 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
B. Zenmap
Zenmap is a graphical user interface for Nmap. In Backtrack5, Zenmap can be started by the following commandline command: root@bt:~#zenmap
Zenmap has several preconfigured scan profiles as shown in the following picture.
6 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
A profile can be edited or a new custom profile can be created selecting the Profile | Edit
Selected Profile menu (or simply use the Crtl+E key combination). Let us analyze the options for Profile Intense Scan plus UDP.
The Profile tab displays general information about the scan.
7 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
As shown below, port scan types can be specified in the Scan tab. Profile Intense scan plus
UDP performs TCP SYN scan (sS flag) and UDP scan (sU). Timing templates are named as: paranoid (0), sneaky (1), polite (2), normal (3), aggressive (4), and insane (5). If there is enough bandwidth in the target network, and intrusion detection is not a concern, timing template T5 can be selected. The higher the timing template number is, the quicker the scan would be performed.
However, a quick scan may cause network congestions and be likely to be detected by intrusion detection systems (IDS).
Option A, which is checked in this profile, enables OS detection, version detection, script scanning, and traceroute. These options can also be selected individually if Option A is not selected.
8 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
One of the important concerns in host/network enumeration is Firewall/IDS Evasion and IP
Spoofing. The Source tab has several tools to hide the identity of the scanning host. Option S will spoof the IP address of the scanning host. Option D sends decoy probes to confuse firewall/IDS systems.
9 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
Another way to bypass firewalls/IDS is fragmentation, splitting up the TCP header over several packets. Fragmentation makes it harder for firewalls and IDS to detect scan probes. The fragmentation option is available in the Other tab as shown in the following picture.
10 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
To scan the host 192.168.2.1 using Profile Intense Scan plus UDP, type the host IP in the target window and click Scan . Intense Scan plus UDP is expected to take several minutes. As shown in the following picture, the host has three ports open, one UDP and two TCP. Because advanced option (A) was selected, Nmap displays the service and its version running in each port. For example, the host has a Apache webserver with PHP enabled.
11 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
Option A also provides very detailed information about the OS of the target host as shown in the following picture.
12 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
This time let us scan the network 192.168.2.0 (IP addresses between 192.168.2.1. and
192.168.2.254) using a Regular scan. In the target window, type IP range 192.168.2.1254 and click Scan to start scanning. The result of this scan is shown below. Nmap identified three hosts.
13 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
In the output window, Ports/Hosts tab summarizes the output of a scan in terms of Hosts or
Services. For example, the first picture below lists the open ports of the host 192.168.2.21 and the second picture lists the hosts with http service available.
14 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
Zenmap can also create a picture of the network topology as shown below.
15 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
Quick traceroute scan is useful to discover the network topology. For example, the following picture illustrates a quick scan of the hosts between 10.0.0.1 and 10.0.0.10.
16 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
The results of this scan shows that the localhost is one hop away from IP addresses
192.168.2.1 and 10.0.0.1 and two hops away from IP addresss 10.0.0.2 and 10.0.0.4. To better understand the network topology, we need to scan for host properties as a host may have multiple interfaces.
17 of 18
Collaborative Virtual Computer Lab (CVCLAB)
Penn State Berks
As briefly introduced in this section, Zenmap (Nmap) is an easy to use, yet powerful tool. Nmap and Zenmap must be mastered by penetration testers. In practice, penetration testers should periodically scan networks and compare the changes over time by using the Tools| Compare
Results menu.
Penetration Testing AssignmentPart 2
● Perform host enumeration for the hosts that you have discovered in the network 10.0.0.0.
In your report,
○ explain what type of scans you used and why.
○ indicate the status of the host's ports, what services are available, and their versions for each target host.
● Use Quick traceroute scan to figure the topology of the Backtrack Virtual computer lab that you have been using in this semester.
18 of 18