Question 1
advertisement

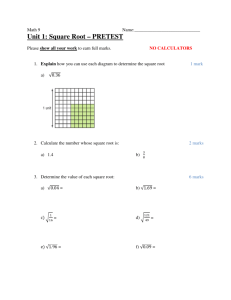
Question 1 1.1 Suppose that we are to transmit the following 10-bit message on the Data Link layer: M = 1011001101. We wish to generate a Cyclic Redundancy Code (CRC) using the following 6-bit generator G = 101101. Hence n = 10 and k = 5. Determine for this situation: a) The required Frame Check Sequence (FCS) [8 + 6 = 14 marks] b) The actual transmitted frame T 1.2 An organisation is granted the block of addresses 130.56.0.0/16. The administrator wants to create 1024 subnets. 1 a) Find the subnet mask required 1 b) Find the number of addresses in each subnet 2 c) Find the first and last addresses in subnet #1 2 d) Find the first and last addresses in subnet #1024 1.3 Briefly explain the procedure for checksum calculation and verification in the IPv4 protocol. What part of an IPv4 packet is covered by the checksum calculation? Why? [2 + 1 + 1 = 4 marks] 1.4 Packet switching techniques require the packet payload to be prefixed with a header. List three (3) essential items that must be included in the packet header. Justify your choice of items. [6 marks] Total [14 + 6 + 4 + 6 = 30 marks] Question 2 This question is concerned with Internet addressing concepts. 2.1 There are 5 different network classes for addressing in the Internet (using IPv4). Compute the theoretical maximum number of addressable hosts in all: (a) Class A networks 2 (b) Class B networks 2 (c) Class C networks 2 2.2 The numbers computed in 2.1 above represent upper bounds on the numbers of addressable hosts for these classes of network: (a) Briefly explain how this number is reduced through the use of special reserved addresses. (b) Provide an estimate of the number of actual available host addresses for a given Class C network. [2 + 4 = 6 marks] 2.3 What is meant by the term fragmentation in the context of the Internet Protocol? Give an example of how it works. [4 marks] 2.4 (a) What is the purpose of a subnet mask? (b) Is the subnet mask 255.255.0.255 valid for a Class A [2 + 2 = 4 marks] address? Explain. 2.5 Briefly explain the difference between a switch and a router. [4 marks] 2.6 Consider the following internet address: 136.27.32.104 a) Convert this address into Binary format. b) Convert this address into Hex format. c) What class does this internet address represent? d) If we apply a subnet mask of FFFFFE00, obtain the relevant network, subnet and host addresses for the given internet address. [1+1+1+3=6 marks] Total [6 + 6 + 4 + 4 + 4 + 6 = 30 marks] Question 3 3.1 Consider the TCP header shown above. Provide a brief explanation of each field in this header. [16 marks] 3.2 Briefly explain the principal differences between UDP and TCP and the reasons for choosing between them for a given internet application. [4 + 4 = 8 marks] 3.3 Briefly describe the key differences between the Link State Protocol OSPF and the protocol known as BGP4. Identify the situations where each of these routing protocols would be applied and reasons for selecting them for those situations. [3 + 3 = 6 marks] Total [16 + 8 + 6 = 30 marks] Q4 Discuss the use masks in the manufacture of integrated circuits. Your answer should explain what masks are, how they are used, and when masks are used. [5 marks] Two computers, X and Y, are being evaluated for use as weather prediction engines. They will run a Fortran program called WETHA. Both computers, X and Y have 20 GHz clocks, and three types of instruction, A, B, and C, which take 1, 2, and 3 clock cycles to execute respectively. When WETHA is compiled on computer X, it will execute 5 x 1010 instructions of type A, 1 x 1010 instructions of type B and 1 x 1010 instructions of type C. When WETHA is compiled on computer Y, it will execute 1 x 1011 instructions of type A, 1 x 1010 instructions of type B and 1 x 1010 instructions of type C. (A) Calculate the MIPS rating for computer X while executing the WETHA program, [5 marks] (B) Calculate the MIPS rating for computer Y while executing the WETHA program, [5 marks] (C) Calculate the execution time for WETHA on computer X [5 marks] (D) Calculate the execution time for WETHA on computer Y [5 marks] (E) Which computer would be preferable? Please state your reasons. [5 marks] Please include your working, and the equations you use. I don’t mind if you structure your answers as some sort of table to avoid repetition, but please clearly indicate the association between the answer and the individual components of the question. Q5 (A) Describe the general purpose of the circuit shown in the diagram below, and how it works. [5 marks] 01100101 B ∑ ∑ ∑ ∑ ∑ ∑ E ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ ∑ D ∑ ∑ ∑ ∑ ∑ ∑ 01100101 C (B) – (F) Describe the specific function of each of the labelled sections of the circuit. Note that the labels run from B to F, to match the section of this question. [5 marks each] [30 marks] Q6 (A) What does it mean to describe the datapath of a computer architectures as gated, and why are some computer architectures constructed this way? [5 marks] (B) In a pipelined architecture, several sequential instructions are running simultaneously. How are the control signals for these instructions amalgamated without causing ambiguities? You may find it helpful to draw a diagram. [5 marks] (C) Is the architecture below a single-cycle architecture or a multicycle architecture? What feature(s) of the design led you to that conclusion? PC memory read adddress write adddress write data PC Write I or Mem D Read Mem Write memory data register instruction register IR Write Mem Reg to Reg Dest write data read data1 write register read register1 read register2 read data2 signextend shift left 2 A 4 B 1 0 zero ALU ALU out 2 3 ALU ALU SelB SelA [5 marks] (D) Describe the problem that the sign-extend component is designed to handle, and describe what it does. [5 marks] (E) What type of circuit is the component labelled ALU SELB in the circuit diagram above, and what is its purpose in the architecture? Why is one of its input values the number 4? [5 marks] (F) The circuit has a control input called I or D. What does the device with this control input do, and why is this action nmecessary? [5 marks]