Network_ Spring 2011 Lesson 52 _OSI Reference Model
advertisement

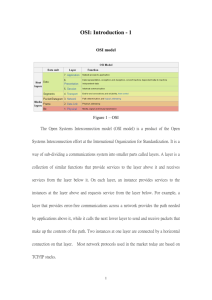
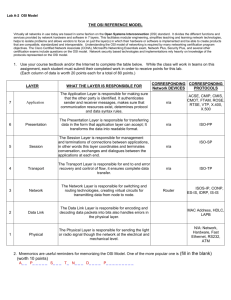
1 Teacher Version L E S S O N P L A N #52 Per. DATE: Wednesday February 16th, 2011 CLASS: Networking TOPIC: OSI Reference Model Name: AIM: What is the OSI Reference Model? NOTE: 1) At the end of the period, leave your computer on the desktop screen, put the keyboard on top of the monitor and push in your chair. H.W. # 52: 1) What are the benefits of breaking down network communication into layers such as the OSI model and the TCP/IP model? 2) What are the names of the Protocol Data Units (PDUs) as they traverse the layers of the OSI model? 3) With respect to the OSI model what is peer to peer communication? DO NOW: Go to www.google.com and do a search for bandwidth meter. What is the measure of your “bandwidth”? What is bandwidth? What is the base unit of measurement for bandwidth? What base is used when increasing units of measure for bandwidth? What base is unit of measurement for data storage? What base is used when increasing units of measure for data storage? What is throughput? What affects throughput? PROCEDURE: Write the AIM and DO NOW. Get students working! Take attendance. Go Over HW Collect HW Go over the Do Now Assignment #1: Previously, we spoke about MAC addresses, which are hard-coded addresses in your NICs that identify the system that has the NIC on the network. The MAC address is also called a Physical address, due to the fact that it is physically coded into ROM on your NIC. An analogy can be drawn between the MAC address and a street address of a home. For example, where is 1313 Mockingbird Lane? It could be anywhere in the United States. We need something else, aside from the street address, which can narrow down, where in the US is 1313 mockingbird lane. What is that something else? Just like a street address, needs a ZIP CODE to narrow down the area of the country that 1313 Mockingbird Lane is in, computers on a network also need something to narrow down where in the world is MAC address AA-BB-CC-DD-EE-FF. That other type of address is not a zip code (no that is used to deliver physical mail). Instead a network, or logical address, is used to let devices know on what network is a MAC, the physical, address located. Where is a network or logical address located? What is the purpose of a network address? What is the purpose of a physical address, such as the MAC address? 2 What networking device filters traffic based on MAC address? The CAM (Content Addressable Memory) table in a switch contains information such as the MAC addresses available on a given physical port of a switch. When a switch receives a frame, the switch looks in the CAM table for the destination MAC address. If an entry exists for the MAC address in the CAM table, the switch forwards the frame to the port designated in the CAM table for that MAC address. If the MAC address does not exist in the CAM table, the switch forwards the frame out every port on the switch, effectively acting like a hub. If a response is seen, the switch updates the CAM table What networking device filters traffic based on network address? Look up router at www.techweb.com/encyclopedia. What does a router do? Where in a network is a router placed? There are various types of logical or network address, but by far, the most popular is the IP address. www.techweb.com/encyclopedia and answer the following questions. Look up IP Address at What is another name for an IP network? What is the format of an IP address? How many bits in an IP address? In what part of a computer system is an IP address stored? What are the different ways an IP addressed can be assigned to a system? Assignment #2: Look up DHCP at www.techweb.com/encyclopedia. What is a DHCP server? Find the IP address of your DHCP server by running WINIPCFG, then click on MORE INFO or if you have Windows NT/2000/XP go to the command prompt and type IPCONFIG /ALL. Before the data gets to the NIC card, there is a frame attached to the data before the NIC card puts its own frame. Just before the NIC card, puts its frame around the data, the software puts a frame around the data that includes among other things the source and destination IP address. This type of frame at the software layer is called a packet. Once the NIC gets the packet, it puts a frame around the packet. When a router gets a frame that contains the packet, it doesn’t read the frame. That is for a NIC. It actually peels off the frame, and looks at the packet for the destination IP address. Once it sees what port to send out the packet, it will attached its own frame with the necessary information to reach the destination appropriately. Before data gets to the part where an IP source and destination information is added, the data is much too large to fit in a frame or packet; the data must be chopped up into pieces. When the data is chopped up into pieces, each piece is given a sequence number. Then each piece gets its own frame and packet. On the receiving end, the receiving system gets the pieces with the different sequence numbers and puts them back in order. Before data gets chopped up into pieces, the receiving system and sending system have to make a connection. Once a connection is made, then the data gets chopped up and sequence. Each piece becomes a packet with a source and destination IP address, then becomes a frame when a source and destination MAC address is added to the packet. Then the the frame is converted into bits to be sent out on the medium The data that you see has to be read by the appropriate software. As a result the data has to be in a certain format. There are different formats in which data can be represented. There is .DOC, .XLS, .BMP, .WAV, .MP3, .PDF, etc. Even if it is in regular text or 3 ASCII code, it might be encrypted. Before data gets converted into any of these formats, it is in a form that we can see using our applications. Basically we have traced the steps in which data gets sent from source to destination, in reverse order. Let’s go over these steps again. 7) User uses some network application to see the data to be sent. This could be a web browser, e-mail client software, ftp client software, telnet client software, or any other network application. 6) The data is then converted from a format we can see into a format that can be read by an application 5) The sending and receiving end then negotiate a session to transfer data 4) Data then gets chopped up into segments. At this stage the data is now called segments. Each segment gets a sequence number 3) After the data is chopped up into pieces, network layer address information is added. The data is now called packets. 2) After the data gets network layer information, physical address (MAC) is added. The data is now called frames. 1) Finally the frames are converted to bits to be placed on the medium. The data is now called bits. These seven steps, or stages, or layers represent what is known as the OSI (Open Systems Interconnection) model. The 7 layers of the OSI model starting from the user and going to the wire are as follows: 7) 6) 5) 4) 3) 2) 1) Application Layer Presentation Layer Session Layer Transport Layer Network Layer Data Link Layer Physical Layer You must remember the order of these layers. I suggest developing a mnemonic to remember. One such as All Pre-School Toys Need Durable Parts. Assignment #3: Go to www.howstuffworks.com and look up OSI model, and answer the following questions: Who made up the OSI model. When was the OSI model made up? What happens at each layer of the OSI model? What is another networking reference model that is used on the Internet? What are the layers of the TCP/IP reference model? 4 Assignment #3: Go to http://en.wikipedia.org/wiki/OSI_model. Click on the Purpose link and start reading from the 5th paragraph of the purpose link. It starts off with “The OSI reference model is a hierarchical structure of seven layers…” Sample Test Questions: 1) Which layer of the OSI model controls assembly and disassembly of data? A) Application Layer B) Presentation Layer C) Session Layer D) Transport Layer 2) Which of the following is an advantage of using peer-to-peer network over using a client/server network? A) A peer-to-peer network allows for more nodes B) A peer-to-peer network provides greater security C) A peer-to-peer network is easier to set up D) A peer-to-peer network allows for easier expansion 3) How can a server tell the difference between many clients on a network? A) Each has a different electromagnetic characteristic to its signal, similar to differences in human voices B) Each regularly transmits a signal that indicates its network location and unique characteristics C) Each is identified by a unique network address D) Each uses uniquely modified versions of the same network protocol 4) Which standards organization developed the OSI model? A) ISO B) ITU C) ISOC D) OSI 5) Layer 2 of the OSI model is named _______________ A) Application Layer B) Network Layer C) Transport Layer D) Data Link Layer 6) You need a network that provides centralized authentication for your users. Which of the following logical topologies should you use? A) VLANs B) Peer-to-peer C) Client / Server D) Mesh 7) Which of the following is a concern when using peer-to-peer networks? A) Where to place the server B) Whose computer is least busy and can act as the server C) The security associated with such a network D) Having enough peers to support creating such a network 5