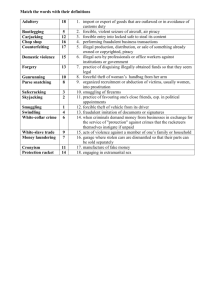
Section 3 – JOINT FORCIBLE ENTRY
advertisement

Action Officer-Level Draft for Collaboration Purposes Only Joint Forcible Entry Operations Joint Integrating Concept Version .92A3 Legend: Yellow: Changes from GO/FO review Blue: Senior Concept Developer review 15 September 2004 Action Officer-Level Draft for Collaboration Purposes Only Action Officer-Level Draft for Collaboration Purposes Only Table of Contents 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 EXECUTIVE SUMMARY 3 Section 1 -- Introduction and Scope 6 1.A 1.B Introduction Scope Section 2 – Description of the Military Problem 2.A Operational Environment 2.A.1 Providing Access 2.A.2 Gaining Operational Access 2.A.3 Forcible Entry 2.B Effects-Based Operations 2.C Operational Art Section 3 – Joint Forcible Entry Operations – The Concept 3.A 3.B Synopsis of the Central Idea Preparing for Joint Forcible Entry Operations 3.B.1 Create organizations and processes 3.B.2 Develop joint leaders for joint forcible entry operations 3.B.3 Train under the right conditions as a cohesive joint force 3.B.4 Shape, develop and maintain infrastructure and resources 3.C Principles of joint forcible entry operations 3.C.1 Start with the end in mind 3.C.2 Gain and maintain Access 3.C.3 Shape the operational battlespace 3.C.4 Establish persistent intelligence, surveillance and reconnaissance profile 3.C.5 Overwhelm and overmatch the adversary in order to achieve end state 3.C.6 Mitigate risk 3.C.7 Achieve desired effects 3.C.8 Achieve decisive conclusions 3.C.9 Provide focused sustainment 3.C.10 Protect the force Section 4 – Capabilities 4.A Future Capabilities 4.A.1 Joint command and control Action Officer-Level Draft for Collaboration Purposes Only 6 7 9 9 11 12 13 15 17 20 20 26 26 27 28 28 30 30 31 32 33 33 34 35 36 37 39 40 40 40 Action Officer-Level Draft for Collaboration Purposes Only 44 45 46 47 48 49 50 51 52 53 54 55 4.A.2 Battlespace awareness 4.A.3 Force application 4.A.4 Focused logistics 4.A.5 Protection 4.B Immediate Actions 2 41 42 43 44 44 CONCLUSION 46 Appendix A – Assumptions and Risks 47 Appendix B – Potential Enemy Capabilities – 2015 49 Action Officer-Level Draft for Collaboration Purposes Only 56 EXECUTIVE SUMMARY 57 "…a future force that is defined less by size and more by mobility and swiftness; one 58 that is easier to deploy and sustain; one that relies more heavily on stealth, precision 59 weaponry and information technologies." 3 George W. Bush 60 61 Joint Publication for Forcible Entry Operations (Joint Publication 3-18) defines 62 forcible entry as “seizing and holding of a military lodgment in the face of armed 63 opposition.” This concept envisions joint forcible entry operations in broader terms. The 64 concept includes using future capabilities to establish a single lodgment for follow-on 65 operations; establishing multiple lodgments for larger-scale, extensive campaigns; or 66 forcible entry as a singular operation. The following definition presents the broader 67 aspects of joint forcible entry operations: 68 69 70 71 72 73 Joint Forcible Entry: A joint military operation conducted against armed opposition to gain entry into the territory of an adversary as rapidly as possible in order to enable the conduct of follow-on operations or conduct a singular operation. The operational environment that will confront commanders in 2015 will be 74 challenging. Future adversaries will have learned to apply all of their capabilities and 75 resources to deny U.S. forces the freedom of movement and unencumbered access our 76 forces, for the most part, have enjoyed to date. Our future opponents will take advantage 77 of natural obstacles, will apply force, and will apply diplomatic and cultural pressures on 78 regional governments—all to prevent or significantly diminish U.S. force access. Their 79 intent will be to disrupt, slow or prevent access, thereby setting conditions for their own 80 strategic success. 81 The Regional Combatant Commanders will endeavor in peacetime to provide access 82 within their areas of responsibility. Where access is denied or restricted commanders will 83 need the capability to gain and maintain operational access and conduct forcible entry 84 operations to accomplish assigned tasks. Forcible entry will require well-trained, well- 85 prepared, interdependent joint forces capable of executing on short-notice. These forces 86 will require dynamically tasked, immediately available lift and tailored joint logistics Action Officer-Level Draft for Collaboration Purposes Only 87 support that can operate from strategic or operational distances and can use non- 88 traditional support bases (e.g. Joint Seabase). 89 4 Joint forcible entry operations require appropriate organizations and processes that 90 facilitate forming, deploying and executing on demand. Critically important: Joint 91 forcible entry operations require the development and training of a cadre of joint leaders 92 and organizations. Developing these leaders and employing them during exercises and 93 actual operations will create that cadre. Joint forcible entry operations training under 94 tough, realistic, and stressful conditions will establish and refine organizational processes 95 and procedures required for coherent, joint, distributed tactical actions. 96 97 98 99 100 101 102 103 104 105 106 107 Joint forcible entry operations are guided by the following principles: Start with the end in mind Gain and maintain operational access Shape the operational battlespace Establish persistent intelligence, surveillance and reconnaissance profile Overwhelm and overmatch the adversary in order to achieve end state Mitigate risk Achieve desired effects Achieve decisive conclusions Provide focused sustainment Protect the force 108 109 Joint forcible entry operations capabilities will continue to be required in the future. 110 Therefore, combatant commanders will require a complete menu of joint forcible entry 111 operations capabilities. The size and composition of a future joint forcible entry 112 operations force are dependent upon the mission assigned, how quickly forcible entry is 113 required, operational conditions, constraints, and capabilities of the opposition. 114 115 116 117 This concept is focused on the time horizon just beyond the Future Years’ Defense Plan (FYDP), roughly 2015 and rests upon the following assumptions: Action Officer-Level Draft for Collaboration Purposes Only 118 Assumptions: 119 The global war on terrorism will continue through 2015. 120 The U.S. will require robust joint forcible entry operations capabilities 121 122 through 2015. Potential adversaries will benefit from the ongoing global diffusion and 123 proliferation of anti-access technologies, including long-range, accurate 124 missiles with supporting information architectures, weapons of mass 125 destruction, weapons of mass effects, and inexpensive technologies. 126 A determined adversary with sophisticated anti-access capabilities may 127 initiate preemptive combat operations on the U.S. C-day in an attempt to 128 preempt a U.S. deployment and prevent the introduction of U.S. combat 129 forces into its operational area. 130 Limitations in overseas port, airfield, infrastructure, and overseas logistics 131 hubs will require alternative basing means and alternative means for 132 deployment and sustainment of the force. 133 5 Action Officer-Level Draft for Collaboration Purposes Only 134 6 Section 1 -- INTRODUCTION AND SCOPE 135 136 “We need to change not only the capabilities at our disposal, but also how we think 137 about war. All the high-tech weapons in the world will not transform the US armed 138 forces unless we also transform the way we think, the way we train, the way we 139 exercise and the way we fight.” 140 U.S. Secretary of Defense Donald Rumsfeld, 141 National Defense University, 31 Jan 02 142 143 1.A Introduction. Four strategic conditions will affect joint forcible entry operations 144 in 2015: 145 First, the U.S. will continue to have global interests and remain engaged with a 146 variety of regional players. The U.S. will continue to develop and nurture 147 alliances and security cooperation agreements that may provide access, but in 148 many cases we will still have to fight for the operational access essential for joint 149 forcible entry operations. 150 151 152 Second, potential adversaries will have access to the global commercial industrial base and many of the same technologies as the U.S. military. Third, potential adversaries will adapt as our capabilities evolve. Future 153 adversaries will look for niche capabilities and employ asymmetric methods to 154 offset U.S. strengths. They will seek to intimidate allies and friendly nations from 155 supporting American military operations. Potential adversaries will continue to 156 operate and acquire new modern surveillance systems and advanced cruise 157 missiles, ballistic missiles and air defense systems. They may possess 158 sophisticated mines and weapons of mass destruction to deter, preempt, delay or 159 defeat U.S. power projection operations as noted in the 2001 Quadrennial Defense 160 Review. These sophisticated anti-access capabilities will be used aggressively in 161 the effort to deny the United States access to regions where its interests are 162 threatened. Action Officer-Level Draft for Collaboration Purposes Only 163 7 Fourth, the U.S. cannot always predict where it may have to conduct a forcible 164 entry, the type of opponent U.S forces will face or the coalition with which we 165 will fight. Forcible entry could take place on the littorals, well inland, or in some 166 combination. 167 These strategic conditions mandate that the United States maintain a credible joint 168 forcible entry operations capability to enter when, where, and how it is needed. Joint 169 forcible entry operations capabilities will provide the future combatant commander with 170 the options he needs, when he needs them. Joint forcible entry operations may be used to 171 establish a lodgment to enable follow-on military operations. Simultaneous joint forcible 172 entry operations may be used to establish a set of distributed lodgments to set the 173 conditions to support larger-scale, extensive campaigns. Joint forcible entry operations 174 may also be executed as a single operation. Each of these situations will present future 175 joint commanders with complex and distinct operational challenges. 176 Joint Publication 3-18 defines forcible entry as the “seizing and holding of a military 177 lodgment in the face of armed opposition.” This definition is too restrictive. It does not 178 describe the full set of forcible entry cases. The definition below provides a more 179 descriptive treatment of the complex nature of joint forcible entry operations. 180 181 182 183 184 Joint Forcible Entry: A joint military operation conducted against armed opposition to gain entry into the territory of an adversary as rapidly as possible in order to enable the conduct of follow-on operations or conduct a singular operation. 185 186 1.B Scope. Herein we focus on joint forcible entry operations against a high-end 187 regional competitor possessing significant military capabilities. No set blueprint for joint 188 forcible entry operations exists. Each joint forcible entry operation is unique, driven by 189 discrete variables and specific situations. Each joint forcible entry operation will be 190 conducted against different opponents, in different geo-political environments, with 191 different coalitions, and for different purposes. Regardless, this joint forcible entry 192 concept presents a set of principles that future joint force commanders can apply to the Action Officer-Level Draft for Collaboration Purposes Only 193 specific case he faces. The paper will also identify the joint operational capabilities 194 essential to execute joint forcible entry operations. 195 8 Action Officer-Level Draft for Collaboration Purposes Only 196 9 Section 2 – DESCRIPTION OF THE MILITARY PROBLEM 197 198 “Future adversaries are seeking capabilities to render ineffective much of the 199 current U.S. military’s ability to project military power overseas…New approaches for 200 projecting power are needed to meet these threats…conducting distributed operations; 201 reducing the dependence of U.S. forces on major air and sea ports for insertion; 202 increasing U.S. advantages in stealth, standoff, hypersonic, and network attacks…” 203 will be required. 204 U.S. Deputy Secretary of Defense Paul Wolfowitz, Prepared Statement for the Senate 205 Armed Services Committee Hearing on Military Transformation, 9 April 2002. 206 207 2.A The operational environment. Countering an adversary’s anti-access and area 208 denial efforts presents the Regional Combatant Commander with a difficult military 209 challenge. Future adversaries will take advantage of natural or geographic obstacles, 210 employ both overt and covert actions, and use complex defense capabilities to deny 211 access or defend against direct Joint or multinational force action. The most complex 212 joint forcible entry operations challenge occurs when all are combined. 213 Distance or geographic obstacles may prevent or inhibit access. Political conditions 214 or actions can also limit access. Adversaries will attempt to shape the regional 215 battlespace in terms of alliances in order to threaten or to prevent our access in a region. 216 Most joint forcible entry operations will occur far from our shores. The enemy may 217 position forces to defend key joint forcible entry operations’ objectives both well inland 218 and along the littorals. This combination of issues presents a complex problem to the 219 joint forcible entry operations commander. Future adversaries will use distance in 220 conjunction with advances in their intelligence, surveillance and reconnaissance 221 capabilities to increase their warning and reaction time. They will use knowledge of 222 tactical lift limitations in an attempt to restrict U.S. and coalition maneuver. Adversaries 223 will most likely seek to offset our intelligence, surveillance and reconnaissance as well as 224 our precision munitions by embedding their forces within urban areas. They will seek to 225 conceal themselves and their assets in complex and difficult terrain. Adversaries may 226 operate in mountainous regions, in caves, in the desert or anywhere else where geography Action Officer-Level Draft for Collaboration Purposes Only 10 227 becomes their ally. Future adversaries may blend in with the indigenous population to 228 further complicate access and joint forcible entry operations efforts. They will combine 229 distance, demographics and geography to their advantage. 230 Attempts to impede joint forcible entry operations may involve overt as well as covert 231 and clandestine enemy actions. Overt efforts to oppose joint forcible entry operations 232 may range from diplomatic or cultural pressure on regional governments to the use of 233 theater or tactical missiles, offensive, defensive, and protective maritime mining, 234 terrorism, asymmetric warfare, or the threat or actual use of weapons of mass destruction 235 or mass effect. Adversaries will use the full range of their military capabilities to directly 236 attack or they may employ hit and hide tactics to prevent or slow the entry of our forces. 237 Our adversaries are adaptable. They have learned lessons from past operations and 238 will further evolve as they learn from future operations. Adversaries will not wait for the 239 U.S. to establish lodgments and to conduct a massive buildup before initiating action. 240 Future adversaries may possess robust intelligence, surveillance, and reconnaissance 241 systems that can be used for targeting and for combat assessment. They may combine 242 well-developed cruise and ballistic missile capabilities to attack in-theater bases and 243 staging areas. Future adversaries will likely employ highly integrated air defense systems 244 to protect their offensive capabilities and infrastructure. Additionally, enemy maritime 245 capabilities, including mines and subsurface assets, may be used to deny U.S. and 246 coalition forces access. Expect future adversaries to use all necessary means to degrade, 247 disrupt or deny U.S. use of space-based intelligence, surveillance, and reconnaissance 248 systems. Combinations of these actions will be used to thwart U.S. attempts to achieve 249 military objectives. Potential enemy capabilities in 2015 are addressed further in 250 Appendix B. 251 Covert and clandestine operations include actions the adversary will employ that can 252 be concealed or allow plausible denial.1 These actions may include the use of special 253 operations forces, agents, provocateurs, and surrogates to pressure regional governments 254 or directly attack U.S. or coalition forces or bases in theater, en route or at home. The 255 local populations may even be used to disrupt or deny U.S. and coalition forces freedom 1 Joint Publication 1-02, 12 April 2001. Action Officer-Level Draft for Collaboration Purposes Only 11 256 of action. Such actions may include the use of labor unions, religious gatherings or 257 student rallies in the joint forcible entry operations area of operations. Covert actions 258 may include cyberspace attacks as part of information operations. Covert activities often 259 target the hearts and minds of the local population and attempt to influence U.S. or 260 coalition resolve or world opinion. Through information operations, adversaries may use 261 neutral countries with cultural or religious ties to advance their cause with the local 262 population. Clandestine operations may include the use of spies and deep-planted agents 263 within friendly governments and agencies. These actions may attempt to intimidate or 264 convince the target audience to support our adversary and oppose U.S. forcible entry or 265 the follow-on operations. Whatever the intent, the goal is to elicit local, regional and 266 world support against our interests and actions. 267 Future adversaries may also employ overt, covert, and clandestine actions around 268 bases and ports in the U.S. and during deployment, employment and sustainment 269 operations. These actions, coupled with the problems of distance and geography, present 270 a complex challenge to joint forcible entry operations. 271 Future conflicts will be uncertain at best, and increasingly dangerous. Future 272 commanders have to think of access in terms of three major requirements: initial access 273 provided, operational access that needs to be gained, and operational access that needs to 274 be maintained throughout joint forcible entry operations. 275 2.A.1 Providing access. Long-term access is a result of continuous shaping efforts. 276 Shaping the operational environment involves the Regional Combatant Commanders, 277 Defense Agencies, State Department, potentially the United Nations and other 278 international agencies, alliances and coalition partners. All instruments of government 279 and international action are applied to ensure access. 280 The Regional Combatant Commander conducts cooperative activities with selected 281 allies and friendly nations to support military superiority and coalition effectiveness 282 across the full range of military operations. His actions enhance multi-national 283 interoperability and self-defense capabilities through standardization agreements, 284 armaments cooperation, security assistance, foreign technologies assessment programs, 285 information and personnel exchanges, and multinational training events and exercises. Action Officer-Level Draft for Collaboration Purposes Only 12 286 This set of military shaping efforts attempts to establish habitual relationships between 287 commanders and forces that are critical to providing access as well as gaining operational 288 access or executing the joint forcible entry operations option when required. 289 The U.S. military supports the other instruments of government or international 290 action in attaining long-term strategic aims. Diplomacy is maintained through consistent 291 contact at the Ambassadorial and Envoy level to encourage cooperation and to support 292 regional stability backed by U.S. military capabilities. Diplomacy may support access 293 through contacts between friendly governments that have diplomatic relations with an 294 adversary government. Providing information is a powerful government action. The 295 print and broadcast media afford both the U.S. and foreign governments’ opportunities to 296 inform public opinion. The economic element of government action includes economic 297 aid, grants, loans, trade and other forms of economic action between governments. 298 Economic packages can be promised or withheld as necessary to influence access. 299 Foreign aid signals U.S. resolve and support, targeting the receiving government and 300 population. Foreign trade agreements, including granting or withholding Most Favored 301 Nation status, are powerful government actions. The instruments of government action 302 are most effective when applied in concert with one another collectively. A future 303 concept will describe in detail military actions necessary for providing access. 304 2.A.2 Gaining Operational Access. Despite our best efforts to provide access 305 wherever and whenever it is needed, operational threats and practical realities may still 306 deny the access required for a military operation. A competent adversary will employ 307 anti-access and area denial capabilities to deny forcible entry forces easy access to areas 308 under his control or influence. The anti-access threat begins at our home stations and 309 ports of embarkation and extends globally to the objective area. Area denial capabilities 310 also include information warfare, inclusive of deception and threats to space platforms. 311 In conjunction with these efforts, the adversary may attempt to establish and enforce an 312 operational exclusion zone encompassing areas within his reach. He may target U.S. and 313 coalition forces and their ports of debarkation, lodgments, entry points, staging bases, 314 operating bases, and logistical support systems. Finally, the enemy may seek to coerce or 315 intimidate the U.S. and allies with threats to non-combatants. The adversary orchestrates 316 these multiple and diverse capabilities to create friction and to deny, delay or disrupt Action Officer-Level Draft for Collaboration Purposes Only 317 access. Failing to confront any one of these possible capabilities may adversely impact 318 U.S. and coalition operations. 319 13 To gain operational access in a competent anti-access and area denial environment, 320 the joint force commander employs tailored, interdependent and capabilities-based 321 forces. This force, informed by pervasive knowledge, can be immediately employed 322 using stealth, standoff, speed and precision. Initial actions employed by the commander 323 will shape the battlespace, setting conditions for success. The joint force subjects the 324 enemy to, and overwhelms him by, immediate, effects-based, knowledge-enhanced, 325 precision engagement and rapid maneuver. In this manner the joint force gains access 326 when and where it is needed throughout the geographic and chronological course of the 327 campaign. 328 2.A.3 Forcible entry. With conditions set for the joint force assault, a joint forcible 329 entry operation is tailored to seize and maintain the initiative, maintain operational 330 access, accomplish the mission and achieve end state employing an effects-based 331 approach. The commander’s intent, derived from assigned strategic aims, identifies the 332 required effects. The joint forcible entry operations commander uses accurate and timely 333 information to assess where he is in the operation and if he is still achieving the effects he 334 desires. He adapts, shifting tasks to his subordinates and adjusting priorities as the 335 situation unfolds. Given the operational environment and the mission assigned, forcible 336 entry operations set the conditions for follow-on operations; support a larger-scale, 337 extensive campaign; or are executed as a singular operation. 338 Joint forcible entry operations are not benign actions. We should expect the enemy 339 force to use all of its capabilities to fight the entry forces. The joint forcible entry 340 operations force uses pervasive knowledge to provide as clear a picture as possible of the 341 enemy location and disposition. No enemy “picture” will ever be perfect, but the effect 342 we want to achieve is that we can “observe” every enemy action and even his intent. 343 That picture must be shared and updated in real time among all elements of the joint 344 forcible entry operations force. The commander requires all available knowledge on the 345 area of operations and adversary options, reactions and potential complications. In many 346 cases, pervasive knowledge will lead to predictive analysis and anticipatory action. Our 347 ability to see and understand first enables us to decide and act first. Knowledge will Action Officer-Level Draft for Collaboration Purposes Only 348 never be perfect; uncertainty remains. We must be prepared with less than perfect 349 knowledge, but better real-time relevant knowledge minimizes risk, increases the 350 probability of success and reduces uncertainty. 351 14 The joint forcible entry operations force should also be network-centric. The degree 352 to which force entities are networked will determine the quality of information that is 353 available to various entities and their ability to interact in the information domain. The 354 level of interoperability achieved and the characteristics of command and control 355 processes will determine the extent that information is shared, as well as the nature and 356 quality of the interactions that occur between and among force entities. Taken together, 357 these capabilities and other organizational characteristics will determine the effectiveness 358 of the force, its agility, and the degree to which decisions, plans, action, and entities are 359 synchronized2. Network-centricity provides all involved with joint forcible entry 360 operations immediate information and access to joint maneuver and fires. Additionally, 361 network-centricity enhances the commander’s ability to orchestrate the actions of his 362 joint forcible entry operations force. The different elements within the force can 363 communicate and coordinate their logistical requirements and shift assets to react to 364 planned contingencies or to cover unexpected requirements. The importance of the 365 networked force and the information flow supporting command and control necessitates 366 protecting the network from all threats. 367 Joint forcible entry operations are combat operations supported by the other 368 instruments of national and international action—diplomacy, information and economic. 369 At the strategic level, the scope of providing access includes the full application of all 370 elements of government action. The military is a supporting element. At the operational 371 level, the scope of joint forcible entry operations is such that the military is the supported 372 element of government action. These operations are effects-based in approach and are 373 intended to create the perception by the adversary that they are simultaneous in 374 execution. 375 2 Alberts, David and Hayes, Richard. Power to the Edge Washington, DC: CCRP Publications, June 2003 Action Officer-Level Draft for Collaboration Purposes Only 15 376 2.B Effects-based operations. Effects-based operations are coordinated sets of actions 377 directed at shaping the behavior of friends, foes, and neutrals in peace, crises, and war. 378 Effects-based operations focus “coordinated sets of actions” on objectives defined in 379 terms of human behavior in multiple dimensions and on multiple levels, and measure 380 their success in terms of behavior produced. Effects can occur simultaneously on the 381 tactical, operational, military-strategic, and geo-strategic levels of military operations, in 382 domestic and international political arenas, and in the economic arena as well.3 Effects- 383 based operations encompass the full range of diplomatic, informational, military and 384 economic actions that the U.S. might undertake to shape the behavior of the enemy and 385 attain the assigned strategic aims. 386 Forcible entry forces, tapping the technologies and thinking of network-centric 387 operations, can apply the four key ingredients of successful effects-based operations: 388 options, agility, coordination, and knowledge mobilization. Decision makers tailor 389 actions to produce a useful option to deal with a given situation and employ responsive, 390 networked forces with shared awareness and speed of command. Shared situational 391 awareness and an understanding of command intent facilitate synchronization and 392 coordination of complex actions and effects. Mobilizing knowledge provides timely, 393 relevant support to decision makers at all levels.4 394 Effects-based operations increase the probability of preventing the enemy from 395 interfering with forcible entry forces by focusing on more efficient destruction of the 396 enemy’s decision-making capability and his ability to create coherent actions. Through 397 the execution of overwhelming asymmetrical attacks, the defeat of enemy will be both 398 psychological and physical. To achieve the desired effects, joint force packaging, the 399 blending of packaged joint forces and adapting those forces to specific theater 400 requirements will be required to shape and sustain the entry forces and allow for a more 401 seamless transition to follow-on operations. 402 There are several overall objectives to be achieved in support of joint forcible entry 403 operations: to prevent the enemy from interfering with the forcible entry operation at any 404 point; to overmatch the enemy in all domains when and where the joint commander 3 Smith, Edward A. Effects-based Operations, Applying Network Centric Warfare in Peace, Crisis, and War, Washington, DC: CCRP Publications, November 2002 Action Officer-Level Draft for Collaboration Purposes Only 16 405 directs; to facilitate transition to follow-on operations, if any, as quickly as possible; and 406 to create the sense of simultaneity of actions in the eyes of the enemy. 407 To create these effects, the commander must continuously analyze the operating 408 environment. This analysis will result in a decision as to how to conduct the joint 409 forcible entry operation. Neither simultaneity nor sequentiality of actions is always the 410 “right” approach. It is the balance that must be right and is up to the commander to 411 “dial” the correct blend. 412 Figure 1 that follows illustrates how the commander must set the dial to apply actions and 413 create effects, given the mission he is assigned and the situation he is in. Historical 414 examples can illustrate how the blend between sequential and simultaneous actions 415 results in mission accomplishment. During WWII, OPERATION OVERLORD was 416 conducted at the left end of the meter. OPERATION DESERT STORM, more toward 417 the left center; OPERATION IRAQI FREEDOM, more to the right center. 418 OPERATION JUST CAUSE was executed more towards the far right side of the meter. 419 420 421 Figure 1 How a JFEO Commander achieves effects is situational dependent 422 423 Interagency and multinational action at the operational level of war provides the 424 commander the opportunity to affect the enemy’s warmaking ability to a greater extent 425 than U.S. military action alone. In the application of an effects-based approach to 426 operations, the joint forcible entry commander must be cognizant of effects that occur in 4 Ibid Action Officer-Level Draft for Collaboration Purposes Only 427 three domains: physical, informational and cognitive. How a joint forcible entry 428 operations commander of the future embodies the effects-based operations approach 429 requires operational art. 17 430 431 2.C Operational art. Operational art begins in the mind of the commander and is 432 implemented through his organization. Joint forcible entry operations will, in most cases, 433 be employed in support of or as an element of Major Combat Operations. Therefore, the 434 operational art described in this section is naturally linked to and supports what has been 435 described in the Major Combat Operations concept. While the joint forcible entry 436 commander is cognizant of this linkage, there are specific considerations he must address 437 relative to the unique characteristics of joint forcible entry operations. 438 The joint forcible entry commander must envision the scope of the forcible entry 439 mission within the broader context of the campaign he supports. He must also visualize it 440 in terms of time, space, cyberspace and physical dimensions. The commander must also 441 understand the actual conditions (friendly and enemy, political and military, domestic and 442 international) that dictate the most appropriate action. Finally, the joint forcible entry 443 commander must visualize, describe and direct a clear, coherent plan that expresses the 444 unitary vision of his senior commanders and achieves strategic aims and operational 445 objectives. 446 The joint forcible entry commander determines the best way to conduct joint forcible 447 entry operations anywhere in the world with globally sourced and interdependent forces. 448 He must visualize the physical space in which he will conduct the forcible entry, and then 449 use that space to his advantage to both defeat the adversary’s attempts to deny entry and 450 set conditions for follow-on operations, if any. The joint forcible entry commander 451 continuously adapts as the situation unfolds. 452 The nature and pace of joint forcible entry operations accentuates the requirement for 453 a well-established informational domain. The joint force commander must also be able to 454 communicate information required to maintain international and domestic public support 455 of the operation while simultaneously conducting offensive and deceptive information 456 operations against the adversary. The joint forcible entry commander’s objective in the 457 information domain is to diminish his adversary’s capabilities while retaining and Action Officer-Level Draft for Collaboration Purposes Only 18 458 expanding his own. The commander requires an information system that is flexible, fully 459 networked and secure. Joint forcible entry operations include the ability to employ 460 computer network operations as appropriate when the opportunity warrants. Finally, the 461 joint forcible entry information network provides the commander the means to observe, 462 decide and act faster than the enemy. 463 Actions taken in the physical and information domains create effects in the cognitive 464 domain. The joint forcible entry commander must have a good understanding of what is 465 in the mind of the enemy, as well as the enemy’s capability and will to fight. His 466 Information Operations plan should exploit every capability in order to outwit and 467 outfight the enemy. Integration of Information Operations, and in particular deception 468 operations, is critical throughout the conduct of joint forcible entry operations. When 469 applicable, the commander attempts to impart to the enemy that the joint forcible entry 470 force could strike any place at any time. Execution of the forcible entry not only defeats 471 enemy capabilities but also conveys a sense of futility in the mind of the adversary. The 472 joint forcible entry commander introduces confusion and doubt in the adversary in order 473 to upset the enemy’s ability to command and control his forces. 474 The joint forcible entry operations commander acts through his organizational staff 475 and subordinates. Because of the expeditionary nature of joint forcible entry forces, the 476 organization must be adaptive and capable of collaborative, parallel planning to include 477 planning while enroute to the objective. The challenge to the commander and his staff is 478 to integrate actions at the tactical level while employing forces from across the globe. 479 Fully integrated within the Regional Combatant Command, his organizational structure 480 should encompass agility, robustness, and the capability to self-synchronize. A self- 481 synchronizing force demonstrates clear and consistent understanding of the commander’s 482 intent, high quality information and shared situational awareness, competence at all levels 483 of the force, and mutual trust throughout the organization. 484 The commander, practicing operational art, creates harmony among the previously 485 stated characteristics. That is to say that the plan developed can be executed by the 486 forces and leaders on hand, within the space available, and leveraging all capabilities in 487 place. The force must be imbued with a sense of a mission and have the trust and 488 confidence of the commander to act with initiative, creativity and audacity. If any of Action Officer-Level Draft for Collaboration Purposes Only 489 these components are inadequate, the commander must be adaptive, adjusting either his 490 aims or plans in order to address these deficiencies. 491 19 Action Officer-Level Draft for Collaboration Purposes Only 492 20 Section 3 – JOINT FORCIBLE ENTRY OPERATIONS – THE CONCEPT 493 494 “The idea… is to create a U.S. global military capability where "individuals and 495 units will receive training and experience in joint operations at the strategic, 496 operational and tactical levels…to train as we fight - as a coherently integrated team." 497 U.S. Deputy Secretary of Defense Paul Wolfowitz, 498 Naval War College Graduation, June 20, 2003 499 500 3.A Synopsis of the central idea. Joint forcible entry operations require a tailored 501 combination of forward-based, forward deployed, pre-positioned and CONUS surge 502 forces. These various force postures will enhance the ability to maneuver from 503 operational and strategic distances. Additionally, using an effects-based approach, the 504 joint forcible entry operations force will employ complimentary force multiplying effects 505 that will result from synchronizing Joint, inter-agency, and possibly multinational forces. 506 Joint forcible entry operations take full advantage of forward presence, a mix of basing 507 options, and operational and strategic maneuver in order to gain and maintain access 508 to ensure entry. Joint forcible entry operations employ distributed operations to attack 509 from multiple directions and dimensions throughout the battlespace. The net result 510 will be a coordinated attack to overwhelm the adversary and achieve the desired effects 511 before the adversary has time to react, thus ensuring conditions for follow-on 512 operations or achieving end state for a singular operation. 513 One challenge facing national defense leaders structuring the future force will be to 514 determine the most appropriate and effective mix of forward-based, CONUS-based and 515 forward-presence forces. The advantageous placement of the force will both enhance and 516 be reinforced by our capability to conduct strategic and operational maneuver. For those 517 forces located in forward locations, intra-theater lift assets will support operational 518 maneuver, while CONUS-based and more distant forward-based forces will use inter- 519 theater lift to support strategic maneuver. 520 Regardless of the lift used, the force will require the ability to attack the adversary 521 from multiple directions, using multiple entry points, and multiple dimensions—air, land, 522 sea, space and cyberspace. To be most effective the attack should appear simultaneous to Action Officer-Level Draft for Collaboration Purposes Only 21 523 the adversary, achieve at least tactical surprise, and immediately seize the initiative. With 524 appropriate access gained and maintained, multidirectional, multidimensional and 525 simultaneous entry execution should confound and overwhelm the adversary’s decision- 526 making process and contribute to a successful joint forcible entry operation and the 527 adversary’s defeat. 528 One method for contributing to the aforementioned desired effects is Joint Seabasing. 529 Joint Seabasing represents the ability to rapidly employ networked expeditionary joint 530 forces; contribute to assuring access and entry; project, support and sustain distributed 531 and dispersed offensive and defensive combat power from the sea; and significantly 532 reduce reliance on land bases within the Joint Operating Area. This capability mitigates 533 risks associated with joint forcible entry operations. Joint Seabasing is an emerging 534 concept consisting of a system of systems, ships, forces, offensive and defensive 535 weapons, aircraft, communications and logistics. Joint Seabasing, various fixed facilities, 536 rapid expeditionary basing, and CONUS-bases, provide the potential for forward 537 deterrence and provide national leaders and joint force commanders the set of options 538 required. This set provides the joint forcible entry commander with operational reach for 539 a credible and rapid response for forcible entry operations in an anti-access environment. 540 The set also poses multiple problems an adversary must be prepared to solve 541 simultaneously. Access, or the adversary’s attempt to deny access, is central when planning for 542 543 military operations. The following diagram conceptually frames the tasks that create the 544 framework for successful joint forcible entry operations.5 Figure 2 illustrates that 545 shaping operations are continuously ongoing. Shaping may take form during peacetime 546 operations in the diplomatic, information, economic, or military arenas. One of the 547 important objectives of peacetime shaping is to provide access in the geographic area. 548 Shaping will not only be prevalent during forward presence but during operations to gain 549 and maintain operational access. The extent to which forward presence is required will 550 be situationally dependent. Events might transpire that a significant forward presence 551 will be established to deter aggression or to provide access or the reverse might be true. 5 The tasks, and the capabilities that enable them, will be the focus of rigorous experimentation directed by DepSecDef memorandum dtd 12 Dec 03, Forcible Entry PDM II Study, and JROCM 199-03 dtd 20 Oct 03. Action Officer-Level Draft for Collaboration Purposes Only 22 552 In almost every case, however, if access is denied and the need for forcible entry 553 operations arises, forward presence may be used as a springboard to gain and maintain 554 operational access. Operational access sets conditions for opening entry points and 555 assault by establishing the necessary control of air, sea, space and cyberspace required to 556 deliver forcible entry forces. Continued access will be required to receive follow-on 557 forces or transition to follow-on operations should the need require. Sustainment will be 558 paramount throughout the entire operation. Although an apparent sequential series of 559 actions was just described, ensuring access and executing forcible entry tasks may be 560 simultaneously executed depending on the range, depth and persistent nature of the anti- 561 access capabilities of our adversary. This construct is illustrated by overlapping tasks. 562 563 564 565 566 567 568 569 570 Figure 2 Joint Forcible Entry Operations Tasks in context with access 571 572 The following series of diagrams depict the three types of joint forcible entry 573 operations treated in this concept. Each of the diagrams suggests a number of actions to 574 be accomplished. These actions are guided by the enduring principles described in 575 section 3.C. The actions are non-prescriptive in nature. There is no standardized solution 576 to meet all contingencies. These tasks are not necessarily sequential; they may be 577 executed near simultaneously to gain surprise and momentum, reduce risk, and achieve 578 success. The commander should develop his specific plan of “how to” conduct joint 579 forcible entry operations using the principles applicable to his unique situation. 580 Figure 3 depicts using joint forcible entry operations to establish a single lodgment to 581 support follow-on military action. A single lodgment joint forcible entry operation may 582 begin by establishing forward presence or by repositioning deployed expeditionary Action Officer-Level Draft for Collaboration Purposes Only 583 assets. Either the entire or selected portions of the Joint Task Force for forcible entry 584 may move forward. In some cases, a headquarters element could be formed forward to 585 establish communications links and reachback capabilities. 586 23 The joint forcible entry operations force will prepare, or shape, the operational area. 587 Preparing the operational area may include insertion of special operations forces or other 588 agency assets. The special operations forces or inter-agency assets provide intelligence, 589 surveillance and reconnaissance capabilities and may conduct direct action operations. 590 The enhanced intelligence capabilities provide improved, accurate and timely information 591 that helps defeat anti-access strategies and helps preposition lift and sustainment. The 592 Joint Force Commander will gain and maintain operational access to the battlespace he 593 deems necessary for joint forcible entry operations and supporting operations. Setting 594 conditions for joint forcible entry operations and supporting operations requires close 595 coordination. The entry force may open several entry points. Some will be used to 596 approach objective areas from multiple directions; others may be used for deception. 597 Forcible entry point lodgments allow a smooth transition without operational pause to 598 follow-on force arrival. Follow-on operations may commence and the lodgment 599 expanded to support sustainment of the follow-on operations. Action Officer-Level Draft for Collaboration Purposes Only 24 600 601 602 603 Figure 3 Joint Forcible Entry Operations to Establish a Single Lodgment for Follow-on Operations Figure 4 depicts joint forcible entry operations using multiple entry points to establish 604 multiple, interconnected and distributed lodgments to support a larger-scale extensive 605 campaign. Most of the actions previously discussed for establishing a single lodgment 606 are also applicable for multiple lodgments. Multiple entry points will also be required for 607 this operation to support moving forces to different objectives or deceptions. Receiving 608 follow-on forces for larger-scale, extensive campaigns require close coordination. 609 Establishing and sustaining the joint forcible entry operation and the follow-on forces 610 requires agility, coordination and strategic and operational lift that does not necessarily 611 rely upon fixed air and sea ports. By conducting forcible entry into remote coastal or 612 austere landing areas, we force our adversary to react to the joint forcible entry operation 613 where he does not expect it. This reaction provides the forcible entry force a measure of 614 protection and time to further develop the situation as the enemy reacts. Action Officer-Level Draft for Collaboration Purposes Only 25 615 616 617 Figure 4 Joint Forcible Entry Operations to Establish Multiple Lodgments for Large Scale Follow-on Campaign 618 The multiple lodgment operation is the most complex and challenging scenario for 619 forcible operations. Joint forcible entry operations to establish multiple lodgments may 620 require different joint forcible entry forces operating in close proximity to each other and 621 requiring well-coordinated execution. Establishing multiple lodgments through joint 622 forcible entry operations could require a single joint forcible entry force, or multiple joint 623 forcible entry forces under the overall command and control of single joint forcible entry 624 operations commander. 625 Figure 5 presents a joint forcible entry operation situation where a lodgment is not 626 established for follow-on operations. This type of joint forcible entry operation uses a 627 force that directly attacks the objective or distributed objectives as a singular mission. 628 Examples of singular operations where joint forcible entry operations may be required 629 range from assaults, raids or evacuation operations up to large-scale operations. Action Officer-Level Draft for Collaboration Purposes Only 26 630 631 Figure 5 Joint Forcible Entry Operations as a singular operation 632 633 3.B Preparing for joint forcible entry operations. The U.S. may no longer have a 634 “grace” period while transitioning to war. In this case, there is no “time-out” to catch up 635 and absolutely no reprieve from being strategically and operationally prepared. The U.S. 636 prepares by creating adaptive organizations and processes, emphasizing an expeditionary 637 posture and rapid surge capabilities, and developing and educating its leaders. Joint 638 training should be conducted under realistic conditions using collaborative planning and 639 continuous assessment. Preparing for success requires adaptability, flexibility, creativity, 640 and audacity. 641 642 3.B.1 Create organizations and processes. A near-immediate response to 643 developing crises enhances the probability of success by friendly forces. Little time may 644 be available to stand up a traditional Joint Task Force, identify forces, deploy to the area 645 of concern, and conduct reception, staging, onward movement, and integration as is the Action Officer-Level Draft for Collaboration Purposes Only 27 646 current practice. The dynamic nature of joint forcible entry operations may require the 647 creation of at least one standing Joint Task Force Headquarters with assigned component 648 commands specializing in joint forcible entry operations. Commanders could then assign 649 rotational forces that would be available for immediate response. This headquarters and 650 subordinate forces will refine the concept as well as train and exercise together to master 651 expertise in the joint forcible entry operations mission and be ready to respond 652 immediately. Such a standing force allows rapid, dynamic, and aggressive response 653 diminishing the adversary’s advantage of anticipating our actions. Additionally, the 654 standing Joint Task Force Headquarters will benefit from deliberate planning and 655 repetitive, focused training. 656 657 3.B.2 Develop joint leaders for joint forcible entry operations. By their nature 658 joint forcible entry operations are distributed and decentralized. Although centralization 659 may accommodate some aspects of joint military activity, the reliance on decentralized 660 decision-making and execution expands in importance during joint forcible entry 661 operations. The dynamic nature of a joint forcible entry operation demands leaders who 662 can anticipate and adapt; are agile, flexible, and audacious. For example, in the initial 663 period of a forcible entry operation, organic ground fire support assets are limited. 664 Ground forces will be extremely dependent on the joint force for fire support. Trained 665 leaders will enhance the effectiveness of joint forcible entry operations. 666 Future joint forcible entry operations leaders will require not only mastery in their 667 own specialization in joint forcible entry operations, but also require an in-depth 668 understanding of the capabilities and limitations of joint, inter-agency and coalition 669 partners. These leaders must be able to think on the move, adapting to an ever-changing 670 environment. At all levels, leaders must be skilled as communicators, flexible thinkers, 671 and in empowering others during the ebb and flow of joint forcible entry operations. 672 Working together as a team, well in advance of a crisis requiring joint forcible entry 673 operations, enhances teamwork and mitigates the stress of execution under fire. The 674 future joint forcible entry operations force will practice adaptive command and control 675 and resourceful teamwork under realistic conditions so they are ready when called upon. 676 Action Officer-Level Draft for Collaboration Purposes Only 677 28 3.B.3 Train under the right conditions as a cohesive joint force. Joint forcible 678 entry operations are “tip of the spear” operations. Joint forcible entry forces, more than 679 any other force, will have to transition from peacetime to combat quickly. Joint forcible 680 entry operations training strengthens joint, interagency, and multi-national coordination 681 and prepares the force for the unique and demanding aspects of their operations. 682 Training involving the U.S. military, the interagency community, and multinational 683 partners expands our capabilities to conduct forcible entry. Training under realistic 684 conditions contributes to building trust, confidence, and shared understanding among the 685 joint forcible entry operations partners who will execute joint forcible entry operations. 686 Training should be geared to stimulate synergy, adaptability, and opportunism. These 687 are critical attributes for leaders and forces charged with the joint forcible entry 688 operations mission. Training forces to accept and cope with uncertainty, risk, change, 689 friction, chaos, and the fog of war is likewise critical to joint forcible entry operations. 690 This training will enhance the development of individuals and organizations that 691 intuitively improvise and adapt to joint forcible entry operations requirements. 692 693 3.B.4 Shape, develop and maintain infrastructure and resources. Through global 694 engagement the U.S. will continue to develop long term conditions and capabilities that 695 provide the foundation for access. Coherent involvement of the interagency and 696 multinational communities creates powerful partnerships. Interagency and multinational 697 support is essential to acquiring basing rights, developing airports and seaports of 698 debarkation, and establishing a network of contingency bases tailored to specific mission 699 needs (i.e., aerial strike, air assault, fixed-wing air-landed air assault, etc.). Fielding 700 assured access capabilities, advanced force delivery means, and reducing lift 701 requirements through tailored, capabilities-based modular force packages are enablers 702 that provide joint forcible entry operations forces speedy access to objective areas. 703 The U.S. and coalition partners will employ various means to ensure the use of 704 needed lines of communication and infrastructure. Forward deployment and presence of 705 U.S. forces reassure friends and allies and tend to dissuade potential adversaries. These 706 forward-deployed forces are likely to be the first responders to counter anti-access and 707 area denial strategies. Forward presence capabilities depend on establishing long-term Action Officer-Level Draft for Collaboration Purposes Only 29 708 basing rights within the Regional Combatant Commanders areas of responsibility. These 709 bases may include a combination of fixed, long-term, continuously available facilities 710 and bases that are available on an as-needed basis joint sea basing or joint 711 expeditionary land basing, for example. 712 Providing the kind of access required by joint forcible entry operations forces 713 necessitates rapid maneuver capabilities. Key to providing access is the development of 714 assured access and lift capabilities that enable strategic and operational maneuver. This 715 lift must also provide the joint forcible entry force the capability to go where the enemy is 716 not; go where the joint forcible entry commander wants without relying on the 717 predictable use of air and sea ports.6 Additionally, creating tailorable, modular forces 718 that require little or no reception, staging, onward movement, and integration provides 719 the foundation for conducting joint forcible entry operations when required. These lift 720 and tailorable, modular force packages must operate from the existing fixed bases, sea 721 bases and austere bases. The tailorable, modular force packages assembled to execute 722 joint forcible entry operations must seamlessly and rapidly reinforce, reconstitute and or 723 reconfigure as the mission progresses and the situation changes. 724 The joint forcible entry forces will be expeditionary, more deployable, more 725 maneuverable and survivable. These fast, agile forces will reduce logistics demand by 726 displacing mass with tempo and responsiveness. A joint logistics system that employs 727 speed, accuracy and agility, combines Service capabilities, and creates a small footprint 728 supports distributed operations. Rapid integration of technological advances in 729 alternative fuels, multi-power systems and materials sciences (composites, etc.) will 730 provide the next generation of smaller, lighter, faster and less energy consuming 731 platforms. These new weapon systems should additionally offer increased precision, 732 effectiveness, firepower and reliability further reducing required lift. Better intelligence 733 will help meet logistics requirements, especially for common bulk items such as water 734 and fuel, in the operations area reducing the need to ship from CONUS or from 735 intermediate supply bases. 736 6 Lift capabilities will be developed through experimentation process Action Officer-Level Draft for Collaboration Purposes Only 737 30 3.C Principles for joint forcible entry operations. Figures 3-5 depicted the general 738 shape of forcible entry operations. While described in sequence for clarity’s sake, many 739 of the actions are executed simultaneously. A forcible entry operation begins with the 740 establishment of a forward presence and the conduct of shaping operations—overt, 741 covert, and clandestine. When directed, the joint force gains operational access and 742 opens multiple entry points — some for actual use, others possibly for deception 743 purposes. Access is maintained and entry points are kept open as long as they are needed 744 to conduct and sustain forcible entry operations or introduce follow-on forces and their 745 sustainment. 746 While every joint forcible entry operation will be different, the following principles 747 attempt to capture what will be common to some degree in every joint forcible entry 748 operation. They provide a set of tools that commanders may use to help guide their 749 thoughts. Not every principle is “new.” Most are evolutionary applications of new tools 750 or methods to classic principles of military art. Joint force commanders use these 751 principles when planning, preparing and executing joint forcible entry operations tasks. 752 753 754 755 756 757 758 759 760 761 762 Start with the end in mind Gain and maintain operational access Shape the operational battlespace Establish persistent intelligence, surveillance and reconnaissance profile Overwhelm and overmatch the adversary in order to achieve end state Mitigate risk Achieve desired effects Achieve decisive conclusions Provide focused sustainment Protect the force 763 764 3.C.1 Start with the end in mind 765 766 Determine the final purpose of the forcible entry 767 Derive from that purpose the desired effects in terms of: 768 - Task organization 769 - Courses of action 770 - Distributed marshalling and delivery plans Action Officer-Level Draft for Collaboration Purposes Only 771 The joint forcible entry commander begins by determining the final purpose of the 772 forcible entry, either to support follow-on operations or as a singular operation. From 773 that purpose the commander develops operational objectives that translate into desired 774 effects. He then crafts the course of action. The distributed marshalling and delivery 775 plan supports final preparations to maneuver the forces to the objective area. All 776 supporting actions focus on the final purpose. 777 31 The joint forcible entry commander must ensure he clearly communicates the final 778 purpose of the mission to his subordinate commanders to ensure singular focus. The 779 actions of the entire joint forcible entry force should be intent on achieving that purpose. 780 781 3.C.2 Gain and maintain operational access 782 783 784 Establish necessary control of air, sea, space and cyberspace required to gain operational access 785 Thwart enemy efforts to establish operational exclusion zones 786 Overwhelm the enemy through right-timed employment of rapid maneuver 787 and precision engagement capabilities 788 Collaborate with Joint Inter-Agency Coordination Group 789 Use immediately employable forces to conduct operations that neutralize 790 competent anti-access capabilities when and where freedom of movement and 791 maneuver is needed to set conditions for direct delivery, sustainment and 792 support of distributed forcible entry forces 793 Use stealth, stand-off, speed, precision, and pervasive knowledge to force our 794 way through the anti-access exclusion zone and defeat the adversary’s area 795 denial forces 796 Gaining operational access is a condition upon which the conduct of forcible entry 797 operations depends. It includes continued application of all elements of government 798 power. These activities are coordinated with the Joint Inter-Agency Coordination Group 799 (JIACG) to ensure synchronization with the planning staff of the commander. In most 800 cases, future adversaries will defend centers of gravity, critical vulnerabilities, and their 801 multi-dimensional, multi-directional approaches with competent anti-access capabilities. Action Officer-Level Draft for Collaboration Purposes Only 32 802 Joint forcible entry operations depend upon the ability to move through the battlespace in 803 order to employ distributed operations and attack from multiple directions and 804 dimensions. Even more critical, most of the capabilities upon which entry forces depend 805 also require the ability to move or maneuver through the battlespace to accomplish 806 interdependent tasks. The joint force will knock down anti-access threats and forces 807 setting conditions as directed. The opening of multiple entry points and lodgments can 808 continue to expand access into the battlespace as required. A multidimensional joint 809 interdependency exists between providing, gaining, and maintaining access. 810 811 3.C.3 Shape the operational battlespace 812 813 814 815 Create a networked, integrated force that includes intelligence, strike and sustainment forces with robust command and control 816 Integrate inter-agency and multi-national capabilities during planning and operations 817 Exploit the capabilities provided by Special Operations Forces 818 Employ Information Operations assets to shape the battlespace environment 819 Maximize the use of all intelligence assets 820 Shaping actions are ubiquitous. Shaping occurs throughout joint forcible entry 821 operations ─ from forward presence through transition to follow-on operations. The 822 commander must be cognizant of the shaping efforts that have occurred in attempts to 823 provide access, but in preparing for forcible entry his focus will be on creating a 824 networked, integrated force to execute shaping actions that enable gaining and 825 maintaining access. These shaping actions are designed to set the conditions necessary 826 for successful forcible entry. Shaping actions in this context also pertain to actions 827 required to open entry points and sustain the force. 828 Commanders prepare, or shape the operational battlespace through detailed 829 integration of all assets at their disposal. The commander must draw critical information 830 from multi-national and interagency sources. Human intelligence in conjunction with 831 other intelligence assets, Special Operations Forces and Information Operations provide Action Officer-Level Draft for Collaboration Purposes Only 33 832 capabilities that must be employed early and continuously to fully prepare the operational 833 battlespace and set conditions for operational and sustainment forces. 834 835 3.C.4 Establish persistent intelligence, surveillance and reconnaissance profile 836 837 Focus on the commander’s critical times, places and decisions 838 Use intelligence, surveillance and reconnaissance products to support commander’s decisions from start to finish 839 840 The speed, precision and associated high risk of joint forcible entry operations 841 requires the joint forcible entry commander to have superior intelligence, surveillance 842 and reconnaissance support. The commander applies information from all available 843 sources during critical times and at critical locations to make informed, timely decisions. 844 The establishment of a persistent intelligence, surveillance and reconnaissance profile 845 assists in setting the conditions for success in all phases of forcible entry and follow-on 846 operations. 847 848 3.C.5 Overwhelm and overmatch the adversary in order to achieve end state 849 850 Gain pervasive knowledge that allows the Joint Forcible Entry Operations 851 Commander the ability to see and understand first, enabling him to decide and 852 act quicker than the adversary 853 854 Create multiple dilemmas for the adversary: be audacious, tough, fast and strong 855 Conduct asynchronous or patternless operations 856 Employ tactical deception and surprise 857 Attack from multiple directions and dimensions; move forces swiftly with 858 859 stealth and lethality 860 861 Use multiple entry points and routes; move with rapidity to the objective area if a lodgment is established Maximize the effects of information and deception operations Action Officer-Level Draft for Collaboration Purposes Only 34 862 The joint forcible entry operations force is most effective when utilizing the full 863 capabilities of our strategic and operational lift to support multi-directional approaches. 864 Additionally, effectiveness significantly increases by employing the full spectrum of U.S. 865 military and interagency capabilities, including information and other domains. 866 Attacking the enemy where he least expects it implies knowing where the enemy is 867 located, what his capabilities are, and what his options are. By attacking the enemy 868 where he least expects it, the joint forcible entry operations commander adversely affects 869 the adversary’s ability to observe, orient, decide and act. The picture our operation 870 should paint in the enemy’s mind is an asynchronous one. While our operations must 871 retain unity of purpose and coherency of action, our unity and coherency should not be 872 recognizable from the enemy’s perspective. To him, we should be “patternless,” thus 873 diminishing his ability to react effectively. These adverse effects can be manifested via 874 combinations of surprise, seizing the initiative, psychological and disruptive shock and 875 information operations. 876 Joint forcible entry forces will employ lift to attack and maneuver from operational 877 and strategic distances using multiple entry points and approaches to overwhelm and 878 confound the adversary. Our advantages in vertical lift, stealth and lethality will be 879 maximized to envelop and attack the adversary from multiple directions further adding to 880 his confusion and defensive dilemma. 881 Joint forcible entry operations forces must be bold and audacious in accomplishing 882 their tasks. Future joint forcible entry leaders must develop the strength of character and 883 conviction to guide their actions. These leaders mitigate risk and take action based on a 884 thorough knowledge of the operating environment. Paramount is the support of the 885 higher-level military commanders to accept and defend decisions made in the heat of 886 battle. 887 888 3.C.6 Mitigate risk 889 890 891 Conduct a detailed risk assessment to identify high-risk, high-value assets and single points of failure Action Officer-Level Draft for Collaboration Purposes Only 892 893 894 Use intelligence, surveillance and reconnaissance products to detect, assess, and warn of impending actions of the adversary 895 Conduct counter reconnaissance, surveillance and target acquisition operations 896 Retain operational and tactical flexibility to react to the unexpected 897 Develop and rehearse a detailed, collaborative and effects-based operational 898 899 plan 900 901 35 Take action against enemy anti-access capabilities to ensure success of joint forcible entry operations Risk mitigation is relevant to all operations but is critical for joint forcible entry 902 operations given the nature of these missions and the uncertainty of the military 903 environment. The distances from which the force is delivered, supported and sustained 904 constrain forced entry operations. Planning for these constraints must be taken into 905 account to mitigate the risk. Maintaining persistent intelligence, surveillance and 906 reconnaissance will establish a common picture of the operational area throughout the 907 joint forcible entry operations force. At the same time, the adversary’s reconnaissance, 908 surveillance and target acquisition capabilities should be significantly impaired. A 909 common picture will enhance the force’s capability to see and hit the enemy, as well as 910 enable the force to see and maneuver from impending danger. Furthermore, dynamic 911 tasking for intelligence, surveillance and reconnaissance and protection assets should be 912 established prior to execution. 913 914 3.C.7 Achieve desired effects 915 916 Articulate an effects-based commander’s intent clearly 917 Use current operational net assessment to facilitate effects-based operations 918 Create and exploit favorable asymmetries; Fight with overmatching power in 919 all domains 920 Empower tactical forces to act decisively on the commander’s intent 921 Establish dynamic tasking of strike assets 922 Identify then disrupt, delay, destroy and disorient the enemy exclusion zone Action Officer-Level Draft for Collaboration Purposes Only 923 924 925 926 Use intelligence, surveillance and reconnaissance products to determine whether the desired effects are achieved Create simultaneity of effects as viewed from the enemy’s perspective Joint forcible entry operations require the right force with the right capabilities at the 927 right time. The force must be tailored so that it is lethal, yet properly sized such that it 928 can be delivered and sustained. Properly identified and allocated forces that habitually 929 train and exercise together as a team will directly enhance effectiveness. 930 36 The Regional Combatant Commander communicates the desired effects through his 931 intent. Once the Regional Combatant Commander defines and communicates the 932 parameters of the mission, the joint forcible entry operations commander plans and 933 executes within those parameters. Empowered by commander’s intent and in receipt of a 934 timely common operational picture, subordinate joint forcible entry operations 935 commanders will be able to visualize how well the force is achieving the desired effects 936 or to adapt as necessary to ensure the effects are achieved. 937 938 3.C.8 Achieve decisive conclusions 939 940 Align operational objectives with strategic objectives 941 Articulate goals and fight until the end-state is achieved 942 Use intelligence, surveillance and reconnaissance products to determine when 943 the final purpose is achieved 944 Plan for smooth transition to future operations 945 Seamlessly and rapidly reinforce, reconstitute or reconfigure for follow-on 946 947 948 operations as required Employ rapid battlefield assessment capability The joint forcible entry operations commander focuses on the desired effects as its 949 end-state. These effects dictate the duration required to accomplish the objectives. The 950 joint forcible entry operations commander tenaciously sustains continuous pressure for as 951 long as it takes. Prudent planning bounds the mission and articulates the commander’s 952 objectives. The joint forcible entry force must be adaptable to change and prepared to 953 rapidly reconfigure for any follow-on operation that occurs. Joint forcible entry Action Officer-Level Draft for Collaboration Purposes Only 954 operations conclude when the Commander’s end state is achieved through the 955 accomplishment of specified objectives and the planned withdrawal, redeployment, 956 extraction, or transition to a follow-on mission is completed. 37 957 958 3.C.9 Provide focused sustainment 959 960 961 Establish the smallest logistical footprint but deliver with speed, accuracy and efficiency 962 Eliminate strategic, operational and tactical boundaries 963 Distribute to the point of requirement 964 Integrate a joint deployment, employment and sustainment process which dynamically “senses” requirements and is adaptive and responsive 965 966 967 Ensure freedom of movement for sustainment platforms Joint forcible entry operations forces require the ability to rapidly deploy and be 968 sustained anywhere they execute and for as long as necessary in order to enable campaign 969 execution without the necessity of extensive force buildup or operational pauses. The 970 joint forcible entry operations force should be capable of deploying and employing with 971 the smallest possible logistics “footprint” in or near the operating area. This requires new 972 capabilities to command and direct resources, fully integrate the joint deployment, 973 employment and sustainment planning process, exponentially improve situational 974 awareness and provide dynamic logistics, which includes the use of precision all-weather 975 aerial delivery. The result is sense and respond logistics that are faster, adaptive, more 976 responsive, and that execute movement and sustainment operations through multiple 977 means. Additionally, this requires leveraging future technological advancements that will 978 reduce the requirement for lift and sustainment while increasing employment options and 979 flexibility. 980 Joint forcible entry operations forces will depend less on developed ports and large 981 destination airfields and more on smaller, distributed logistics bases and joint seabasing. 982 The force will exploit pre-positioned assets, afloat or ashore, to include enemy 983 infrastructure, to substantially improve speed and agility. The ultimate goal is to provide Action Officer-Level Draft for Collaboration Purposes Only 984 faster, more focused, better-integrated logistics with on-demand support to the joint 985 forcible entry operations force. 986 38 Action Officer-Level Draft for Collaboration Purposes Only 987 39 3.C.10 Protect the force 988 989 Protect forces from point-of-origin to the battlefield 990 Establish multi-dimensional battlespace dominance 991 Use battlespace awareness capabilities to detect, assess and warn of impending 992 actions of the adversary 993 994 Develop a detailed and collaborative plan to protect personnel, physical assets and information 995 Defeat the adversary’s electronic warfare threat capabilities 996 Rehearse the plan to identify shortfalls; fill the gaps 997 Conduct force protection exercises that prepare forces to defend and recover 998 from adversarial actions 999 With increased emphasis on rapid global force projection, protection of the Joint 1000 Force must be assured from locations of origin to points of employment. Joint forcible 1001 entry operations are missions that demand clear guidance, total support and 1002 empowerment to the lowest levels of on-scene command. Force protection is required 1003 across the entire spectrum of operations: air, land, sea, space, and cyber-space, to include 1004 chemical, biological, radiological, nuclear and high yield explosives (CBRNE). 1005 Protection of joint forcible entry operations forces extends beyond the responsibility 1006 of the tactical commander. In peacetime, combatant commanders establish measures and 1007 procedures that preserve the combat power of their forces. In wartime, combatant 1008 commanders carry out assigned and implied missions in pursuit of strategic aims. Force 1009 protection responsibilities are modified as necessary in order to ensure the security of 1010 assigned forces and protect U.S. interests in their areas of responsibility. 1011 Force protection is significantly improved with the proper mix of intelligence and 1012 information gathering.7 In addition to intelligence gathering, the commander must 1013 designate forces responsible for acting on this intelligence. Finally, the force protection 1014 plan is developed, rehearsed and exercised in a collaborative environment. 1015 7 Joint Doctrine Encyclopedia, 16 Jul 97 Action Officer-Level Draft for Collaboration Purposes Only 1016 40 Section 4 – CAPABILITIES 1017 1018 “We need rapidly deployable, fully integrated joint forces, capable of reaching distant 1019 theaters quickly and working with our air and sea forces to strike adversaries swiftly, 1020 successfully and with devastating effect. We need improved intelligence, long-range 1021 precision strike, and sea-based platforms to help counter the “access-denial” 1022 capabilities of adversaries.” 1023 U.S. Secretary of Defense Donald Rumsfeld 1024 National Defense University, January 31, 2002 1025 1026 4.A Future Capabilities Sections 4.A.1 through 4.A.5 list the essential joint 1027 forcible entry operations capabilities. The capabilities are categorized by functional 1028 concepts of joint command and control, battlespace awareness, force application, focused 1029 logistics, and protection. To execute future joint forcible entry operations, the forcible 1030 entry commander and his force require the ability to: 1031 1032 4.A.1 Joint command and control capabilities 1033 1034 4.A.1.a Conduct dynamic and persistent joint command and control that supports 1035 planning and execution, from pre-execution through en route transit, execution at 1036 the objective area and transition to follow-on operations. 1037 4.A.1.b Plan, rehearse and synchronize missions between the deploying force, the 1038 objective area, joint forces, interagency and multi-national forces en route to an 1039 objective by accessing the global information grid to update the common 1040 operating picture. 1041 4.A.1.c Conduct collaborative decision-making under conditions of ambiguity, 1042 friction and stress. 1043 4.A.1.d Achieve coherency of action at decisive points supported by planning and 1044 decision-making tools and common rules of engagement. 1045 4.A.1.e Fully integrate fires and maneuver at the joint point of action. Action Officer-Level Draft for Collaboration Purposes Only 1046 4.A.1.f Expedite mission changes and fully informed decision-making through 1047 reach back. 1048 4.A.1.g Provide logistics command and control with complete global network 1049 visibility. 41 1050 1051 4.A.2 Battlespace awareness capabilities 1052 1053 4.A.2.a Translate pervasive knowledge and predictive analysis into anticipatory 1054 decisions and precise actions that achieve desired effects. 1055 4.A.2.b Provide persistent intelligence, surveillance and reconnaissance that 1056 integrate all intelligence capabilities, including human intelligence assets, into the 1057 overall intelligence, surveillance and reconnaissance architecture. 1058 4.A.2.c Provide a networked force linked and synchronized in time and purpose 1059 that can capitalize on near-instantaneous information and near simultaneous 1060 dissemination to turn information into action through a common operating 1061 picture. 1062 4.A.2.d Provide the joint forcible entry operations commander with field 1063 assessments that give him immediate information critical for decision making, 1064 entry point selection, force disposition, fire support and protection schemes. 1065 4.A.2.e Train with interagency and multinational partners to develop habitual 1066 associations and personal relationships to expand the network. 1067 4.A.2.f Find, isolate, and neutralize enemy elements that seek refuge in complex, 1068 difficult terrain, such as urban areas. 1069 4.A.2.g Detect and expose enemy covert and clandestine activities designed to 1070 disrupt, delay, and hinder the joint forcible entry operation. 1071 4.A.2.h Provide positive force identification. 1072 Action Officer-Level Draft for Collaboration Purposes Only 1073 42 4.A.3 Force application capabilities 1074 1075 4.A.3.a Fully integrate joint fires and maneuver through kinetic, non-kinetic, 1076 lethal and non-lethal weapons to achieve desired effects, while minimizing 1077 collateral damage. 1078 4.A.3.b Conduct offensive information operations in order to defeat the enemy 1079 without direct force. 1080 4.A.3.c Use air and sea lift to bypass fixed, predictable air and sea ports of 1081 debarkation and deliver forces in places the adversary does not expect. 1082 4.A.3.d Quickly establish or upgrade joint contingency air bases and sea bases 1083 that support tailored mission requirements. 1084 4.A.3.e Execute immediate response with modular, tailorable force packages pre- 1085 positioned in strategic locations. 1086 4.A.3.f Conduct joint forcible entry via vertical envelopment8 and surface 1087 amphibious assault across the global battlespace from strategic, operational and 1088 tactical distances. 1089 4.A.3.g Provide near-continuous force application ranging from localized small- 1090 scale effects, to persistent effects that can dominate defined geographic regions in 1091 order to deny the enemy freedom of action. 1092 4.A.3.h Defeat or bypass enemy access denial strategies to enable the use of 1093 multi-dimensional battlespace. 1094 4.A.3.i Immediately deliver forces in multiple unpredictable locations with 1095 sufficient combat power to achieve decisive effects. 1096 4.A.3.j Rapidly deploy and employ mounted forces that are lethal, mobile and 1097 survivable. 1098 4.A.3.k Produce desired effects using precise fires and maneuver in order to limit 1099 the demand on logistics sustainment. 1100 4.A.3.l Seamlessly and rapidly reinforce, reconstitute or reconfigure joint forcible 1101 entry forces. 1102 8 Vertical envelopment for this joint forcible entry operations concept includes the means to introduce land forces via air. Action Officer-Level Draft for Collaboration Purposes Only 1103 43 4.A.4 Focused logistics capabilities 1104 1105 4.A.4.a Deliver and sustain the joint forcible entry operations force, in all weather 1106 conditions, to objectives independent of existing infrastructure, from remote and 1107 austere bases; from sea-bases; and across strategic and operational distances. 1108 4.A.4.b Rapidly deploy the joint forcible entry force across the global battlespace, 1109 with little or no RSOI constraints, and transition to immediate employment in the 1110 objective area. 1111 4.A.4.c Provide a dynamic planning, tasking and execution process that supports 1112 the force flow and sustainment of the force. 1113 4.A.4.d Seamlessly and rapidly reconstitute or reconfigure joint forcible entry 1114 forces and sustain operations. 1115 4.A.4.e Establish additional contingency airfields or ports, or significantly 1116 increase the existing throughput capacity. 1117 4.A.4.f Reduce supply and re-supply demands through weapon systems with 1118 increased precision, effectiveness, firepower and reliability. 1119 4.A.4.g Recognize and rapidly apply technological advances that reduce the 1120 demand for all classes of supply in order to enhance joint forcible entry 1121 operations: e.g., reduce demand on fossil fuels, miniaturization of ordinance, etc. 1122 4.A.4.h Provide what is needed, where it is needed, and when it is needed, to 1123 distributed forces through enhanced capabilities such as predictive logistics, 1124 reachback, improved throughput systems and precise delivery systems. 1125 4.A.4.i Rapidly treat, stabilize and evacuate casualties. 1126 Action Officer-Level Draft for Collaboration Purposes Only 1127 44 4.A.5 Protection capabilities 1128 1129 4.A.5.a Disrupt, delay, destroy or disorient enemy fires through persistent, precise 1130 and timely counter fires. 1131 4.A.5.b Protect the joint force from all threats to include chemical, biological, 1132 radiological, nuclear and high yield explosives as it deploys, transits, engages, and 1133 redeploys in a multi-dimensional battlespace. 1134 4.A.5.c Provide on-call, immediate-response extraction airlift requiring little or no 1135 airfield infrastructure support. 1136 4.A.5.d Positively identify all entities in the battlespace that includes friend, foe 1137 and noncombatants. 1138 4.A.5.e Disrupt, delay, destroy or disorient the full range of enemy 1139 reconnaissance, surveillance and target acquisition. 1140 4.A.5.f Disrupt, delay, destroy or disorient electromagnetic threats. 1141 4.A.5.g Protect the joint collaborative network from all forms of attack. 1142 1143 4.B Immediate actions. Following are several recommended actions that might be 1144 considered for immediate implementation. These recommendations are derived from 1145 several sources: the various writers and reviewers of the concept, analysis of lessons 1146 learned of ongoing operations, and from the results of Joint experimentation to date. 1147 These are suggestions as to ways we might “jump start” while building the long-term 1148 capabilities described in section 4. 1149 4.B.1 Assess the requirement for a Standing Joint Task Force Headquarters to 1150 refine the concept and develop leader and organizational expertise with assigned 1151 rotational forces. 1152 4.B.2 Identification of joint forcible entry packages that conduct routine joint 1153 training, which will develop habitual operating relationships. 1154 4.B.3 Practice joint forcible entry operations using the forcible entry Standing 1155 Joint Task Force Headquarters in selected Combatant Commanders exercise 1156 programs. Action Officer-Level Draft for Collaboration Purposes Only 45 1157 4.B.4 Institute joint forcible entry operations in professional military education 1158 courses and programs of instruction. 1159 4.B.5 Develop a future concept that discusses shaping the strategic and 1160 operational environment. 1161 4.B.6 Rapidly field the hardware and software systems and doctrine that enhance 1162 the joint force’s ability to integrate fires. 1163 4.B.7 Place properly trained and certified “Joint Terminal Controllers” with 1164 current forcible entry forces capable of controlling and executing fires from all 1165 domains: air, land and sea. 1166 4.B.8 Integrate with appropriate service representatives to identify joint seabasing 1167 issues for experimentation. 1168 4.B.9 Research and develop heavy lift alternatives that enable tactical maneuver 1169 from operational distance. 1170 4.B.10 Research and develop over the horizon (OTH), beyond line of sight 1171 (BLOS) and on the move (OTM) communications. 1172 Action Officer-Level Draft for Collaboration Purposes Only 1173 46 CONCLUSION 1174 1175 “Improvement will require not only technological solutions, but also cultural change— 1176 a willingness to challenge standard practices, and question current organizational 1177 patterns and command practices.” 1178 General Richard B. Myers, Chairman Joint Chiefs of Staff 1179 1180 The complex nature and challenges of the future operational environment will require 1181 commanders to employ creative ways to conduct military operations. They will no 1182 longer have the time to move large force packages and their mountains of sustainment 1183 slowly into a region to build up to an overwhelming force. Future adversaries will use all 1184 of their available capabilities to prevent, disrupt or delay access to an area or areas. The 1185 enemy’s preference will be to defeat us before we have time to act or react. The 1186 adversary will use all means available to deny us freedom of action and maneuver. 1187 Future commanders will rely more and more on the ability to conduct joint forcible 1188 entry operations rapidly and forcefully from multiple directions and multiple dimensions 1189 to overcome access denial strategies. The dimensions include air, land, sea, space and 1190 cyberspace. A joint forcible entry operation will achieve one of three purposes: establish 1191 a lodgment for follow-on operations; establish multiple, networked lodgments to support 1192 larger-scale, extensive campaigns; or conduct a singular operations. Future commanders 1193 need the capabilities inherent to complete joint forcible entry operations. 1194 Joint forcible entry operations begin with a coherent plan with clear and achievable 1195 aims and objectives. There are common characteristics and processes relevant to all joint 1196 forcible entry operation, but each will be unique and distinct requiring its own mission 1197 analysis, plan and preparation. Forcible entry requires tactically proficient, cohesive, 1198 properly equipped and right sized forces. Joint forcible entry operations will require 1199 dynamic execution, blurring the lines between deployment, employment and sustainment. 1200 The joint forcible entry operations force requires the dexterity to deploy from a cold start 1201 and execute immediately on arrival. The dynamic nature and fast pace of joint forcible 1202 entry operations make it imperative that there be harmony throughout the force and 1203 throughout all phases of the operation. 1204 Action Officer-Level Draft for Collaboration Purposes Only 1205 47 APPENDIX A – Assumptions and Risks 1206 1207 This concept is focused on the time horizon just beyond the Future Years’ Defense Plan 1208 (FYDP), roughly 2015 and rests upon the following assumptions: 1209 1210 Assumptions: 1211 The global war on terrorism will continue through 2015. 1212 The U.S. will require robust joint forcible entry operations capabilities 1213 through 2015. 1214 Potential adversaries will benefit from the ongoing global diffusion and 1215 proliferation of anti-access technologies, including long-range, accurate 1216 missiles with supporting information architectures, weapons of mass 1217 destruction, weapons of mass effects, and inexpensive technologies. 1218 A determined adversary with sophisticated anti-access capabilities may 1219 initiate preemptive combat operations on the U.S. C-day in an attempt to 1220 preempt a U.S. deployment and prevent the introduction of U.S. combat 1221 forces into its operational area. 1222 Limitations in overseas port, airfield, infrastructure, and overseas logistics 1223 hubs will require alternative basing means and alternative means for 1224 deployment and sustainment of the force. 1225 1226 Risks: 1227 1228 envisioned for 2015 will not be feasible. 1229 1230 The vulnerability of afloat prepositioning stocks of 2015 could jeopardize seabased joint forcible entry operations. 1231 1232 Without a range of adequate basing options, joint forcible entry operations Army air assault capabilities will be ineffective if their forward staging bases are more than 150 miles from their objective areas. Without an adequate and sufficient on-call airlift capability executing, 1233 sustaining and extracting forcible entry forces from operational and strategic 1234 distances may not be feasible. Action Officer-Level Draft for Collaboration Purposes Only 1235 1236 1237 48 Without an adequate number of joint contingency air bases, required tailored air operations to support joint forcible operations may not be available. Without an adequate Theater Air and Missile Defense capability on C-day an 1238 adversary with sophisticated anti-access capabilities may be able to effectively 1239 defeat a U.S. strategic deployment to conduct joint forcible entry operations. 1240 1241 1242 Without rapid inter-theater lift the reinforcement and sustainment of a lodgment may not be timely. Without the critical enabling capability of Regional Combatant Commanders 1243 to exercise Joint Theater Logistics Management the intratheater deployment 1244 and sustainment of joint forcible entry operations forces will be significantly 1245 less efficient and effective, especially after first 30 days when naval forces 1246 normally become dependent on a joint logistics pipeline. 1247 Without an adequate number of combat logistics and sealift ships, sustainment 1248 of large-scale joint sea-based joint forcible entry operations may not be 1249 feasible. 1250 Without adequate counter measures an adversary with an effective and 1251 survivable low-altitude air defense system can deny U.S. assault forces a 1252 vertical assault option and disrupt the air sustainment of a lodgment. 1253 Without ability to rapidly project a maritime shield against asymmetric anti- 1254 access threats (mines, small boats, etc.), joint forcible entry forces may not be 1255 able to successfully gain entry to enemy territory. 1256 1257 1258 Without a link to the Joint National Training Center, required training can not be accomplished. Action Officer-Level Draft for Collaboration Purposes Only 49 1259 1260 APPENDIX B – Potential Enemy Capabilities – 2015 1261 1262 1263 1264 1265 1266 Recognizing victory over the United States through force-on-force combat is unrealistic, adversaries are designing capabilities and doctrine to deny or limit U.S. forces ability to gain access to a region. Most potential adversaries conclude that by developing the ability to limit and/or interrupt access, it will be possible to reduce U.S. military capability to a manageable and, in certain cases, vulnerable level ― if only for a limited time. 1267 1268 1269 1270 1271 1272 1273 Adversaries are devising new and different ways to engage the United States. They will adapt to counter or degrade the United States’ overwhelming strengths — airpower, technology, precision, strategic reach, and sea control employing various methods organized around the seven operational designs described below. Threats will employ many distinct, though inextricably linked dimensions at all stages of conflict to deny or control U.S. access to the region. In turn, the U.S. must adapt and improve forcible entry capabilities to overcome these known or anticipated anti-access efforts. 1274 Threat Operational Designs 1275 1276 1277 1278 1279 1280 1281 1282 1283 Strategic Attack. Defensive operations at the operational and tactical levels will often be combined with strategic attack. Strategic attack is any enemy action designed to have direct effect on American national will, leadership, and strategy. Future adversaries will continuously employ strategic actions, such as information operations, terrorism, crime, attacks on coalition and supporting nations, and economic sabotage, to wear down America’s will to fight. Strategic attack will seek to exploit seams in alliances and coalitions, focusing on the most vulnerable partners. Strategic attack will be conducted in the U.S. homeland, on the battlefield, and anywhere in between, but in all cases will be fully integrated with tactical and operational design. 1284 1285 1286 1287 1288 1289 1290 1291 1292 1293 1294 1295 Operational Exclusion. Potential adversaries are developing operational methods to counter US involvement, attempting to limit the extent of U.S. involvement, or cause early termination by collapsing international and national support. Based on their perceptions of historical patterns of deployment and employment, future opponents will apply operational exclusion to prevent U.S. forces from obtaining and using operating bases in the region, and in doing so, delay or preclude American military operations. Increased threats to forward bases raise the risks to forces, hindering operational phasing and diminishing host nation support for protection of the U.S. lines of communication. Elements other than conventional belligerents—for example, terrorist groups or criminal elements—are also likely to conduct operational exclusion, either for their own purposes or to support operational exclusion of others. In the latter case, such operations would signal sympathy or accomplish complementary goals. 1296 1297 1298 1299 1300 1301 Access Limitation. Along with constant operational exclusion actions, an adversary will attempt to limit or disrupt access to the area of conflict, CONUS and/or OCONUS. The threat will conduct attacks continuously on our forces using all available means to strike key or critical force components, such as air and sea ports of embarkation/debarkation, staging bases, and lift. Success in this endeavor to extend the battlefield will greatly improve an enemy’s ability to disrupt, delay or defeat U.S. forces. Action Officer-Level Draft for Collaboration Purposes Only 50 1302 1303 1304 1305 1306 1307 1308 1309 1310 Shielding. Along with controlling or limiting the introduction of large, highly capable U.S. forces, adversaries will also attempt to manage the conflict environment. Shielding tactics involve systems, terrain and methods designed to offset the effects of precision long-range air and missile attacks, giving the opponent a degree of operational freedom and a way to preserve his military capabilities. Opponents recognize that defeating the United States is not a matter of winning battles, but rather of not losing the military power necessary to preserve the regime, while pursuing strategic and operational victory. The longer an enemy delays an effective U.S. response, the greater the chances for success. 1311 1312 1313 1314 1315 1316 1317 1318 1319 1320 Systemology. Force-on-force combat exposes the enemy to U.S. strengths. To avoid this form of combat, the enemy will focus on denying U.S. forces the ability to conduct networked “system-of-systems” operations. Potential opponents will understand that American forces derive their overwhelming force effectiveness from the synergy of their systems functioning together. Opponents will attempt to take advantage of such “systemology,” employing multi-dimensional, simultaneous, and sequential actions across a wide spectrum of operations to destroy or damage discrete U.S. capabilities in order to cause the greatest degradation of the overall force. An opponent will accomplish this by finding and attacking those critical links, nodes, seams, and vulnerabilities in U.S. systems that offer the best opportunity to “level the playing field.” 1321 1322 1323 1324 1325 1326 1327 Strike. Future opponents will use maneuver adaptively. Although the threat strategy against the United States is primarily defensive in nature, it will allow for offensive maneuver during periods of opportunity including adverse weather. Enemy maneuver will focus on massing effects rather than forces. This adaptation will allow opponents to gain the benefits of maneuver and mass without exposing themselves to the United States’ overwhelming advantage in standoff precision. However, opponents will employ maneuver in this manner only when tactical decision is likely. 1328 1329 1330 1331 1332 Recon and Surveillance Fires. Reconnaissance fires, the principal strike component of systems warfare, link intelligence, surveillance, and reconnaissance to long and shortrange precision fires from dispersed locations. As critical nodes, links, and vulnerabilities are discovered through reconnaissance, the threat employs fires to engage these decisive points, creating significant effects while avoiding force-on-force combat. 1333 1334 1335 1336 1337 1338 Threat Strategies. Having anticipated the possibility of U.S. intervention in regional conflicts, opponents’ forces, tactics, and strategy will be designed around the ability to exploit U.S. vulnerabilities and patterns while countering or mitigating strengths. Adversaries will integrate less conventional capabilities such as paramilitary forces, “hugging” civilian populations, terrorism, and weapons of mass effects while dispersing and shielding conventional forces. 1339 1340 1341 1342 1343 1344 Understanding the ready availability of technology and the limitations of their resources, potential opponents will develop investment strategies that provide them the means to achieve their regional and extra regional goals, while accounting for the need to counter the United States’ overwhelming conventional military capabilities. Generally they will invest in off-the-shelf technologies first, seeking a few high-tech niche systems such as information and communications technology, intelligence collection systems, counter- Action Officer-Level Draft for Collaboration Purposes Only 51 1345 1346 mobility technology, modern air defenses, and precision munitions, all of which enhance their anti access capabilities. 1347 1348 1349 1350 1351 1352 1353 1354 1355 It is clear from analysis and published thought on warfare design that future threats will develop asymmetric strategies that allow them to oppose the United States in the future. Opponents will seek to gain advantage by moving quickly and acting early, expecting to preempt or reduce the effectiveness of U.S. diplomacy, economic pressure, and information operations. By limiting the United States’ ability to influence the situation, opponents expect to degrade the synergy of any military operations that follow. Possessing the ability to rapidly project power whether with airborne, air assault or other forces, the U.S. demonstrates its willingness to conduct forcible entry operations to overcome these threat strategies.9 9 References: TRADOC Pam 525-2-60, The Operational Environment and the Threat.