CCNA 2 Skills-Based Assessment

CCNA 2 Skills-Based Assessment
Student name _____________________ Date _________________ Start time ____________
Circle one:
Location: Anniston or Boaz
Circle one:
Version 1 2 3 4 5 6 7 8 9 10
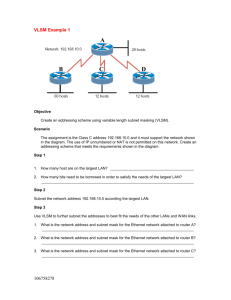
Anniston 3 192.168.3.0 /24 192.168.3.1 3
Instructor provided information: (given by the teacher/instructor)
The WAN IP network address is 192.168.3.0
with a subnet mask of
255.255.255.0 (but take the less bit’s nececcary for your subnets)
The local LAN has been assigned an IP network address of
14.38.20.0
Each subnet of the above network needs to accommodate 14 host addresses.
Use the 3th usable subnet for the LAN. Do not use subnet zero as the first subnet.
The IGRP AS number is 3 .
14 hosts 2^4 = 16 (-2 not usable) 14 usable ip’s 4 bits to use :
192.168.3.16 is the first usable subnet
This exam will occur in stages. Each element is a set of instructions that needs to be accomplished.
The instructor will initial each task as it is completed. Proceed to the next task only after the instructor has approved the current task.
The six elements of this exam are:
1. Basic planning
2. Security planning
3. Cabling
4. Basic configuration
5. Security configuration
6. Troubleshooting
The scenario is that Gadsden (GAD) is regional headquarters of the company. Anniston and
Boaz are branch offices. Each network associate (student) will be responsible for a single branch office. The internetwork team leader (instructor) is responsible for the regional router
(GAD). A network address and specific number of hosts per subnet has been assigned for the local LAN. From the instructor provided information, the subnet address, the subnet mask, the first and last usable addresses, and the broadcast address for each site’s LAN need to be determined.
CCNA 2 Hands-on Version Assignment
Router Segment Final Version
Router segment Final version
Anniston
Anniston number
1
2
Anniston
Anniston
Anniston
Anniston
Anniston
Anniston
Anniston
Anniston
Boaz
Boaz
Boaz
Boaz
3
4
5
6
7
8
9
10
1
2
3
Boaz
Boaz
Boaz
4
5
6
7
Boaz
Boaz
Boaz
8
9
10
Wan network address
Gad router interface address
192.168.1.0 /24
192.168.2.0 /24
192.168.3.0 /24
192.168.4.0 /24
192.168.5.0 /24
192.168.6.0 /24
192.168.1.1
192.168.2.1
192.168.3.1
192.168.4.1
192.168.5.1
192.168.6.1
192.168.7.0 /24
192.168.8.0 /24
192.168.9.0 /24
192.168.10.0 /24
192.168.7.1
192.168.8.1
192.168.9.1
192.168.10.1
192.168.1.101 /24 192.168.101.1
192.168.2.102 /24 192.168.102.1
192.168.3.103 /24 192.168.103.1
192.168.4.104/24 192.168.104.1
192.168.5.105 /24 192.168.105.1
192.168.6.106 /24 192.168.106.1
192.168.7.107 /24 192.168.107.1
192.168.8.108 /24 192.168.108.1
192.168.9.109 /24 192.168.109.1
192.168.10.110 /24 192.168.110.1
Igrp as
Step 1: Basic Planning
Time: 20 minutes Points __________________
Using the chart below, plan the first 10 usable subnets of the LAN network address that was
5
6
7
8
1
2
3
4
9
10
101
102
103
104
105
106
107
108
109
110
1
2
3
4
5
6 provided by the instructor.
Subnet Subnet address
14.38.20.0
Subnetmask (/X)
/16
14.38.10.16 /16
14.38.10.32 /16
14.38.10.48 /16
14.38.10.64 /16
14.38.10.80 /16
First host
14.38.20.1
Last host broadcast
14.38.20.14 14.38.20.15
14.38.10.17 14.38.10.30 14.38.10.31
14.38.10.33 14.38.10.46 14.38.10.47
14.38.10.49 14.38.10.62 14.38.10.63
14.38.10.65 14.38.10.78 14.38.10.79
14.38.10.81 14.38.10.94 14.38.10.95
7
8
14.38.10.96 /16
14.38.10.112 /16
14.38.10.97 14.38.10.110 14.38.10.111
14.38.10.113 14.38.10.126 14.38.10.127
9
10
14.38.10.128 /16
14.38.10.144 /16
14.38.10.129 14.38.10.142 14.38.10.143
14.38.10.145 14.38.10.156 14.38.10.159
The WAN interface of GAD is assigned the lowest usable address in the subnetwork.
Identify and use the second lowest usable WAN address for the S0, or S0/0, interface of the assigned router 192.168.3.2 For security reasons, the IP addresses of the assigned subnet are split in two groups. The production workstations will be assigned the lower half of the IP addresses. The network devices and management stations will be assigned the upper half of the
IP addresses. The Ethernet router interface is to be assigned the highest usable address.
Identify the required IP address of the Ethernet interface on the assigned router.
14.38.10.33 (based on exam version number and subnet assignment)
The host configurations must also be planned. Using the chart below, complete the host information.
Branch: Anniston or Boaz
IP address range 3th subnet : from ip 14.38.10.33 to ip 14.38.10.46 + 1 broadcastaddress ip Bytes bits
So 14.38.10.33 14.38.10. 00010001
14.38.10.34 14.38.10. 00010010
14.38.10.35 14.38.10. 00010011
14.38.10.36 14.38.10. 00010100
14.38.10.37 14.38.10. 00010101
14.38.10.38 14.38.10. 00010110
14.38.10.39 14.38.10. 00010111
14.38.10.40 14.38.10. 00011000
14.38.10.41 14.38.10. 00011001
14.38.10.42 14.38.10. 00011010
14.38.10.43 14.38.10. 00011011
14.38.10.44 14.38.10. 00011100
14.38.10.45 14.38.10. 00011101
14.38.10.46 14.38.10. 00011110
14.38.10.47 14.38.10. 00011111 (this is broadcast and don’t count for ip-address)
Production Host Range(Lower half) ip Bytes bits
So 14.38.10.33 14.38.10. 00010001
14.38.10.34 14.38.10. 00010010
14.38.10.35 14.38.10. 00010011
14.38.10.36 14.38.10. 00010100
14.38.10.37 14.38.10. 00010101
14.38.10.38 14.38.10. 00010110
14.38.10.39 14.38.10. 00010111
Management Host Range(Upper half) ip Bytes bits
So 14.38.10.40 14.38.10. 00011000
14.38.10.41 14.38.10. 00011001
14.38.10.42 14.38.10. 00011010
14.38.10.43 14.38.10. 00011011
14.38.10.44 14.38.10. 00011100
14.38.10.45 14.38.10. 00011101
14.38.10.46 14.38.10. 00011110
14.38.10.47 14.38.10. 00011111
Production Host ( take the first usable ip address)
IP address 14.38.10.34 coz 14.38.10.33 is for the fastethernet interface of the LAN router
Subnet Mask 255.255.255.0
Default Gateway 192.168.3.2
Management Host
IP address 14.38.10.40
Subnet Mask 255.255.255.0
Default Gateway 192.168.3.2
Step 2: Security Planning
Time: 30 minutes Points __________________
There are several security concerns in the internetwork. Develop Access Control Lists (ACLs) to address security issues. The following are the concerns: putting up your EIGRP:
Because some routers of sisco aren’t all the same they don’t all support IGRP that’s why you have to use RIP or EIGRP. EIGRP you could use the same as IGRP!
I shose EIGRP
enable
router1#config t
(config-f)#router1 eigrp 25 ( this number is for your autonomisch system if you have more than 1 access-list you have more routers to configure you have to put each time the same number!)
(config-router)# network 14.38.10.0
(config-router)# network 192.168.3.0
This you do also for your GAD router! But only these:
(config-f)#router1 eigrp 25
(config-router)# network 192.168.3.0 this is because you have only to make the left or the right part of the network construction. You have or Anniston or Boaz so you don’t have to be able to ping from a pc of the subnet of boaz to a pc of the subnet of Anniston.
1. The company has an Intranet Web server host that all systems can reach at IP address
172.16.0.1 with only HTTP access. No other protocols will be permitted to this site.
2. The company also has a server pool in the 209.0.0.0/24 network. The server pool addresses are divided in half. The servers in the upper half of the address range are reachable only by management hosts using all possible IP protocols. The servers in the upper half of the address range are not reachable by production hosts using all IP protocols The servers in the lower half of the address range are reachable by all LAN hosts using all possible IP protocols. The servers should not be accessible by any other hosts.
3. The company has discovered an Internet Web server at 198.0.0.1 that is known to contain viruses. All hosts are to be banned from reaching this site.
2)
3
4
4. All other traffic should be permitted to any destination. These security requirements should be accomplished with a single access list. Plan the access list required to accomplish these tasks, to which interface this will be applied, and the direction the list will be applied.
Place the ACL plan information below:
1) access-list 101 permit tcp 127.16.0.1 255.255.255.255 any eq 80 access-list 101 deny ip 172.16.0.1 255.255.255.255 any this is the hardest acl-instruction and I can ’t make it sorry access-list 101 deny ip host 198.0.0.1 255.255.255.255 any access-list 101 permit ip any any
Step 3: Cabling
Time: 10 minutes Points __________________
I hope you can do this !
Step 4: Basic Configuration
Time: 15 minutes Points _________________
Apply a basic configuration to the router. This configuration should include all the normal configuration items. These items include but are not limited to router name, passwords, interface descriptions, routing, host table, and a banner to be displayed before login.
The management workstation and the production workstation should also be configured with the appropriate information. Routing and connectivity should be verified before notifying the instructor. Before proceeding to the next step have the instructor approve this step.
Router Anniston
Enable
router1# config t
config-t# hostname Anniston
config-t# interface fastethernet 0/0
config-int# ipaddress 14.38.20.33 255.255.255.0
config-int#no shutdown
config-int# exit
config-t# interface serial 0/0
config-int# ipaddress 192.168.3.2
config-int# no shutdown
you don’t have to set the clockrate because the DTE is on the side of GAD and
GAD is configured by the teachers!
Step 5: Security Configuration
Time: 15 minutes Points _______________
After the basic functionality is in place, security needs to be added to the configuration. Using the security requirement and planning from previous steps, implement and test these basic security functions. The listed security requirements should be verified before notifying the instructor. Before proceeding to the next step have the instructor approve this step.
implementing the acl
enable
anniston#config t
config-t# interface serial 0/0
config-int# ip-accessgroup 101 in
if you use IN then you will set the statements within your subnet!, everything that is going out of your subnet that will be checked by your acl! If you use OUT you do the same with alle traffic that enters you subnet!
Step 6: Troubleshooting
Time: 10 minutes Points __________________
the teacher will ask you to leave for a couple off minutes and will change something to your configuration. You will have to correct the mistake so your network works proper again.
Some handy commands:
Show running-config
Show ip route show interfaces