Exploring Cisco Router Capabilities
advertisement

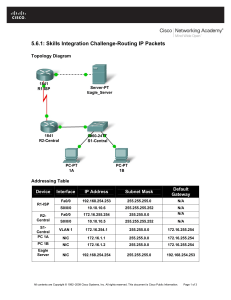
Exploring Cisco Router Capabilities 1. Introduction The objective of this laboratory experiment is to acquire some basic knowledge in IP routing and to learn how routers work. When you are done with this lab, you should know what router is and how to configure it for simple tasks like interconnecting several physical networks and building firewalls. In our experiments we will use Cisco router 2600 as an example router and a set of utilities to communicate with the router and display or modify its current configuration. 2. Example Network Interface FastEthernet0/1 10.10.10.254 Network 10.10.10.0/24 Switch Interface FastEthernet0/0 192.116.0.254 Cisco Router 2600 Workstation 10.10.10.146 Network 192.116.0.0/24 Switch Workstation 192.116.0.150 2.1 Network components Our experiment starts from building our toy network. It consists of two subnets, or two physical networks, interconnected by Cisco router. To create it, you will need two switches and two PCs running. Switch is another kind of network device, connecting hosts into one physical network. 2.2 IP addresses and network masks Each host connected to IP network must have an address, which uniquely identifies it. IP addresses are 32-bit integers usually written in so-called dotted decimal notation, e.g. 192.116.0.1. IP address is divided into 1 network and host parts. All hosts in the same physical network have the same network part. In our toy network, hosts in right-hand side network have network part of IP address equal to 192.16.0; while in left-hand-side network the network part of IP address is 10.10.10. The size of network part is defined by so called netmask, which is also a 32-bit integer, consisting of some number of consecutive 1’s, followed by consecutive 0’s. Number of 1’s in netmask is the size of address network part. Netmasks are also written in dotted decimal notation. In both our physical networks the netmask is 255.255.255.0, i.e. the size of network part is 24. It is common to specify the address of the whole network like 192.116.1.0/24, meaning that network part of IP address is 24 bits long and is equal to 192.116.1. 3. Configuring network devices and hosts You need 4 Ethernet cables to connect all devices and hosts together. This part is trivial and we well not dwell upon it. Network interfaces of Cisco router are located on the back panel, and are labeled. Make sure to connect them to switches as specified in the figure. Now that all devices are physically connected, it’s time to connect them logically, i.e. provide IP addresses and netmasks to router and Linux hosts. 3.1 Validating configuration on Hosts. Log on to the computers with username student and password student domain ’local computer’. On the right-hand side Linux host execute the following commands: Press Start run cmd <Enter> ipconfig <Enter> You should see the following result : C:\>ipconfig Windows 2000 IP Configuration Ethernet adapter Local Area Connection: Connection-specific DNS Suffix . : cs.bgu.ac.il IP Address. . . . . . . . . . . . : 192.116.0.150 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.116.0.1 On the left-hand side do the same procedure described above. You should get this result : 2 C:\>ipconfig Windows 2000 IP Configuration Ethernet adapter Local Area Connection: Connection-specific DNS Suffix . : cs.bgu.ac.il IP Address. . . . . . . . . . . . : 10.10.10.146 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 10.10.10.254 3.2 Configuring Cisco Router 3.2.1 Setting serial console The initial router configuration is usually done via serial console. There is a special port, labeled “Console” on the router back panel. Ask your network administrator to provide a serial console cable. Connect one end of the cable to the router, and another to a COM port of some PC running Microsoft Windows. On PC, run either TeraTerm or Hyperterminal. In serial port configuration menu provide the following parameters: Port name: Baud rate: Stop bits: Parity: Flow control: usually either COM1 or COM2 9600 1 None Hardware When you’re done with port configuration, press Enter several times. If you’re lucky, the router’s password prompt should appear. If nothing happens, try changing port name in configuration menu and try again, or ask your network administrator for assistance. 3.2.2 Logging into router Let’s suppose you’ve finally got to the router’s password prompt. There are two router passwords that you should know. One is for initial login, and another is so called “enabled mode” password, which you need to view/modify router configuration. Ask your network administrator to provide both of them. 3 At password prompt type initial login password. If login was successful, you’ll see another prompt, which looks like: router> Now type command “en” and press enter. At password prompt type “enable mode” password. If the password was correct, you’ll see a slightly different prompt, like: router# Now you’re ready to issue configuration commands. 3.2.3 Configuring network interface Issue the command “conf term”. When prompt reappears, issue the command “interface FastEthernet0/0”. We are now in the interface configuration mode. Now configure IP address and netmask of the interface, by running the command: ip address 192.168.0.254 255.255.255.0 Exit configuration mode by typing “^Z”. You should now be able to access our Linux host 192.116.1.50. To verify that Linux host is reachable, run the following command: ping 192.116.1.50 If ping was successful, you’ll see a message saying “Success rate 100 percent”. In the case of failure, please recheck that: both host and Cisco router are connected to the same switch network interfaces of host and Cisco are functioning, i.e. there is a green light near the interface and at the corresponding port of the switch both host and Cisco router have the same network number. On PC, run ipconfig to see the interface configuration. On Cisco, run show ip interface FastEthernet 0/0 to view interface configuration 4 4. Using Router Configuration and Monitoring Tools We assume that you can now reach your Cisco router from host 192.116.1.50. We will use the router command line interface to perform actions, commands and show the current router configuration. To access the router command interface, telnet to the router ip address or use the serial interface. 4.1 Viewing and modifying router interface configuration Let’s start by viewing the current interface configuration of our router. On host 192.116.1.50 start TeraTerm program connect the Router via Serial and type the following : Show running-conf In the output, there will a part that’s should look something similar to the table below: FastEthernet0/0 ip address192.116.0.254 netmask 255.255.255.0 no ip directed-broadcast ………………………………………………… FastEthernet0/1 ip address 10.10.10.1 netmask 255.255.255.0 no ip directed-broadcast ………………………………………………… Serial0/0 no ip address ………………………………………………… 5 We should only be concerned about Fast Ethernet interfaces. We will now try to set the ip address and netmask of the FastEthernet0/1 interface to meet the requirements of our example network. To do that, we’ll use: Conf t Interface FastEthernet0/1 Ip address 10.10.10.254 255.255.255.0 Exit You can now rerun show running-conf command above to verify that changes you made are effective. 4.2 Viewing and modifying router’s routing table As we have mentioned above, the primary task of a router is to interconnect several physical networks, allowing hosts in different networks to communicate. The process of forwarding network traffic originated in one network to another is called routing. The data in Internet flows in packets. Each IP packet contains an ip address of a destination host. When packet arrives to some interface of a router, the latter should decide how to forward it, i.e. to find an interface to send the packet through. To make such decisions routers maintain so called routing tables. Routing table maps ip addresses of hosts and networks to router’s interfaces. When trying to send a packet, the router searches is routing table attempting to find an entry which most closely matches the destination ip address of a packet. If the match is found, the packet is send through the corresponding interface. Otherwise the packet is dropped. Basically there are 3 types of entries in routing tables: host routes, network routes and default gateways. Host routes map IP addresses of specific hosts to router’s interfaces. Network routes map entire networks, and default gateways are used as last resort, when no exact match can be found. 6 We can explore the current state of IP routing in our Cisco router using the following command: Show ip route The output will look something like this: IP routing enabled Router IP routing table Destination 132.72.45.3 10.10.1.0 10.20.1.0 0.0.0.0 Gateway 10.10.10.254 0.0.0.0 0.0.0.0 10.20.1.5 Netmask 255.255.255.255 255.255.255.0 255.255.255.0 0.0.0.0 Flags UGH U U UG Interface FastEthernet0/1 FastEthernet0/1 FastEthernet0/0 FastEthernet0/0 Let’s try to understand what this means. First of all, the IP routing is enabled, i.e. router is forwarding packets between its interfaces. The first line of the routing table defines host route. It says that packets destined to host 132.72.45.3 should be sent to gateway 10.10.10.3 via interface FastEthernet0/1. Flag U means that the route is UP, i.e. active. G means gateway, that is destination is not directly connected to one of our router’s networks, but is accessible via some intermediate router. H means host route. Second and third lines define network routes. They say packets destined to networks 10.10.1.0/24 and 10.20.1.0/24 should be forwarded via interfaces FastEthernet0/1 and FastEthernet0/0 respectively. The last line defines default gateway, i.e. all other packets (not matched by the previous routing table entries) should be sent to gateway 10.20.1.5 via interface FastEthernet0/0. The matching is done is follows: for each routing table entry the router extracts netmask field and performs logical AND with both destination field of the entry and destination IP address of the packet. If results are equal, the match was found and the process terminates. Otherwise next table entry is tried. If no match was found, the packet is sent via default gateway. If no default gateway defined, the packet is dropped. Now that we know how routing works, let’s configure it for our toy network. First of all, if IP routing is disabled, we should enable it. This can be done using the following command: Conf t Ip routing Exit 7 Now we should add two network routes for our physical networks. To do that, run: Conf t Ip route 192.116.0.0 255.255.255.0 FastEthernet0/0 Ip route 10.10.10.0 255.255.255.0 FastEthernet0/1 Exit If you rerun the Show ip route command, you should see the following routing table: IP routing enabled Router IP routing table Destination Gateway Netmask Flags Interface ………………………………………………………………………………… 192.116.0.0 0.0.0.0 255.255.255.0 U FastEthernet0/0 10.10.10.0 0.0.0.0 255.255.255.0 U FastEthernet0/1 …………………………………………………………………………… …… You should now be able to reach our second Linux host, 10.10.10.10. Try running the following command ping 10.10.10.146 If ping was successful, you’ll see the following output: PING 10.10.10.146 (10.10.10.146): 56 octets data 64 octets from 10.10.10.10: icmp_seq=0 ttl=255 time=1.5 ms 64 octets from 10.10.10.10: icmp_seq=1 ttl=255 time=1.5 ms ……………………………………………………………….. Type “^C” to terminate the ping program. Now try disabling IP routing by running Conf t No ip routing Exit and verify that the above ping command will not work. Restore ip touting 8 4.3 Creating firewall to block certain types of traffic It is often desirable to deny certain types of traffic to specific hosts or networks for security reasons. For instance network administrator can decide to block all telnet traffic to some important server from all computers except his own. Routers are ideal for implementing such blocking policies, as all traffic between networks passes through them. Network devices that perform traffic filtering are often called firewalls. To create a firewall on Cisco router one should define one or several access lists and associate them with interfaces. Access list is a set of traffic filtering rules. Rule specifies traffic source and destination and a policy to apply to this kind of traffic (permit or deny). Each access list has a numeric ID. We are interested in so called extended access lists, numbered from 100 to 199 inclusive. To view the status of access lists on our router, run the following command: Show access-list The command output may look as follows: Num Src Addr Src Port Dst Addr Dst Port Prot Policy 100 100 10.10.1.3 any any any 10.20.1.5 any ftp any tcp ip deny permit As we can see access list number 100 denies ftp traffic from host 10.10.1.3 to host 10.20.1.5 and allows all other traffic. Let’s define our own access list to block web traffic from 192.116.1.50 to 10.10.10.146 and allow all other. Before we do that, let’s check that Http to 10.10.10.10 indeed works. Start the browser and type the address 10.10.10.146 : If you get a web page it works Now lets define our access list. Conf t Access-list 110 deny tcp host 192.116.1.50 host 10.10.10.146 eq www Access-list 110 permit ip any any Exit We gave our access list number 110. You can select any other in the range 100-199, provided that access list with such number does nor exist. 9 Now let’s associate interface FastEthernet0/0 with this access list: Conf t Interface FastEthernet0/0 Ip access-group 110 in Exit This command instructs interface FastEthernet0/0 to filter all incoming traffic according to the rules defined in access list 110. Click on refresh web page. You shouldn’t get any page display. if you get any response try to delete local cache files. The ping should work. Let’s disable our firewall, by running Conf t Interface FastEthernet0/0 No Ip access-group 110 in Exit Click on refresh web page. It should succeed this time. You can define more complex firewalls using the above programs. For a complete set of options, please refer to a document titled “Cisco Router Monitoring and configuration utilities. User Manual” 4.4 Additional problem Try to ping to 132.72.40.8 and to browse our department home page from host 10.10.10.146. What should you do? What should you define and where? If you want that computers from network 10.10.10.0 won’t be able to use the net but could telnet and ftp outside, and you want that from outside people could only visit pages on your web server and won’t be able to do anything else. What should you do? What should you define and where? 10