Microsoft Windows Server Update
Services Operations Guide
Microsoft Corporation
Published: June 3, 2005
Author: Ben Aguiluz
Editor: Sean Bentley
Abstract
This paper documents the major tasks involved in administering and troubleshooting
Microsoft® Windows Server™ Update Services.
The information contained in this document represents the current view of Microsoft
Corporation on the issues discussed as of the date of publication. Because Microsoft
must respond to changing market conditions, it should not be interpreted to be a
commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any
information presented after the date of publication.
This White Paper is for informational purposes only. MICROSOFT MAKES NO
WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN
THIS DOCUMENT.
Complying with all applicable copyright laws is the responsibility of the user. Without
limiting the rights under copyright, no part of this document may be reproduced, stored in
or introduced into a retrieval system, or transmitted in any form or by any means
(electronic, mechanical, photocopying, recording, or otherwise), or for any purpose,
without the express written permission of Microsoft Corporation.
Microsoft may have patents, patent applications, trademarks, copyrights, or other
intellectual property rights covering subject matter in this document. Except as expressly
provided in any written license agreement from Microsoft, the furnishing of this document
does not give you any license to these patents, trademarks, copyrights, or other
intellectual property.
Unless otherwise noted, the example companies, organizations, products, domain
names, e-mail addresses, logos, people, places, and events depicted herein are fictitious,
and no association with any real company, organization, product, domain name, e-mail
address, logo, person, place, or event is intended or should be inferred.
© 2005 Microsoft Corporation. All rights reserved.
Microsoft, SQL Server, Windows, and Windows Server are either registered trademarks
or trademarks of Microsoft Corporation in the United States and/or other countries.
The names of actual companies and products mentioned herein may be the trademarks
of their respective owners.
Contents
Microsoft Windows Server Update Services Operations Guide ....................................... 11
Administering Windows Server Update Services ............................................................. 11
Overview of Windows Server Update Services ................................................................ 12
The WSUS Solution ....................................................................................................... 12
Managing Windows Server Update Services.................................................................... 12
Setting Up and Running Synchronizations ....................................................................... 13
Synchronizing Updates by Product and Classification .................................................. 13
Configuring Proxy-server Settings ................................................................................. 14
Configuring the Update Source ..................................................................................... 15
Specifying Where to Store Updates .............................................................................. 16
Synchronizing Manually or Automatically ...................................................................... 16
Managing Computers and Computer Groups ................................................................... 17
Managing Client Computers ............................................................................................. 17
Managing Computers on the Computers Page ............................................................. 18
Managing Computer Groups ............................................................................................. 19
Server-side Targeting .................................................................................................... 20
Client-side Targeting...................................................................................................... 20
Managing Computer Groups on Your WSUS Server ................................................. 21
Managing Updates ............................................................................................................ 22
Updates Overview ............................................................................................................. 22
How WSUS Stores Updates .......................................................................................... 22
Managing Updates by Using WSUS.............................................................................. 23
Update Products and Classifications ............................................................................. 24
Products Updated by WSUS ...................................................................................... 24
Update Classifications ................................................................................................ 24
Viewing Updates ............................................................................................................... 26
Approving Updates ............................................................................................................ 27
Approving Updates for Detection ................................................................................... 28
Approving Updates for Installation ................................................................................. 28
Declining Updates .......................................................................................................... 30
Approving Updates for Removal .................................................................................... 30
Approving Updates Automatically .................................................................................. 31
Automatically Approving Updates for Detection ............................................................ 31
Automatically Approve Updates for Installation ............................................................. 32
Automatically Approving Revisions to Updates ............................................................. 33
Approving Superseding or Superseded Updates .......................................................... 34
Recommended Process for Approving a Superseding Update ................................. 35
Approving Office Updates ................................................................................................. 35
Approving SQL Server and Exchange Server Updates .................................................... 36
Updating Microsoft SQL Server Instances .................................................................... 36
Updating Microsoft SQL Server and Microsoft Exchange Servers that are Part of a
Cluster ........................................................................................................................ 36
Testing Updates ................................................................................................................ 37
Storing Updates ................................................................................................................ 38
Specifying Where to Store Updates .................................................................................. 38
Local Storage Considerations ....................................................................................... 38
About Express Installation Files ................................................................................. 39
Changing the Location where You Store Update Files Locally ..................................... 40
Managing the Databases .................................................................................................. 41
Running in Replica Mode .................................................................................................. 42
Backing Up Windows Server Update Services ................................................................. 43
Best Practices with Windows Server Update Services ..................................................... 47
Use Group Policy to Update Multiple Computers .......................................................... 47
Schedule Update Installations when there is Little Chance for Lost Productivity.......... 49
For maximum control over when your servers are restarted as necessitated by an
update installation, set Group Policy to Download the updates automatically and
notify when they are ready to be installed, and then create a script that enables to
you accept and install the updates and then restart the computer on demand ......... 50
Managing WSUS from the Command Line ....................................................................... 51
Running WSUSutil.exe .................................................................................................. 51
Export ......................................................................................................................... 55
Syntax ..................................................................................................................... 55
Import ......................................................................................................................... 55
Syntax ..................................................................................................................... 55
Migratesus .................................................................................................................. 56
Syntax ..................................................................................................................... 56
Movecontent ............................................................................................................... 56
If the drive is full ...................................................................................................... 57
If the hard disk fails ................................................................................................. 57
Syntax ..................................................................................................................... 58
Reset .......................................................................................................................... 58
Syntax ..................................................................................................................... 58
Deleteunneededrevisions ........................................................................................... 58
Syntax ..................................................................................................................... 59
Listinactiveapprovals .................................................................................................. 59
Syntax ..................................................................................................................... 60
Removeinactiveapprovals .......................................................................................... 60
Syntax ..................................................................................................................... 60
Monitoring Windows Server Update Services .................................................................. 60
Update Status Terminology .............................................................................................. 61
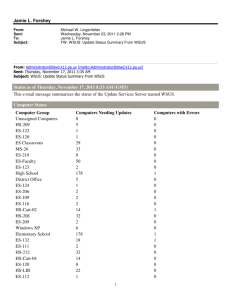
Running Reports ............................................................................................................... 63
Using the Reports Page................................................................................................. 63
Status of Updates Report ........................................................................................... 64
Update summary view ............................................................................................ 65
Computer group view .............................................................................................. 66
Computer view ........................................................................................................ 67
Printing the report ................................................................................................... 68
Status of Computers Report ....................................................................................... 69
Synchronization Results Report ................................................................................. 70
Settings Summary Report .......................................................................................... 71
Running Compliance Status Reports ............................................................................ 73
Securing Windows Server Update Services ..................................................................... 74
Troubleshooting Windows Server Update Services ......................................................... 74
WSUS Server Administration Issues ................................................................................ 74
Setup Issues ..................................................................................................................... 75
Check for required software and hardware ................................................................... 75
In some cases, setup might fail if you choose the WMSDE database .......................... 75
If the Server service is not running when you install WSUS, the WSUS installation fails
.................................................................................................................................... 75
Upgrade Issues ................................................................................................................. 75
When an upgrade fails, WSUS might be uninstalled ..................................................... 75
Uninstalling WSUS from SQL Server ................................................................................ 76
Uninstalling might leave some WSUS configurations on computers running SQL server
.................................................................................................................................... 76
Cannot access the WSUS console ................................................................................... 76
Grant users permissions for WSUS console access ..................................................... 76
You cannot access the WSUS console with an IP address when WSUS is configured to
use a proxy server ...................................................................................................... 77
Cannot access the WSUS console and a timeout error message appears .................. 77
Cannot access the WSUS console on a Windows 2000 server after applying the hisec
server.inf security template ........................................................................................ 77
Promoting the WSUS server to a domain controller might disrupt your ability to access
the WSUS console ..................................................................................................... 78
Cannot access the WSUS console on Windows 2000 Server configured as a domain
controller ..................................................................................................................... 79
Update storage issues ...................................................................................................... 80
The updates listed in the WSUS console do not match the updates listed in your local
folder........................................................................................................................... 80
Synchronization issues ..................................................................................................... 80
Check proxy-server settings by using the WSUS console ............................................ 81
Check the name of the upstream WSUS server ........................................................... 81
Check update storage options ....................................................................................... 82
Verify that users and the network service have Read permissions to the local update
storage directory......................................................................................................... 82
On a downstream WSUS server, check that the updates are available on the upstream
WSUS server .............................................................................................................. 82
Restart the BITS service ................................................................................................ 83
If you are unable to download update files to your local WSUS server, your server
might not support the necessary HTTP protocol ........................................................ 83
The number of updates that are approved on a parent upstream server does not match
the number of approved updates on a replica server ................................................ 84
Update approval issues..................................................................................................... 84
If IIS Lockdown is installed on WSUS and client computers, do not download updates
stored on the WSUS server........................................................................................ 84
New approvals can take up to one minute to take effect ............................................... 85
Remote computers accessed by using Terminal Services cannot be restarted by nonadministrators ............................................................................................................. 85
The number of updates that are approved on a parent upstream server does not match
the number of approved updates on a replica server ................................................ 85
Client computers do not appear in the WSUS console ..................................................... 85
Problem with client self-update ...................................................................................... 86
Backup and restore issues ................................................................................................ 86
If you cannot access WSUS data after restoring the database, check the WSUS server
name and user permissions for the database ............................................................ 86
General error messages ................................................................................................... 86
…some services are not running. Check the following services… ............................... 86
Selfupdate .................................................................................................................. 86
WSUSService.exe ...................................................................................................... 87
Web services .............................................................................................................. 87
SQL service ................................................................................................................ 87
Client Computer Administration Issues ............................................................................. 87
Automatic Updates must be updated ................................................................................ 88
Troubleshooting client self-update issues ..................................................................... 88
How to differentiate between the SUS client and WSUS client ................................. 88
Verify that the client software in your organization can self-update ........................... 90
Verify that the SUS clients are pointed to the WSUS server ..................................... 90
Check for the selfupdate tree on the WSUS server ................................................... 91
Check IIS logs on the WSUS Server .......................................................................... 91
If you have installed SharePoint on the default Web site in IIS, configure SharePoint
to not interfere with Self-update .............................................................................. 91
Check network connectivity on the WSUS client computer ....................................... 92
Check logs on the SUS client computer..................................................................... 93
Manipulate registry settings on the SUS client computer .......................................... 94
Computers are not appearing in the correct computer groups ......................................... 96
Verify that the WSUS console is set to use client-side targeting .................................. 96
Verify that target computer group names match groups on the WSUS server ............. 96
Wait an hour for changes to take effect ......................................................................... 96
Additional Resources for Windows Server Update Services ............................................ 97
Windows Server Update Services Communities ........................................................... 97
More Documentation ..................................................................................................... 97
11
Microsoft Windows Server Update
Services Operations Guide
This guide describes the major tasks involved in administering and troubleshooting
Windows Server Update Services.
Note:
A downloadable copy of this document is available on the Microsoft Download
Center at
http://www.microsoft.com/downloads/details.aspx?FamilyId=E26BCDB4-EF0B4399-8A71-9B3B00C4F4CD&displaylang=en
In this guide
Administering Windows Server Update Services
Troubleshooting Windows Server Update Services
Additional Resources for Windows Server Update Services
Administering Windows Server Update
Services
This section contains background information and procedures for performing the major
tasks involved in administering Windows Server Update Services.
In this guide
Overview of Windows Server Update Services
Managing Windows Server Update Services
Monitoring Windows Server Update Services
Securing Windows Server Update Services
12
Overview of Windows Server Update
Services
By using Windows Server Update Services (WSUS), you can fully manage the process of
getting software updates that are released through Microsoft Update, and then distribute
them to servers and client computers in your network.
The WSUS Solution
The WSUS solution provides a management infrastructure consisting of the following:
Microsoft Update: the Microsoft Web site that WSUS components connect to for
updates to Microsoft products.
Windows Server Update Services server: the server component that is installed on
a computer running a Microsoft Windows 2000 Server with Service Pack 4 (SP4) or a
Microsoft Windows Server 2003 operating system inside the corporate firewall.
WSUS server software enables administrators to manage and distribute updates
through a Web-based tool, which can be accessed from Internet Explorer on any
computer running a Windows operating system in the corporate network. In addition,
a WSUS server can be the update source for other WSUS servers. In a WSUS
implementation, at least one WSUS server in the network must connect to Microsoft
Update to get available updates. The administrator can determine, based on network
security and configuration, how many other servers connect directly to Microsoft
Update.
Automatic Updates: the client computer component built into Windows 2000 with
SP3, Microsoft Windows XP, and Windows Server 2003 operating systems.
Automatic Updates enables both server and client computers to receive updates from
Microsoft Update or from a server running WSUS.
Managing Windows Server Update Services
In this section
Setting Up and Running Synchronizations
Managing Computers and Computer Groups
Managing Updates
Running in Replica Mode
Backing Up Windows Server Update Services
13
Managing WSUS from the Command Line
Setting Up and Running Synchronizations
During synchronization, your server running Windows Server Update Services (WSUS)
downloads updates (update metadata and files) from an update source. When your
WSUS server synchronizes for the first time, it will download all of the updates you
specified when you configured synchronization options. After the first synchronization,
your WSUS server determines if any new updates have been made available since the
last time it made contact with the update source, and then downloads only new updates.
The Synchronization Options page is the central access point in the WSUS console for
customizing how your WSUS server synchronizes updates. On this page, you can specify
which updates are synchronized automatically, where your server gets updates,
connection settings, and the synchronization schedule.
After you synchronize updates to your WSUS server, you must then approve them before
the WSUS server can perform any action for them. The exceptions to this are updates
classified as Critical Updates and Security Updates, which are automatically approved
for detection. For more information, see "Approving updates for detection in Approving
Updates.
Note:
Because WSUS initiates all its network traffic, there is no need to configure
Windows Firewall on a WSUS server connected directly to Microsoft update.
Synchronizing Updates by Product and Classification
Your WSUS server downloads updates based on the products or product families (for
example, Windows, or Windows Server 2003, Datacenter Edition) and classifications (for
example, Critical Updates or Security Updates) that you specify. At the first
synchronization, your WSUS server downloads all of the updates available in the
categories you have specified. At subsequent synchronizations, your WSUS server
downloads only the newest updates (or changes to the updates already available on your
WSUS server) in the categories you specified.
You specify update products and classifications on the Synchronization Options page
under Products and Classifications. Products are grouped in a hierarchy, by product
family. For example, if you select Windows, you automatically select every product that
falls under that product hierarchy. By selecting the parent check box you not only select
all items under it, but all future releases too. Selecting the child check boxes will not
select the parent check boxes. The default setting for Products is All Windows Products,
14
and for Update classifications, the default setting is Critical Updates and Security
Updates. You must specify update classifications individually.
If your WSUS server is running in replica mode, you will not be able to perform this task.
For more information about replica mode, see Running in Replica Mode.
To specify update products and classifications for synchronization
1. On the WSUS console toolbar, click Options, and then click Synchronization
Options.
2. Under Products and Classifications, under Products, click Change.
3. In the Add/Remove Products dialog box, under Products, select the products
or product families for the updates you want your WSUS server to synchronize,
and then click OK.
4. Under Products and Classifications, under Update classifications, click
Change.
5. In the Add/Remove Classifications dialog box, in Classifications, select the
update classifications for the updates you want your WSUS server to
synchronize, and then click OK.
6. Under Tasks, click Save settings, and then click OK.
Note:
If you want to stop synchronizing updates for one or more specific products
or product families, clear the appropriate check boxes in the Add/Remove
Products dialog box, and then click OK. Your WSUS server will stop
synchronizing new updates for the products you have cleared. However,
updates that were synchronized for those products before you cleared them
will remain on your WSUS server and will be available on the Updates page.
Configuring Proxy-server Settings
You can configure your WSUS server to use a proxy server during synchronization with
an upstream server or Microsoft Update. In addition, you can specify a port number and
whether you want your server to connect to the proxy server by using specific user
credentials.
You specify proxy-server settings on the Synchronization Options page under Proxy
server. This setting will apply only when your WSUS server runs synchronizations. By
default this option is not enabled, and your WSUS server will connect directly to the
upstream server or Microsoft Update. By default, the proxy-server option is not selected,
15
which means that your WSUS server will attempt to connect directly to another WSUS
server or Microsoft Update during synchronization.
Because WSUS initiates all of its network traffic, you do not need to configure Windows
Firewall on a WSUS server connected directly to Microsoft Update.
To specify a proxy server for synchronization
1. On the WSUS console toolbar, click Options, and then click Synchronization
Options.
2. Under Proxy server, select the Use a proxy server when synchronizing check
box, and then type the server name and port number (port 80 is the default) of
the proxy server.
If you want to connect to the proxy server by using specific user credentials,
select the Use user credentials to connect to the proxy server check box,
and then enter the user name, domain, and password of the user in the
corresponding boxes.
If you want to enable basic authentication for the user connecting to the
proxy server, select the Allow basic authentication (password in clear
text) check box.
3. Under Tasks, click Save settings, and then click OK.
Configuring the Update Source
The update source is the location from which your WSUS server gets its updates and
update information (metadata). You can specify that the update source be either
Microsoft Update or another WSUS server (in this scenario, the WSUS server that acts
as the update source is the upstream server, and your server is the downstream server).
Options for customizing how your WSUS server synchronizes with the update source
include the following:
You can specify a custom port for synchronization. For general information about
configuring ports, see Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
You can use SSL to secure synchronization of update information between WSUS
servers. For more information about using SSL, see Securing Windows Server
Update Services.
16
To specify the update source for your WSUS server
1. On the WSUS console toolbar, click Options, and then click Synchronization
Options.
2. Under Update Source, do one of the following:
If you want your WSUS server to synchronize directly from Microsoft Update,
click Synchronize from Microsoft Update. If your server is running in
replica mode, this option will is disabled. For more information, see Running
in Replica Mode.
If you want to synchronize from another WSUS server in your network, click
Synchronize from an upstream Windows Server Update Services
server, and then type the server name and port number in the corresponding
boxes.
If you want to use Secure Socket Layers (SSL) when synchronizing update
information (metadata) synchronization, type the port number that the
upstream server uses for SSL connections, and then select the Use SSL
when synchronizing update information check box. For more information
about using SSL during synchronization, see Securing Windows Server
Update Services.
If your WSUS server is running in replica mode, you just need to type the
server name in the Server name box. The upstream server does not have to
be the administration server (for example, it can be another replica mode
server). For more information about replica mode, see Running in Replica
Mode.
3. Under Tasks, click Save settings, and then click OK.
Specifying Where to Store Updates
For more information, see Specifying Where to Store Updates.
Synchronizing Manually or Automatically
You can either synchronize your WSUS server manually or specify a time for it to
synchronize automatically on a daily basis.
To synchronize your server manually
1. On the WSUS console toolbar, click Options, and then click Synchronization
17
Options.
2. Under Schedule, click Synchronize manually.
3. Under Tasks, click Save settings, and then click OK.
To synchronize your WSUS server immediately
1. On the WSUS console toolbar, click Options, and then click Synchronization
Options.
2. Under Tasks, click Synchronize now.
To set up an automatic synchronization schedule
1. On the WSUS console toolbar, click Options, and then click Synchronization
Options.
2. Under Schedule, click Synchronize daily at, and then in the list select the time
you want synchronization to start each day.
3. Under Tasks, click Save settings, and then click OK.
Managing Computers and Computer Groups
In this section
Managing Client Computers
Managing Computer Groups
Managing Client Computers
WSUS enables you to manage the entire process of updating your computers, including
manually and automatically determining which updates they need and receive, specifying
when the updates are installed, and monitoring the status of update deployment on your
computers.
The central access point in the WSUS console for managing computers is the
Computers page, which displays a list of computers that have been configured to get
updates from the WSUS server. The computers are displayed by computer group, and
you can filter the computer list to a specific computer group. By selecting a computer in
the list, you can view its properties, which include general details about the computer and
18
the status of updates for it—for example, the installation or detection status of an
update for a particular computer.
You can also manage computer groups on the Computers page, which includes creating
the groups and assigning computers to them. For more information about managing
computer groups, see Managing Computer Groups.
Important:
You must first set up a client computer to contact the WSUS server before you
can manage it from that server. Until you perform this task, your WSUS server
will not recognize your client computer, and will not display it in the computer list
on the Computers page. For more information about setting up a client
computer, see Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
A client computer can only be set to communicate with one WSUS server at a
time. If you later change this setting and specify a different WSUS server, the
client computer stops contacting the WSUS server specified earlier. However,
the client computer will remain on the list of computers and in the computer
groups specified on that earlier WSUS server. In addition, the original WSUS
server will report the last time the client computer contacted it (which will be
accurate—it will be before the client computer stopped connecting to it). To stop
the client computer from displaying on the earlier specified WSUS server, you
must remove the computer from the WSUS server.
Managing Computers on the Computers Page
The following are common tasks you can perform on the Computers page. Before you
can add a computer to a computer group, you must have created a computer group. For
more information about creating computer groups, see Managing Computer Groups.
To view the properties for a computer
1. On the WSUS console toolbar, click Computers.
2. In Groups, click the computer group to which the computer currently belongs to.
3. In the list of computers, click the computer for which you want to view properties.
4. In the properties pane, do either of the following:
Click the Details tab for general information about the computer.
Click the Status tab for approval and update status for the computer.
19
To add a computer to a computer group
1. On the WSUS console toolbar, click Computers.
2. In Groups, click the computer group to which the computer currently belongs.
3. In the list of computers, click the computer that you want to move.
4. Under Tasks, click Move selected computer.
5. In the Computer group dialog box, click the computer group that you want to
move the computer to, and then click OK.
Note:
If your computer already belongs to a computer group, then after you perform
this task it will belong to the new computer group you specify and not to the
earlier computer group. However, it will remain a member of the All
Computers group.
To remove a computer from a WSUS server
1. On the WSUS console toolbar, click Computers.
2. In Groups, click the computer group to which the computer currently belongs to.
3. In the list of computers, click the computer you want to remove.
4. Under Tasks, click Remove the selected computer, and then click OK.
Note:
After you perform this task, you will not be able to manage update distribution
for the client computer on the WSUS console, nor will the client computer will
not be able to receive updates from the WSUS server.
Managing Computer Groups
WSUS enables you to target updates to groups of client computers. This capability can
help you ensure that specific computers get the right updates at the most convenient
times on an ongoing basis. For example, if all computers in one department of your
organization have a specific configuration (such as all computers in the Accounting
team), you can determine what updates those computers get, at what time, and then use
WSUS reporting features to evaluate the success of update activity for that computer
group.
20
By default, each computer is already assigned to the All Computers group. Computers
will also be assigned to the Unassigned Computers group until you assign them to
another group. Regardless of the group you assign a computer to, it will also remain in
the All Computers group. A computer can be in only one other group in addition to the All
Computers group.
You can assign computers to computer groups by using one of two methods, server-side
or client-side targeting, depending on whether or not you want to automate the process.
With server-side targeting, you use the Move the selected computer task on the
Computers page to move one or more client computers to one computer group at a time.
With client-side targeting, you use Group Policy or edit the registry settings on client
computers to enable those computers to automatically add themselves into the computer
groups. You must specify which method you will use by selecting one of the two options
on the Computers Options page.
Note:
If your WSUS server is running in replica mode, you will not be able to create
computer groups on that server, you will only inherit the computer groups created
on the administration server from which your server inherits its settings. For more
information about replica mode, see Running in Replica Mode.
Server-side Targeting
With server-side targeting, you use the WSUS console to both create groups and then
assign computers to the groups. Server-side targeting is an excellent option if you do not
have many client computers to update and you want to move client computers into
computer groups manually.
To enable server-side targeting on your WSUS server, click the Use the Move
computers task in Windows Server Update Services option on the Computers
Options page.
Client-side Targeting
With client-side targeting, you enable client-computers to add themselves to the
computer groups you create in the WSUS console. You can enable client-side targeting
through Group Policy (in an Active Directory network environment) or by editing registry
entries (in a non-Active Directory network environment) for the client computers. When
the client computers connect to the WSUS server, they will add themselves into the
correct computer group. Client-side targeting is an excellent option if you have many
client computers and want to automate the process of assigning them to computer
groups.
21
To enable client-side targeting on your WSUS server, click the Use Group Policy or
registry settings on client computers option on the Computers Options page.
To specify the method for assigning computers to groups
1. On the WSUS console toolbar, click Options, and then click Computer Options.
2. In Computer Options, do one of the following:
If you want to create groups and assign computers through the WSUS
console (server-side targeting), click Use the Move computers task in
Windows Server Update Services.
If you want to create groups and assign computers by using Group Policy or
by editing registry settings on the client computer (client-side targeting), click
Use Group Policy or registry settings on computers.
3. Under Tasks, click Save settings, and then click OK.
Managing Computer Groups on Your WSUS Server
Regardless of the method you use to assign client computers to computer groups, you
must also create the computer groups in the WSUS console. In you use the client-side
targeting method, you must create the computer groups in the WSUS console before
your client computers can add themselves to them.
To create a computer group in the WSUS console
1. On the WSUS console toolbar, click Computers.
2. Under Tasks, click Create a computer group.
3. In Group name, type a name for your new computer group, and then click OK.
To remove a computer group
1. On the WSUS console toolbar, click Computers.
2. In Groups, click the computer group you want to remove.
3. Under Tasks, click Delete the selected group, and then click OK.
Note:
You cannot remove the Unassigned Computers or All Computers group.
Every client computer remains a member of the All Computers group in
addition to any group you assign it to. Client computers are members of the
Unassigned Computers group only until you assign them to a computer
22
group.
Managing Updates
In this section
Updates Overview
Viewing Updates
Approving Updates
Testing Updates
Storing Updates
Updates Overview
Updates are used for patching or providing a full file replacement for software that is
installed on a computer. Every update that is available on Microsoft Update is made up of
two components:
Metadata provides information about the update. For example, metadata supplies
information for the properties of an update, thus enabling you to find out what the
update is useful for. Metadata also includes end-user license agreements (EULAs).
The metadata package downloaded for an update is typically much smaller than the
actual update file package.
Update files are the actual files required to install an update on a computer.
How WSUS Stores Updates
When updates are synchronized to your WSUS server, the metadata and update files are
stored in two separate locations. Metadata is stored in the WSUS database. Update files
can be stored either on your WSUS server or on Microsoft Update servers, depending on
how you have configured your synchronization options. If you choose to store update files
on Microsoft Update servers, only metadata is downloaded at the time of synchronization;
you approve the updates through the WSUS console, and then client computers get the
update files directly from Microsoft Update at the time of installation. For more information
about your options for storing updates, see Deploying Microsoft Windows Server Update
Services at http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
23
Managing Updates by Using WSUS
Whether you have just deployed WSUS or are performing daily tasks, you will be setting
up or (reconfiguring) and running synchronizations, adding computers and computer
groups, and deploying updates on a regular basis. The order in which you perform any of
these general tasks might change, depending on a number of circumstances—for
example, you might change your client computer configurations, (such as adding new
computers, upgrading software).
Although the order you might need to perform the following general tasks might be
different, necessitated by your organizational needs, the following is an example of the
order of general tasks you might undertake in updating computers by using WSUS.
1. Before configuring options in the WSUS console, determine an overall update
management plan based on your network capabilities, company needs, and layout.
Considerations might include the following:
If and how you want to set up a hierarchy of WSUS servers
Which database to use to store update metadata (for example, MSDE, WMSDE,
SQL Server 2000)
What computer groups you want to create, and the method you will use to assign
computers to them (for example, server-side or client-side targeting)
Whether you want updates to synchronize automatically at a specific time
2. Set synchronization options on the Options page, such as update source, product
and update classification, language, connection settings, storage location, and
automatic synchronization schedule.
3. Get the updates and associated metadata on your WSUS server through
synchronization from either Microsoft Update or an upstream WSUS server,
depending on the location you have specified for your update source.
4. Approve or decline updates by group from the Updates page. You can approve
updates for either installation or detection only. For detection only, WSUS does not
install updates but instead checks computers in the groups you specified, to see if a
specific update is needed. To get the result of the detection (or, in other words, to find
out if the update is needed), check the Status of Updates report. You can set a
deadline for automatic installation or detection. For installation, you have the option
of allowing users to install the updates themselves (if they are local administrators on
their client computers).
5. Configure automatic approvals for either installation or detection (by classification
and groups) in Options, on the Automatic Approvals page. If the installation and
detection rules conflict, WSUS will use the installation rule. On this page, you can
24
also configure whether you want to enable automatic approval of revisions to
existing updates or approve revisions manually. If you choose to approve manually,
then your WSUS server will continue using the older version until you manually
approve the revision.
6. Check status of the updates on the Updates page or in the Status of Updates report.
Update Products and Classifications
Updates available on Microsoft Update are differentiated by product (or product family)
and classification.
Products Updated by WSUS
A product is a specific edition of an operating system or application, for example
Microsoft Windows Server 2003, Datacenter Edition. A product family is the base
operating system or application from which the products are derived. An example of a
product family is Microsoft Windows, of which Microsoft Windows Server 2003,
Datacenter Edition is a member. On the Synchronization Options page under Products
and Classifications, products are displayed in a hierarchy, under their product family. At
this location on the WSUS console, you can select the products or product families for
which you want your server to automatically synchronize updates. You can specify many
products at once if they belong to the same product family, because by selecting a parent
check box you also select all items under it. Selecting the child check boxes will not
select the parent check boxes. For every selection, you also are automatically selecting
future releases.
Update Classifications
Update classifications represent the type of update. For any given product or product
family, updates could be available among multiple classifications (for example,
Windows XP family Critical Updates and Security Updates). The following table lists
examples of update classifications.
Update Classification
Description
Connectors
Software components designed to support
connection between software
Critical Updates
Broadly released fixes for specific problems
addressing critical, non-security related
bugs
25
Update Classification
Description
Development Kits
Software to aid the writing of new
applications that usually includes a visual
builder, an editor, and a compiler
Drivers
Software components designed to support
new hardware
Feature Packs
New product functionality usually included
in the next full product release
Guidance
Scripts, sample code, and technical
guidance designed to help in the
deployment and use of a product or
technology
Security Updates
Broadly released fixes for specific products,
addressing security issues
Service Packs
Cumulative sets of all hotfixes, security
updates, critical updates, and updates
created since the release of the product
Service packs might also contain a limited
number of customer requested design
changes or features.
Tools
Utilities or features that aid in
accomplishing a task or set of tasks
Update Rollups
Cumulative set of hotfixes, security
updates, critical updates, and updates
packaged together for easy deployment
A rollup generally targets a specific area,
such as security, or a specific component,
such as Internet Information Services (IIS).
Updates
Broadly released fixes for specific problems
addressing a non-critical, non-security
related bugs
26
Viewing Updates
On the Updates page, you can do the following:
View the list of updates. The list of updates displays updates that have been
synchronized from the update source to your server running Windows Server Update
Services (WSUS) and are available for approval. You can filter the list of updates by
using criteria such as classifications and products, approval status, synchronization
date, and text string. In addition, you can sort the list of updates by clicking the
appropriate column heading in the list of updates title bar
View details, status, and revision history for each update.
Approve updates for installation.
Approve updates for detection.
Decline updates.
To open the Updates page
On the WSUS console toolbar, click Updates.
To view updates
1. On the WSUS console toolbar, click Updates. Updates are displayed in the list of
updates.
2. To sort by additional information, download status, title, classification, release
date, or approval status, click the appropriate column heading.
To filter the list of updates displayed on the Updates page
1. On the WSUS console toolbar, click Updates.
2. Under View, select the appropriate criteria for your filter in the list boxes, and
then click Apply. The list of updates will reflect your chosen criteria. The
Contains Text box, under View, enables you to enter text to search on the
following criteria for an update: Title, Description, and Microsoft Knowledge
Base (KB) article number. Each of these items is a property listed on the
Details tab in the update properties.
To view the properties for an update
1. On the WSUS console toolbar, click Updates.
2. In the list of updates, click the update for which you want to view properties.
27
3. In the properties pane, click one of the tabs for the following:
The Details tab displays both general properties (for example, title,
description, and release date) and installation information (for example,
requirements for installation, including whether the update is uninstallable)
about the update. In addition, the Details tab indicates if the update
supersedes or is superseded by another update.
The Status tab displays download, approval, and installation status for the
update by computer group. You can further expand computer groups to see
update status by computer.
The Revisions tab displays revision information about the update, including
general properties about the revision and approval status.
Note:
You can perform this procedure on only one update at a time. If you select
multiple updates, the first update selected will be displayed in the properties
pane.
Approving Updates
After updates have been synchronized to your WSUS server, you must approve them to
initiate a deployment action. When you approve an update, you are essentially telling
WSUS what to do with it (for example, your choices are Install, Detect only, Remove, or
Decline update). When approving an update, you specify a default approval setting for
the All Computers group, and any necessary settings for each computer group in the
Approve Updates dialog box. If you do not approve an update, its approval status
remains Not approved and your WSUS server performs no action for the update. The
exceptions to this are in the Critical Updates and Security Updates classifications,
which by default are automatically approved for detection after they are synchronized.
The Updates page is the central access point in the WSUS console for approving
updates. On the Updates page, you can specify the action you want WSUS to exercise
for the update by computer group. You do this by selecting one of the options under
Tasks. The following provides more information about the different approvals you can
enable on the Updates page.
If your WSUS server is running in replica mode, you will not be able to approve updates
on your WSUS server. For more information about replica mode, see Running in Replica
Mode.
28
Approving Updates for Detection
When you approve an update for detection, the update is not installed. Instead, WSUS
checks whether the update is compliant with or needed by computers in the groups you
specify for the Detect only approval option in the Approve Updates dialog box. The
detection occurs at the scheduled time that the client computer communicates with the
WSUS server. You can see the result of the detection either in the Status of Updates
report or on the Updates page, by clicking the Status tab for a specific update. In either
case, the information you need will appear in the Needed column, which represents the
number of computers that have been detected as needing a particular update. If the client
computer does not need the update, the number in Needed is zero.
By default, Critical Updates and Security Updates are automatically approved for
detection.
To approve updates for detection
1. On the WSUS console toolbar, click Updates.
2. In the list of updates, click one or more updates that you want to approve for
detection.
3. Under Update Tasks, click Change approval.
4. In the Approve Updates dialog box, verify that Approval is set to Detect only
for the All Computers group.
5. If you want to set a different default approval setting for one or more groups,
under Group approval settings for the selected updates, find the group(s) for
which you want to set the special approval setting, and then, in the Approval
column, select an approval setting.
Approving Updates for Installation
You can select one or multiple updates; if you select multiple updates, you can approve
them for installation at once; you can also approve installation by computer group. This
would be the Install approval option in the Approve Updates dialog box. In addition,
when you specify this approval action, you can do one of the following:
Use the settings on the client computers to determine when to install updates. When
you select this option, users in the targeted computer group will receive a notification
dialog box and an Automatic Updates icon on their taskbar when updates are ready
to be installed on their computers. They can then install the updates immediately, or
at a later time, by clicking the Automatic Updates icon. If you have configured
Automatic Updates, either by Group Policy or locally, to notify the user before
29
installation, these notifications will be offered to any non-administrator who logs
onto the computer in the targeted computer group.
Set a deadline for automatic installation. When you select this option, you set specific
times and dates to install updates, overriding any settings on the client computers. In
addition, you can specify a past date for the deadline if you want to run an approval
action immediately (that is, when the client computers next contact the WSUS
server).
Important:
You cannot set a deadline for automatic installation for an update if user input is
required (for example, accepting a license agreement or specifying a setting
relevant to the update). If you set a deadline for such an installation
synchronization will fail. To determine whether an update will require user input,
look at the May request user input field in the update properties for an update
displayed on the Updates page. Also check for a message in the Approve
Updates box which says "The selected update requires user input and does
not support and installation deadline."
To approve updates for installation
1. On the WSUS console toolbar, click Updates.
2. In the list of updates, click one or more updates that you want to approve for
installation.
3. Under Update Tasks, click Change approval.
4. In the Approve Updates dialog box, verify that Approval is set to Install for the
All Computers group.
5. To specify how and when the update will be installed for computers in the
computer group, next to Deadline, click None, and then click one of the following
options:
If you want to enable users to determine when to install the updates, click
Use client settings to determine update installation time, and then click
OK. If you have configured Automatic Updates, either by domain-based or
local Group Policy, to notify the user before installation, these notifications
will be offered to any non-administrator who logs onto the computer in the
targeted computer group.
If you want the update to be installed automatically, click Install the update
by the selected date and time, specify the date and time of the deadline,
and then click OK. If you want the install to occur immediately (that is, when
30
the client computers next contact the WSUS server), you can specify a past
date for the deadline.
6. If you want to set a different default approval setting for one or more groups,
under Group approval settings for the selected updates, find the group(s) for
which you want to set the special approval setting, and then, in the Approval
column, click an approval setting.
Note:
For more information about downloading and installing updates, see Best
Practices with Windows Server Update Services.
Declining Updates
This option is available as a task under Update Tasks on the Updates page. If you
select this option, the update is removed from the list of available updates. Declined
updates will appear in the updates list only if you select either Declined or All updates in
the Approval list when specifying the filter for the update list under View.
To decline updates
1. On the WSUS console toolbar, click Updates.
2. In the list of updates, click one or more updates that you want to decline.
3. In Update Tasks, click Decline update or Decline selected updates,
depending on whether you have selected one or multiple updates to decline.
Approving Updates for Removal
You can approve an update for removal (that is, approve uninstalling the update). This
option is only available if the update supports uninstalling, and you would choose the
Remove approval option in the Approve Updates dialog box. You can specify a
deadline for the update to be uninstalled, as well as specify a past date for the deadline if
you want to run an approval action immediately (that is, when the client computers next
contact the WSUS server).
To approve updates for removal
1. On the WSUS console toolbar, click Updates.
2. In the list of updates, click one or more updates that you want to approve for
removal.
31
3. Under Update Tasks, click Change approval.
4. In the Approve Updates dialog box, verify that Approve is set to Remove for
the All Computers group.
5. If you want to set a deadline for the update(s) to be automatically removed, next
to Deadline, click None, specify the date and time for the deadline, and then
click OK. If you want the update removal to occur immediately (that is, when the
client computers next contact the WSUS server), you can specify a past date for
the deadline.
6. If you want to set a different default approval setting for one or more groups,
under Group approval settings for the selected updates, find the group(s) for
which you want to set the special approval setting, and then, in the Approval
column, click an approval setting.
Approving Updates Automatically
On the Automatic Approval Options page, you can configure your WSUS server to
automatically approve installation or detection for updates and associated metadata
when they are downloaded to the WSUS server during synchronization. This is different
from approving updates on the Updates page, where, by default, updates are approved
for detection.
You can configure automatic approval for updates by update classifications and groups. If
the installation and detection rules you set conflict, your WSUS server will follow the
installation rules.
On the Automatic Approval Options page, you can also select an option to
automatically approve revisions to existing updates as they become available. This option
is selected by default. A revision is a version of an update that has had changes made to
it (for example, it might have expired, or UI text, the EULA, or applicability rules for
computers might have changed). If you do not choose to automatically approve the
revised version of an update, WSUS will use the older version, and you must manually
approve the update revision.
Automatically Approving Updates for Detection
When you select this option, you can create a rule that your WSUS server will
automatically apply during synchronization. For the rule, you specify what updates you
want to automatically approve for detection, by update classification and by computer
group. This applies only to new updates, as opposed to revised updates. This setting is
available on the Automatic Approval Options page.
32
On this page, you can also set a rule for automatically approving updates for
installation. In the event that rules conflict (for example, you have specified the same
update classification and same computer group combination in both the rule to
automatically approve for detection and automatically approve for installation), then your
WSUS server applies the rule to automatically approve for installation.
To automatically approve updates for detection
1. On the WSUS console toolbar, click Options, and then click Automatic
Approval Options.
2. In Updates, under Approve for Detection, select the Automatically approve
updates for detection by using the following rule check box (if it is not
already selected).
3. If you want to specify update classifications to automatically approve during
synchronization, do the following:
Next to Classifications, click Add/Remove Classifications.
In the Add/Remove Classifications dialog box, select the update
classifications that you want to automatically approve, and then click OK.
4. If you want to specify the computer groups for which to automatically approve
updates during synchronization:
Next to Computer groups, click Add/Remove Computer Groups.
In the Add/Remove Computer Groups dialog box, select the computer
groups for which you want to automatically approve updates, and then click
OK.
5. Under Tasks, click Save settings, and then click OK.
Automatically Approve Updates for Installation
When you select this option, you can create a rule that your WSUS server will
automatically apply during synchronization. For the rule, you specify what updates you
want to automatically approve for installation, by update classification and by computer
group. This applies only to new updates, as opposed to revised updates. This setting is
available on the Automatic Approval Options page.
On this page, you can also set a rule for automatically approving updates for detection. In
the event that rules conflict (for example, you have specified the same update
classification and same computer group combination in both the rule to automatically
33
approve for installation and automatically approve for detection), then your WSUS
server applies the rule to automatically approve for installation.
To automatically approve updates installation
1. On the WSUS console toolbar, click Options, and then click Automatic
Approval Options.
2. In Updates, under Approve for Installation, select the Automatically approve
updates for installation by using the following rule check box (if it is not
already selected).
3. If you want to specify update classifications to automatically approve during
synchronization, do the following:
Next to Classifications, click Add/Remove Classifications.
In the Add/Remove Classifications dialog box, select the update
classifications that you want to automatically approve, and then click OK.
4. If you want to specify the computer groups for which to automatically approve
updates during synchronization:
Next to Computer groups, click Add/Remove Computer Groups.
In the Add/Remove Computer Groups dialog box, select the computer
groups for which you want to automatically approve updates, and then click
OK.
5. Under Tasks, click Save settings, and then click OK.
Automatically Approving Revisions to Updates
The Automatic Approval Options page contains an option to automatically approve
revisions to existing updates as they become available. This option is selected by default.
A revision is a version of an update that has changes (for example, it might have expired,
or have an updated EULA, UI text, or applicability rules for computers). If you configure
your WSUS server to automatically approve new revisions of an update but an expired
revision for the update is synchronized, your WSUS server will automatically decline the
update. If you choose not to automatically approve the revised version of an update, your
WSUS server will use the older revision, and you must manually approve the update
revision.
To automatically approve revisions to updates
1. On the WSUS console toolbar, click Options, and then click Automatic
34
Approval Options.
2. Under Revisions to Updates, click Automatically approve the latest revision
of the update.
3. Under Tasks, click Save settings, and then click OK.
Approving Superseding or Superseded Updates
Typically, an update that supersedes other updates does one or more of the following:
Enhances, improves, and/or adds to the fix provided by one or more previously
released updates.
Improves the efficiency of its update file package, which is installed on client
computers if the update is approved for installation. For example, the superseded
update might contain files that are no longer relevant to the fix, or to the operating
systems now supported by the new update, so those files are not included in the
superseding update's file package.
Updates newer versions of operating systems. It is also important to note that the
superseding update might not support earlier versions of operating systems.
Conversely, an update that is superseded by another update does the following:
Fixes a similar vulnerability to the update that supersedes it. However, the update
that supersedes it might enhance the fix that the superseded update provides.
Updates earlier versions of operating systems—in some cases these versions of
operating systems are no longer updated by the superseding update.
In the list of updates on the Updates page, an icon next to the update indicates that it
has a supersedure relationship to another update. The Details tab in the properties for
the update tells you whether the update supersedes or is superseded by another update.
In addition, you can determine which updates supersede or are superseded by the
update by looking at the Supersedes and Superseded by entries. The properties box for
the update is available at various locations in the WSUS console (for example, on the
Updates page, on the Computers page).
WSUS does not automatically decline superseded updates, and it is recommended that
you do not assume that superseded updates should be declined in favor of the new,
superseding update. Before declining a superseded update, make sure that it is no longer
needed by any of your client computers. Following are examples of scenarios where you
might need to install a superseded update:
If a superseding update supports only newer versions of an operating system, and
some of your client computers run earlier versions of the operating system.
35
If a superseding update has more restricted applicability than the update it
supersedes, which would make it inappropriate for some client computers.
If an update no longer supersedes a previously released update due to new changes.
It is possible that through changes at each release, an update no longer supersedes
an update it previously superseded in an earlier version. In this scenario, you will still
see a message on the Details tab for the superseded update that it has been
superseded, even though the update that supersedes it has been replaced by an
update that does not.
Recommended Process for Approving a Superseding Update
Because a superseding update typically enhances a fix provided by a previously
released, superseded update, it is recommended that you first see how many client
computers will be compliant with the new update, and work backward from there. Use the
following process.
To approve a superseding update
1. Approve the superseding update for Install on all computers where the fix
provided by the update is appropriate.
2. Check the resulting status of the approval action on your computers. Note which
computers show status as Not needed for the update, and then compare the
properties of those computers with the properties of the update.
3. Use the information available in the update properties to help you determine
which previously released version of the updates are available. For example,
look under Supersedes on the Details tab, and check the Description and KB
article number entries if appropriate.
4. Get information about the superseded, previously released versions of the
updates; for example, view their properties.
5. When you find a superseded update that seems appropriate for the remaining
client computers, approve the update for installation.
6. Repeat this process until all of your client computers are updated with the
intended fix.
Approving Office Updates
If you use WSUS to update Microsoft Office on your network computers, consider the
following:
36
If you have purchased a "per user" license agreement for Office, you must ensure
that each user's installation of Office is updated (for example, there might be two
users who run individually licensed copies of Microsoft Office on the same computer).
This means a particular user has to be logged on to the computer for that specific
copy of Office to be updated. For example, if two people both have accounts on a
computer that is running Microsoft Office, then each of them has to log on and update
his or her Office installation, otherwise one of them will not have an updated version
of Office.
Users can access the public Microsoft Office Online Web site and can look for
updates to their Office installation through the Microsoft Office Update wizard. Using
Group Policy, you might want to create policies that prevent users from getting their
own Office updates from Microsoft Office Online.
Unlike Windows Update or Microsoft Office Online, which are public Web sites that
users can visit directly, Microsoft Update is accessed only by WSUS servers. It is
currently in beta release and makes security updates available only for Office XP and
Office 2003. Some critical updates are not available through Microsoft Update.
Therefore, some updates might appear on the Microsoft Office Online Web site that
are not available on Microsoft Update.
Approving SQL Server and Exchange Server Updates
Updating Microsoft SQL Server Instances
Your installations (instances) of Microsoft SQL Server on one computer can possibly get
complex, because you can enable any of the following SQL Server scenarios:
Multiple instances of SQL server on the computer at the same time
Multiple versions (releases) of SQL
SQL Server instances in multiple languages on the same computer
Typically, there is nothing extra you have to do to update these multiple instances,
you just need to make sure that when you specify your synchronization options (for
example, product, update classifications, and language options) you account for
requirements for the versions of the SQL Server instances you have on the
computer. For more information about configuring synchronization options, see
Setting Up and Running Synchronizations.
Updating Microsoft SQL Server and Microsoft Exchange Servers that are Part of a
Cluster
Both Microsoft SQL Server and Microsoft Exchange Server can be installed in a clustered
environment. If there is an update available for servers in a cluster that are running these
37
programs, each server in the cluster must be updated individually. Microsoft
recommends that you install updates in sequence of the cluster configuration. For
example, you would first update the active cluster node, then initiate a fail-over and make
the next passive cluster node active to update it, and so on until all cluster nodes are
updated.
Note:
You can have both a stand-alone instance and a cluster instance of SQL Server
on the same server. If you are updating the active cluster node in this scenario,
the stand-alone instance of SQL Server on the same server will also be updated
if you have specified the correct synchronization options (product, update
classification, and language). For more information about setting synchronization
options, see Setting Up and Running Synchronizations.
Testing Updates
Until you install an update, you cannot be certain about the impact it will have on the
existing code running on your systems. By installing an update in a test environment
before deploying it to your production environment, you can analyze and assess its
impact before it has the opportunity to harm your production systems. This can prevent
unplanned downtime and lost productivity.
WSUS enables you to create custom computer groups, which you can use to test
updates. For example, the following figure depicts three computer groups: two custom
groups created by the administrator (Test and Accounting), as well as the built-in All
Computers group.
In this example, the Test group contains a small number of computers representative of
all the computers contained in the Accounting group. This creates a virtual test lab. The
administrator can first approve updates for the Test group. If the testing goes well, the
administrator can roll out the updates to the Accounting group.
38
You can expand this basic scenario to fit testing needs for your organization. For
example, you can create multiple test computer groups that resemble actual computer
groups containing computers with different configurations.
Storing Updates
In this section
Specifying Where to Store Updates
Managing the Databases
Specifying Where to Store Updates
You can specify whether you want to store update files on your local WSUS server or on
Microsoft Update. If you choose to store the updates locally, you can limit the updates
downloaded to your server by language. If you choose to store the update files on
Microsoft Update, then your WSUS server obtains only update information (metadata) for
the criteria you have specified on the Synchronization Options page. In this scenario,
the update files come directly from Microsoft Update and are downloaded at the time of
installation on the client computers receiving updates. You will need to make sure your
client computers have direct access to Microsoft Update in this scenario.
Local Storage Considerations
If you decide to store update files on your server, the recommended minimum disk size is
30 GB. However, depending on the synchronization options you specify, you might need
to use a larger disk. For example, when specifying advanced synchronization options, as
39
in the following procedure, if you select options to download multiple languages and/or
the option to download express installation files, your server disk can easily reach 30 GB.
Therefore if you choose any of these options, install a larger disk (for example, 100 GB).
If your disk gets full, you can install a new, larger disk and then move the update files to
the new location. To do this, after you create the new disk drive, you will need to run the
WSUSutil.exe tool (with the movecontent command) to move the update files to the new
disk. For this procedure, see Managing WSUS from the Command Line.
About Express Installation Files
Express installation files download in a package that is usually multiple times larger than
a regular update package. The express installation file package contains the different
versions of the update that will apply to specific client computer configurations. If you
select this option, the package containing all multiple versions of update files is
downloaded to your WSUS server. However, when your client computers connect to the
server, they will download only the update files they need, which are the files that are
compliant for the specific computer. You might have selected the express installation file
option if you are less concerned with external bandwidth than internal bandwidth usage.
Besides bandwidth, another consideration when choosing to download express
installation files, as mentioned earlier, is disk space. If you choose to download express
installation files, they will take more disk space. Therefore, use a larger disk (more than
30 GB) if you select this option.
The option to download and store express installation files is in covered in step 3 in the
following procedure.
To specify where to store downloaded update files
1. On the WSUS console toolbar, click Options, and then click Synchronization
Options.
2. Under Update Files and Languages, click Advanced.
3. Under Update Files, select whether to store update files on the server running
Windows Server Update Services (WSUS) or on Microsoft Update. If you choose
to store update files on your server, you can choose either to download update
files only when they are approved, or to download express installation files.
4. If you selected to store the files on the WSUS server, under Languages, select
whether you want to limit the updates downloaded to your WSUS server by
language, and then click OK. Note that if you select to download all languages
(which is selected by default) that this will take more disk space. If possible,
consider limiting the languages you download if you are also choosing to store
40
update files on your WSUS server.
5. In Tasks, click Save settings, and then click OK.
Note:
If your WSUS server is running in replica mode, you will not be able to
perform this task. For more information about replica mode, see Running in
Replica Mode.
Changing the Location where You Store Update Files Locally
You might need to change the location where WSUS stores updates locally. This might
be required if the disk becomes full and there is no longer any room for new updates. You
might also have to do this if the disk where updates are stored fails and the replacement
disk uses a new drive letter.
You accomplish this move with the movecontent command of WSUSutil.exe, a
command-line tool that is copied to the file system of the WSUS server during WSUS
Setup. By default, Setup copies WSUSutil.exe to the following location:
WSUSInstallationDrive:\Program Files\Microsoft Windows Server Update Services\Tools\
You must be a member of the local Administrators group on the WSUS server to use the
movecontent command of WSUSutil.exe. These operations can only be run from the
WSUS server itself, which must be a 32-bit platform.
You must create the new path for local WSUS update storage prior to using
WSUSutil.exe. The movecontent command takes an optional -skipcopy parameter. The
-skipcopy parameter enables you to change the location of local WSUS update storage
without copying any files. For more information about WSUSutil.exe, see Deploying
Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
To change the location of local WSUS update storage
1. Click Start, and then click Run.
2. In the Open box, type cmd, and then click OK.
3. At the command prompt, navigate to the directory that contains WSUSutil.exe.
4. Type the following, and then press ENTER:
wsusutil.exe movecontent contentpath logfile [-skipcopy]
For example, type:
wsusutil.exe movecontent D:\WSUS1\ D:\move.log
41
where D:\WSUS1 is the new path for local WSUS update storage, and
D:\move.log is the path to the log file.
Note:
If you do not want to use WSUSutil.exe to change the location of local WSUS
update storage, you can also use NTFS functionality to add a partition to the
current location of local WSUS update storage. For more information about
NTFS, go to Help and Support Center in Windows Server 2003.
Managing the Databases
The WSUS database is a required component of WSUS (which is configured during
setup) that stores the following types of information:
WSUS server configuration information
Metadata that describes what each update is useful for
Aside from the actual update files, the metadata is the second part of every update
available on Microsoft Update. Update files are stored separately, either on Microsoft
Update, or on your WSUS server. For more information, see Specifying Where to Store
Updates.
Information about client computers, updates, and client interaction with updates
Depending on your server and network configurations, you are running an MSDE,
WMSDE, or SQL Server 2000 database for your WSUS installation (for more information
about your database options when installing WSUS, see "Choose the Database Used for
WSUS" in Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
The following table describes non-deployment tasks you might have to perform as part of
regular operations.
42
Database management tasks
Database
Tasks
MSDE
Make space in the database when the
2-GB limit is reached. For more
information, see Managing WSUS from
the Command Line.
Backup / restore. For more information,
see Backing Up Windows Server
Update Services.
Move data to a SQL Server 2000
database (for example, if you are
upgrading the database from MSDE to
SQL Server 2000).
Backup / restore. For more information,
see Backing Up Windows Server
Update Services.
Move data to a SQL Server 2000
database (for example, if you are
upgrading the database from WMSDE
to SQL Server 2000). See
Backup / restore.
Move data to another SQL Server 2000
database (for example, if you move
WSUS to another server and you will
again use SQL Server 2000 for the
database).
WMSDE
SQL Server 2000
Running in Replica Mode
A WSUS server running in replica mode inherits the update approvals and computer
groups created on an administration server. In a scenario that uses replica mode, you
typically have a single administration server, and one or more subordinate replica WSUS
servers spread out throughout the organization, based on site or organizational
topography. You approve updates and create computer groups on the administration
43
server, which the replica mode servers will then mirror. Replica mode servers can be
set up only during WSUS Setup, and if you implemented this scenario, it is likely because
it is important in your organization that update approvals and computer groups are
managed centrally.
If your WSUS server is running in replica mode, you will be able to perform only limited
administration capabilities on the server, which will primarily consist of:
Adding and removing computers from computer groups
Computer group membership is not distributed to replica servers, only the computer
groups themselves. Therefore, on a replica mode server, you will inherit the computer
groups that you created on the administration server. However, the computer groups
will be empty. You must then assign the client computers that connect to the replica
server to the computer groups.
Setting a synchronization schedule
Specifying proxy-server settings
Specifying the update source
This can be a server other than the administration server.
Viewing available updates
Monitoring update, synchronization, and computer status, and monitoring WSUS
settings on the server
All standard WSUS reports are available on replica mode servers.
For more information about setting up and running in replica mode, see Deploying
Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
Backing Up Windows Server Update Services
Although WSUS does not provide a built-in backup tool, you can use the Backup Utility
that is available on all servers running Windows 2000 or Windows Server 2003 to easily
back up and restore both the WSUS database and update file storage folder. The Backup
Utility is also known as Ntbackup.exe.
Backing up WSUS involves backing up the following:
The WSUS database, which contains:
Update metadata, including information about updates (for example, properties).
Metadata is also where EULAs are stored.
44
WSUS server configuration information, which includes all settings for your
WSUS server (that is, options you specified through the WSUS console and
settings configured by WSUS automatically during setup).
Information about client computers, updates, and client interaction with updates.
You can access this information through the WSUS console when you view
status and run reports on update status and client computer status.
The folder where the update files are stored. Update files are the actual files required
to install an update on a computer. By default, update files are stored in the
%systemdrive%\WSUS\WSUSContent folder on your WSUS server. If you have
chosen to store update files on Microsoft Update (either during setup or on the
Options page), you do not have to back up the update file storage folder on your
WSUS server.
If you are using a full version of Microsoft SQL Server 2000 for your database, which is
not installed by WSUS, you can use SQL Server Enterprise manager as an alternative to
the Backup Utility. For more information about SQL Server Enterprise Manager, refer to
your SQL Server documentation. For more information about database options and
configurations for WSUS, see Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
To back up the update file storage folder
1. On your WSUS server, click Start, and then click Run.
2. In the Open box, type %systemdrive%\%windir%\system32\ntbackup.exe and
then click OK.
3. In the Backup or Restore Wizard, click Next.
4. Verify that Back up files and settings is selected, and then click Next.
5. Click Let me choose what to back up, and then click Next.
6. Select the WSUSContent folder (under %systemdrive%\WSUS\), and then click
Next.
7. Use the Browse button to choose a place to save your backup, type a name for
the backup, and then click Next.
8. If you want to set additional specifications for your backup, including whether it
will be an incremental backup, whether you want to verify the backup, set a
recurring schedule for the backup, or other options, click Advanced, and then
follow the instructions in the wizard.
9. When the wizard is finished, click Finish.
45
10. When the message appears that informs you that the backup is complete, click
Close.
To back up the WSUS database
1. On your WSUS server, click Start, and then click Run.
2. In the Open box, type %systemdrive%\%windir%\system32\ntbackup.exe and
then click OK.
3. In the Backup or Restore Wizard, click Next.
4. Verify that Back up files and settings is selected, and then click Next.
5. Click Let me choose what to back up, and then click Next.
6. Under %systemdrive%\WSUS\MSSQL$WSUS\, select the Data and LOG
folders, and then click Next.
7. Use the Browse button to choose a place to save your backup, type a name for
the backup, and then click Next.
8. If you want to set additional specifications for your backup, including whether it
will be an incremental backup, whether you want to verify the backup, set a
recurring schedule for the backup, or other options, click Advanced, and then
follow the prompts that appear in the wizard.
9. When the wizard is finished, click Finish.
10. When the message appears that informs you that the backup is complete, click
Close.
To restore the update file storage folder
1. On your WSUS server, click Start, and then click Run.
2. In the Open box, type %systemdrive%\%windir%\system32\ntbackup.exe and
then click OK.
3. In the Backup or Restore Wizard, click Next.
4. Click Restore files and settings, and then click Next.
5. In the What to restore dialog box, under Items to restore, expand the file that
contains the WSUSContent folder (under %systemdrive%\WSUS\), and then
click Next.
Alternatively, you can select a subset of the
%systemdrive%\WSUS\WSUSContent folder to restore. Within the
46
%systemdrive%\WSUS\WSUSContent folder, you can restore one, all, or a
combination of its subfolders and files.
6. If you want to set additional specifications for your restore, including whether you
want to restore the files or folders to a different location, replace existing files,
restore security settings, or specify other options, click Advanced, and then
follow the instructions in the wizard.
7. When the wizard is finished, click Finish.
8. When the message appears that informs you that restoring is complete, click
Close.
To restore the WSUS database
1. On your WSUS server, click Start, and then click Run.
2. In the Open box, type %systemdrive%\%windir%\system32\ntbackup.exe and
then click OK.
3. In the Backup or Restore Wizard, click Next.
4. Click Restore files and settings, and then click Next.
5. In the What to restore dialog box, under Items to restore, expand the file that
contains the Data and LOG folders (under
%systemdrive%\WSUS\MSQL$WSUS), and then click Next.
Alternatively, you can select a subset of the
%systemdrive%\WSUS\MSQL$WSUS\Data or
%systemdrive%\WSUS\MSQL$WSUS\LOG folders to restore. Within the
%systemdrive%\WSUS\MSQL$WSUS\Data and
%systemdrive%\WSUS\MSQL$WSUS\LOG folders, you can restore one, all,
or a combination of their subfolders and files.
6. If you want to set additional specifications for your restore, including whether you
want to restore the files or folders to a different location, replace existing files,
restore security settings, or specify other options, click Advanced, and then
follow the instructions in the wizard.
7. When the wizard is finished, click Finish.
8. When the message appears that informs you that restoring is complete, click
Close.
47
Best Practices with Windows Server Update Services
This section provides best practices for managing updates through WSUS.
Use Group Policy to Update Multiple Computers
If you have set up Active Directory in your network, you can configure one or multiple
computers simultaneously, by including them in a Group Policy object (GPO), and then
configuring that GPO with WSUS settings. Microsoft recommends that you create a new
Group Policy object (GPO) that contains only WSUS settings. Link this WSUS GPO to an
Active Directory container appropriate for your environment. In a simple environment, you
might link a single WSUS GPO to the domain. In a more complex environment, you might
link multiple WSUS GPOs to several organizational units (OUs), which will enable you to
apply different WSUS policy settings to different types of computers.
Important:
Microsoft recommends that you do not edit the Default Domain or Default
Domain Controller GPOs.
Typically, when you configure WSUS through Group Policy (in an Active Directory
network environment), you set up your client computers to connect to a WSUS server
and download updates once a day. By default, this is every 22 hours (minus a random
time offset, described later in this topic) at which time the approval actions you specified
for the new updates (for example, installation, detection, or removal) run on the client
computer.
However, if you are aware of and want to protect computers against immediate security
threats, you might want to set up more a more frequent schedule for computers to
contact the WSUS server, download, and install updates.
To specify how and when computers are updated through Group Policy
1. In Group Policy Object Editor, expand Computer Configuration, expand
Administrative Templates, expand Windows Components, and then click
Windows Update.
2. In the details pane of Group Policy Object Editor, configure the appropriate
policies. See the following table for examples of the policies you might want to
set.
48
Policies for Configuring Automatic Updates Behavior
Policy
Description
Configure Automatic Updates
By enabling this setting you enable your
computer to receive updates through
Automatic Updates on a computer or
computer group. To complete this setting,
you must then select one of the following
four options:
No auto-restart for scheduled Automatic
Updates installations
Notify before downloading any updates
and notify again before installing them.
Download the updates automatically
and notify when they are ready to be
installed (default setting)
Automatically download updates and
install them on the schedule specified
below
Allow local administrators to select the
configuration mode that Automatic
Updates should notify and install
updates
Specifies that to complete a scheduled
installation, Automatic Updates will wait for
the computer to be restarted by any user
who is logged on, instead of causing the
computer to restart automatically.
49
Policy
Description
Automatic Updates detection frequency
Configures the frequency with which
computers contact the WSUS server. The
exact time between contact will actually be
the number of hours you specify here,
minus zero to twenty percent of the hours
specified. For example, if this policy is used
to specify a 20-hour contact frequency, then
all client computers to which this policy is
applied will check for updates anywhere
between 16 and 20 hours. If you leave this
policy set to Disabled or Not Configured,
Windows will check for available updates at
the default interval of 22 hours.
Allow Automatic Updates immediate
installation
Specifies whether Automatic Updates
should automatically install certain updates
that neither interrupt Windows services nor
restart Windows.
It will take a few minutes before the new policies you have configured take effect. It will
be about 20 minutes after Group Policy refreshes (applies any new settings to the client
computer). By default, computer Group Policy refreshes in the background every 90
minutes, with a random offset of 0 to 30 minutes. If you want to refresh Group Policy
sooner, you can go to a command prompt on the client computer and type:
gpupdate /force.
For more information about Group Policy, see Group Policy at
http://go.microsoft.com/fwlink/?LinkID=14232. For more information about options for
setting up and configuring your client computers in both Active Directory and non-Active
Directory network environments, see Deploying Microsoft Windows Server Update
Services at http://go.microsoft.com/fwlink/?LinkID=41777.
Schedule Update Installations when there is Little Chance for Lost
Productivity
In managing the process of updating computers (which includes WSUS servers), one of
your main goals is to have any planned downtime occur when there is little chance for
lost productivity. The following are suggestions for accomplishing this:
50
To update WSUS servers or specific computers efficiently, put the WSUS servers
or computers in their own computer group, and deploy to that group with a deadline
set for a time when it is feasible for the WSUS servers or computers to be down (for
example, on Sunday at 3:00 A.M).
Deploy updates by using a deadline in the future. For example, set the WSUS
servers or computers with a scheduled installation at a time when it is feasible for
them to be briefly offline (for example, on Sunday at 3:00 A.M).
Configure client computers or WSUS servers through Group Policy to immediately
install updates that do not require a restart. (Before you approve an update for
installation, you can read the Description field in the properties for an update in
order to determine whether the update will require restarting the computer. You can
view the properties for an update by selecting it in the list of updates on the Updates
page in the WSUS console.) Enable the policy to install immediately any updates that
do not require a computer restart, so that they are installed every day. Computers
can then install any updates that do not interrupt service when they are ready to
install (that is, scheduling for Sunday morning installation would be unnecessary).
The tile of this policy is Allow Automatic Updates immediate installation (see the
table earlier in this topic for more information).
For maximum control over when your servers are restarted as
necessitated by an update installation, set Group Policy to Download
the updates automatically and notify when they are ready to be
installed, and then create a script that enables to you accept and
install the updates and then restart the computer on demand
Some updates require a computer restart after they are installed (and, by default, will
restart computers 5 minutes after they are installed.) By not restarting your servers after
installing these updates, you leave them at risk. [benag] However, depending on your
network configuration, it might also risky to restart your servers automatically, since many
other resources in your network could depend on a single server. In this case, it might not
be feasible to schedule automatic scheduled restarts of your server.
There are a couple of Group Policies that enable you to configure when a computer is
restarted. However, when talking about servers, these policies have some limitations
over control:
No auto-restart for scheduled Automatic Updates installations—this policy will
prevent automatic restarts of your server, and will enable manual restart—however,
you have to log on to the server and then initiate the restart. This might not be
practical if your server is typically unattended.
51
Delay restart for scheduled installations—this policy can delay the time between
the update installation and the computer restart, however, the maximum time you can
set here is 30 minutes.
If these are issues for you, consider the following procedure:
1. Use Group Policy to configure automatic download, and manual installation of the
updates. To do this, you would enable the Configure Automatic Updates Group
Policy setting by selecting the Download the updates automatically and notify when
they are ready to be installed option.
2. Create a script to automate installing the updates and then restarting of your server.
This script would have the effect of a “button” you would push to initiate all this,
therefore the updates install and the server restarts when you run the script. You can
do this at the most appropriate time. For more information about creating scripts to
automate Automatic Updates tasks (for example downloading and installing updates
on server and client computers), see Windows Update Agent Software Developer's
Kit (http://go.microsoft.com/fwlink/?LinkID=43101)
Managing WSUS from the Command Line
This topic does the following
Summarizes the purpose and functionality of WSUSutil.exe and its parameters.
Provides and defines the syntax you would use to run specific tasks.
Links to "Deploying Microsoft Windows Server Update Services" where more
information (for example, scenarios) is available.
Running WSUSutil.exe
WSUSutil.exe is a tool that you can use to manage your WSUS server from the
command line. WSUSutil.exe is located in the %drive%\Program Files\Update
Services\Tools folder on your WSUS server. You can run specific commands with
WSUSutil.exe to perform specific functions, as summarized in the following table. The
syntax you would use to run WSUSutil.exe with specific commands follows the table.
52
Summary of Commands You Can Use with WSUSutil
Command
What it enables you to
When you might use it
do
export
The first of the two
parts that make up
the export / import
process.
On an ongoing basis, if you
are running a network with
limited or restricted Internet
connectivity
On an ongoing basis, if you
are running a network with
limited or restricted
connectivity
The export
command enables
you to export update
metadata to an
export package file.
You cannot use this
parameter to export
update files, update
approvals, or server
settings.
import
The second of the
two parts that make
up the export/import
process.
The import
command imports
update metadata to a
server from an export
package file created
on another WSUS
server. This
synchronizes the
destination WSUS
server without using
a network
connection.
53
Command
What it enables you to
When you might use it
do
migratesus
This command
migrates update
approvals from a
SUS 1.0 server to a
WSUS server.
If you are upgrading your
implementation SUS 1.0 to
WSUS.
movecontent
Changes the file
system location
where the WSUS
server stores update
files, and optionally
copies any update
files from the old
location to the new
location
Hard drive is full
Disk fails
reset
deleteunneededrevisions
Checks that every
update metadata row
in the database has
corresponding update
files stored in the file
system. If update files
are missing or have
been corrupted,
WSUS downloads
the update files
again.
Purges the update
metadata for
unnecessary update
revisions from the
database.
After restoring the WSUS
database.
When troubleshooting
To free up space when an
MSDE is full
54
Command
What it enables you to
When you might use it
do
listinactiveapprovals
Returns a list of
update titles with
approvals that are in
a permanently
inactive state
because of a change
in server language
settings.
When you change
language settings on an
upstream server (that is the
parent to a replica server)
and want to see which
updates are no longer
active because they are not
in the new languages you
have specified. You can
run this command if you
want to see a list of inactive
approvals (for example, to
help you decide if you want
to remove the inactive
approvals). You do not
have to run this command
before running the
removeinactiveapprovals
command.
removeinactiveapprovals
Removes approvals
for updates that are
in a permanently
inactive state
because of a change
in WSUS server
language settings.
When you change
language settings on an
upstream server (that is the
parent to a replica server)
and want to remove
updates that are no longer
active because they are not
in the new languages you
have specified. This would
fix the resulting mismatch
in the number of updates
displayed on the parent
and replica servers in this
scenario. You do not have
to run the
listinactiveapprovals
command before running
this command.
55
Export
For background and procedural information about exporting and importing updates, see
"Set Up a Disconnected Network (Import and Export Updates)" in Deploying Microsoft
Windows Server Update Services at http://go.microsoft.com/fwlink/?linkid=41777.
Syntax
At the command line %drive%\Program Files\Update Services\Tools>, type:
wsusutil export package logfile
The parameters are defined in the following table.
Parameter
Definition
package
The path and file name of the package .cab
to create.
logfile
The path and file name of the log file to
create.
/help or /?
Displays command-line help for export
command.
Import
For background and procedural information about exporting and importing updates, see
"Set Up a Disconnected Network (Import and Export Updates)" in Deploying Microsoft
Windows Server Update Services at http://go.microsoft.com/fwlink/?linkid=41777.
Syntax
At the command line %drive%\Program Files\Update Services\Tools>, type:
wsusutil import package logfile
The parameters are defined in the following table:
Parameter
Definition
package
The path and file name of the package .cab
to import.
56
Parameter
Definition
logfile
The path and file name of the log file to
create.
/help or /?
Displays command-line help for import
command.
Migratesus
SUS 1.0 to WSUS migration scenarios and related procedures are covered extensively in
the "Migrate from a SUS Server to a WSUS Server" topic in Deploying Microsoft
Windows Update Services at http://go.microsoft.com/fwlink/?LinkID=41777.
Syntax
At the command line %drive%\Program Files\Update Services\Tools>, type:
wsusutil migratesus [/content contentshare] [/approvals servername [computergroup]]
[/log logfile] [/?]
The parameters are defined in the following table:
Parameter
Definition
/content contentshare
Migrates content from a SUS 1.0, where
contentshare is the path to the folder that
contains SUS 1.0 content.
/approvals servername
Migrates approvals from the SUS 1.0
server, where servername is the name of
the SUS 1.0 server.
computergroup
Computer group for which you want to
apply the approvals.
/help or /?
Displays command-line help for the
migratesus parameter.
/log logfile
File in which migration activities are
logged.
Movecontent
When you run this command, WSUSutil.exe does the following:
57
Copies the update files from the old location into the new location.
Updates the WSUS database to refer to the new location of the update files.
The destination folder where update files are moved to must be on an NTFS partition.
The content move tool will not try to copy update files if they already exist in the
destination folder. WSUSutil.exe sets the same permissions on the destination folder that
were set on the original folder.
Note:
You can use xcopy, the Backup utility, or other non-WSUS specific methods to
copy update files from the old location into the new one. If you copy the files by
using a method other than WSUSutil.exe, you still need to run WSUSutil.exe to
perform the second part of the move. In this case you would use the skipcopy
parameter when running WSUSutil.exe. See "Syntax" below for more
information.
There are two scenarios in which you might move update files from one WSUS drive to
another:
If the drive is full
If the hard disk fails
If the drive is full
If the drive where WSUS stores update files is full, you can do one of the following:
Add more space to your current drive by using NTFS functionality. This is done
without using WSUSutil.exe. This method does not affect WSUS configuration or
operation.
Install a new drive, and then move the update files from the old drive to the new
location by using Wsusutil.exe.
If the hard disk fails
If the hard disk that stores update files fails, you must do the following:
1. Install the new disk on your computer, and then restore the update files from your
backup files. Note: If you have not backed up your update files, WSUSutil.exe
downloads the missing files at the end of the content move operation.
2. Run the content move operation, specifying the location for the new disk. In addition,
you specify the skipcopy parameter, because you are either putting the files in the
new folder through the Backup utility or the source folder does not exist; the update
files will be downloaded at the end of this process.
58
3. When the move operation is complete, all the missing files are downloaded.
Syntax
At the command line %drive%\Program Files\Update Services\Tools>, type:
wsusutil movecontent contentpath logfile -skipcopy [/?]
The parameters are defined in the following table.
Parameter
Definition
contentpath
The new root for content files. The path
must exist.
logfile
The path and file name of the log file to
create.
-skipcopy
Indicates that only the server configuration
should be changed, and that the content
files should not be copied.
/help or /?
Displays command-line help for
movecontent command.
Reset
You use this command if you store updates locally on your WSUS server and want to
ensure that the metadata information stored in your WSUS database is accurate. With
this command, you verify that every update metadata row in the WSUS database
corresponds to update files stored in the local update file storage location on your WSUS
server. If update files are missing or have been corrupted, WSUS downloads the update
files again. This command might be useful to run after you restore your database, or as a
first step when troubleshooting update approvals.
Syntax
At the command line %drive%\Program Files\Update Services\Tools>, type:
wsusutil reset
Deleteunneededrevisions
If you use an MSDE database in your WSUS implementation (for example, if you are
using WSUS on a server running Windows 2000), you might need to run this command
periodically when the database reaches its 2-GB limit because once the database is full,
59
you cannot synchronize new updates to your server, add new computers, or import
events from existing client computers.
With regular use, it is possible that the 2 GB will be reached quickly, as updates can be
very large, and update publishers typically create multiple revisions of each update,
which your server will synchronize automatically for the products and update
classifications you specify. In addition, event information for client computers also
populates the database. When your MSDE database is close to reaching its limit, you will
receive a notification on the WSUS console Home page alerting you to run this command
soon. When you run this command, unneeded revisions and the events associated with
those revisions are deleted from the database.
Unneeded revisions are revisions to software or drivers updates that have not been
deployed to a computer group in at least one month; they are also the latest revisions to
expired driver updates that have not been deployed to a computer group for at least one
month. The one-month time period in both of these cases can be changed, indirectly. It
automatically gets reduced by 7 to 15 days if you reduce the size of a database that is
larger than 1 GB by less than 25 percent in the process of running this command.
Note:
For more information about the databases you can use with WSUS, see the
"Choose the Database Used for WSUS" topic in Deploying Microsoft Windows
Update Services at http://go.microsoft.com/fwlink/?LinkID=41777.
Syntax
At the command line %drive%\Program Files\Update Services\Tools>, type:
wsusutil deleteunneededrevisions
Important:
Before running this command, you must stop the World Wide Web publishing
service in IIS. You must restart it only after you have finished running this
command. To stop or start the IIS service, open IIS, navigate to and then rightclick the Web site where WSUS is is installed (by default this is the Default Web
Site), and then click Stop or Start.
Listinactiveapprovals
If you change language options on an upstream WSUS server, you can create a situation
where the number of updates approved on a parent upstream server does not match the
number of approved updates on a replica server.
Here is a scenario where this might occur:
60
You have configured your upstream parent server to synchronize from Microsoft
Update and have left the language setting set to All Languages (the default). You then
run synchronization and approve 300 updates, of which 50 are not English language
updates. You then change the language setting on the server to English only. After this,
a replica server synchronizes from the parent upstream server and downloads only the
"active" approvals, which now are only the English language ones (replica servers always
only synchronize active approvals). At this point, if you look on the WSUS console on the
parent server, you will see that 300 updates are approved. If you do the same on the
replica server, you will see that only 250 are approved. You would use
listinactiveapprovals to see a list of the updates on the parent upstream server that are
permanently inactive—in this case, you would see the 50 updates that are not English.
You can run this command if you want to see a list of the inactive approvals (for example,
to help you decide if you want to remove the inactive approvals). You do not have to run
this command before running the removeinactiveapprovals command.
Syntax
At the command line %drive%\Program Files\Update Services\Tools>, type:
wsusutil listinactiveapprovals
Removeinactiveapprovals
The scenario in which you would use this command is the same as the one described for
listinactiveapprovals. However, while you use listinactiveapprovals to list the inactive
approvals on the parent upstream server, you use removeinactiveapprovals to remove
them. You do not have to run the listinactiveapprovals command before running this
command.
Syntax
At the command line %drive%\Program Files\Update Services\Tools>, type:
wsusutil removeinactiveapprovals
Monitoring Windows Server Update Services
In this section
Update Status Terminology
Running Reports
61
Update Status Terminology
You can access update status from various locations in the WSUS console. The following
table defines each possible status that can be reported by WSUS for an update.
Typically, WSUS presents update status for a particular computer (for example, the
status of an update on one computer) or computer group (for example, status for the five
computers in Computer Group X on which the update has been installed).
Update Status Definitions
Status
Description
Installed
The update was installed on the computer.
62
Status
Description
Needed
This is the positive result of a Detect only
approval. When referring to the status of
one computer, Needed means the update is
compliant with (and should be installed on)
the computer. When referring to status for a
computer group, the Needed column
displays the number of computers in the
group with which the update is compliant.
Additionally, a positive Needed result
means, technically, that as of the last time
client computers made contact with the
WSUS server, the update was determined
to be compliant, but has not been installed.
Therefore, it is possible that any of the
following could be true when the status for
an update is Needed:
You have approved the update for
installation but the client computers have
not yet contacted the WSUS server since
you made this change.
You have not yet approved the update for
installation, although the Detect only action
has been performed.
The update has already been downloaded
and installed, but the client computer has
not contacted the WSUS server since the
update was installed.
The update has already been downloaded
and installed but the update requires that
the client computer be restarted before
changes go into effect, and the client
computer has not yet been restarted.
The update has been downloaded to the
computer but not installed.
The update has been neither downloaded
nor installed on the computer.
63
Status
Description
Not needed
This is the negative result of a Detect only
approval. When referring to the status of
one computer, Not needed means the
update is not compliant with or required by
that computer. When referring to the status
for a computer group, the Not needed
column displays the number of computers
in the group for which the update is not
compliant or required.
Unknown
Typically, this means that since the time
that the update was synchronized to the
WSUS server, the computer has not
contacted the WSUS server.
Failed
An error occurred when either a detection
or an installation was attempted on the
computer for the update.
Last contacted
This is the date on which the computer last
contacted the WSUS server.
Running Reports
Reports enable you to monitor the components of your Windows Server Update Services
implementation.
Using the Reports Page
You can generate three main reports from the Reports page, as described in the
following table, and in the sections that follow.
Reports Available on Reports Page
Report Name
Function
Status of Updates
View the status of all approved updates by
computer group and computer.
64
Report Name
Function
Status of Computers
View the status of client computers and the
status of updates on those computers (for
example, a summary of updates that have
been installed or are needed for a particular
computer).
Synchronization Results
View a list of new updates, update
revisions, and errors that occurred during
synchronization.
Settings Summary
View or print a summary of the settings
configured through the Options page.
Status of Updates Report
The Status of Updates report enables you to view the status for all of your approved
updates. You can view the report in three ways: you can view the status of an update at a
high level, by computer group, and by computer.
The report displays information resulting from the most recent contact between client
computers and the WSUS server. The frequency with which client computers contact the
WSUS server is configured through Group Policy. By default, this is every 22 hours.
Unless you want to change the contact frequency for your client computers, generate this
report the day after you approve updates, so that it reflects your latest approvals. For
more information about configuring Group Policy, see Deploying Microsoft Windows
Server Updates Services at http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
Note:
You can use a command-line tool on client computers that are running the
WSUS client software (Automatic Updates) in order to initiate contact between
the client computer and WSUS server. This can be useful if you want to get
immediate update status for a particular computer—you can run this tool to force
connection and then generate a Status of Updates report.
To initiate immediate contact between a client computer and WSUS server
On the client computer, at the command prompt, type wuauclt.exe /detectnow,
and then press ENTER.
65
To run a Status of Updates report
1. On the WSUS console toolbar, click Reports.
2. On the Reports page, click Status of Updates.
Update summary view
The update summary view is the default view that appears when you run a Status of
Updates report. By default, the report displays an alphabetical list of approved updates.
You can filter the display by both approval action and computer group by making
appropriate selections under View and then clicking Apply. Your filter is reset to the
default list of all updates when you close the Status of Updates report.
The columns displayed in the update summary view are described in the following table.
Description of Columns Displayed in Update Summary View
Column Name
Description
Title
The name of the update.
To view the properties for an update, click
an update in this column. The update
properties box provides the following
information:
The Details tab contains general
information about the update.
The Status tab contains status information
for the update by computer group. This is
also what you see in computer group view.
You can also expand this view into
computer view by expanding a computer
group.
The Revisions tab displays information
about changes to the update.
Installed
The number of computers on which the
update has been installed.
66
Column Name
Description
Needed
The number of computers for which the
update is applicable but not installed. For
these computers, a detect-only action has
been performed for the update. If an update
requires a restart, then a computer that has
installed the update will continue to appear
in the Needed column until it is restarted.
Failed
The number of computers that last reported
a failed download, installation, or removal
(uninstallation).
Last Updated
The date that the latest action for this
update occurred.
Computer group view
The computer group view displays the status of an update by computer group. To use
this view, expand any update that is listed in update summary view.
The columns displayed in the computer group view are described in the following table.
Description of Columns Displayed in Computer Group View
Column Name
Description
Computer Group
The name of the computer group to which
the update has been targeted.
Approval
The action that this update has been
approved for, specific to the group.
Deadline
The deadline for the action, if you have set
a deadline.
Installed
The number of computers on which the
update has been installed.
67
Column Name
Description
Needed
The number of computers for which the
update is applicable but not installed. For
these computers, a detect-only action has
been performed for the update. If an update
requires a restart, then a computer that has
installed the update will continue to appear
in the Needed column until it is restarted.
Failed
The number of computers that last reported
a failed download, installation, or removal
(uninstallation).
Computer view
The computer view displays the status of each computer in a computer group. To use the
computer view, expand a computer group.
The columns displayed in this view are described in the following table.
Description of Columns Displayed in Computer View
Column Name
Description
Computer Name
Name of the computer
To see the properties for the computer, click
the computer name. The computer
properties dialog box that appears displays
details and status for the computer. The
Status tab displays the result of the last
communication between the WSUS server
and the computer, and the status of
updates for which an action has been
approved on the computer.
68
Column Name
Description
Status
The status will be one of the following:
Failed - The download, installation, or
removal action for the update on this
computer was not completed.
Needed - The update is applicable but
not installed. If an update requires a
restart, then a computer that has
installed the update will continue to be
counted as needed until it is restarted.
Not needed - The update is not
applicable.
Installed - The update has been
installed.
Unknown - No action has been
performed on the computer.
To see details for an event, click the result
in the Status column.
Printing the report
You can print the report in update summary, computer group, or computer view,
depending on how you have expanded the Status of Updates report.
To print the Status of Updates report
1. Expand your report into update summary, computer group, or computer view,
depending on the information you want to print.
2. Under Tasks, click Print report.
Note:
You cannot use the Print report task to print a dialog box, and the Print report
task is not enabled if a dialog box is open.
69
Status of Computers Report
The Status of Computers report provides both a cumulative and individual update status
summary for computers in the computer group and for the update status results you
specify. The following table provides more information about the status provided for each
update.
Description of Status Displayed in Status of Computers Report
Status
Description
Installed
The update was installed on the computer.
Needed
A detection was performed on the computer
for the update, which determined that the
update should be installed on the computer.
Not needed
Either the update is already installed on the
computer, or the update does not belong to
a product or classification you specified
when configuring synchronization options.
Unknown
Typically, this means that since the time
that the update was synchronized to the
WSUS server, the computer has not yet
contacted the WSUS server.
Failed
An error occurred when either a detection
or an installation was attempted on the
computer for the update.
Last contacted
This is the date on which the computer last
contacted the WSUS server.
You can also print the report, including the list of individual updates with status for
individual computers, if you have expanded the computers (clicked the + symbol).
However, you cannot print the dialog box that appears when you click individual updates
in the list or when you click the status for an individual update.
To run a status report for computers
1. On the WSUS console toolbar, click Reports, and then click Status of
Computers.
2. Under View, select the criteria you want to use to filter the report, and then click
70
Apply. The report displays a cumulative update status summary for all of the
computers in the computer group and for the status you specified.
3. If you want more information about a specific computer, you can do the following:
To view the status of individual updates for the computer, expand the
computer (click the + sign next to the computer). In addition, you can see the
properties of an individual update by clicking the title of the update.
To view more information about the specific status result of an update (or,
the event details), click the status for the update.
4. To print the report, under Tasks, click Print report.
Synchronization Results Report
The Synchronization Results report enables you to see synchronization information for
your server for a given time period, including errors that occurred during synchronization
and a list of new updates. In addition, you can get general, status, and revision
information for each new update.
To run a Synchronization Results report
1. On the WSUS console toolbar, click Reports.
2. On the Reports page, click Synchronization Results. By default, the report
displays synchronization results for the last 30 days.
3. To change the synchronization period for the report, under View, select another
synchronization period in the list, and then click Apply.
4. To print the report, under Tasks, click Print report.
Note:
The Print report task is not enabled if you have a dialog box open. You
cannot use the Print report task to print a dialog box.
The report has four components, which are described in the following table.
Components of Synchronization Results Report
Component Name
Purpose
Last Synchronization
Displays information about the last time the
WSUS server synchronized with Microsoft
Update or another WSUS server, and if it
was a successful synchronization.
71
Component Name
Purpose
Synchronization Summary
Displays summary information about new
updates and errors that occurred during
synchronization.
Errors
For each error, displays the date of the
error, a description of the error, and the
update ID associated with the error.
New Updates
Displays the updates that have been
synchronized to the WSUS server for the
given time period.
You can view the properties for each new
update by clicking the update in the New
Updates list. The update properties dialog
box that appears contains details, status,
and revision for the update. It is identical to
the update properties box that appears in
the Status of Updates report when you click
an update in the list. It is also identical to
the properties tabs associated with each
update on the Updates page.
Settings Summary Report
The Settings Summary report enables you to view and print a summary of all of the
settings that can be specified on the Options page.
To run a Settings Summary report
1. On the WSUS console toolbar, click Reports.
2. On the Reports page, click Settings Summary.
The following table describes the components of the Settings Summary report.
72
Components of Settings Summary Report
Component Name
Purpose
Synchronization Schedule
The time that your WSUS server
automatically synchronizes to the update
source.
Products and Classifications
The update products and classifications
that you want to synchronize with your
server.
Update source
The location from which the server
synchronizes.
Proxy server
The proxy server used during
synchronization.
Update Files
The location where update files are stored
(on the WSUS server or on Microsoft
Update). Also, the download options you
have selected.
Languages
The languages for the updates that
synchronize to the server. Only updates
available in the languages specified are
synchronized with the WSUS server.
Automatic Approval
The automatic approval settings for specific
update classifications, targeted by
computer group.
Revisions to Updates
The approval action that your WSUS server
will perform when revisions to existing
updates are available; whether update
revisions are automatically approved by
your server, or whether they must be
manually approved.
Downstream servers
The servers which receive updates from
the WSUS server.
Client computer Options
The method you have selected for
assigning computers to groups.
73
Component Name
Purpose
Database
The name of the database used by the
WSUS server.
To print a Settings Summary report
Under Tasks, click Print report.
Running Compliance Status Reports
You can view or print two types of compliance status reports, one for individual
computers and one for individual updates:
To run a computer compliance status report
1. On the WSUS console toolbar, click Computers, and then click the computer for
which you want to produce the compliance status report.
2. Click Print status report.
3. If you want more information about a specific update under Update Status, you
can do the following:
To view the properties of an individual update, click the title of the update.
To view more information about the specific status result of an update (or the
event details), click the status for the update.
4. To print the report, click the File menu, and then click Print.
To run an update compliance status report
1. On the WSUS console toolbar, click Updates, and then click the update for
which you want to produce the compliance report.
2. Click Print status report.
3. To print the report, click the File menu, and then click Print.
74
Securing Windows Server Update Services
For synchronization with upstream WSUS servers, you can use Secure Sockets Layer
(SSL) protocol to secure the update metadata portion of the synchronization. WSUS can
use SSL to:
Enable client computers and downstream WSUS servers to authenticate an
upstream WSUS server.
Encrypt metadata passed on to client computers and downstream WSUS servers.
For more information about configuring your WSUS server to use SSL, see Deploying
Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
Troubleshooting Windows Server Update
Services
This guide provides troubleshooting information for Windows Server Update Services.
In this guide
WSUS Server Administration Issues
Client Computer Administration Issues
WSUS Server Administration Issues
In this section
Setup Issues
Uninstalling WSUS from SQL Server
Cannot access the WSUS console
Update storage issues
Synchronization issues
Update approval issues
Client computers do not appear in the WSUS console
Backup and restore issues
75
General error messages
Setup Issues
If you are having trouble installing WSUS, use the following information to troubleshoot
the problem.
Check for required software and hardware
WSUS has a number of requirements that need to be met prior to installation. For more
information, see Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
In some cases, setup might fail if you choose the WMSDE database
In some cases, when you choose the WMSDE database, Setup tries to repair WMSDE
and falls into an infinite loop. This is a known issue with the RC release of WSUS. Use
this Knowledge Base article at http://go.microsoft.com/fwlink/?LinkId=48007 to recover
from this problem and install WSUS by using WMSDE.
If the Server service is not running when you install WSUS, the
WSUS installation fails
If you select WMSDE for your database software and the Server service is not running on
the computer where you intend to install WSUS, the WSUS installation fails. This is
because WMSDE requires the Server service to be running to install, and if WMSDE fails
to be installed, the WSUS installation fails.
To work around this issue, turn on the Server service, and run WSUS Setup again. Use
the Knowledge Base article You cannot install MSDE 2000 if the Server service is not
running at http://go.microsoft.com/fwlink/?LinkId=48009 to recover from this problem and
install WSUS by using WMSDE.
You cannot install MSDE 2000 if the Server service is not running
Upgrade Issues
When an upgrade fails, WSUS might be uninstalled
Depending on at what point an upgrade fails, you might lose your previous WSUS
settings and data. Therefore, before attempting an upgrade, back up the following:
76
WSUS database
Update file storage folder
For information about backing up and restoring your existing WSUS installation, see
Backing Up Windows Server Update Services.
Uninstalling WSUS from SQL Server
If you uninstall WSUS, read the following information.
Uninstalling might leave some WSUS configurations on computers
running SQL server
Local SQL Server accounts that are created by WSUS Setup are not removed by the
WSUS uninstall component. The WSUS uninstall component does not remove Network
Service and ASP.NET accounts from the local computer running SQL server. If some
other application or database is using these accounts, this ensures that these
applications or databases do not fail. If you are sure that no other application or database
requires the Network Service or ASP.NET accounts, you can manually remove them from
the computer running SQL server.
For information about how to manually remove Network Service or ASP.NET accounts
from a computer running SQL Server 2000 or MSDE, see SQL Server product
documentation. You can download product documentation for SQL Server 2000 from the
SQL Server 2000 Books Online (Updated 2004) page of the Microsoft Web site at
http://go.microsoft.com/fwlink/?LinkId=13959.
Cannot access the WSUS console
If you get an error when using or trying to access the WSUS console, use the following
information to troubleshoot the problem.
Grant users permissions for WSUS console access
If users do not have appropriate permissions for the WSUS console, they receive an
"access denied" message when trying to access the WSUS console. You must be a
member of the Administrators group or the WSUS Administrators group on the server on
which WSUS is installed in order to use the WSUS console.
77
Note:
If WSUS is installed on a domain controller, only a member of the Domain
Administrator group can use the WSUS console.
To add a user to the WSUS Administrators group
1. On the WSUS server, click Start, click Administrative Tools, and then click
Computer Management.
2. In Computer Management, expand Local Users and Groups, click Groups,
and then double-click WSUS Administrators.
3. In the WSUS Administrators Properties dialog box, click Add.
4. In the Enter the object names to select (examples) box, type the object name,
and then click OK.
You cannot access the WSUS console with an IP address when
WSUS is configured to use a proxy server
If you have WSUS configured to use a proxy server, then you cannot access the WSUS
console by using an IP address. To work around this issue, use a domain name to
access the WSUS server, for example, for the username, type: DomainName\username
for the username, when prompted to log in on the WSUS console.
Cannot access the WSUS console and a timeout error message
appears
If you cannot access the WSUS console and a timeout error message appears, the CPU
of the WSUS server may be at, or very close to, maximum utilization, causing the
database to time out. If the database software times out, the WSUS console cannot be
displayed.
One way of inadvertently overtaxing your WSUS server is to have antivirus software
installed on it, which is monitoring the WSUS content directory. During synchronization,
the antivirus software can overload out the CPU. You can work around this situation by
setting the antivirus software to ignore where WSUS content is stored.
Cannot access the WSUS console on a Windows 2000 server after
applying the hisec server.inf security template
This issue applies only to Windows 2000 servers. If you cannot access the WSUS
administrative console after applying the hisec server.inf security template, you need to
78
relax security permissions for ASP.NET and IWAM local machine accounts in order for
the WSUS console to function.
The workaround is to give read access for IWAM and ASP.NET accounts to the following
registry key.
HKEY_LOCAL_MACHINE\software\microsoft\update services
To give read access for the IWAM account on Windows 2000 Server configured
as a domain controller
1. Click Start, and then click Run.
2. In the Open box, type regedit.exe and then click OK.
3. In Registry Editor, navigate to the following key:
HKEY_LOCAL_MACHINE \Software\Microsoft\Update Services
4. Point to Edit, and then click Permissions.
5. In the Permissions for Microsoft Windows Server Update Services properties
dialog box, click Add.
6. In the Select Users, Computers, or Groups box, click Locations.
7. In the Locations dialog box, select the local computer, and then click OK.
8. In the Select Users, Computers, or Groups box, type
computer_name\ASPNET and computer_name\IWAM_computer_name in the
Enter the object name to select (examples) box. Use a semicolon to separate
names. For example, type
computer_name\ASPNET;computer_name\IWAM_computer_name
where computer_name is the name of the computer.
9. Select computer_name\ASPNET, and click the Read box in the Allow column.
10. Select computer_name\IWAM_computer_name, and click the Read box in the
Allow column, and then click OK.
Promoting the WSUS server to a domain controller might disrupt
your ability to access the WSUS console
When you promote a WSUS server to a domain controller and then try to access the
WSUS console, you might receive a message similar to the following:
79
Server Error in '/' Application.
Access to the path "C:\WINDOWS\Microsoft.NET\Framework\v1.1.4322\Temporary ASP.NET
Files\wsusadmin\8c91a6b5\649b28ba\global.asax.xml" is denied.
This occurs if IIS 6.0 and ASP.NET are installed on the server before the server is
promoted to a domain controller. This is because the Network Service group does not
have sufficient permissions for the Temporary ASP.NET Files folder. To avoid this
problem, make sure that you promote the WSUS server to a domain controller before you
install IIS 6.0 and ASP.NET. To resolve this issue, enable appropriate permissions for the
Network Service group by using the following procedure.
To enable appropriate permissions for the Network Service group
1. Click Start, and then click Run.
2. In the Open box, type cmd, and then click OK.
3. At the command prompt, type the following, and then press ENTER:
drive:\windows\microsoft .net\framework\v1.1.4322\aspnet_regiis -i
where drive is the drive letter of the disk on which you installed Windows.
Cannot access the WSUS console on Windows 2000 Server
configured as a domain controller
If you cannot access the WSUS administrative console and you are using Windows 2000
Server configured as a domain controller, you need to relax security permissions for
ASP.NET in order for the WSUS console to function. The workaround is to give read
access for IWAM account to %windir%\assembly.
To give read access for the IWAM account on Windows 2000 Server configured
as a domain controller
At the command prompt, type the following, and then press ENTER:
cacls %windir%\assembly /e /t /p IWAM_xxxx:R
where %windir% is the Windows directory of the computer and where
IWAM_xxxx is the IWAM computer account.
80
For details, see the Knowledge Base article at
http://support.microsoft.com/default.aspx?scid=kb;[LN];317012
Update storage issues
Updates can be stored on the local WSUS server or on Microsoft Update. Use this
section to troubleshoot problems with update storage.
The updates listed in the WSUS console do not match the updates
listed in your local folder
This can happen under different circumstances. For example, if updates are stored on a
disk separate from the WSUS application itself, and that disk fails, when you replace the
failed disk with a new (empty) disk, the WSUS application will still show all of the updates
as downloaded.
To have WSUS verify which updates are stored on the disk, you must run the
WSUSutil.exe using the reset command.
Note:
Performing a reset causes the WSUS server to be unresponsive for up to five
minutes.
To have WSUS verify locally stored updates
1. Click Start, and then click Run.
2. In the Open box, type cmd, and then click OK.
3. At the command prompt, navigate to the directory that contains WSUSutil.exe.
4. Type the following, and then press ENTER: wsusutil.exe reset
Synchronization issues
Synchronization is the process in which the WSUS server connects to Microsoft Update
or to another WSUS server and downloads updates. During synchronization, WSUS
determines if any new updates have been made available since the last time you
synchronized. If it is your first time synchronizing WSUS, all updates are made available
for approval. If synchronizations are failing, you can try the following procedures.
81
Check proxy-server settings by using the WSUS console
If your WSUS server is connected to Microsoft Update via a proxy server, you must use
the WSUS console to allow WSUS to access the Internet. For basic instructions about
setting up a proxy server, see Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409. If your proxy server supports
authentication, make sure you have the correct user name, password, and domain. Note
that if you use the WSUS console option for Allow basic authentication (password in
clear text), the password for the account is sent over the network in unencrypted text.
Check the name of the upstream WSUS server
If your WSUS uses another WSUS server as its update source, make sure you are using
the correct name for the upstream WSUS server and that you have spelled it correctly.
For basic instruction about synchronizing two WSUS servers, see Deploying Microsoft
Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409. The name that you enter in the
WSUS console on the downstream WSUS server must match the name of the upstream
WSUS server.
To determine if there is a problem with network name resolution services, use the ping
command from the downstream WSUS server that cannot synchronize. You should use
the same naming convention that is used in the WSUS console. For example, if you used
a NetBIOS name in WSUS console, use the NetBIOS name of the upstream server with
the ping command. If you cannot ping the upstream server, you might have a problem
with network name resolution services. To work around this type of issue, you could use
a different name resolution service or the IP address of the upstream server.
To ping an upstream WSUS server by using the ping command
1. Click Start, and then click Run
2. In the Open box, type cmd, and then click OK.
3. Type the following, and then press ENTER:
ping WSUSServerNname
where WSUS server name is the name of the upstream WSUS server you are
trying to synchronize with.
82
Check update storage options
If you have multiple WSUS servers chained together in a hierarchy, the entire hierarchy
must use the same update storage option or else synchronizations fail. For example, if
the upstream WSUS server stores content locally, all the downstream WSUS servers
must store content locally. Check that each WSUS server in the chain uses the same
update storage option. For information about how to set WSUS update storage options,
see Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
Verify that users and the network service have Read permissions to
the local update storage directory
If you store update files on your WSUS server, you need to ensure that the folder to
which you download update files has at least Read permissions for the network service
and for users. This is true whether the server you download the update files to is an
upstream or downstream WSUS server. The folder where update files are stored if you
have chosen to store them locally (as opposed to storing them on Microsoft Update
servers) is %systemdrive%\Update Services\US content.
On a downstream WSUS server, check that the updates are available
on the upstream WSUS server
There are number of situations where the updates on the upstream server no longer
match the updates being requested at synchronization by the downstream server. Some
of the following are examples of when this might occur:
An upstream WSUS server is re-installed and the list of classifications and products
the administrator selects is a reduced number than previously selected on the earlier
installation of the WSUS upstream server. The downstream server(s) might then
attempt to synchronize updates that the newly rebuilt upstream server has no
knowledge of. Therefore the synchronization would fail for those updates that do not
exist on the upstream server.
If you configure a downstream server to get updates from a different upstream server
with different products and classifications selected.
To troubleshoot this issue, on the downstream server, make a note of the title of the
updates for which download failed. These will be visible on the Updates page, and
marked with a red X. Then, check if these updates exist on the upstream server (look at
the Updates page. If they do not match, do one of the following, depending on which
updates you need:
83
Specify the missing updates on the upstream server, and then synchronize from
the update source.
On the downstream server, cancel the updates that are not on the upstream server, if
these updates are no longer needed. Then decline the old updates on the
downstream server.
If the missing updates (according to the downstream server) are actually available on
the upstream server, then the error is transient, meaning the update might have been
downloaded to the upstream server after it was requested by the downstream server.
This issue will resolve itself the next time the downstream server synchronizes to the
upstream server.
Restart the BITS service
If the BITS service was disabled during synchronization, synchronization will fail. To
ensure that the BITS services is properly enabled, restart both the BITS service and
restart the WSUS service.
To restart the BITS service and the WSUS service
1. On the WSUS server, click Start, point to Administrative Tools, and then click
Services.
2. Right-click Background Intelligent Transfer Service, and then click Restart, or
click Start if the BITS service is not running or has been disabled.
3. Right-click Windows Update Service, and then click Restart.
4. Retry synchronization: in the WSUS console, click Options, click
Synchronization Options, and then under Tasks, click Synchronize now.
If you are unable to download update files to your local WSUS server,
your server might not support the necessary HTTP protocol
If synchronization of update files to your WSUS server fails, you might see the following
message in the corresponding event log:
Content file download failed. Reason: The server does not support the necessary
HTTP protocol. Background Intelligent Transfer Service (BITS) requires that the
server support the Range protocol header.Source File: /msdownload/update/v319990518/cabpool/windows2000-kb873339-x86enu_500e4656b4f0ca3431565631989090bbeeb74bcc.exe Destination File:
84
%drive%\wsus\WsusContent\WsusContent\CC\500E4656B4F0CA3431565631989090BBEEB74BCC
.EXE.
This problem occurs if your proxy environment doesn’t support HTTP 1.1 Protocol. You
can manually work around this by running the following commands at the command
prompt to configure BITS.
To resolve this issue:
1. Type: net stop WSUSService, and then press ENTER.
2. Type: "%programfiles%\Update Services\tools\osql\osql.exe" S SQL_InstanceName -E -b -n –Q "USE SUSDB update tbConfigurationC set
BitsDownloadPriorityForeground=1" and then press ENTER.
3. Type: net start WSUSService.
4. Close the command prompt window and retry synchronization: in the WSUS
console, click Options, click Synchronization Options, and then under Tasks,
click Synchronize now.
The number of updates that are approved on a parent upstream
server does not match the number of approved updates on a replica
server
This might occur if you have changed language settings on the parent upstream server
after first synchronizing with the old language settings. For more information see
"Listinactiveapprovals" in Managing WSUS from the Command Line.
Update approval issues
If you are having problems with approvals, use the following sections to troubleshoot the
problem.
If IIS Lockdown is installed on WSUS and client computers, do not
download updates stored on the WSUS server
If you are using the IIS Lockdown Wizard and have installed the URLScan tool, ensure
that you edit the Urlscan.ini file to allow *.exe requests.
After you edit this file, you must restart both IIS and the WSUS server. You can find the
Urlscan.ini file in the\WINNT\System32\Inetserv\Urlscan directory on the boot drive of
your computer.
85
To edit the Urlscan.ini file
1. Open Urlscan.ini in a text editor.
2. Remove ".exe" from the [DenyExtensions] section.
3. Make sure the following settings appear under the [AllowVerbs] section:
GET
HEAD
POST
OPTIONS
New approvals can take up to one minute to take effect
If you approve an update on the WSUS console and there are client computers running
detection at that exact moment, those computers might not get the approved update until
they go through another detection cycle. The WSUS server requires approximately one
minute to begin offering newly approved updates to client computers.
Remote computers accessed by using Terminal Services cannot be
restarted by non-administrators
Non-administrators using terminal services computers will not be able to restart their
computers remotely. Therefore, if a remote computer on which an update is installed
needs to be restarted for the update to take effect, users without administrative
permissions will be unable to complete the updating of their remote computer.
The number of updates that are approved on a parent upstream
server does not match the number of approved updates on a replica
server
This might occur if you have changed language settings on the parent upstream server
after first synchronizing with the old language settings. For more information see
"Listinactiveapprovals," in Managing WSUS from the Command Line.
Client computers do not appear in the WSUS console
If you are having problems with client computers not appearing on the Computers page
in WSUS console, use the following sections to troubleshoot the problem.
86
Problem with client self-update
If you cannot get clients to appear on the Computers page in the WSUS console, it is
almost always a problem with client self-update, which is the mechanism that WSUS
uses to update the SUS client to the WSUS client (Automatic Updates) software. For
more information about client-self update, see Automatic Updates must be updated.
Backup and restore issues
If you cannot access WSUS data after restoring the database, check
the WSUS server name and user permissions for the database
If you restore a WSUS database but cannot access the restored from the WSUS console
check for the following:
If you have changed the WSUS server name since the backup, you must add the
corresponding users to the database to enable the WSUS console to access the
data.
If you restore the backup to a WSUS server other than the one from which you
backed up the database, you will have the same result and must also add the
corresponding users.
In either case, the users need to be granted permissions for public and Web service.
General error messages
This topic covers general error messages displayed on the Home page or in dialog boxes
that open from the WSUS console.
…some services are not running. Check the following services…
On the Home page, you might receive a message telling you to check specific services.
The following briefly covers the services.
Selfupdate
See Automatic Updates must be updated for information about troubleshooting the
Selfupdate service.
87
WSUSService.exe
This service facilitates synchronization. If you have problems with synchronization,
access WSUSService.exe by clicking the Start button, pointing to Administrative Tools,
clicking Services, and then finding Windows Server Update Service in the list of
services. Do the following:
Verify that this service is running. Click Start if it is stopped or Restart to refresh the
service.
You can also use Event Viewer to check the Application, Security, and System
event logs to see if there are any events that might indicate a problem.
You can also check the SoftwareDistribution.log to see if there are events that might
indicate a problem.
Web services
Web services are hosted in IIS. If they are not running, ensure that IIS is running (or
started). You can also try resetting the Web service by typing iisreset at a command
prompt.
SQL service
Every service except for the selfupdate service requires that the SQL service is running.
If any of the log files indicate SQL connection problems, check the SQL service first. To
access the SQL service, click the Start button, point to Administrative Tools, click
Services, and then look for one of the following:
MSSQLSERVER (if you are using WMSDE or MSDE, or if you are using SQL Server
and are using the default instance name for the instance name)
MSSQL$WSUS (if you are using a SQL Server database and have named your
database instance "WSUS")
Right-click the service, and then click Start if the service is not running or Restart to
refresh the service if it is running.
Client Computer Administration Issues
In this section
Automatic Updates must be updated
Computers are not appearing in the correct computer groups
88
Automatic Updates must be updated
WSUS uses IIS to automatically update most computers to the WSUS-compatible
Automatic Updates (WSUS client). This process is called client self-update. To
accomplish client self-update, WSUS Setup creates a virtual directory under the WSUS
Web site named Selfupdate. This virtual directory holds the WSUS-compatible Automatic
Updates. This is called the selfupdate tree.
Using Group Policy to point client computers to your WSUS server should eventually
cause an Automatic Updates detection and client self-update. For more information about
this process, see Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
Troubleshooting client self-update issues
If the client self-update does not work automatically, use the following suggestions to
troubleshoot the problem.
How to differentiate between the SUS client and WSUS client
Use the Automatic Updates user interface (UI) to differentiate between the SUS and
WSUS clients. The following illustrations show the user interface of the SUS and WSUS
clients.
89
SUS Client
90
WSUS Client
Verify that the client software in your organization can self-update
Some computers might already have the WSUS client installed. Other computers might
have a version of Automatic Updates that is incapable of performing self-update. For
more information see Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409. If the clients in your
organization are capable of and require self-update but are still not self-updating, see the
next section.
Verify that the SUS clients are pointed to the WSUS server
If you have the WSUS client installed but the client computer is pointed to a SUS server,
Automatic Updates falls into legacy mode and the client computer uses the SUS client
user interface. In this case you need to redirect the computer away from the SUS server
91
to get the WSUS client to function. When you point Automatic Updates away from the
SUS server, it automatically comes out of legacy mode and the new client user interface
appears.
If your client computers are pointed to the WSUS server and you do not see the WSUS
client user interface shown above, see the next section.
Check for the selfupdate tree on the WSUS server
WSUS uses IIS to automatically update most client computers to the WSUS-compatible
Automatic Updates. To accomplish this, WSUS Setup creates a virtual directory named
Selfupdate, under the Web site running on port 80 of the computer where you install
WSUS. This virtual directory, called the self-update tree, holds the latest WSUS client.
For this reason, you must have a Web site running on port 80, even if you put the WSUS
Web site on a custom port. The Web site on port 80 does not have to be dedicated to
WSUS. In fact, WSUS only uses the site on port 80 to host the self-update tree.
To ensure that the self-update tree is working properly, first make sure there is a Web
site set up on port 80 of the WSUS server. Next, type the following at the command
prompt of the WSUS server:
cscript WSUSInstallationDrive:\program files\microsoft windows server update
services\setup\InstallSelfupdateOnPort80.vbs
If you have WSUS client self-update running on port 80 of the WSUS server, see the next
section.
Check IIS logs on the WSUS Server
Check the IIS logs on the WSUS server. IIS logs are typically located in
%windir%\system32\LogFiles\W3SVC1 for the default Web site. If you copied the
Wutrack.bin file to the \InetPub\wwwroot folder on the WSUS server when you set up
client self-update, you can open the IIS logs and search for Wutrack.bin to attempt to
locate error messages about why self-update is failing. Typical errors might be 404 (file
not found) 401/403 (authentication/access), and 500 (Internal server error). Use IIS Help
to troubleshoot any problems found in the IIS logs.
If you have installed SharePoint on the default Web site in IIS, configure
SharePoint to not interfere with Self-update
If you install Microsoft SharePoint on the same server that is running WSUS, you might
get the following issues:
An "Access denied" message appears when Automatic Updates tries to update itself,
and the latest Automatic Updates will not be running.
92
On the Home page, you a message appears warning you that the SelfUpdate
service is not available.
If client computers are not running the WSUS-compatible version of Automatic Updates,
they will not be able to receive updates through WSUS.
To resolve this issue
1. Grant Anonymous access (Anonymous Auth) to the Default Web site,
ClientWebService and Selfupdate v-roots in IIS.
2. Exclude specific requests from being intercepted by the SharePoint ISAPI DLL
by doing the following:
a. Open the SharePoint Central Administration Site (click Start, point to
Administrative Tools, and then click Sharepoint Central Administration).
b. Click Virtual Server Configuration, and then click Configure Virtual
Server Settings.
c.
Click Default Web Site.
d. Click Virtual Server Management, and then click Define managed paths.
e. In the Add a new pathbox, set the type to excluded path. Under Path, type
the following:
"/iuident.cab"
"/wutrack.bin"
"/clientwebservice"
"/Selfupdate"
Check network connectivity on the WSUS client computer
Check network connectivity on the WSUS client computer. Use Internet Explorer to
determine if self-update files on the WSUS server are accessible to the client computer. If
you perform the following procedure and are prompted to download or open the files, you
have verified network connectivity. It is not necessary to save or open the files. You
cannot self-update Automatic Updates this way. If you do not have access to these files,
troubleshoot network connectivity between the WSUS client computer and the WSUS
server.
To check network connectivity on the WSUS client computer
1. Click Start, and then click Run.
93
2. In the Open box, type iexplore and then press ENTER
3. In the Internet Explorer Address bar, type:
http://WSUSServerName/iuident.cab
where WSUS server name is the name of your WSUS server. Ensure that you are
prompted to download or open Iuident.cab. This verifies network connectivity from the
WSUS client and the availability of the Iuident.cab file on the WSUS server.
4. If there are any boxes prompting you to download or save, click Cancel. In Internet
Explorer Address bar, type:
http://WSUSServerName/selfupdate/AU/x86/osvariable/languagevariable/wuaucomp.cab
where WSUSServerName is the name of your WSUS server and where osvariable is a
variable indicating the operating system of the client computer. The possible variables for
osvariableare NetServer, W2K or XP, and where languagevariable is a variable indicating
the language of the operating system of the client computer. The possible variables for
oslanguage are based on the standard 2- to 4-letter language abbreviations. For example,
here is a URL for a client computer running an English version of Windows XP:
http://WSUSServerName/selfupdate/AU/x86/XP/EN/wuaucomp.cab
Ensure that you are prompted to download or save Wuaucomp.cab. This verifies network
connectivity from the WSUS client and the availability of the Iuident.cab file on the WSUS
server.
If you are prompted to save or download both of these files, see the next section.
Check logs on the SUS client computer
Check the %windir%\windows update.log on the client computer to see if there has been
any activity or any attempts to contact the server. Check the %systemdrive%\program
files\windowsupdate\v4\urllog.dat file on the client computer for cached server pingbacks
if the client computer has not been able to communicate with the server.
These files are hidden by default. Use the following procedure to display hidden files and
folders in Windows Server 2003.
To display hidden files and folders on Windows Server 2003
1. In Control Panel, open Folder Options.
2. On the View tab, under Hidden files and folders, click Show hidden files and
folders.
If you can find no problem with the logs on the WSUS client, see the next section.
94
Manipulate registry settings on the SUS client computer
If all else has failed, you can attempt to manually manipulate registry settings to get the
client computer to self-update to the WSUS client.
To manually manipulate registry settings on the SUS client computer
1. Click Start, and then click Run.
2. In the Open box, type regedit and then click OK.
3. In Registry Editor, navigate to the WindowsUpdate key by expanding the following:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\
If the WindowsUpdate key does not exist, do the following:
4. On the menu, click Edit, point to New, and then click Key.
5. Type WindowsUpdate as the name for the new key.
6. Double-click the WUServer setting, type the URL to your WSUS server, and then press ENTER.
If the WUServer setting does not exist, do the following:
7. Type WUServer as the setting name.
8. Double-click the WUStatusServer setting, type the URL to your WSUS server, and then press
ENTER.
If the WUStatusServer setting does not exist, do the following:
9. Type WUStatusServer as the setting name.
10. Navigate to the following:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate\AU
If the AU key does not exist, do the following:
11. Type AU as the name for the new key.
12. Verify that the UseWUServer setting has a value of 1 (0x1).If it does not, modify it by doubleclicking the setting and then changing the value.
If the UseWUServer setting does not exist, do the following:
13. Type UseWUServer for the setting name.
14. Navigate to the following:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto
Update
95
15. Enable and configure Automatic Updates through Control Panel:
Click Start, click Control Panel, and then double-click Automatic Updates.
16. In the Automatic Updates dialog box, specify download and installation options, and then click
OK. Make sure that Turn off Automatic Updates is not selected.
17. Ensure that the AUState setting has a value of 2 (0x2). If it does not, modify it by double-clicking
and changing the value.
18. If the LastWaitTimeout setting exists, delete it.
19. If the DetectionStartTime setting exists, delete it.
20. At the command prompt, type the following, and then press ENTER to stop the Automatic Updates
service:
net stop wuauserv
21. At the command prompt, type the following, and then press ENTER to restart the Automatic
Updates service:
net start wuauserv
22. Wait approximately 6 to 10 minutes for the self-update to occur.
To force the SUS client computer to check with the WSUS server
Wait approximately one minute, and then refresh the registry. You should now
see the following settings and values:
DetectionStartTime (REG_SZ) YYYY.MM.DD HH.MM.SS. The
DetectionStartTime value is written in local time, but the detection actually
occurs 5 minutes after the time noted.
LastWaitTimeout (REG_SZ) YYYY.MM.DD HH.MM.SS. The
LastWaitTimeout value is written in GMT or Universal Time, and represents
the actual time that detection occurs.
Although these values refer to the time that detection is going to start, the first phase of
detection is the process of checking whether a self-update is necessary. Therefore, these
values actually refer to when self-update from SUS client to the WSUS client should
occur.
If the client software has not self-updated after ten minutes, refresh the \Auto Update
registry key. If the LastWaitTimeout value has changed and is now 24 hours later than
its previous value, that indicates that Automatic Updates was not able to contact the
server URL that you specified in the WUServer value.
96
Computers are not appearing in the correct computer
groups
Client-side targeting is when you use Group Policy or registry settings to move computers
into target groups. For more information about how to set up client-side targeting, see
Deploying Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409. There are a number or
reasons why computers might not appear in groups when you are using client-side
targeting. Use the following information to try to resolve this problem.
Verify that the WSUS console is set to use client-side targeting
By default, the WSUS server is set to use server-side targeting. If you are using clientside targeting, you need to set an option on the WSUS server. For more information
about how to set up client-side targeting, see Deploying Microsoft Windows Server
Update Services at http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
Verify that target computer group names match groups on the WSUS
server
Make sure the name of the target computer group in Group Policy matches the name of
the computer group on the WSUS server. Check the Group Policy object (GPO) or the
registry setting where you enabled client-side targeting. Make sure that there are no
discrepancies between the name of the computer group used in Group Policy and the
name of the group used on the server. If WSUS cannot find a computer group on the
server reported by a client computer, it loads the computer into the Unassigned
Computers group.
Wait an hour for changes to take effect
If you make a change to group membership by using client-side targeting and the client
computer has already contacted the WSUS server, it takes an hour for the server to
change the computer’s group membership. This is because WSUS uses cookies to
manage group membership with client-side targeting and these cookies are set to expire
after one hour.
If you cannot wait an hour, use command-line options to reset the cookie and initiate
detection. For information about how to use command-line options, see Deploying
Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?linkid=41777&clcid=0x409.
97
Additional Resources for Windows
Server Update Services
For more information and support, see the following resources.
Windows Server Update Services
Communities
Microsoft communities are great places to exchange ideas with other users and discuss
common issues. You can read and write messages by using an NNTP-based newsreader
such as Microsoft Outlook Express. You can also use the Web-based newsreader
provided by Microsoft to access all of the newsgroups. To access the WSUS
Communities, go to the following:
Windows Server Update Services Communities Homepage at
http://go.microsoft.com/fwlink/?LinkID=45215
Windows Server Update Services Public Newsgroup at
http://go.microsoft.com/fwlink/?LinkID=42318.
More Documentation
For high-level information about what's new and features of WSUS, see Microsoft
Windows Server Update Services Overview at
http://go.microsoft.com/fwlink/?LinkID=42213.
For step-by-step guidance for getting started, including installing WSUS, setting up a
client computer, and deploying your first set of updates, see Step-by-Step Guide to
Getting Started with Microsoft Windows Server Update Services at
http://go.microsoft.com/fwlink/?LinkID=41774.
For information about planning for, installing, and then configuring WSUS
components and infrastructure, see Deploying Microsoft Windows Server Update
Services at http://go.microsoft.com/fwlink/?linkid=41777.
For information that helps you automate tasks or customize WSUS, see the Microsoft
Windows Server Update Services Software Developer's Kit at
http://go.microsoft.com/fwlink/?LinkID=43099 and Windows Update Agent Software
Developer's Kit at http://go.microsoft.com/fwlink/?LinkID=43101. Note that the
Windows Update Agent is the Automatic Updates service. Both SDKs contain
98
information about the application programming interface (API), as well as sample
scripts and ready-to-use tools for your WSUS deployment and implementation.