SOX Documentation Template Final 08
advertisement

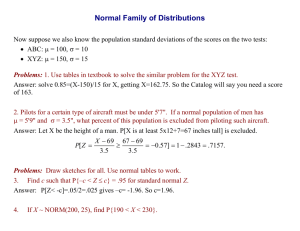
Last Update - 08/07/2004 Sarbanes-Oxley 404 Business Process Documentation Template Page 1 of 18 Last Update - 08/07/2004 Overview - SOX Documentation Requirements Sarbanes-Oxley (SOX), section 404 requires company management to ensure that they have a comprehensive system of internal controls which enables them to consistently report complete and accurate financial information for all of their key business transactions. Internal process controls, as well as the system controls over transaction processing, must be in place to ensure the accuracy and completeness of the financial information being reported. These controls should be designed in such a way that they address the potential risks associated with the recording of key business transactions. In addition, a risk assessment by an independent party must be performed to demonstrate and confirm the design effectiveness of the system of internal controls. The first step in performing a risk assessment is a review of the existing end-to-end business process procedures and process flows. As stipulated by SOX section 404, internal controls do not exist unless they are documented. Business process documentation must include sufficient content to clearly capture and communicate all of the key control steps and activities. This is necessary so that the individuals responsible for performing their portion of the business process will be aware of their key control accountabilities. The documentation should be written from the perspective of how you would describe your business process to a person who has never been exposed to it before. The purpose of this document is to provide our business process owners with guidelines for completing the process documentation portion of the SOX effort including the documentation on the key controls. The suggested format addresses all of the requirements of sound process documentation. In this example, we include “nice to have” items which we believe add value to the documentation but are not required to meet the documentation minimum. We make reference to those “nice to have” items by stating they “can” be included. They are not required as part of your documentation. Page 2 of 18 Last Update - 08/07/2004 Table of Contents Section - I Documentation Elements & Content Section - II Documentation Components Section - III Sample Documentation Section - IV Sample of a Completed RCM Page 3 of 18 Last Update - 08/07/2004 Section - I Documentation Elements & Content There are 3 elements of business process documentation. They are the: executive summary (can be included, but is not required) end-to-end description of the business process flow to include supporting documentation (required), e.g., job descriptions, standard operating procedures, desk procedures, etc., and the completed risk control matrix (required) We will briefly explain each. Executive Summary – See Section D on page 11 for an example of this section of the documentation. This is a high level description of the end-to-end business process highlighting the key internal / financial control touch points. This section of the documentation can include a high level process flow diagram. The process flow diagram will describe the flow of the transactions and individual responsibilities in enough detail that the reader will gain a general understanding of the process flow, responsibilities, and the key internal controls. It serves as a guide or starting point for the next component of documentation. End-to-End Process Flow – See Section F on page 11 for an example of this section of the documentation. This is a detailed description of the end-to-end business process and includes the process steps that cover all of the sub-processes. This section identifies and describes in detail individual responsibilities, transaction initiators, how transactions are recorded, how they are authorized and reported, the key control steps that are performed and who performs them. This section is at a level of detail that ensures the individual performing the control step is aware of it and that they are responsible to comply with it. NOTE: The process documentation must specify the evidence that the control step was performed, e.g., an authorization signature based upon dollar limits, a system audit trail that identifies the user that performed the step, a control check list that is initialed by the individual performing the control step, an edit listing that is signed by an authorized individual, etc. The description of the control steps in this portion of the documentation must be in English so that during the testing phase, an individual can review and re-perform the control steps. Other supporting documentation, i.e., job descriptions, organization charts, authorization matrix, can be in the local language. As to the key control activities, the documentation must include the following information: description of the key control activities to include methods and assumptions used, (“What”) by job title, the individual(s) that perform and approve this control activity, (“Who”) Page 4 of 18 Last Update - 08/07/2004 the frequency and timing the control is performed, (“When”) the point in the process that the control takes place; either automated or manual (Where) and, evidence that demonstrates that the control step was performed to include identification of the forms, documents, and system applications used. (“How”) NOTE: Information as to “Why” a key control is necessary is included in the Risk Control Matrix (RCM / ICM tool) and does not have to be included in the documentation described above. Handover to Others It is very important to identify the points within your process documentation where an entire processing step or a single transaction may be handed over to another department for continuation or completion. Once these points are identified and noted in your documentation, you will need to contact the appropriate individual in the department or group to whom the hand off is going and obtain their agreement with the handoff point you have identified. It is critical that the receiving department or group capture the identification and documentation of any key risks and controls they perform related to the completion of this transaction in their RCM. New or Existing? Business process documentation can be a new document that you create which contains all of the required information described above or multiple existing documents that can be attached in the ICM application tool to constitute the SOX documentation requirement. For example, existing documentation describing an end-to-end business process, its sub-processes, or evidence of the related key controls can include, but does not have to be limited to, the following: a flowchart depicting each of the steps in the process, written site policies on the activity which may make reference to corporate policies, a listing of all of the in place system controls to prevent unauthorized changes to transactions without the proper authorizations, a checklist of month-end closing procedures, a form used to request user access to system modules with related instructions, minutes from senior management meetings, a job description that includes details of key control responsibilities. Page 5 of 18 Last Update - 08/07/2004 Is this a Rewrite of Our Existing Operating Procedures? We do not wish to limit the form of key control process documentation to any one type and request that you use your judgment. It is important to keep in mind however, that whatever format you select, it must contain the elements described on the prior page. To reiterate, the documentation should contain clear statements on the key control activities and identify by job title the individual(s) responsible for performing the key control activity. Risk Control Matrices ("RCMs") – See Section I on page 14 for an example of the Procure to Pay RCM. SOX, section 404 requires companies to formally evaluate the risks associated with their operations and to specifically identify the key internal control activities that are performed to mitigate the identified risks. The RCMs were developed to identify the key risks and related controls for all of Pfizer’s key business processes. These are defined as “primary annual processes”, i.e., primary annual processes are those processes at a location that, if not properly controlled, could cause a material financial misstatement (at a consolidated company level). You can populate your controls in this EXCEL based RCM or directly into the Oracle Internal Control Manager (ICM) database. For sub processes that comprise each parent process, the RCMs identify the risk areas and control steps that are in place to mitigate the control risk. They start with the identification of the business risk within the overall business process. This is followed by an identification of the COSO (Committee of Sponsoring Organizations) pillars and financial statement assertions that relate to the identified risk. It is important to note that the RCMs must show the linkage between the identified business risk and the key controls that support each of the assertions identified in the COSO pillars. This linkage is made by referencing the key control activity to one or more of the COSO pillars. See Appendix I on page 17 for a schedule of the risks identified to COSO pillars on RCMs. In some cases, the RCMs you received already identify the risk elements that must be addressed. This information was provided in order to minimize the time and effort required on behalf of each site in performing and documenting their risk assessments. Should you identify additional risk and key control items specific to your site, they should be noted and immediately communicated to an Internal Audit manager or supervisor. They will review your suggestions and if deemed appropriate, have them added to the RCM for that key process. The flow of the columns on the RCM will lead you to sections or columns in which you must identify the key control activity that addresses the risk exposure. Your risk responses should reference the underlying end-to-end process documentation related to each control. Please note that documentation is mandated for the risks that represent primary exposures (key risks) under SOX, section 404. These key risks are identified in the column headed “404 risk” and contain a letter "Y" for yes. You must fill out a response to all of the risks identified as a 404 risk. To the extent the RCM includes a risk Page 6 of 18 Last Update - 08/07/2004 for which you cannot identify a currently functioning control process, you should develop and clearly document a control process to address that risk or document why the risk may not apply. In addition, system edit reports and evidence of analytical reviews or the performance of an internal control step should also be referenced on the Risk Control Matrix. Once the RCMs are complete, i.e., the key risks and related controls have been identified; the information contained on these documents must be entered into the ICM tool. We realize that several sites started the RCM process using the EXCEL spreadsheets and have completed all of their documentation on these sheets. For these sites, the control step information contained on the spreadsheets can be entered directly into the ICM tool. Guidelines for Identifying Key Controls The process of identifying the primary or “key controls” requires careful thought and good business judgment. While performing the process documentation step you will no doubt identify many controls related to the financial reporting assertions and the business risks associated with those assertions. You will therefore need to be able to identify and prioritize the key controls. One method is to label the controls you have identified as “A”, “B” and “C” where the “A” controls would represent the key controls. The key controls are normally found at the activity or process level as opposed to the entity level, i.e., they are not top side controls. They relate specifically to transaction processing. Additionally, you can apply the below “tests” as a further means of isolating key controls. A key control step is a control step that: is especially critical to the mitigation of risk and directly linked to one or more financial reporting assertions, is directly linked to a key control, i.e., the achievement of a key control is dependent on another control, is deemed critical. Should it not operate as designed or not be performed, it would expose the company to a significant risk, is based upon the generation of critical information (be it generated by IT or manually) such that should that information not be generated or be generated but not be accurate and complete, would expose the company to high risk, if not performed, would have a pervasive impact on financial reporting. An example of this would be authorization limits, segregation of duties, restrictions in data access and processing, etc. Page 7 of 18 Last Update - 08/07/2004 Summary of the Business Process Documentation Effort In summary, the flow of the documentation is from the executive summary (if you included one) high level overview of the business process to the Risk Control Matrix which makes reference to the underlying control documentation. The internal control points identified in your end-to-end detailed process description should correlate to the internal controls identified on the RCM. The RCM will include a summary description of the internal control and reference the related business process documentation. The documentation should address the six (6) items listed below: Who? - the people involved in the processing of the transactions and those responsible for approving results What? - the methods and assumptions that were used When? - the frequency and timing of the transactions Where? - the place where the supporting documentation resides and processing takes place Why? - the control objective How? - the forms, documents and system applications used to process these transactions Section - II SOX Documentation Components NOTE: The components marked as “optional” are not required A. B. C. D. E. F. G. H. I. J. Business process documentation cover page (includes process name) - optional Documentation history, approver / sign-off, file name and location - optional Table of contents - optional Executive summary - optional Process flow diagram - optional End-to-end detailed business process description that includes identification of all of the sub-processes, a description of key roles and responsibilities, and process background information - required Sub-process detail for each sub-process step - required. Can be satisfied by documents that have been appended to the ICM tool Reference to any supporting system(s)or tools used in the performance of the process step - required Completed RCM - key risks and control activity summary - required Appendix - For attachments that are deemed necessary to further explain or understand the overall business process - optional Page 8 of 18 Last Update - 08/07/2004 In order to illustrate how you would complete your process documentation, each of the above components is described in a little more detail below. Please note that the documentation example shown below conforms to the above listed documentation components, some of which are not required to meet the documentation minimum. Section - III Sample Documentation A. Business process documentation cover page (optional) Each documented business process can contain a cover page that describes the specific business process being addressed. The cover page contains a reference to the version number of the documentation and the last revision date. See the example below: (Business unit, e.g., PGM) Business Process Documentation The full name of the end-to-end business process being documented Sub-process number and name Version Number – X.X Procedure Status - Initial Draft Last Updated – XX/XX/XX NOTE: The process description name should be put into the procedure document header and the version information should be put into the procedure document footer so that they will appear on every page. Page numbers should also be added so that they can be referenced back to the RCM. B. Documentation History, Sign-Off, and File Location (optional) In order to provide management and audit with a trail that allows them to track and monitor the status of your process documentation, a page containing the document history, sign-off / approvals, and the location of the documentation can be included. See the sample below. Page 9 of 18 Last Update - 08/07/2004 Document History Version 1.00 1.01 1.02 1.03 1.04 Date 3/23/04 3/29/04 4/8/04 4/8/04 4/27/04 1.05 2.00 5/4/04 5/0/04 Author Full Name Status & Description / Impact to Document First draft Second draft Reformatting Third Draft Fourth Draft – revised to reflect comments noted during the GAP analysis meeting. Update comments were received from John Doe on xx/xx/xx. Final Draft Final Update with control step updates from the remediation plan Document Sign-Off Name Title Department Signature Department Manager Finance Director/Team Lead PGX Headquarters Finance Senior Director PGX HQ Finance Signature Date File Name & Location of the Documentation File Name File Location Department Name C. Process Number – Process Name, Version #, Rev Date.doc S:/PGX/404 Documentation/file name.doc XXXXX Accounting Table of Contents (optional) This page can be included and would contain the names of each section in the procedure with associated page references. See the example below. Document Contents Section Page reference Executive Summary Process Flow Diagram Process Narrative 4 4 4 Sub Process 01: Sub Process Name Key Process Roles Process Background Process Steps 4 4 5 5 Page 10 of 18 Last Update - 08/07/2004 Sub Process 02: Sub Process Name Key Process Roles Process Background Process Steps 10 10 10 10 Supporting Systems/Tools Key Risks and Control Activities (RCM) Additional Supporting Documentation (if any) 13 14 19 Appendix 20 COSO Pillars 20 Assertions 20 D. Executive Summary (optional) The executive summary can contain a narrative of the entire end-to-end business process. Also included would be the process name and the process ID. See the example below: Process Name XYZ Accruals Process ID 3 Executive Summary This section contains a high level description of the end-to-end business process and includes a reference to any system or systems that are used. E. Process Flow Diagram (optional) The business process flow diagram can be included, particular for complex or unique processes. This can be a high level pictorial flow of the end-to-end business process and identify any sub-processes contained in the overall process. This process flow should also highlight the Key control areas as identified in the overall Risk Control Matrix. For each of the sub-processes identified, include a sub process narrative explaining how that sub-process is performed. See a sample process flow diagram below: XYZ Accruals (2) (3) Calculation of Recording of Current XYZ Quarter XYZ Expense/Accrual Accrual F. End-to-end process narrative - includes all of the sub-processes, key process roles, and process background information. (required) NOTE: this can be a process narrative that includes the description of the sub-processes (1) Forecasting of XYZ Page 11 of 18 Last Update - 08/07/2004 This is required. It is recommended that the business process narrative be divided into three sections, (1) the sub-process inventory, (2) key roles and process responsibilities, and (3) background information on the sub-process. In the sub-process inventory, each sub-process can be given a sub-process id number and a sub-process name so that they can be referenced in the narrative. See the example below; (1) Sub Process Inventory Sub Process ID 1 2 3 Sub-Process Name XYZ Forecasting Current Quarter XYZ Accrual Calculation XYZ Expense/Accrual Recording Next is a description of the key roles and responsibilities by job title within each subprocess. (2) Sub Process 1: XYZ Forecasting - Key Process Roles & Responsibilities Title Process Responsibilities Consultant – Business Technology Finance Manager – HQ Finance Director/Team Leader – HQ Finance Senior Director – HQ Finance Director/Team Leaders – Marketing Finance Senior Vice President – Finance Extracts XYZ payment data from data warehouse Prepares XYZ Forecast & Quarterly Journal Entry, Reconciles Forecast to G/L & Galileo Reviews XYZ Forecast / XYZ Exp. Recorded Reviews XYZ Forecast / XYZ Exp. Recorded Reviews XYZ Forecast Reviews XYZ Forecast (3) Process Background Pfizer forecasts XYZ payments by product. XYZ payments are forecasted by quarter by applying an historical Base Rate to the product’s forecasted gross sales less any forecasted credits for the current quarter. This calculation will result in the Basic XYZ Forecast. After the basic XYZ forecast is determined, HQ Finance will review the XYZ forecast to determine if any top side adjustments are necessary to reflect anticipated / new XYZ trends. After any adjustments are made, the result will be the Final XYZ Forecast. The forecast formula is depicted below: Base Qtr XYZ Rate for Product * Forecast Sales less any credits = Basic XYZ Forecast + / - Page 12 of 18 HQ Adj. = Final XYZ Forecast for Qtr. Last Update - 08/07/2004 G. Sub-process detail for each sub process step (required) Sub Process ID 1 2 Process Owner Process Activity Finance Manager – HQ Finance Receipt of XYZ utilization information from contracting groups As a starting point, the Finance Manager – HQ Finance obtains actual XYZ payment data by product, by quarter. Business Technology aids in the reporting of payment data from the ABC System in the following manner: On a weekly basis, payment data from the ABC system is completely and accurately extracted from Pfizer’s data warehouse and downloaded into an Excel file by business technology utilizing an export table prepared by the Data Warehouse group. Hash totals of the extracted data are compared to the source data in the ABC system to validate the extraction. (Key Control 1.) Business technology utilizes Excel to sort the data by brand and reviews the brand data to verify that all expected brands and related data are included. An Intranet web link has been created to automatically, completely, and accurately extract the data from the export table when activated. Only the Finance Manager – HQ Finance has user access to this web link. (Key Control 2.) The web link allows the user (Finance Manager – HQ Finance) to sort payment data (by product, plan, etc.) for a particular time period. Four extractions of information are performed: (1) Buss Unit A (2) Buss Unit B, (3) Buss Unit C, and (4) Buss Unit D. The administrative Assistant, HQ Finance aids in the compilation of payment data from the Computron General Ledger system. Individual payments are downloaded from Computron to an excel spreadsheet. From this download, the administrative assistant obtains additional supporting data i.e. check request number, invoice dollar data, etc. that is resident in Computron. This data is then linked to their applicable payment periods. All supporting documentation related to the creation of this schedule is retained by HQ Finance in a payment support binder and reviewed periodically by the Finance Manager. Finance Manager – HQ Finance Determine the most recent quarter for which payment data is complete This is determined by reviewing reports of XYZ payments from the contracts group. These reports provide the following detail: XYZ payments by product, by quarter based upon when the XYZ payment was established. Since the product data within these reports is on a slight lag as compared to the payment data obtained from the Computron G/L, the Finance Manager – HQ Finance, compares the total XYZ payments made by product for the most completed quarter (i.e., base quarter) to the total XYZ payments per Computron G/L. (Key Control 3.) The Company then distributes any difference between the aforementioned total XYZ payments per Computron and the total EYZ payments per the ABC system across all products by adding a flat mark-up rate to each product’s XYZ payment data per the DEF system. From the above, you can get an idea of the type of information that needs to be included in each sub-process description. It is very important to make specific reference to the key control activity (if one applies to that sub-process) in the sub-process descriptions. The control activity has to be in sufficient detail as to include the evidence that the control step was performed. Page 13 of 18 Last Update - 08/07/2004 H. Supporting Systems / Tools (required) System Name ABC DEF GHI Microsoft Excel Data Warehouse Process Description Forecast and actual review tool Validation of XYZ claims system and reporting tool Validation of XYZ claims system and reporting tool Used as a forecasting tool for XYZ expenses and accruals, as well as a tracking tool for reserve utilization Data warehouse stores contract data from the customer claims systems Business Owner PGX PGX Contracts PGY Contracts PGX Finance PGX Contracts I. Completed Risk Control Matrix - A summary of the key risks and control activities (required) Section - IV A sample RCM is presented on the next few pages. * Full descriptions of the Assertions and COSO Pillars are listed in Appendix I which is on page 18. Page 14 of 18 Last Update - 08/07/2004 Parent Process: Procure to Pay SubProcess COSO Pillars* Risk Type Assertions* 404 Cash Disbursements Control Activity O, F E, V, O Y Cash Disbursements Control Activity O, F E, V, O Y Risk Inappropriate or inaccurate disbursements Unauthorized payments. Opportunity to obtain discounts may be lost. Risk Description Control Objectives Control Objectives Description Failure to ensure all disbursements are authorized may cause fictitious documentation to be created and allow for company funds to disbursed fraudulent or inappropriately. Additionally unusual one-time payments may be processed without detection. To disburse cash only for authorized purchases and that all large and unusual cash disbursements be reviewed by management. Payments should be approved by individuals independent of procurement, receiving and accounts payable based on proper supporting documentation including original authorized invoice. The supporting documents for the payments made should be canceled to prevent resubmission for payment. Secure interface should exist between the account payable and the payment system. Two signatures are required on checks and on letters of instruction to banks requesting funds transfers or disbursements. Failure to ensure payments are authorized and remitted appropriately may lead to the occurrence of payments to unauthorized vendors or accounts. Additionally, opportunities to obtain cash discounts for To process accurate payments. Describe how you ensure that all of your operation's disbursements are properly documented and authorized. Page 15 of 18 Payments are made per the vendor's remittance instructions. Proper controls should exist to ensure integrity and accuracy of the payment information and ensure the authenticity of the counterparty. Discounted payment terms should be identified within the system. Changes to vendor information should be monitored. How do you ensure all payments are remitted appropriately? Existing Controls - Provide a Control Description Last Update - 08/07/2004 SubProcess COSO Pillars* Risk Type Assertions* 404 Risk Risk Description Control Objectives Control Objectives Description prompt payment of invoices may be lost. Accounting Control Activity F C, E, V, P Y Inaccurate Accounts Payable Information Failure to record information accurately and timely may lead to the occurrence of fraud or misappropriation of assets and disbursements not reported accurately to Accounts Payable. Transactions with vendors are not complete or accurately accumulated in AP. To accurately and timely record accounts payable activity Accurate recording of accounts payable information depends upon the following factors: • Complete and timely information regarding a purchase • Accurate input of transaction details in the purchasing system and proper data entry validation • Secure interfaces and monitoring controls to ensure consistency of purchasing, inventory and account payable information • System controls to prevent entering duplicate invoices To ensure Accounts Payable is accurate vendors statements should be periodically received and reconciled to records. Credit memos should be assigned unique document number and referenced to a valid PO. In addition, AP balances should be periodically reviewed for reasonableness and to ensure rounding or other differences on foreign exchange rates are properly accounted for. How do you ensure all current activity is recorded in an accurate and timely manner (especially for monthly closing balances)? Accounting Control Activity F C, E, V, P Y Inappropriate adjustments / journal entries Inaccurate reporting of Accounts Payable balance in the G/L. End of period processing may be accidentally or inappropriately executed, resulting in To ensure completeness and accuracy of General Ledger The General Ledger Accounts Payable account must accurately reflect the actual conditions of the business. Management must implement controls to ensure the following: • Secure interface exist between the Accounts Payable sub-ledgers and GL • GL and subsidiary ledgers monthly closing balances reconcile (if not, all discrepancies are investigated timely) • Any adjustments made to the GL are reviewed and approved. The system should not allow for Page 16 of 18 Existing Controls - Provide a Control Description Last Update - 08/07/2004 SubProcess COSO Pillars* Risk Type Assertions* 404 Risk Risk Description Control Objectives incomplete recording or the recording of transactions in the incorrect period. Control Objectives Description processing of unauthorized adjustments • Only authorized users should have the ability to perform period end processing. • All un-invoiced receipts are accounted for. How do you ensure the GL is accurate? Page 17 of 18 Existing Controls - Provide a Control Description Last Update - 08/07/2004 J. Appendix – used for attachments that the site deems necessary to further explain or understand the overall business process. (optional) Appendix - I COSO Pillars Pillar Monitoring Description The processes that assess the quality of internal control over time. The process that ensures relevant information is identified and communicated in a timely manner to enable people to carry out their responsibility. Examples On-going reviews, separate evaluations, reporting and correcting deficiencies Timely, adequate information; open communication Control Activity The policies and procedures put in place to mitigate risks. Segregation of duties, preventative controls, detective controls Risk Assessment Identification and analysis of relevant risk to the achievement of objectives. Clear objectives, identification of risks, risk management Control Environment “Tone at the top”; intolerance of unethical behavior at all levels Integrity, ethical values, management style, organizational structure, authority and responsibility, policy and procedures Information and Communication Financial Reporting Assertions: E – Existence, C – Completeness, O – Ownership, V – Valuation, and P - Presentation Abbreviation Assertion Financial Statement Assertions E Existence C Completeness O Ownership V Valuation P Presentation Description These assertions deal with whether assets, liabilities, and equities included in the financial statements actually existed on the balance sheet date and whether revenues and expenses included in the financial statements actually occurred during the accounting period. These assertions state that all transactions and accounts that should be included in the financial statement are included. These assertions deal with whether assets are the rights of an entity and obligations of an entity at a given date. These assertions deal with whether asset, liability, equity, revenue, and expense components have been included in the financial statements at appropriate amounts. These assertions deal with whether components of the financial statements are properly classified, described, and disclosed in the financial statements. Page 18 of 18


![[Date] [Policyholder Name] [Policyholder address] Re: [XYZ](http://s3.studylib.net/store/data/008312458_1-644e3a63f85b8da415bf082babcf4126-300x300.png)
![waiver of all claims [form]](http://s3.studylib.net/store/data/006992518_1-099c1f53a611c6c0d62e397e1d1c660f-300x300.png)